Newsletter Archives
-
2000011: Group A, Group B and Group W – what’s the difference?
@elly has kindly put together an overview for you Win7 and 8.1 users.
If you aren’t quite sure if you want to be in Group A, Group B, or Group W — when it comes to struggling with patches — check out AKB 2000011.
-
New Windows 7/8.1 updating method coming
It’s almost time to move the MS-DEFCON level, but when I do, I want to get it right – and get your input.
As you all know, I’ve recommended “Group A” – install all Rollup patches – to folks who don’t mind the added snooping. I’ve also recommended “Group B” to those who want the security updates only. I’ve acknowledged, but not recommended “Group W” for those who never patch.
The world’s changed since last October.
With Shadow Brokers guaranteeing that major Windows vulnerabilities are coming every month – I call it “Malware as a Service” – Group W is just plain dangerous. It’s not an option. Sorry.
Group B, which is based on Microsoft’s commitment to deliver Security-only updates every month, has gone from relatively simple to very complex. Officially, Internet Explorer patches have been broken off from the main download. There’s all sorts of confusion about .NET patches — which are Security-only, which Rollups? We’ve seen security patches released outside the monthly Security-only stream. There have been bugs in Security-only patches that were fixed outside of the Security-only stream. There’s a host of problems documented in this Topic.
Group B isn’t dead, but it’s no longer within the grasp of typical Windows customers. Many of you reading this post are fully capable of sticking with Group B. Most Windows customers are not.
Starting this month, I’ll mention Group B in my InfoWorld posts and the MS-DEFCON posts here — but I won’t include details. Instead, I’ll refer you to the AskWoody KB article AKB 2000003, maintained by PKCano. We’ll modify that AKB article with generic installation instructions. The MS-DEFCON level will apply to Group B folks, too, but the instructions most people see won’t include the Group B details.
Which leaves me with new adornments for Group A. Starting this month, I’m going to recommend that just about everybody move to Group A, and install the Monthly Rollups (waiting until we’ve had time to thoroughly vet the patches, of course).
For those of you who are sensitive to the manifest (but still undefined) snooping included in Win7 and 8.1 updates, I’ll include instructions for reducing – but not eliminating – Microsoft’s “telemetry.” As a reader here, I’m looking for your input, but keep in mind that:
- What you recommend can’t hurt anything other than telemetry.
- Novice “For Dummies” level users have to be able to understand what’s involved, and how to do it.
- I don’t want to recommend a third party app. Yes, I know there are apps that block telemetry.
There are three approaches that have caught my eye:
- A short list of KB numbers, listing patches that should be removed. @PKCano has an example in the AKB 200003 documentation.
- A simple batch script, like the one @abbodi86 maintains. The problem is that some people will have a hard time figuring out how to run it.
- A combination of directions, as @MrBrian has proposed.
I realize that Microsoft has promised that it will release a completely cumulative update for Win7 — a Service Pack 3, if you will, available through Windows Update — at some point in the future. I don’t think we have the luxury of waiting for Microsoft to get its act together.
I think, given the Shadow Brokers promise, that we need to come up with a solution now — and pick up the pace, shortening the length of time between the release of Monthly Rollups and a go-ahead, through the MS-DEFCON level, when it’s safe to install.
Don’t get me wrong. Automatic Update is still for your Great Aunt Martha, who doesn’t want to follow along, and can’t be trusted to apply patches consistently. For those of you who can take your patches proactively, waiting a week or two is still the best way to go.
What do you think? What would you recommend for Group A anti-snooping instructions?
-
The case for not updating Windows 7. Ever.
When I wrote in InfoWorld about the Windows 7 and 8.1 “patchocalypse” – last month’s abrupt change in the way Microsoft patches Win7 and 8.1 – I described two groups. I called them “Group A” and “Group B” (imaginative, eh?). In broad terms:
- Those in Group A are willing to take all of Microsoft’s new telemetry systems, along with potentially useful nonsecurity updates.
- Those in Group B don’t want any more snooping than absolutely necessary, and they don’t care about improvements like daylight saving time zone changes, but want to keep applying security patches.
I also described the hold-outs:
A third group, Group W, doesn’t want anything from Microsoft — no patches, no security updates, nada. I don’t recommend that you sit on the Group W bench, but it can be understood given changes Microsoft has made to Win7 and 8.1 machines, without our permission, in the past.
Since that time, I’ve written a lot of words about Group A and Group B. There are procedures, and nuances, for both. But I’ve generally avoided writing about Group W (named in homage to Arlo Guthrie; some people call it Group C). There’s a reason why.
I have a recurring nightmare – no, really – where somebody comes up with a really pernicious piece of malware that knocks out unpatched Win 7 and 8.1 machines, even when the owners of those machines are super-cautious. I’m talking about responsible Group W benchers who use alternative browsers (Firefox, Chrome), never click on anything that looks remotely dicey, and religiously run both antivirus programs and periodic antimalware scans.
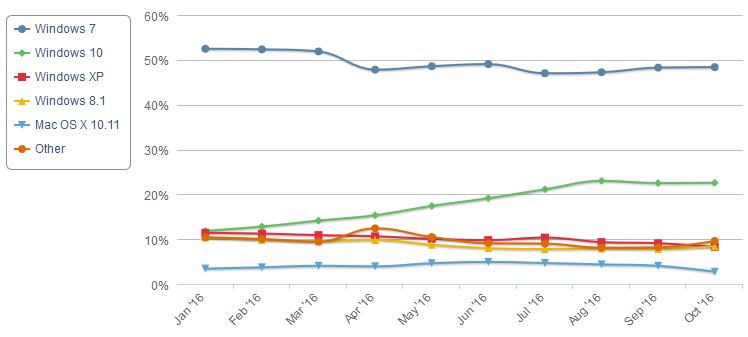
I would never forgive myself for recommending a course of action that puts a big swath of Windows 7 users in harm’s way. After all, Windows 7 still accounts for about half of all PC use world-wide, and it’s likely to continue to be the dominant desktop operating system for years to come.
Source: NetMarketShare
I’m convinced that Group A (Monthly rollup) and Group B (Security-only updates) are viable alternatives, but there’s a lurking demon in the Group B closet. If we ever get a bad bug in a Security-only update, and that bug is fixed in a non-security Monthly rollup, all bets are off. If Microsoft breaks something in a Security-only patch, they need to fix it in a Security-only patch. Otherwise, those who only install Security-only patches are going to end up with bug-infested systems.
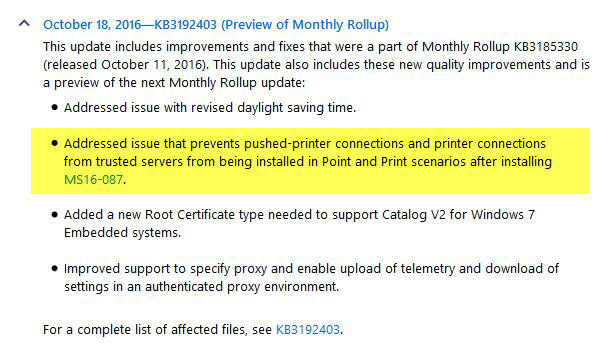
I’ve fretted over this problem in many of my InfoWorld blogs these past two months. In fact, we’ve already seen a minor example, where a Security-only update bug in MS16-087 was fixed in a non-security part of a Monthly rollup. Microsoft documents it here:
As best I can tell, that bug hasn’t been fixed in a Group B Security-only update. It may never be fixed in a Security-only update. That means someone who sticks to Group B and only installs Security-only updates will have the flaw in MS16-087 forever.
That’s simply inexcusable, even if the bug only affects a small number people in an esoteric way, even if Microsoft has documented complex manual fix instructions.
So we’re stuck between a rock and a hard place. On the one hand, Group B seems like an excellent approach for those who don’t want Microsoft’s Windows 7 snooping enhancements. On the other hand, if Microsoft can’t fix its own mistakes in Group B, there’s nothing you or I can do about it.
With that as background, I’ve asked Canadian Tech – who slogs through these problems with hundreds of users – to repeat a recommendation he’s made many times:
It now appears that B is an impractical strategy for 99% of users. And, here is the reason why: When an error is made in a security-only update, if the error turns out not to have a security affect, it may be corrected in a non-security update. In that case if you were following B strategy, you would be left with an un-corrected defective update installed on your computer. If you were extremely diligent and knew about it, you may be able to get the correction in specific cases. This would entail an extreme amount of diligence that few would be willing or able to provide.
The new rollup style of updates that Microsoft is now providing to what we would call Group A, which include all kinds of updates (security and non-security), are cumulative. That means if you miss a month or even more, it will not matter because by installing the latest month’s rollup, you would be up to date.
NOTE well, that Security-only updates are NOT cumulative. Which means if you miss a month, you may never get the missed updates.
So one strategy that you may wish to consider is following Group C, but still updating .net and Microsoft Office through Windows Update, but installing no Windows updates at all. It would be advisable in this case that you stop using Internet Explorer because you would not be getting those updates, but instead use an alternative browser.
Then, after following this strategy for some time, if things take a turn for the worse, and you decide you made the wrong choice (Group C with .net an Office updates), you can easily shift to A by simply using the latest offered Rollup offered in Windows Update.
So, as things have evolved, it looks like the vast majority have really only two choices: A as described above or C (modified as described above). The good news is that if you follow the modified C strategy, you have a way back to the Microsoft way, that is easy to implement.
There’s been an extensive discussion of Canadian Tech’s advice on the “Malwarebytes stumbles with false positive on KB 3197868, the Win7 November Monthly Rollup” post. Unfortunately, WordPress makes it very difficult to move comments from that post to this post, so I would ask those of you with strong opinions to please restate them (or copy and paste them) into the comments here.