I’m just starting to digest all of it, but Martin Brinkmann has his usual all-encompassing overview on the ghacks site. Top points, from my point of v
[See the full post at: April 2018 Patch Tuesday is here — and it’s a biggie]

|
Patch reliability is unclear. Unless you have an immediate, pressing need to install a specific patch, don't do it. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
-
April 2018 Patch Tuesday is here — and it’s a biggie
Home » Forums » Newsletter and Homepage topics » April 2018 Patch Tuesday is here — and it’s a biggie
- This topic has 128 replies, 50 voices, and was last updated 6 years, 10 months ago.
AuthorTopicViewing 46 reply threadsAuthorReplies-
PKCano
Manager -
MikeFromMarkham
AskWoody LoungerApril 10, 2018 at 1:27 pm #183406 -
PKCano
Manager -
Seff
AskWoody PlusApril 10, 2018 at 1:57 pm #183411Indeed, but what we need to know in due course is whether the April rollup includes that fix for Total Meltdown or simply maintains the same vulnerability as the January, February and March rollups.
I’ve been waiting to see what happens on this point, but if there is still a vulnerability in the April rollup then I do intend to install the fix through KB4100480 and, once approved, I’ll install the April rollup itself. Is it necessary in those circumstances also to install KB4099950? I’ve rather lost track of what that particular update is for!
1 user thanked author for this post.
-
PKCano
Manager -
Seff
AskWoody PlusApril 10, 2018 at 2:34 pm #183419Thanks PK, but do I assume that the fixed IP problem derives from the March rollup, so if that hasn’t been installed, whether it is still needed presumably depends on the situation with the April rollup? Given that all updates come with significant risks these days, it’s important that we only install those that are absolutely necessary given what else we are installing. Installing updates that provide fixes for problems we don’t have because we didn’t install the updates that created them is likely to cause its own problems!
1 user thanked author for this post.
-
Pim
AskWoody PlusApril 10, 2018 at 2:48 pm #183427I have not installed the March cumulative update, the last updates I installed are the February cumulative update plus KB4100480. Today I get offered both KB4099950 and the April cumulative update. I therefore assume that KB4099950 has not been included in the April cumulative update.
-
OldBiddy
AskWoody LoungerApril 11, 2018 at 2:49 pm #183666@PKCano, I think in one of your previous posts you mentioned following this order for installing March patches:
Follow this order
1. kb4099950
2. kb4088878
3. kb4100480
4. kb4096040I’ve installed the middle two patches before seeing your post. Is it too late to install the first and last patches in your order? I only have one laptop not connected to a network. Thanks for your help!
-
PKCano
Manager -
OldBiddy
AskWoody Lounger -
PKCano
ManagerApril 11, 2018 at 5:43 pm #183706 -
walker
AskWoody LoungerApril 12, 2018 at 9:22 am #184106@PKCano: Is the KB4088878 update, “safe”, if it is not checked? It seems that there could be serious problems for some computers. It is definitely unchecked which in the past we’ve always been told to “not change”. Thank you for any guidance you may be able to provide on this one. Your help is most sincerely appreciated, as always. 🙂
-
PKCano
Manager
-
-
-
-
MikeFromMarkham
AskWoody Lounger -
PKCano
Manager
-
-
-
GoneToPlaid
AskWoody Lounger
abbodi86
AskWoody_MVP-
Seff
AskWoody Plus -
abbodi86
AskWoody_MVPApril 10, 2018 at 9:53 pm #183527Not really, i analyze each update components
see @MrBrian reply
https://www.askwoody.com/forums/topic/april-2018-patch-tuesday-is-here-and-its-a-biggie/#post-183508
Pim
AskWoody Pluslaidbacktokyo
AskWoody LoungerApril 10, 2018 at 2:44 pm #183425As usual I gave an immediate try install to KB4093118 (Monthly Rollup) for win7.
At the first glance it looks same as all previous massive patches of 2018 – at least so far I see both chaotic dwm.exe errors in log and leftovers in taskbar of already closed windows as reported by me repeatedly like here:
https://www.askwoody.com/2018/patch-lady-new-update-for-windows-7-kb-4100480/#post-179435
Then a bit of odd stuff:
1. It seems m$ gets nuts with IE11 version numbering – now it’s version of the integrated update is again v11.0.56:
https://support.microsoft.com/en-us/help/4092946/cumulative-security-update-for-internet-explorer
which is literally same as it was of KB4089187 included into KB4088875 March rollup.
KB4096040 included into KB4088881 March rollup preview was of v11.0.57
2. There is a sense to install KB4099950 – 29KB registry patch concerning this key HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\PCI marked as Recommended before KB4093118, otherwise it’s remaining uninstall in offering list.
I’ll duly prompt further testing results.
Rgds,
-
abbodi86
AskWoody_MVPApril 10, 2018 at 3:09 pm #183436Another interesting thing about KB4093118 is that they removed IE 8 components (which were added in January 2018 to address Spectre mess)
they also removed inetcomm.dll (Internet Messaging API)
notice the drop in rollup size in catalog
-
bifido
AskWoody Lounger
-
laidbacktokyo
AskWoody LoungerApril 11, 2018 at 4:20 pm #183687UPDATE:
A bit of extra testing report:
Well, while I definitely don’t wanna loose laptop performance with older hardware as Intel T9500 CPUID 10676, and both mentioned issues now mainly occurred/noticed with Meltdown protection disabled [when Spectre protection isn’t yet(?) provided by CPU firmware] thru InSpectre utility by adding 2 win7 default registry keys:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management\ DWORD ‘FeatureSettingsOverride’ value = 2
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management\ DWORD ‘FeatureSettingsOverrideMask’ value = 3
and changing the 1st key value from its default 2 to 3 as below doesn’t return any clear effect:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management\ DWORD ‘FeatureSettingsOverride’ value = 3
I’ve anyway changed above key value to 3 and then done a clean install of same version (not latest but assumed best) of nVidia driver but this time including its integrated PhysX performance component. And it seems resolved both issues.
Anyhow, I’ll duly prompt here further issues if any.
Meanwhile I assume this April rollup as more or less acceptable for a permanent deployment.
Rgds,
-
laidbacktokyo
AskWoody LoungerApril 12, 2018 at 12:28 am #183747UPDATE 2:
Assuming the above combination of settings as a bit fragile I’ve finally:
1. Set the 1st registry key to its default value according to InSpectre utility #7:
KEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management\ DWORD ‘FeatureSettingsOverride’ value = 2
2. Replaced a nVidia driver to even older one but released by m$ itself.
END
1 user thanked author for this post.
-
laidbacktokyo
AskWoody LoungerApril 12, 2018 at 4:39 pm #184232UPDATE 3:
Sorry, my optimistic guess regarding April full rollup KB4093118 was wrong.
Same 2 issues again. Mainly – The Desktop Window Manager has encountered a fatal error (0x8898009b). Chaotic. A culprit remains unclear but when rollup removed both issues vanished immediately.
Final present win7x64 config:
1. KB4093118 removed & put to hidden list so win7 is now back to a massive patching status of Dec2017 full rollup KB4054518.
2. KB4099950 29kb registry patch remains installed w/o any network issues both before its installation and afterwards.
3. IE11 patch KB4092946 v11.0.9600.18977 build 11.0.56 installed as standalone and performs normally except that odd stuff in its build numbering when previous IE11 patch KB4096040 of late March was v11.0.9600.18954 build 11.0.57!
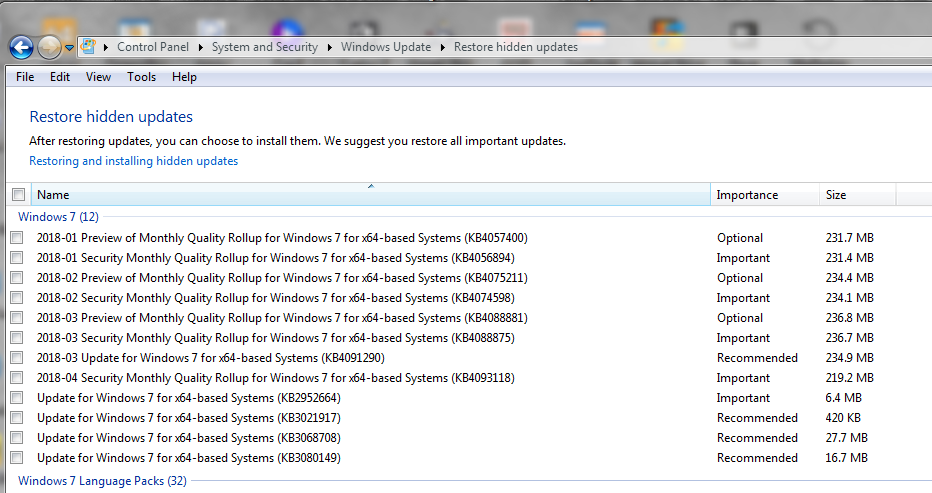
4. Current list of hidden KBs:
Awaiting for April rollup preview fun. 🙂
END
-
laidbacktokyo
AskWoody LoungerApril 17, 2018 at 12:43 pm #185304UPDATE #4 – FINAL & FUNNY:
Meanwhile I’ve installed April 10, 2018—KB4093108 (Security-only update) only for testing purpose aimed to narrow search for a culprit of both issues occurred if any of 2018 massive patches installed and got a funny result – there is no any sign of both issues with any value of win7 registry key of enabling/disabling Spectre and/or Meltdown protection as 0-1-2-3.
Thus these issues aren’t related to security but to some of win7 new features introduced in 2018 massive patches.
END
-
-
abbodi86
AskWoody_MVP-
ch100
AskWoody_MVP -
abbodi86
AskWoody_MVPApril 13, 2018 at 10:03 am #184420😀
https://marc.info/?l=patchmanagement&m=151608432804215&w=2
you only need the first messege (up until — line), then click on the top [next in thread] to continuei think it’s @Kirsty that did the analysis
Anonymous
InactiveApril 10, 2018 at 2:59 pm #183431-
PKCano
Manager -
Individualist
AskWoody LoungerApril 10, 2018 at 3:39 pm #183448Hello…Don’t know if this is any help, but I pretty much did the same routine as you yesterday, it went well..the one thing I did differently however was to not install KB4099467, otherwise we installed the same items. My reboot was extremely fast and uneventful and my machine has performed without issue since…having done one extra test reboot just for good measure, again no issue. I will add that I usually run my computer pretty much 24/7…and only do a restart every 30 days or so, usually during updates, and a total shutdown and rest for cleaning and reboot every 3 months as a rule, unless I am seeing excessive memory usage, which is rare. I am a bit nervous now given your experience, but I wonder about the KB4099467 being the only differentiation in our installs.(I replied to you yesterday about adding someone’s username to your replies by using @ then name but it came up as anonymous!)
Dell Otiplex 780 Windows 7×64 SP1 Group A
A ship in harbor is safe, but that is not what ships are built for. --John Augustus Shedd
-
Anonymous
InactiveApril 10, 2018 at 4:01 pm #183457@Individualist
Hi — that drove me crazy yesterday because when I read the post I was sure it was you and then I saw Anonymous — too funny! I’m glad you are happily patched. I believe that MrBrian also shared that he also did not install KB4099467 and he did not get the BSOD. It was intermittent with me.
I log out of my desktop computer every time I leave it so I log out many times a day — which may be why I get the BSOD sometimes. Maybe others leave the computer on all day and only log off once at night. Even though this is a home computer I am very security conscious so that I have to log on every time I come to use it — many times a day. I’m just guessing at the cause of the BSOD — I’m not a computer expert “I just play one on TV”. 🙂3 users thanked author for this post.
-
EP
AskWoody_MVP -
Anonymous
Inactive
-
-
-
anonymous
GuestApril 10, 2018 at 3:41 pm #183443What confuses me still is why Microsoft continues to patch Office 2007 when documented end-of-life occurred in October 2017. From Microsoft:
“Office 2007 has reached the end of its support lifecycle, meaning there are no new security updates, non-security updates, free or paid assisted support options, or online technical content updates. Customers who are using Office 2007 products and services should move to Office 365 or upgrade to supported versions of Office products and services, such as Office 2016.”
Mind you, I’m not complaining, I’m just confused. Why does Office 2007 get patches while Vista, XP, 2003 do not? I just don’t understand.
Anyway, I guess we’ll sit back and watch the message boards for any reported problems. Like Magneto quipped in X-Men (The Last Stand), “In chess, the pawns go first.”
I’m not surprised that Microsoft postponed 1803. The update servers will be hammered this week. Pulling down gigabytes 1803 won’t help. Better to do a staggered release.
Of course, the possibility exists of a show-stopper bug, but that’s par for the course.
-
abbodi86
AskWoody_MVPApril 10, 2018 at 4:40 pm #183469 -
ch100
AskWoody_MVPApril 12, 2018 at 3:33 pm #184197Windows 2003 is a cash cow for Microsoft. This OS still gets updates, but it all comes at a price for the large enterprises not migrated yet. Probably not so critical as they sound, but useful nevertheless, especially that many of those enterprises paying for support are potentially prime targets for malware and attacks.
There may still be vulnerabilities in all versions of Office which require patching for the sanity of the Internet very much like the out-of-band XP patch of few months ago and this takes precedence over short term financial gains like in the case of Windows 2003.1 user thanked author for this post.
BobT
AskWoody Lounger-
PKCano
ManagerApril 10, 2018 at 4:00 pm #183456You need to install KB 4099950 from Windows Update. You should also read this topic about the March patches – some have to be installed in a certain order.
You do not need to uninstall KB 4100480
1 user thanked author for this post.
anonymous
Guestanonymous
GuestApril 10, 2018 at 4:49 pm #183470I have not installed KB4099950 because it came out after the March rollup got installed. KB4099950 was sent by windows update and it is still unchecked, on my W7 x64.
– Is that why it is unchecked, because it is a prerequisite to the March update, which I have already installed?If I leave the March rollup as is and install KB4099950 before the April monthly rollup, will the script make the changes it is designed to make, or do nothing?
As I have had no problems with any of the bugs in the March rollup, including the network problems, I am thinking I can hide KB4099950. However, I am unsure if there will be a price to pay down the road if I do this.
pulsar
AskWoody LoungerApril 10, 2018 at 5:42 pm #183478Win 7, 64 bit non techie Group A here. Last week I installed KB41000480 and KB4099950. The March roll-up was never offered and I would not have installed it even if it had been. I’ve seen some discussion about KB4099467, which I have never been offered either. Today, I was offered the April roll-up (which I will hold off on until Woody gives the ok) but not offered KB4099467 again. Is KB4099467 something that I should be installing? Thanks for all the help and guidance!
1 user thanked author for this post.
-
PKCano
Manager -
Anonymous
InactiveApril 10, 2018 at 6:40 pm #183491@pulsar
KB4099467 I believe is only available from the Windows Update Catalog and is supposed to fix the BSOD problem. However, there is a tricky installation for it: First install KB99950. Then install KB4088875 but you must “reboot later” by clicking “cancel” before the computer reboots. Then you go to the Update Catalog and download KB4099467 and then reboot. I don’t believe I was able to perform this correctly. -
Anonymous
InactiveApril 10, 2018 at 6:46 pm #183493@pulsar
My previous answer only applied to the March rollup (I’m Group A). From what I’m reading KB4099467 will be included in the April rollup and we will not have to do the intricate installation that I was referring to.
Please correct me if I am wrong fellow sufferers. 🙂1 user thanked author for this post.
EP
AskWoody_MVPApril 10, 2018 at 6:22 pm #183480Ahhh, the KB2952664 update for Win7 SP1 and KB2976978 update for Win8.1 have a new date (4/8/2018) listed on MS Update Catalog.
WU is offering these updates again today thru recent WU scans on my Win7/8.1 machines – rated as Important but not checked.by the way, I went ahead and installed the KB4093118 update on my family’s Dell Inspiron 620 computer running Win7 and have found no problems so far. seems like MS did make amends with this April 2018 update.
Others should wait for either woody or susan to give the okay for the april 2018 updates if there are unforseen problems.
-
alpha128
AskWoody PlusApril 11, 2018 at 6:47 am #183565Ahhh, the KB2952664 update for Win7 SP1 and KB2976978 update for Win8.1 have a new date (4/8/2018) listed on MS Update Catalog. WU is offering these updates again today thru recent WU scans on my Win7/8.1 machines – rated as Important but not checked.
Same here. In addition to the April Rollup for Windows 7 (KB4093118), Windows Update once again offered me infamous snooping patch (KB2952664). I hid that immediately.

T
AskWoody LoungerApril 10, 2018 at 7:33 pm #183503Are microsoft still peddling the lie that win 10 is the most secure windows? From where i’m sitting it looks like another patching month has arrived with the most number of vulnerabilities going to the aforementioned.
At the moment i’m more inclined to never install march security-only due to the many unknowns. It was never even offered to me in update and you had to go through a labyrinthine effort just to get it to show up so no, i might leave well alone and accept the risks.
2 users thanked author for this post.
-
Noel Carboni
AskWoody_MVPApril 10, 2018 at 11:31 pm #183534The phrase “most secure” is meaningless and unprovable, not even accounting for there being no measure of benefit tied to it. Thinking in the extreme, a computer that’s powered-off is really quite secure, you have to admit – but it is also useless.
I’ve noticed that Microsoft occasionally makes statements about data it has received from its own telemetry, selecting months where there have been fewer reports of certain malware found on Windows 10 than some other versions and claiming a “win” for Windows 10, even though the tables turn in subsequent months. I’m not sure what statistics they could even be using to determine a “security” level… Are there exploits or infections that get by Windows Defender but which somehow get reported? Wouldn’t a system that successfully detects and blocks malware – and reports that in – actually be considered secure? Do they count systems that were almost infected? For me it all starts to fail a “sniff test”.
The odor of marketing is apparent in statements like “Windows 10 is the most secure Windows ever”. That one’s right up there in my book with “Save up to 50% – and more!”
-Noel
-
anonymous
GuestApril 12, 2018 at 4:43 pm #184226Like so many others, I’m done with Windows 10 now. I couldn’t stand the forced build upgrades and the compatibility issues they brought with them, so I managed to get hold of a copy of LTSB from work. I used it for a couple of months and it was tolerable. Until in the last few days… it forced on a Synaptics touchpad driver that for some reason causes my left touchpad button to double-click instead of single click when only briefly pressed. (HP’s own Synaptics driver works fine.) This was despite the fact I had the GPO enabled to exclude drivers from Windows Update and also had the driver hidden via wushowhide.diagcab. In fact, I wasn’t even able to hide the update again yesterday because it was already hidden previously.
So, this evening, it managed to get the driver on. And I promptly restored a Windows 8.1 backup image I had. That’s it for me. I’ve used every version of Windows since 3.00a and even Vista didn’t infuriate me as much as 10 does. It makes me sad to think that this is most likely the end of the line for me with Windows.
1 user thanked author for this post.
MrBrian
AskWoody_MVPApril 10, 2018 at 7:40 pm #183508Some notes about the Windows 7 April 2018 Windows updates:
1. KB4093118 and KB4093108 contain v6.1.7601.24094 of files ntoskrnl.exe and ntkrnlpa.exe, which is newer than the v6.1.7601.24093 files ntoskrnl.exe and ntkrnlpa.exe contained in the Total Meltdown fix KB4100480. (My analysis of KB4100480.) Thus, KB4093118 and KB4093108 very likely fix Total Meltdown without needing to install KB4100480.
2. KB4093118 and KB4093108 contain v6.1.7601.24093 of file win32k.sys, which is newer than the v6.1.7601.24061 file win32k.sys contained in KB4099467. (abbodi86’s analysis of KB4099467.) Thus, KB4093118 and KB4093108 very likely fix the same issue fixed by KB4099467 without needing to install KB4099467.
StruldBrug
AskWoody LoungerApril 10, 2018 at 9:58 pm #183528W7 x64 Home Group B
Decided to take the point this time for April. I turned off scr and put VShield into install mode, but left NVT OSA and MSE running. I ran OS KB4093108 1st and IE KB4092946 next. Each asked for restart, which I did. Also checked event viewer, services, and devices after both restarts … no problems. So, mission complete. I just made an image two days ago and thought it was my turn to test. Most should wait for a good Defcon though. I might just be lucky.gkarasik
AskWoody Plus-
Microfix
AskWoody MVPApril 11, 2018 at 3:03 am #183541@gkarasik: Thank you for the heads-up.
Hopefully someone with 2012 R2 Server will be along soon to assist you or confirm the issue.
Description of patch:
KB4093114 — Windows 8.1 and Windows Server 2012 R2 April 2018
Lifted blocking of updates via Windows Update and WSUS if “antivirus compatibility” Registry key was not set.
Security updates to Internet Explorer
Microsoft scripting engine
Microsoft graphics component
Windows Server
Windows kernel
Windows datacenter networking
Windows Hyper-V
Windows virtualization and kernel
Windows app platform and frameworks.
ActiveX printing issue in IE.
SVG rendering issue causing high load issue in IE.
Custom controls identifying issue in IE.kb4093114 (April Rollup) is failing to install on 2012 R2 Server
If debian is good enough for NASA...
anonymous
GuestApril 11, 2018 at 4:16 am #183543Asking for some confirmation here.
Win 7 32-bit (so not affected by Total Meltdown, I gather), Group B, only installed March IE patch, not the security-only one or any of the others yet. But with critical RCEs in the April ones, I will install them quickly, and will do March too while at it. So, is it right to do it like so, including the order:
4099950 (static IP fix, and do have that)
4088878 (March security-only)
4099467 (logoff BSOD fix)
4092946 (April IE patch)
4093108 (April security-only)Or would either or both of 4099950 and 4099467 no longer need to be installed, as the description for 4088878 says 4099950 will be automatically installed along with it and MrBrian’s post above would indicate that 4093108 includes 4099467? But in that case, even if not necessary, would it be harmful to install them anyway, and just reboot after? Because it seems like it’d be safer to just install all instead of rely on the possibility that some are included in others, but not sure whether that won’t cause issues, if the same file will be updated by multiple updates installed at once. (And I don’t want to risk BSODs, and with one fixed by 4099467 (and possibly also 4093108) and another by 4093108, don’t want to reboot after 4088878 without having those installed as well.)
— Cavalary
-
PKCano
ManagerApril 11, 2018 at 4:50 am #183547Installing 4099467 (logoff BSOD fix) should not hurt anything, but is probably not necessary as @mrbrian says it is contained in 4093108 (April security-only). However, Windows Update is “smart” enough not to overwrite later versions of files with earlier ones.
I have always installed the IE11 Cumulative Update after the security patch, in your case, last.
-
MrBrian
AskWoody_MVPApril 11, 2018 at 4:58 am #183548That order looks right to me. KB4099467 shouldn’t be needed because you’re installing KB4093108, but be sure to not reboot in between installing KB4088878 and KB4093108. It shouldn’t be harmful to install KB4099467 if you want to though, but be sure to not reboot in between installing KB4088878 and KB4099467.
-
anonymous
Guest
MrBrian
AskWoody_MVPApril 11, 2018 at 5:05 am #183550“The old restriction on compatible antivirus products has been lifted on Win7 and 8.1 — it was already lifted on Win10.”
The restrictions apparently haven’t been lifted for those updates for which they have already been applied to. I just did a test in Windows x64 using Windows Update MiniTool with “Include superseded” ticked. Without the QualityCompat registry item, there were 302 applicable updates. With the QualityCompat registry item, there were 311 applicable updates.
-
abbodi86
AskWoody_MVPApril 11, 2018 at 5:37 am #183555Without QualityCompat the metadata chain is not complete, and i get two rollups 2017-12 and 2018-04
PCIClearStaleCache.exe is now bundled within rollup KB4093118 msu file, and applied automatically by WU
so KB4099950 doesn’t really matter now -
MrBrian
AskWoody_MVPApril 11, 2018 at 5:59 am #183558 -
planet
AskWoody LoungerApril 11, 2018 at 11:15 am #183608I didn’t install 4099950 before 4088878 due to error. I’m not having any network issues. Should I install 4099950 now? Would there be any problems or should I ignore it and continue onwards in Group B without it. Thanks for input.
Group L (Linux Mint 19)
Dual Boot with Win 7
Former
Group B Win 7 64 bit1 user thanked author for this post.
-
-
anonymous
GuestApril 11, 2018 at 5:48 am #183556Not sure what’s wrong with updates for Windows 10 Pro 1709 and Windows 8.1/Server 2012 R2 this month, but it took ages to install and restart (3 times longer than usual). Best of all, after restart, Windows was complaining about Windows activation on some Windows 10 boxes and it took a few more restarts until Windows finally figured that Windows 10 Pro is properly licensed. Wonder what expert approved the updates. Well, Microsoft — the patchwork company..
anonymous
GuestApril 11, 2018 at 6:17 am #183563April Security Only Windows 7 64 bit patches probably cleans up some of the mess from the Meltdown Spectre patches.
Some fixes and kernel reliability improvements sounds like it will be worth installing when Woody gives the green light.
Maybe next month I might consider Group W. How to get off this update treadmill and still feel secure. Damned if I do yet damned if I don’t.
geekdom
AskWoody_MVPApril 11, 2018 at 7:25 am #183567Installation Report
- KB4093118 for Windows 7 installed on two systems.
- Both systems rebooted without error.
On permanent hiatus {with backup and coffee}
offline▸ Win10Pro 2004.19041.572 x64 i3-3220 RAM8GB HDD Firefox83.0b3 WindowsDefender
offline▸ Acer TravelMate P215-52 RAM8GB Win11Pro 22H2.22621.1265 x64 i5-10210U SSD Firefox106.0 MicrosoftDefender
online▸ Win11Pro 22H2.22621.1992 x64 i5-9400 RAM16GB HDD Firefox116.0b3 MicrosoftDefenderMr. Natural
AskWoody Loungeranonymous
Guest-
PKCano
Manager -
anonymous
Guest -
ch100
AskWoody_MVPApril 12, 2018 at 3:47 pm #184204Now it is clear that KB4099950, while included in the 2018-04 Monthly Update, most if not all of the times is missed due to a bug in the bundling mechanism. The better option is to install it manually or from WU when offered, regardless of the order. It fixed issues with 2018-03 Monthly update, it fixes issues with 2018-04 update and will likely fix issues at any time in the future.
It is not a core patch as such and it can be skipped by a large majority of users, but it fixes an issue for the remainder of users, which are more likely to be enterprise users who use virtualisation in specific ways. KB3125574 includes an equivalent update as far as I know and may be a better alternative for those affected by this issue.
https://support.microsoft.com/en-us/help/2550978/0x0000007b-stop-error-after-you-replace-an-identical-iscsi-network-ada
There is much more attention than it is necessary given to this patch.
-
MrBrian
AskWoody_MVPAnonymous
InactiveApril 11, 2018 at 9:11 am #183583I just checked Brian Krebs comments section on KB4093118 reviews. Two people who installed it on Windows 7 Professional computers now can’t access the computer getting message on Startup “user profile not found.” Then underneath it says okay — they click okay and it logs off. Then it comes back and the same thing happens. Anyone else aware of this?
-
anonymous
Guest -
geekdom
AskWoody_MVPApril 11, 2018 at 9:34 am #183595Thanks for the information. Krebs article is here:
https://krebsonsecurity.com/2018/04/adobe-microsoft-push-critical-security-fixes-12/
On permanent hiatus {with backup and coffee}
offline▸ Win10Pro 2004.19041.572 x64 i3-3220 RAM8GB HDD Firefox83.0b3 WindowsDefender
offline▸ Acer TravelMate P215-52 RAM8GB Win11Pro 22H2.22621.1265 x64 i5-10210U SSD Firefox106.0 MicrosoftDefender
online▸ Win11Pro 22H2.22621.1992 x64 i5-9400 RAM16GB HDD Firefox116.0b3 MicrosoftDefender -
samak
AskWoody PlusApril 11, 2018 at 1:40 pm #183654Following this has worked for some people with the user profile error:
https://support.microsoft.com/en-us/help/947215/you-receive-a-the-user-profile-service-failed-the-logon-error-messageWindows 10 Home 22H2, Acer Aspire TC-1660 desktop + LibreOffice, non-techie
anonymous
GuestApril 11, 2018 at 9:37 am #183594Can anyone explain wat 4B and 3B stand for?
~Annemarie
1 user thanked author for this post.
anonymous
GuestApril 11, 2018 at 10:04 am #183600There seems to be a problem with 4099950 and 4093118 when delivered through WU/WSUS: the seesntial .exe is missing, all that gets downloaded is .cabs…
https://www.reddit.com/r/sysadmin/comments/8ba4sm/patch_tuesday_megathread_20180410/dx6n7e8/
Geo
AskWoody PlusTJ
AskWoody PlusApril 11, 2018 at 11:31 am #183610Didn’t install any updates (except KB41000480) since February on my Group B pc (and don’t plan to do so till things get cleared up), but today I noticed something else:
I took a lot longer than usual for my pc to get ready, and as I expected it was because of my AV.
Its log showed that it had prevented an unauthorized connection attempt by conhost.exe, that a new firewall rule had been made for Outgoing UDP Ports 137 and 138 and that firewall rules has been updated Furthermore a new shortlink of the AV had appeared on my desktop (which only occurs when the engine is updated).
So my guess is, that [something] is coordinated between MS and the AV.Can anyone here clarify what’s going on?
(Note to TS: the tag that was showing in the field below my text pane read “2012 April Rollup”. Typo?)
LMDE is my daily driver now. Old friend Win10 keeps spinning in the backgroundNoel Carboni
AskWoody_MVPApril 11, 2018 at 11:57 am #183622A data point:
I’ve just done some fitness testing with the latest patches in my Windows 10 test VM, v1709, which now shows:
Tests included Subversion operations and product builds with Visual Studio (after taking the latest VS 2017 updates)…
So far, everything seems to work just fine.
-Noel
-
Jan K.
AskWoody LoungerApril 11, 2018 at 12:42 pm #183636So far, everything seems to work just fine.
Hmmm… a most unexpected and highly suspecious behaviour…
I would roll back ASAP!
😀
6 users thanked author for this post.
-
Noel Carboni
AskWoody_MVPApril 11, 2018 at 1:03 pm #183646LOL, well put.
In all seriousness, I believe my experience helps prove the efficacy of a “wait to update to version X until version Y’s release is imminent” strategy with regard to Windows 10 – presuming you want to use the Pro edition for real work. Things get remarkably trouble-free 6 months or more after release.
Here’s a bit more detail of what I’m thinking, presuming you want to run Win 10 on your hardware and want to minimize failures:
1. Keep your hardware on the older version of the OS, and evaluate a new Win 10 release in a throwaway virtual machine when it first comes out, presuming you’re curious about new features, etc.
2. Continue running your hardware on the older system, and download the ISO for the latest version when the OS is moved to the “Semi-Annual Channel”. Upgrade a VM directly from the older version using that ISO and begin to seriously evaluate it for fitness for purpose.
3. At around the time the next major version is about to be released to the unpaid beta testing public, upgrade your hardware system from the ISO you downloaded (in step 2, roughly 3 months prior), then update it immediately to the latest patch level.
The only thing we might hope for that would be better than this would be an ISO from Microsoft containing all the latest patches at the time of step 3, but that’s not likely to be provided.
-Noel
-
anonymous
GuestBill C.
AskWoody PlusApril 11, 2018 at 2:16 pm #183662I just checked Brian Krebs comments section on KB4093118 reviews. Two people who installed it on Windows 7 Professional
computers now can’t access the computer getting message on Startup “user profile not found.” Then underneath it says okay — they click okay and it logs off. Then it comes back and the same thing happens. Anyone else aware of this?
I had this on April 6 at 12.34AM EDT. At that point I had NOT installed the March Security only KB4088878, KB4099950, KB4099467, or KB4100480.
Multiple attempts at reboot did not fix it. The only updates had been installed in the past 2 weeks had been the daily MSE definition updates with the last being 1.265.111.0 on April 5 at 5.52PM EDT, and a Steam update after that on April 5.
I discovered the issue whan I returned to the PC after dinner and an errand and found the internet connection was broken. I rebooted the cable modem, but it did not help. I then shut down and again rebooted the cable modem. Upon reboot I discovered the problem.
I was able to get into startup repair mode and it was not successful and initiated a system restore to the previous day. It was successful and I was able to log-in. I checked Malwarebytes Premium and MSE for any detections or quarantines and nothing. I did a full scan with MSE, and initiated Chameleon scans with MWB, all negative. I also checked both the installed updates and the WU history and neither shows any activities except the MSE definitions.
I then did a total backup of all my data.
I checked the Windows logs and found a number of error events: 1502, 1508, 1515, 1511, 1500.
As this is not a diagnostic section, I have not posted verbose descriptions.
jelson
AskWoody LoungerApril 11, 2018 at 2:19 pm #183663April Security Only Windows 7 64 bit patches probably cleans up some of the mess from the Meltdown Spectre patches. Some fixes and kernel reliability improvements sounds like it will be worth installing when Woody gives the green light. Maybe next month I might consider Group W. How to get off this update treadmill and still feel secure. Damned if I do yet damned if I don’t.
AN answer — if you’re really up to it — is to do some serious hardening of your Win 7 system and employ a multi-layered defense. Best place for advice and expertise I’m aware of –other sources appreciated– it is at MalwareTips forums; this post will get you started.
Although Application Whitelisting & a Software Restriction Policy are at the top of the list, there’s one thing even more important: developing a regular routine of system imaging and data backup. I always image my system before & after I install Win Updates… or any program that hooks deeply into the OS.
5 users thanked author for this post.
Sailor
AskWoody Loungeranonymous
GuestApril 11, 2018 at 4:43 pm #183694@YP
Peacelady & Bill C
I had the “user profile not found.” problem last week. It happened after MSE (Microsoft Security E) installed the “new malware engine” fix. I was not able to log into my non-administrator account. My 64bit/Pro fixed itself upon restart. I had to fix the profile problem on my 64bit/Premium; but my 32bit was OK.I used the link:
and “Method 1” from the link. Basically, use regedit to locate folder in ProfileList and rename the *bak file. It was my first time and it really was not that bad.
For me, it happened after MSE update because I had not installed any Win7 updates at that time. I am in group B, and I have updated all 3 machines to March updates Monday.
I hope this helps.
1 user thanked author for this post.
KWGuy
AskWoody PlusApril 11, 2018 at 5:03 pm #183700I GIVE UP! Group B, on top of the Total Meltdown saga, is overwhelmingly confusing!
When Woody gives the word, I want to join Group A. Can I do so by “simply” installing the Monthly Quality Rollup and whatever else WU offers? I’m current thru FEB 2018 Security only. NO March updates installed. As of today (4/11) WU is offering me only the FEB Quality Rollup (4074598) along with 4100480 and 2952664.
Advice will be greatly appreciated!
-
The Surfing Pensioner
AskWoody PlusApril 11, 2018 at 7:34 pm #183716I understand the March rollup has been withdrawn because it had so many issues. But beware of the assumption that joining ‘Group A’ will make life easier – see #183616 above. It’s guerilla warfare we’re in now!
2 users thanked author for this post.
-
MrBrian
AskWoody_MVPApril 11, 2018 at 10:53 pm #183740‘When Woody gives the word, I want to join Group A. Can I do so by “simply” installing the Monthly Quality Rollup and whatever else WU offers?’
Yes. For more info see 2000011: Group A, Group B and Group W – what’s the difference?
anonymous
GuestApril 11, 2018 at 9:37 pm #183719I’m seeing something curious on my Win7 SP1 64-bit Home Premium laptop. I’m Group A and installed only KB4100480 and KB4099950. On Monday the March Rollup KB4088875 was sitting in Windows Update, unchecked. I didn’t install it.
I have WU set to check but let me choose etc. Yesterday, on Patch Tuesday, I was offered the April Rollup, checked, and the March Rollup no longer appeared, as expected. The same was true this morning. I noticed that KB2952664 had reappeared today so I hid it once again. Later I shut down for several hours. This afternoon when I turned the computer back on and Windows Update checked for updates, the April Rollup disappeared and the March Rollup is back again, unchecked.
Of course, I won’t be installing the April Rollup until Defcon 3 anyway, but has this happened to anyone else?
-
Elly
AskWoody MVPApril 11, 2018 at 10:05 pm #183729Since I, too, have a Win7 SP1 64-bit Home Premium laptop, I was curious as to what Windows Update would bring me today. I am a Group B updater, and have Windows Update set to never check, and am updated through December 2017.
Yesterday I was offered, and hid, the April Rollup. Last month, on Patch Tuesday, I had been offered, and hid March’s Rollup. I unhid it, to test for something, a few days later, and it disappeared, never to show up, checked or unchecked again.
So, just now, I unhid the April Rollup, and ran a check for updates. The April Rollup disappeared, and March’s is still missing in action, too. Very curious…

Non-techy Win 10 Pro and Linux Mint experimenter
5 users thanked author for this post.
-
DrBonzo
AskWoody PlusApril 11, 2018 at 10:31 pm #183735@Elly – Same here (Pro instead of Home Premium). Was offered the April Rollup earlier today for about 6 hours, then it disappeared and was replaced by the March Rollup Preview and the February Rollup – which is what I had been offered before the April Rollup showed up!. I’m current in patches through March (in other words through the following: 4100480, 4099950, 4088878, 4099467, and 4096040)
The April Rollup is still in the Update Catalog, but I’m thinking it was, or is in the process of, being pulled?
-
Cybertooth
AskWoody PlusApril 11, 2018 at 11:12 pm #183744I GIVE UP! Group B, on top of the Total Meltdown saga, is overwhelmingly confusing!
When Woody gives the word, I want to join Group A. Can I do so by “simply” installing the Monthly Quality Rollup and whatever else WU offers? I’m current thru FEB 2018 Security only. NO March updates installed. As of today (4/11) WU is offering me only the FEB Quality Rollup (4074598) along with 4100480 and 2952664.
Advice will be greatly appreciated!
No question that it it can be mighty confusing to follow the twists and turns caused by Microsoft’s patching incompetence. But once you sit down to carry out the monthly patching using the guidance given at Woody’s, you may find that it’s not nearly as complicated as it seems. That was my experience of it, anyway.
To keep things simple, and Group B viable for you, you can ignore the ongoing back-and-forth of botched updates, withdrawn patches, and patches to patches, and just wait for Woody to reset the MS-DEFCON level to 3. That will probably be a few days before the May patches are due out.
Since you are updated through February, just follow Woody’s and PKCano’s patching guidance for March 2018. I’m in Group B, and I installed the March patches over the weekend. I was relieved to find that it wasn’t as hard as all the ongoing drama would suggest.
Take your usual precautions before updating (at least set a restore point, and preferably also do a system backup), and then do it. Good luck.
-
SueW
AskWoody PlusApril 12, 2018 at 12:11 pm #184156@KWGuy, I think @Cybertooth offers good advice (providing you’re still willing to stay in Group B). If it will help at all, here are the steps I took to update through March. Like you, I had been updated through February: #182757.
I also do not pay much attention until Woody gives the go-ahead with DEFCON 3 (or higher) for the next month’s updates . . .
Good luck in whatever you decide.
Win 7 SP1 Home Premium 64-bit; Office 2010; Group B (SaS); Former 'Tech Weenie'2 users thanked author for this post.
Frwin
AskWoody PlusApril 12, 2018 at 1:08 am #183748Hi, I’m W7 group A and following Woody’s advice, I didn’t install any of the March updates.
I will wait for Woody’s April instructions, but i already have a question : I’ve always only used WU; if you download a patch from the catalog, is it applied automatically, does it go into WU,… ?
This is my first registered post; I’m from France, so sorry for my poor English. And thanks again for all you do.
-
DrBonzo
AskWoody PlusApril 12, 2018 at 1:27 am #183753@Frwin – When you download the patch, save it on your computer. It will either be a file or a file inside a folder. If it’s a file, just double click and follow the directions – usually all you do is click a few buttons – and it will install. When it’s done you typically will get a window asking if you want to restart now or wait. If no restart is required it will say so. If it’s a folder, open the folder, then double click the file you see and proceed as just described.
Basically it’s just like installing a small program. You’ll get the hang of it during your first try.
PS – Welcome to AskWoody, and, there’s nothing wrong with your English – it’s excellent.
3 users thanked author for this post.
anonymous
GuestApril 12, 2018 at 1:48 am #183754So maybe it’s just me, but on my work computer (Windows 7 Pro, domain joined) and my home computer (Windows 7 Pro, standalone), I checked for updates yesterday and discovered they both had the Windows 7 2018-04 security update available as Important. Today, I checked for updates this afternoon, and both the work computer and my home computer no longer have the update listed. It’s gone. Did it get pulled?
1 user thanked author for this post.
-
DrBonzo
AskWoody PlusApril 12, 2018 at 3:56 am #184021See the three posts starting here:
https://www.askwoody.com/forums/topic/april-2018-patch-tuesday-is-here-and-its-a-biggie/#post-183719
I don’t know if it got pulled or not. Last I checked, it was still offered in the Update Catalog.
1 user thanked author for this post.
-
COBKA
AskWoody Lounger -
anonymous
Guest
dgreen
AskWoody LoungerApril 12, 2018 at 4:56 am #184039Windows 7 64 bit Home Premium Group A
Had done a windows update check yesterday. KB4093118 was offered and checked.
This morning, it is still being offered but now unchecked.After reading here this morning, I’m figuring that MS doesn’t want me to install April’s rollup through WU but rather go to the catalog?
Of course not installing anything until we get the green light here.My computer remains rolled back to December without applying any patches at all.
All previews and rollups not applied, that were hidden, are gone.(ie Jan Feb)KB4091290 and KB4099950 were/are still in my hidden list.
Should I restore them?MrBrian
AskWoody_MVPApril 12, 2018 at 6:13 am #184057Testing on my Windows 7 x64 virtual machine has revealed that KB4093118 has unusual behavior in regards to whether it is listed or not in Windows Update. Using Windows Update MiniTool with “Include superseded” ticked, KB4093118 is listed. Using Windows Update MiniTool with “Include superseded” unticked, KB4093118 is not listed. Usually this would mean that KB4093118 isn’t listed in Windows Update because it’s metadata-superseded by other listed update(s). But the metadata for KB4093118 for Windows 7 x64 shows that there are no updates that metadata-supersede KB4093118 for Windows 7 x64. I suspect that KB4093118 has update attribute supersedenceBehavior=1, just like KB4088875 does.
dgreen
AskWoody LoungerApril 12, 2018 at 6:28 am #184062Testing on my Windows 7 x64 virtual machine has revealed that KB4093118 has unusual behavior in regards to whether it is listed or not in Windows Update. Using Windows Update MiniTool with “Include superseded” ticked, KB4093118 is listed. Using Windows Update MiniTool with “Include superseded” unticked, KB4093118 is not listed. Usually this would mean that KB4093118 isn’t listed in Windows Update because it’s metadata-superseded by other listed update(s). But the metadata for KB4093118 for Windows 7 x64 shows that there are no updates that metadata-supersede KB4093118 for Windows 7 x64. I suspect that KB4093118 has update attribute supersedenceBehavior=1, just like KB4088875 does.
MrBrian:
So do you think because I have those 2 updates hidden KB4091290 and KB4099950 is why KB4093118 is unchecked now? That they may be prerequisite to the April Rollup?1 user thanked author for this post.
-
MrBrian
AskWoody_MVP
crypto3d
AskWoody LoungerApril 12, 2018 at 7:52 am #184083-
jburk07
AskWoody PlusApril 12, 2018 at 9:16 am #184101Yes, I had the same experience. I was offered the April Rollup for one day, starting on Patch Tuesday. On Wednesday afternoon after WU checked for updates, it was gone and the March Rollup was back, unchecked on my Win7 Home Premium SP1 64-bit laptop. I had installed only KB4100480 and KB4099950 before the April Patch Tuesday. I have hidden KB4091290. See MrBrian’s posts at #184057 and 184064.
Linux Mint Cinnamon 21.1
Group A:
Win 10 Pro x64 v22H2 Ivy Bridge, dual boot with Linux
Win l0 Pro x64 v22H2 Haswell, dual boot with Linux
Win7 Pro x64 SP1 Haswell, 0patch Pro, dual boot with Linux,offline
Win7 Home Premium x64 SP1 Ivy Bridge, 0patch Pro,offline -
crypto3d
AskWoody LoungerApril 12, 2018 at 10:53 am #184137I had installed KB4099950 and KB4100480 and have no updates hidden. Was offered 4093118 and then not offered it so I am not sure this has anything to do with having updates hidden, for me anyway. This whole thing is a mess. If I did not need Windows for a few things I would dump it. I already run Linux Mint 18.3 and for 90% of what I do, it’s just fine.
1 user thanked author for this post.
-
rontpxz81
AskWoody Lounger-
geekdom
AskWoody_MVPApril 13, 2018 at 9:01 am #184406Hide KB4093118 and do not install it… yet. The alert is at DEFCON-2 and the patch keeps changing.
On permanent hiatus {with backup and coffee}
offline▸ Win10Pro 2004.19041.572 x64 i3-3220 RAM8GB HDD Firefox83.0b3 WindowsDefender
offline▸ Acer TravelMate P215-52 RAM8GB Win11Pro 22H2.22621.1265 x64 i5-10210U SSD Firefox106.0 MicrosoftDefender
online▸ Win11Pro 22H2.22621.1992 x64 i5-9400 RAM16GB HDD Firefox116.0b3 MicrosoftDefender1 user thanked author for this post.
MrBrian
AskWoody_MVPgkarasik
AskWoody PlusApril 12, 2018 at 8:51 pm #184281@gkarasik: Thank you for the heads-up. Hopefully someone with 2012 R2 Server will be along soon to assist you or confirm the issue. Description of patch: KB4093114 — Windows 8.1 and Windows Server 2012 R2 April 2018 Lifted blocking of updates via Windows Update and WSUS if “antivirus compatibility” Registry key was not set. Security updates to Internet Explorer Microsoft scripting engine Microsoft graphics component Windows Server Windows kernel Windows datacenter networking Windows Hyper-V Windows virtualization and kernel Windows app platform and frameworks. ActiveX printing issue in IE. SVG rendering issue causing high load issue in IE. Custom controls identifying issue in IE. kb4093114 (April Rollup) is failing to install on 2012 R2 Server
Just a followup on the off-chance anyone else ran into this–looking in the log (%windir%\windowsupdate.log), I saw several references to WSUS-related failures and warnings. I didn’t have WSUS installed, so I installed it. The update succeeded.
I won’t attempt to make any sense of Microsoft’s requiring WSUS for the successful install of an update retrieved from WIndows Update because I think we are way past attempting to make any sense of MS 2.0/Nadella.
GaryK
2 users thanked author for this post.
-
Microfix
AskWoody MVP
anonymous
Guest-
PKCano
Manager
radosuaf
AskWoody LoungerApril 13, 2018 at 3:36 pm #184527Office 2007 again? 🙂
 Fractal Design Pop Air * Thermaltake Toughpower GF3 750W * ASUS TUF GAMING B560M-PLUS * Intel Core i9-11900K * 4 x 8 GB G.Skill Aegis DDR4 3600 MHz CL16 * ASRock RX 6800 XT Phantom Gaming 16GB OC * XPG GAMMIX S70 BLADE 1TB * SanDisk Ultra 3D 1TB * Samsung EVO 840 250GB * DVD RW Lite-ON iHAS 124 * Windows 10 Pro 22H2 64-bit Insider * Windows 11 Pro Beta Insider
Fractal Design Pop Air * Thermaltake Toughpower GF3 750W * ASUS TUF GAMING B560M-PLUS * Intel Core i9-11900K * 4 x 8 GB G.Skill Aegis DDR4 3600 MHz CL16 * ASRock RX 6800 XT Phantom Gaming 16GB OC * XPG GAMMIX S70 BLADE 1TB * SanDisk Ultra 3D 1TB * Samsung EVO 840 250GB * DVD RW Lite-ON iHAS 124 * Windows 10 Pro 22H2 64-bit Insider * Windows 11 Pro Beta Insidernickyburnell
AskWoody LoungerViewing 46 reply threads -

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Latest Firefox requires Password on start up
by
Gordski
3 hours, 12 minutes ago -
Resolved : AutoCAD 2022 might not open after updating to 24H2
by
Alex5723
7 hours, 34 minutes ago -
Missing api-ms-win-core-libraryloader-11-2-1.dll
by
IreneLinda
3 hours, 25 minutes ago -
How Much Daylight have YOU Saved?
by
Nibbled To Death By Ducks
4 hours, 8 minutes ago -
A brief history of Windows Settings
by
Simon Bisson
3 hours, 5 minutes ago -
Thunderbolt is not just for monitors
by
Ben Myers
4 hours, 14 minutes ago -
Password Generators — Your first line of defense
by
Deanna McElveen
3 hours, 26 minutes ago -
AskWoody at the computer museum
by
Will Fastie
3 hours, 46 minutes ago -
Planning for the unexpected
by
Susan Bradley
4 hours, 44 minutes ago -
Which printer type is the better one to buy?
by
Bob99
9 hours, 19 minutes ago -
Upgrading the web server
by
Susan Bradley
7 hours, 44 minutes ago -
New Windows 11 24H2 Setup – Initial Win Update prevention settings?
by
Tex265
1 day, 2 hours ago -
Creating a Google account
by
DavidofIN
1 day, 1 hour ago -
Undocumented “backdoor” found in Bluetooth chip used by a billion devices
by
Alex5723
1 day, 7 hours ago -
Microsoft Considering AI Models to Replace OpenAI’s in Copilot
by
Alex5723
1 day, 19 hours ago -
AI *emergent misalignment*
by
Alex5723
1 day, 20 hours ago -
Windows 11 Disk Encryption/ Bitlocker/ Recovery Key
by
Tex265
4 hours, 16 minutes ago -
Trouble signing out and restarting
by
Tech Hiker
20 hours, 52 minutes ago -
Windows 7 MSE Manual Updating
by
Microfix
2 days, 4 hours ago -
Problem running LMC 22 flash drive
by
Charlie
1 day, 3 hours ago -
Outlook Email Problem
by
Lil88reb
1 day, 3 hours ago -
“Microsoft 365 Office All-in-One For Dummies, 3rd Edition FREE
by
Alex5723
1 day, 11 hours ago -
Cant use Office 2013 – Getting error message about Office 2013
by
SAAR
2 days, 4 hours ago -
Nearly 1 million Windows devices targeted in advanced “malvertising” spree
by
bbearren
2 days, 4 hours ago -
Windows 11 Insider Preview build 27808 released to Canary
by
joep517
3 days, 5 hours ago -
Windows 11 Insider Preview Build 22635.5025 (23H2) released to BETA
by
joep517
3 days, 5 hours ago -
Sysprep issue
by
Evit
3 days, 4 hours ago -
Android Security Bulletin—March 2025
by
Alex5723
3 days, 7 hours ago -
23h2: PIN TO START randomly available on right-click
by
dataman1701
3 days, 7 hours ago -
Microsoft Defender
by
agoldhammer
3 days, 12 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.