Newsletter Archives
-
RIP Office 2010? Not so fast!
PATCH WATCH
By Susan Bradley
Well … we thought we’d seen the last of Office Version 2010.
But Microsoft surprised us by pushing out a batch of November updates for its suite of productivity apps. Note that this isn’t a completely novel event. Microsoft has dribbled out patches for other products that have reached their end of service.
Going forward, Office 2010 will become more dangerous to use — especially when it comes to email phishing attacks.
Read the full story in AskWoody Plus Newsletter 17.45.0 (2020-11-16).
-
July’s Outlook Click-to-Run update lays an egg
PATCH WATCH
By Susan Bradley
Yes, it’s a bit macabre, but I affectionately call the day after Patch Tuesday “dead-body Wednesday.”
I coined that term because Wednesday morning is when we get to see whether our systems survived the updates installed the night before. (These are, of course, my test platforms; I would never subject my production machines to immediate/automatic updating.)
There’s always some anticipation as to which Windows or Office component will be wounded by an update. This time around, it was Outlook’s turn to be placed on the life-support list.
Read the full story in AskWoody Plus Newsletter 17.28.0 (2020-07-20).
-
Patch Lady – late to the microcode party
This occurred the other day on my Lenovo Laptop that I was seeing why I wasn’t getting 2004. So I kicked a “seeking”… you know where you make it check for updates. And it offered up to me https://support.microsoft.com/en-us/help/4497165/kb4497165-intel-microcode-updates
with the slightly confusing title of 2020-01 Update for Windows 10 Version 1909 for X64 based Systems (KB4497165). So it appears to me that this only gets on machines that “seek”. If you never seek it never gets pushed. Does that sound about right to everyone who has already seen this for months?
I received the same experience tonight on another computer. Once again I was seeking to see if I’d get 2004 and sure enough this January patch is offered up and installed.
As someone joked … apparently it’s like the USA tax refunds – they are VERY much delayed by the lack of IRS employees able to work from home.
-
More Intel microcode updates released through the Update Catalog
I count 14 separate updates in the Microsoft Update Catalog, all of which are dated “2019-01” but released on Feb. 4. The main ones:
Win10 1809 – KB 4465065
Win10 1803 – KB 4346084
Win10 1709 – KB 4346085
and several lesser releases of the same ilk.
Of course, you shouldn’t install them, unless your company’s mentat predicts a Spectre 3a, 4, or L1TF attack that no one else has seen.
-
Mind boggled: The Meltdown/Spectre microcode patches
I just read a tweetstorm from @Karl_F1_Fan to @Crysta that has my head swimming. Here’s what he says:
Hi Crysta,
Your quotes to Microsoft articles are right but things have developed over time. First they asked to set the bitmask for meltdown and Spectre 2 to
FeatureSettingsOverride 1
FeatureSettingsOverrideMask 3for intel clients and servers + the QualityCompat flag
The qualitycompatflag was removed with a patch in March for both clients and servers. Then Microsoft advised the same registry mask for Intel but for AMD it was
FeatureSettingsOverride 64
FeatureSettingsOverrideMask 3(I won’t handle disable flags here for easiness.)
With the appearance of Spectre NG the flags changed again for both AMD and Intel to
FeatureSettingsOverride 8
FeatureSettingsOverrideMask 3which Microsoft is falsely or incompletely advising now in the L1TF article. If a user is setting 1/3 it will DISABLE protection CVE-2018-3639 [speculative store bypass] also it will disable AMD protections.
Meltdown, Spectre 2 / 3, 3a / 4 / L1TF need microcode updates or the seperate updates deployed for Windows 10 in August 2018 + 2018-08 CUs. In addition Microsoft choose that only servers need the registry keys to enable protection. I would advise all customers to apply them.
The current situation is unbearable for average sys admins and there is too much confusion.
IMHO Microsoft should roll out all microcode updates for any OS and enable protection by default without any registry keys it is much easier to understand how to disable it.
The current situation is that only @Dell really cares to bring out BIOS updates for ANY systems back to 2009 whilst other OEMs don’t give a ****.. no matter if we are talking about enterprise or home.
@ASUS there are no microcodes for all systems, as Intel provided. @HP is not updating their site accordingly so the theme sites indicate updates are missing or pending, while being partially available on the product site. We better don’t talk about lack of support from @Acer Lenovo or Medion etc. Without Win10 we would have no protection at all
Based on a variety of 70 client pcs and servers of various OEMS / vendors only 18 received all BIOS microcode updates. 6 had too old Intel / AMD CPUs, more than 21 are only patches because Microsoft rolled out (optional) Microcode Updates. Others unprotected due to old Windows Client / Server version.
How’s that for the very definition of falling into the briar patch?
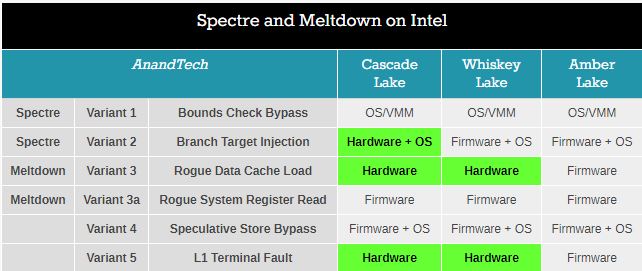
UPDATE: I just followed a link from @teroalhonen to a discussion on Anandtech of the new Intel processors and how they fare with Meltdown and Spectre. Clearly, whoever put together this slide didn’t have a clue.
I sympathize. If Anandtech can’t get it right, what chance do we mortals have? Whotta mess.
ANOTHER UPDATE: ‘Softie Jorge Lopez (@J0RGEL0P3Z) posted a few hours ago:
The 0 / 3 combo enables CVEs 2017-5715 and CVE 2017-5754. The 8 / 3 combo enables Speculative Store Bypass (SSB) protection (CVE 2018-3639) *and* -5715/-5754. L1TF kernel protection requires only for 5754 to be on (so either 0 or 8 works for L1TF). Will see about making clearer
— Jorge Lopez (@cybericua) August 31, 2018
-
Patch Lady – what’s up with the Microcode updates?
Yesterday we’ve been seeing potential issues with the microcode updates and they were expired off of WSUS servers last night…
Unsure what’s up, but Microsoft appears to be pulling these updates back.
I think there is/was metadata detection issues and they were offered up and installed on machines they shouldn’t have been installed.
UPDATE: Günter Born has a compelling history posted on his Born City site.
-
Microsoft Patch Alert: August is much, much better than July
There are still some well-known (even acknowledged) bugs, and the inanities performed in the name of Meltdown and Spectre continue to boggle my mind.
And, of course, you can’t post any before-and-after performance statistics about the Intel microcode patches.
Computerworld Woody on Windows.
UPDATE: Intel has backed off its ridiculous (and likely unenforceable) gag order. See Paul Alcorn’s article on Tom’s Hardware.
-
Patch Lady – Microcode confusion
Patch Lady here on the Microcode updates.
So here’s my take on all of this:
Unless you are a nation state, have a key asset in a cloud server, or are running for a government office, I think we are spending way way more time worrying about this than we should. I still think that attackers will nail me with malware, attack me with phishing, ransomware, etc etc, way more than someone will use these side channel attacks to gain information from me. Remember that the attacker has to get on your system first and I still think they will use the umpteen other ways to attack me easier than this attack. Also keep in mind that we won’t really have a full fix for this issue for several years. Intel and AMD will need to redesign the chips to ultimately get fixed.
That said… if you are as confused as I am about all these updates, join the club. There are a few facts to keep in mind:
You need two updates to ultimately be patched. An operating system update (of which the August patches have the latest updates that include L1 Terminal Fault (L1TF) that affects Intel® Core® processors and Intel® Xeon® processors (CVE-2018-3620 and CVE-2018-3646) aka the latest ones.
You then need EITHER a firmware patch from your OEM vendor or one of these Microcode updates that Microsoft have been offering up.
You don’t need both a firmware and a Microcode. It’s probably wiser to get a firmware update as I’ve found in patching windows 10 and getting all the feature updates on, that machines really need a firmware update to patch well in general.
In my office where we have standardized on HP, I am making sure that all machines have the HP support assistant to monitor firmware updates. On my Lenovo laptops I’ve made sure they have the solution center installed.
If you have a relatively recent Windows 10 OEM build computer, look to the vendor for a firmware update.
If you want a Microcode update keep in mind that Microsoft released in August to the MU channel *just* for 1803. Per this page: https://support.microsoft.com/en-us/help/4093836/summary-of-intel-microcode-updates 1803 is getting them from Windows Update, Windows Server Update Service, and Microsoft Update Catalog. The other versions are only getting them from the catalog.
For those folks that run WSUS servers, you saw a bunch of Microcode updates out yesterday. Those are JULY versions of the Microcode update, not the same as the AUGUST ones out yesterday. Notice the 2018-07 dates on the updates that came out on WSUS, not the 2018-08.
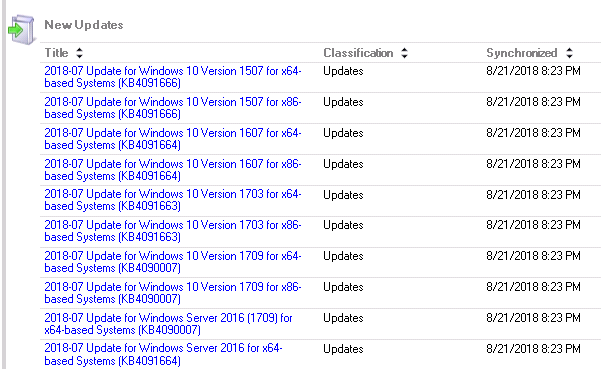
Took me a while to figure out that these AREN’T the same updates even though they came out on the same day.
They did come out on the C week. They are not replacing the cumulative update of August 14th.
 Unfortunately, I’m rating these Microcode updates as not simple.
Unfortunately, I’m rating these Microcode updates as not simple.