Newsletter Archives
-
Microsoft re-releases Intel microcode patches for all versions of Win10
Last night, Microsoft released these new Intel microcode patches:
KB 4100347 for Win10 1803
KB 4090007 for Win10 1709
KB 4091663 for Win10 1703
KB 4091664 for Win10 1607
KB 4091666 for Win10 1507And there’s an official Summary of Intel microcode updates. You can stop yawning now.
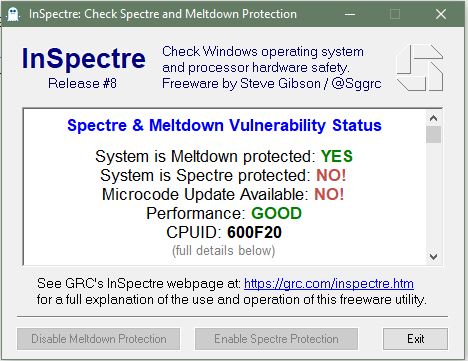
The updates seem to be directed at Spectre 2. Remember, we’re looking at Spectre Vn where n = 1, 2, 3, 3a, 4, and the Spectre NG series where n = 1.1, 1.2, 1.3, 1.4, 1.5, 1.6, 1.7 and 1.8. If I read the tea leaves correctly.
Of course, Spectre (and Meltdown) don’t exist in the wild. Many people feel that the chances of them ever appearing are very slim because it’d take a whole lot of work to get them going and parse the incoming data.
Those of you who run servers with multiple users and sensitive data might be concerned. The rest of us… Meh.
UPDATE: Günter Born has a great exploration of the patches, WSUS, and a Microsoft bot on his Born City blog.
-
Microsoft offers more Spectre v2 microcode updates, KB 4090007, KB 4091663, KB 4091664
Yesterday, I posted a note about two new Spectre v2 patches, KB 4078407 and KB 4091666.
The first is a Win10-only fix that has to be combined with a microcode change from your hardware manufacturer in order to accomplish anything. As @abbodi86 notes:
KB4078407 is not a patch, it’s just an executable that enables the Spectre mitigation protection by changing two registry entries
The second is a microcode-only, Intel-only, Win10 1507-only patch that changes the microcode for a large number of Intel processors.
This morning, Günter Born notes on Borncity that there are now four of these microcode patches:
- KB4090007 for Win10 1709/”Server 2016 version 1709″
- KB4091663 for Win10 1703
- KB4091664 for Win10 1607/Server 2016
In addition to the one I described yesterday, KB4091666 for Win10 1507.
None of them are available through Windows Update. You have to manually dig into the Update Catalog to get them.
As noted (voluminously) there are no known exploits as yet for Meltdown, Spectre v1 or Spectre v2. You might want to tuck these away in case we ever see a reason to use them.
-
So tell me again what’s happening with the two new Spectre v2 patches, KB 4078407 and KB 4091666
Yesterday, Microsoft released two patches that tackle the Spectre v2 vulnerability — the one that’s never been seen in public.
The first patch, KB 4078407, is a Windows 10-only fix that has to be combined with a microcode change from your hardware manufacturer in order to be effective.
The second patch, KB 4091666, is a microcode-only, Intel-only, Win10 1507-only patch that covers a lengthy list of affected Intel processors. The KB article says:
This update is a standalone update available through the Microsoft Update Catalog and targeted for Windows 10 Release To Market (RTM). This update also includes Intel microcode updates that were already released for these Operating Systems at the time of Release To Manufacturing (RTM). We will offer additional microcode updates from Intel thru this KB Article for these Operating Systems as they become available to Microsoft.
… which is as muddled a bunch of gobbledygook as I’ve ever seen in a KB article. If you can parse it, tell me. All I know for sure is that the Microsoft Update Catalog entry tells me that the patch is only for Win10 1507.
You may recall that Microsoft released KB 4090007 back in March. It was intended to provide Intel-offered microcode patches to Win10 1709 machines for 6th gen Skylake processors, but it mutated several times — to the point that I don’t know what it does now.
Of course, there’s no advice about the obvious overlap between KB 4090007 and KB 4091666.
Sigh.
-
Microsoft “helps” Intel by releasing KB 4090007, a Spectre 2 microcode update for Win10 1709, Skylake processors only
UPDATE: Correcting myself (thanks to the anonymous poster) — this is a microcode update, which is kind of a transient firmware override, for lack of a better description. There’s a more thorough description on the Debian wiki, “Processor microcode is akin to processor firmware. The kernel is able to update the processor’s firmware without the need to update it via a BIOS update. A microcode update is kept in volatile memory, thus the BIOS/UEFI or kernel updates the microcode during every boot.”
I can’t recall ever seeing Microsoft issue a firmware update (other than a Surface firmware update) as a security patch. This one comes with its own KB, no less.
The announcement is very specific. KB 4090007 only deals with the Spectre Variant 2 / CVE 2017-5715 (“Branch Target Injection”) mitigation, and only on 6th generation Skylake H/S, U/Y and U23e processors. It’s only for Win10 1709. It’s not a cumulative update.
And — importantly — it’s an Intel microcode update. Not a Windows patch.
Says Microsoft:
We will offer additional microcode updates from Intel as they become available to Microsoft. We will continue to work with chipset and device makers as they offer more vulnerability mitigations.
which is a noble goal, at least to my way of thinking.
You won’t get the patch via Automatic Update. If you really, really want to test it on your Win10 1709 / Skylake machine, you can download it from the Microsoft Update Catalog and manually install.
Spectre v2 is a vulnerability in just about everything — Intel, AMD, ARM. As I’m fond of repeating, neither Meltdown nor Spectre (either variant) has been found in the wild.
As you might imagine, I’m highly skeptical. I mean… what could possibly go wrong?