As promised, I’d like to start a discussion about “Group B” and its future. More coming momentarily….
[See the full post at: Is the “Group B” approach of installing Security-only updates still viable?]

|
Patch reliability is unclear. Unless you have an immediate, pressing need to install a specific patch, don't do it. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
-
Is the “Group B” approach of installing Security-only updates still viable?
Home » Forums » Newsletter and Homepage topics » Is the “Group B” approach of installing Security-only updates still viable?
- This topic has 260 replies, 46 voices, and was last updated 7 years, 5 months ago.
AuthorTopicViewing 72 reply threadsAuthorReplies-
anonymous
GuestApril 25, 2017 at 8:47 am #110692I’m writing this now, as 10 minutes from now my PC may no longer work. This is a W7 machine, updates are set to “check but let me choose” and I have not done any updates at all since MS started their new system (since I’m working hard on changing all my machines to Linux). I just got a warning message I need to reboot to install the updates. I did not give permission for anything. And settings are still the same. If this does not prove that MS can do just about anything on my PC without their permission (like update to W10 without users’ permission) I don’t know what will convince people. Time to seriously accelerate the move to Linux.
1 user thanked author for this post.
-
PKCano
ManagerApril 25, 2017 at 8:54 am #110702Before you reboot
Open Windows Update, click on the “important updates” list, and uncheck anything you don’t want installed.
Under “Change settings” be sure your setting is either “Never check” or “Check but let me choose whether to download and install”If you have Microsoft Security Essentials on your PC of Defender, the updates will download and install not dependent on your WU settings.
2 users thanked author for this post.
-
zero2dash
AskWoody LoungerApril 25, 2017 at 8:53 am #110701If I may add an “unofficial” wrinkle to this dilemma:
Over the last 30 days, I’ve decided to run WSUS Offline, install any deemed necessary updates, and then run the regular WU client. Reason being, they changed WSUS Offline to allow you to choose Security-Only updates (instead of the rollups), which is good because I don’t want the rollups. Well, now I come to find that it installed them anyway.Here is a list of updates that have been installed on my primary workstation in the last 30 days, with the ones grabbed from WU designated with (wu) after the update info. I also put some abbreviated info to describe what the update was for.
4/24
kb3075226 sec rdp
kb3020388 sec rdp
kb2923545 rdp (wu)
kb2857650 rdp (wu)
kb2574819 rdp (wu)
kb2830477 rdp (wu)4/22
kb4014565 sec and quality rollup .net
kb4015549 april monthly rollup
kb4015546 april sec only
kb4014661 cum sec ie
kb3212642 jan sec only
kb3188730 sec .net
kb3168965 sec kernal
kb3138962 sec
kb3033929 sec
kb3018238 11/14 sec
kb3005607 11/14 sec
kb890830 msrt april (wu)
kb4014981 sec and quality rollup .net (wu)3/30
kb4012212 march sec only quality update
kb4012204 sec for ie ms17-006I had done a fresh install on 3/3, so you’ll see there’s only 2 updates pulled and installed on 3/30. You’ll also notice that 3 days ago, when I installed updates (a bit pre-emptively, but I saw Woody’s note that he’d be changing the DEFCON rating so I jumped the gun a few days early), it pulled both April Security Only and the April Rollup. In addition, it pulled the Jan Security Only update, despite grabbing the April Rollup. Why? This makes no sense. April Rollup includes the Jan Sec Only fixes. If it installed April Sec Only, it doesn’t need April Rollup. April Rollup is the odd man out here…that update should not have been necessary. And now I’m concerned as to what is going on with my machine that I don’t know about.
The sad thing is, going forward, I’m not using WSUS Offline anymore. And I don’t know what to do from this point, because I had thought it was safe to count on that to keep my machines updated without any of the junk. It’s getting to where I think it’ll be easier to just shut down WU for good and join Group W, if this is how things are going to go from now on.
2 users thanked author for this post.
-
woody
ManagerApril 25, 2017 at 9:55 am #110726they changed WSUS Offline to allow you to choose Security-Only updates (instead of the rollups), which is good because I don’t want the rollups. Well, now I come to find that it installed them anyway.
ARRRRRGH! That was one of my great hopes for a way out of the conundrum.
-
Sessh
AskWoody LoungerApril 25, 2017 at 9:58 am #110729It’s getting to where I think it’ll be easier to just shut down WU for good and join Group W, if this is how things are going to go from now on.
Beware: I had my WU service disabled in Services and before that, it was set to never check for updates and yet, yesterday I saw that WU had re-enabled itself. It changed it’s setting from disabled to Automatic (Delayed) and had started itself and I never use that “Delayed” setting ever for anything. It doesn’t appear to have installed anything and I’m not sure what could have triggered it, but it happened. Make sure you keep checking on it every now and then.
I can’t wait to get on Linux. I am still reading up on Unix/Linux stuff and doing preparation-oriented research and I will buy a fourth HDD so I can run Linux on it’s own drive and VM Win7 on the same drive by restoring the Win7 backup image straight into the VM, but hopefully I won’t need it much in short order. It’s amazing how anyone continues to sing MS’s praises in any way at this point. I never thought I’d be so passionately wanting to get off Windows now. Only a few months ago, I was a loyal MS customer that didn’t think twice about trusting them unconditionally with my PC and data. My how things change quickly sometimes.
2 users thanked author for this post.
-
fp
AskWoody LoungerApril 25, 2017 at 12:08 pm #110794Win10 1511 — group W no updates whatsoever, never will. Win7 — security updates from MS catalog only @defcon 1 for as long as it makes sense, after which Group W too. Both systems have WU updates disabled and all other settings configured to prevent auto updates. I check the WU service on a frequent basis to make sure it’s not re-enabled. I scan my systems and backup my Windows partition every week. If ever MS messes up my system I will restore it from backup. This will also take care of any security corruptions, if I am attacked, which has not ever happened since I’ve been using WinNT–the first Windows version I migrated to from DOS. In my estimate the risks are way smaller than the all-consuming nonsense I would have to put up if I went to group A or B, which may be defeated by MS soon anyway.
This enables me to keep working without spending enormous time to monitor and figure out how to cope with patches and their consequences, to escape increasingly overwhelming spying and to waste time and effort learning how to work with a constantly changing OS for no added value whatsoever.
There will never be any update or upgrades to the current versions on my systems for as long as I live. And at this stage of my life I do not intend to put up with the absurdities of Linux or Mac.
I suspect that if a vast majority of users did the same MS would stop its nonsense. But users can be easily herded and I am sorry to say, they deserve what they get.
2 users thanked author for this post.
-
Sessh
AskWoody LoungerApril 25, 2017 at 12:21 pm #110804I don’t blame you. I have been passively keeping an eye on Linux for years, but it’s only now that it seems to be good enough to give it a try. I think it’ll get better over time and has nowhere to go but up. When a company is so desperate to control what people want as MS seems to be, that’s a huge red flag to me. How much more desperate are they willing to get over time? I feel like I have less control over my PC now than ever before.
Linux is far from perfect, but I am so jaded with Microsoft now that I’m finally pushed to wanting to actually try it. The stars have aligned just right and Ubuntu and Ubuntu-based Linux distros seem to be pretty good systems and only getting better. I’ve never been a fan of Mac, though. Not sure why that is, but oh well. Like you, I haven’t felt like dealing with learning a new OS.. until now. We’ll see what happens.
1 user thanked author for this post.
-
anonymous
GuestApril 26, 2017 at 12:54 pm #111211Even if I agreed with you about Linux — and I don’t — it’s too late for me. I have never used any OS other DOS and Windows from NT on. For me to learn Linux and find new apps that correspond to the ones I’ve been using for decades it’s not worth it.
I have cleaned out Win10 1511 of Edge, Cortana and bloat and I will continue to use it without updates as long as I can. I make frequent backups of the system partition and if anything goes wrong I will simply restore it.
Ditto for my Win7 system in group W. When the hw dies, I have an ISO of Win10 1511 which I will install on the new hw, clean it up too (I kept a journal of what I did) and continue without updates.
That’s the only strategy I see that won’t bogg me down and destroy my ability to work.
3 users thanked author for this post.
-
-
-
-
zero2dash
AskWoody LoungerApril 25, 2017 at 12:59 pm #110828I’m kinda there and kinda not.
I’ve split a partition on my boot SSD several times now, installed Ubuntu MATE, and then after a few days, deleted the partition.
Eventually, it’ll stay…I’m just not fully there yet.A word of advice, if I may – stick with a flavor of Ubuntu, no matter what you do. Their software repository is huge and has pretty much anything and everything you could ask for. Mint is based off Ubuntu (which itself is based off Debian), but Mint stays a bit farther behind and I’m not as big a fan of the Cinnamon DE as some people. After trying quite a few (MATE, Cinnamon, KDE, XFCE, Budgie, and Unity), MATE is easily my favorite. It’s laid out and organized so well. Ubuntu MATE is basically Ubuntu with the MATE DE; for instance, Kubuntu is Ubuntu+KDE, Xubuntu is Ubuntu+XFCE.
Linux is a lot easier of a reach nowadays. Any apps you can’t find in the repositories or the software catalog/software center, you can probably download online as a .deb file (which is basically Ubuntu’s version of a .exe/.msi installer). You don’t have to compile apps or any crazy stuff like that with Ubuntu, which is another positive for it. Again, Linux has come a long way to being a useful desktop environment for the masses.
1 user thanked author for this post.
-
anonymous
GuestApril 30, 2017 at 11:56 am #112022I saw the same (WU suddenly appeared to have been changed to automatically install) some weeks ago. At the time I simply assumed that I had made a mistake somehow and was fortunate enough to catch it downloading updates before it installed them.
I’ve managed to avoid issues with W7 updating so far but I agree with a few others here that I have finally lost my patience and am in the process of moving to Linux. This move is non-trivial. The benefit of Windows had always been the consumer-level model for compatibility and support of hardware with software across a very broad range, a benefit I have always been willing to pay good money for. My calculation now is that even with Group B style instructions widely available, I can’t stand the hassle, I don’t want to wait for Microsoft to pull the rug by some forced method (which I am sure is coming), and I’m not willing to go Group W.
So I installed Mint last week, will try Ubuntu this week, and probably Fedora or CentOS the week after. Then I’ll make a decision and run Linux with a W7 virtual machine as long as I can, before shifting to a W10 virtual machine, just to have Windows when it is needed.
This is a personal choice driven not by an idealogical dislike for Microsoft or Windows, but by the threshold of reasonable business practice being overstepped and me having the ability to avoid the monopoly. I’ve paid money for the Operating System and do not accept that this includes a license to forcibly monetize my ongoing use of said OS (straws breaking the camel’s back being GWX, the blackmail around security only updates, the obfuscation and hiding of actual content in updates, and the lack of visibility around what Microsoft take from machines).
4 users thanked author for this post.
-
anonymous
GuestApril 30, 2017 at 7:08 pm #112067Could not agree more Bro, I am doing the same thing. (Linux Mint) M$ will someday rue the day it started this downward path of destroying its user base, using us Home O/S users as Beta testers and all the other accompanied nonsense of forced updates etc. Power to the people!! who refuse to accept this Win10 “1984” garbage. Linux will be the dominant O/S one day in the future and M$ execs will be left in desperation wringing their hands in the meeting rooms trying to workout how to extract M$ from the mess of their own making. lol.
1 user thanked author for this post.
-
anonymous
GuestApril 30, 2017 at 9:32 pm #112070@ anonymous#112067
M$ will someday rue the day it started this downward path of destroying its user base, using us Home O/S users as Beta testers and all the other accompanied nonsense of forced updates etc.
Very unlikely because M$ have got most of the corporations in the bag since M$ have an effective market-monopoly since the late 1990s, ie most corporations are locked into the Windows Enterprise ecosystem. M$ make most of their money from the sales of Windows licenses from the Enterprises, and not from Consumers. That is why Win 10 Home users are being used by M$ as Beta-testers to mostly benefit the Enterprise-users.
. . So, M$ won’t really be bothered if some consumers reject Win 10 and move to Linux or MacOS. Furthermore, many Consumers are also locked into the Windows ecosystem, eg online gamers.
. . Come 2020/2023, if things don’t change, many corporations and consumers will have no choice but to upgrade to Win 10 from Win 7/8.1, similar to what happened when the 2001 Win XP reached EOL in 2014.2 users thanked author for this post.
-
anonymous
GuestMay 1, 2017 at 1:48 am #112096@ anonymous#112070
“Very unlikely”
Yes agreed, that’s more than likely the case and us Home users could more or less be considered collateral damage in the M$ distorted desire to chase the high end dollars and not keep its current user base. However, If enough Home users went to other o/s’s then the question is, who does the Beta testing for the more desired customers that M$ is angling for? If the Home (even Pro as they are becoming very similar to the Home user situation) user base shrunk enough to make the current Beta testing regime untenable because of sheer loss of numbers, then that would be an interesting situation as I doubt the Enterprise/Business users would put up with the quality of the upgrades that Home users are currently subjected to. The whole shebang could very well be a house of cards, in the end.
For me, being a Win10 Home user is akin to being slapped in the face continually (that’s the poor quality forced updates), and one may put up with it for an indeterminate length of time, but it will eventually take its toll and one will eventually look elsewhere for one’s own sanity. So it boils down to just how much and for how long can the Win10 Home user take. This little duck is flying the coop, and I think many others will do the same, so it is just how many say “enough is enough” and act, to start the snowball rolling. Power to the people!!
1 user thanked author for this post.
-
anonymous
GuestMay 1, 2017 at 3:02 am #112104
-
-
anonymous
GuestApril 25, 2017 at 11:00 am #110755zero2dash
AskWoody LoungerApril 25, 2017 at 9:30 pm #111018All the sudden now I have an unstable system. Just had a BSOD; Nirsoft BlueScreenView says it’s Hal.dll and ntoskrnl.dll related. System has been rock solid until now. Anecdotal, but now I have another time I’ve updated and MS has screwed my machine up. I’m done. Thank goodness for Veeam Endpoint Backup, I can reimage to the 21st before I installed these updates.
Ubuntu MATE partition is going back on too ASAP. I’m done. My reliance on MS at home is over. My system is still thrashing my D drive for some reason too, and is unusable. I’m just done.
3 users thanked author for this post.
-
anonymous
Guest
Gaugino
AskWoody LoungerApril 26, 2017 at 3:20 pm #111264Also noticed that kb4015550 (Security Monthly Quality Rollup for Windows 8.1) was downloaded by WSUS offline several days ago. I also use the option to download ‘security only updates’ instead of ‘quality rollups’, so such a behavior of WSUS offline was rather unpleasant for me. Just in case, today I decided to run UpdateGenerator once again and found the following line in the log file – “Info: Deleted ..\client\w63-x64\glb\windows8.1-kb4015550-x64_eff3caa14297b47e4c19d28df23fd56599a27a45.cab”. Now the corresponding file is absent in the client directory.
I think that some time is necessary for the WSUS offline team to check the list of updates and to adjust it properly.1 user thanked author for this post.
Schnarph
AskWoody LoungerApril 26, 2017 at 4:49 pm #111291I have been using WSUS offline for the last few months. On the UpdateGenerator, have checked “Use ‘security only updates’ instead of ‘quality rollups’ “. I check the wsusoffline\client\w61-x64\glb folder for before running the UpdateInstaller. So far there are no unnecessary KB’s (KB2952664, etc). It is much easier for me to double check the .cab files and standalone packages now than it was at first, sorting by date created. I doubt it makes any difference, but I use the UpdateGenerator to copy the updates to a USB stick before running the UpdateInstaller on the stick.
I run a Macrium image backup of all drives before running the UpdateInstaller but have not needed to rollback yet on the three Win7 machines here. The only thing I haven’t figured out yet is how to get WSUS offline to download or install the monthly MSRT so I download that one manually, copy it to the same stick, and run it after the UpdateInstaller is done.
*Edit* I have not yet run WSUS offline since April patch Tuesday, I will do so tonight and see if it grabs the April Quality Rollup. I always wait for MS-Defcon 3 but still check the w61-x64\glb folder before running.
1 user thanked author for this post.
anonymous
GuestApril 25, 2017 at 8:58 am #110696Applying the monthly Group B security only updates doesn’t seem unwieldy to me. There are very few security only updates to download, perhaps one for Windows, one for IE, one for .Net frameworks. Let WU/MU take care of Office updates.
If you want to go from Group W to Group B then some effort is involved because the security only updates are not cumulative. But if you have been in Group B all along and have stayed current then Group B, in my opinion, remains a viable alternative to giving MS a free hand.
-
wdburt1
AskWoody PlusApril 25, 2017 at 9:07 am #110704I’ll second that. I have kept up with the security-only updates on two machines, installing them about the end of the month in which they are issued. At that time I have also checked Windows Update. I have found few head-scratchers there; very few Important updates at all and the snoopware conveniently grouped in the Optional updates, unchecked. Some months I have found nothing in Windows Update that I needed to install. Overall, the process is far from ideal but tolerable. Keeping fingers crossed that M$ doesn’t take it all away…
-
fp
AskWoody LoungerApril 25, 2017 at 12:21 pm #110803Yes, doing that too for Win7. But I think the issue here is MS increasingly disabling this strategy by messing with the user settings that prevent automated patch installs.
As to Win10 — 1511 is all I need and after cleaning it off Cortana, Edge and the rest of the bloat there is no justification for patching that would bring them back. In case of trouble I restore from backup.
1 user thanked author for this post.
-
Bill C.
AskWoody PlusApril 25, 2017 at 3:50 pm #110909I whole heartedly agree with this post. I have been Group B for my home built desktop (Win7Pro-64 SP1) and my Lenovo T440 laptop (also Win7Pro-64 SP1) since its founding/creation/inception here on AskWoody.com. I initially had the GWX applet installed, but then found it made the machine sluggish and found out about the whole telemetry issue and uninstalled all the bad patches. I suffered though the sabotaged WU phase and the Intel Bluetooth mess.
I have found that for me, the nest way is to stage the rollout of the Patch Tuesdays. I wait a week at least for Office updates and check here and a number of other sources and do a Google search for issues. I then install them via manually initiated Windows Update (set to Do Not Check) on the desktop. A few days later I do the same for the Laptop. I test for any issues, including printing, etc., checking if it opens in Protected Mode or Compatibility Mode, etc. A week later I do the .net rollup from WU. Same process as Office. A few days later I do the IE Updates. The last for me it the Monthly Security Only patch. That is usually when the Def-con here is lowered.
Precautions I take are I check all the patches in the MS Update Catalog to see if they are removable, and read what they include and supercede. I always check to make sure they install OK. I also never install any hardware driver via WU. I always check before and after updating to ensure that WU settings have not changed.
The other PC I personally update is an older AMD Acer Laptop that is Group A. It is Win7Home-64 SP1. The only MS software remaining is Windows. It runs LibreOffice and relies on web-based email. The default browser is 64bit Firefox. That one is set to Do Not Check, but when it goes back to its original owner, I will set it to Check but let me decide or Automatic. The one thing I do see with that machine is more HDD thrashing, probably due to the telemetry scans. I use Belarc Advisor and the GRC testing website for security testing for all the machines.
I am comfortable with the Group B as long as it works. It is a pain, but I will not reward MS for their sabotage by going group A or using Win10 on my personal machines. If Group B becomes untenable, it will be Group W. An organizational laptop I have to use with Win10 is only connected via wired network when it is specifically being updated as it has to work when it is being used and cannot stop for an update. I have turned off wireless and do not connect it except for updating. I have gotten used to the interface of Win10 (sort of reminds me of a Fisher-Price device), but the other Win10 objectionable issues are not going away.
I am also moving to a Linux machine for the main machine. I currently have 4 Linux machines, an old AMD Athlon desktop with LXLE, an older AMD laptop with Ubuntu 12.04 awaiting a new OS, an AMD netbook with Ubuntu 16.04.1 LTS, and a Lenovo T420 with Ubuntu 16.04.1 LTS. The Lenovo is a daily user, and the netbook is a travel laptop when not suing the Windows 7 laptop. I also do a lot of document exchanging to test the MSOffice 2010-LibreOffice compatibility issues (no major issues with what I do).
I am gathering parts and still looking at distros for a new built up Linux machine. It will probably be either Ubuntu 16.04 or Mint 18. It will be either a Sky Lake Z170 or Kaby Lake Z270 motherboard using an i7 CPU (still researching Ryzen alternatives) for using the M.2 interface for SSD. It will have removable HDD bays for distro testing. I am also using Tails on a USB3 thumb drive on all the machines.
Sorry for the length of this post.
2 users thanked author for this post.
ebrke
AskWoody LoungerApril 29, 2017 at 1:49 pm #111844I’m trying hard to continue in Group B for elderly parent’s win7 machine. With the info I’ve been able to get here at AskWoody (very grateful), I’ve not had too much trouble so far. Will continue as long as possible out of sheer cussedness and not wanting MS to manipulate me. I’ve personally been running OpenSuSE linux for years on older hardware inherited from parent after it won’t support win any longer.
2 users thanked author for this post.
-
Northwest Rick
AskWoody LoungerApril 30, 2017 at 6:25 pm #112062
abbodi86
AskWoody_MVPApril 25, 2017 at 9:08 am #110705What I want to know is if there’s a real, valid, easy way for Win7 and 8.1 customers to install Monthly Rollups yet opt out of most of the snooping.
Sure, simple commands gathered in batch script takes care and disable the “snooping” components effects in the Rollup
https://pastebin.com/vv3cgmjNjust run it as administrator after any Rollup installation
-
woody
ManagerApril 25, 2017 at 9:57 am #110728So you would recommend installing the Monthly Rollup, then running the telemetry-negating script, every month?
I see https://pastebin.com/vv3cgmjN is being updated regularly….
2 users thanked author for this post.
-
abbodi86
AskWoody_MVPApril 25, 2017 at 12:41 pm #110814As i said, it doesn’t need to be ran every month
that’s only for users who have no knowledge or read the Windows Update history KB articlesother users should only needs it once
and in the future, only if the history page mentioned that telemetry service is updated or “addressed”
http://go.microsoft.com/fwlink/p/?LinkId=821934
-
ch100
AskWoody_MVPHiFlyer
AskWoody LoungerMay 1, 2017 at 4:41 am #112113What I want to know is if there’s a real, valid, easy way for Win7 and 8.1 customers to install Monthly Rollups yet opt out of most of the snooping.
Sure, simple commands gathered in batch script takes care and disable the “snooping” components effects in the Rollup
https://pastebin.com/vv3cgmjNjust run it as administrator after any Rollup installation
Dumb question: Just the “Raw Paste Data” script?
1 user thanked author for this post.
-
satrow
AskWoody MVP
radosuaf
AskWoody LoungerApril 25, 2017 at 9:17 am #110707I’m in Group A and just opted out of CEIP and turned off as much as possible from Task Scheduler.
The other option would be to leave clean 8.1 Update 3 install with all updates disabled.
Group B is a bit too much of a hassle, really.
Fractal Design Pop Air * Thermaltake Toughpower GF3 750W * ASUS TUF GAMING B560M-PLUS * Intel Core i9-11900K * 4 x 8 GB G.Skill Aegis DDR4 3600 MHz CL16 * ASRock RX 6800 XT Phantom Gaming 16GB OC * XPG GAMMIX S70 BLADE 1TB * SanDisk Ultra 3D 1TB * Samsung EVO 840 250GB * DVD RW Lite-ON iHAS 124 * Windows 10 Pro 22H2 64-bit Insider * Windows 11 Pro Beta Insider1 user thanked author for this post.
anonymous
GuestApril 25, 2017 at 9:24 am #110706All I can say is, I have been in Group B from the beginning and so far, so good. True, tomorrow Microsoft ight decide to exclude all 64bit machines from WU, as being too advanced – I wouldn’t put it beyond them. But until something like that happens, my W7 system is doing OK.
As for our future: our future is three ears at the most; I suspect that, as 2020 approaches Microsoft will realize that we are never switching, and just leave us be. After W7 i sno longer supported, it is W10, MAC or Linux for us (no disrespect meant to other OS!) so why spend effort and collect bad publicity when time will do their dirty work for them?
2 users thanked author for this post.
anonymous
GuestApril 25, 2017 at 9:28 am #110710I went with Group A when the cumulative updating started simply because I did not believe the Group B security updates would remain “pure” over time given MS’s penchant for inconsistency in the application of their stated policies. My primary fear was that they would introduce a bug in a security update and then later include the fix in a non-security update. The more general problem now is that MS is using Windows Update to pretty much do whatever they want as they try to “goose step” W7 and W8/8.1 users toward W10. In it’s current iteration, I do not intend on using W10 and have been evaluating Linux distros in VMs using apps like Libre Office, GIMP and Mozilla Thunderbird to see how I get by with most needs. I am also beginning to look at Mac OS as a future alternative. At the current time, these options all have some hairs on them as I do use some Windows only software that will not run under using Wine on Linux. I am running W8.1 x64 and so I have time to figure the future out as the OS is supported to 2023 unless MS changes its mind. I do hope for a change of certain personnel currently at MS in that the W10 issues I detest have largely originated out of the failed Windows mobile strategy. However, hope is not a strategy and some combo of Linux and Apple may be my future.
2 users thanked author for this post.
jimdunn
AskWoody LoungerApril 25, 2017 at 9:44 am #110718-
woody
ManagerApril 25, 2017 at 10:01 am #110732 -
Microfix
AskWoody MVP -
walker
AskWoody LoungerApril 29, 2017 at 2:07 pm #111848@Microfix: I had a problem with the IE11 update (KB4014661) I mistakenly started to install it before I had turned off the Windows Services, so like an idiot I tried to cancel it in the middle of the installation, and it didn’t want to stop so I deleted it.
Had a problem with the Security Only update before that, because after it had been DL & installed, and the computer had been restarted, the screen came up black, so I did a hard shut-down, and let it sit for about 5 minutes. After I turned it back on, it was functional, however “slow” to begin with.
I don’t know what I did but now when I try to install the KB4014661 I get the following message: “THE UPDATE IS NOT APPLICABLE TO YOUR COMPUTER”.
Anyone have a clue as to how I can get this “fixed” at all? I’m so weary, I almost ready to go to group A/W/ or D. Can’t take much more of this, and apologize for my complete lack of computer skills. Thank you to to anyone who could possibly help me!!
1 user thanked author for this post.
-
anonymous
GuestMay 1, 2017 at 3:18 am #112106Walker, don’t be sorry about your computer skills. You are on this forum and doing everything you can to stay up to date. I had a problem with the IE update, and gave up. (Probably because it is cumulative, and I have not updated since last October). Someone here will be sure to help you.
I haven’t updated Windows and it has been fine. Malwarebytes, Spybot, Avira, Firefox with some good security addons, IE explorer disabled and Libre Office. I scan a bit more often, but it really has been ok. Don’t despair, you are doing really well. It has reached the stage where people here are a bit confused (thread about Group B is still worthwhile) and many are expert users.
Which reminds me, Congratulations Mr Brian! You are a treasure!
2 users thanked author for this post.
-
walker
AskWoody LoungerMay 3, 2017 at 6:06 pm #112606@anonymous: Thank you so much for your message! You have really “made my day”. I’m so thankful to hear something positive about my “lack of computer knowledge and over-all ignorance about these issues”. When there are so many references which are “acronyms”, and those who are “computer literate” use them frequently while many of the others (like me) cast about trying to determine what they are talking about.
Being listed as an “administrator” alone is something that can be complex, and the “registry” is nothing a person messes with unless they really know what they are doing.
I admire your self-confidence, and the ability to stay away from so many problems which others are experiencing (with no logical explanation). I’ve never used the IE, however have tried to keep it current, and this past one from April is my first failure.
Thank you once again for your very positive and sensible approach! It is most appreciated and admired! 🙂
-
-
-
ch100
AskWoody_MVPRCPete
AskWoody LoungerApril 25, 2017 at 9:51 am #110721Our two Windows 7 machines were both Group B, but now the desktop is running LInux (Slackware–I’m old school). My browser is Pale Moon, search engine is DuckDuckGo, and my encyclopedia is Infogalactic. Adblock and Noscript both work in Pale Moon, and I’ve never installed Flash. I think it’s about as locked down as I need.
I don’t recommend Slackware for non-Linux geeks; it’s far enough off the beaten path that new software usually has to come as source code. OTOH, the Slackbuilds setup (when available) makes it pretty easy. When Pale Moon did an update, it took the machine (another underpowered laptop) about 90 minutes to make up and install it. Not sure how long it will take for the desktop. Haven’t done a script to automate most of the process, but that will happen. For those considering Group “L” as a newbie, Linux Mint or any of the Ubuntu variations seem like a good bet, and you can get software pretty much ready to go.
The laptop (used occasionally) was group B, but I’m shifting it to Group W, <i>and</i> keeping it offline. I have Quicken on it, and if I need to do any printing, I can sneakernet the data to a machine connected to the LAN. It’s getting run whenever I update Quicken, backed up, and shut down.
2 users thanked author for this post.
-
MrJimPhelps
AskWoody MVPMay 1, 2017 at 10:02 am #112139I went from Group B to Group A to Group L (Xubuntu) on my Windows 7 machine.
Actually, I have dual boot on that machine; one side has Windows 7, and the other side has Xubuntu. The Windows 7 side is in Group A. I keep Windows 7 around in case I can’t do some essential task in Xubuntu.
Group "L" (Linux Mint)
with Windows 10 running in a remote session on my file server1 user thanked author for this post.
MrBrian
AskWoody_MVPApril 25, 2017 at 9:53 am #110724My advice is referenced in knowledge base article: 2952664: Telemetry in Win7/8.1 – KB2952664, KB2977759, KB2976978, & KB3150513. Due to test results that I have not posted yet, my advice there is insufficient in some cases, because for Windows 7 if KB2952664 is installed and Diagnostics Tracking Service is not installed, KB2952664 can send data to Microsoft via another process (not via Diagnostics Tracking Service).
If you want to stop transmission to Microsoft of the newly added telemetry (in recent few years) in Windows 7, I believe that blocking network traffic to IP address 64.4.54.254 is sufficient. Optionally, you could also block network traffic to IP address 64.4.54.253, which Microsoft documents as being for telemetry settings. This page shows how to block an IP address in Windows Firewall: http://www.easysecurityonline.com/how-to-protect-windows-7-and-8-from-getting-windows-10-privacy-intrusions-too/. I have had IP addresses 64.4.54.253 and 64.4.54.254 blocked for months on my Windows 7 computer, with no apparent negative effects so far.
Also, be sure to set the operating system’s Customer Experience Improvement Program setting = No.
-
woody
ManagerApril 25, 2017 at 9:59 am #110731Any idea how this compares to Abbodi’s script https://pastebin.com/vv3cgmjN ?
1 user thanked author for this post.
-
MrBrian
AskWoody_MVP -
Microfix
AskWoody MVP -
abbodi86
AskWoody_MVPApril 25, 2017 at 12:33 pm #110810The script only removes/disable what the updates add related to telemetry
why would you need to reverse that? 🙂nonethelss, uninstalling/reinstalling monthly rollup will reverse all that
and no, it doesn’t need to be executed monthly, that’s just a fail-safe for unknowledgable users
it’s only needed if UTC (diagtrack service) get updated in future rollup, or a new version of Appraiser (KB2952664/KB2976978) is installed2 users thanked author for this post.
-
-
MrBrian
AskWoody_MVPApril 25, 2017 at 10:07 am #110736Alternately, if you are able to block network traffic by DNS endpoints (which I believe Windows Firewall can’t do), these pages contain DNS endpoints to block:
https://technet.microsoft.com/en-us/itpro/windows/deploy/upgrade-readiness-get-started
https://blogs.technet.microsoft.com/ukplatforms/2017/03/13/upgrade-readiness-client-configuration/
-
walker
AskWoody LoungerApril 25, 2017 at 1:14 pm #110839@MrBrian: I have no knowledge of what DNS actually is. I’m a (very) simple user. Win 7, 64 bit with no sophisticated programs. I don’t know if other “computer illiterate” users get confused by terms which they don’t comprehend. I’m sure most users are much more capable than I am. This is merely a reference about my own lack of capability insofar as being computer illiterate.
Thank you for all of the good advice you have provided. It is very much appreciated.
1 user thanked author for this post.
PKCano
ManagerApril 25, 2017 at 9:55 am #110725Let me start off by saying that my latest processors are Haswell, so I’m not subject to having WU blocked.
And, although I have two laptops and a desktop that still run Win7 on actual hardware, most of my Win experience now is in VMs. I can’t get away from Win yet, but for my daily use I started gradually shifting to Macs five years ago.I have Win7/8.1/10 VMs. For my Win7 and Win8.1 updating, I have been doing a cross between Group A and Group B.
1. I have hidden (only) the telemetry/compatibility related updates as listed in AKB2000003. I DO NOT hide any other updates.
2. I have “Give me updates for other Microsoft products” CHECKED
3. I have “Give me recommended updates the same way I get important updates” CHECKED, so I have very few on the “optional updates” list. Mostly Skype, drivers, Silverlight, Preview, language packs.
4. Each month, I have been manually installing the Security Only Quality UPDATE and the Cumulative Update for IE11.
5. Then I UNCHECK (not hide) the Security Monthly Quality ROLLUP for Win (and any driver updates) and install the rest that are CHECKED by default.There is not much effort to this – only the manual installation of two updates. The only hidden patches are the telemetry related ones.
The only thing I am missing from being in Group A is the non-security portion of the monthly updates.I have had no problems with updates, either on the machines running Win7 natively or the Win7/8.1 VMs
-
ch100
AskWoody_MVP -
Canadian Tech
AskWoody_MVPApril 30, 2017 at 8:54 am #111995ch100, you raise a good question. I do not believe there is any way to tell. Even if you were very organized and applied all the “security only” patches, there is no way of knowing if MS has offered the right content in that stream. They may have so far, but who knows about tomorrow?
The concept of Group B is a solid one, but the big question in my mind is whether it is based on a solid assumption: That MS will continue to faithfully and accurately reflect all the security patches there.
CT
-
MrBrian
AskWoody_MVP
-
Noel Carboni
AskWoody_MVPApril 25, 2017 at 10:10 am #110739I have a Windows 7 x64 Ultimate system that’s almost “single use” as a server. I don’t use it interactively to surf the net or do much of anything besides the very occasional test of my own products under development (it has an Intel on-chip GPU, which none of my other systems have).
Anyway, it’s been a “Group W” machine for a while, with my applying a VERY occasional security update.
With good backups in hand, I’ve just this morning applied the April security only updates for Internet Explorer and the OS. The command WMI qfe list shows ONLY KB4014661 “Cumulative security update for Internet Explorer: April 11, 2017” and KB4015546 “April 11, 2017—KB4015546 (Security-only update)” installed since the last round of updates went in back in May, 2016 (almost a year ago).
I wasn’t certain that layering the latest “Security Only” updates would leave the system viable, since it’s been out of the update loop for so long, but they went in just fine, and the system so far has started up great and is running without logged errors and without apparent operational problems (noting I have had time for only limited testing so far). I’ve been monitoring resources and so far there appear to be no leaks.
This seems to be a single data point arguing in favor of the continued ability to install Security Only updates onto an otherwise quiet system.
I suggest that the old adage “if it works, don’t fix it” still has merit, and thus continuing the line of thinking that leads to managing Group B still seems to have merit as well.
And what’s the alternative on a case by case basis? Say you can’t run some brand new version of an application because your local .net subsystem isn’t up to date, or similar… At that point you re-evaluate the risk of bringing the whole system up to date with the cumulative everything update. So the difficulty taking a “fire exit” from Group B over to Group A is pretty small, right?
-Noel
NoLoki
AskWoody LoungerApril 25, 2017 at 10:11 am #110740For all the bombast from MS about their new across the board update strategy, they reluctantly fell to pressure from sys admins who wanted the security and non-security updates separated on W7. Home and Pro W7 users should be rejoicing that they were the beneficiaries of this.
As a tech spec I prefer Group B (for W7). It is not at all unwieldy or difficult to obtain the security-only patches. For those who do not want to navigate the MS Catalog, there a many sites that provide direct downloads. It couldn’t be easier, just click on it. There is also WUMT.
MS has stated that W7 will not be improved, just maintained until EOL. There is no reason to doubt that statement. If they break something that is non-security, my W7 systems will be immune. When MS screws up a security fix or sneaks a non-security patch into the bundle, that month’s patch can be ignored as the security-only patches are non-cumulative. It is not ideal, but at least I get to make the decision.
3 users thanked author for this post.
-
Noel Carboni
AskWoody_MVPApril 25, 2017 at 10:35 am #110748…that month’s patch can be ignored as the security-only patches are non-cumulative.
I have never been clear on that point…
Note the wording of the KB4015549 patch:
- This Security Monthly Quality Rollup also includes improvements and fixes from previous monthly rollups.
(emphasis mine)
and
- The security fixes that are listed in the “Summary” section of Security Monthly Quality Rollup 4015549 are also included in April 2017 Security Only Quality Update 4015546
4015546 is the one that excludes Internet Explorer patches so they can be delivered in their own cumulative security only updates.
All that sure sounds like the security updates ARE in fact cumulative.
-Noel
-
anonymous
GuestApril 29, 2017 at 9:46 pm #111891There are two types of security patches – Security Monthly Quality Rollups, which are cumulative, and Security Only Quality Updates, which aren’t. This information comes directly from Microsoft (https://blogs.technet.microsoft.com/windowsitpro/2016/10/07/more-on-windows-7-and-windows-8-1-servicing-changes/).
1 user thanked author for this post.
-
grayslady
AskWoody LoungerApril 25, 2017 at 10:41 am #110751I have been in Group B all along with no problems, thanks to this website. When I had to re-install my Windows 7 Pro back in January, due to a hard drive crash, I also eliminated all the HP bloatware, and now have a machine running cleaner and faster than I thought possible. I don’t use any ancillary MS products, because I simply can’t afford them. Even if I could afford them, I prefer Open Office and Thunderbird because each program has never lost sight of what it was originally designed for. New does not necessarily equal improved. MS seems to be moving to a rentier format, and I simply don’t trust the motives of a rentier-based company.
Increasingly, I believe that the OS is only part of the equation when it comes to running a secure, private and reasonably convenient system. The OS settings, the browser and its settings, the router and its settings, the firewall and its settings, the email server, and the isp, are all part of the equation, not to mention common sense usage.
5 users thanked author for this post.
EyesOnWindows
AskWoody LoungerApril 25, 2017 at 10:50 am #110754Beware: I had my WU service disabled in Services and before that, it was set to never check for updates and yet, yesterday I saw that WU had re-enabled itself. It changed it’s setting from disabled to Automatic (Delayed) and had started itself and I never use that “Delayed” setting ever for anything. It doesn’t appear to have installed anything and I’m not sure what could have triggered it, but it happened. Make sure you keep checking on it every now and then.
This is remarkably similar to what Noel Carboni encountered:
It CAN happen. I’ve personally seen it happen.
This year, for example, at the time I installed TurboTax on my Windows 8.1 workstation I shortly thereafter found unexpected entries in my firewall log that showed Windows Update had been started – even though I had set it to Disabled – and was trying to contact Microsoft (it failed, because I also reconfigure my firewall to disallow updates).
HP Compaq 6000 Pro SFF PC / Windows 10 Pro / 22H2
Intel®Core™2 “Wolfdale” E8400 3.0 GHz / 8.00 GB
HP ProDesk 400 G5 SFF PC / Windows 11 Pro / 23H2
Intel®Core™ “Coffee Lake” i3-8100 3.6 GHz / 16.00 GB4 users thanked author for this post.
-
Sessh
AskWoody Lounger -
Noel Carboni
AskWoody_MVPApril 25, 2017 at 11:15 am #110764Also note that (on Win 8.1 at least) there are jobs in the Task Scheduler in the Task Scheduler Library > Microsoft > Windows > Windows Update section that could try to re-enable things. I find I have to re-disable them from time to time.
Though possibly justified at a “big picture security” level, it sure seems Microsoft really, really doesn’t want to lose the ability to change the software on our computers upon their choice.
-Noel
-
fp
AskWoody Lounger -
Noel Carboni
AskWoody_MVP
-
-
PKCano
ManagerApril 25, 2017 at 11:17 am #110768I have seen it happen if you install Office or any of the Office Service packs. At the end of the installation, there is a box that pops up with two choices – Use “recommended settings” (which include updates Office) or keep you current settings. If you choose “recommended settings” (implies auto update for Office, which comes through WU) you are actually setting WU to auto. Surprise!
There are other MS products with this popup box at the end of installation. And Noel found that Turbo Tax installation flips WU also.
-
Sessh
AskWoody LoungerApril 25, 2017 at 11:26 am #110771I’m not sure what did it with me. Only thing I can think of is I uninstalled a few updates, but that has never turned WU on before as it’s not the first time I’ve selectively removed updates. The ones I removed were KB3021917, KB3068708 and KB3080149. That shouldn’t trigger WU to take on a mind of it’s own. It never did before?
1 user thanked author for this post.
MrBrian
AskWoody_MVPApril 25, 2017 at 10:58 am #110756-
Noel Carboni
AskWoody_MVPApril 25, 2017 at 11:27 am #110774Can that software watch the Microsoft catalog and advise when security only updates are made available? If so, that sounds pretty cool.
As far as checking what’s installed yourself, there’s the WMIC qfe list command.
Beyond that, I wrote a simple script that when scheduled to run regularly can be used with a file comparison tool to check for changes to the list of installed updates, among a number of other lists such as scheduled jobs, services, what processes are running…
For those who haven’t seen it:
https://www.askwoody.com/forums/topic/a-tool-for-keeping-track-of-system-changes
This can be valuable for helping to determine whether something’s been unexpectedly changed, and if you run it via the scheduler, when it happened.
-Noel
2 users thanked author for this post.
MrBrian
AskWoody_MVP-
woody
Manager -
Noel Carboni
AskWoody_MVPApril 25, 2017 at 11:47 am #110781The Sphinx Windows Firewall Control package can block or allow specific network traffic by some services, though the breakdown isn’t complete. However, it’s possible (I’m doing it) to reconfigure the firewall setup easily to block or allow Microsoft’s Windows Update sites, which will effectively block or allow Windows Update operations.
On my Win 8.1 system I reassign the above zone to svchost.exe whenever I want to check Windows Updates. I normally have a zone that does not include the “WU” prefixed entries shown above assigned to svchost.exe, which effectively means Windows Update will not be possible.
Another approach, if you don’t want to go with a 3rd party firewall, could be to block the name resolution of specific site names used for Windows Update via your hosts file or even better a DNS proxy server. These things can be reconfigured fairly easily to allow updates as well. Here’s a list of the servers I’ve seen contacted during Windows Updates from Win Vista, 7, 8, and 10 systems over the past few years.
au.download.windowsupdate.com au.ds.download.windowsupdate.com au.v4.download.windowsupdate.com download.windowsupdate.com ds.download.windowsupdate.com fe2.update.microsoft.com fe2.ws.microsoft.com fg.ds.b1.download.windowsupdate.com fg.ds.download.windowsupdate.com fg.v4.download.windowsupdate.com officeclient.microsoft.com sls.update.microsoft.com update.microsoft.com v4.download.windowsupdate.com windowsupdate.microsoft.com ww.download.windowsupdate.com www.update.microsoft.com
-Noel
-
fp
AskWoody Lounger -
Noel Carboni
AskWoody_MVPApril 25, 2017 at 6:16 pm #110961Do you mean adding these to HOSTS file? Incidentally, how do you get access to edit the file?
If not, what do you mean?
I implied perhaps the hosts file might be useful, but I don’t actually do that myself any more… I have an open source software package that I use called “Dual DHCP DNS Server” that fields DNS requests, and attempts to resolve the requests from it’s local definitions and cache before sending the names out to a real online DNS server (e.g., OpenDNS).
One possibility is to set up a particular site name to locally resolve to 0.0.0.0, which effectively causes a “not found” response without ever having asked the online server. Voila, blacklisted.
I’ve written about this in my description of my security environment. Within that there are some further links…
https://www.askwoody.com/forums/topic/a-description-of-my-quite-effective-security-environment-long/
-Noel
1 user thanked author for this post.
-
-
-
MrBrian
AskWoody_MVPApril 25, 2017 at 1:04 pm #110831Caveat: I may have read that the hosts file is bypassed by Windows on purpose in some cases.
3 users thanked author for this post.
-
satrow
AskWoody MVPApril 25, 2017 at 1:18 pm #110840I’ve read the same and if that’s correct then blocking specific IPs at the router would be preferable, where possible – DD-WRT, Tomato or Open WRT on a suitably secure compatible router might be required for the necessary fine-grained blocking needed – if all those router distros are still current, I’m not up to date on that.
1 user thanked author for this post.
-
MrBrian
AskWoody_MVP -
Noel Carboni
AskWoody_MVPApril 25, 2017 at 4:24 pm #110913What addresses? Most of those servers are actually banks of machines. The different addresses I’ve seen in recent history for fe2.update.microsoft.com alone are:
134.170.165.248 134.170.165.249 134.170.165.251 134.170.165.253 134.170.51.190 134.170.51.246 134.170.51.247 134.170.53.29 134.170.53.30 134.170.58.118 134.170.58.121 134.170.58.123 134.170.58.125 134.170.58.189 134.170.58.190 157.56.96.123 191.232.80.58 191.232.80.60 191.232.80.62 191.234.72.183 191.234.72.186 191.234.72.188 191.234.72.190 207.46.114.58 23.103.189.125 23.103.189.126 23.103.189.157 23.103.189.158 65.55.138.112 65.55.138.114 65.55.138.126 65.55.138.186 65.55.163.221 65.55.163.222 66.119.144.157 66.119.144.158 66.119.144.190
And there’s no guarantee there won’t be others tomorrow.
That’s why a name-based firewall like the one I’ve chosen – and/or DNS-based blocking is practically a necessity.
-Noel
2 users thanked author for this post.
-
MrBrian
AskWoody_MVPApril 25, 2017 at 4:47 pm #110929@Noel: The only IP addresses that I’ve seen in my tests for the telemetry added by Microsoft in the past few years are:
64.4.54.254 (for telemetry data)
64.4.54.253 (for telemetry settings)
It’s possible that there could be other telemetry-related IP addresses that I haven’t seen in my tests, or that the telemetry-related IP addresses could change in the future.
1 user thanked author for this post.
-
Noel Carboni
AskWoody_MVPApril 25, 2017 at 5:42 pm #110949That’s just one kind of telemetry.
In recent history, I’ve seen telemetry server statsfe2.update.microsoft.com resolved to these addresses:
131.253.14.153 64.4.54.22 65.52.108.153
vortex.data.microsoft.com (and a couple of synonyms, v10.vortex-win.data.microsoft.com and web.vortex.data.microsoft.com) to these:
111.221.29.254 191.232.139.254 64.4.54.254 65.55.44.109
What you call “telemetry settings” is aka settings-win.data.microsoft.com or settings.data.microsoft.com (settings sync?), which have resolved to:
111.221.29.253 191.232.139.253 64.4.54.253 65.55.44.108
Nothing is simple, unfortunately.
-Noel
-
Noel Carboni
AskWoody_MVPApril 25, 2017 at 5:45 pm #110950Just a small part of my anti-snooping blacklist entries, this part being (mostly) Microsoft…
iecvlist.microsoft.com=0.0.0.0 ieonline.microsoft.com=0.0.0.0 r20swj13mr.microsoft.com=0.0.0.0 spynet2.microsoft.com=0.0.0.0 spynetalt.microsoft.com=0.0.0.0 wdcp.microsoft.com=0.0.0.0 wdcpalt.microsoft.com=0.0.0.0 a-0001.a-msedge.net=0.0.0.0 ac3.msn.com=0.0.0.0 blu405-m.hotmail.com=0.0.0.0 bn2-s.gateway.messenger.live.com=0.0.0.0 choice.microsoft.com.nsatc.net=0.0.0.0 choice.microsoft.com=0.0.0.0 cm.ac3.msn.com=0.0.0.0 compatexchange.cloudapp.net=0.0.0.0 corp.sts.microsoft.com=0.0.0.0 corpext.msitadfs.glbdns2.microsoft.com=0.0.0.0 cs1.wpc.v0cdn.net=0.0.0.0 df.telemetry.microsoft.com=0.0.0.0 diagnostics.support.microsoft.com=0.0.0.0 feedback.microsoft-hohm.com=0.0.0.0 feedback.search.microsoft.com=0.0.0.0 feedback.windows.com=0.0.0.0 i1.services.social.microsoft.com.nsatc.net=0.0.0.0 i1.services.social.microsoft.com=0.0.0.0 m.hotmail.com=0.0.0.0 oca.telemetry.microsoft.com.nsatc.net=0.0.0.0 oca.telemetry.microsoft.com=0.0.0.0 onesettings-hk2.metron.live.com.nsatc.net=0.0.0.0 onesettings-bn2.metron.live.com.nsatc.net=0.0.0.0 onesettings-cy2.metron.live.com.nsatc.net=0.0.0.0 pre.footprintpredict.com=0.0.0.0 redir.metaservices.microsoft.com=0.0.0.0 reports.wes.df.telemetry.microsoft.com=0.0.0.0 s.gateway.messenger.live.com=0.0.0.0 services.wes.df.telemetry.microsoft.com=0.0.0.0 settings-sandbox.data.microsoft.com=0.0.0.0 settings-win.data.microsoft.com=0.0.0.0 sls.update.microsoft.com.akadns.net=0.0.0.0 sqm.df.telemetry.microsoft.com=0.0.0.0 sqm.telemetry.microsoft.com.nsatc.net=0.0.0.0 sqm.telemetry.microsoft.com=0.0.0.0 stats.update.microsoft.com=0.0.0.0 statsfe1.ws.microsoft.com.akadns.net=0.0.0.0 statsfe1.ws.microsoft.com=0.0.0.0 statsfe2.update.microsoft.com.akadns.net=0.0.0.0 statsfe2.update.microsoft.com=0.0.0.0 statsfe2.ws.microsoft.com.akadns.net=0.0.0.0 statsfe2.ws.microsoft.com=0.0.0.0 survey.watson.microsoft.com=0.0.0.0 telecommand.telemetry.microsoft.com.nsatc.net=0.0.0.0 telecommand.telemetry.microsoft.com=0.0.0.0 telemetry.appex.bing.net=0.0.0.0 telemetry.microsoft.com=0.0.0.0 telemetry.urs.microsoft.com=0.0.0.0 vortex-db5.metron.live.com.nsatc.net=0.0.0.0 vortex-hk2.metron.live.com.nsatc.net=0.0.0.0 vortex-sandbox.data.microsoft.com=0.0.0.0 vortex-win.data.microsoft.com=0.0.0.0 vortex.data.microsoft.com=0.0.0.0 watson.live.com=0.0.0.0 watson.microsoft.com=0.0.0.0 watson.ppe.telemetry.microsoft.com=0.0.0.0 watson.telemetry.microsoft.com.nsatc.net=0.0.0.0 watson.telemetry.microsoft.com=0.0.0.0 wes.df.telemetry.microsoft.com.nsatc.net=0.0.0.0 wes.df.telemetry.microsoft.com=0.0.0.0
Imagine each of the above resolving into banks of server addresses and you begin to get an idea…
-Noel
2 users thanked author for this post.
-
MrBrian
AskWoody_MVP -
Noel Carboni
AskWoody_MVPApril 25, 2017 at 6:03 pm #110958DNS proxy server logs, and lists I’ve gathered over time from other sources online.
I’ve obsessed over controlling what my computers contact for quite a while.
My current fully qualified site blacklist is currently 61,840 lines long, and my wildcarded list – which is where some real additional protection occurs – is 25,236 lines long.
-Noel
-
ch100
AskWoody_MVP -
PKCano
Manager -
fp
AskWoody Lounger
-
-
MrBrian
AskWoody_MVPApril 25, 2017 at 11:57 am #110789Blocking a service:
How to Create Advanced Firewall Rules in the Windows Firewall
-
MrBrian
AskWoody_MVP
cyberSAR
AskWoody PlusApril 25, 2017 at 11:25 am #110770I’ve been thinking about switching over to group A just because it’s so tedious to keep up with all the updates. We have clients running Win7, 8.1 and 10 with a few 32-bit versions of each mixed in. Group B isn’t so hard on the clients we maintain weekly or monthly, but becomes a chore on the ones we do quarterly or on no defined schedule, or for new clients signing up for a maintenance service with us.
Heck I had an HP AIO machine come in last week that has been “running slow” for a year according to the client. It was still trying to install the upgrade from 8.1 to 10! Was able to stop it, clean it up and had it running decently but ended up doing a clean install of 8.1 for other reasons. For these clients, after we get them sorted, we set them to automatically install updates but not recommended.
How I long for the good ole days when a weekly maintenance task took a few minutes.
1 user thanked author for this post.
JNP
AskWoody LoungerApril 25, 2017 at 11:26 am #110772Aside from the matter of telemetry, which is a consideration, in a sense what Woody just posted about Win10, and a Group B, illuminates why I decided to go with Group B and will continue to do so. In the past year, or so, as we have all witnessed, Windows Update has been a mess. Bad files, bogus drivers, etc. Windows is presently, uncertain, unclear, unreliable, directionless, etc. when it comes to updating, whether it be Win 7, Win 8.1 and even Win 10. Until the dust settles, assuming a fact not in evidence (as we say in the legal field), a less is more approach seems advisable with updates; hence Group B. My system is stable, I possess several layers of third party security programs. So, keep it simple, varied, and less Microsoft (like don’t use Microsoft Word or IE unless you have to) seems to be a safer, more stable approach.
As something of an aside, but illustrative, for the past month or so, WU has been pushing, at least to me, Silverlight. I keep hiding it, WU keeps pushing it back at me. This is new behavior. I have no definitive answer as to why this is happening but, as the trust level is so low right now with Microsoft, I see no compelling reason to install this optional plug-in.
-
fp
AskWoody Lounger -
ch100
AskWoody_MVP -
Noel Carboni
AskWoody_MVPApril 25, 2017 at 6:33 pm #110972This is what can cause exponentially more problems than any Microsoft update.
And yet he clearly states his system is stable. Perhaps “this” isn’t what you imply it to be.
I personally employ a fair number of layers as well, and my systems are rock solid. I only ever need to reboot because of such things as installation of updates.
And I’ll wager mine are also as efficient as any out there, because my layers are not turnkey antivirus solutions sloppily installed on top of one other, as you may have implied. Not at all.
Don’t assume multi-layered approaches are necessarily done ham-handedly. We have a lot of smart experts weighing in on this forum.
No, multiple security layers, set up and managed well, can be a Very Good Thing. 🙂
-Noel
-
anonymous
GuestMrBrian
AskWoody_MVPApril 25, 2017 at 12:54 pm #110825Here is what I’ve done on my computer regarding the telemetry additions of the past few years:
1. Set the operating system’s Customer Experience Improvement Program setting = No.
2. In Windows Firewall, added block rules for IP addresses 64.4.54.253 and 64.4.54.254. See https://www.askwoody.com/forums/topic/is-the-group-b-approach-of-installing-security-only-updates-still-viable/#post-110724 for more info.
3. Have not installed any updates listed at https://www.askwoody.com/forums/topic/2952664-telemetry-in-win78-1-kb2952664-kb2977759-kb2976978-kb3150513/.
1 user thanked author for this post.
MrBrian
AskWoody_MVPApril 25, 2017 at 1:23 pm #110842@Woody: To help you narrow down the instruction choices, I recommend deciding whether your instructions will support those who want to keep kb2952664 (or its equivalents for Win 7 without service pack 1, and Win 8.1), or whether you will always recommend to not install (or uninstall if already installed) kb2952664.
Recap: kb2952664 appears to be the main gatherer of telemetry that was added in recent few years. According to my tests, kb2952664 (as of the older version 20 that I tested) mostly but not entirely respects the operating system’s Customer Experience Improvement Program setting as far as the sending of gathered telemetry data to Microsoft. kb2952664 seems to gather telemetry data regardless of the setting of the operating system’s Customer Experience Improvement Program setting, which in some cases can cause noticeable CPU and disk usage.
1 user thanked author for this post.
David F
AskWoody PlusApril 25, 2017 at 1:26 pm #110844I’ve been Group B and not found it to be particularly difficult or onerous, so far instructions have been clear and easy to follow.
What does concern me more with going with Group A, is that if I remember correctly there was talk that ultimately the rollup patches would be back porting all previous patches if they were missing. Now I know I am in the small ignored minority (by MS) but I am one of those for whom KB3121461 breaks SFC /scannow as after applying this patch it constantly reports errors, so should that come about I would either be forced to not patch at all or risk having an unstable system.
1 user thanked author for this post.
-
MrBrian
AskWoody_MVPApril 25, 2017 at 1:48 pm #110852If the code in kb2952664 (or its equivalents for Win 7 RTM and Win 8.1) gets put into a future monthly rollup, the IP address blocks of 64.4.54.253 and 64.4.54.254 that I recommended above should still block transmission of the telemetry added to Windows in the past few years.
-
David F
AskWoody Plus
-
scregio
AskWoody Lounger-
Canadian Tech
AskWoody_MVP
anonymous
GuestApril 25, 2017 at 3:07 pm #110897Guys-I’m very confused right now. Where is the direct link to install the security patch for april so I can unclick april’s monthly patch and stuff? I mean right now I’m so confused as to what to do.
Woody-Anybody? I got a win 7 with 64 bit on it. So does anyone know the clear instructions on how to install this month’s patch? Which updates are safe? Which ones to install manually?
1 user thanked author for this post.
-
PKCano
ManagerApril 25, 2017 at 3:10 pm #110902The Security Only Update and the patch for IE11 (the two to manually install) are here
https://www.askwoody.com/forums/topic/2000003-ongoing-list-of-group-b-monthly-updates-for-win7-and-8-1/Uncheck the Monthly Rollup for Windows in Windows Update, and the rest are ready to install.
-
MrBrian
AskWoody_MVPApril 25, 2017 at 3:10 pm #1109031 user thanked author for this post.
Canadian Tech
AskWoody_MVPApril 25, 2017 at 3:56 pm #110910Woody, This thread sounds like a bunch of hobbyists back in the old Radio Shack days. When you had to be really dedicated to learning to even get involved.
It would be wise for the people in this forum to realize that the vast majority of non-corporate kinds of Windows OWNERS are nothing like them. They are the ones that think about as much about their PCs as they do about their electric tooth brushes. These people don’t even know what Windows Update is, let alone whether it is working. These people fall into two categories:
1. Windows Update has been working silently and relatively un-noticed since they bought their PCs.
2. Windows Update stopped working a long time ago and they either did not notice or stopped caring.
So the 1st category are Group A and have no idea of it. The 2nd category and are c (W) and don’t care.
I am in the strange position of providing assistance and guidance to about 100 of these kinds of people who own about 150 computers. Every single one of them has Win7 (the last and best Windows there will ever be). I have taken great pains to encourage them up to last Fall to replace their hardware or have it in good shape.
All of these systems are set to never. None of these people have done any Windows Updates since last September.
Starting a month ago, I used PKCano’s guide to manually update all 150 of them remotely. I have applied Oct, Nov, Dec, Jan, Mar, .net, IE11 and Office up to but not including Mar or Apr.
Before doing this, I tried to write an email to my clients to explain to them how they should do this. It turned out to be an impossible task. So, I just bit the biscuit and did it for them.
It is likely I have done the last Windows Update I will ever do and these machines will essentially be Group C as long as they continue to operate usefully. In the past, my clients would buy around 30 computers a year. Not a one has been purchased since last October and I am pretty certain not a single one of them expects to ever buy another PC again in their lifetimes. I used to be a regular (about once a week) at the local computer store and have not been there for months.
Most of my clients now use an iPad or iPhone. Their actual usage of their computers is probably less than 25% of what it was a few years back.
I have had a few occasions in which friends or acquaintances asked me what I would recommend for a replacement. I have grudgingly told them that it would be Apple. Apple is just as much of a snoop as Microsoft, but at least they know how to spell C U S T O M E R. In fact their customer service is legendary. Microsoft has yet to meet a customer it could not easily ignore.
All of my clients, without exception, are very happy with the state of affairs. Their systems run well and reliably. Not a single infection or attack in the last several years. They are all protected by Bitdefender ANTIVIRUS+.
My own machine is an i5-6600 and would be locked out, but I could care less, because I do not ever intend to install another update anyway.
CT
-
PKCano
ManagerApril 25, 2017 at 4:17 pm #110912I was in a large computer club up until a couple of years ago, teaching basic Windows classes to non-techies 16 hours per week and supporting the group (gratis) for hardware and software. Like your “clients” mine knew little about computers, couldn’t understand them, or just plain didn’t care.
We sweated through GWX together – I sent out detailed e-mails or put my hands on their computers. Hours on the phone – click on this, now click on that. It was a full time job.
When the GWX campaign finally ended, I spent the next two months putting all the computers back on Automatic Updates. I know, DEFCON. But that would never get done. So for their “protection” I exposed them to possibly buggy patches instead of multiple malware exploits. And at a time like this, I’m glad I did. They all had the March patches within a couple of days, and have been fully updated since around April 11-12th.And except for a couple of HDD failures where I’ve had to rebuild the machines, I have had no calls. BTW: the folks I talked into Macs have thanked me a thousand time.
6 users thanked author for this post.
-
MrBrian
AskWoody_MVPApril 25, 2017 at 4:42 pm #110924This quote makes it seem that Group B may indeed be too complicated for some people:
“Starting a month ago, I used PKCano’s guide to manually update all 150 of them remotely. I have applied Oct, Nov, Dec, Jan, Mar, .net, IE11 and Office up to but not including Mar or Apr.
Before doing this, I tried to write an email to my clients to explain to them how they should do this. It turned out to be an impossible task. So, I just bit the biscuit and did it for them.”
1 user thanked author for this post.
-
Canadian Tech
AskWoody_MVPApril 25, 2017 at 4:46 pm #110927
-
-
PKCano
Manager -
Noel Carboni
AskWoody_MVPApril 25, 2017 at 6:37 pm #110973 -
Canadian Tech
AskWoody_MVPApril 25, 2017 at 6:58 pm #110979Noel. Only a few very curious people with specific interest would be interested in “education.” Most see a toothbrush that requires the use of a manual to learn how to use, the wrong product. Lawyers want to practice law. Teachers, teach. Physicians, heal people. Not spend most of their time learning how to use their computers.
Let’s remember the original Gates dream. A PC in every home. Thought of then as an appliance that would be useful, entertaining, and require no training. The design concept was one of make the machine fit the human task. Not, make the human make the machine work. Human interface is supposed to be a natural experience. Steve Jobs understood these principles better than anyone on the planet.
The very idea of Group B is a defensive strategy to protect oneself from the threat of an organization trying to use you, your resources, your identity, and your interests for their own perverted purposes. Group B practice takes a whole defence department to design and operate, when the “enemy” is much better armed, skilled and motivated. Who wants to be forced to use such a product?
The entire concept of Windows Update in Windows 7, provides for the simplest and likely the most effective defensive strategy. Simply prevent it. I am dead sure that the original designers of Windows Update did not have this in mind, and the designers of Windows 10 have made certain it is not a usable strategy for their product.
What other product do you know of that you buy and use, requires people to spend huge amounts of effort and resources to protect themselves from the product and the people who sell it?
CT
-
JNP
AskWoody LoungerApril 25, 2017 at 7:14 pm #110983Nearly all of this is correct, DEFCON being too complicated for most home users (I am a home user only), Group B being too complicated for most (I am in Group B), Canadian Tech’s points about how people de facto become Group A or Group W.
But what is also true is Microsoft made it this way for no legitimate, helpful, real discernible reason. Rather, this happened through indifference, or negligence that they failed to correct, or breaking things that they then couldn’t correct, like breaking WU with no way for the normal home user to figure out how to get WU back up and running, assuming they figured out WU had been broken by MS in the first place. Sure, people like the people here figured out how to fix WU, and any home user, like myself, should be grateful for this, which I am, and for the education Ask Woody provides, which I am, but this should be what Microsoft should be doing. And it isn’t. This seems to be one of the few companies that can put out, or make, a product defective, and has no obligation, and quite possibly no way, to recall that product or make it work again. How whack is that?
Seriously, does MS need to survey its customers about bringing the old Security Bulletins back? Of course not. It was a valuable service to many, it was little, to no, skin off Microsoft’s back to provide this “SERVICE”. And it would be little to no skin off Microsoft’s back to bring it back. Using another company’s slogan: “Just Do It!”. It’s call admitting a mistake and correcting it.
2 users thanked author for this post.
-
anonymous
GuestApril 26, 2017 at 7:56 am #111126I have rambled on this site before and as then stated I am a novice computer person and would consider myself very much in the “user” category, but I care and try to learn what I can, and take whatever I can in. All I want to say is thanks for the contributing “techies” (and WOODY) who take the time and effort to at least try and give us “users” SOMETHING/ANYTHING that would be of assistance to us. As IMO we users would be in the do do up to our necks with out the resources of this site and all of its contributors. If I can take in and learn just a minute fraction of what is written here, I go away happy that I have learnt something that arms me to be better at beating M$ shenanigans. I just have this thing in my head to do my best to not allow M$ to pluck this little black duck. Thankyou again to one and all.
-
-
-
walker
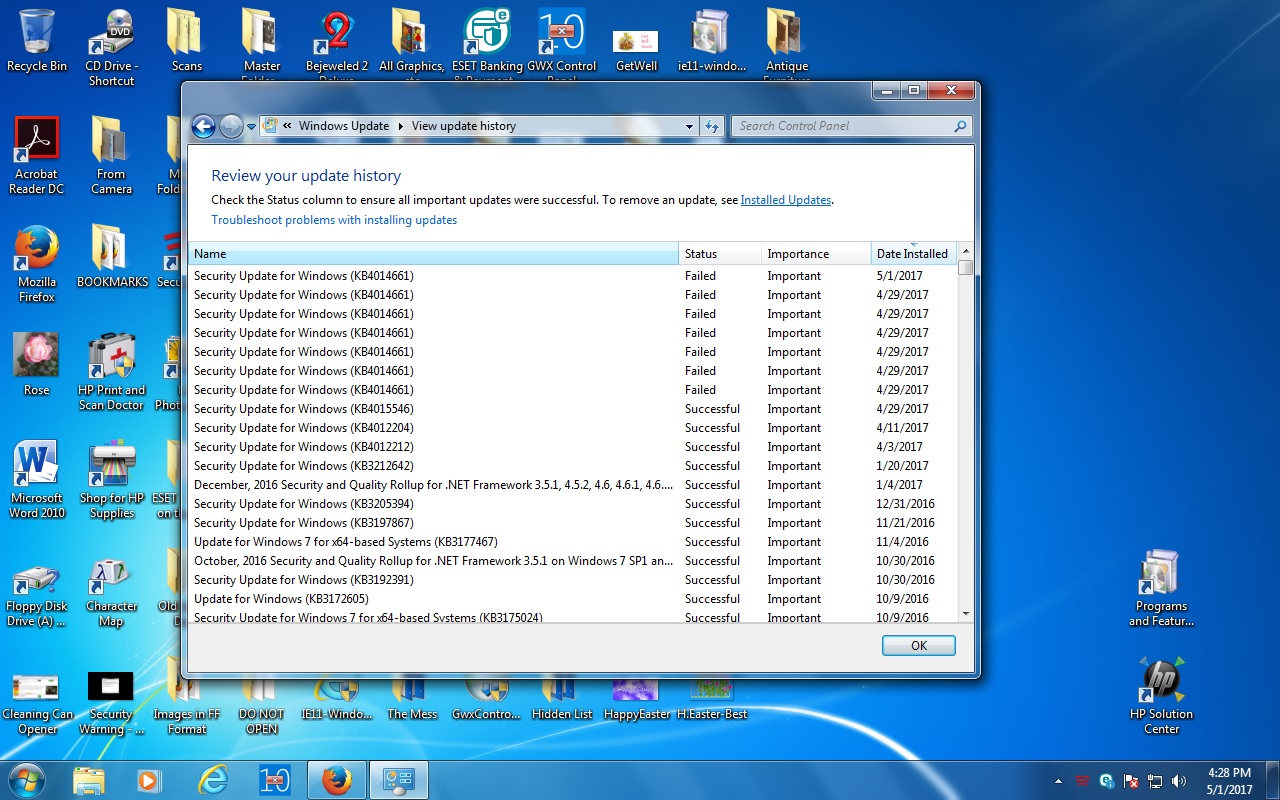
AskWoody LoungerMay 1, 2017 at 5:45 pm #112228@PKCano: “Yes”, I agree with you. I’ve tried to DL & Install the IE11 April update till I’m dizzy. I give it, and hope that the cumulative IE11 coming up will have everything in it that this one did (KB4014661). The “Check History” menu in the Update listing has shown for quite some time that the last time it was updated was 1/4/2017. I have ignored it as everything I updated went through with no problems until the IE11 refused to install it, although it stated that it was installing.
The strange thing about this is that everything since the referenced update on 1-4-17, has shown it’s successfully installed. Win 7, 64 bit, Home Premium. Group B. There seems to be something corrupted in the update menu. I’m attaching print screens of both of the scenarios I’ve mentioned. I tried one last time today to get the IE11 for April. I won’t attempt it again.
Will May’s new IE11, contain everything that I missed in April’s IE11? I’m assuming that cumulative means that these accumulate every new update with the older ones? Is this correct?
You are so knowledgeable about these issues I’m hoping that you may have seen or heard about this previously? Thank you for all of your very significant contributions to all of the users who utilize this wonderful website!!
1 user thanked author for this post.
davinci953
AskWoody PlusApril 25, 2017 at 6:03 pm #110956It’s group B for me on my Windows 7-64 bit system. I have no intention of installing Windows 10 on the computer. At least Group B provides some modicum of control over what Microsoft feeds the system. I keep the CEIP task disabled, so, hopefully, what the system feeds back to MS is minimal.
MrBrian
AskWoody_MVPApril 25, 2017 at 7:22 pm #110986A few places in this topic I have mentioned telemetry-related IP addresses (for new Windows updates from past few years) that I have personally seen in testing: 64.4.54.253 (telemetry settings) and 64.4.54.254 (telemetry data).
Spurred on by Noel, I did some more research, and found other IP addresses which might be currently being used for these purposes: see the IP addresses listed at https://www.robtex.com/ip-lookup/64.4.54.253 and https://www.robtex.com/ip-lookup/64.4.54.254. I’m not sure if we can guarantee that these are all of the IP addresses being used, based upon the answer at http://stackoverflow.com/questions/33023558/nslookup-not-returning-all-ip-addresses-for-host.
I’m withdrawing my recommendation about blocking specific IP addresses.1 user thanked author for this post.
-
MrBrian
AskWoody_MVPApril 25, 2017 at 8:51 pm #111012Based upon the posts above, here are IP addresses or DNS endpoints that seem to be associated with telemetry for new Windows updates from the past few years:
Telemetry data:
40.77.226.250
64.4.54.254
65.55.44.109
111.221.29.254vortex.data.microsoft.com
vortex-win.data.microsoft.com
v10.vortex-win.data.microsoft.com
v20.vortex-win.data.microsoft.com
web.vortex.data.microsoft.com
asimov.vortex.data.microsoft.com.akadns.net
asimov-win.vortex.data.microsoft.com.akadns.net
cy2.vortex.data.microsoft.com.akadns.net
db5.vortex.data.microsoft.com.akadns.net
bn2.vortex.data.microsoft.com.akadns.net
hk2.vortex.data.microsoft.com.akadns.net
geo.vortex.data.microsoft.com.akadns.net
v10-win.vortex.data.microsoft.com.akadns.net
v20-asimov-win.vortex.data.microsoft.com.akadns.net
web.vortex.data.microsoft.com.akadns.netTelemetry settings:
40.77.226.249
64.4.54.253
65.55.44.108
111.221.29.253
191.232.139.253settings.data.microsoft.com
settings-win.data.microsoft.com
asimov.settings.data.microsoft.com.akadns.net
asimov-win.settings.data.microsoft.com.akadns.net
cy2.settings.data.microsoft.com.akadns.net
db5.settings.data.microsoft.com.akadns.net
bn2.settings.data.microsoft.com.akadns.net
hk2.settings.data.microsoft.com.akadns.net
geo.settings.data.microsoft.com.akadns.netFor Microsoft’s lists of DNS endpoints, see https://www.askwoody.com/forums/topic/is-the-group-b-approach-of-installing-security-only-updates-still-viable/#post-110736.
-
MrBrian
AskWoody_MVPApril 26, 2017 at 6:52 pm #111314Here are the IP addresses that various DNS servers around the world resolved for vortex.data.microsoft.com: https://www.whatsmydns.net/#A/vortex.data.microsoft.com.
Here are the IP addresses that various DNS servers around the world resolved for settings.data.microsoft.com: https://www.whatsmydns.net/#A/settings.data.microsoft.com.
In both cases, all of the IP addresses are listed in post https://www.askwoody.com/forums/topic/is-the-group-b-approach-of-installing-security-only-updates-still-viable/#post-111012.
1 user thanked author for this post.
-
MrBrian
AskWoody_MVPApril 25, 2017 at 7:30 pm #110990My latest proposal for instructions is:
1. Set the operating system’s Customer Experience Improvement Program setting = No.
2. Do not install these updates: KB2952664 (Windows 7 with service pack 1), KB2977759 (Windows 7 without service pack 1), KB2976978 (Windows 8 and 8.1).
I’ll research whether any other updates listed at https://www.askwoody.com/forums/topic/2952664-telemetry-in-win78-1-kb2952664-kb2977759-kb2976978-kb3150513/ should also be avoided.
1 user thanked author for this post.
-
MrBrian
AskWoody_MVPApril 25, 2017 at 9:15 pm #1110173. If the code from KB2952664 (or its equivalent for other operating systems) is someday integrated into a monthly rollup, before you install that monthly rollup, block the IP addresses or DNS endpoints listed in https://www.askwoody.com/forums/topic/is-the-group-b-approach-of-installing-security-only-updates-still-viable/#post-111012. To block an IP address in Windows Firewall, see http://www.easysecurityonline.com/how-to-protect-windows-7-and-8-from-getting-windows-10-privacy-intrusions-too/.
1 user thanked author for this post.
-
MrBrian
AskWoody_MVPApril 26, 2017 at 1:18 am #111054Another reason to consider doing step 3 is that some software changes the Windows Update setting to update automatically, in which case KB2952664 (or its equivalent for other operating systems) might be installed automatically.
I will now block the 10 IP addresses listed in https://www.askwoody.com/forums/topic/is-the-group-b-approach-of-installing-security-only-updates-still-viable/#post-111012 and see how things go.
1 user thanked author for this post.
-
MrBrian
AskWoody_MVPMrBrian
AskWoody_MVPApril 26, 2017 at 2:26 am #1110684. For the same reasons as step 3, create an outbound firewall rule blocking service Diagnostics Tracking Service. See https://www.askwoody.com/forums/topic/is-the-group-b-approach-of-installing-security-only-updates-still-viable/#post-110789 for how to create an outbound firewall rule to block a specific service.
Step 4 can be used instead of step 3, or in conjunction with step 3.
I haven’t tested this step yet.
1 user thanked author for this post.
samak
AskWoody PlusApril 25, 2017 at 7:51 pm #110996Is the “Group B” approach of installing Security-only updates still viable?
From where I’m sitting, the answer is a resounding “Yes”. Although I’m a non-techie who doesn’t know his DNS from his elbow, I don’t find the “Group B” approach to installing Security-only patches unwieldy nor do I find @pkcano’s list in AKB 2000003 oppressive. For April, the list is showing 2 patches – even I can cope with that.
I also have no difficulty following the wonderfully detailed instructions each month when we are given the go-ahead to install the patches.I fully understand the comments by the tech support posters that their clients might not be able to cope with it or don’t care to, but the non-techies on this site are interested in learning and coping with the MS plague and find Group B invaluable.
Windows 10 Home 22H2, Acer Aspire TC-1660 desktop + LibreOffice, non-techie
-
PKCano
ManagerApril 25, 2017 at 8:03 pm #111000Somewhere back up this thread I describe what I’ve been doing with my Win7 and Win8.1 installations. It’s not exactly Group B, But it’s not Group A either. I install the security-only patches, uncheck the Monthly Rollup, then let the others rip. I have never installed the telemetry patches on any of them.
I have 3 VMs with upgrades to Win10, at the moment v1607, and a Win10 Insider Preview that I have been dealing with since Oct 2014, but this has been such circus that I doubt I’ll ever move to a Win10 production machine.2 users thanked author for this post.
-
anonymous
GuestApril 25, 2017 at 10:21 pm #111019…but this has been such circus that I doubt I’ll ever move to a Win10 production machine.
I’ve wasted far too much time wrangling with Win10 so just avoid it for production use. When the telemetry malware and TrustedInstaller.exe with its cohort monster goon TiWorker.exe starts they’ll kill your productivity.
1 user thanked author for this post.
-
anonymous
GuestApril 26, 2017 at 12:13 am #111041Is the “Group B” approach of installing Security-only updates still viable?
How did it come to this ?
We need to look at some computer history.
M$ were able to out-market Apple MacOS during the late 1990s and 2000s by offering their customers cheaper OEM Windows computers and the very attractive free updating support for about 10 years.
Initially, annual revenue for M$ from Windows license sales during the 2000s boomed or kept on growing because computers were a new industry/market. But by the 2010s, market saturation crept in, ie nearly every home and office were already using Windows computers = annual revenue for M$ from Windows license sales stopped growing.
. . Hence, to grow their annual revenue from the sales of Windows licenses, M$ began adopting aggressive policies to push their Win 7/8.1 customers into buying new licenses for the 2015 Win 10 long before the EOL of Win 7/8.1 in 2020/2023, esp their money$-loaded corporate customers who have bought Win 7/8.1 Ent Volume Licenses.One of these policies that degrade Win 7/8.1 is the mandatory monthly Patch Rollups in Oct 2016. To lessen the negative impact on their corporate customers, M$ had to give them the option of Security-Only Quality Updates/Patches or Group B.
In effect, the hidden message of M$ to Win 7/8.1 users is like, “if you don’t upgrade to Win 10 and let us make more money$, we will make Win 7/8.1 to be as bad as or worse than Win 10, so just upgrade to Win 10 pronto.”
.
.
P S – Most corporate customers who had leased/rented/subscribed Win 7/8.1 Ent VL have upgraded to Win 10 since they are required by M$ to buy Software Assurance which allows “free” Version upgrades within 3 years.MrBrian
AskWoody_MVPApril 26, 2017 at 5:22 am #111092I have a different proposal that I now favor because most steps are one-time only.
One-time only steps for telemetry avoidance:
1. Set the operating system’s Customer Experience Improvement Program setting = No.
2. Install this update: KB2952664 (for Windows 7 with service pack 1), KB2977759 (for Windows 7 without service pack 1), or KB2976978 (for Windows 8 and 8.1).
3. When requested to reboot, disable Internet connection (preferably physically) before rebooting.
4. Reboot.
5. In Task Scheduler, end (if running) and disable these tasks in Task Scheduler (Local) -> Task Scheduler Library -> Microsoft -> Windows -> Application Experience:
AitAgent
Microsoft Compatibility Appraiser
ProgramDataUpdater
6. Reconnect to Internet if you want to.
One-time only steps for everyone:
1. Use these Windows Update settings:
Important Updates = Never check for updates
Give me recommended updates the same way I receive important updates = Checked
Give me updates for Microsoft products and check for new optional Microsoft software when I update Windows = Checked
If the last checkbox does not appear, see https://www.askwoody.com/2016/how-to-restore-give-me-updates-for-microsoft-products/.
Monthly steps:
1. Check for updates manually in Windows Update. Leave everything at defaults, except for any Optional updates that you wish to install. Proceed to install updates.
2. Reboot if requested.
3. Repeat steps 1 and 2 until there are no updates listed that didn’t appear the last time you did step 1.
2 users thanked author for this post.
-
MrBrian
AskWoody_MVP -
PKCano
ManagerApril 26, 2017 at 6:33 am #1111092. Install this update: KB2952664 (for Windows 7 with service pack 1), KB2977759 (for Windows 7 without service pack 1), or KB2976978 (for Windows 8 and 8.1). 3. When requested to reboot, disable Internet connection before rebooting.
So now you are recommending installing KB2952664 (and its equivalent in other versions)? I assume this will also include installing KB3150513 (definitions updater).
1. Check for updates manually in Windows Update. Leave everything at defaults, except for any Optional updates that you wish to install. Proceed to install updates.
And this would seem a recommendation for the Cumulative Security Monthly Quality ROLLUP.
Questions:
What changed you mind about installing the telemetry patch?
Why disconnect from the Internet when rebooting – what does that do?
There is no mention of the Diagnostic Tracking Service. Should it be left on?
What about the other telemetry related patches as listed in AKB2000003?Edit to add 4th question
6 users thanked author for this post.
-
ch100
AskWoody_MVPApril 26, 2017 at 7:34 am #111119The recommendation to install KB2952664 (and KB3150513) and their equivalent for other OS is accompanied by the second recommendation which is
5. In Task Scheduler, end (if running) and disable these tasks in Task Scheduler (Local) -> Task Scheduler Library -> Microsoft -> Windows -> Application Experience:
AitAgent
Microsoft Compatibility Appraiser
ProgramDataUpdater
This is to block the effect of the components introduced by KB2952664.
I suppose this is proposed to simplify the Windows Update mechanism and move fully into Group A as it is the best practice for functionality and is intended for non-managed environments, but it introduces another layer of complexity instead, which is to disable those relevant Scheduled Tasks.
I don’t know if there are any side-effects related to disabling the relevant scheduled tasks, but this was proposed many times before, so it may be safe enough.
-
PKCano
ManagerApril 26, 2017 at 7:42 am #111124I have had all tasks disabled under Application Experience since GWX days (when I first noticed that KB2952664 changed things there and raised the alarm to Woody and Mayfield), as well as the tasks under Autochk and CEIP. Haven’t had any ill effects at all (that I know of).
I just didn’t understand the logic of “install it to disable it.”2 users thanked author for this post.
-
Noel Carboni
AskWoody_MVPApril 26, 2017 at 8:39 am #111134^ What PKCano said.
I agree with the concept of installing the cumulative updates, but why go out of one’s way to install telemetry increasing code if just to then block it? To remove all worry over the system being “fragmented”?
The update is STILL optional as far as I can see. As long as Microsoft has it optional, it’s pretty clearly unnecessary to the operation of the basic system, no?
Edited for Identity
-Noel
-
PKCano
Manager -
Noel Carboni
AskWoody_MVPApril 26, 2017 at 9:29 am #111144It’s optional under some conditions, which means Microsoft themselves don’t think it needs to be integrated into the system for Windows to run. Thus it’s reasonable to avoid installing it.
That being said, I do see how it could just be shoveled in with all the others in the general case, then telemetry blocking be invoked. Thus MrBrian’s procedure is as general as possible, for the least technical users. It also future-proofs things in case the telemetry ultimately IS rolled by Microsoft into the big cumulative updates. (I wonder if legally they are barred from doing so…)
I do suggest that a suggested procedure also strive to prevent the telemetry gathering as well. No sense in the computer continually taking resources away from the user by evaluating itself if the resultant data is never going to go anywhere.
Lastly, food for thought…
No matter how you configure Windows at run-time, who knows what could be sent where when the system as delivered by Microsoft has full control during, say, an in-place upgrade. Maybe they just choose to upload all the stored telemetry then. It’s one reason I like my approach of an external DNS server blocking all those sites, and it does also justify router-based blocking.
-Noel
-
MrBrian
AskWoody_MVP -
Noel Carboni
AskWoody_MVP
-
-
-
-
MrBrian
AskWoody_MVPApril 26, 2017 at 9:09 am #111138First of all, this is only a preliminary proposal based upon my prior knowledge of these updates. If given the green light by Woody, I will test this procedure for both Windows 7 and Windows 8.1. If I judge it successful, then advanced users with virtual machines could try it next. If successful, the next stage could then be advanced users on their real computers. Then maybe a few “normal Joe” users could try it and give feedback.
[Question] “So now you are recommending installing KB2952664 (and its equivalent in other versions)? I assume this will also include installing KB3150513 (definitions updater).”
Yes and yes.
[Question] “And this would seem a recommendation for the Cumulative Security Monthly Quality ROLLUP.”
Yes. We’re now avoiding being in Group B.
[Question] “What changed you mind about installing the telemetry patch?”
This makes the monthly steps very simple :). There is no avoiding of updates every month. There is no need to uninstall updates either. Some of you may recall that there can be multiple versions of KB2952664 installed, and that uninstalling all of them can be a pain (although there is an easy way). By installing KB2952664 in the controlled manner that I recommend, and then neutering it (step 5) while the internet is disconnected, we don’t have to worry that in the future KB2952664 could be installed in a less controlled manner in any of these ways:
1. By the user not correctly following monthly directions in my previous proposal to not install KB2952664.
2. Automatically if Windows Update is changed to update automatically. Some programs change Windows Update to update automatically :(.
3. The code in KB2952664 is integrated into a future monthly rollup.
Keep in mind that setting the operating system’s Customer Experience Improvement Program setting = No, all by itself shuts off the vast majority of telemetry that KB2952664 would transmit even if it weren’t neutered (step 5), according to my tests.
[Question] “Why disconnect from the Internet when rebooting – what does that do?”
After rebooting, the tasks that KB2952664 installs or modifies could start running before the user has the chance to complete step 5. And if those tasks get far enough along, some telemetry could be sent to Microsoft, although as I mentioned before, setting the operating system’s Customer Experience Improvement Program setting = No stops the vast majority of KB2952664 telemetry according to my tests. Disconnecting from the internet before rebooting, preferably physically disconnecting, should hopefully prevent any such transmission.
[Question] “There is no mention of the Diagnostic Tracking Service. Should it be left on?”
I recommend leaving it enabled. Third-party programs can use Diagnostic Tracking Service for telemetry, so disabling it would also affect those third-party programs. If the user doesn’t care about that, then the user could choose to either disable Diagnostic Tracking Service, or at least stop it in the firewall from communicating. Whether we mention this in the instructions can be discussed further.
[Question] What about the other telemetry related patches as listed in AKB2000003?
If given the green light, I will test those during testing to see if any of them need to be avoided. For the sake of simplicity, I hope none of them need to be avoided.
-
PKCano
Manager -
MrBrian
AskWoody_MVP -
MrBrian
AskWoody_MVPApril 26, 2017 at 9:28 am #111143If that remains a big enough concern, step 3 and/or step 4 from my previous proposal (https://www.askwoody.com/forums/topic/is-the-group-b-approach-of-installing-security-only-updates-still-viable/#post-110990) or disabling Diagnostic Tracking Service could be recommended to the user.
2 users thanked author for this post.
-
MrBrian
AskWoody_MVPApril 26, 2017 at 1:57 pm #111239More kb2952664 tests:
v3 to v22: some tasks reenabled
v11 to v22: some tasks reenabled
v16 to v22: some tasks reenabled
v17 to v22: some tasks reenabled
v18 to v22: some tasks reenabled
v19 to v22: no tasks reenabled
v20 to v22: no tasks reenabledMaybe my previous method (avoiding installation of kb2952664) is better after all.
1 user thanked author for this post.
-
PKCano
ManagerApril 26, 2017 at 2:13 pm #111246Just an FYI
It is easier to tell the average user to hide the patch than to go into Task Scheduler and disable the tasks then go into Services and disable DiagTrack.
To begin with, showing Administrative Tools in the Start Menu or the link to it on the right side of the menu are turned off by default. The average user probably has never seen Administrative Tool. The only place it shows is in the Control Panel, and the average User doesn’t wander there either.2 users thanked author for this post.
-
-
woody
Manager-
MrBrian
AskWoody_MVPApril 26, 2017 at 9:20 am #1111411. Some people might not like using a script (“What’s it going to do to my system?”), while others may prefer to use a script. I could write a script for my procedure also if desired.
2. I believe that Woody mentioned previously that InfoWorld does not allow the use of scripts or programs unless they are from well-known entities?
3. abbodi86 mentioned that there may be occasions when his script may need to be run again. My procedure avoids this.
Hopefully abbodi86 and others can also comment on any weaknesses in my proposal.
1 user thanked author for this post.
-
grayslady
AskWoody LoungerApril 26, 2017 at 10:23 am #111168Keep the Group B list. It is not only about telemetry, it is about whether any of MS’s non-security updates improve performance. Readers here know that, quite often, the non-security updates cause nothing but problems, or, at least are marketing-oriented rather than value-added. As Canadian Tech has opined, Windows 7 is the last of the best, and many of us want to keep it that way by adding only the essentials. abbodi’s list is a real reader service.
Sessh
AskWoody LoungerApril 26, 2017 at 9:40 am #111149Ok, so I don’t even update really anymore and I’m confused for everyone else. How long did you guys promote Group B as a viable strategy to combat MS’s antics? Avoid certain telemetry patches that are now being recommended for install? That’s confusing. There are numerous users on here who are doing the Group B thing following the instructions laid out on here and are happy with it, so are we now turning our backs on them and forcing them into Group A? That is my concern just from reading through here.
It seems more confusing to tell people to install updates just to go through more steps messing with a firewall and poking around in task scheduler to neuter them. The question then becomes why install it at all at that point? For those who have trouble avoiding updates, is it really going to be easier for them to go poking around in Control Panel and setting all kinds of things in their firewall?
There’s a major flip-flop going on here now; that is confusing as well. Just my 2cents. 🙂
-
MrBrian
AskWoody_MVP -
Sessh
AskWoody LoungerApril 26, 2017 at 10:03 am #111157I think there would be plenty of demand and I would at least make the suggestion that said interest should be gauged before abandoning Group B. It seems this strategy has been around a long time now on these forums, am I correct? It is a valid approach to updating Windows and is, IMO, a LOT easier than doing anything in control panel or fiddling around in the menus of a firewall inserting dozens of IP and web address entries, but first having to go to other websites to read about how to do it and I think that last step is where you’re going to lose a lot of people. IP addresses and firewall settings may as well be Chinese to many regular users. I know a few people like that myself.
Anyway, I think the users here should be asked before doing away with it all of a sudden. I don’t think the reasons as adequate IMO and if I were in Group B, I’d feel like I was left out to dry a little bit. Maybe that’s just me, though.
-
MrBrian
AskWoody_MVPApril 26, 2017 at 10:15 am #111162My latest procedure currently doesn’t involve adding firewall rules. That was from the older procdure. Step 5 in the current procedure should neuter KB2952664 from gathering telemetry, and if the KB2952664 telemetry isn’t gathered, it can’t be transmitted :).
1 user thanked author for this post.
-
-
PKCano
ManagerApril 26, 2017 at 9:57 am #111154What’s going on here now is a Think Tank. We haven’t changed anything YET. We are testing the waters at this point. The Groups weren’t there to begin with, they evolved because MS changed their way of doing business with Cumulative Monthly Rollups (not so long ago).
In the light of the latest Security fiasco with the Shadow Brokers dump, we are reassessing the possibilities. Be patient. We’re working on what’s best for you – that’s why the concept of Groups A, B, and W arose in the first place. You just haven’t seen the process going on out in the open like it is now.
The first order of business here is looking at the current situation and recommending what, in our opinion, is best for the Users.
Isn’t that why you come to the AskWoody website for advice?Edited to add reason for “MS changed way of doing business”
-
Sessh
AskWoody LoungerApril 26, 2017 at 10:08 am #111158Of course, it’s why anyone comes here I would imagine. Fair enough, just giving my opinion is all. Reading through here, I’m pretty sure I saw a rather definitive looking excerpt from one of Brian’s posts that said the object is to get away from Group B. I could have read it wrong, though. Giving instructions to everyone that are in opposition to those of Group B seems like more than a discussion, does it not? Maybe it just seems that way, though.
Edit to add: It’s not about not being patient, though. Brian asked for feedback, so I gave him some. That’s all.
2 users thanked author for this post.
-
MrBrian
AskWoody_MVP -
Sessh
AskWoody Lounger -
anonymous
GuestApril 26, 2017 at 11:56 am #111189@ Sessh
No, you did not read MrBrian wrong because earlier he had said, …
[Question by PKCano] “And this would seem a recommendation for the Cumulative Security Monthly Quality ROLLUP.”
Yes. We’re now avoiding being in Group B.
IOW, MrBrian is recommending those in Group B be moved to Group A or S(for Sheep).
.
.In my case, I am in Group C or W and I recommend those in Group B should stay in Group B, except for those with Kabylake/Ryzen and unlisted Skylake processors, or move to Group C or W.
2 users thanked author for this post.
-
Sessh
AskWoody LoungerApril 26, 2017 at 12:13 pm #111199No, you did not read MrBrian wrong because earlier he had said, …
Question by PKCano] “And this would seem a recommendation for the Cumulative Security Monthly Quality ROLLUP.”
Yes. We’re now avoiding being in Group B.
IOW, MrBrian is recommending those in Group B be moved to Group A or S(for Sheep).
Ah, that’s what I thought I read. My issue was that this thread was supposed to be a discussion on whether or not Group B should be continued or not and instead, it seems to jump right to the conclusion that Group B isn’t being continued and gives recommendations based on that instead of just polling people as to what they think before making any recommendations. The fact that there’s several different recommendations throughout only adds to the confusion.
Anyway, not trying to be overly critical, I’m just not sure the title of this thread matches what’s going on in it. It asks a question and it seems there is quite a lot of support for Group B still. Just because GWX is a thing of the past (for now) doesn’t mean everyone has changed their minds about Microsoft. I just hope that we can come to a consensus on the future of ABC before we start recommending people to do this or that. Based on the posts here so far, it seems ABC shouldn’t be going anywhere at this time. Don’t fix what isn’t broken, yes?
-
PKCano
ManagerApril 26, 2017 at 10:21 am #111166Groups didn’t exist until Cumulative Rollups – Oct 2016 or so. We forget what was before.
@MrBrian’s purposed recommendations have changed several times in this thread alone.
Woody has not announced anything different as yet.
And then the real question:
If things change, would you want to cling to older methods if they left you vulnerable to threats from the Internet (or MS for that matter)?Edited to change time frame of Group creation
1 user thanked author for this post.
-
anonymous
GuestApril 26, 2017 at 12:17 pm #111192@ PKCano
Actually, Groups A, B and W or C only began when M$ implemented mandatory monthly Patch Rollups for Win 7/8.1 in Oct 2016. Please refer to …
https://www.askwoody.com/2016/windows-7-security-only-group-b-patching-remains-viable/Group W’s where they put you if you may not be moral enough to join the army after committing your special crime, and there was all kinds of mean nasty ugly looking people on the bench there. Mother rapers. Father stabbers. Father rapers!
https://en.wikiquote.org/wiki/Arlo_Guthrie
To be called Group W is quite offensive to some of those in Group C.
1 user thanked author for this post.
-
PKCano
ManagerApril 26, 2017 at 12:21 pm #111205We forget what was before.
You’re right.
Oh well, Groups existed for an even shorter time that I suggested. When you get old, one day is like another!
Strange how we get into habits in such a short time and remember it was forever.1 user thanked author for this post.
-
Noel Carboni
AskWoody_MVPApril 26, 2017 at 9:10 am #111139Overall, some thoughts…
1. I have several virtual machines on which I initially test Microsoft’s patches for myself, and of course I read here and in other places to learn whether others are having problems with Windows Updates.
2. I have a Win 8.1 daily hard use workstation. I install only cumulative updates on it, and I’ve hidden a few optional ones (e.g., KB2976978). You could say I’m following a substantially Group A policy with it.
3. I have a limited use Win 7 system that’s primarily a file server and not used interactively or for surfing online. I have installed only the April security updates – for no direct reason other than the fact that I weighed the risks and decided that the SMB patch was something I should have. The last update it got before that was in May 2016. This system would be considered Group B now, up from a long stint of being in Group W.
So far, I’ve had no problems with stability, performance, compatibility, or keeping any of these systems from being overly chatty online.
Based on my experience:
Group A, B, and W approaches are perfectly viable.
Exercising manual update control and following a conservative / delayed Group A, B, or W approach depending on needs, I have not had a Microsoft patch botch anything up for me in quite a few years.
-Noel
Ascaris
AskWoody MVPApril 26, 2017 at 9:53 am #111152I am in group “A” (for the most part; I continue to vet any non-rollup updates individually) using Windows 8.1 on both of my main PCs, though with modifications.
I’ve verified that CEIP is still off, deleted the diagtrack service, removed all of the tasks related to telemetry from the task manager, and done the rest of the stuff listed here as suggested by abbodi86 and relayed by Woody.
None of the telemetry or “latest version of Windows” patches during the GWX assault were ever installed on this system, so all of the added telemetry would have come from the rollups.
I’ve also wiped the \windows\system32\compatTel directory (contents zipped in-place and left there in case they ever need to be restored), and I have several generations of system images (including one before I went to group “A,” which I will retain long-term).
I only had to delete diagtrack once, right after I installed the first rollup after MS started putting it in there. Rollups after that have not restored it or any of the other stuff I removed. I will, of course, continue to watch.
The reasons for my move to “A” are simple: It’s already been noted to happen on at least one occasion that MS would release a security-only patch that manages to introduce a new non-security bug, which MS will then only fix in the rollup. Going forward, it seems like MS would continue to “accidentally” introduce new bugs into the security-only updates. With that in mind, I wanted to see how effectively the added telemetry can be thwarted.
So far, I have not noticed any suspicious connections while I’ve had Wireshark running. I am new at Wireshark, though, so it is possible something’s escaping my notice. If anyone has any suggestions what to look for in Wireshark as far as telemetry, I will certainly be interested.
Dell XPS 13/9310, i5-1135G7/16GB, KDE Neon 6.2
XPG Xenia 15, i7-9750H/32GB & GTX1660ti, Kubuntu 24.04
Acer Swift Go 14, i5-1335U/16GB, Kubuntu 24.04 (and Win 11)2 users thanked author for this post.
-
anonymous
GuestApril 26, 2017 at 12:57 pm #111212? says:
Take a look at this tutorial from how to geek:https://www.howtogeek.com/107945/how-to-identify-network-abuse-with-wireshark/
1 user thanked author for this post.
-
MrBrian
AskWoody_MVP
TJ
AskWoody PlusApril 26, 2017 at 10:40 am #111171I’m a B-grouper and I find Woody’s and other people’s contributions very (and still) valuable.
I have a stand-alone Windows 7 Pro x64 pc which I use for both work and play, so being secure -without snooping practices from anyone- is essential to me.Without all your input (on InfoWorld as well of course) , I would find it very hard to make the right choices between necessary and unnecessary updates. And it would take too much time as well.
So ‘Hooray’ for Group B!
BTW Woody, please know this blog is valued very highly and is often used as a reference here at home by users on sites like https://tweakers.net/ and https://www.security.nl/ every time they are facing the update conundrum.
P.S. Can anyone please confirm that WU does NOT offer any Security ONLY updates? Thanks.
MintDE is my daily driver now. Old friend Win10 keeps spinning in the background2 users thanked author for this post.
-
PKCano
ManagerApril 26, 2017 at 11:09 am #111176WU DOES NOT offer the Security-only updates. If you install them, you also need the Cumulative Update for IE11 which is no longer a part of them. The Security-only patches ARE NOT cumulative, so you will need one for every month.
You can down load them from the MS Update Catalog or find the links on AKB2000003 here on AskWoody. They have to be manually installed.2 users thanked author for this post.
TJ
AskWoody PlusApril 26, 2017 at 11:16 am #111180This quote makes it seem that Group B may indeed be too complicated for some people…
Thanks for all the input about whether the Group B is valuable to home users. It depends on how you determine that group. Like I explained in my single comment, I’m a home user, but I use my pc for both work and play. (Work from home)
I’m kind of self-taught, but surely no real ‘techie’, nor do I have the budget to hire one. But my knowledge is sufficient to understand the information and advices/instructions given by Woody and you guys, and subsequently ‘do the right thing’. (Couldn’t do without it)I think that if a home user ‘only’ runs Windows 7 Home, he/she will probably only do basic stuff with his/her pc, and therefore not have enough knowledge to understand the Group B stuff. Furthermore, he/she will probably never end up here at Woody’s.
If he/she’s working on Pro 7 AND has the wit to go search for good information on the web AND recognizes the value of the information given on this blog, it clearly shows he or she wants and needs the Group B-like set up.MintDE is my daily driver now. Old friend Win10 keeps spinning in the backgroundThe Surfing Pensioner
AskWoody PlusApril 26, 2017 at 11:34 am #111185I’m not particularly technical, but I cannot see the problem with Group B continuing. Thanks to the very specific guidance provided by Woody and his team, I have had no difficulty at all in updating Group-B-wise – actually, I find it a doddle. Much simpler and quicker than in the old days, when I used to stare at a list of kb numbers, not have a clue which of them were applicable to my PC and so end up installing all sorts of rubbish I didn’t want as well as overlooking the odd update that I needed. I have read the articles on the bugs in this month’s updates, but as I understand the issues, they have affected not only Group B but Group A as well. So why can’t we carry on as we are? If Group B becomes unworkable in the future, we can make our choices individually then.
TJ
AskWoody PlusApril 26, 2017 at 12:12 pm #111198WU DOES NOT offer the Security-only updates. If you install them, you also need the Cumulative Update for IE11 which is no longer a part of them. The Security-only patches ARE NOT cumulative, so you will need one for every month. You can down load them from the MS Update Catalog or find the links on AKB2000003 here on AskWoody. They have to be manually installed.
Thanks. I know, thanks to the Group B info 🙂
MintDE is my daily driver now. Old friend Win10 keeps spinning in the background1 user thanked author for this post.
anonymous
GuestApril 26, 2017 at 1:00 pm #111169The only thing unwieldy is the nouns. Group A, Group B, Group W, Group ABC, Group NBC, Group 69, Group Woody, DEFCON 1, 2, 3, 4, 5, Group DEFCON. What is the need for all of this? How did Group A survive without instructions before?
“Here’s a list, use these, don’t care? Don’t visit!”. If a patch is a new put a little “new patch” warning tag and the more cautious of us will wait a couple weeks. I don’t understand the over complicating of everything for no reason.
1 user thanked author for this post.
-
woody
ManagerApril 26, 2017 at 1:13 pm #111224How would you improve it?
Remember that we had 644 patches earlier this month with 210 of them marked “critical.”
We also have folks who use all versions of Windows, all versions of Office.
And some of our readers are very concerned about snooping – while others don’t care.
I’m painfully aware of how complex it’s become. What would you recommend?
1 user thanked author for this post.
-
woody
ManagerApril 26, 2017 at 1:20 pm #111226P.S. I created the MS-DEFCON system about a decade ago to simplify things.
“Group A” and “B” didn’t exist prior to the patchocalypse last October. I invented that terminology to easily distinguish between those who didn’t want any snooping patches, and those who didn’t mind (and, later, those who didn’t want to patch at all). I never really liked the nomenclature, but it’s a decent shorthand.
Group W — and the quote — are directly from Arlo Guthrie. It’s not exactly derogatory. Or maybe it is. I’m not sure.
-
MrBrian
AskWoody_MVPApril 26, 2017 at 1:49 pm #111236 -
woody
ManagerApril 26, 2017 at 2:04 pm #111241Interesting idea, but…
Windows 7: Either April Monthly Rollup or Security-Only update unless you have Kaby Lake or Ryzen or … ???
Internet Explorer 11: Either tweedledum or tweedledee
.NET Framework 3.5.1: Some other tweedledum or tweedledee
.NET Framework 4.6.2: Etc
Office Click-to-Run: Another (note that Office CtR was pulled and re-released this month)
Office 2016: Blah
Office 2013: Blech
Office 2010: Argh
Silverlight: Dah dah dah
And that’s just for Windows 7!
Then I have to explain how to install each of those…
It’s a monstrous problem.
2 users thanked author for this post.
-
MrBrian
AskWoody_MVP -
samak
AskWoody Plus -
woody
ManagerApril 27, 2017 at 6:25 am #111398That may be a good modification. I’ll have to think about it.
Generally, I use 1, 4 and 5 as signals for folks who are used to the settings. Running up to 1 should raise a red flag (as it did earlier this month). Going down to 5 (as I did last year) should make people rest easy about installing patches.
-
Sessh
AskWoody LoungerApril 27, 2017 at 10:04 am #111435Woody, maybe three DEFCON levels would be sufficient?
-DEFCON 1: Do not patch.
-DEFCON 2: Patch, but follow specified instructions from our resident experts only!
-DEFCON 3: All clear! No problems with current patches.
Though I would be careful about using D3, it certainly seems like a clearer system. Keep up with the Group B posts and Group A folks don’t need any steps other than 1 and 3 since D2 would be the same as D3 for them essentially. Alternatively, you could just use a color code system instead of a number system. For example, D-Red, D-Yellow and D-Green. Just spit-balling here and seeing if anything sticks.
1 user thanked author for this post.
-
ht
AskWoody LoungerMay 1, 2017 at 3:01 pm #112201I didn’t understand the MS-DEFCON system when I first, and thankfully, found @Woody, but it took just a beat to go to the page that explains what it means and how it applies. I printed it out and have been comfortable since. I like the way the system is more than a green light/red light for action. I find the prod to “pay attention” with MS-DEFCON 1 useful, and the rare MS-DEFCON 5 does reduce the stress of that month’s patching (group B). I don’t recall seeing a MS-DEFCON 4. Although I might be as happy with another system, I’d vote to focus first on understanding and managing the changes MS is throwing at us and defer tweaking the MS-DEFCON system to a calmer time if/when it arrives.
1 user thanked author for this post.
-
ch100
AskWoody_MVP -
anonymous
Guest -
ch100
AskWoody_MVPApril 28, 2017 at 4:18 am #111597I don’t know if you have a good understanding of the issues involved or your post is based only on the hype associated with a lot of posts on this forum, which attract large numbers of users, but many of those do not contribute with useful posts, rather maintaining the scare campaign and creating confusion among those less computer literate.
1 user thanked author for this post.
-
-
-
-
anonymous
GuestApril 27, 2017 at 3:47 am #111378I’m mostly ranting about how sorting through things had been up to now and what I saw as a lot of information overload for people who just wanted their security patches. pkcano’s list is actually more or less what I’ve been wanting and as I’ve just found it, I’m mostly ranting at the idea that it’s too unweildy when it’s the thing that’s made everything finally manageable.
The problem with the Defcon system is that it’s completely unclear as to “up to what”. If you’re coming to this site constantly and following it, it makes more sense but if for whatever reason you’re a couple months behind on patching or trying to catch up with a fresh install and you read ‘don’t install any patches’, it’s not all that useful. That’s why I suggested marking any update that would be considered too new too proceed without caution with some kind of warning mark.
-
Sessh
AskWoody LoungerApril 27, 2017 at 10:07 am #111436Perhaps making a link at the top of the page (without taking up a lot of space) directing people to a thread with instructions for installing the last known safe batch of patches or individual patches would be sufficient. That way when people come here and see D1, there will be a link somewhere at the top directing people to said thread so they can catch themselves up.
-
AlexN
AskWoody LoungerApril 26, 2017 at 1:05 pm #111223Watching all this unfold and, as much as people say we’re headed toward full-blown “1984” world, I have a feeling that in the next few years we’re going to see some major OS’s switch back toward the business model of the 1990s and early 2000s. As more code is put in the computer, so too there are more potential holes put into things.
Fortran, C++, R, Python, Java, Matlab, HTML, CSS, etc.... coding is fun!
A weatherman that can code1 user thanked author for this post.
James Bond 007
AskWoody LoungerApril 26, 2017 at 11:36 pm #111350At present it is Group B for me.
I find it workable right now (though with the inclusion of non-security things such as the Kaby Lake / Ryzen CPU block I don’t know for how long). I can easily figure out myself what updates to install each month. I will NEVER go to Group A, and if Group B becomes unworkable in the future then Group C it is for me.
So please keep the Group B instructions as a reference.
Hope for the best. Prepare for the worst.
MrBrian
AskWoody_MVPApril 27, 2017 at 2:13 pm #1114682 users thanked author for this post.
TonyS
AskWoody PlusApril 27, 2017 at 3:50 pm #111483Has anybody tried Spybot Anti-Beacon 1.6 that claims to block telemetry in win 7-8-10. I use it on my 3 pc’s but I’m not sure it really works.
I’ve been running it for several months now. As Canadian Tech says, I have no idea how well it works, but it tells me that it has disabled telemetry in addition to the MS CIEP stuff so I’m running with it until I know any better.
Win10 22H2 Pro, MBAM Premium, Firefox, OpenOffice, Sumatra PDF.1 user thanked author for this post.
TonyS
AskWoody PlusApril 27, 2017 at 4:05 pm #111486Late arrival at the party due to holidays etc. I’m Group B on W7 x32 and x64 and intending to stay that way for the foreseeable future. Just updated using latest April security only patches and so far, so good (as the man said when he jumped out of the twelfth floor window). I don’t use IE unless forced into it (Firefox user for years), use Open Office instead of MS Office, use Thunderbird for email and replace other ‘standard’ MS products with respected 3rd party software wherever possible. I provide support to several less knowledgeable users who are classed as Group A, but only update these machines several weeks after patches released and then only after Woody’s Defcon is favourable.
Spent many years in ‘the appliance of science’ and IT support so know my way around the block, but still send ongoing thanks to Woody, Noel Carboni, MrBrian, Canadian Tech and others for keeping me on the straight and narrow.
Win10 22H2 Pro, MBAM Premium, Firefox, OpenOffice, Sumatra PDF.1 user thanked author for this post.
anonymous
GuestApril 28, 2017 at 2:11 pm #111680Personally, I think some of you guys are over analyzing this stuff.
I’m Group B on all of my machines (Win 7 Ult, Pro 32/64). My work as a contractor for letter agencies dictates that outbound connections be monitored in real-time. So far, all is good. No telemetry c**p slipping through (unless I explicitly allow it). I certainly don’t want MS, or anyone else, to know what pen testing apps and tools are on my machines. Nor do I want any “sensitive” data disclosed.
Group B is simple if you just:
1) manually install the monthly security update and IE update
2) let WU handle .Net, Office 2010, etc.
3) hide any drivers that might show upLike others here, I dedicate one, sometimes two, machines as sacrificial lambs. After patch testing, I deploy across my other machines.
Installing 664, or any of the other telemetry patches, will just make life more complicated. These patches have hooks embedded deeply into the OS. Keeping a machine secure/quiet will be harder.
It’s not just MS that we have to fight. For example, after each update, I have to disable nVidia and Adobe telemetry. And then there’s the application firewall that has to be monitored. It’s a battle for sure.
Also like others here, my Group B Win 7 hardware is running just dandy – fast and incredibly stable (and I do mean stable). So, I’m voting for maintaining Group B.
CA
-
anonymous
GuestMay 10, 2017 at 5:04 pm #114114LMAO, guess my security practices match up with 3LA’s concerning auditing all outbound connections. I’ve configured my system to just pull DHCP and shut up when connecting to networks. If you check with wireshark by default you get to see just how noisy windows machines are when connecting to a new network.
Keeping this up on multiple machines all at once has been a pain, however.
MrBrian
AskWoody_MVPApril 29, 2017 at 3:36 am #111769Here are the “ingredients” in the approach that I recommend:
1. Give instructions and/or script to set the operating system’s Customer Experience Improvement Program setting = No.
2. Give instructions and/or script to set these Windows Update settings:
Important Updates = Never check for updates.
Give me recommended updates the same way I receive important updates = Checked.
Give me updates for Microsoft products and check for new optional Microsoft software when I update Windows = Checked.
3. Check for updates manually in Windows Update. Leave everything at defaults, except uncheck KB2952664 (Windows 7 with service pack 1), KB2977759 (Windows 7 without service pack 1), KB2976978 (Windows 8 and 8.1), and perhaps other updates (to be determined).
4. Since KB2976978 can’t be uninstalled in some circumstances, give instructions and/or script to disable tasks associated with KB2976978.
5. Provide instructions and/or script that uninstalls KB2952664, KB2977759, KB2976978, KB3150513, and perhaps other updates (to be determined). The script has a list of updates to uninstall, and can be easily be modified for those who are unhappy with the default list of updates to uninstall.
These “ingredients” will probably not be included: adding firewall rules, disabling Diagnostics Tracking Service, removing Diagnostics Tracking Service.
Your thoughts on this approach?
-
woody
ManagerApril 29, 2017 at 3:02 pm #111857There’s a lot of merit to that….
I’m thinking of replacing both Group A and Group B with a very, very simple set of steps – if it’s possible – that installs the latest Monthly Rollup then disables known telemetry patches. E.g., https://www.askwoody.com/forums/topic/script-that-uninstalls-all-installed-versions-of-kb2952664-kb2976978-kb2977759/#post-111462
But I need to make it very, very simple. Something my mother could follow.
Suggestions?
1 user thanked author for this post.
-
Canadian Tech
AskWoody_MVPApril 29, 2017 at 3:38 pm #111862Woody, that presumes the ONLY undesirable part of the Monthly Rollup is telemetry. That may be correct today, although I doubt it. It surely is a risk for the future.
My sense of it is that MS would like to essentially convert Win7 machines to as much like Win10 as they can. They may not just stop at telemetry.
Looking for input on this thought???
CT
-
MrBrian
AskWoody_MVP -
Canadian Tech
AskWoody_MVP -
MrBrian
AskWoody_MVP
-
-
-
-
MrBrian
AskWoody_MVP -
woody
ManagerApril 30, 2017 at 7:17 am #111981I’m looking for a very simplified variant of what you posted above.
People should be able to keep their @in7/8.1 machines updated, without telemetry, even if they don’t know a filename extension from a hotdog, and can’t imagine how to elevate a command prompt.
That’s an exaggeration, but every detailed step add to the hassle.
It’s the dummies dilemma.
-
samak
AskWoody PlusApril 29, 2017 at 5:27 pm #111874I think CT had it right with :
“Woody, that presumes the ONLY undesirable part of the Monthly Rollup is telemetry. That may be correct today, although I doubt it. It surely is a risk for the future.”
At the moment all I have to do is install the right Group B patches and I’m done. This proposal would mean I have to install patches and then mess around disabling known telemetry patches.
It’s an interesting idea, but no thanks.
Best wishes to all.
Windows 10 Home 22H2, Acer Aspire TC-1660 desktop + LibreOffice, non-techie
5 users thanked author for this post.
-
Canadian Tech
AskWoody_MVPApril 29, 2017 at 5:34 pm #111875samak, One more thing to keep in mind. Can you really trust MS to always maintain those “security only” patches as only security???
MS has proven itself way beyond trustworthy. It has no profit motive whatsoever to maintain this, and clearly, short term profit is the only thing this short term management has in mind.
Add to that the current level of incompetence being delivered in defective updates one after another, and you have a picture of Windows Update as nothing short of a minefield.
That’s the way I see it.
CT
MrBrian
AskWoody_MVPApril 29, 2017 at 10:39 am #111810Something to keep in mind about Group B: Some updates that Microsoft classifies as “Recommended” (which Group B avoids, right?) are actually security-related. Example: KB3004394: Support for urgent Trusted Root updates for Windows Root Certificate Program in Windows.
2 users thanked author for this post.
-
Canadian Tech
AskWoody_MVP -
MrBrian
AskWoody_MVPApril 29, 2017 at 11:04 am #111819In case anyone does a web search for this update, for Windows 7 the first version of this update caused a lot of problems. Microsoft later issued another update that uninstalled the first version of this update for Windows 7 users. Version 2 of this update was released a few months later.
1 user thanked author for this post.
SueW
AskWoody PlusApril 29, 2017 at 11:42 am #111823Give me recommended updates the same way I receive important updates = Checked.
Why, if one is staying in Group B (raises hand!), do I want Recommended updates in my Important updates list? If they are Recommended, I want them in my Optional list as a precaution.
Ever since I purchased my current computer in late 2014, I have had to research what each update meant prior to applying Windows Updates each month. This became a process that would take up to 3 &^%$ hours each time! It was through my research that I found Woody and AskWoody.com plus InfoWorld.com.
I have avoided any GWX c*** or installing questionable updates, have disabled CEIP and DiagTrack, avoiding — knock wood — MS’ telemetry c***.
When AskWoody’s DEFCON System is at “3,” that’s my trigger to apply the most recent Group B updates. I find the process for doing so straight-forward, and easy to follow.
I realize that there are tons of behind-the-scenes activities (downloading/installing/testing/tweaking) plus a great deal of time involved going on beforehand in order to provide us with this simple, streamlined process, and for that I am very grateful.
Provided MS doesn’t really [mess] it up, I’d like to see the Group B approach [as well as the DEFCON system] continue as a viable method.
My $.02
Windows 7 HE; Office 2010; Group B; Former ‘Tech Weenie’
Win 7 SP1 Home Premium 64-bit; Office 2010; Group B (SaS); Former 'Tech Weenie'-
MrBrian
AskWoody_MVP
ebrke
AskWoody LoungerSessh
AskWoody LoungerApril 29, 2017 at 6:28 pm #111877At the moment all I have to do is install the right Group B patches and I’m done. This proposal would mean I have to install patches and then mess around disabling known telemetry patches.
..and herein lies the issue. What is the b***** point of downloading updates if you’re just going to neuter them immediately afterwards and how is not downloading the update at all somehow more confusing than that? On top of that, Windows may decide at any time to re-enable those telemetry settings without your consent or knowledge. I really don’t understand. There has been a lot of input on this matter from people in Group B and the general consensus is this:
1.) The group B instructions are not too confusing or difficult to follow and 2.) they are happy with group B and wish to continue being group B.
I don’t get all the force being applied to these people to change their updating ways. There is no real demand for that on these forums and it is in fact the opposite; there is demand for the continuation of Group B that seems to be falling on deaf ears here. There is also the fact that people no longer trust Microsoft to distribute patches that aren’t buggy and/or give them malware based on the hardware they have which breaks functionality. It is way more than telemetry at this point.
-
anonymous
Guest -
samak
AskWoody PlusApril 29, 2017 at 7:04 pm #111882“I don’t get all the force being applied to these people to change their updating ways. There is no real demand for that on these forums and it is in fact the opposite; there is demand for the continuation of Group B that seems to be falling on deaf ears here.”
Ha ha. I just realised that this is identical to the way MS operates. Wonderful irony!
Windows 10 Home 22H2, Acer Aspire TC-1660 desktop + LibreOffice, non-techie
Sessh
AskWoody LoungerApril 29, 2017 at 7:15 pm #111884Ha ha. I just realised that this is identical to the way MS operates. Wonderful irony!
As did I though I was trying not to be quite that heavy handed, but it’s absolutely true. We have a lot of dictators on here lately that think there is only one right way to do things for everyone and the fact that what Group B users are saying on here has had no apparent impact on the direction this is taking is, as you put it, exactly what MS is doing that caused Group B to exist in the first place! Irony indeed! The message is “You can do it your own way if it’s done just how I say!” It makes absolutely zero sense, zero!
It has been made perfectly clear and obvious that there was no point of starting this thread. No questions were asked and none of the answers have been acknowledged. This thread has instead made the decisions for everyone and already started giving out so much conflicting advice that it has confused people who were not confused before. It’s pretty ridiculous IMO. Why even ask if Group B is viable if you’ve already decided (for everyone else) that it isn’t?
It’s exactly what MS is doing to people that has cost them their credibility and the loyalty of their customers and as a result are no longer trusted, so what do you think will happen on AskWoody.com? Something different?
1 user thanked author for this post.
-
anonymous
GuestApril 29, 2017 at 8:38 pm #111887Woody was the one who asked if Group B was viable. He is the one who will make the final decision and hopefully he will do the right thing by those of us in Group B
for whom it is viable. (Crossed out because no one who thinks that Group B isn’t viable is still in Group B unless there’s something seriously wrong with them.) -
anonymous
GuestApril 29, 2017 at 11:39 pm #111897@ Sessh
We have a lot of dictators on here lately that think there is only one right way to do things for everyone and the fact that what Group B users are saying on here has had no apparent impact on the direction this is taking is, as you put it, exactly what MS is doing that caused Group B to exist in the first place! Irony indeed! The message is “You can do it your own way if it’s done just how I say!” It makes absolutely zero sense, zero!
We should know where some of these “dictators” on AskWoody are coming from. Usually their livelihood depends on the continued success of M$ and Windows, eg Windows System Admins and Windows Software/Game Developers. Imagine M$ and Win 10 going bankrupt = these “dictators” will lose their jobs or livelihood.
. . So, for self-preservation, they are innately biased for M$ and Win 10, ie to them, M$ are always right, and not ‘customers are always right’.1 user thanked author for this post.
-
ch100
AskWoody_MVPApril 30, 2017 at 12:01 am #111906There are few issues here.
One is the amount of work which those supporting the so called Group B are doing in their free time.
Nobody is trying to dictate your own method of updating, on the condition it is your own.
Woody has created Group B for the benefit of users who are over sensitive to telemetry issues. Woody is the only high profile author who supports this method for home users, against the trend. Susan Bradley does not support it even for enterprise users to give an example. Do you realise that those who provide solutions here are in favour of Group A (with one notable exception) while those who ask for solutions are in the other category? Have you ever wondered why?
Those same Group B followers do not realise that telemetry has been built in a large number of products like MSRT, Office, antivirus products, browsers and the list goes on and this has been happening long before Microsoft started implementing telemetry in the OS.
In a technical sense, all those following Group B, do not know if they are fully patched, because there is only one way to know for home users and nobody except for me once or twice has mentioned that method here. If the level of patching does not matter, then why patching at all?
Microsoft’s survival does not depend on few posters on this forum.4 users thanked author for this post.
-
samak
GuestApril 30, 2017 at 1:32 am #111915“There are few issues here. One is the amount of work which those supporting the so called Group B are doing in their free time.”
I’m having difficulty understanding this point. MS itself differentiates between Groups A and B in effect by offering security-only updates and full rollups. If Woody is going to write an article every month on InfoWorld about the updates, then he has to understand what all the different options mean anyway. Once he’s done that then updating the instructions to groups A and B should be mainly a copy and paste job (changing KB numbers) unless MS has changed the process during the month. I would argue that it is obviously more work, but not much more.
“Woody has created Group B for the benefit of users who are over sensitive to telemetry issues.”
Not over-sensitive, just sensitive.
“Woody is the only high profile author who supports this method for home users, against the trend.”
Well done to Woody for doing so. It is never a safe option to lift your head above the parapet and go against the trend. Kudos to Woody for having the intestinal fortitude to do so.
“Those same Group B followers do not realise that telemetry has been built in a large number of products like MSRT, Office, antivirus products, browsers and the list goes on”
They do realise that telemetry has been built in a large number of products and are trying to minimise it, that is why they are in Group B.
“If the level of patching does not matter, then why patching at all?”
I haven’t heard any Group B person saying that the level of patching does not matter – it matters to them that they get the level of security updates only, that is why they are in Group B. -
anonymous
GuestApril 30, 2017 at 2:11 am #111924“Woody has created Group B for the benefit of users who are over sensitive to telemetry issues.”
Please try to be objective… Woody has created Group B for the benefit of users who are sensitive to telemetry issues. Calling them “users who are over sensitive to telemetry issues” is your opinion.
“Do you realise that those who provide solutions here are in favour of Group A (with one notable exception) while those who ask for solutions are in the other category?”
All those who ask for solutions are not “in the other catagory”. To say that they are is contrary to fact.
“Those same Group B followers do not realise that telemetry has been built in a large number of products like MSRT, Office, antivirus products, browsers and the list goes on”
This is also contrary to fact. There are those in Group B who have been doing their best to minimize telemetry on their systems for years.
“If the level of patching does not matter, then why patching at all?”
The level of patching does matter. This is not the same as being as fully patched as possible. Does it really matter, for example, if I am not patched against a vulnerability which requires physical access to a computer and no one but me has access to the computer unless they break in to my house?
And, finally, to give you your due –
“Microsoft’s survival does not depend on few posters on this forum.”
No, it doesn’t, and those who have suggested boycotting Microsoft were, to say the least, unrealistic.
-
anonymous
GuestApril 30, 2017 at 2:14 am #111925@ ch100
Do you realise that those who provide solutions here are in favour of Group A (with one notable exception) while those who ask for solutions are in the other category? Have you ever wondered why?
Because many of those who look for advice reject those who provide advice (not solutions or fixes) here in favour of Group A (= same advice as M$’s), similar to how they have rejected the recommended GWX KB3035583 update of M$’s Win 10 and remained on Win 7/8.1.
Like I said before, a few self-interested posters here have M$-blinders on.
2 users thanked author for this post.
-
anonymous
GuestApril 30, 2017 at 7:50 am #111932No, M$ created Group B for Enterprise-users in Oct 2016 because the Enterprise-users wanted a security-only Group B. Woody only adapted it for home-users.
https://blogs.technet.microsoft.com/windowsitpro/2016/10/07/more-on-windows-7-and-windows-8-1-servicing-changes/Edited – Please follow the Lounge Rules- no personal attacks, no swearing, and politics/religion are relegated to the Rants forum.
2 users thanked author for this post.
-
-
Elly
AskWoody MVPApril 29, 2017 at 8:53 pm #111890I am comfortable with Group B, Win 7 Home. It matches my intention of a secure and telemetry-free operating system.
I understand the concern that it might not be possible long term to maintain it doing that safely and securely. I am grateful that longer term solutions are being explored and proposed.
I am comfortable with referring other non-techy people to this site, but do have to explain a bit about the Defcon system and Group choices. I know that Woody would like all of us to have a good Windows experience… but Microsoft seems h*** bent on making that impossible.
I like the idea of having a link at the DEFCON number at the top, that goes to a post about the current number… then the newcomer doesn’t have to go through multiple posts to find it.
I’m glad I don’t have a processor that Microsoft intentionally blocks from updates… It has to be a support nightmare… but (deep breath) the fixes seem to come out almost as fast as the problem was implemented. Long ago (my kids were small) EA Games used DRM that disabled (permanently, unless worked around) my CD/DVD burner. They have changed their approach, but no one here uses any EA Games ever since. They never replaced or fixed the problems they caused. My kids learned pirating techniques to get around the DRM (which was implemented to prevent pirating), use their games, and keep me happy. Now I’m learning how to circumvent Mircosoft’s intentions… and keep my operating system happy and stable.
Group B for Win 7 has been simple… much simpler than all the updating problems of W 10. I’d like it to stay that way, but will go to Group W if forced. Thank you, Woody, and all the MVPs.

Non-techy Win 10 Pro and Linux Mint experimenter
anonymous
GuestApril 30, 2017 at 1:48 am #111917The Win7 Home Premium system here has nearly always been set for manual updating – ie WU service disabled until patch Tuesday, when it was enabled, used to update the system with its own routine, then disabled until the next month. This was decided on in the first week of the system’s install when WU set to advise before downloading was ignored and patches were both downloaded and applied without admin advice. Natch, one had interfered with a card reader. ho hum.
At the point when the WU service began stuttering and taking hours to go through its routine, I made the unilateral decision to begin fully manual updating using the Security Bulletin as a reference, rather than trying to patch WU itself.
This entailed downloading the msu packages and running them manually but was actually a touch more smooth than using the WU interface to link through to the same Security Bulletin articles.Having had so much experience admining XP machines on the home network from the days of the Blaster worm patch not getting applied by yet one more WU misconfiguration, I’m chary of taking anything MS promises in the way of remote/auto care for any of its systems. The petition on restoring the Security Bulletin pages is where I landed when MS removed that sure way of deciding on what and how to patch my home network machines without the ‘help’ of WU.
This site has become a page one resident in web searches, so the A, B and Defcon systems seemed worth some investment of time for us self-helpers until MS comes to the party about restoring some kind of basic information tables about its ‘rollups’.
I can’t fault the logic behind Group B; it’s what I’ve been following myself and hasn’t left any of the big net threats unpatched – mind you, the big ones of the last few months have been more in Office and dotNET – both of which I’ve eschewed for some years now.
IE patching independent of Security Only is welcome here, since IE is only deployed rarely now for the occasional check of obscure legacy flash behaviour. Both Firefox and Chromium have long since superseded IE as the secure browser to use in Win7.I continue to run the Win7 machine because it has so much legacy software and multimedia functionality that is valuable to the household. MS advice that Win7 development has ceased except for security maintenance makes it logical that Group B should be continued as a good simple approach to manual patch maintenance on a useful 5yo machine that won’t be getting any hardware upgrades.
Telemetry has never been any consideration in my administration of any Win system; MS is welcome to gather data and I remain able to work out what offer I want to accept. More of a consideration is the avoidance of unwanted patching of drivers and non-essential software that take so much of an admin’s time to adjust and fix when they go awry. Win kernels have always been great compendiums of drivers, and therein lies the problem if patching is applied without careful vetting by admins. If MS continues to balk at reinstating the Security Bulletin format, the Woodies Group B will remain a very valuable tool for many of us using systems that we bought with Win7 and for which we want to extract best value before updating.Your contributor pkcano’s group B patch history is exemplary.
I was happy to find it confirmed my own decisions for Jan, Mar and April.An Australian resident.
5 users thanked author for this post.
MrBrian
AskWoody_MVPApril 30, 2017 at 4:01 am #111949I have a solution that is partially done. There are two scripts involved: PreWinUpdateProc and PostWinUpdateProc.
The order of running is as follows:
Run PreWinUpdateProc.
Run Windows Update. Install updates that are checked by default.
Run PostWinUpdateProc.What PreWinUpdateProc will do:
1. Sets the operating system’s Customer Experience Improvement Program setting = No.
2. Sets the Windows Update settings to use.
3. Checks for Windows updates (doesn’t install any) and hides unwanted ones.What PostWinUpdateProc will do:
1. Uninstalls unwanted updates.
2. Disables telemetry appraiser tasks. Needed because KB2976978 can’t be uninstalled for Windows 8.1 users in some circumstances.Both PreWinUpdateProc and PostWinUpdateProc have a list of updates that the user can customize if the defaults aren’t what the user wants.
1 user thanked author for this post.
Sessh
AskWoody LoungerApril 30, 2017 at 9:12 am #111997There are few issues here. One is the amount of work which those supporting the so called Group B are doing in their free time.
As for the ones doing this work, wasn’t the whole issue supposedly that Group B was “too confusing” for people? I haven’t seen anyone complain about how much work it is to put together and all the work done on testing this stuff is amazing and fantastic information for everyone here. I’m sure the ones doing that work know that it is much appreciated here, but even then, they choose to do it for people. They seem willing to help people and spend their time doing so. What’s wrong with that?
Woody has created Group B for the benefit of users who are over sensitive to telemetry issues. Woody is the only high profile author who supports this method for home users, against the trend.
Mass surveillance is a reality that is getting harder and harder to avoid and people want to avoid it as much as possible. People come to this site because they want to “go against the trend” of accepting this kind of surveillance instead of falling in line. Let them!
Susan Bradley does not support it even for enterprise users to give an example.
Group B works for people and for that matter, so does Group C. Their computers are stable and run just as fast as they ever have for months and months.
Do you realise that those who provide solutions here are in favour of Group A (with one notable exception) while those who ask for solutions are in the other category? Have you ever wondered why?
Yeah, it’s because they are not interested in Group A. They prefer Group B. It’s very, very simple.
Those same Group B followers do not realise that telemetry has been built in a large number of products like MSRT, Office, antivirus products, browsers and the list goes on and this has been happening long before Microsoft started implementing telemetry in the OS.
Of course they do. There are numerous discussions on these forums of knowledgeable users sharing ALL of their security settings for browsers and their opinions on things like antivirus programs, registry cleaners and all these types of programs so people can learn things and adopt things they choose to adopt and reject the rest. Just because it’s been happening for a very long time in Windows does not mean anyone has to continue to accept it today.
In a technical sense, all those following Group B, do not know if they are fully patched, because there is only one way to know for home users and nobody except for me once or twice has mentioned that method here.
People in Group B don’t want to be fully patched! They want the security updates without everything else!
[Edited by Woody to remove ad hominem attacks. C’mon guys. Let’s focus on issues, not personalities.]
8 users thanked author for this post.
-
ebrke
AskWoody Lounger -
woody
ManagerMay 1, 2017 at 11:29 am #112146Group B works for people and for that matter, so does Group C.
That was true, for the most part, until last month with MS17-010 (which EVERYONE running Win7 or 8.1 should install) and this month with the Word and concomitant Windows patches.
Life’s getting considerably more complicated. I don’t intend to abandon “Group B” or Group B users. I’ll continue to talk about Group B and post instructions on this site to stay on the Group B trail. But I’m getting more and more concerned that folks who should be in Group A are trying to get into Group B, not understanding that there are limitations.
The ideal situation would be, as I have described, where most people can follow the Group A path, then get rid of the dicey parts. The solution has to be ultra-simple. It won’t be easy for those working behind the scenes to come up with a patching method “for dummies,” but the result should be something that everybody can work with.
I’m not going to spout the Microsoft Party Line. Few people who have really worked with patches, and seen their deleterious effect, do. I still think Automatic Update is a poor choice for everyone except those who absolutely can’t (or won’t) maintain their own machines. I still take extreme umbrage at people who feel that Auto Updates must be pushed on everyone “for the good of the community” and I’m particularly incensed by those who compare Auto Update opponents to anti-vaxxers. Still, you gotta update sooner or later.
Everybody has to.
-
ebrke
AskWoody Lounger
-
Northwest Rick
AskWoody LoungerApril 30, 2017 at 1:52 pm #112034Hey Woody,
Ever since I stumbled onto your ongoing MS Windows commentary, I have been a keen and interested follower. As soon as you elaborated the two-track approach for machines running a pre-10 MS Windows OS (I use 7, 8’s touch screen and other vapid “enhancements” did not entice me) I became a dedicated member of Group B.
I loathe OS 10 and the mentality that spawned it. I know whereof I speak, because I sacrificed a perfectly good OS 7 laptop to the free OS 10 upgrade as a trial run. Therefore I appreciate and support your efforts on this topic. I have even benefited from your tips on OS 10, such as “wushowhide”.
I do know that the future of Group B is doomed by the eventual demise of MS support for OS 7 less than three years from now, when extended support is scheduled to end. I will deal with that when the time comes (was considering switching to an Apple machine rather than capitulating, until I read your “mac OS’s snooping remains open to debate” – something ELSE I will now have to investigate! Borrowing Captain Haddock’s exclamation, “Blistering barnacles!”)
For now, though, I would very much like to see Group B continue! Thanks again for your efforts on our behalf! I don’t think @PKCano’s list is “oppressive”, once one gets caught up. I would guess that even Johnny-come-latelies would be more elated than defeated on discovering it – at least, that would be MY response!
BTW, it doesn’t bother me that you have been “assimilated”; while it is easy to dismiss an external critic, no one speaks with more authority than an internal one.
Northwest Rick
anonymous
GuestApril 30, 2017 at 3:50 pm #112051I just finished reading the entire thread. Lots of guidance and viewpoints. Excellent.
The Group B adopters have convinced me that the security-only approach is viable. It is not for a user with no computer skills, but it is by no means difficult. It takes a little bit of extra effort. Group B adopters are not being arrogant about their decision, they are just saying that they are comfortable with it and uncomfortable with the alternatives.
Furthermore, it is so refreshing to visit a forum for the first time and see so many users with varying levels of knowledge having the courage to participate in the discussion and stand up for what they think is right for them. Very impressive.
James Bond 007
AskWoody LoungerMay 1, 2017 at 12:01 am #112087It seems there is a proposal here along the lines that “we shall install the rollup (Group A) anyway, and then try to remove all the telemetry and other undesirable stuff”. Well, for me, I much prefer not to have those undesirable stuff in the first place. I want to try to avoid or minimize the impact of these things. I don’t want to “fall in line”. So I vote for B.
I am a bit concerned that in the future the Group B instructions may be removed from here, and in such a case I will still find the Group B patches myself and apply them when I think they are ready, or skip them if they cause problems for me.
I welcome ways of removing these undesirable things, however. It may be useful for me in the future if I am not vigilant enough at all times and allow some of them to pass through on my PCs.
Hope for the best. Prepare for the worst.
4 users thanked author for this post.
MrBrian
AskWoody_MVPMay 2, 2017 at 7:14 am #112307I have written three scripts. If anybody wants to use them to get an idea of how the approach works, I could put the scripts online. At this point I’m not looking for bug reports, since the scripts are not necessarily done or well-tested yet.
The three scripts are:
1. A script that checks for Windows updates online that are applicable to your computer (including applicable updates that are superseded by other applicable updates), and hides the applicable updates that are specified in the script, so that future runs of Windows Update will not install those hidden updates.
2. A script that uninstalls Windows updates that are specified in the script.
3. A script that lists the installation status of Windows updates that are specified in the script. This script could also be useful for Group B users as a compliance checker.
2 users thanked author for this post.
MrBrian
AskWoody_MVPMay 6, 2017 at 1:33 pm #113027I think I will be writing a console application using VBScript that has various Windows Update-related functionality. I will probably have more time to work on it next weekend. If anybody has some Windows Update-related functionality you’d like to see included, feel free to request. Also, if anybody has a suggestion for development using something else other than VBScript, feel free to suggest alternatives.
1 user thanked author for this post.
anonymous
GuestMay 8, 2017 at 4:07 pm #113419Coming in a bit late, I know. But I just wanted to note that I will happily remain in Group B as long as someone is willing to post a list of direct links to necessary security-only patches for Windows 7 each month.
Checking whether I have a particular patch installed or not is trivial; watching for any reports of possible problems, and figuring out whether they apply to me, is doable. What consistently has been a headache for me, is figuring out where Microsoft hid the d**n things, and whether I actually have a browser installed on my system that doesn’t have to be run in Safe Mode or some form of emulation in order to download them!
-
PKCano
ManagerMay 8, 2017 at 4:11 pm #113427The Security-only updates for Win7 and the Cumulative Update for IE11 are available through the Microsoft Update Catalog.
But you can download them from AKB2000003 on this site.
They will need to be manually installed.
MrBrian
AskWoody_MVPMay 9, 2017 at 11:10 am #113624Status update:
1. Code isn’t done yet. Maybe will work on it this Saturday. Whenever it’s done, then it needs to be tested by me, then by a few more, etc.
2. I want to do more testing of various updates and of Diagnostics Tracking Service itself. Also, testing of Windows 8.1 (which I have not tested yet).
3. List of updates to avoid needs to be decided. Others could help with this in parallel with my efforts, but I will also be doing tests to aid in my advice. Maybe some other qualified people could do technical tests also?
4. Would like to see what happens with the upcoming integration of existing updates into the monthly rollups. Example: Will code from KB2952664 be integrated into Windows 7 monthly rollups?
MrBrian
AskWoody_MVPGoneToPlaid
AskWoody LoungerMay 10, 2017 at 9:34 pm #114151My advice is referenced in knowledge base article: 2952664: Telemetry in Win7/8.1 – KB2952664, KB2977759, KB2976978, & KB3150513. Due to test results that I have not posted yet, my advice there is insufficient in some cases, because for Windows 7 if KB2952664 is installed and Diagnostics Tracking Service is not installed, KB2952664 can send data to Microsoft via another process (not via Diagnostics Tracking Service). If you want to stop transmission to Microsoft of the newly added telemetry (in recent few years) in Windows 7, I believe that blocking network traffic to IP address 64.4.54.254 is sufficient. Optionally, you could also block network traffic to IP address 64.4.54.253, which Microsoft documents as being for telemetry settings. This page shows how to block an IP address in Windows Firewall: http://www.easysecurityonline.com/how-to-protect-windows-7-and-8-from-getting-windows-10-privacy-intrusions-too/. I have had IP addresses 64.4.54.253 and 64.4.54.254 blocked for months on my Windows 7 computer, with no apparent negative effects so far. Also, be sure to set the operating system’s Customer Experience Improvement Program setting = No.
Blocking that one IP address is far from sufficient. Telemetry is sent to dozens of IP addresses all over the world, and to third parties including Facebook.
-
MrBrian
AskWoody_MVPMay 11, 2017 at 6:48 am #114228There indeed are more. I think it would be best if posters would specify what source of telemetry they are referring to. For example, we could talk about Microsoft Compatibility Appraiser telemetry. For Microsoft Compatibility Appraiser telemetry, the latest info on IPs involved is at this post.
GoneToPlaid
AskWoody LoungerMay 10, 2017 at 9:54 pm #114154You don’t need to run any script if CEIP is disabled. The only patch which needs to be avoided is KB2952664 for Windows 7 SP1 and equivalent for the other OS.
Not true.
-
woody
Manager -
GoneToPlaid
AskWoody LoungerMay 11, 2017 at 3:06 pm #114442I had KB2999226, the Update for Universal C Runtime in Windows, installed for several months on my computer. It turns out that this is another update which installs deep telemetry.
Here is a list of all web addresses which were visited by rundll32.exe during regular use of my computer:
Date/Time Web address
——————————————————————————————————————————————————————-
05/06/2016 04:13 AM http://go.microsoft.com/fwlink/?LinkID=616099
05/05/2016 03:15 AM http://wscont.apps.microsoft.com/winstore/OSUpgradeNotification/appraiser/2015_07_24_16_20_X64.CAB
05/05/2016 03:15 AM http://go.microsoft.com/fwlink/?LinkID=616099
05/04/2016 04:11 AM http://go.microsoft.com/fwlink/?LinkID=619677
05/03/2016 04:26 AM http://go.microsoft.com/fwlink/?LinkID=619677
05/02/2016 10:08 AM http://go.microsoft.com/fwlink/?LinkID=619677
04/30/2016 03:37 AM http://go.microsoft.com/fwlink/?LinkID=619677
04/29/2016 08:35 AM http://go.microsoft.com/fwlink/?LinkID=619677
04/28/2016 08:46 AM http://go.microsoft.com/fwlink/?LinkID=619677
04/27/2016 03:25 AM http://go.microsoft.com/fwlink/?LinkID=619677
04/26/2016 04:38 AM http://go.microsoft.com/fwlink/?LinkID=619677
04/25/2016 04:42 AM http://go.microsoft.com/fwlink/?LinkID=619677
04/24/2016 04:26 AM http://go.microsoft.com/fwlink/?LinkID=619677
04/23/2016 03:58 AM http://go.microsoft.com/fwlink/?LinkID=619677
04/22/2016 04:51 AM http://go.microsoft.com/fwlink/?LinkID=619677
04/21/2016 04:50 AM http://go.microsoft.com/fwlink/?LinkID=619677
04/20/2016 04:11 AM http://go.microsoft.com/fwlink/?LinkID=619677
04/19/2016 03:04 AM http://go.microsoft.com/fwlink/?LinkID=619677
04/18/2016 03:10 AM http://go.microsoft.com/fwlink/?LinkID=619677
04/17/2016 04:33 AM http://go.microsoft.com/fwlink/?LinkID=619677
04/16/2016 07:20 AM http://go.microsoft.com/fwlink/?LinkID=619677
04/15/2016 09:34 AM http://go.microsoft.com/fwlink/?LinkID=619677
04/14/2016 03:29 AM http://go.microsoft.com/fwlink/?LinkID=619677
04/13/2016 04:39 AM http://go.microsoft.com/fwlink/?LinkID=619677
04/12/2016 07:37 AM http://go.microsoft.com/fwlink/?LinkID=619677
04/11/2016 03:42 PM http://go.microsoft.com/fwlink/?LinkID=619677
04/10/2016 08:36 AM http://go.microsoft.com/fwlink/?LinkID=619677
04/09/2016 06:19 AM http://go.microsoft.com/fwlink/?LinkID=619677
04/08/2016 03:40 AM http://go.microsoft.com/fwlink/?LinkID=619677
04/07/2016 08:29 AM http://go.microsoft.com/fwlink/?LinkID=619677
04/06/2016 03:15 AM http://go.microsoft.com/fwlink/?LinkID=619677
04/05/2016 07:40 AM http://go.microsoft.com/fwlink/?LinkID=619677
04/04/2016 08:49 AM http://go.microsoft.com/fwlink/?LinkID=619677
04/02/2016 06:48 AM http://go.microsoft.com/fwlink/?LinkID=619677
04/01/2016 03:17 AM http://go.microsoft.com/fwlink/?LinkID=619677
03/31/2016 03:05 AM http://go.microsoft.com/fwlink/?LinkID=619677
03/30/2016 08:55 AM https://settings.data.microsoft.com
03/30/2016 08:55 AM http://go.microsoft.com/fwlink/?LinkID=619677
03/29/2016 10:55 AM http://go.microsoft.com/fwlink/?LinkID=619677
03/28/2016 06:13 AM http://go.microsoft.com/fwlink/?LinkID=619677
03/27/2016 06:29 AM http://go.microsoft.com/fwlink/?LinkID=619677
03/26/2016 03:52 AM http://go.microsoft.com/fwlink/?LinkID=619677
03/25/2016 07:04 PM http://go.microsoft.com/fwlink/?LinkID=619677
03/24/2016 03:01 AM http://www.microsoft.com/pkiops/crl/Microsoft%20Windows%20Third%20Party%20Component%20CA%202012.crl
03/24/2016 03:01 AM http://sf.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTSqZMG5M8TA9rdzkbCnNwuMAd5VgQUz5mp6nsm9EvJjo%2FX8AUm7%2BPSp50CEF5HdTXGg0O6ccdNcLnpfVs%3D
03/24/2016 03:00 AM http://wscont.apps.microsoft.com/winstore/OSUpgradeNotification/appraiser/2015_08_28_08_27_x64.cab
03/24/2016 03:00 AM http://go.microsoft.com/fwlink/?LinkID=619677
03/22/2016 11:02 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
03/22/2016 11:02 AM https://telecommand.telemetry.microsoft.com
03/22/2016 11:02 AM https://telecommand.telemetry.microsoft.com
03/22/2016 10:24 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
03/22/2016 10:24 AM https://telecommand.telemetry.microsoft.com
03/22/2016 10:24 AM https://telecommand.telemetry.microsoft.com
03/21/2016 09:48 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
03/21/2016 09:48 AM https://telecommand.telemetry.microsoft.com
03/21/2016 09:48 AM https://telecommand.telemetry.microsoft.com
03/21/2016 09:02 AM https://telecommand.telemetry.microsoft.com
03/21/2016 09:02 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
03/21/2016 09:02 AM https://telecommand.telemetry.microsoft.com
03/20/2016 08:15 AM https://telecommand.telemetry.microsoft.com
03/20/2016 08:15 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
03/20/2016 08:15 AM https://telecommand.telemetry.microsoft.com
03/19/2016 12:06 AM https://telecommand.telemetry.microsoft.com
03/19/2016 12:06 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
03/19/2016 12:06 AM https://telecommand.telemetry.microsoft.com
03/18/2016 12:56 AM https://telecommand.telemetry.microsoft.com
03/18/2016 12:56 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
03/18/2016 12:56 AM https://telecommand.telemetry.microsoft.com
03/17/2016 12:57 AM https://telecommand.telemetry.microsoft.com
03/17/2016 12:57 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
03/17/2016 12:57 AM https://telecommand.telemetry.microsoft.com
03/16/2016 08:06 AM https://telecommand.telemetry.microsoft.com
03/16/2016 08:06 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
03/16/2016 08:06 AM https://telecommand.telemetry.microsoft.com
03/12/2016 01:48 AM https://telecommand.telemetry.microsoft.com
03/12/2016 01:48 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
03/12/2016 01:48 AM https://telecommand.telemetry.microsoft.com
03/10/2016 11:57 PM https://telecommand.telemetry.microsoft.com
03/10/2016 11:57 PM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
03/10/2016 11:57 PM https://telecommand.telemetry.microsoft.com
03/10/2016 12:51 AM https://telecommand.telemetry.microsoft.com
03/10/2016 12:51 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
03/10/2016 12:51 AM https://telecommand.telemetry.microsoft.com
03/09/2016 12:40 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
03/09/2016 12:40 AM https://telecommand.telemetry.microsoft.com
03/09/2016 12:40 AM https://telecommand.telemetry.microsoft.com
03/07/2016 11:44 PM https://telecommand.telemetry.microsoft.com
03/07/2016 11:44 PM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
03/07/2016 11:44 PM https://telecommand.telemetry.microsoft.com
03/06/2016 11:36 PM https://telecommand.telemetry.microsoft.com
03/06/2016 11:36 PM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
03/06/2016 11:36 PM https://telecommand.telemetry.microsoft.com
03/06/2016 01:13 AM https://telecommand.telemetry.microsoft.com
03/06/2016 01:13 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
03/06/2016 01:13 AM https://telecommand.telemetry.microsoft.com
03/05/2016 01:08 AM https://telecommand.telemetry.microsoft.com
03/05/2016 01:08 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
03/05/2016 01:08 AM https://telecommand.telemetry.microsoft.com
03/04/2016 12:30 AM https://telecommand.telemetry.microsoft.com
03/04/2016 12:30 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
03/04/2016 12:30 AM https://telecommand.telemetry.microsoft.com
03/02/2016 11:56 PM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
03/02/2016 11:56 PM https://telecommand.telemetry.microsoft.com
03/02/2016 11:56 PM https://telecommand.telemetry.microsoft.com
03/01/2016 11:55 PM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
03/01/2016 11:55 PM https://telecommand.telemetry.microsoft.com
03/01/2016 11:55 PM https://telecommand.telemetry.microsoft.com
02/29/2016 11:39 PM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
02/29/2016 11:39 PM https://telecommand.telemetry.microsoft.com
02/29/2016 11:39 PM https://telecommand.telemetry.microsoft.com
02/28/2016 11:32 PM https://telecommand.telemetry.microsoft.com
02/28/2016 11:32 PM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
02/28/2016 11:32 PM https://telecommand.telemetry.microsoft.com
02/27/2016 11:54 PM https://telecommand.telemetry.microsoft.com
02/27/2016 11:54 PM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
02/27/2016 11:54 PM https://telecommand.telemetry.microsoft.com
02/26/2016 12:25 AM https://telecommand.telemetry.microsoft.com
02/26/2016 12:24 AM https://telecommand.telemetry.microsoft.com
02/25/2016 12:09 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
02/25/2016 12:09 AM https://telecommand.telemetry.microsoft.com
02/25/2016 12:09 AM https://telecommand.telemetry.microsoft.com
02/24/2016 01:17 AM https://telecommand.telemetry.microsoft.com
02/24/2016 01:17 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
02/24/2016 01:17 AM https://telecommand.telemetry.microsoft.com
02/23/2016 12:25 AM https://telecommand.telemetry.microsoft.com
02/22/2016 12:31 AM https://telecommand.telemetry.microsoft.com
02/22/2016 12:31 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
02/22/2016 12:31 AM https://telecommand.telemetry.microsoft.com
02/21/2016 12:11 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
02/21/2016 12:11 AM https://telecommand.telemetry.microsoft.com
02/21/2016 12:11 AM https://telecommand.telemetry.microsoft.com
02/20/2016 12:04 AM https://telecommand.telemetry.microsoft.com
02/20/2016 12:04 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
02/20/2016 12:04 AM https://telecommand.telemetry.microsoft.com
02/18/2016 11:49 PM https://telecommand.telemetry.microsoft.com
02/18/2016 11:49 PM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
02/18/2016 11:49 PM https://telecommand.telemetry.microsoft.com
02/17/2016 11:30 PM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
02/17/2016 11:30 PM https://telecommand.telemetry.microsoft.com
02/17/2016 11:30 PM https://telecommand.telemetry.microsoft.com
02/17/2016 12:55 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
02/17/2016 12:55 AM https://telecommand.telemetry.microsoft.com
02/17/2016 12:54 AM https://telecommand.telemetry.microsoft.com
02/15/2016 11:59 PM https://telecommand.telemetry.microsoft.com
02/15/2016 11:59 PM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
02/15/2016 11:59 PM https://telecommand.telemetry.microsoft.com
02/14/2016 11:32 PM https://telecommand.telemetry.microsoft.com
02/14/2016 12:09 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
02/14/2016 12:09 AM https://telecommand.telemetry.microsoft.com
02/14/2016 12:09 AM https://telecommand.telemetry.microsoft.com
02/12/2016 11:57 PM https://telecommand.telemetry.microsoft.com
02/12/2016 11:57 PM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
02/12/2016 11:57 PM https://telecommand.telemetry.microsoft.com
02/11/2016 11:58 PM https://telecommand.telemetry.microsoft.com
02/10/2016 11:44 PM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
02/10/2016 11:44 PM https://telecommand.telemetry.microsoft.com
02/10/2016 11:44 PM https://telecommand.telemetry.microsoft.com
02/10/2016 12:19 AM https://telecommand.telemetry.microsoft.com
02/08/2016 11:46 PM https://telecommand.telemetry.microsoft.com
02/08/2016 11:46 PM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
02/08/2016 11:46 PM https://telecommand.telemetry.microsoft.com
02/07/2016 11:37 PM https://telecommand.telemetry.microsoft.com
02/07/2016 11:37 PM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
02/07/2016 11:37 PM https://telecommand.telemetry.microsoft.com
02/07/2016 01:05 AM https://telecommand.telemetry.microsoft.com
02/07/2016 01:05 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
02/07/2016 01:05 AM https://telecommand.telemetry.microsoft.com
02/06/2016 12:50 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
02/06/2016 12:50 AM https://telecommand.telemetry.microsoft.com
02/06/2016 12:50 AM https://telecommand.telemetry.microsoft.com
02/04/2016 11:47 PM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
02/04/2016 11:47 PM https://telecommand.telemetry.microsoft.com
02/04/2016 11:47 PM https://telecommand.telemetry.microsoft.com
02/04/2016 01:22 AM https://telecommand.telemetry.microsoft.com
02/04/2016 01:21 AM https://telecommand.telemetry.microsoft.com
02/03/2016 12:14 AM https://telecommand.telemetry.microsoft.com
02/03/2016 12:14 AM https://telecommand.telemetry.microsoft.com
02/02/2016 01:01 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
02/02/2016 01:01 AM https://telecommand.telemetry.microsoft.com
02/02/2016 01:01 AM https://telecommand.telemetry.microsoft.com
02/01/2016 01:22 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
02/01/2016 01:22 AM https://telecommand.telemetry.microsoft.com
02/01/2016 01:22 AM https://telecommand.telemetry.microsoft.com
01/31/2016 12:16 AM https://telecommand.telemetry.microsoft.com
01/31/2016 12:16 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
01/31/2016 12:16 AM https://telecommand.telemetry.microsoft.com
01/29/2016 11:42 PM https://telecommand.telemetry.microsoft.com
01/29/2016 11:42 PM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
01/29/2016 11:42 PM https://telecommand.telemetry.microsoft.com
01/29/2016 01:22 AM https://telecommand.telemetry.microsoft.com
01/29/2016 01:22 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
01/29/2016 01:22 AM https://telecommand.telemetry.microsoft.com
01/27/2016 11:39 PM https://telecommand.telemetry.microsoft.com
01/27/2016 11:39 PM https://telecommand.telemetry.microsoft.com
01/27/2016 01:11 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
01/27/2016 01:11 AM https://telecommand.telemetry.microsoft.com
01/27/2016 01:11 AM https://telecommand.telemetry.microsoft.com
01/25/2016 11:45 PM https://telecommand.telemetry.microsoft.com
01/25/2016 11:45 PM https://telecommand.telemetry.microsoft.com
01/25/2016 01:20 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
01/25/2016 01:20 AM https://telecommand.telemetry.microsoft.com
01/25/2016 01:20 AM https://telecommand.telemetry.microsoft.com
01/24/2016 01:29 AM https://telecommand.telemetry.microsoft.com
01/24/2016 01:29 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
01/24/2016 01:29 AM https://telecommand.telemetry.microsoft.com
01/23/2016 01:19 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
01/23/2016 01:19 AM https://telecommand.telemetry.microsoft.com
01/23/2016 01:19 AM https://telecommand.telemetry.microsoft.com
01/21/2016 01:14 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
01/21/2016 01:14 AM https://telecommand.telemetry.microsoft.com
01/21/2016 01:14 AM https://telecommand.telemetry.microsoft.com
01/19/2016 11:51 PM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
01/19/2016 11:50 PM https://telecommand.telemetry.microsoft.com
01/19/2016 11:50 PM https://telecommand.telemetry.microsoft.com
01/19/2016 12:23 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
01/19/2016 12:23 AM https://telecommand.telemetry.microsoft.com
01/19/2016 12:23 AM https://telecommand.telemetry.microsoft.com
01/18/2016 12:47 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
01/18/2016 12:47 AM https://telecommand.telemetry.microsoft.com
01/18/2016 12:47 AM https://telecommand.telemetry.microsoft.com
01/17/2016 12:39 AM https://telecommand.telemetry.microsoft.com
01/17/2016 12:39 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
01/17/2016 12:39 AM https://telecommand.telemetry.microsoft.com
01/16/2016 12:58 AM https://telecommand.telemetry.microsoft.com
01/16/2016 12:58 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
01/16/2016 12:58 AM https://telecommand.telemetry.microsoft.com
01/15/2016 12:07 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
01/15/2016 12:07 AM https://telecommand.telemetry.microsoft.com
01/15/2016 12:07 AM https://telecommand.telemetry.microsoft.com
01/14/2016 12:56 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
01/14/2016 12:56 AM https://telecommand.telemetry.microsoft.com
01/14/2016 12:56 AM https://telecommand.telemetry.microsoft.com
01/13/2016 12:11 AM https://telecommand.telemetry.microsoft.com
01/13/2016 12:11 AM https://telecommand.telemetry.microsoft.com
01/12/2016 12:15 AM https://telecommand.telemetry.microsoft.com
01/12/2016 12:15 AM https://telecommand.telemetry.microsoft.com
01/11/2016 12:55 AM https://telecommand.telemetry.microsoft.com
01/11/2016 12:55 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
01/11/2016 12:55 AM https://telecommand.telemetry.microsoft.com
01/09/2016 11:49 PM https://telecommand.telemetry.microsoft.com
01/09/2016 11:49 PM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
01/09/2016 11:49 PM https://telecommand.telemetry.microsoft.com
01/09/2016 01:18 AM https://telecommand.telemetry.microsoft.com
01/09/2016 01:18 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
01/09/2016 01:17 AM https://telecommand.telemetry.microsoft.com
01/04/2016 12:54 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
01/04/2016 12:54 AM https://telecommand.telemetry.microsoft.com
01/04/2016 12:54 AM https://telecommand.telemetry.microsoft.com
01/03/2016 01:03 AM https://telecommand.telemetry.microsoft.com
01/03/2016 01:03 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
01/03/2016 01:03 AM https://telecommand.telemetry.microsoft.com
01/01/2016 11:50 PM https://telecommand.telemetry.microsoft.com
01/01/2016 11:50 PM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
01/01/2016 11:49 PM https://telecommand.telemetry.microsoft.com
01/01/2016 12:49 AM https://telecommand.telemetry.microsoft.com
01/01/2016 12:49 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
01/01/2016 12:49 AM https://telecommand.telemetry.microsoft.com
12/30/2015 11:31 PM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
12/30/2015 11:31 PM https://telecommand.telemetry.microsoft.com
12/30/2015 11:31 PM https://telecommand.telemetry.microsoft.com
12/30/2015 01:04 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
12/30/2015 01:04 AM https://telecommand.telemetry.microsoft.com
12/30/2015 01:04 AM https://telecommand.telemetry.microsoft.com
12/28/2015 11:35 PM https://telecommand.telemetry.microsoft.com
12/28/2015 11:35 PM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
12/28/2015 11:35 PM https://telecommand.telemetry.microsoft.com
12/28/2015 11:35 PM https://telecommand.telemetry.microsoft.com
12/27/2015 11:35 PM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
12/27/2015 11:35 PM https://telecommand.telemetry.microsoft.com
12/27/2015 11:35 PM https://telecommand.telemetry.microsoft.com
12/26/2015 11:46 PM https://telecommand.telemetry.microsoft.com
12/26/2015 11:46 PM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
12/26/2015 11:46 PM https://telecommand.telemetry.microsoft.com
12/26/2015 11:46 PM https://telecommand.telemetry.microsoft.com
12/26/2015 12:19 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
12/26/2015 12:19 AM https://telecommand.telemetry.microsoft.com
12/26/2015 12:19 AM https://telecommand.telemetry.microsoft.com
12/25/2015 12:58 AM https://telecommand.telemetry.microsoft.com
12/25/2015 12:58 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
12/25/2015 12:58 AM https://telecommand.telemetry.microsoft.com
12/24/2015 01:36 AM https://telecommand.telemetry.microsoft.com
12/24/2015 01:36 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
12/24/2015 01:36 AM https://telecommand.telemetry.microsoft.com
12/24/2015 01:06 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
12/24/2015 01:06 AM https://telecommand.telemetry.microsoft.com
12/24/2015 01:06 AM https://telecommand.telemetry.microsoft.com
12/23/2015 12:56 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
12/23/2015 12:56 AM https://telecommand.telemetry.microsoft.com
12/23/2015 12:56 AM https://telecommand.telemetry.microsoft.com
12/22/2015 12:02 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
12/22/2015 12:02 AM https://telecommand.telemetry.microsoft.com
12/22/2015 12:02 AM https://telecommand.telemetry.microsoft.com
12/21/2015 01:03 AM https://telecommand.telemetry.microsoft.com
12/21/2015 01:03 AM https://telecommand.telemetry.microsoft.com
12/20/2015 12:23 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
12/20/2015 12:23 AM https://telecommand.telemetry.microsoft.com
12/20/2015 12:23 AM https://telecommand.telemetry.microsoft.com
12/19/2015 12:58 AM https://telecommand.telemetry.microsoft.com
12/19/2015 12:58 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
12/19/2015 12:58 AM https://telecommand.telemetry.microsoft.com
12/18/2015 12:04 AM https://telecommand.telemetry.microsoft.com
12/18/2015 12:04 AM https://telecommand.telemetry.microsoft.com
12/17/2015 12:23 AM https://telecommand.telemetry.microsoft.com
12/17/2015 12:23 AM https://telecommand.telemetry.microsoft.com
12/15/2015 11:32 PM https://telecommand.telemetry.microsoft.com
12/15/2015 11:32 PM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
12/15/2015 11:32 PM https://telecommand.telemetry.microsoft.com
12/14/2015 11:56 PM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
12/14/2015 11:56 PM https://telecommand.telemetry.microsoft.com
12/14/2015 11:56 PM https://telecommand.telemetry.microsoft.com
12/14/2015 12:10 AM https://telecommand.telemetry.microsoft.com
12/14/2015 12:10 AM https://telecommand.telemetry.microsoft.com
12/13/2015 01:08 AM https://telecommand.telemetry.microsoft.com
12/13/2015 01:08 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
12/13/2015 01:08 AM https://telecommand.telemetry.microsoft.com
12/12/2015 01:29 AM https://telecommand.telemetry.microsoft.com
12/12/2015 01:29 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
12/12/2015 01:29 AM https://telecommand.telemetry.microsoft.com
12/11/2015 01:14 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
12/11/2015 01:14 AM https://telecommand.telemetry.microsoft.com
12/11/2015 01:14 AM https://telecommand.telemetry.microsoft.com
12/10/2015 01:20 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
12/10/2015 01:20 AM https://telecommand.telemetry.microsoft.com
12/10/2015 01:19 AM https://telecommand.telemetry.microsoft.com
12/09/2015 12:29 AM https://telecommand.telemetry.microsoft.com
12/09/2015 12:29 AM https://telecommand.telemetry.microsoft.com
12/08/2015 12:13 AM https://telecommand.telemetry.microsoft.com
12/08/2015 12:13 AM https://telecommand.telemetry.microsoft.com
12/07/2015 12:20 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
12/07/2015 12:20 AM https://telecommand.telemetry.microsoft.com
12/07/2015 12:20 AM https://telecommand.telemetry.microsoft.com
12/06/2015 01:15 AM https://telecommand.telemetry.microsoft.com
12/06/2015 01:15 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
12/06/2015 01:15 AM https://telecommand.telemetry.microsoft.com
12/05/2015 12:07 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
12/05/2015 12:07 AM https://telecommand.telemetry.microsoft.com
12/05/2015 12:07 AM https://telecommand.telemetry.microsoft.com
12/04/2015 12:09 AM https://telecommand.telemetry.microsoft.com
12/04/2015 12:09 AM https://telecommand.telemetry.microsoft.com
12/03/2015 01:18 AM https://telecommand.telemetry.microsoft.com
12/03/2015 01:18 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
12/03/2015 01:18 AM https://telecommand.telemetry.microsoft.com
12/02/2015 12:04 AM https://telecommand.telemetry.microsoft.com
12/02/2015 12:04 AM https://telecommand.telemetry.microsoft.com
11/30/2015 11:49 PM https://telecommand.telemetry.microsoft.com
11/30/2015 11:49 PM https://telecommand.telemetry.microsoft.com
11/29/2015 11:59 PM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
11/29/2015 11:59 PM https://telecommand.telemetry.microsoft.com
11/29/2015 11:58 PM https://telecommand.telemetry.microsoft.com
11/29/2015 01:00 AM https://telecommand.telemetry.microsoft.com
11/29/2015 01:00 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
11/29/2015 01:00 AM https://telecommand.telemetry.microsoft.com
11/28/2015 12:51 AM https://telecommand.telemetry.microsoft.com
11/28/2015 12:51 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
11/28/2015 12:51 AM https://telecommand.telemetry.microsoft.com
11/27/2015 12:16 AM https://telecommand.telemetry.microsoft.com
11/27/2015 12:16 AM https://telecommand.telemetry.microsoft.com
11/26/2015 12:36 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
11/26/2015 12:36 AM https://telecommand.telemetry.microsoft.com
11/26/2015 12:36 AM https://telecommand.telemetry.microsoft.com
11/25/2015 12:42 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
11/25/2015 12:42 AM https://telecommand.telemetry.microsoft.com
11/25/2015 12:42 AM https://telecommand.telemetry.microsoft.com
11/23/2015 11:58 PM https://telecommand.telemetry.microsoft.com
11/23/2015 11:58 PM https://telecommand.telemetry.microsoft.com
11/23/2015 12:54 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
11/23/2015 12:54 AM https://telecommand.telemetry.microsoft.com
11/23/2015 12:54 AM https://telecommand.telemetry.microsoft.com
11/22/2015 12:57 AM https://telecommand.telemetry.microsoft.com
11/22/2015 12:57 AM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
11/22/2015 12:57 AM https://telecommand.telemetry.microsoft.com
11/20/2015 11:39 PM https://telecommand.telemetry.microsoft.com
11/20/2015 11:39 PM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
11/20/2015 11:39 PM https://telecommand.telemetry.microsoft.com
11/19/2015 11:53 PM http://tele.trafficmanager.net/%7B8EF07F6C-75D7-4CB3-845F-95808577C1F2%7D
11/19/2015 11:53 PM https://telecommand.telemetry.microsoft.com
11/19/2015 11:53 PM https://telecommand.telemetry.microsoft.com
11/19/2015 12:21 AM https://telecommand.telemetry.microsoft.com
11/19/2015 12:21 AM https://telecommand.telemetry.microsoft.com1 user thanked author for this post.
-
owdrtn
AskWoody LoungerMay 12, 2017 at 11:25 am #114577Thanks for reporting this !
couple missing info that would help seal the deal:
1] Have you saved some screenshot/cast as proof-of-report ? would seal the deal.
2] Can you double check you actually refer to 2999226, not 3118401 ?
3] Can you confirm this machine was actually running 7x, not Visa or else ? (reason for asking: catalog report 2999226 as being Visa/Server2k8-applicable only, no mention of Win7x.
4] How can you affirm with some “reasonable certitude” those captured packets actually stems from 2999226/3118401, since you mention it was installed 1 month ago ? (if true, I presume you haven’t installed any later KB since 2999226 1 month ago?, or maybe you used some packet isolation technique ? If so, sharing this info would help us sneak off the blur of FUD a little.Again, thanks for the report. Hope you can provide those info and make this report a sound one.
MrBrian
AskWoody_MVPMay 14, 2017 at 8:24 am #115144I recommend to wait on alternative Group A instructions (if there will be any) until Microsoft has consolidated updates into the monthly rollups. I have read in comments from a Microsoft employee that this is supposed to be completed by this summer (USA), which would be sometime in September. I have plenty of things to do in the meantime anyway.
GoneToPlaid
AskWoody LoungerMay 14, 2017 at 11:53 am #115197Thanks for reporting this ! couple missing info that would help seal the deal: 1] Have you saved some screenshot/cast as proof-of-report ? would seal the deal. 2] Can you double check you actually refer to 2999226, not 3118401 ? 3] Can you confirm this machine was actually running 7x, not Visa or else ? (reason for asking: catalog report 2999226 as being Visa/Server2k8-applicable only, no mention of Win7x. 4] How can you affirm with some “reasonable certitude” those captured packets actually stems from 2999226/3118401, since you mention it was installed 1 month ago ? (if true, I presume you haven’t installed any later KB since 2999226 1 month ago?, or maybe you used some packet isolation technique ? If so, sharing this info would help us sneak off the blur of FUD a little. Again, thanks for the report. Hope you can provide those info and make this report a sound one.
Hello,
1. No screenshot. Instead, I simply copied and pasted the log file from my AV program of all IP addresses which were visited.
2. It was KB2999226, not KB3118401.
3. The computer was my main Windows 7 work computer. I occasionally use it for testing, but only after making a full offline backup.
4. After uninstalling KB2999226, and then clearing my AV’s log file and testing again, the telemetry was gone. Uninstalling KB2999226 was fun since it would not uninstall since it also tried to unsuccessfully integrate into my Office 365 installation. The only way I could get KB2999226 to uninstall was to uninstall Office 365, then uninstall KB2999226, and then reinstall Office 365. If you don’t uninstall Office 365 first, and after you think that you have uninstalled KB2999226, then when you launch any program (even old XP programs) you will get this error message:
SystemPropertiesProtection.exe – System Error
The program can’t start because api-ms-crt-runtime-l1-1-0.dll is missing from your computer. Try reinstalling the program to fix the problem.
Following is a Dropbox link for my ZIP file (1.2MB in size) which documents my findings. The size of the ZIP file was a bit too big to upload to the forum.
KB2999226.zip
https://www.dropbox.com/s/f2hnx8tk6e39gj8/KB2999226.zipThe ZIP file only contains text documents and JPEG screen captures. Included are the text EULAs for the Microsoft Visual C++ 2005, 2010, and 2012 Runtime Libraries, and the text EULA for the Microsoft Visual Studio 2015 Add-Ons, Visual Studio Shells And C++ Redistributable which includes Visual C++ 2015 Runtime Libraries. The latter EULA is the EULA which is included in KB2999226. Don’t just look at paragraph 3 in the EULA for KB2999226. You should follow the other links in the EULA which give you hints about just how deep the telemetry gathering really goes.
Everyone thinks that KB2952664 is the really nasty telemetry update to avoid, when in fact the telemetry gathered by KB2999226 is much deeper. For the time being, the equivalent of KB2999226 which is embedded in Office 365 honors your CEIP settings. Yet if you installed KB2999226 via Windows Update, then you silently consented to deep telemetry since the EULA for KB2999226 was not presented to you for your review! The EULA is only presented to you if you manually download and install KB2999226.
Best regards,
–GTP
1 user thanked author for this post.
-
PKCano
ManagerMay 14, 2017 at 12:08 pm #115207Following is a Dropbox link for my ZIP file (1.2MB in size) which documents my findings. The size of the ZIP file was a bit too big to upload to the forum.
It wasn’t the file size that kept you from uploading the .zip file to the forum.
The only files that can be “attached” to the posts are pictures.1 user thanked author for this post.
-
GoneToPlaid
AskWoody LoungerMay 14, 2017 at 12:32 pm #115211I got an erroneous error message when I tried to attach the ZIP file. The error message I got was that the file size was too large. Apparently, I should have received an error message that ZIP files were not allowed as an attachment. Thanks for the “heads up” that the forum doesn’t allow attaching ZIP files. This of course is for good reason.
-
abbodi86
AskWoody_MVPMay 14, 2017 at 3:22 pm #115260There is no EULA associated with KB2999226
Visual C++ Redistributables are not relevant here
KB2999226 is dependency component for Office 2016 (or Office 365)
are you sure you are not mixing Office telemetry with KB2999226?
if you want to have conclusive results, just install KB2999226 without Office
then see you IP activitiesKB2999226 in Windows Update = KB2999226 included with Office 2016
1 user thanked author for this post.
-
GoneToPlaid
AskWoody LoungerMay 16, 2017 at 7:55 am #115663Thank you for the info. This weekend, I will test by following the procedures you outlined. Now I am wondering if the EULA which I saw was shown to me when KB2999226 tried to integrate into my Office 365 installation? I vaguely recall that when I installed this KB back in 2016, I might have had Office 365 configured to not check for any updates.
MrBrian
AskWoody_MVPMay 16, 2017 at 9:29 am #115688Would anyone be interested in the creation of a new topic called “Windows 7 or 8.1 updates or other code that have evidence of privacy issues”? To prevent the new topic from becoming unwieldy, each alleged issue could have its own thread, with the topic “Windows 7 or 8.1 updates or other code that have evidence of privacy issues” having a link to each alleged issue.
MrBrian
AskWoody_MVP-
Bill C.
AskWoody PlusMay 16, 2017 at 10:24 am #115707I have found over the past months (after the GWX fiasco) that even with ‘no’ checked it will still transmit some data. I have disabled CEIP in Task Manager. It has not transmitted since and I have not detected any adverse effect.
I also remember reading here that other MS software at install can enable it, but I believe it actually asks. After Windows OS and Office, I have not installed any MS software.
-
MrBrian
AskWoody_MVP -
Bill C.
AskWoody PlusMay 17, 2017 at 11:24 pm #116047Sorry for the delay. I lost internet for half a day (first time in ages), due to a cable modem failure.
In the Task Manager it will say when the task was last run, and whether it was successful. Since disabling, it has not run. Before that even though I had said no, it was showing a successful run. Whether it actually transmitted data, that I could not tell. I was going by the successful run aspect. Unfortunately I never made a screenshot before disabling CEIP.
I check it every so often and it has not re-started since I disabled it in Task Manager.
-
-
Rydan
AskWoody LoungerMay 26, 2017 at 9:35 am #118228Pointer: some things I didn’t quite see in this topic:
Be advised that some Security Updates are Superseded by the Security Monthly (as such have the Supersedence tag in SUS etc.) and some are not Superseded (=still needed) by the Security Only updates. This is also true for the .NET updates.
Also some functional updates are Superseded by the Security Monthly updates that you still might like to have next to your Security Only updates, such as Time zone updates.
Some KB articles have errors, conflict with detection rules or just not mention superseding updates. Having a cumulative WSUS database helps a lot.
Recently I saw some mentioning of WSUS Offline problems with update referral due to the new numbering (.NET). I’ve not used it for a while, but in the past I sometimes got updates from WSUS Offline I did not want, because I was of a different opinion than WSUS Offline concerning undesirable updates (check first).MrBrian
AskWoody_MVPOctober 4, 2017 at 2:51 am #135157“Be advised that some Security Updates are Superseded by the Security Monthly (as such have the Supersedence tag in SUS etc.) and some are not Superseded (=still needed) by the Security Only updates. This is also true for the .NET updates.
Also some functional updates are Superseded by the Security Monthly updates that you still might like to have next to your Security Only updates, such as Time zone updates.”Rydan in post #118228 is correct.
Two issues have been identified that can cause a Group B user to not see applicable updates in Windows Update that should be installed:
1. The issue that Rydan identified above. An anonymous poster recently noticed the results of this issue at https://www.askwoody.com/forums/topic/missing-security-updates-as-from-ms16-027-in-group-b-fresh-installation/. I verified the poster’s claims. There might exist similar instances of this issue for Group A, but none have been identified yet.
2. There are updates that Microsoft has declared must not be installed in a batch with other updates. These exclusive updates apparently do not appear in Windows Update unless there are no Important updates listed. This issue applies to Group A as well.
The general solution to these two issues is that all updates in Windows Update must either be installed or hidden, which may require multiple update checks to complete. Topic “Unwanted Win updates must be hidden to ensure that you see all available updates” for this issue was created a few days ago but was lost due to site issues. It will be recreated again sometime soon hopefully.
Viewing 72 reply threads -

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Hacktool:Win32/Winring0
by
Marvel Wars
8 minutes ago -
Microsoft Defender as Primary Security Question
by
blueboy714
1 hour, 14 minutes ago -
USB printers might print random text with the January 2025 preview update
by
Alex5723
2 hours, 1 minute ago -
Google’s 10-year-old Chromecast is busted, but a fix is coming
by
Alex5723
11 hours, 37 minutes ago -
Expand the taskbar?
by
CWBillow
11 hours, 28 minutes ago -
Gregory Forrest “Woody” Leonhard (1951-2025)
by
Susan Bradley
21 minutes ago -
March 2025 updates are out
by
Susan Bradley
1 hour, 34 minutes ago -
Windows 11 Insider Preview build 26120.3380 released to DEV and BETA
by
joep517
1 day, 5 hours ago -
Update Firefox to prevent add-ons issues from root certificate expiration
by
Alex5723
1 day, 12 hours ago -
Latest Firefox requires Password on start up
by
Gordski
1 day, 6 hours ago -
Resolved : AutoCAD 2022 might not open after updating to 24H2
by
Alex5723
2 days, 1 hour ago -
Missing api-ms-win-core-libraryloader-11-2-1.dll
by
IreneLinda
23 hours, 59 minutes ago -
How Much Daylight have YOU Saved?
by
Nibbled To Death By Ducks
1 day, 2 hours ago -
A brief history of Windows Settings
by
Simon Bisson
20 hours, 34 minutes ago -
Thunderbolt is not just for monitors
by
Ben Myers
19 hours, 11 minutes ago -
Password Generators — Your first line of defense
by
Deanna McElveen
1 day ago -
AskWoody at the computer museum
by
Will Fastie
28 minutes ago -
Planning for the unexpected
by
Susan Bradley
1 day, 1 hour ago -
Which printer type is the better one to buy?
by
Bob99
2 days, 2 hours ago -
Upgrading the web server
by
Susan Bradley
2 days, 1 hour ago -
New Windows 11 24H2 Setup – Initial Win Update prevention settings?
by
Tex265
2 days, 20 hours ago -
Creating a Google account
by
DavidofIN
2 days, 19 hours ago -
Undocumented “backdoor” found in Bluetooth chip used by a billion devices
by
Alex5723
3 days, 1 hour ago -
Microsoft Considering AI Models to Replace OpenAI’s in Copilot
by
Alex5723
3 days, 12 hours ago -
AI *emergent misalignment*
by
Alex5723
3 days, 13 hours ago -
Windows 11 Disk Encryption/ Bitlocker/ Recovery Key
by
Tex265
1 day, 21 hours ago -
Trouble signing out and restarting
by
Tech Hiker
21 hours, 1 minute ago -
Windows 7 MSE Manual Updating
by
Microfix
17 hours, 49 minutes ago -
Problem running LMC 22 flash drive
by
Charlie
2 days, 21 hours ago -
Outlook Email Problem
by
Lil88reb
2 days, 21 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.


