Newsletter Archives
-
Win7 and Server 2008 R2 users take notice: It’s only a matter of time before Total Meltdown comes a-knockin’
I haven’t seen anything in the wild as yet, but there’s new, improved exploit code on GitHub — and it won’t be long.
Consolation and advice in Computerworld Woody on Windows.
-
Total Meltdown (not Meltdown!) exploit now available
Remember Total Meltdown, the gaping 64-bit Win7/Server 2008R2 security hole introduced by Microsoft in all of these patches?
- KB 4056894 Win7/Server 2008 R2 January Monthly Rollup.
- KB 4056897 Win7/Server 2008 R2 January Security-only patch.
- KB 4073578 Hotfix for “Unbootable state for AMD devices in Windows 7 SP1. and Windows Server 2008 R2 SP1” bug installed in the January Monthly Rollup and Security-only patches.
- KB 4057400 Win7/Server 2008 R2 Preview of the February Monthly Rollup.
- KB 4074598 Win7/Server 2008 R2 February Monthly Rollup.
- KB 4074587 Win7/Server 2008 R2 February Security-only patch.
- KB 4075211 Win7/Server 2008 R2 Preview of the March Monthly Rollup.
- KB 4091290 Hotfix for “smart card based operations fail with error with SCARD_E_NO_SERVICE” bug installed in the February Monthly Rollup.
- KB 4088875 Win7/Server 2008 R2 March Monthly Rollup.
- KB 4088878 Win7/Server 2008 R2 March Security-only patch.
- KB 4088881 Win7/Server 2008 R2 Preview of April Monthly Rollup.
The chickens have come home to roost. In the past few hours there’s been exploit code posted on GitHub that takes advantage of the Total Meltdown hole. Self-described “Hacker and Infosec Researcher” XPN has details.
Thank you, Microsoft.
At this point, I figure Win7/Server 2008 R2 users have three options:
- Take Susan Bradley’s advice and roll back your machine to its state before the patching insanity started in January. That’s a massive, thankless, task, and it leaves you exposed to the (few) real security holes plugged this year.
- Download and manually install the KB 4093108 Security-only patch.
- Use Windows Update to install all of the checked April patches, including the KB 4093118 Monthly Rollup.
If you take either of the last two approaches, make a backup first. There are loads of known bugs with this month’s patches.
Alternatively, you could install KB 4100480, which fixes the Total Meltdown bug, but introduces all sorts of problems, per MrBrian and Susan Bradley.
Welcome to the cesspool that has become Windows 7.
UPDATE: XPN has published a new version of his exploit.
Thx @GossiTheDog.
-
New versions of buggy March Win7 patches are out
I have no idea what changed, but Günter Born reports (and a check of the Update Catalog confirms) that there are new versions of:
KB 4088875 – Win7 March Monthly Rollup (dated, in the Update Catalog, as April 4)
KB 4088878 – Win7 March Security-only patch (also April 4)
KB 4088881 – Preview of the Win7 April Monthly Rollup (also April 4)
KB 4090450 – Spectre V2 patch for Server 2008 (dated April 3)
Looking at the KBNew page, I also see new versions of:
KB 4099950 – the hotfix patch for bugs in the March Win7 patches (now dated April 4) – I talked about this fix of a fix of a … earlier this week in Computerworld.
KB 4088879 – the Win8.1 Security-only patch (still dated March 10)
And, as noted in several places on AskWoody, there’s a new version of the old favorite KB 2952664 — the patch that so helpfully makes it easier to upgrade Win7 to Win10 — and its Win8.1 cohort, KB 2976978.
Born identifies new notes in the KB articles for the Win7 Monthly Rollup and the Preview Monthly Rollup that say:
Important Please apply KB4100480 immediately after applying this update. KB4100480 resolves vulnerability in the Windows kernel for the 64-bit (x64) version of Windows. This vulnerability is documented in CVE-2018-1038 .
You may recall that KB 4100480 is the “OMG” patch issued by MS when they figured that all of this year’s Win7 patches opened a huge “Total Meltdown” security hole in Win7.
In addition, the description of the KB 4088875 Monthly Rollup patch and the KB 4088878 Security-only patch now advise:
After you install this update, you may receive a Stop error message that resembles the following when you log off the computer:
SESSION_HAS_VALID_POOL_ON_EXIT (ab)
The solution on offer is KB 4099467, which is a single-shot hotfix for Win7 designed specifically to fix this bluescreen.
How about them apples….
Can any of you shed light on the reasons for the changes — in particular, do they fix any of the gazillion security holes in last month’s patches? If so, care to speculate on why Microsoft just slipped this stuff out without any announcement?
And… when will it be safe to get back in the Win7 patching water?
-
Patch Lady – to patch or not to patch?
 I am cringing as I’m typing this – as I hate it when I tell people to roll back on updates. But after reading this and especially Kevin Beaumont’s tweet about the risk of Spectre/Meltdown [low risk] versus the risk of the bug introduced by ALL of the updates released since January, [high risk] one is kinda stuck between a rock and a hard place.
I am cringing as I’m typing this – as I hate it when I tell people to roll back on updates. But after reading this and especially Kevin Beaumont’s tweet about the risk of Spectre/Meltdown [low risk] versus the risk of the bug introduced by ALL of the updates released since January, [high risk] one is kinda stuck between a rock and a hard place.The problem is between January and March there are a lot of OTHER updates released in addition to the Spectre and Meltdown that are bundled in the Windows 7/Server 2012 R2 updates. For those following the Woody patching recommendations I think I’m going to go even farther out on a limb and propose that if you are holding off on the March updates, you need to roll all the way back to pre-January and hold tight.
Me personally, I still would determine how paranoid of a user base you have. If there are users in your patching environment that they surf and click on ANYTHING, I’d hope you’d make them do their random surfing on an ipad, not a Windows machine (probably still with local admin rights) until this Windows 7 patching mess gets straightened out. I don’t like telling people to roll back to pre-January updates, but neither do I appreciate Microsoft having constant side effects that are measurable and impactful and all that happens is that they keep on telling us that they are working on the issues and this will be fixed in a future release. That SMB memory leak has been happening since January. And in the Security triad of (Confidentiality, Integrity, and Availability) information security, availability is important. On servers in particular that SMB memory leak has availability side effects.
I see many of you asking for the order of updates to install and right now my recommendation is:
If you have any January through March update installed, make sure KB4100480 is installed.
Otherwise go into add/remove programs and roll back to December’s KB4054521 (security only) or KB4054518 (rollup) and then hang tight and keep our fingers crossed that April’s updates will resolve these issues.
And then Microsoft please please please, do something about these known issues and fix them, because it pains me greatly to publically type this.
(Edit, please note that this only applies to 64bit not 32bit, apologies for not noting that. Also be aware that if you see any patch with AMD64 in the name, it applies to Intel 64 as well.)
-
Sorting through the Patch Thursday and Friday offerings
My head is still spinning. Over the past two days (in addition to learning that Windows honcho Terry Myerson is leaving, and the Windows team is being scattered to the winds) we’ve had an enormous number of poorly documented, overlapping, and completely inscrutable patches.
Let me see if I can bring some sanity to the mess.
A destructive fix for Total Meltdown
KB 4100480 kicked off the two days from patching purgatory with a Windows 7/Server 2008R2 kernel update for CVE-2018-1038, the “Total Meltdown” bug Microsoft introduced in Win7 back in January and kept re-installing ever since, most recently with the March Patch Tuesday Monthly Rollup KB 4088875 and Security-only patch KB 4088878. Susan Bradley immediately jumped into the fray with an initial warning Thursday afternoon. Microsoft’s documentation was so bad we had no idea what was being fixed, which bugs were being passed along — and whether this fix introduced even more bugs in the original Meltdown/Spectre January patch.
Just a reminder that there are NO known exploits of Meltdown or Spectre in the wild.
Ulf Frisk, the guy who discovered this gaping security hole (where a program can read or write data essentially everywhere on Intel PCs running 64-bit Win7/Server 2008R2), said on Wednesday that this month’s Monthly Rollup fixes the hole. The next day he said that, oops, this month’s Monthly Rollup doesn’t fix the hole and Microsoft revealed that, uh, this month’s Monthly Rollup actually introduces the hole.
How bad is the hole? Kevin Beaumont (@GossiTheDog) says:
https://twitter.com/GossiTheDog/status/979488659689889797
An anonymous poster says:
Ah, yeah… we’ve produced at least 11 botched up hotfixes in a row which made a gaping security hole out of a theoretical exploit, the most recent of them not even one week old yet, but 12th time’s the charm… absolutely trust us.
Many folks were wondering how this patch stacks up with all of the (many!) other problems we’ve seen with this month’s Win7 Monthly Rollup and Security-only patches. The Folks Who Know Such Things now say that this patch does, indeed, introduce all of those problems — the SMB server memory leak that brings down servers, random re-assignment of static IP addresses, and three separately triggered bluescreens.
A fix for patches that don’t have problems
Also on Thursday afternoon, Microsoft dropped a handful of patches that fix other bad bugs in previous patches. Susan Bradley has a short list that includes KB 4096309 for Win10 1607/Server 2016 that “Addresses an issue that can cause operational degradation or a loss of environment because of connectivity issues in certain environment configurations after installing KB4088889 (released March 22, 2018) orKB4088787 (released March 13, 2018).” As Susan notes, both of the referenced fixes are still listed in the KB articles as “Microsoft is not currently aware of any issues with this update.”
Bluescreen stoppers
Then there are the patches that fix bluescreens generated by earlier botched patches:
- KB 4099467 – Stop error 0xAB when you log off a Windows 7 SP1 or Windows Server 2008 R2 SP1 session. That’s a bug introduced in this month’s Win7/Server2008R2 patches.
- KB 4099468 – Stop error 0xAB when you log off a Windows Server 2012 session. That bug was introduced in this month’s Server 2012 patches
- KB 4096310 -Stop error 0xAB when you log off a Windows Server 2008 session. Ditto ditto ditto.
Save your IP if you’re prescient
And then there’s KB 4099950, Network Interface Card settings can be replaced, or static IP address settings can be lost, released Friday, chronicled by MrBrian. Ends up this is just a package for the (modified) VBScript that, when run prior to installing this month’s patches for Win7, avoids the static IP busting nature of the patch. I talk about the VBScript program in my Computerworld Patch Alert article.
Abbodi86 describes it:
So it’s the easy automated version of the VBscript. It checks if KB2550978 hotfix is installed (or any superseder). [Note: KB 2550978 is a many-year-old hotfix, last updated more than a year ago.] The hotfix actually describe the mess with NIC and March updates in very informative way
I wonder why Microsoft didn’t roll out that important fix years ago through Windows Update
The important note is that you have to run KB 4099950 before you install this month’s Win7/Server 2008R2 patches.
MrBrian goes on to note that the KB article for 4099950 contains this gem:
Important: This update must be installed prior to installing KB408875 or KB408878
Which is hogwash, of course. Microsoft’s missing an “8” or two.
What else?
So what did I miss?
-
Patch Lady – new update for Windows 7 KB 4100480
 Just sync’d up to my WSUS server is KB4100480. Based on trying to follow the KB I can’t tell if this fixes the Spectre/Meltdown fix that introduced new vulnerabilities, fixes our known issues introduced by the prior updates or anything other than confuse me more. What I can tell you is that while it does say in the KB link that Microsoft is not aware of any issues…. the KB links to all the prior updates that DID have known issues. For now, stick your head under the sand until further notice until we figure out what this update is doing.
Just sync’d up to my WSUS server is KB4100480. Based on trying to follow the KB I can’t tell if this fixes the Spectre/Meltdown fix that introduced new vulnerabilities, fixes our known issues introduced by the prior updates or anything other than confuse me more. What I can tell you is that while it does say in the KB link that Microsoft is not aware of any issues…. the KB links to all the prior updates that DID have known issues. For now, stick your head under the sand until further notice until we figure out what this update is doing.It is being flagged as a security update as I got a security notification for it, so if you have automatic updates enabled (because you love to live on the edge), be aware that you’ll probably get it installed tonight.
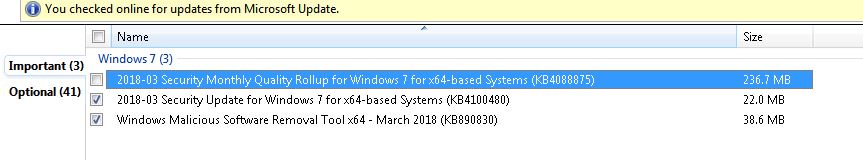
Microsoft update now shows it checked for KB4100480.
Update: Yes it fixes the vulnerability introduced by the prior updates as per https://twitter.com/UlfFrisk/status/979470561964449794 However it’s unknown if the known issues are fixed.


