Newsletter Archives
-
Windows 11 22H2 — one month left
PATCH WATCH

By Susan Bradley
On October 8, 2024, Microsoft will release the last round of security updates for Windows 11 version 22H2.
So right now, go to Settings | System | About to check your version of Windows 11. If your version is 22H2 and your edition is Home or Pro, security updates will cease less than a month from now.
Here’s what Microsoft had to say about this via the Windows Admin portal.
Read the full story in our Plus Newsletter (21.38.0, 2024-09-16).
-
Patch Lady – Issues installing updates on Server 2016
Carl Katz had an interesting situation…. he was attempting to install .net 3.5 on an Essentials 2016 server and it would fail.
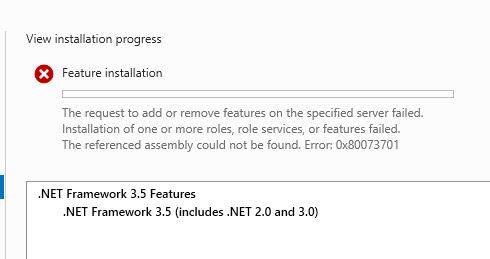
We found two posts that pointed to the root cause being orphaned registry entries related to a language pack – Turkish to be exact (tr-TR). The .net 3.5 feature installed without issue after deleting the all entries containing tr-TR in HKLMSOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing\PackageDetect. He used RegeditX an easier way than using raw regedit to find these entries.
Interestingly enough, he never installed a language pack. So clearly something is going on the install to get these servers into a slightly messed up state.
So if Santa got you a new server for Christmas and you are having issues patching it or getting server roles installed, dig into the registry and see if your problem is registry keys that shouldn’t be there in the first place.
-
Server 2016: Is the sysvol sync bug in July showing up in August?
From @njmalm1:
Has anyone else experienced their GPOs not syncing permissions after applying KB4338814 to Server 2016?
We were getting the ACL error
“The sysvol permissions for one or more GPOs on this domain controller are not in sync with the permissions for the GPOs on the baseline domain”.
Went through an Non-authoritative SYSVOL restore, demoting and promoting a domain controller, and finally uninstalled patch KB4338814 to resolve the issue.
This problem existed on our test domain (two DCs 2012 and 2016) and our production (three DCs 1-2012 and 2-2016) The ACL sync issues only happened on one of the production 2016 DCs which was strange. Once we removed the patch we had to go to any GPOs still showing ACL errors and restore the delegation permissions to defaults in order for it to start syncing.
I have blocked patch KB4338814 from July in WSUS but the issue is now happening again in our test Active Directory after applying the August cumulative updates. I’d love to know if anyone else is seeing this issue and if Microsoft has reported it as a problem.
-
AADConnect still isn’t working with the latest Server 2016 patch
This report from PS:
Just wanted to let you know of another issue that seems to be biting a lot of people with the July updates.
Even with the updated patch on Server 2016 (KB4345418) is still causing an issue with AADConnect servers that triggers a 100% CPU spike on some of the Health and Reporting monitoring services, only fix at this point is to uninstall the latest update. It seems to impact at least 2012 and 2016 servers.
More information here: https://social.msdn.microsoft.com/Forums/en-US/e9b621f6-f38c-488e-8fcb-ff85d406f256/azure-ad-connect-health-sync-monitor-high-cpu-usage?forum=WindowsAzureAD
We just cancelled of our Windows patching for the month, hope MS gets this sorted out soon. What a mess.
In the same vein, Matt Wilkinson tweeted me this.
@woodyleonhard KB 4345418 is causing issues on Server 2016 RDS with a black screen upon login. Have mitigated this issue with a script to delete firewall rules that are created per user. Black screen returned with this update.
— Matt (@bigfoot780) July 18, 2018
-
Eight new entries in the Update Catalog – appear to be metadata changes
On the 17th, Microsoft re-released eight patches in the Update Catalog.
They cover Win10 1803, 1709, and Server 2016.
As best I can tell, there have been no changes to the patches themselves, so it’s likely these are “metadata” changes — adjustments to the installation logic for the patches.
The KB articles now have correct build numbers listed, by the way. But only at the top of each KB article. The slider on the left still has the incorrect build numbers. For example, the latest Win10 1803 patch is listed at the top as build 17134.167, while on the left index it’s shown as 17134.166.
A foolish inconsistency.
-
Microsoft releases Server 2016 update 14393.729 using new, superior hotfix distribution method
I’m really impressed. It took Microsoft two years to figure out that their Win10 patching method was unwieldy, but it looks like they’re slowly straightening it out.
InfoWorld Woody on Windows


