Newsletter Archives
-
The Shadow Brokers, in new taunt, threaten to release even more NSA sourced malware
If you thought WannaCry was bad, you ain’t seen nothin’ yet.
Malware as a Service. Do they really have Win10 sploits, nuke details from Russia and North Korea? Their story lines up with what we know from the inside. Are their tales of bribery and double-crossing true, too?
It’s a bombshell of a story.
InfoWorld Woody on Windows
-
DoublePulsar infections picking up steam
If you don’t have last month’s MS17-010 installed, better get off your duff.
InfoWorld Woody on Windows
Good point from Michael Horowitz:
99.99% of the time ShieldsUP does not scan the computer it is run from, it scans the router the computer is connected to. Also, if the computer is using a VPN, it scans the VPN server rather than the router or the computer.
What you wrote is true, but its not the whole story. That is, while a PC is connected to the router that was scanned, it is safe. But, if and when it connects to the Internet through another router, it may not be safe.
-
Time to get off the Group W bench – at least for a few minutes
UPDATE: Technical details have been posted by zero sum at the @zerosum0x0 blog. Bottom line, “Many of the vulnerabilities that are exploited were fixed in MS17-010, perhaps the most critical Windows patch in almost a decade.”
UPDATE: Catalin Cimpanu, BleepingComputer: “Over 36,000 Computers Infected with NSA’s DoublePulsar Malware” and “5.5 million computers haven’t installed patches Microsoft made available for the SMB flaws exploited by the NSA tools, they are vulnerable to exploits.”
UPDATE (Sunday morning, Central time): tweet from Below0Day: 56,586 DoublePulsar infections detected.
If you haven’t yet installed March patches for Windows, listen up.
One of those leaked NSA exploits, EternalBlue, has been pulled out of the Shadow Brokers steaming pile of malware and used to install a backdoor called DoublePulsar. Dan Goodin at Ars Technica says that:
there’s growing consensus that from 30,000 to 107,000 Windows machines may be infected by DoublePulsar. Once hijacked, those computers may be open to other attacks.
EternalBlue can attack any machine with the Windows “SMB” service accessible to the internet. Our tax dollars at work.
Rik van Duinj at dearBytes has published step-by-step instructions for locating exposed SMB services, running EternalBlue, using it to install DoublePulsar, and then using DoublePulsar to run just about anything. It’s pretty straightforward.
Yesterday Iain Thomson posted a delightful expose in The Register:
DOUBLEPULSAR, being a nation-state-grade backdoor, is extremely stealthy and unlikely to be discovered on a hacked box unless whichever miscreant is using it gets clumsy.
Amazon’s AWS and Microsoft’s Azure showed up on the top 100 most-infected domains as you’d expect as large hosts of customer virtual machines. Then there are systems at big names such as Ricoh in India, various universities, and machines on Comcast connections.
Moral of the story: If you haven’t yet installed March’s MS17-010, better pull your machine out of the mothballs and get it patched. If it’s connected to the internet, it’s exposed.
It looks like I’ll be changing the MS-DEFCON level in the next few days, to take the sting out of some other exposed problems, but for now, if you haven’t installed the March updates, better get to it.
Not sure if you’re caught up? Here’s how to check.
For Win10: In the Cortana search box, type winver.
- If you have version 1703, you’re fine.
- If you have version 1607, you need to be on Build 14393.953 or later. (Note that the documentation in the KB article is wrong.)
- If you have version 1511, you need to be on Build 105867.839 or later.
- If you have Build 10240 (commonly called “version 1507” but Microsoft didn’t figure out the naming until later), you need to be on Build 10240.17319 or later.
In all cases, for Win10, if you aren’t up to those build numbers, you need to install the latest cumulative update. Follow my instructions to get your build number up to snuff, but don’t be tempted to install anything else at this point.
For Win7: Right-click Start > Control Panel > Windows Update > View installed updates. You should have one of these listed:
- KB 4012212 the Security-Only “Group B” patch, or
- KB 4012215 the March Monthly Rollup “Group A” patch, or
- KB 4015549 the April Monthly Rollup
If you don’t have any of those listed, at a very minimum, you should download and install KB 4012212. Don’t worry about Group A or Group B at this point. Installing KB 4012212 will protect you without committing your system to either Group A or Group B. There’s a full description at @PKCano’s AKB 2000003, but if you only want the download links, look at this line:
Mar 2017 KB 4012212 – Download 32-bit or 64-bit
Similarly, for Win 8.1, look for these installed updates:
- KB 4012213 the Security-Only “Group B” patch, or
- KB 4012216 the March Monthly Rollup “Group A” patch, or
- KB 4015550 the April Monthly Rollup
If you don’t have any of those, look at @PKCano’s list:
Mar 2017 KB 4012213 – Download 32-bit or 64-bit
That’s what you need to do right now, to protect yourself from the NSA’s swirling spitstorm.
-
What every Windows customer should know about last week’s deluge of malware
It’s been a crazy week. Last Monday we learned about the Word zero-day that uses a booby-trapped Word DOC attached to an email message to infect machines. Then, on Friday, came the deluge of exploits collectively identified with their leaker, Shadow Brokers, which appear to originate with the US National Security Agency.
In both cases, many of us thought the sky was falling on Windows users — the exploits touch all versions of Windows, all versions of Office. Now we have more insight and the situation isn’t as bad as was first thought. Here’s what you need to know.
Word zero-day
As I explained last Monday, the Word zero-day takes over your PC when you open an infected Word document attached to an email. The attack takes place from inside Word, so it doesn’t matter which email program you’re using, or even which version of Windows.
In a twist I’ve never seen before, subsequent research into the exploit revealed that it was first used by suspected nation-state attackers, but was then incorporated into garden-variety malware. Zach Whittaker on ZDNet and Dan Goodin on Ars Technica report that the exploit was originally used in January to hack Russian targets — but the same code snippet turned up in a Dridex banking malware email campaign from last week. Exploits aimed at the spooky set rarely get unleashed on the world at large, but this one is a big exception.
In theory, in order to block the exploit’s path, you have to apply both the appropriate April Office security patch and either the Windows 7 or 8.1 April Monthly Rollup or the April Security-only patch, or the Windows 10 April cumulative update. That’s a big problem for a lot of folks because the April patches — 210 security patches, 644 in all — are causing all sorts of mayhem.
Be of good cheer. I’m seeing verification from all over the web — including our own AskWoody Lounge — that you can avoid infection by sticking with Word’s Protected View Mode (in Word, click File > Options > Trust Center > Trust Center Settings and check Protected View). Protected View Mode is enabled by default in Word 2010 and later, but Word 2007 and earlier don’t have Protected View. (Thanks to anonymous tipster.) See screenshot.
If you click “Enable Editing,” the malware fires automatically — you don’t need to do anything more. If you open an attached DOC from Gmail, it’s harmless, unless you download the file, then open the DOC in Word and then click Enable Editing.
Moral of the story: Use Gmail. Failing that, don’t click Enable Editing. If you have to edit the file, and don’t want to use Google Docs, move it over to OneDrive and use Word Online. Details in this How-To Geek article by Chris Hoffman.
Shadow Brokers last gasp
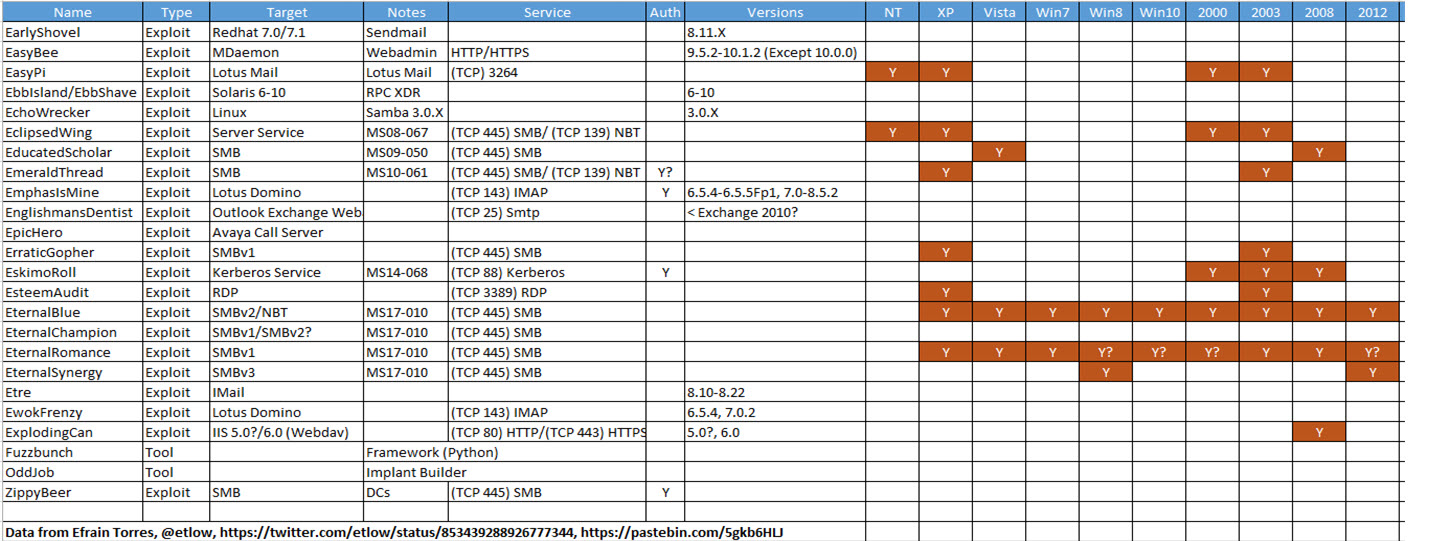
The Shadow Brokers hacks originally appeared to harbor all sorts of zero-days across all versions of Windows, but as last weekend wore on, we found that wasn’t even close to the truth. Security researcher Efrain Torres kindly provided the information in the screenshot to show that the currently supported versions of Windows are (nearly) immune.
To paraphrase, the MS17-010 patch released last month fixes all of the exploits in Windows Vista and later. NT and XP users can kiss their bits goodbye.
Late Friday night, Microsoft offered the following analysis:
Most of the exploits that were disclosed fall into vulnerabilities that are already patched in our supported products. Below is a list of exploits that are confirmed as already addressed by an update. We encourage customers to ensure their computers are up-to-date.
Of the three remaining exploits, “EnglishmanDentist”, “EsteemAudit”, and “ExplodingCan”, none reproduces on supported platforms, which means that customers running Windows 7 and more recent versions of Windows or Exchange 2010 and newer versions of Exchange are not at risk. Customers still running prior versions of these products are encouraged to upgrade to a supported offering.
(It appears as if “Eskimo Roll” is mis-spelled.)
There’s a lot of speculation online that the NSA, in fact, fed Microsoft a list of security holes well in advance of last Friday’s Shadow Brokers disclosure — early enough for Microsoft to fix the SMB-related problems last month, in the March Patch Tuesday batch. The known timing certainly supports that theory, or a variation on it: As Dan Goodin reported in January, Shadow Brokers started dropping hacking tools after they failed to sell their cache for 10,000 bitcoins (currently worth US$12 million).
The follow-up offer for the remaining exploits at 750 BTC fell on deaf ears. Did the NSA figure out what was still in the unreported cache and slip the info to Microsoft? Did Microsoft buy the remaining cache? Did Shadow Brokers turn gray hat and beam advance warning to Microsoft? Was an early peek at all the troubles the main reason we didn’t see patches in February? There are lots of possible explanations, but I doubt that we’ll ever know for sure.
Bottom line: If you have last month’s MS17-010 installed, you’re fine. According to the KB 4013389 article, that includes any of these KB numbers:
- 4012598 MS17-010: Description of the security update for Windows SMB Server: March 14, 2017
- 4012216 March 2017 Security Monthly Quality Rollup for Windows 8.1 and Windows Server 2012 R2
- 4012213 March 2017 Security Only Quality Update for Windows 8.1 and Windows Server 2012 R2
- 4012217 March 2017 Security Monthly Quality Rollup for Windows Server 2012
- 4012214 March 2017 Security Only Quality Update for Windows Server 2012
- 4012215 March 2017 Security Monthly Quality Rollup for Windows 7 SP1 and Windows Server 2008 R2 SP1
- 4012212 March 2017 Security Only Quality Update for Windows 7 SP1 and Windows Server 2008 R2 SP1
- 4013429 March 13, 2017—KB4013429 (OS Build 933)
- 4012606 March 14, 2017—KB4012606 (OS Build 17312)
- 4013198 March 14, 2017—KB4013198 (OS Build 830)
It appears to me that the above info has a mistake — the KB 4013429 patch for Win10 Anniversary Update runs the build number up to 14393.953. I don’t see any reference to 14393.933.
What you need to do, to stay safe
If you have to use Outlook and Windows, and you receive an email with a DOC file attached, don’t click the Enable Editing box in Protected View. (Different versions of Outlook, Outlook.com, and the Windows UWP Mail app all behave a bit differently.) As an alternative, use Gmail, because DOC attachments in Gmail open in a viewer-only mode. If you have to edit the DOC, go through Word Online where a bad DOC will detonate in the cloud.
If you didn’t get caught up on March’s Windows patches, make sure you install MS17-010. For Win7 and 8.1, you can use either the Monthly Rollup or the Security-Only version. For Win10, you may be able to roust out a copy of KB 4013429 for the Anniversary Update, which moves to build 14393.953. (See comments.) You don’t — repeat, don’t — need to install the April patch mess.
UPDATE
Oh boy. Now it looks like it’s possible to bypass Office Protected View. Thx to MrBrian. It’s not clear to me if that bypass can occur with Outlook.com or Outlook 2016 preview panes – but I bet Protected View can be bypassed in Windows 10 Mail.
Hang on. The story continues. In the interim, it’s by far simpler and safer to open attached DOCs using Gmail. That kicks the DOC into a Google Docs viewer which can’t execute anything.
-
Shadow Brokers and what the leaks mean to Windows users
I’m a little late to the party on this one.
As many/most/all of you know, on Friday a group called Shadow Brokers published an enormously damaging trove of code, apparently from the NSA, with all sorts of exploits and hacking tools. Most (if not all) versions of Windows are in the crosshairs.
Our tax dollars at work.
To catch up, there’s a series of articles every Windows user should read.
Dan Goodin, Ars Technica: NSA-leaking Shadow Brokers just dumped its most damaging release yet
Andy Greenburg, Wired: Major leak suggests NSA was deepn in Middle East banking system
Philip Misner, Microsoft Security Response Center: Protecting customers and evaluating risk
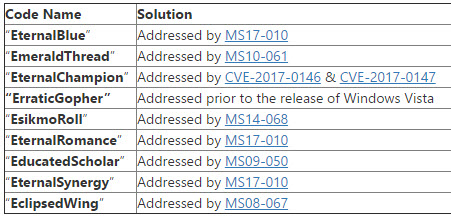
Microsoft’s analysis (which is undoubtedly accurate, but will be debated endlessly):
Most of the exploits that were disclosed fall into vulnerabilities that are already patched in our supported products. Below is a list of exploits that are confirmed as already addressed by an update. We encourage customers to ensure their computers are up-to-date.
Code Name Solution “EternalBlue” Addressed by MS17-010 “EmeraldThread” Addressed by MS10-061 “EternalChampion” Addressed by CVE-2017-0146 & CVE-2017-0147 “ErraticGopher” Addressed prior to the release of Windows Vista “EsikmoRoll” Addressed by MS14-068 “EternalRomance” Addressed by MS17-010 “EducatedScholar” Addressed by MS09-050 “EternalSynergy” Addressed by MS17-010 “EclipsedWing” Addressed by MS08-067 Of the three remaining exploits, “EnglishmanDentist”, “EsteemAudit”, and “ExplodingCan”, none reproduces on supported platforms, which means that customers running Windows 7 and more recent versions of Windows or Exchange 2010 and newer versions of Exchange are not at risk. Customers still running prior versions of these products are encouraged to upgrade to a supported offering.
MS17-010, which figures prominently in that table, is the one that fixed the SMBv1 hole in all versions of Windows. This month’s patches don’t figure in any of the discussions. We’re still at MS-DEFCON 1.
I haven’t seen any evidence that the disclosure is being used by Microsoft to convince folks to move to Windows 10. (I do note, with some nostalgia, that the demise of the Security Bulletin system will make such analysis and communication much more cumbersome in the future.)
So… the sky isn’t falling. But there are some very gray clouds out there, and a whole bunch of cretins jumping around trying to incorporate the Shadow Brokers code into their products. Those of you who patched through last month’s Patch Tuesday crop are OK, according to Microsoft – and they should know. Windows XP and Vista remain debatable. Those of you in Group W — who aren’t patching at all — should take note.
Last night, MrBrian started a Lounge thread on the topic. I’ve moved it to the location referenced above. Thanks, MrBrian.