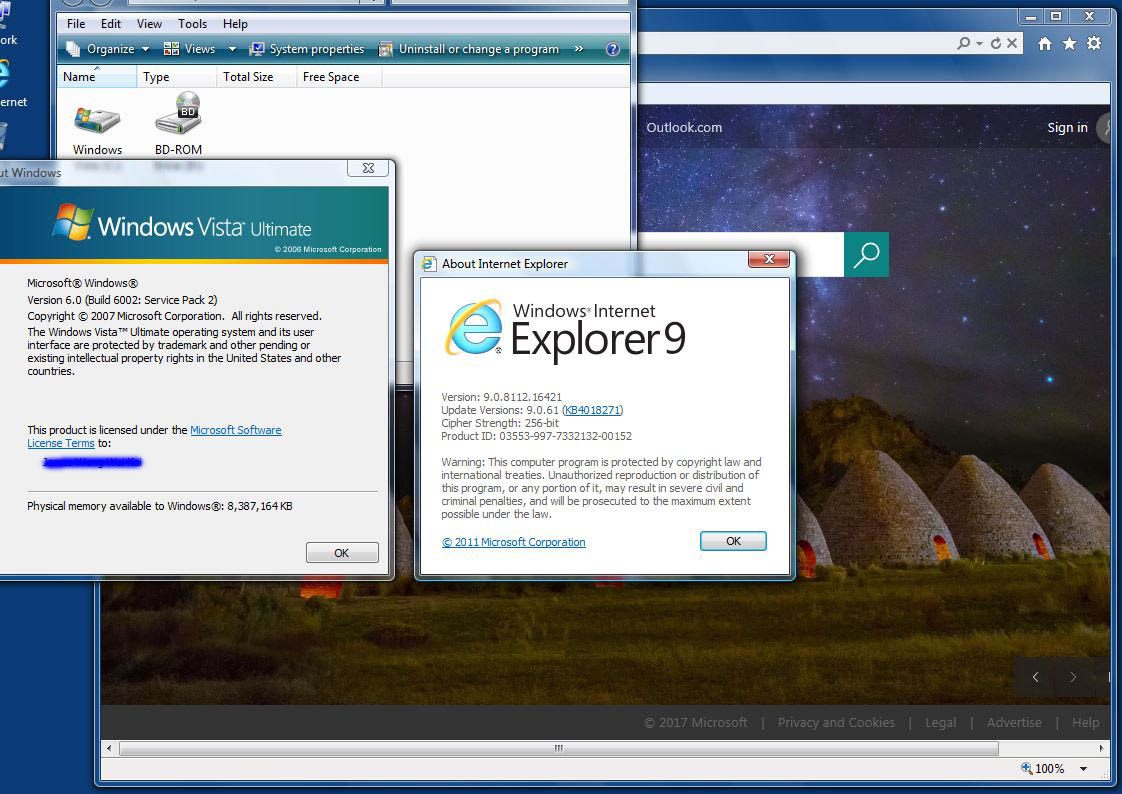
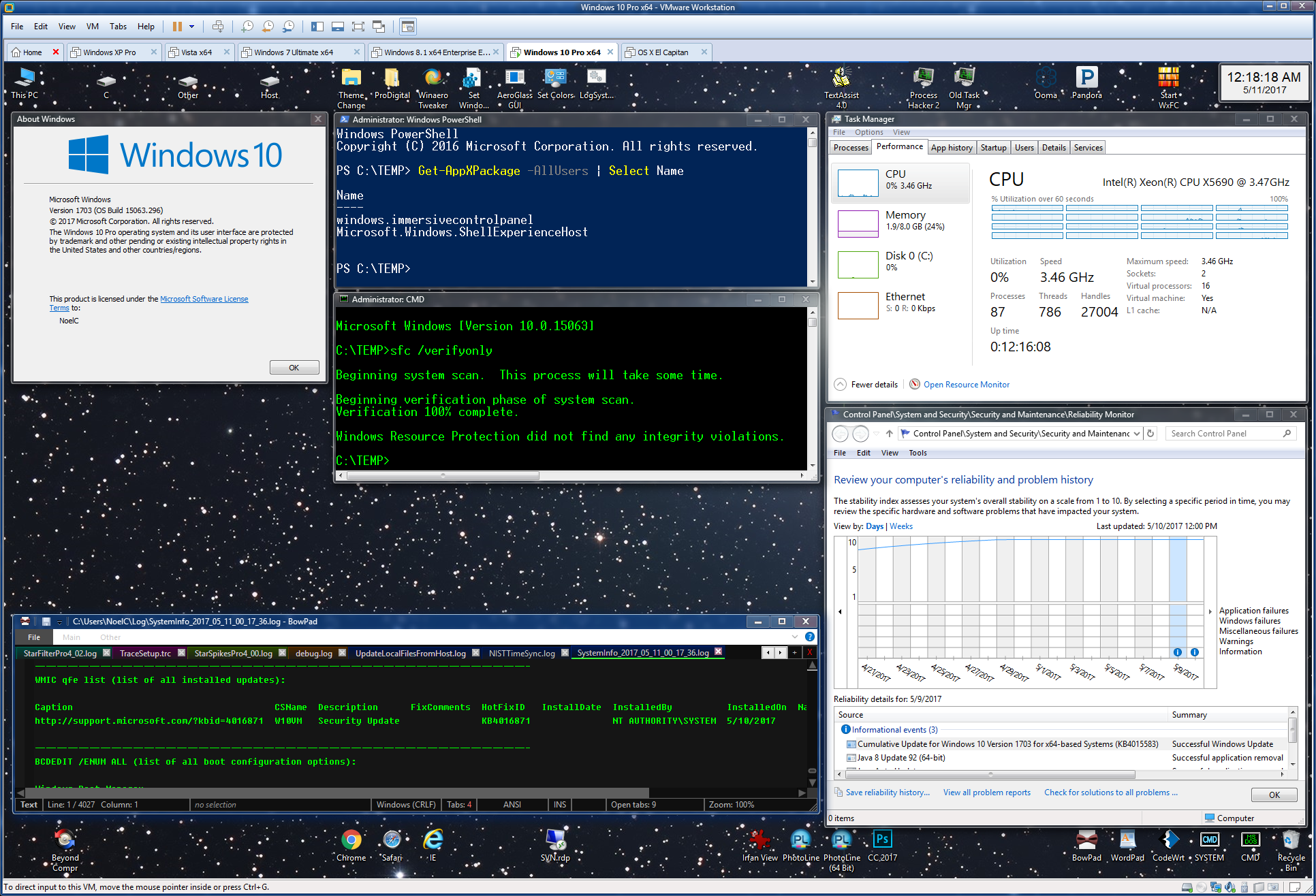
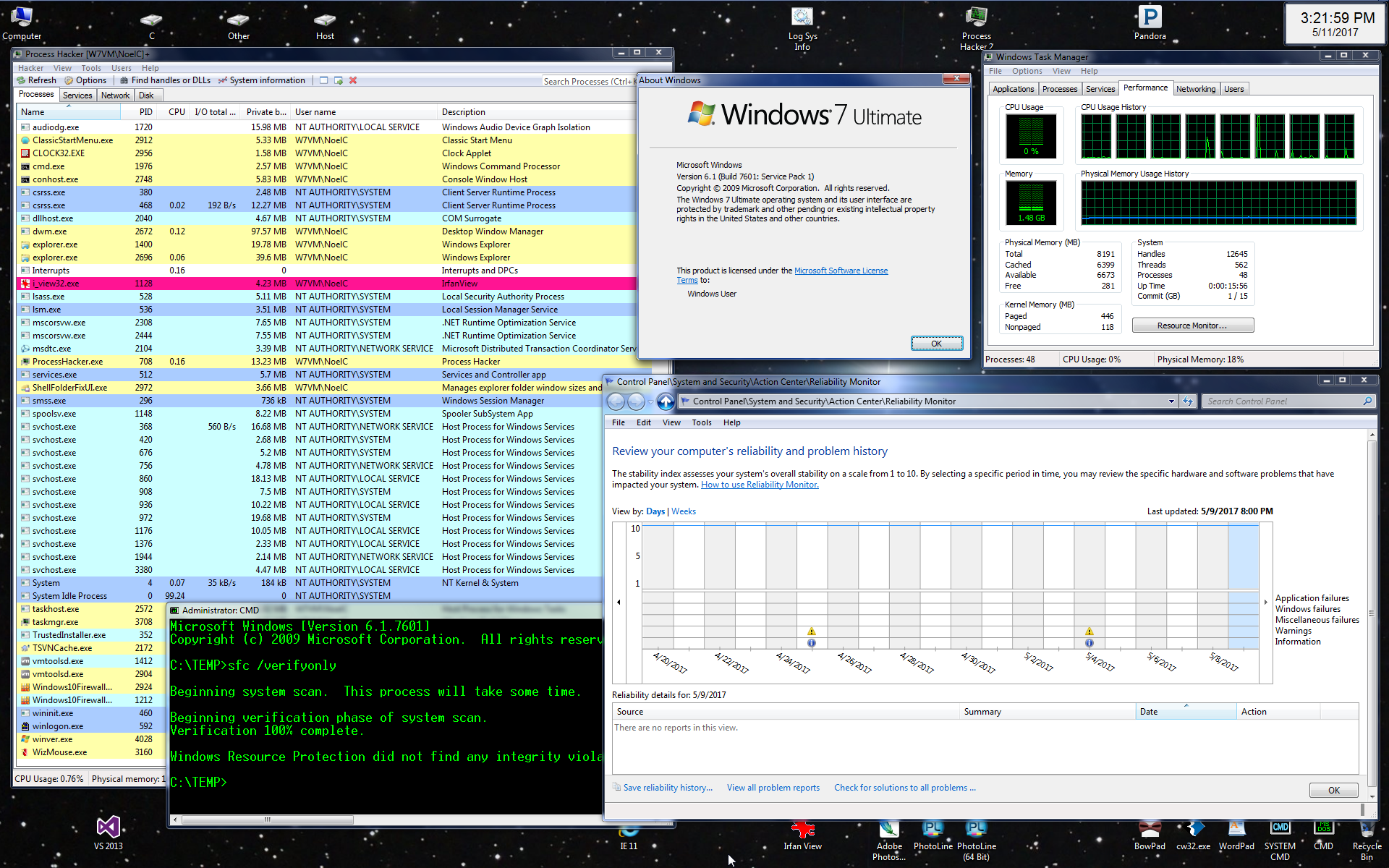
I count 243 updates in the Security Update Guide. Release Notes for May are out, too. I don’t see any vestiges of the promised “delta only” patches fo
[See the full post at: Patch Tuesday is rolling out]

|
Patch reliability is unclear. Unless you have an immediate, pressing need to install a specific patch, don't do it. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
-
Patch Tuesday is rolling out
Home » Forums » Newsletter and Homepage topics » Patch Tuesday is rolling out
- This topic has 143 replies, 30 voices, and was last updated 7 years, 7 months ago.
AuthorTopicViewing 61 reply threadsAuthorReplies-
NetDef
AskWoody_MVPMay 9, 2017 at 12:14 pm #113649Woody, remember the odd prefix labeling we saw last week for KB3150513? We’re seeing that label on the Windows 10 Adobe Flash patch today. And yes, it’s really messing with my lists while I go through to decide what’s getting approved or not . . .
I suspect MS has a new hire in the documentation department that’s not yet gotten fully integrated into the concept of standardization. Consistency would be golden . . .
2017-05 Security Update for Adobe Flash Player for Windows 10 Version 1607 for x64-based Systems (KB4020821)
~ Group "Weekend" ~
-
NetDef
AskWoody_MVPMay 9, 2017 at 12:29 pm #113656On second thought: If they keep this new labeling “standard” and if they started using it for all other patches in the future, it would actually be helpful. But this month it’s inconsistent and not applied to all patches.
Yeah . . . I get told I’m a bit OCD all the time . . .
~ Group "Weekend" ~
5 users thanked author for this post.
-
remco8264
AskWoody Plus -
Noel Carboni
AskWoody_MVPMay 9, 2017 at 7:32 pm #113787I get told I’m a bit OCD all the time . . .
Yeah but…
Details actually DO matter.
-Noel
-
-
PKCano
Managerabbodi86
AskWoody_MVPMay 9, 2017 at 12:50 pm #113664The “delta only” patch for Win10 1607? you mean this?
http://www.catalog.update.microsoft.com/Search.aspx?q=KB4019472Win10 1703 also got one
1 user thanked author for this post.
MrBrian
AskWoody_MVPMrBrian
AskWoody_MVPMay 9, 2017 at 1:14 pm #113686Reminder of past topic: Installing Win updates on Win 7 or 8.1 computers with Kaby Lake or Ryzen CPUs.
1 user thanked author for this post.
MrBrian
AskWoody_MVPMay 9, 2017 at 1:20 pm #113688The May 2017 security-only updates for Windows 7 and 8.1 include an updated version of file msado15.dll. File msado15.dll is referenced as a non-security fix for Windows 7 and 8.1 in the May 2017 monthly rollups (“Addressed issue where, after installing security update KB______, applications that use msado15.dll stop working.”)
-
abbodi86
AskWoody_MVP
MrBrian
AskWoody_MVPMay 9, 2017 at 1:27 pm #113694From Coming together to address Encapsulated PostScript (EPS) attacks:
“Today’s security updates include three updates that exemplify how the security ecosystem can come together to help protect consumers and enterprises. We would like to thank FireEye and ESET for working with us.
Customers that have the latest security updates installed are protected against the attacks described below. As a best practice to ensure customers have the latest protections, we recommend they upgrade to the most current versions.”
MrBrian
AskWoody_MVPMay 9, 2017 at 1:43 pm #113699From Announcing the .NET Framework 4.7 General Availability (May 2, 2017):
“Today, we are announcing the general availability of the .NET Framework 4.7. The .NET Framework 4.7 was released as part of Windows 10 Creators Update a month ago. You can now install the .NET Framework 4.7 on other versions of Windows.”
1 user thanked author for this post.
-
EP
AskWoody_MVPMay 9, 2017 at 6:43 pm #113779A few caveats about .NET Framework 4.7 MrBrian – you can only find this download at the Microsoft Download Center (just like with the full .NET 4.6.2 package):
(web installer)
https://www.microsoft.com/en-us/download/details.aspx?id=55170(full offline installer)
https://www.microsoft.com/en-us/download/details.aspx?id=55167.NET Framework 4.7 WPF features take a dependency on D3DCompiler_47.dll . This D3DCompiler_47.dll is not present by default in Windows 7 SP1, Windows 2008 R2 SP1 and Windows 2012 OS platforms. Hence these OS platforms require D3DCompiler_47.dll to be installed for .NET Framework 4.7 WPF features to work as expected. Please see known issues article for D3DCompiler_47.dll install information details.
You will need the KB4019990 D3DCompiler_47.dll update for Win7 SP1 if you want to install .NET Framework 4.7 under Windows 7.
anonymous
GuestMay 9, 2017 at 1:43 pm #113698I’m noticing on my WSUS server that all of the Win server 2016 patches are missing for May. Meaning that any patch for any product targeted for Win 2016 was not synchronized. Such as the OS patch, .NET, etc. I’ve rechecked all of the long-standing settings and they are as they should be.
Is anyone else seeing this?
Thanks,
A non-moose cow-herd
-
ch100
AskWoody_MVP -
abbodi86
AskWoody_MVPMay 9, 2017 at 3:28 pm #113743https://support.microsoft.com/en-us/help/894199
Cumulative Update for Windows 10 Version 1607 and Windows Server 2016 (KB4019472)
Deployment: Catalog
-
NetDef
AskWoody_MVPMay 9, 2017 at 3:27 pm #113742I’m noticing on my WSUS server that all of the Win server 2016 patches are missing for May. Meaning that any patch for any product targeted for Win 2016 was not synchronized. Such as the OS patch, .NET, etc. I’ve rechecked all of the long-standing settings and they are as they should be. Is anyone else seeing this? Thanks, A non-moose cow-herd
Yes, and this has happened several times in the past for us for Server 2016 and Server 2012 R2. I’m expecting them to hit WSUS later this week.
~ Group "Weekend" ~
1 user thanked author for this post.
anonymous
Guestanonymous
GuestMay 9, 2017 at 2:25 pm #113711Sorry for posting as “anonymous”, but there is a question that is worrying me and which answer, I suspect, might be also of more general interest:
I have Windows 7 Professional x64, with Windows Update set to “tell me but do not install”, and these two options:
(1) To install the “Security Monthly Quality Rollup” I am being offered right now through Windows Update (after waiting a few days to hear about any problems that might crop up.)
(2) Manually install the “Security Only Quality Update” plus the “Cumulative Security Update for Internet Explorer 11”, which I have downloaded already, just in case (1) turns out to be a worse idea.
Both, of course “for Windows 7 x64.”What, if any, is the difference between both options?
For example:
Would the “Security Monthly Quality Rollup” include also nagware and telemetry software?Thank you all in advance.
Oscar L. Colombo
-
PKCano
ManagerMay 9, 2017 at 2:43 pm #1137231) To install the “Security Monthly Quality Rollup” I am being offered right now through Windows Update (after waiting a few days to hear about any problems that might crop up.)
The “Security Monthly Quality ROLLUP” contains three parts – the non-security patch, the security patch, and the cumulative patch for IE11. It is cumulative.
The “Security Only Quality UPDATE” contains only security patches and is is NOT cumulative.
If yoy have been installing the “Security Monthly Quality ROLLUP” through Windows Update each month since November 2016, you should go ahead and install the May ROLLUP.
If you have NOT been installing the ROLLUPS, and this is the one for October or November 2016, let us know and we can provide instructions for using the ‘Security Only Quality UPDATES.” -
woody
ManagerMay 9, 2017 at 2:47 pm #113727Right now, don’t do anything.
It’s much, much too early to tell if there are any problems with this enormous crop of patches.
Watch the MS-DEFCON level. When the time comes, your options should be more obvious.
A bit of a spoiler, though: I’m coming around to the idea that most people should be installing the Monthly Rollup, then wiping out as much of the snooping as they can, after the fact.
Note that I don’t say “everybody.” But for a whole lot of people, Group B has become difficult.
-
zero2dash
AskWoody LoungerMay 9, 2017 at 4:57 pm #113757A bit of a spoiler, though: I’m coming around to the idea that most people should be installing the Monthly Rollup, then wiping out as much of the snooping as they can, after the fact.
Is this even possible, and how?
I was under the impression that because of how these are structured, it’s “take it or leave it”. You get the update, it’s 1 KB, it installs everything. Or, you refuse it, and grab Security-Only which is also 1 KB file, but without the wicked aftertaste.I’ve relegated to Security-Only, and I’m starting to lean to “nothing” (group W) anyway.
1 user thanked author for this post.
-
The Surfing Pensioner
AskWoody PlusMay 9, 2017 at 7:21 pm #113785I wish I could understand what is supposed to be difficult about updating Group B-style. For me, updating has never been so quick and easy as it is now – largely thanks to the guidance I have found on this site, of course. On the other hand, the thought of installing monthly rollups and then trying to pick out the telemetry makes my hair stand on end. Is there any way of knowing whether extracting elements of a composite kb is not going to cause problems – possibly massive problems – further down the line?
-
anonymous
GuestMay 12, 2017 at 6:11 pm #114642There is simply no parallel universe in which having a 5-10 email conversation with everyone on my network about when it’s safe to let Windows Update patch and hand holding step by steps on what needs to be dug into and disabled is going to be EASIER for me than to upload patches as I install them for myself and ask everyone once to check their network folder once a day for anything new to install on their end.
-
-
-
Ascaris
AskWoody MVPMay 10, 2017 at 5:44 am #113895A bit of a spoiler, though: I’m coming around to the idea that most people should be installing the Monthly Rollup, then wiping out as much of the snooping as they can, after the fact.
Me too. I’d been doing the security-only updates since the first rollup with snooping rolled out, but I do want the bug fixes too. It’s not that the security-only updates are difficult, per se… they’re less convenient than the rollups since those are handled automatically by Windows Update, but it’s not hard to see this month’s rollup arrive in Windows Update, click the link for more information, then follow the link in that page to the equivalent security-only update. Install it, and only then hide the rollup (sort of like checking that month off the list). I haven’t had any issues doing it that way, though I must also add that I only did that for about five patch Tuesdays.
I switched to downloading the full rollups a month or two ago (8.1), then obliterated the telemetry stuff the best I could using abbodi86’s guide. After that, I’ve watched on Wireshark to see if there is any telemetry left, and so far I have not seen anything that definitely seems like it is. Some connections to MS I do want, like CRL download requests, Windows update checks, stuff like that, and I do see those happening. The volume of data sent to MS is quite low, so if there is still telemetry going on, it’s very sparse. If I had to guess, I’d say that the unwanted telemetry isn’t happening.
Dell XPS 13/9310, i5-1135G7/16GB, KDE Neon 6.2
XPG Xenia 15, i7-9750H/32GB & GTX1660ti, Kubuntu 24.04
Acer Swift Go 14, i5-1335U/16GB, Kubuntu 24.04 (and Win 11)1 user thanked author for this post.
-
ch100
AskWoody_MVP
-
ch100
AskWoody_MVPMay 9, 2017 at 2:49 pm #113729We are in for a big treat this month.
Huge rollups superseding tons of older updates.
Looks like the rollup of exactly 1 year ago for Windows 7/2008 R2 in a new version, this time released for Windows 8.1/2012 R2 in addition to Windows 7/2008 R2.
Hope it will all work well for everyone.
Just do not install yet if you are not confident enough that you can recover from any undesired side-effects.4 users thanked author for this post.
-
ch100
AskWoody_MVPMay 10, 2017 at 6:05 am #113899I did a bit more testing with the current patches for Windows 7/2008R2 and 8.1/2012R2.
Each of them, but in particular the Windows 8.1/2012R2 versions supersede a very large number of older patches. Add to this the recent maintenance done by Microsoft on the update servers when they expired about 300 old updates from each operating system discussed here – nothing in this post applies to Windows 10.
However, there is a subtle difference between current patches and KB3125574.
After installing KB3125574 on a fully patched system and running Disk Cleanup, the number of installed patches on a typical Windows 7 system drops from about 200 to between 80-100.
After installing the current patches, only less than 10 older updates are removed by Disk Cleanup and the total number stays somewhere in the range of 190 for each operating system. I don’t know why if so many old patches are claimed to be superseded.
Anyway, the rollup system started in October 2016 (according to Microsoft it is in fact in place since July 2016) is getting traction slowly, but it needs more work to be completed.
https://support.microsoft.com/en-us/help/4009469/windows-7-sp1-windows-server-2008-r2-sp1-update-history
https://support.microsoft.com/en-us/help/4009470/windows-8-1-windows-server-2012-r2-update-historyOn the positive side, after the massive maintenance done few days ago and another big round of expiring patches done few months ago, I think there should be no more issues with slow Windows Update on systems installed cleanly from the ISO with the relevant SP or Updates, or even from the very original gold images.
3 users thanked author for this post.
-
Ascaris
AskWoody MVPMay 10, 2017 at 6:15 am #113901Just do not install yet if you are not confident enough that you can recover from any undesired side-effects.
Backups… always backups!
I’m pretty fanatical about my backups. I’ve used Norton Ghost, and I’ve probably got about nine Acronis True Image licenses accumulated by now, and I’ve used free ones too (Macrium Reflect’s free version remains a great choice). Prior to that, I used to have a Jumbo 350 tape backup drive, and before that… 1.44MB floppies and pkzip.exe.
I’ve only had to use backups for disaster recovery a handful of times (keeping in mind that I’ve been using PCs since 1990): Once when a laptop was stolen (by people I was trying to help… grrrr), a few times when hard drives failed, and maybe once or twice that I managed to foul something up badly.
That would be reason enough to insist on backups, but I use them for things beyond recovering from catastrophic loss. If something goes wrong and Windows starts acting funny, it’s easier to just restore the system partition (data is on another volume) and not worry about it. I could fix it, but restoring the system partition takes about 9 minutes on my laptop and less than that on my desktop, and I can do something else while it’s going on.
I have also used backups for non-catastrophic hard drive/SSD replacement, and for setting up test cases that I want to do on a specific machine (and thus not something that would lend itself to a VM). Just grab my most recent backup image, stick it on whatever spare hard drive I want to use (if you’re like me, you’ve accumulated a bunch of them that are too small to be primary drives anymore, but they still work), install that (or pop it into my USB 3 external enclosure), and do whatever I want without concern for messing up my “real” drive.
Dell XPS 13/9310, i5-1135G7/16GB, KDE Neon 6.2
XPG Xenia 15, i7-9750H/32GB & GTX1660ti, Kubuntu 24.04
Acer Swift Go 14, i5-1335U/16GB, Kubuntu 24.04 (and Win 11)4 users thanked author for this post.
-
ch100
AskWoody_MVPMay 10, 2017 at 6:30 am #113904Sometimes is useful to “burn your bridges” to move ahead because of not having any other alternative. The expression comes from an ancient event when a military commander physically burnt the return bridges (or the boats on which himself and his soldiers arrived at the destination according to other sources) to convince his soldiers that there is no other way than winning. 🙂
Not recommended for everyone though…1 user thanked author for this post.
-
woody
Manager
-
-
-
James Bond 007
AskWoody LoungerMay 10, 2017 at 8:00 am #113926If something goes wrong and Windows starts acting funny, it’s easier to just restore the system partition (data is on another volume) and not worry about it. I could fix it, but restoring the system partition takes about 9 minutes on my laptop and less than that on my desktop, and I can do something else while it’s going on.
I have also used backups for non-catastrophic hard drive/SSD replacement, and for setting up test cases that I want to do on a specific machine (and thus not something that would lend itself to a VM).
Yeah, I agree that if Windows starts having obscure problems, it is easiest to just restore from a recently created image known to be problem-free, instead of trying to find what problems there are. Images are also useful for transferring Windows installations from one drive to another. With a SSD as boot drive the restore process is quick.
I use Acronis True Image (2011 to 2016) myself. For the X99 systems I am using, I find that only Boot CDs created by the 2016 version are able to recognize the hardware and successfuly launch the program. For the older Sandy Bridge and Ivy Bridge hardware I use a Boot CD created by the 2011 version. I keep the CD isos created by Acronis so that if the CDs fail I can recreate one easily.
Hope for the best. Prepare for the worst.
anonymous
GuestMay 9, 2017 at 4:34 pm #113754Would anyone mind summarizing whether KB4020513 is necessary to install or not? I can’t get the https://support.microsoft.com/kb/4020513 page to load on this computer. They always come up as a blank white page and I have been unable to figure out the cause in order to read that site myself.
It is listed as non-security related to .Net 3.5.1. Only a small file.
Thank you.
-
Kirsty
ManagerMay 10, 2017 at 12:41 am #113849The page you link gives this information:
This article describes an update for the .NET Framework 3.5.1 on Windows 7 and Windows Server 2008 R2. The update fixes the issue that is described in Knowledge Base article 4020459 for customers who experience “privilege not held” errors after the April 2017 security updates from CVE-2017-0160 are applied.
I have found occasional problems loading MS Support pages in Firefox ESR, but find if I try again, it usually works, eventually 🙂

PKCano
ManagerMay 9, 2017 at 4:38 pm #113756About that patch MS says
“This article describes an update for the .NET Framework 3.5.1 on Windows 7 and Windows Server 2008 R2. The update fixes the issue that is described in Knowledge Base article 4020459 for customers who experience “privilege not held” errors after the April 2017 security updates from CVE-2017-0160 are applied.”KB4020459 says
“After you apply the April 2017 security updates described in Microsoft security update guidance <u>CVE-2017-0160</u>, the PowerShell v3.0+ stop-computer command fails. You get a “Privilege not held” error message.”JNP
AskWoody LoungerMay 9, 2017 at 6:24 pm #113774I know it is an extremely small cohort, those running Windows XP in LTSB, but there appears to be, at least with my XPLTSB running in a virtual machine, a problem with: May, 2017 Security and Quality Rollup for .NET Framework 4 on WES09 and POSReady 2009 (KB4014605). It will neither install with WU or as a download of the file to be executed manually from the hard drive: http://www.catalog.update.microsoft.com/Search.aspx?q=kb4014605 . If you have Win XPLTSB set to load automatically, consider disabling and going to notify me of updates. Then download the updates, select custom install, and deselect KB4014605. Installation should proceed normally thereafter of the other XPLTSB updates and then you can see if your experience matches mine with regard to KB 4014605.
-
BusinessSellCanada
AskWoody LoungerMay 12, 2017 at 7:13 pm #114663
anonymous
GuestMay 9, 2017 at 7:36 pm #113786Once more as “anonymous”:
Thanks, particularly to PKCano for listing the three components of the Security Monthly Quality Rollup, and for his offer:
“If you have NOT been installing the ROLLUPS, and this is the one for October or November 2016, let us know and we can provide instructions for using the ‘Security Only Quality UPDATES.”
Well, I have NOT installed any of the Rollups so far, but I am being offered the May 2017 one through Windows Update.Concretely now: what does one might gain by installing the Rollup rather than the Security Only plus the Explorer 11 Security Updates, and what might be lost?
Finally, let me try this once more: Is the “Non Security” component of the Rollup likely to include nagware and MS spy-telemetry software, or only harmless if, to many of us, largely useless tweaks to obscure features, such as correcting the setting for the time of day in Uttar Pradesh?
Thanks,
Oscar L. Colombo
-
PKCano
ManagerMay 9, 2017 at 7:54 pm #113790Woody has created “Groups” related to the telemetry in Windows Update.
Group A accepts whatever Microsoft offers. Group B doesn’t install the telemetry-containing updates and opts to instead manually install the Security-Only Updates. This started in October os 2016 when MS started rolling up all the patches into one ROLLUP.The Security Only Updates are not cumulative, so you have to manually install a new one each month. In addition, since March 2017 there is an additional update for IE11 that has to be installed manually. Then, you avoid the Monthly Rollup by UNCHECKING it, and install the rest of the updates (waiting until Woody gives the go-ahead that they are safe by changing the DEFCON number to 3 or above). You can read about this system in AKB2000003
Security Only patches and those for IE11 from Oct 2016 through April 2017 are safe to install. The May patches are on hold until the DEFCON number is 3 or above.
1 user thanked author for this post.
anonymous
GuestMay 9, 2017 at 8:10 pm #113763Since many people had issues with figuring out what .NET updates they need, here is my methodology to help you out.
What is the main article describing .NET Framework Patches?
For this month it’s 4019108.
OK, what version of .NET do I have installed on my Windows 7 x64 Machine?
For my case it’s 3.5.1 and 4.6.2. If you are unsure about this you can use Asoft’s .NET Version Detector.
What Updates from that list do I need then?
KB4014579 and KB4014588.
Noted. Onto the Microsoft Catalog and search has to be done on the initial KB, KB4019108.
Clicking on the download button brings up the list of 4 hotfixes out of which I only need the 2 compatible with my machine’s .NET Framework versions: KB4014579 and KB4014588.
And that’s it 🙂 Granted if you have updated from 4.6.2 to 4.7 you will only need 1 update since there are no security hotfixes for 4.7 released. Yet 🙂 This methodology can easily be extrapolated for any other Windows version, like 8.1. As long as you know your correct KB starting point and properly identify your .NET versions, it should be a breeze if you follow the guidelines above.
MrBrian
AskWoody_MVPMay 9, 2017 at 9:37 pm #113803JohnW
AskWoody LoungerMay 9, 2017 at 10:40 pm #113827My solution these days …
Windows 7 – if it’s optional, don’t install.
Windows 10 – hold nose and open up the chute! 🙂

Windows 10 Pro 22H2
1 user thanked author for this post.
anonymous
GuestMay 10, 2017 at 12:14 am #113836In early April I was catching up on updates and installed these two
with no problems:Security Update for Windows March -(KB4012212)
Windows Malicious Software Removal Tool (KB890830)I checked your blog for info on the .Net patch and saw the “lockdown”
notice advising people to hold off patching so I waited. I then got
called away on important business and am now catching up again.I will hold off on the May updates but can you give me the links to the
Win 7 updates for March and April I need. I imagine the .Net for both
and the Security only for April.
Thanks
– firemind.-
Kirsty
ManagerMay 10, 2017 at 12:31 am #113847For the Win 7 March and April updates, see AKB2000003 – also check out the IE updates on that page.
This page has the April Security Only .net update links.

samak
AskWoody PlusMay 10, 2017 at 1:54 am #113856I wish I could understand what is supposed to be difficult about updating Group B-style. For me, updating has never been so quick and easy as it is now – largely thanks to the guidance I have found on this site, of course. On the other hand, the thought of installing monthly rollups and then trying to pick out the telemetry makes my hair stand on end.
Agreed. I think a lot of habitual non-techie visitors to this site have come to understand and be comfortable with the Group B system. This was well-demonstrated on a different thread. We’re happy with it, our computers are working well, don’t change it.
Windows 10 Home 22H2, Acer Aspire TC-1660 desktop + LibreOffice, non-techie
James Bond 007
AskWoody LoungerMay 10, 2017 at 7:02 am #113908With the release of the May patches, I decided to do some experiment.
(1) Windows Defender needs to be updated to 1.1.13704 or later in order to fix the just-revealed serious code execution vulnerability. I launched a virtual machine running Windows Vista x64, with IE9 installed and fully patched to April 2017, and proceeded to see if I can download the update in Vista. I reenable Windows Defender (I said before it was my policy to disable Windows Defender as soon as Windows had been installed), and then asked it to check for updates. After a while Windows Defender was updated to mpengine.dll version 1.1.13704. So it seems that even though Vista’s support had ended in April, Windows Defender updates are still available. For how long I don’t know.
(2) I downloaded the Windows Server 2008 x64 version of KB4018271 (the May 2017 IE9 cumulative security update). Then I attempted to install the update in the same Vista virtual machine. Guess what? The installation was successful and IE9 was updated. I have not tried other security updates yet but I have no reason to believe that they will fail to install. It seems to me that I can continue to patch Windows Vista by manually downloading the corresponding Windows Server 2008 updates, at least for this month.
Hope for the best. Prepare for the worst.
2 users thanked author for this post.
-
abbodi86
AskWoody_MVPMay 10, 2017 at 8:30 am #113942Windows Client x64 shares the same updates with the corresponding Server version
except very few individual updatesluckily for Vista, Server 2008 have x86 edition, so both Vista 32/64 bit should be able to get use of Server 2008 updates
Windows 8 has similar experience, there are Server 2012 updates for 64 bit, and Embedded 8 for 32 bit
-
James Bond 007
AskWoody LoungerMay 10, 2017 at 11:05 am #114014Windows Client x64 shares the same updates with the corresponding Server version except very few individual updates.
Luckily for Vista, Server 2008 have x86 edition, so both Vista 32/64 bit should be able to get use of Server 2008 updates.
Windows 8 has similar experience, there are Server 2012 updates for 64 bit, and Embedded 8 for 32 bit.
Yeah, I know that Windows Vista and Windows Server 2008 are basically based on the same code, so Vista “should be able to” make use of Server 2008 updates. But with Vista out of support, there is no way to know if that is still true unless we try to install them on Vista.
When it was discovered that Windows XP can continue to receive updates by adopting the “POSReady hack”, Microsoft has this to say “The security updates that could be installed are intended for Windows Embedded and Windows Server 2003 customers and do not fully protect Windows XP customers. Windows XP customers also run a significant risk of functionality issues with their machines if they install these updates, as they are not tested against Windows XP. The best way for Windows XP customers to protect their systems is to upgrade to a more modern operating system, like Windows 7 or Windows 8.1.”
So now Microsoft can say “The security updates that could be installed are intended for Windows Windows Server 2008 customers and do not fully protect Windows Vista customers. Windows Vista customers also run a significant risk of functionality issues with their machines if they install these updates, as they are not tested against Windows Vista. The best way for Windows Vista customers to protect their systems is to upgrade to Windows 10.” Haha.
Anyway, Vista customers can continue to patch, at least for this month, provided they know what updates to download.
Hope for the best. Prepare for the worst.
1 user thanked author for this post.
-
anonymous
GuestMay 11, 2017 at 8:04 am #114209So now Microsoft can say “The security updates that could be installed are intended for Windows Windows Server 2008 customers and do not fully protect Windows Vista customers. Windows Vista customers also run a significant risk of functionality issues with their machines if they install these updates, as they are not tested against Windows Vista. The best way for Windows Vista customers to protect their systems is to upgrade to Windows 10.”
I appreciate the humor. But I would suggest one small change to the last sentence. How about “The best way for Windows Vista customers to protect their systems is to upgrade to Linux.”
I have several Vista (x86 & x64) real and virtual systems. I may try the Windows Server 2008 updates on the VMs where I can easily roll back a snapshot. But when it comes to the real systems I’ve decided that the best way to move forward is to install Linux. After evaluating a number of distros (CentOS, Debian, Ubuntu, Mandriva, Gentoo, OpenSuse, Mint) I decided to install Linux Mint 18 to dual boot with Vista and installed it on the x86 iron.
The installation went easily and Mint 18 was extremely well behaved in the way its installer recognized existing partitions and offered to resize them as necessary to make space for itself. Copying existing profiles for Firefox/Thunderbird into Linux was simple and computer usage continued without a hitch.
After getting my backups done I will soon install Mint 18 on the x64 box.
Windows 10? Bah, humbug!
1 user thanked author for this post.
-
anonymous
GuestMay 11, 2017 at 12:22 pm #114364There’s a very good site on optimizing Linux Mint 18.1 once it’s installed that you might find useful here:
https://sites.google.com/site/easylinuxtipsproject/mint-cinnamon-first
The page is for the Cinnamon desktop, but there are also links on it to XFCE and Mate desktops as well (my preference is XFCE, as it is very stable).
Some very good information on configuring for SSD’s that may be hard to find on the regular Mint forums is also here. I would suggest making sure your Windows partition is well backed up (just in case), and that you create a bootable USB drive in case you run into dual boot problems.
-
-
-
alpha128
AskWoody PlusMay 10, 2017 at 7:11 am #113913I did a bit more testing with the current patches for Windows 7/2008R2 and 8.1/2012R2. Each of them, but in particular the Windows 8.1/2012R2 versions supersede a very large number of older patches. Add to this the recent maintenance done by Microsoft on the update servers when they expired about 300 old updates from each operating system discussed here…
Yes, I noticed that Microsoft FINALLY stopped offering me some old Windows Update clients – plural.
I didn’t install a new Windows Update client until the slowdown bug made it necessary. I ended up first installing the June 2016 update rollup for Windows 7 SP1 (KB3161608), and followed that up with the July 2016 update rollup for Windows 7 SP1 (KB3172605).
But for a long time my list of hidden Windows Updates included ALL of the old clients I passed on.
Only now, have the following updates stopped being offered to me:
Windows Update Client for Windows 7: June 2015 (KB3050265)
Windows Update Client for Windows 7 and Windows Server 2008 R2: July 2015 (KB3065987)
Windows Update Client for Windows 7 and Windows Server 2008 R2: August 2015 (KB3075851)
Windows Update Client for Windows 7 and Windows Server 2008 R2: September 2015 (KB3083324)
Windows Update Client for Windows 7 and Windows Server 2008 R2: October 2015 (KB3083710)However, all the following old Windows Update Clients are STILL being offered to me:
Windows Update Client for Windows 7 and Windows Server 2008 R2: December 2015 (KB3112343)
Windows Update Client for Windows 7 and Windows Server 2008 R2: February 2016 (KB3135445)
Windows Update Client for Windows 7 and Windows Server 2008 R2: March 2016 (KB3138612)So now I’m only being offered three obsolete clients instead of eight. I guess that’s progress.

Anonymous
InactiveMay 10, 2017 at 9:27 am #113965hi guys, new here. Love the great info.. I’ve got a question about the .net updates this month.
In my WSUS I received :
May, 2017 Security and Quality Rollup for .net Framework 3.5-4.62 for both win7/2008r2 and win8.1/2012R2 KB 4019112/KB4019114
Also Get Security only versions of these KB4019108/KB4019111.
The normal OS Monthly rollups versus Security only updates state that you should choose one or the other.
The .net Monthly rollups/security do not mention this in KB articles.
My gut is to decline the security only and approve monthly rollups for .net like I do for OS patching.
Also one last think, I might be mistaken, but I remember April monthly rollups OS patches specifically saying that Internet explorer fixes were included and that I should either approve security only updates and internet explorer patches or just monthly quality rollups.
May patches now state that IE fixes are not included in Monthly Quality rollups. Did this switch or am I nuts?
Thanks
-
PKCano
ManagerMay 10, 2017 at 9:36 am #113981The Rollups for the .NET versions are good unless you are restricted to security-only patches.
The Security Monthly Quality ROLLUPS contain three parts: non-security, security and cumulative IE11 patches.
The Security Only Quality UPDATE contained the cumulative IE11 update from Oct 2016 through Feb 2017. As of March 2017, MS split the IE11 patch out. So if you go the Security-only route, you need to install the IE11 patch as well (both manually). Downloads can be obtained each month from the MS Update Catalog or from AKB2000003 on this site.1 user thanked author for this post.
anonymous
Guest-
anonymous
Guest -
anonymous
GuestMay 10, 2017 at 2:09 pm #114074 -
anonymous
GuestMay 10, 2017 at 2:42 pm #114088Update: I just did a search for updates again, and this time it succeeded (no 8024402F error). It said there was an MSE definition update available, and I applied it via Windows Update successfully, and it is visible in View Update History. So, I am not sure what was happening before; a temporary situation at Microsoft?
-
woody
Manager
-
-
Anonymous
InactiveMay 10, 2017 at 10:05 am #113989thanks PKCano. I just reread the May Monthly Quality rollups More information (Its a bit confusing, but you are correct, thanks again):
The security fixes that are listed in this Security Monthly Quality Rollup KB4019215 are also included in the May 2017 Security-Only Quality Update, KB4019213, except for the security fixes for Internet Explorer. Those are instead included in the Cumulative Security Update for Internet Explorer KB4018271. Installing either this May 2017 Security Monthly Quality Rollup or both the May 2017 Security-Only Quality Update and the Cumulative Security Update for Internet Explorer will install the security fixes that are listed here. This Security Monthly Quality Rollup also includes improvements and fixes from previous monthly rollups.
- If you use update management processes other than Windows Update, and you automatically approve all security update classifications for deployment, May 2017 Security Monthly Quality Rollup KB4019215, May 2017 Security-Only Quality Update KB4019213, and the Cumulative Security Update for Internet Explorer KB4018271 are deployed. We recommend that you review your update deployment rules to make sure that the desired updates are deployed. <b></b><i></i><u></u>
Geo
AskWoody Plusgkarasik
AskWoody PlusMay 10, 2017 at 10:54 am #114008Yes, just echoing Geo above–wassup w/kb3003057, which I’m being offered today on my test machine (Win7/32bit/Ent/SP1/fully patched)? I installed all patches offered yesterday (no problems so far after a pretty good workout). This morning there’s a taskbar bang telling me “New updates are available,” and KB3003057 (Cumulative Update IE11 blah blah blah) is the offering. It installs without requiring a reboot, leading me to wonder whether it’s just another cataloging mistake. Any insight?
GaryK
anonymous
Guest-
PKCano
Manager
Scribe
AskWoody LoungerMay 10, 2017 at 11:51 am #114028I’m mystified as to why the quality rollup KB4019264 for WIN7, has this prerequisite:
‘To apply this update, you must have Windows 8.1 and Windows Server 2012 R2 update April 2014 KB2919355 installed.’1 user thanked author for this post.
MrBrian
AskWoody_MVPMay 10, 2017 at 12:18 pm #114037gkarasik
AskWoody PlusMay 10, 2017 at 1:03 pm #114050Yes, just echoing Geo above–wassup w/kb3003057, which I’m being offered today on my test machine (Win7/32bit/Ent/SP1/fully patched)? I installed all patches offered yesterday (no problems so far after a pretty good workout). This morning there’s a taskbar bang telling me “New updates are available,” and KB3003057 (Cumulative Update IE11 blah blah blah) is the offering. It installs without requiring a reboot, leading me to wonder whether it’s just another cataloging mistake. Any insight?
Followup: Although I ran WinUp immediately after installing KB3003057, and it showed clean, half-an-hour later KB2987107 has shown up. Also installed without needing a restart. Anyone else old enough to remember Mickey Rooney and Judy Garland? “Hey, kids, let’s start a software company! We can call it ‘Microsoft’!”
GaryK
-
Anonymous
Inactive
anonymous
GuestMay 10, 2017 at 1:13 pm #114046Ascaris wrote: Backups… always backups!
I too depend on backups of my system drive to recover from system disasters. I use the windows ‘Create A System Image’ function to make the backups and have successfully used it to recover on several occasions. But I’ve noticed that one else here seems to use it. Am I missing something?
Gene
-
Ascaris
AskWoody MVPMay 10, 2017 at 10:42 pm #114163I use the windows ‘Create A System Image’ function to make the backups and have successfully used it to recover on several occasions. But I’ve noticed that one else here seems to use it. Am I missing something? Gene
I tried that initially on Windows 7, but it didn’t work on my data drive, which is a GPT-formatted volume of a little over 2TB, which is apparently beyond the capabilities of Windows backup.
I am not sure what features it has, but Acronis has a few that may not be in there, like incremental image creation and encryption of the backup image. I’d gone off Acronis as it has had some issues with bugs (though once the image was written, it always worked), but its replacement (Macrium Reflect Free) does not do encryption, and the paid version is much more expensive than Acronis (which I had already paid for), so back I went.
Dell XPS 13/9310, i5-1135G7/16GB, KDE Neon 6.2
XPG Xenia 15, i7-9750H/32GB & GTX1660ti, Kubuntu 24.04
Acer Swift Go 14, i5-1335U/16GB, Kubuntu 24.04 (and Win 11) -
Kirsty
ManagerMay 10, 2017 at 11:01 pm #114167I use the windows ‘Create A System Image’ function to make the backups and have successfully used it to recover on several occasions. But I’ve noticed that one else here seems to use it.
@gene
I think you’ll find many around these parts do use system images regularly 🙂
1 user thanked author for this post.
anonymous
GuestMay 10, 2017 at 1:30 pm #114058Guinea pig reporting in again. Win 7 32-bit, installed 4018271 (IE update) and 4019263 (security-only bundle) several hours ago, so far so good. Just the .NET one left since that was available in Windows Update while I obviously had to download the others and run them manually and then if opened Windows Update would demand a reboot before doing anything else, so leaving it for some later time.
gkarasik
AskWoody PlusMay 10, 2017 at 1:35 pm #114064In my WSUS controlled Environment. I also just got KB3003057 after getting the KB3308923 the other day..I installed 3008923 and it did not want reboot. seems like MS is doing some shady things behind the scenes…
Sadly it’s recently become easy to believe MS is doing shady things behind the scenes, but more than likely it’s simply incompetence. Neither is good, but a lot of these problems are consistent with a department getting its budget slashed and people being frantically overworked.
GaryK
1 user thanked author for this post.
-
Anonymous
InactiveMay 10, 2017 at 1:41 pm #114066agreed, neither is good.. but inconsistency of Updates that affect millions of PC’s especially in and enterprise environment is very scary…
1 user thanked author for this post.
gkarasik
AskWoody PlusMay 10, 2017 at 1:50 pm #114073agreed, neither is good.. but inconsistency of Updates that affect millions of PC’s especially in and enterprise environment is very scary…
Agreed. Terrifying.
GaryK
anonymous
GuestMay 10, 2017 at 2:23 pm #114082I refreshed my Windows 8.1 machine, installed all updates, ran a disk clean up and now I have 9 old updates available. What should I do?
-
anonymous
Guest
ch100
AskWoody_MVPMay 10, 2017 at 3:41 pm #1141041607 and Windows 2016 Server update KB4019472 released with delay of few hours.
More expired updates, among them KB3008923 and KB3003057.
Instead of them, now you will see KB2987107 as required.
Same treatment like for the other two: either ignore, or pretend to install to get rid of it from the picture.KWGuy
AskWoody PlusMay 10, 2017 at 5:17 pm #114117Are the monthly quality roll ups for Win7/8.1 now including patches NOT installed prior to Oct 2016? If not, any word about MS’s future intentions for doing this?
The prospects for this is the primary reason I’m in Group B. I have hidden patches which, if installed, will create USB issues with my Dell Win 7 machines.
Thanks!
-
PKCano
Manager -
ch100
AskWoody_MVPMay 11, 2017 at 1:38 am #114186I wouldn’t say it is a mess. There is no harm done in “installing” the incorrectly non-expired old updates, as they just flag the supersedence chain and do not install anything. There is no reboot required.
The benefit in doing this current cleanup is far greater than any annoyance caused by those temporarily missed updates from expiring.
It is only that people here are more aware of those updates. 99.99999% of users would not see this as an issue and both of us know that this is the case.
2 out of the 3 mistakenly non-expired updates have already been expired in the last few hours, only one left.
-
abbodi86
AskWoody_MVPanonymous
GuestMay 10, 2017 at 5:33 pm #114118I too had KB3003057 show up in WU today. A quick lookup reveals that KB3003057 is:
Cumulative security update for Internet Explorer: November 11, 2014
https://support.microsoft.com/en-us/help/3003057/In the above KB, it states:
“The update that this article describes has been replaced by a newer update. We recommend that you install the most current cumulative security update for Internet Explorer.”
In other words, it should be ignored. Looking at the IE files it replaces clearly indicates that this should not be installed, but if it is, then all should be fixed by installing the latest cumulative update.
I was going to sacrifice one of my other Win 7 machines by ignoring this patch and installing the latest IE11 cumulative patch to determine if WU would resolve things. Much to my surprise, KB3003057 wasn’t offered by WU.
This 2nd machine (aka machine #2) has the same version of Windows 7 Ult and is also fully patched, so how could this be?
Going back to machine #1, I searched installed updates and discovered that KB3003057 had never been installed. However, it had been installed on machine #2. Keep in mind that both machines have always been fully patched.
So why has this happened?
Well, machine build dates gives a clue:
1) Machine #1 – built 2010
2) Machine #2 – built late 2014Machine #2 likely had a more recent IE cumulative update installed upon initial setup. KB3003057 was never offered because it had been superseded at that time.
So it appears that the error is on Microsoft’s part.
Now I have to figure out why WU is offering:
1) Machine #1 – 3 Office 2010 patches
2) Machine #2 – 5 Office 2010 patchesMore than likely, it too relates to when Office 2010 was initially installed.
CA
-
PKCano
ManagerMay 10, 2017 at 5:34 pm #114123Your answer is here
https://www.askwoody.com/forums/topic/massive-batch-of-old-windows-updates-retired/1 user thanked author for this post.
GoneToPlaid
AskWoody LoungerMay 10, 2017 at 9:01 pm #114146A few caveats about .NET Framework 4.7 MrBrian – you can only find this download at the Microsoft Download Center (just like with the full .NET 4.6.2 package): (web installer) https://www.microsoft.com/en-us/download/details.aspx?id=55170 (full offline installer) https://www.microsoft.com/en-us/download/details.aspx?id=55167
.NET Framework 4.7 WPF features take a dependency on D3DCompiler_47.dll . This D3DCompiler_47.dll is not present by default in Windows 7 SP1, Windows 2008 R2 SP1 and Windows 2012 OS platforms. Hence these OS platforms require D3DCompiler_47.dll to be installed for .NET Framework 4.7 WPF features to work as expected. Please see known issues article for D3DCompiler_47.dll install information details.
You will need the KB4019990 D3DCompiler_47.dll update for Win7 SP1 if you want to install .NET Framework 4.7 under Windows 7.
I deliberately have not installed any versions of .NET Framework higher than the 4.5 branch on my Windows 7 computers since .NET Framework 4.6 and higher include telemetry and are only needed if you want to run Windows 10 applications on Windows 7 and Windows 8x computers. Just a “heads up” for everyone on Group B.
-
James Bond 007
AskWoody LoungerMay 10, 2017 at 11:01 pm #114168I deliberately have not installed any versions of .NET Framework higher than the 4.5 branch on my Windows 7 computers since .NET Framework 4.6 and higher include telemetry and are only needed if you want to run Windows 10 applications on Windows 7 and Windows 8x computers. Just a “heads up” for everyone on Group B.
Really? That is news to me. Thanks for the heads up.
The highest version of .NET Framework on my computers running Windows 7 and Windows 8.1 is 4.5.2 as well, but only because 4.5.2 works well and is supported to the end of support (of Windows 7) so that I consider 4.6.x (and now 4.7) unnecessary.
Hope for the best. Prepare for the worst.
-
abbodi86
AskWoody_MVP
-
MrBrian
AskWoody_MVPPerthMike
AskWoody PlusMay 10, 2017 at 10:04 pm #114156I’m noticing on my WSUS server that all of the Win server 2016 patches are missing for May. Meaning that any patch for any product targeted for Win 2016 was not synchronized. Such as the OS patch, .NET, etc. I’ve rechecked all of the long-standing settings and they are as they should be. Is anyone else seeing this? Thanks, A non-moose cow-herd
My WSUS server is just not synching at all.
Last month, syncs would fail until I disabled the Updates category. But this month, the last successful sync was the day before Patch day and nothing since. Not even showing failed attempts this time.
When I hit Synchronize Now, it just sits there “Running…” for hours.
No matter where you go, there you are.
PerthMike
AskWoody PlusMay 10, 2017 at 10:11 pm #114157Yes, and this has happened several times in the past for us for Server 2016 and Server 2012 R2. I’m expecting them to hit WSUS later this week.
Check your synch log. Mine is showing no synch (not failed, nothing) after Monday (last day before patch day). For some reason, it’s not even attempting any more. I have kicked off a manual synch, but it’s been running for over three hours with no apparent activity.
(Yes, I know it says “9/05” was successful, but I’m in Western Australia, so that was still before Patch Tuesday, we don’t see them until Wednesdays with the timezone difference.)
No matter where you go, there you are.
-
NetDef
AskWoody_MVPMay 11, 2017 at 12:56 pm #114388Not sure what to make of that. I manage several WSUS servers that sync nightly, including one older SBS server running WSUS 3.2 . . . and they are all syncing on schedule successfully. However, those do NOT have the Upgrade option enabled.
I have one site that won’t sync until tomorrow night (it’s a client with multiple Windows 10 workstations, we defer syncs to end of week in order to control update reboots during the work week.) It will be interesting to see if that one fails the same way your log indicates.
And my test bed WSUS – which does have Upgrades enabled, has been working fine all week too.
Wondering if there is a problem due to time zones? (Nothing would surprise me these days.)
You might try canceling the sync, restarting the “Update Service” and try another manual sync. You may also need to run a full WSUS cleanup.
Another forum I rely on (spiceworks) does not seem to be full of complaints of this nature this week about WSUS, which to me means the problem is likely not widespread.
~ Group "Weekend" ~
-
ch100
AskWoody_MVPMay 11, 2017 at 4:40 pm #114484I think the same problem was reported on patchmangement.org for the latest synchronisation by those with Upgrades enabled.
I stopped synchronising Upgrades long time ago so this may be an issue, but I just don’t know.
Upgrades category is enabled automatically any time when Windows 10 is enabled under Products, so it has to be manually disabled if desired (and I would recommend it, at least until it becomes more reliable).
Like Service Packs, I think upgrades are better performed offline manually if possible.
Normally, with WSUS, all categories should be enabled, less Drivers and anything related and Upgrades.
-
Noel Carboni
AskWoody_MVP-
anonymous
Guest -
Noel Carboni
AskWoody_MVPMay 11, 2017 at 8:50 am #114267The wallpaper is one of the astroimages I’ve processed from data my friend and collaborator Greg Parker captured at his New Forest Observatory. That particular background is a picture of the brightest star in the sky, Sirius, though the star is hidden behind some of the windows in that screen grab.
The desktop theme is Aero 7 by Sagorpirbd, facilitated by beta copy of the Aero Glass for Win 8+ product by Big Muscle, and topped off by caption button graphics done by me.
More info on my experiences with tweaking Win 10 v1703: Here.
-Noel
1 user thanked author for this post.
-
ch100
AskWoody_MVPMay 11, 2017 at 1:21 am #114182The highest version of .NET Framework on my computers running Windows 7 and Windows 8.1 is 4.5.2 as well, but only because 4.5.2 works well and is supported to the end of support (of Windows 7) so that I consider 4.6.x (and now 4.7) unnecessary.
In fact the minimum version of .NET Framework which you need is dictated by the version which the software developer restricted in the software.
If a certain software is designed to require .NET Framework 4.6.1 for example, you would be able to use it only if you have 4.6.1, 4.6.2 or 4.7 or later installed on your machine.
This has nothing to do with the end of support for the Windows edition on which .NET Framework is installed.-
James Bond 007
AskWoody LoungerMay 11, 2017 at 3:33 am #114196In fact the minimum version of .NET Framework which you need is dictated by the version which the software developer restricted in the software.
If a certain software is designed to require .NET Framework 4.6.1 for example, you would be able to use it only if you have 4.6.1, 4.6.2 or 4.7 or later installed on your machine.
This has nothing to do with the end of support for the Windows edition on which .NET Framework is installed.Well, no doubt you are right. But as all of the programs I use works fine (e.g. Handbrake), it shows clearly to me that I don’t require 4.6.x or above of the .NET Framework. So I will just keep 4.5.2 all the way.
Actually I would prefer not having to install the .NET Framework 4.x at all in Windows 7 as it requires a whole batch of security updates to itself. Unfortunately there are many common programs that require it now (e.g. Display Driver software) so it is not possible. I would just keep the lowest supported version that works for me. In my case that will be 4.5.2.
Hope for the best. Prepare for the worst.
-
ch100
AskWoody_MVPMay 11, 2017 at 5:45 am #114208@James Bond 007
My post was not an invite to upgrade the version of .NET Framework to the latest one if you don’t need it or you don’t feel like being proactive for future software which you may use.
I was only trying to explain as posts like @GoneToPlaid’s (almost all if not all of them on this forum) are actually trolling and trying to mislead unsuspecting users only for fun (of their author).
-
radosuaf
AskWoody LoungerMay 11, 2017 at 2:57 am #114195I’ve read somewhere that there are still 1.8% of W10 users that have RTM (1507) version installed – since they’re now out of support (and must be on RTM for valid reasons), are they coming back to W7 or W8.1 that are still supported?
Fractal Design Pop Air * Thermaltake Toughpower GF3 750W * ASUS TUF GAMING B560M-PLUS * Intel Core i9-11900K * 4 x 8 GB G.Skill Aegis DDR4 3600 MHz CL16 * ASRock RX 6800 XT Phantom Gaming 16GB OC * XPG GAMMIX S70 BLADE 1TB * SanDisk Ultra 3D 1TB * Samsung EVO 840 250GB * DVD RW Lite-ON iHAS 124 * Windows 10 Pro 22H2 64-bit Insider * Windows 11 Pro Beta Insider-
abbodi86
AskWoody_MVP -
radosuaf
AskWoody LoungerMay 25, 2017 at 7:57 am #118105According to the methodology:
http://blog.adduplex.com/2017/04/adduplex-windows-device-statistics-report-april-2017.html
it is based on Store apps usage, so we can rather rule LTSB 2015 out.
Fractal Design Pop Air * Thermaltake Toughpower GF3 750W * ASUS TUF GAMING B560M-PLUS * Intel Core i9-11900K * 4 x 8 GB G.Skill Aegis DDR4 3600 MHz CL16 * ASRock RX 6800 XT Phantom Gaming 16GB OC * XPG GAMMIX S70 BLADE 1TB * SanDisk Ultra 3D 1TB * Samsung EVO 840 250GB * DVD RW Lite-ON iHAS 124 * Windows 10 Pro 22H2 64-bit Insider * Windows 11 Pro Beta Insider1 user thanked author for this post.
-
anonymous
GuestMay 11, 2017 at 9:03 am #114260Well, I checked WU this morning on one of my Win 7 machines and IE cumulative update KB3003057 was gone only to be replaced by KB2987107. Both refer to patches for Internet Explorer: October 14, 2014:
https://support.microsoft.com/en-us/help/3003057/
https://support.microsoft.com/en-us/help/2987107/Note that I haven’t applied any of the May patches on this machine. Looks like MS is working on things.
@PKCano – Not the same thing. By my count, MS retired/superseded 81 Win 7 security related patches in April alone. Different issue.I’m in Group B at my home office and have installed this month’s patches on a few Win 7 test machines. Cold booted multiple times, minimally tested some core apps (e.g. 2010 Office, Apache, MySQL, dev tools) and haven’t found any show stoppers yet. I also haven’t heard any problems from clients in the field (Group A).
As far as .NET goes, I let WU handle that. Why make life difficult.
CA
-
PKCano
ManagerMay 11, 2017 at 9:07 am #114275You are seeing the old patches because. in the process of retiring a massive bunch for all versions of Windows (not just Win7) the supersedence chain has been broken. They are working on it, and that is why one of the patches disappeared (it was retired) and the one it superseded showed up.
anonymous
GuestMay 11, 2017 at 11:26 am #114338You’re missing the point of my posts. I’m fully aware of supersedence and that it’s broken.
In this case, I was trying to determine why two identically patched Win 7 machines had different offerings in WU. The patch number is irrelevant.
These two machines in question are mirrors of one another (except for build dates). If a security related patch shows up on one, then logically the same patch should show up on the other. It struck me as odd, so I did a little digging to determine why this happened. That’s all. 🙂
As a side note, I’ve now taken a “B” machine that has KB2987107 being offered (not hidden) and applied KB4018271. I’m going to leave it in that state to see how MS addresses the issue. On my other test benches, I had already hid the patch(s) in question.
As for the massive amount of patches now being retired, MS had made clear their intent to do so many months ago (much to my dismay). It is part of the plan to move Win 7 to the Win 10 cumulative/delta model – so no news there. I don’t, however, see how this will sit well in specific enterprise or controlled environments (e.g. health industry).
CA
1 user thanked author for this post.
-
Noel Carboni
AskWoody_MVPMay 11, 2017 at 1:59 pm #114408I’ve often had a suspicion that the whole process is pretty “hit and miss” under the covers.
What have I seen over time to warrant that feeling? I don’t know, things like…
Ancient updates that suddenly show up as applicable.
Different systems with entirely different WMI QFE LIST output.
Updates showing up as available right after installing updates.
Different lists of available updates from machine to machine.And of course reading comments like yours over the years.
It’s all served to make me feel that the whole update process has never been nearly as scientific or well defined as we might hope. I don’t find it surprising that Microsoft wants to create “cumulative” update packages to try to get systems in line with one another.
And so far I’ve found I can still control everything that’s running… The only downside seems to be that the disk usage is somewhat higher with everything in “Group A” updated state. That being said, I have a critical Win 7 system functioning as a server that simply ISN’T in group A, on purpose. If it works, don’t fix it.
-Noel
ViperJohn
AskWoody LoungerMay 11, 2017 at 11:27 am #114348Reminder of past topic: Installing Win updates on Win 7 or 8.1 computers with Kaby Lake or Ryzen CPUs.
Just installed the Windows 7-x64 Security Only Quality Update KB4019263. Note the update DID NOT re-install the Kaby / Ryzen unfiendly Windows Update blocking DLL’s. All 8 WU related DLL’s are still the Kaby / Ryzen good version 7.6.7601.23453 after installing KB4019263.
I am surprised!!!
Viper
-
MrBrian
AskWoody_MVPMay 11, 2017 at 12:26 pm #114374File Wuaueng.dll indeed is not present in either the Windows 7 or 8.1 May 2017 security-only update.
-
woody
Manager -
EP
AskWoody_MVPMay 11, 2017 at 9:52 pm #114515Important note: version 7.6.7601.23453 of the wuaueng.dll & other related Windows Update Agent files for Win7 SP1 are included in the KB3161608 & KB3172605 updates.
Also KB4019213 for Win8.1 also excludes the updated WUA files from the April 2017 updates that have blocked AMD Ryzen/Carrizo & Intel Kaby Lake CPUs under Win8.1. the version of wuaueng.dll for Win8.1 that doesn’t block those recent AMD & Intel processors is version 7.9.9600.18340 – included in KB3161606 & KB3172614 updates.
anonymous
GuestNoel Carboni
AskWoody_MVPMay 11, 2017 at 2:14 pm #114415I’ve updated my Windows 7 test system with the latest “Group A” patches…
The update check took just a couple of minutes. I DID notice something called C:c421c1e218fc7873979d267c10setup.exe tried to contact http://www.microsoft.com twice during the update. Blocking that didn’t lead to any failures.
The installation completed successfully, and the requisite reboot went without a hitch.
In comparing my current WMI QFE LIST output to one generated prior to the updates, I see the following:
- KB4015552 “Update” no longer appears.
- KB4014504 “Update” is added.
- KB4019264 “Security Update” is added.
I don’t know what’s supposed to be “retired” or “superseded”, but the list of updates shown installed on this Win 7 x64 Ultimate test system via WMI QFE LIST is still some 226 entries long.
It seems to be working okay. I will follow up if I discover problems.
-Noel
1 user thanked author for this post.
-
abbodi86
AskWoody_MVP
Noel Carboni
AskWoody_MVPMay 11, 2017 at 2:52 pm #114436My Windows 8.1 test system is now on the latest updates. The update check went quickly, the updates went in smoothly, and the reboot went smoothly.
A comparison of my WMI QFE LIST output before and after the update shows:
- KB4015553 “Update” removed.
- KB4014505 “Update” added.
- KB4014510 “Update” added.
- KB4020821 “Security Update” added.
- KB4019215 “Security Update” added.
-Noel
JohnW
AskWoody Loungergkarasik
AskWoody PlusMay 12, 2017 at 6:26 pm #114652There is simply no parallel universe in which having a 5-10 email conversation with everyone on my network about when it’s safe to let Windows Update patch and hand holding step by steps on what needs to be dug into and disabled is going to be EASIER for me than to upload patches as I install them for myself and ask everyone once to check their network folder once a day for anything new to install on their end.
Just a partial solution, but with important updates I sometimes use a login script to install patches downloaded to a network share–sometimes three or four. It makes the login take a bit longer, but this way I’m sure they get installed without having to worry about a user forgetting or just deciding he/she is too busy to bother.
GaryK
-
ch100
AskWoody_MVP
gkarasik
AskWoody PlusMay 12, 2017 at 7:16 pm #114668Why not using tools designed for the purpose like WSUS instead of the old fashioned login scripts?
WSUS is a great alternative. I suggested logon scripts as an alternative to trusting users to check a network share every day to see if there were updates to install, which in my experience (and with my users) is not viable. As far as WSUS, I just never got into it. When I first looked at it lo those many yeas ago I was supporting multiple, space-constricted, SBS 2003 boxes connected to slow DSL lines. The boxes didn’t have the space and the DSL lines didn’t have the bandwidth for the WSUS downloads. At the time, WSUS just seemed like overkill., and I found other ways to cope. I have come to prefer touching user boxes (remotely) on a regular basis. Connecting to them and running Windows Update gives us a feel for how the boxes are running and lets us spot anomalies and catch and release them early and quickly before they do too much damage. Ultimately you have to make choices that work best with how your mind works (or in my case doesn’t).
GaryK
-
ch100
AskWoody_MVPMay 12, 2017 at 7:50 pm #114683Gary, WSUS downloads only those updates which are approved by the WSUS administrator. Many admins tend to approve everything or use the default rule to approve all Important (Critical & Security) updates, but in most cases this is overkill and uses too much bandwidth and storage. The only updates which have to be approved are those which are needed. Those superseded can be declined and the storage released following the cleanup task. I agree with you that there is some work going into learning how to use WSUS effectively, but if you have many users under management, it is a lot more effective than running login scripts.
However, the best solution for the task at hand is the one which works best for you 🙂1 user thanked author for this post.
-
NetDef
AskWoody_MVP
-
gkarasik
AskWoody PlusMay 12, 2017 at 7:53 pm #114685Gary, WSUS downloads only those update which are approved. Many admins tend to approve everything or use the default rule to approve all Important (Critical & Security) updates, but in most cases this is overkill and uses too much bandwidth. The only updates which have to be approved are those which are needed. I agree with you that there is some work going into learning how to use WSUS effectively, but if you have many users under management, it is a lot more effective than running login scripts. However, the best solution for the task at hand is the one which works best for you 🙂
Absolutely. For larger organizations, WSUS is a godsend.
GaryK
-
owdrtn
AskWoody LoungerMay 13, 2017 at 1:08 pm #114870As a single-user consumer (in contrast to some corporate/sysadmin-context), I’ve never really gave an try at MS’s WSUS. It’s only recently, that I moved from using the basic idiot-proof (now “trouble-sure”) WU, to some mixed use of the Catalog (MUC) & their Bulletins .
But the more I hear about WSUS (along with other similar “more Corporate-Targeted Windows update management solutions), the more I feel like I should step-in, or at the very least give those a try.
But having not much experience with servers (yet open to), I’d be tempted to try the unofficial offline version WSUS Offline first.
I’d love to know your insight on this ? Sounds more like a fair “GO” or “NO-GO” to you guys ?Everyone’s opinion are much appreciated, just try to back your claim with some source when possible.
-
PKCano
Manager
-
anonymous
GuestMay 13, 2017 at 11:40 am #114837In carefully reading the info on KB4019264, at the top under the heading of “Improvements and fixes”, the bulletin clearly states “This security update includes improvements and fixes that were a part of update KB4015552 (released April 18, 2017) and also resolves the following: …Security updates to Internet Explorer, Microsoft Graphics Component, Windows COM, Microsoft ActiveX, Windows Server, Windows kernel, and Microsoft Windows DNS.”
BUT, if one reads the info listed under the “More Information” section of the bulletin, it clearly states “This Monthly Rollup update does not include security fixes for Internet Explorer. In order to obtain the security fixes for Internet Explorer, the Cumulative Security Update for Internet Explorer KB4018271 should also be installed. Note that the Security Monthly Quality Rollup does contain security updates for Internet Explorer.
The added emphasis (making the type appear bold) is mine and not included in the original bulletin.
Also note that, at the top of the page, MS clearly calls the update just a monthly rollup, not a Security Monthly Quality Rollup. However, in the listings for Windows Update, it (KB4019264) is labeled as a Security Monthly Quality Rollup.
Could this all just be a case of MS not editing their bulletin’s content well enough (a typo), or does this update indeed NOT contain the security fixes/patches for IE11? If the patch isn’t included, then many folks are going to have to go get it separately from the MS Update Catalog who may not be used to dealing with said catalog and may get very frustrated.
MrBrian
AskWoody_MVPMrBrian
AskWoody_MVPMay 13, 2017 at 2:34 pm #114912From May 2017 monthly rollup for Windows 8.1:
“If a Server 2012 R2 system uses an Intel Xeon (E3 v6) family of processors, installing this update will block downloading and installing future Windows updates.”
1 user thanked author for this post.
Geo
AskWoody Plusch100
AskWoody_MVPMay 16, 2017 at 5:50 am #115630Few more patches for this month, released few hours ago:
2017-05 Update for Windows 10 Version 1607 for x64 based Systems (KB3150513)
2017-05 Update for Windows 10 Version 1607 for x86 based Systems (KB3150513)
2017-05 Update for Windows Server 2016 for x64 based Systems (KB3150513)Windows Server 2016 is the same version 1607, only that it is LTSB (not CB or CBB).
Windows Server 2016 shares much of the code with Windows 10 1607.Edit to change 2106 to 2016 in last line
Edit: Thank you @PKCano 🙂
Now the previous versions of the same updates from May, 5 have been expired after few hours from the release of the newer versions.
-
Kirsty
ManagerMay 31, 2017 at 11:14 pm #118925Gunter Born is reporting that KB3150513 has been re-released, dated 31 May 2017, for AU/1607 & Server 2016.

-
anonymous
GuestJune 1, 2017 at 2:02 am #118931They are being diligent about shipping out these KB3150513 packages, it has been promptly thrown on the waste pile.
This is off topic but interesting: The Microsoft Machine wastes little time if a user plugs in a (new) device, they may be offered a Microsoft driver package for it when checking for updates.
-
MrBrian
AskWoody_MVPMay 16, 2017 at 1:31 pm #115744The May 2017 Windows preview monthly rollups are available:
https://support.microsoft.com/en-us/help/4019265/windows-7-update-kb4019265
https://support.microsoft.com/en-us/help/4019217
https://support.microsoft.com/en-us/help/4019218MrBrian
AskWoody_MVPJune 3, 2017 at 1:21 pm #119219The Windows 8.1 May 2017 monthly rollup and security-only update have this issue documented:
“This security update introduced an issue in which, if an iSCSI target becomes unavailable, attempts to reconnect will cause a leak. Initiating a new connection to an available target will work as expected.”
-
MrBrian
AskWoody_MVP
Viewing 61 reply threads -

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
March 2025 updates are out
by
Susan Bradley
17 minutes ago -
Windows 11 Insider Preview build 26120.3380 released to DEV and BETA
by
joep517
3 hours, 51 minutes ago -
Update Firefox to prevent add-ons issues from root certificate expiration
by
Alex5723
11 hours ago -
Latest Firefox requires Password on start up
by
Gordski
5 hours, 34 minutes ago -
Resolved : AutoCAD 2022 might not open after updating to 24H2
by
Alex5723
23 hours, 48 minutes ago -
Missing api-ms-win-core-libraryloader-11-2-1.dll
by
IreneLinda
1 hour, 27 minutes ago -
How Much Daylight have YOU Saved?
by
Nibbled To Death By Ducks
1 hour, 34 minutes ago -
A brief history of Windows Settings
by
Simon Bisson
15 hours, 32 minutes ago -
Thunderbolt is not just for monitors
by
Ben Myers
4 hours, 21 minutes ago -
Password Generators — Your first line of defense
by
Deanna McElveen
1 hour, 49 minutes ago -
AskWoody at the computer museum
by
Will Fastie
1 hour, 23 minutes ago -
Planning for the unexpected
by
Susan Bradley
15 minutes ago -
Which printer type is the better one to buy?
by
Bob99
1 day, 1 hour ago -
Upgrading the web server
by
Susan Bradley
23 hours, 58 minutes ago -
New Windows 11 24H2 Setup – Initial Win Update prevention settings?
by
Tex265
1 day, 19 hours ago -
Creating a Google account
by
DavidofIN
1 day, 17 hours ago -
Undocumented “backdoor” found in Bluetooth chip used by a billion devices
by
Alex5723
2 days ago -
Microsoft Considering AI Models to Replace OpenAI’s in Copilot
by
Alex5723
2 days, 11 hours ago -
AI *emergent misalignment*
by
Alex5723
2 days, 12 hours ago -
Windows 11 Disk Encryption/ Bitlocker/ Recovery Key
by
Tex265
20 hours, 29 minutes ago -
Trouble signing out and restarting
by
Tech Hiker
3 hours, 46 minutes ago -
Windows 7 MSE Manual Updating
by
Microfix
2 days, 20 hours ago -
Problem running LMC 22 flash drive
by
Charlie
1 day, 19 hours ago -
Outlook Email Problem
by
Lil88reb
1 day, 19 hours ago -
“Microsoft 365 Office All-in-One For Dummies, 3rd Edition FREE
by
Alex5723
2 days, 3 hours ago -
Cant use Office 2013 – Getting error message about Office 2013
by
SAAR
2 days, 20 hours ago -
Nearly 1 million Windows devices targeted in advanced “malvertising” spree
by
bbearren
2 days, 20 hours ago -
Windows 11 Insider Preview build 27808 released to Canary
by
joep517
3 days, 21 hours ago -
Windows 11 Insider Preview Build 22635.5025 (23H2) released to BETA
by
joep517
3 days, 21 hours ago -
Sysprep issue
by
Evit
3 days, 20 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.