Newsletter Archives
-
Patch Lady – we have another Spectre/Meltdown
So included in the July patches was another Spectre/Meltdown patch that the information about it is just coming out today. I’m still not convinced that we’ve seen actual attacks using Spectre/Meltdown nor am I convinced that we will see it in the wild. Rather it’s my opinion that it will be used in targeted attacks but not in widespread ones. Nevertheless, once again there’s another variant that got patched in the July updates:
08/06/2019 08:21 PM EDTOriginal release date: August 6, 2019
The Cybersecurity and Infrastructure Security Agency (CISA) is aware of a vulnerability (CVE-2019-1125) known as SWAPGS, which is a variant of Spectre Variant 1—that affects modern computer processors. This vulnerability can be exploited to steal sensitive data present in a computer systems’ memory.Spectre is a flaw an attacker can exploit to force a program to reveal its data. The name derives from “speculative execution”—an optimization method a computer system performs to check whether it will work to prevent a delay when actually executed. Spectre affects almost all devices including desktops, laptops, and cloud servers.
CISA encourages users and administrators to review the following guidance, refer to their hardware and software vendors for additional details, and apply an appropriate patch when available:
-
“Side channel” vulnerabilities and Windows
I’ve avoided talking much about Spectre, Meltdown and the like because there’s an endless succession of patches to Windows and the hardware – and registry changes to go with them – and we still haven’t seen a real-world exploit.
If you’re running a high profile server, though, you should keep up on this stuff.
Karl Wester-Ebbinghaus (@alqmar) has come up with an exhaustive list of patches, patches to patches, BIOS updates and registry settings, all related to the “side channel” vulnerabilities. Click on the comment link at the top to see the results of his extensive investigation.
-
On Security: Patch Lady Susan Bradley explains why you might — or might not — want to protect your machine from Spectre and Meltdown
Microsoft keeps releasing patches for Spectre, Meltdown, and similar vulnerabilities — tons of them. Do you really need them?
Even if you have the patches installed, they may not be working. That’s intentional — in some cases you have to manually enable the patch.
Here’s a quick overview of the problem, a look at Steve Gibson’s free InSpectre tool that’ll poke at your system, and some solid recommendations for when you might be at risk, and when you can gleefully thumb your nose.
Out this morning to all AskWoody Plus members, in AskWoody Plus Newsletter 16.7.0.
-
Patch Lady – How to update Win10 to fix Spectre, Meltdown and other side channel vulnerabilities
Patch Lady Susan Bradley’s latest column in CSOOnline:
In January 2018, security news media was abuzz over a new class of vulnerability called side channel vulnerabilities. Spectre, Meltdown and Foreshadow are some of the best known. They exploit weaknesses in speculative execution in microprocessors to leak unauthorized information. Side channel vulnerabilities allow attackers to bypass account permissions, virtualization boundaries and protected memory regions.
Patching these vulnerabilities is not easy. They are mitigated by a combination of patches from both the chipset vendor and the operating system provider. Worse, there is often a noticeable performance hit after installing these updates…
Windows servers in particular need specific guidance as most of the protections are not enabled by default.
If you’re running a server that’s potentially at risk, it would behoove you to read this article.
-
Mind boggled: The Meltdown/Spectre microcode patches
I just read a tweetstorm from @Karl_F1_Fan to @Crysta that has my head swimming. Here’s what he says:
Hi Crysta,
Your quotes to Microsoft articles are right but things have developed over time. First they asked to set the bitmask for meltdown and Spectre 2 to
FeatureSettingsOverride 1
FeatureSettingsOverrideMask 3for intel clients and servers + the QualityCompat flag
The qualitycompatflag was removed with a patch in March for both clients and servers. Then Microsoft advised the same registry mask for Intel but for AMD it was
FeatureSettingsOverride 64
FeatureSettingsOverrideMask 3(I won’t handle disable flags here for easiness.)
With the appearance of Spectre NG the flags changed again for both AMD and Intel to
FeatureSettingsOverride 8
FeatureSettingsOverrideMask 3which Microsoft is falsely or incompletely advising now in the L1TF article. If a user is setting 1/3 it will DISABLE protection CVE-2018-3639 [speculative store bypass] also it will disable AMD protections.
Meltdown, Spectre 2 / 3, 3a / 4 / L1TF need microcode updates or the seperate updates deployed for Windows 10 in August 2018 + 2018-08 CUs. In addition Microsoft choose that only servers need the registry keys to enable protection. I would advise all customers to apply them.
The current situation is unbearable for average sys admins and there is too much confusion.
IMHO Microsoft should roll out all microcode updates for any OS and enable protection by default without any registry keys it is much easier to understand how to disable it.
The current situation is that only @Dell really cares to bring out BIOS updates for ANY systems back to 2009 whilst other OEMs don’t give a ****.. no matter if we are talking about enterprise or home.
@ASUS there are no microcodes for all systems, as Intel provided. @HP is not updating their site accordingly so the theme sites indicate updates are missing or pending, while being partially available on the product site. We better don’t talk about lack of support from @Acer Lenovo or Medion etc. Without Win10 we would have no protection at all
Based on a variety of 70 client pcs and servers of various OEMS / vendors only 18 received all BIOS microcode updates. 6 had too old Intel / AMD CPUs, more than 21 are only patches because Microsoft rolled out (optional) Microcode Updates. Others unprotected due to old Windows Client / Server version.
How’s that for the very definition of falling into the briar patch?
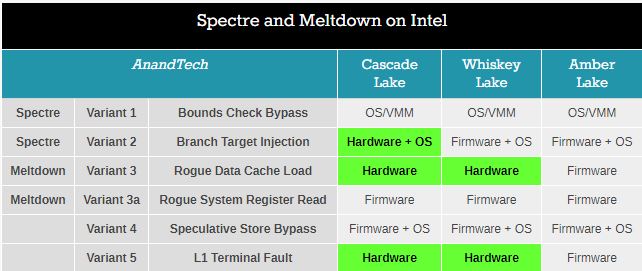
UPDATE: I just followed a link from @teroalhonen to a discussion on Anandtech of the new Intel processors and how they fare with Meltdown and Spectre. Clearly, whoever put together this slide didn’t have a clue.
I sympathize. If Anandtech can’t get it right, what chance do we mortals have? Whotta mess.
ANOTHER UPDATE: ‘Softie Jorge Lopez (@J0RGEL0P3Z) posted a few hours ago:
The 0 / 3 combo enables CVEs 2017-5715 and CVE 2017-5754. The 8 / 3 combo enables Speculative Store Bypass (SSB) protection (CVE 2018-3639) *and* -5715/-5754. L1TF kernel protection requires only for 5754 to be on (so either 0 or 8 works for L1TF). Will see about making clearer
— Jorge Lopez (@cybericua) August 31, 2018
-
Patch Lady – what’s up with the Microcode updates?
Yesterday we’ve been seeing potential issues with the microcode updates and they were expired off of WSUS servers last night…
Unsure what’s up, but Microsoft appears to be pulling these updates back.
I think there is/was metadata detection issues and they were offered up and installed on machines they shouldn’t have been installed.
UPDATE: Günter Born has a compelling history posted on his Born City site.
-
Microsoft Patch Alert: August is much, much better than July
There are still some well-known (even acknowledged) bugs, and the inanities performed in the name of Meltdown and Spectre continue to boggle my mind.
And, of course, you can’t post any before-and-after performance statistics about the Intel microcode patches.
Computerworld Woody on Windows.
UPDATE: Intel has backed off its ridiculous (and likely unenforceable) gag order. See Paul Alcorn’s article on Tom’s Hardware.
-
Patch Lady – light reading for the evening
 For those of you that like to dig a bit deeper into the details of patching, I highly recommend the Zero Day blog. For those who remember the detailed Microsoft MSRC blogs from years ago, the author is one that USED to write those detailed Microsoft blogs: Dustin Childs. Now he works for the Zero day Initiative and writes these fantastic blogs that go a long way to help me understand the risks of *not* patching.
For those of you that like to dig a bit deeper into the details of patching, I highly recommend the Zero Day blog. For those who remember the detailed Microsoft MSRC blogs from years ago, the author is one that USED to write those detailed Microsoft blogs: Dustin Childs. Now he works for the Zero day Initiative and writes these fantastic blogs that go a long way to help me understand the risks of *not* patching.The other day I said that when the point in time occurs that I’m more scared of *not* patching than I am of patching, that’s the point in time I need to patch.
So right now, we are day four of the updating process. I’ve installed updates on a few of my home pcs, I will be rolling an update on a sample (in my office that means ONE) production machine to see if I spot any issues. I’m watching the forums for side effects. I’m waiting for Microsoft to fix any metadata detection issues (they already expired KB4284880 as there was a duplicate up there), and I’m basically not approving anything at this time until my testing process is done.
But what I am doing is reading and understanding what this month’s updates include. Here’s my light reading I’m doing tonight:
https://www.zerodayinitiative.com/blog/2018/6/12/the-june-2018-security-update-review
The blog post spells out the security issues per CVE or Common Vulnerabilities and Exposures, not per patch. So while it doesn’t showcase the updates as you can I see them on your computer, (as we see them in one glob per operating system) it does give a way better deep dirty explanation of the overall risks related to not updating so you and I can get a feel for how long we should wait before we update.
It also helps me to determine what I currently have in place for mitigations or protections that will also give me time to not patch.
Flash zero day – “primarily targeting the Middle East region and is wrapped in an Office document”. Okay so I’m not located in the Middle East and I not only warn users about opening attachments, we have email attachment filtering.
DNS server bug – “The more likely scenario is simply tricking a target DNS server into querying an evil server that sends the corrupted response”. In small firms or home users, the way I see this probably used is getting your system to reach out to a malicious DNS server bypassing your DNS entries (or your ISPs). For servers in large firms that handle handling out DNS inside of a firm, because you can’t always control what your servers connect to, this is one you’ll probably want to patch sooner versus later.
Http.sys bug – bug in a web service, “A remote attacker could cause code execution by sending a malformed packet to a target server”. If I’ve got a web server out there, I’ll be testing this and rolling it out sooner versus later. But we don’t (well, we shouldn’t) run web servers on workstations so this will be lower risk there.
Cortana bug – “someone close enough to speak to a Cortana-enabled system could execute programs with elevated privileges” Doesn’t impact Windows 7, and like the Alexa bugs, you have to be local to the machine to do your evil deeds. Bottom line anything these days that you yell “Hey….” to is being targeted these days because it’s sexy to go after the voice recognition stuff.
The other thing of interest to me that ran across my radar was YASMB (yet another Spectre Meltdown bug). This time the v4 bug is NOT enabled by default. Based on my read it’s due to two things:
Thing one, it’s another Spectre Meltdown with a performance hit. As per this blog post “If enabled, we’ve observed a performance impact of approximately 2 to 8 percent based on overall scores for benchmarks.”. Thing two there are no active attacks and it reads to me that it’s going to be hard to exploit. Not to say it’s impossible to exploit, but there are lots of other low hanging fruit that they can use to get me.
There’s a nice recap on the bottom of the portal page that describes which patches are and are not enabled by default in the Spectre/Meltdown patches:
-
- After installing Windows updates, refer to the following table for further action to be protected from Spectre/Meltdown vulnerabilities:
Operating System CVE-2017-5715 CV-2017-5754 CVE-2018-3639 Windows 10 Enabled by default Enabled by default Disabled by default – see ADV180012 Windows Server 2016 Disabled by default – see KB4072698 Disabled by default – see KB4072698 Disabled by default – see ADV180012 Windows 8.1 Enabled by default Enabled by default Not available – see ADV180012 Windows Server 2012 R2 Disabled by default – see KB4072698 Disabled by default – see KB4072698 Not available – see ADV180012 Windows RT 8.1 Enabled by default Enabled by default Not available – see ADV180012 Windows 7 Enabled by default Enabled by default Disabled by default – see ADV180012 Windows Server 2008 R2 Disabled by default – see KB4072698 Disabled by default – see KB4072698 Disabled by default – see ADV180012 Windows Server 2008 Disabled by default – see KB4072698 Disabled by default – see KB4072698 Not available – see ADV180012 I’m still not convinced that on desktops this is as big of an issue we are making it, I still think this is a bigger risk on cloud servers or hosted servers where you may not monitor the access as much as you do on a desktop in front of you.
Just hot off the presses tonight we have another Intel vulnerability that will make our heads hurt trying to figure out the patches on. Called Lazy FP State restore vulnerability
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/ADV180016
Intel Releases Security Advisory on Lazy FP State Restore Vulnerability
06/13/2018 06:47 PM EDTOriginal release date: June 13, 2018
Intel has released recommendations to address a vulnerability—dubbed Lazy FP state restore—affecting Intel Core-based microprocessors. An attacker could exploit this vulnerability to obtain access to sensitive information.
NCCIC encourages users and administrators to review Intel’s Security Advisory INTEL-SA-00145, apply the necessary mitigations, and refer to software vendors for appropriate patches, when available.
At this time Microsoft is still determining updates to be released. If you have VM’s in Azure they are not affected by this vulnerability.
All of this just showcases that you can’t just update your operating system these days, you HAVE to update your bios and hardware drivers.
Here’s another example of hardware patches — Surface 3 has a standalone TPM update tool in order to fix that vulnerability. It can’t come down via Windows update, it has to be done manually.
Lots of fun.
-