Newsletter Archives
-
How long has it been since we had a patched 0day that jumped up and bit us?
I’m in the middle of a Tweetstorm – par for the course – but had an interesting response to one of my standard questions. The question goes like this:
Can you tell me one, single, zero day patch that resulted in mainstream malware within, let’s say, a few weeks of release? Just one.
I got a well-researched response. (Most of them are long on accusations and short on research – and make for amusing reading.) Here’s the list:
- WannaCry
- Blaster
- Sasser
To my mind, the best feedback I get is from people who take the time to think through their positions and come up with cogent arguments. That list prompted me to go back and check what really happened. Here’s what I found:
- WannaCry/EternalBlue – patched April 11, 2017. Exploited May 12, 2017. More than a month from patch to exploit – and it was a bad exploit! UPDATE: Andy Greenberg at Wired just published an excellent story about Marcus Hutchins, the guy who corralled WannaCry.
- Blaster – patched May 28, 2003. Exploited August 11, 2003. Almost three months.
- Sasser – patched April 13, 2004. Exploited April 30, 2004. Two weeks to exploit, and that’s scary. But it was 16 years ago.
Have I missed something? Can you find a zero-day exploit that was patched, and then widely exploited within a few weeks of the patch?
-
A fascinating story of MalwareTechBlog
I, like many, responded with more than a bit of incredulity to the news that the WannaCry blocking guy had been arrested. How could the person who single-handedly blocked WannaCry be guilty of the of the crimes attributed to him by the FBI?
Now, I see that it’s not so simple.
Brian Krebs just published an excellent, thorough article about Marcus Hutchins, the WannaCry guy. Well worth a read.
-
WannaCry hits Honda car plant in Japan
A vulnerable machine WILL get infected. Only, if the block is accessible, the worm will exit immediately after infecting it…. and, according to Reuters, they shut the plant down.
The automaker shut production on Monday at its Sayama plant, northwest of Tokyo… Production at other plants operated by the automaker had not been affected, and regular operations had resumed at the Sayama plant on Tuesday, she said.
The story doesn’t sound right. Anybody know what really happened?
Interesting. Vess Bontchev just tweeted an explanation:
They probably just discovered the infection. They were not encrypted, because of the block. The block doesn’t prevent infection… A vulnerable machine WILL get infected. Only, if the block is accessible, the worm will exit immediately after infecting it… A vulnerable machine WILL get infected. Only, if the block is accessible, the worm will exit immediately after infecting it… they were running vulnerable, unpatched. They probably got infected repeatedly during the month. Just nobody noticed until now, because the encryption didn’t trigger, due to the block. A more interesting question is how did they discover the problem? The DoublePulsar backdoor remains, not sure if AV detects it.
There’s another good discussion kicked off by Mikko Hypponen here.
-
The “new” XP patch KB 982316 is a dud, but the new MSRT is for real
Yesterday, I wrote about the mysterious “new” Windows XP patch KB 982316. There’s speculation all over the web that Microsoft is now patching Windows XP again.
Wrong.
@abbodi86 dug in and confirmed:
The digital signature of the downloaded file indicates that it’s still the same old one, “Monday, June 14, 2010”. So this is just a review/renew of the download page for some reason
On the other hand, the new Malicious Software Removal Tool, KB 890830, is very real. An anonymous poster notes that it’s marked “Important” in Windows 7. The Windows Update list says that the program has changed, and the metadata has changed. @ch100 theorizes that it’s a WannaCry detector, which is confirmed in the Technet post Customer Guidance for WannaCrypt attacks:
Update 5/22/2017: Today, we released an update to the Microsoft Malicious Software Removal Tool (MSRT) to detect and remove WannaCrypt malware. For customers that run Windows Update, the tool will detect and remove WannaCrypt and other prevalent malware infections. Customers can also manually download and run the tool by following the guidance here. The MSRT tool runs on all supported Windows machines where automatic updates are enabled, including those that aren’t running other Microsoft security products.
As I’ve said many times over the past week, WannaCrypt only attacks Windows 7. No matter which version of Windows you have, you’d be well advised to run the new MSRT and see if it picks up any vestiges.
(Historical note: Microsoft’s sticking to the “WannaCrypt” name while most of the popular press has moved to “WannaCry.” I switched from WannaCrypt to WannaCry, too, in response to an edit. The worm calls itself “Wana Decrypt0r” with a zero. Malware researchers pick their own names, and there’s no central authority assigning names to specific infections. It’s all about branding, folks — I guess “WannaCry” sounds more compelling.)
-
Windows 10 Anniversary Update OK?
Just got this from reader NP:
I have been following your articles about issues with Windows 10. Would you say at this point, it is safe to update, or should we still wait? I am concerned about not having the latest patches because of the WannyCry ransomware.
It’s safe to upgrade to Windows 10 Anniversary Update, version 1607
It’s too early to upgrade to Windows 10 Creators Update, version 1703
This is the part that gets me. WannaCry only infects Windows 7 machines. Period. (And Server 2008R2, which is basically Windows 7.)
WannaCry does NOT infect Windows XP. I’ve been saying that since my first report a week ago. In spite of what you’ve read, WannaCry does not infect WinXP.
WannaCry does NOT infect Windows 8.1.
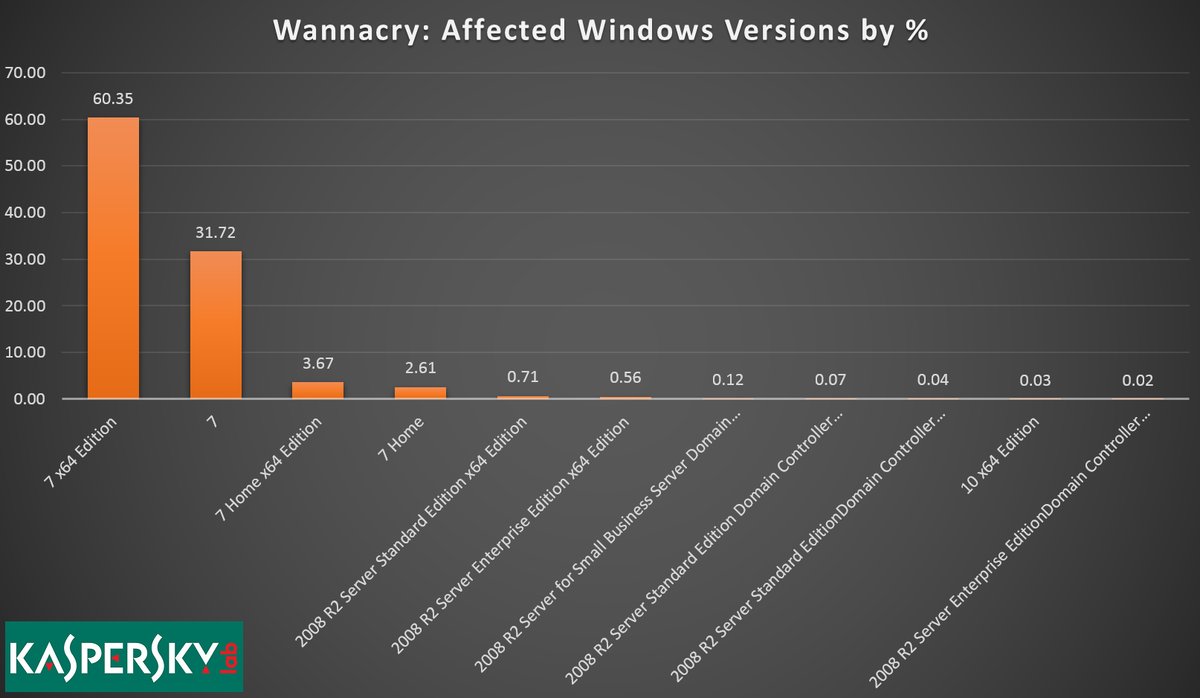
WannaCry does NOT infect Windows 10. Any version. That tiny blip on the Kaspersky chart is no doubt due to mis-reporting, or the possibility that people were running infected WinXP machines in a Virtual Machine on Windows 10. I don’t know of any other way there could be any occurrences.
That said, you need to make sure your Windows computer is fully protected against WannaCry – every version, from XP to Win10. The problem isn’t WannaCry itself. The problem’s all the other malware that’s likely to follow in its footsteps.
-
EternalRocks SMB Worm Uses Seven NSA Hacking Tools
Original posts here:
@MrBrian and @Kirsty just raised the alarm in the Code Red forum….
Researchers have detected a new worm that is spreading via SMB, but unlike the worm component of the WannaCry ransomware, this one is using seven NSA tools instead of two.
The worm’s existence first came to light on Wednesday, after it infected the SMB honeypot of Miroslav Stampar, member of the Croatian Government CERT, and creator of the sqlmap tool used for detecting and exploiting SQL injection flaws.
It’s happening.
-
The original WannaCry does NOT infect Windows XP boxes
I’ve been saying that for a week now – sometimes fighting over it.
I’m not saying the EternalBlue infection method doesn’t work on XP. (Sorry for the double negative.) What I am saying is that no Windows XP boxes were infected, in the wild, by the original WannaCry worm.
I’m also saying that the original WannaCry worm is now a distant memory, with much nastier things to come, and you have to get yourself patched, no matter which version of Windows you’re using.
There’s an interesting debate going on right now about infections on XP boxes that weren’t part of the first wave.
UPDATE: The Scottish National Health Service reports that 1,500 computers came down with WannaCry. Independently, NHS says they still have 6,500 computers running XP. Somehow that’s getting reported in the press that 1,500 XP NHS computers were infected. The announcement from NHS is apparently correct. The poorly-spun media reports are clearly wrong.
ANOTHER UPDATE: Catalin Cimpanu at BleepingComputer comes to the conclusion that we’ve known all along — WannaCry only infects Windows 7 and Server 2008 R2, which is basically the same thing as Windows 7.
The Kaspersky graph shows a tiny, tiny number of Win10 machines infected. My guess is that’s either a false positive, or from people who were intentionally infecting Win7 machines running in a Virtual Machine on Win10.
There’s a commenter (I know, I shouldn’t read the comments) who says:
You want to know why Windows 10 was on the list?
I blame Microsoft for still allowing people to opt-out of auto-updates. The mass do not always know what’s best for them, so it is our responsibility to firmly reject their demand when it’s harmful, and educate them why so.I could pull my hair out. Win10 wasn’t directly affected. Opting in or out of updates isn’t a problem – although if you opted out of Win7 auto updates and you didn’t check for two months, yep, you could’ve gotten stung. But Win10? Puh-lease.
-
Breaking: WannaCry has been decrypted, if you follow the rules
For those of you who were infected with WannaCry, very good news. If you see the WannaCry ransom screen:
DON’T REBOOT.
Matt Suiche has confirmed that the wanakiwi tool can reach into your infected Win7 machine and retrieve the decryption key. The tool was created by Benjamin Delpy, @gentilkiwi. Per Suiche:
His tool is very ingenious as it does not look for the actual key but the prime numbers in memory to recompute the key itself. In short, his technique is totally bad ass and super smart.
Suiche has confirmed that the tool works on WinXP x86, Server 2003 x86, and Win7 x86 “This would imply it works for every version of Windows from XP to 7, including… Vista and 2008 and 2008 R2.”
Remember, the original WannaCry worm ONLY infects Windows 7 computers. Anything you’ve read to the contrary is wrong.
REMEMBER – You have to make sure your Windows machines are updated, to protect against new versions of WannaCry. They’re starting to make an appearance. If you haven’t already done it, drop everything and get patched now. Every Windows machine. No exceptions.