Newsletter Archives
-
A protocol question about KB 4099950
Two questions keep popping up — and as far as I can tell, we don’t have any definitive answers. KB 4099950, you may recall, is supposed to be a precursor to installing the Win7 March Monthly Rollup, KB 4088875, or the Security-only patch, KB 4088878, and it’s designed to bypass the bug in those two March patches that mess up NIC settings and/or static IP addresses. KB 4099950 was tweaked on March 17, changing the installation logic, but not the patched files. It appears as if KB 4099950 is included in the latest release of month’s Monthly Rollup, KB 4093118.
Question 1: For those who installed KB 4099950 before March 17, can you just install KB 4093118? Will the new Monthly Rollup gloss over the problems created by the old version of KB 4099950?
Question 2: Same question for those installing the April Security-only patch KB 4093108 (and the IE 11 patch). Can you just install those patches, or do you need to uninstall the old version of KB 4099950 first?
If the answer’s in the docs, I sure can’t find it….
-
Patch Lady – Mr. Metadata got fixed
 Remember this post? Last night in addition to a new update for 1709, KB4093118 for Windows 7 got refreshed. It appears that once it’s metadata got fixed we no longer have the issue with it being reoffered to that platform.
Remember this post? Last night in addition to a new update for 1709, KB4093118 for Windows 7 got refreshed. It appears that once it’s metadata got fixed we no longer have the issue with it being reoffered to that platform.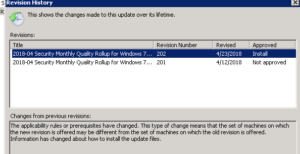
What exactly is metadata and especially when it comes to updates? Metadata is information that Microsoft update and WSUS used to determine which update is applicable to which operating system. In this case the revision info says ….
The applicability rules or prerequisites have changed. This type of change means that the set of machines on which the new revision is offered may be different from the set of machines on which the old revision is offered. Information has changed about how to install the update files.
Before if you installed the preview update for Windows 7, KB4093118 kept getting reinstalled due to the faulty detection. Microsoft fixed the detection and voila… no more reoffered update.
Bottom line patches often have to be told what to apply to, they don’t just “know”.
-
Win7 and Server 2008 R2 users take notice: It’s only a matter of time before Total Meltdown comes a-knockin’
I haven’t seen anything in the wild as yet, but there’s new, improved exploit code on GitHub — and it won’t be long.
Consolation and advice in Computerworld Woody on Windows.
-
Total Meltdown (not Meltdown!) exploit now available
Remember Total Meltdown, the gaping 64-bit Win7/Server 2008R2 security hole introduced by Microsoft in all of these patches?
- KB 4056894 Win7/Server 2008 R2 January Monthly Rollup.
- KB 4056897 Win7/Server 2008 R2 January Security-only patch.
- KB 4073578 Hotfix for “Unbootable state for AMD devices in Windows 7 SP1. and Windows Server 2008 R2 SP1” bug installed in the January Monthly Rollup and Security-only patches.
- KB 4057400 Win7/Server 2008 R2 Preview of the February Monthly Rollup.
- KB 4074598 Win7/Server 2008 R2 February Monthly Rollup.
- KB 4074587 Win7/Server 2008 R2 February Security-only patch.
- KB 4075211 Win7/Server 2008 R2 Preview of the March Monthly Rollup.
- KB 4091290 Hotfix for “smart card based operations fail with error with SCARD_E_NO_SERVICE” bug installed in the February Monthly Rollup.
- KB 4088875 Win7/Server 2008 R2 March Monthly Rollup.
- KB 4088878 Win7/Server 2008 R2 March Security-only patch.
- KB 4088881 Win7/Server 2008 R2 Preview of April Monthly Rollup.
The chickens have come home to roost. In the past few hours there’s been exploit code posted on GitHub that takes advantage of the Total Meltdown hole. Self-described “Hacker and Infosec Researcher” XPN has details.
Thank you, Microsoft.
At this point, I figure Win7/Server 2008 R2 users have three options:
- Take Susan Bradley’s advice and roll back your machine to its state before the patching insanity started in January. That’s a massive, thankless, task, and it leaves you exposed to the (few) real security holes plugged this year.
- Download and manually install the KB 4093108 Security-only patch.
- Use Windows Update to install all of the checked April patches, including the KB 4093118 Monthly Rollup.
If you take either of the last two approaches, make a backup first. There are loads of known bugs with this month’s patches.
Alternatively, you could install KB 4100480, which fixes the Total Meltdown bug, but introduces all sorts of problems, per MrBrian and Susan Bradley.
Welcome to the cesspool that has become Windows 7.
UPDATE: XPN has published a new version of his exploit.
Thx @GossiTheDog.
-
Now we know why this month’s Win7 Monthly Rollup, KB 4093118, installs itself over and over
Our own abbodi86 traced down the problem.
You gotta wonder who’s putting together these kludges for Microsoft’s second-most-popular version of Windows. Half a billion users. Billions and billions of bucks. And a dumb mistake that has some Win7 users pulling their hair out.
Computerworld Woody on Windows.
UPDATE: Abbodi86 has a more detailed analysis — and a fascinating discussion of the different levels of metadata — here. He also has a suggested fix for Microsoft, if they’re listening.
It looks like Microsoft needs to fix things before the May Monthly Rollup, to avoid the same endless re-installation problems.
-
The gift that keeps on giving: Win7 Monthly Rollup KB 4093118 installs over and over
Short version: Microsoft released a buggy Win7 Monthly Rollup this month, KB 4093118. Then, last week, it quietly replaced the buggy version with a new version.
Now there are reports everywhere that this new version installs itself — 5, 7, 12 times — and keeps on demanding to be installed again.
You can do it.
Computerworld Woody on Windows.
-
Patch Lady – B patchers need a pre patch
 Business patchers: Right now you should still be in “test” mode in installing patches, not production roll out mode. For those that install the Windows security only updates for Server 2008 R2 and Windows 7 – your April update is KB4093108. Make sure you install KB4099950 FIRST to prevent the issue where static IP address settings were lost in the network interface card. If you are wondering how to do this in WSUS, set a deadline in WSUS in the past which will kick an immediate install. It does not kick a reboot. Then schedule the April update after that.
Business patchers: Right now you should still be in “test” mode in installing patches, not production roll out mode. For those that install the Windows security only updates for Server 2008 R2 and Windows 7 – your April update is KB4093108. Make sure you install KB4099950 FIRST to prevent the issue where static IP address settings were lost in the network interface card. If you are wondering how to do this in WSUS, set a deadline in WSUS in the past which will kick an immediate install. It does not kick a reboot. Then schedule the April update after that.I’m still trying to get definitive information as to whether the 2008 R2/Windows 7 April update rollup KB4093118 does or does not include this fix.
There are indications from the Patchmanagement.org list that it does include the fix in KB4099950 and thus you don’t need to install that proactively, but I can’t find it documented anywhere to be 100% certain.For standalone computers that use the B patching process of applying security only updates- again you should be in wait and see mode right now. If you have a spare computer and want to live on the edge, install now. Otherwise get the popcorn out and wait to see what happens.
P.S. you have to manually import KB4099950 into WSUS to get it up there. It’s not in the WSUS patches. To import follow this blog.
Update: The KB4093118 now states this confirming it does NOT include it and implies that KB4093108 does include the networking fix so if you are a Security only B patcher you don’t have to worry about it. It also includes a workaround for the memory leak issue and I’ll address that in another blog post:
After installing KB4056897 or any other recent monthly updates, SMB servers may experience a memory leak for some scenarios. This occurs when the requested path traverses a symbolic link, mount point, or directory junction and the registry key is set to 1:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\LanManServer\Parameters\EnableEcp
Microsoft is working on a resolution and will provide an update in an upcoming release.
***
A stop error occurs on computers that don’t support Streaming Single Instructions Multiple Data (SIMD) Extensions 2 (SSE2).
Microsoft is working on a resolution and will provide an update in an upcoming release.
***
A new Ethernet Network Interface Card (NIC) that has default settings may replace the previously existing NIC, causing network issues after you apply this update. Any custom settings on the previous NIC persist in the registry, but are unused.
Microsoft is working on a resolution and will provide an update in an upcoming release.
In the meantime, please apply KB4093108 (Security-only update) to stay secure, or use the Catalog release of KB4093118 to stage the update for WU or WSUS.
***
Static IP address settings are lost after you apply this update.
Microsoft is working on a resolution and will provide an update in an upcoming release.
In the meantime, please apply KB4093108 (Security-only update) to stay secure, or use the Catalog release of KB4093118 to stage the update for WU or WSUS.


