Newsletter Archives
-
MS jiggles — but doesn’t fix — buggy Win7 patches KB 4088875, KB 4088878
A big shake-up last night re-arranged the way the buggy March Win7 patches install and clean up after themselves and adds to the lengthy list of known bugs. The key looming bug — “Total Meltdown” — remains a patching enigma: Dammed if ya do, dammed if ya don’t.
Computerworld Woody on Windows.
-
New versions of buggy March Win7 patches are out
I have no idea what changed, but Günter Born reports (and a check of the Update Catalog confirms) that there are new versions of:
KB 4088875 – Win7 March Monthly Rollup (dated, in the Update Catalog, as April 4)
KB 4088878 – Win7 March Security-only patch (also April 4)
KB 4088881 – Preview of the Win7 April Monthly Rollup (also April 4)
KB 4090450 – Spectre V2 patch for Server 2008 (dated April 3)
Looking at the KBNew page, I also see new versions of:
KB 4099950 – the hotfix patch for bugs in the March Win7 patches (now dated April 4) – I talked about this fix of a fix of a … earlier this week in Computerworld.
KB 4088879 – the Win8.1 Security-only patch (still dated March 10)
And, as noted in several places on AskWoody, there’s a new version of the old favorite KB 2952664 — the patch that so helpfully makes it easier to upgrade Win7 to Win10 — and its Win8.1 cohort, KB 2976978.
Born identifies new notes in the KB articles for the Win7 Monthly Rollup and the Preview Monthly Rollup that say:
Important Please apply KB4100480 immediately after applying this update. KB4100480 resolves vulnerability in the Windows kernel for the 64-bit (x64) version of Windows. This vulnerability is documented in CVE-2018-1038 .
You may recall that KB 4100480 is the “OMG” patch issued by MS when they figured that all of this year’s Win7 patches opened a huge “Total Meltdown” security hole in Win7.
In addition, the description of the KB 4088875 Monthly Rollup patch and the KB 4088878 Security-only patch now advise:
After you install this update, you may receive a Stop error message that resembles the following when you log off the computer:
SESSION_HAS_VALID_POOL_ON_EXIT (ab)
The solution on offer is KB 4099467, which is a single-shot hotfix for Win7 designed specifically to fix this bluescreen.
How about them apples….
Can any of you shed light on the reasons for the changes — in particular, do they fix any of the gazillion security holes in last month’s patches? If so, care to speculate on why Microsoft just slipped this stuff out without any announcement?
And… when will it be safe to get back in the Win7 patching water?
-
Patch Lady – KB4088875 side effects to watch out for
 Following up on the March Windows 7/Server 2008 R2 patch situation of KB 4088875 …. uh ..mess, I saw another side effect of the known issues.
Following up on the March Windows 7/Server 2008 R2 patch situation of KB 4088875 …. uh ..mess, I saw another side effect of the known issues.First off a bit of background, as Woody pointed out we are in a darned if we do/darned if we don’t mode right now in Windows 7/Server 2008 R2 updating. On Windows 7 and Server 2008 R2 Microsoft is still “throttling” this update when offered up from Microsoft update – that is it’s still offered up but unchecked and thus it won’t automatically install, however it has not been pulled of the Catalog site, nor expired from WSUS (Windows Server Update Service) which is my benchmark for being “pulled”. Therefore it’s not been officially pulled by Microsoft but it sure is in this limbo state.
There is a new script that is recommended to be run on machines with static IPs before installing – and yes you can run the script ahead of time.
Based on what I’ve seen the issues and side effects are more critical on Server 2008 R2:
Reputable reports from several consultants that are monitoring and patching Small Business Server 2011 machines that the “memory leak” side effect will cause remote web access to time out and fail to work.
After you install this update, SMB servers may leak memory. Microsoft is working on a resolution and will provide an update in an upcoming release. For now the consultants are removing this update and holding off to see what Microsoft does to fix this hopefully in April.
A couple of other reports of blue screens of death that were resolved after uninstalling the update.
Also for those in the B patching category, be aware of a new side effect showing up today so if you have installed the March updates, you may want to install the March 23 IE update. If you have not installed these March updates, hang loose until April’s updates.
After you install this update, security settings in some organizations that are running Windows 7 SP1 or Windows Server 2008 R2 may prevent Internet Explorer 11 from starting because of an invalid SHA1 certificate. Whitelist the SHA1 certificate to allow Internet Explorer 11 to start. – OR –
Install Cumulative update for Internet Explorer: March 23, 2018.
To all of this, I’m just wincing and hoping that we can get back to a bit more normal in April (I’m an optimist). While patching an older operating system does get a bit more bumpy as we get to it’s end of life, 41% is still a lot of boxes that are sitting out there possibly unpatched.
-
Patch Lady – KB4088875 more questions
 The following update has had a revision: KB4088875 But in doing so I’m scratching my head a bit more.
The following update has had a revision: KB4088875 But in doing so I’m scratching my head a bit more.Remember our original side effects relate to networking issues and loss of a static IP upon reboot:
A new Ethernet virtual Network Interface Card (vNIC) that has default settings may replace the previously existing vNIC, causing network issues after you apply this update. Any custom settings on the previous vNIC persist in the registry but are unused. Microsoft is working on a resolution and will provide an update in an upcoming release. Static IP address settings are lost after you apply this update. Microsoft is working on a resolution and will provide an update in an upcoming release. On the page on KB4088875 a script is now linked and the following wording has been added:
Prerequisites
Follow these steps before you apply this update to a physical computer or a virtual machine:
- Back up the following registry key and subkey:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\PCI
- Copy the following VBScript (VBS) code, paste it into Notepad, save the file with a “.vbs” extension, and then run the .vbs file.Note The script also includes binary version checks around PCI.SYS file.
(note the KB has the script in detail)
Okay so here are my questions:
- Is this needed for all deployments or only where a static IP has been used? As I’ve seen the loss of networking side effect more where a static IP was assigned to the network adapter.
- Can an admin run this script before the install of the update? (based on admins testing this it appears the answer is yes)
- In a consumer setting, where we only go to Windows update, do we need this? (I don’t think so but it would be nice to know for sure)
- If we’ve already installed the update, should we run this script? (again, I don’t think so but it would be nice to know for sure)
Right now I only have questions, not answers but here’s my mode of attack:
- If it’s a workstation where I have physical access and can easily fix any networking stack issue I’ve installed the update as is and honestly have had no issues. I am mostly deploying this in settings where my router is handing out the DHCP and I’ve seen no issues.
- If it’s a server, I’m deploying this based on how comfortable I am with alternative ways to reach that server and deal with patching issues. If I can walk over to the server, I’ve gone ahead and patched. If I’m remote to the server, it depends on if there is a remote network management tool like an iLO or Drac (HP or Dell) and/or how responsive the support team is in the datacenter.
The side effect of losing networking still feels like there is some other trigger at play in non VMware shops. I’ve seen people report the issue mostly where a static IP has been assigned.
One concern as Woody has already pointed out, next month’s preview of non security updates already has the same side effect.
So bottom line, determine your zeal for updating, throw a bit of salt over a shoulder, squint your eyes real tight, and keep your fingers crossed while you update. Hey, wouldn’t hurt would it?
-
Macrium Reflect triggers BSOD on 32-bit Win7 systems after installing KB 4088875, this month’s Monthly Rollup
There aren’t a lot of details just yet, but Macrium has posted a warning:
After installing the Windows 7 update patch released on 13th March 2018, 32 bit installations of Macrium Reflect may cause Windows to be unable to restart. The error displayed in the BSOD is:
pagefault_in_non-paged_area pssnap.sys
We believe that this is related to the Spectre meltdown protection added in the Windows update KB 4088875.
Windows 10 32 bit installs that have been upgraded from Windows 7 may also received this error.
Also not clear if the bluescreen strikes after installing the Security-only downloadable patch KB 4088878.
Thx, @cesmart4125.
-
Patch Lady – KB 4088875 issue acknowledged
 Microsoft has officially acknowledged the issue Woody pointed to yesterday.
Microsoft has officially acknowledged the issue Woody pointed to yesterday.In the release notes of KB 4088875 this is now listed:
A new Ethernet virtual Network Interface Card (vNIC) that has default settings may replace the previously existing vNIC, causing network issues after you apply this update. Any custom settings on the previous vNIC persist in the registry but are unused. Apply the resolution documented in KB3125574 (Convenience Rollup) for Known issue 1: A new Ethernet virtual Network Interface Card (vNIC) that has default settings may replace the previously existing vNIC, causing network issues after you apply this update. Any custom settings on the previous vNIC persist in the registry but are unused.
IP address settings are lost after you apply this update. Microsoft is working on a resolution and will provide an update in an upcoming release. -
Buggy Windows 7 Monthly Rollup KB 4088875 — no acknowledgment from Microsoft
Microsoft no longer installs the Win7 March Monthly Rollup automatically, but KB 4088878 is still available in the Update Catalog. Aren’t you glad you held off on patching this month?
Computerworld Woody on Windows.
UPDATE: Microsoft now acknowledges the IP address setting bug. From KB 4088875:
A new Ethernet virtual Network Interface Card (vNIC) may be created with default settings in place of the previously existing vNIC, causing network issues after applying this update. Any custom settings on the previous vNIC are still persisted in the registry but unused.
Apply the resolution documented in KB3125574 (Convenience Rollup) for Known issue 1:
IP address settings are lost after applying this update.
Microsoft is working on a resolution and will provide an update in an upcoming release.
You really have to wonder who’s testing this stuff.
-
Patch Lady – Networking issues and KB 4088875
 As Woody pointed out earlier today there are some reports of networking issues after the install of this month’s Server 2008 r2 and Windows 7 patch. The issues are not widespread and they appear to be limited to two scenerios:
As Woody pointed out earlier today there are some reports of networking issues after the install of this month’s Server 2008 r2 and Windows 7 patch. The issues are not widespread and they appear to be limited to two scenerios:Scenerio 1 – VMware. As noted on a reddit post a new virtual Ethernet network card is installed/enabled after the update. The side effect has occurred before with other convenience rollups and a workaround was previously posted to this KB and a script is provided to fix the issue. It is not impacting all servers, it appears to be impacting virtual machines on VMware.
You can see more threads here.
Scenerio 2 – workstations. This one is a bit more fuzzy and not clear cut. I’ve seen reports where workstations with static IPs may be impacted with this update. There are definitely enough credible reports of chipsets being reset and losing their networking IP addresses.
Note that I’m seeing this more in businesses than in consumer/peer to peer settings.
On my Windows 7 (my old machine that we keep around for older programs), I’m seeing this update unchecked:
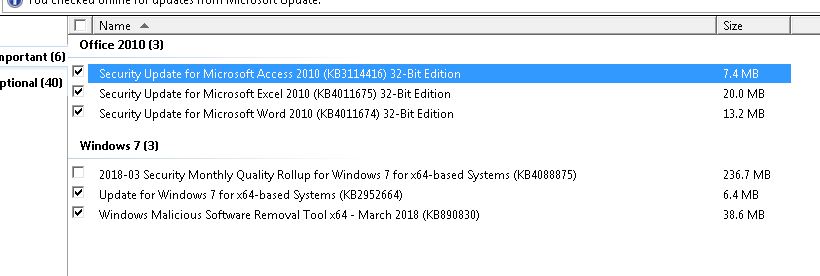
Which normally means that Microsoft is throttling the patch while they monitor issues.
What is honestly a bit more concerning is this documented side effect:
After installing this update, SMB servers may leak memory. Microsoft is working on a resolution and will provide an update in an upcoming release. If you run a file server, you may want to run tests and determine if you do see THIS side effect as that one may impact.
More on this as I see issues.


