Newsletter Archives
-
MS-DEFCON 5: Get your systems patched
The problems this month — which is to say, the December patches — are relatively benign (as long as you aren’t manually installing WIn7/Server 2008 Security-only patches). If you’re running Win10 version 1903, life’s much simpler.
Step-by-step instructions in Computerworld Woody on Windows.
P.S. Yes, that’s an MS-DEFCON 5. Get ’em while the gettin’s good.
-
Where we stand with the December 2019 updates
It was a hairy month for many admins. Individual users didn’t have quite so many problems.
My usual monthly rundown of problems with Microsoft patches — December 2019 edition — is in Computerworld Woody on Windows.
We’re still on MS-DEFCON 2. No need for normal users to get patched just yet.
-
Reported problem with Drive Mappings after installing this month’s Win10 1909 cumulative update, KB 4530684
The bugs keep rolling in.
shaun calton reports:
Just had an interesting blip on my Windows 10 -1909 device with the 12-2019 Cumulative Update (KB4530684).
After the update was installed and the PC was restarted, I noted that my Drive Mappings were no longer available and my AD management tools could not find the domain to PC is bound to. The associated message was that Naming was not available due to the RPC server not being available.
Rolling the update back has corrected the issues but I wanted to put this out there for anyone listening.
Can you confirm?
-
Installing November’s Win7 Servicing Stack Update KB 4523206 may lock up your PC
Report in from Seff :
Since installing the monthly rollup and service stack update on my main Win7 x64 on Friday, the machine booted and ran normally yesterday but today has black screened on reaching the desktop. It booted normally in safe mode, and on happening again in normal mode I was able to ctl-alt-del and open task manager when I experimented with ending and restarting explorer.exe which resulted in the desktop appearing. I’ve since rebooted to see if that fixed it, and it waited for several minutes on the “Welcome” screen before the desktop appeared normally.
and from hms:
… on 2 laptops (one is Pro; other is Home) that have not been problematic heretofore. They get hung on “Welcome” after selecting user. This started after restarting them the day after installation of svc stack.
After the suggestion, ran scannow; nothing found.
Tried to uninstall SSU KB4523206; cannot be uninstalled.
Then did system restore just prior to SSU install. This seems to work; I have restarted it a couple of times and it logs into the user right away.
Looks like a complete rollback is the best bet at this point. Any better ideas?
-
Windows Server 2012 (not R2) goes into reboot loop after installing .NET patch KB 4533096
I’m seeing many reports of reboot loops after folks install KB 4533096 – the “Security and Quality Rollup for .NET Framework 3.5, 4.5.2, 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2, 4.8 for Windows Server 2012 ”
From Pradeep Soni on the Patchmanagement list:
Post installation server stuck in reboot loop with onscreen repetitive notifications, “Notifying services that Windows is shutting down -> Stopping services -> Restarting”.
Later, pressed F8 to bring out the Advanced Boot Options and selected “Start Windows Normally” and server booted without any issues. Again restarted the server and it came up normally and no further issues detected.
Apparently you can also boot into Safe Mode. That boot won’t work, either, but your next normal boot will.
UPDATE: It’s possible that this month’s MSRT is at fault, instead of the .NET patch. Note this thread on the Technet forum that describes the same problem with the November MSRT update.
This Spiceworks thread talks about this month’s problem, but (so far) the culprit hasn’t been identified.
-
December 2019 Patch Tuesday foibles and quibbles
Microsoft has officially yanked the bogus Autopilot patch, KB 4532441, that some of you saw yesterday. Reminds me a lot of the same stupid thing in October.
The new MSRT appeared several hours after the rest of this month’s patches.
And that new end-of-life nag for Win7 has a bypass – if you’d rather change a registry key, instead of clicking to dismiss it permanently. (Or if you don’t trust Microsoft to do what they say.)
Screenshot of the nag, thx @Microfix
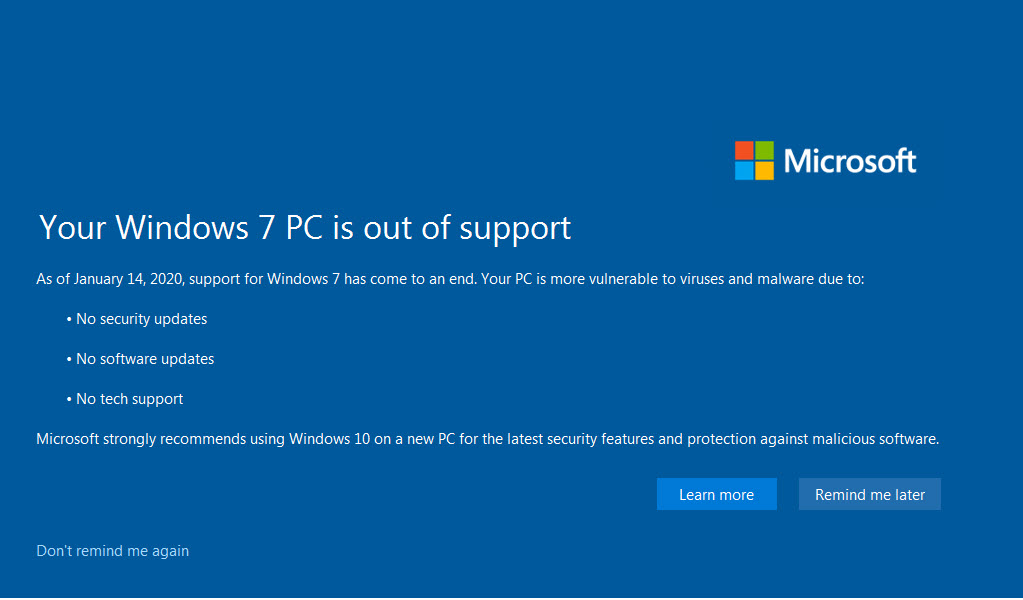
Credit: Taken on my Seven Semper Fi test machine
Full details in Computerworld Woody on Windows
-
December 2019 Patch Tuesday running commentary
I’m looking at 133 downloadable patches on the Update Catalog.
Dustin Childs reports on the Zero Day Initiative blog:
Microsoft released security patches for a mere 36 CVEs [separately identified security holes]. While this is a much lower quantity of CVEs compared to other months, it is quite common for Microsoft to have a light December release. None of the patches released this month are listed as publicly known, but one is listed as being actively exploited at the time of release.
That exploited security hole, CVE-2019-1458, is described as:
To exploit this vulnerability, an attacker would first have to log on to the system. An attacker could then run a specially crafted application that could exploit the vulnerability and take control of an affected system.
I’m not going to lose any sleep over it.
Martin Brinkmann has his usual thorough report on ghacks.
Remarkably, according to the Update History page, the 1903 and 1909 patches have not diverged just yet. It’ll be interesting to see if MS fixed the File Explorer Search bugs in 1909 that have been widely reported.
Mary Jo Foley reports that the Win7 Monthly Rollup includes a nag screen about upgrading to Win10. (The Security-only Update also includes the nag screen.) Sure enough, the Monthly Rollup KB article says:
IMPORTANT Starting on January 15, 2020, a full-screen notification will appear that describes the risk of continuing to use Windows 7 Service Pack 1 after it reaches end of support on January 14, 2020. The notification will remain on the screen until you interact with it. This notification will only appear on the following editions of Windows 7 Service Pack 1:
- Starter.
- Home Basic.
- Home Premium.
- Professional. If you have purchased the Extended Security Update (ESU), the notification will not appear. For more information, see How to get Extended Security Updates for eligible Windows devices and Lifecycle FAQ-Extended Security Updates.
- Ultimate.
Note The notification will not appear on domain-joined machines or machines in kiosk mode.
Looks like an uncharacteristically drama-free bunch of patches. (Although it’s typical for December.) We’ll keep you posted on any identified bugs, of course.
UPDATE: AutoPilot’s back – Win10 1909 Pro users are being offered an AutoPilot fix — even if they don’t have AutoPilot. The KB article has been updated to say it’s been re-issued. Back in October, MS admitted that the AutoPilot patch had been pushed to Pro users incorrectly – and that it was offered repeatedly, even after it was installed. Wonder if we’ll see it pulled again?
And the 1909 cumulative update doesn’t fix the File Explorer Search bug. See this Reddit thread.
-
MS-DEFCON 2: Make sure automatic update is blocked
Tomorrow’s Patch Tuesday. Now’s a good time to double-check and make sure the patches won’t hit you the minute they roll out the Windows Update chute.
Step by step instructions in Computerworld Woody on Windows.


