Newsletter Archives
-
Patch lady – targeted attacks using zero day
Per https://www.zdnet.com/article/google-discloses-windows-zero-day-exploited-in-the-wild/:
On Twitter, Hawkes said the Windows zero-day (tracked as CVE-2020-17087) was used as part of a two-punch attack, together with another a Chrome zero-day (tracked as CVE-2020-15999) that his team disclosed last week.
“We have confirmed with the Director of Google’s Threat Analysis Group, Shane Huntley, that this is targeted exploitation and this is not related to any US election-related targeting.”
It will be patched November 10th.
So the good news is that this is targeted only – not by us mere mortals. Until then keep your tinfoil on and in the ready mode
-
OMG! Run for the hills! FIVE new Windows zero-days published

I love the headlines these days. “Microsoft warns meeeeelions of customers that the world is coming to an end!” “New zero-days announced and you better get patched NOW!” “Microsoft says your computer is at risk from Snidely Whiplash or somebody who looks just like him.”
I just read a tweet from Catalin Cimpanu — the ZDNet security guy — that puts a refreshing spin on things.
Seems that late last week the Trend Micro Zero Defense Intiative, ZDI, published descriptions of five new Windows zero-days. Four of the five are Privilege Escalation Vulnerabilities. (OMG! Those are the WORST KIND.) Microsoft (those scoundrels!) didn’t patch them quickly enough, so ZDI acted according to its conventions – waited four months to give Microsoft time to fix the hole – and then published “a limited advisory.” I can read the Forbes headline already: More than a billion Windows users at risk and there’s no fix. Take THAT, you languid Windows lizards!
Meh.
The five zero-days aren’t very interesting. Microsoft told ZDI they wouldn’t be patching them any time soon. ZDI has a policy of disclosing what they’ve found if a particular security hole isn’t fixed in 120 days. Thus, the post.
Here’s what Cimpanu says:
These appear to be the most harmless 0-days in the history of 0-days, so no need to panic… and most likely the reason MSFT didn’t hurry to patch them
And that seems, to me, to describe the situation perfectly.
-
How long has it been since we had a patched 0day that jumped up and bit us?
I’m in the middle of a Tweetstorm – par for the course – but had an interesting response to one of my standard questions. The question goes like this:
Can you tell me one, single, zero day patch that resulted in mainstream malware within, let’s say, a few weeks of release? Just one.
I got a well-researched response. (Most of them are long on accusations and short on research – and make for amusing reading.) Here’s the list:
- WannaCry
- Blaster
- Sasser
To my mind, the best feedback I get is from people who take the time to think through their positions and come up with cogent arguments. That list prompted me to go back and check what really happened. Here’s what I found:
- WannaCry/EternalBlue – patched April 11, 2017. Exploited May 12, 2017. More than a month from patch to exploit – and it was a bad exploit! UPDATE: Andy Greenberg at Wired just published an excellent story about Marcus Hutchins, the guy who corralled WannaCry.
- Blaster – patched May 28, 2003. Exploited August 11, 2003. Almost three months.
- Sasser – patched April 13, 2004. Exploited April 30, 2004. Two weeks to exploit, and that’s scary. But it was 16 years ago.
Have I missed something? Can you find a zero-day exploit that was patched, and then widely exploited within a few weeks of the patch?
-
Google comes clean on that “emergency” security patch – and shows how it was used to trigger a Windows 7 0day
Now I understand.
Google releases patches for its Chrome browser all the time. As @b explained about 36 hours ago, Google sent out a special alert to get Chrome updated specifically to head off a 0day attack.
I didn’t get too excited about it because Chrome automatically updates itself quite reliably, and because the threat didn’t seem to be all that great.
A few hours ago, Clement Lecigne of the Google Threat Analysis Group added some key details:
On Wednesday, February 27th, we reported two 0-day vulnerabilities — previously publicly-unknown vulnerabilities — one affecting Google Chrome and another in Microsoft Windows that were being exploited together.
To remediate the Chrome vulnerability (CVE-2019-5786), Google released an update for all Chrome platforms on March 1; this update was pushed through Chrome auto-update. We encourage users to verify that Chrome auto-update has already updated Chrome to 72.0.3626.121 or later.
The second vulnerability was in Microsoft Windows. It is a local privilege escalation in the Windows win32k.sys kernel driver that can be used as a security sandbox escape. The vulnerability is a NULL pointer dereference in win32k!MNGetpItemFromIndexwhen NtUserMNDragOver() system call is called under specific circumstances.
We strongly believe this vulnerability may only be exploitable on Windows 7 due to recent exploit mitigations added in newer versions of Windows. To date, we have only observed active exploitation against Windows 7 32-bit systems.
Pursuant to Google’s vulnerability disclosure policy, when we discovered the vulnerability we reported it to Microsoft. Today, also in compliance with our policy, we are publicly disclosing its existence, because it is a serious vulnerability in Windows that we know was being actively exploited in targeted attacks. The unpatched Windows vulnerability can still be used to elevate privileges or combined with another browser vulnerability to evade security sandboxes. Microsoft have told us they are working on a fix.
As mitigation advice for this vulnerability users should consider upgrading to Windows 10 if they are still running an older version of Windows, and to apply Windows patches from Microsoft when they become available. We will update this post when they are available.
Google’s vulnerability disclosure policy says, to a first approximation, that it gives software manufacturers 90 days to fix a security hole, and if no fix appears, they disclose the details.
It’ll be interesting to see how Microsoft reacts.
UPDATE: Catalin Cimpanu has a thorough timeline on ZDNet.
-
Microsoft Security Response Center: The biggest malware threat comes from zero-days; delayed patches, not so much
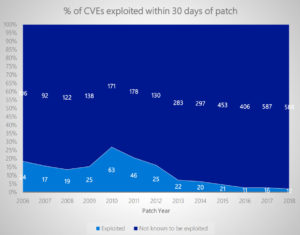
Of course your greatest security threat lies between the ears and in the twitching clicking fingers of people at the console. That hasn’t changed, and likely never will.
What’s startling to me, though, is that numbers from Microsoft now confirm that waiting 30 days to install those monthly patches realistically doesn’t put you at greater risk for getting clobbered by a cretin.
Computerworld Woody on Windows.
Thx, Susan!
-
Exchange Server elevation of privilege bug acknowledged
Remember the 0day exploit in Microsoft Exchange that we talked about two weeks ago?
As I suspected, your Exchange Server is only vulnerable to a man-in-the-middle attack. It isn’t an all-purpose attack: The miscreant has to be able to sit in the middle of an interaction with the Server.
Microsoft finally has an explanation in ADV190007 | Guidance for “PrivExchange” Elevation of Privilege Vulnerability.
A planned update is in development. If you determine that your system is at high risk then you should evaluate the proposed workaround.
The workaround is a one-line PowerShell script that @b talked about last week.
-
February missing security patch toll: Two zero-days and counting
Good report from Dan Goodin at Ars Technica.
Google’s Project Zero sticks to its 90-day notification policy, and a second 0day has been revealed, this time apparently involving CSS tokens.
The details are important. For example, there’s no exploit code available for this second 0day. But the first 0day, involving a gdi32.dll heap boundary, is still at large.
So is the SMBv3 bug that causes crashes, and may lead to deeper exploits.
Security patches are scheduled to resume on March 14.
-
Another Windows 0day appears – gdi32.dll heap boundary error
As 0day bugs go, this isn’t an earth-shattering development. But it’s still enough to cause concern.
Mateusz Jurczyk at Google Project Zero discovered a memory disclosure vulnerability and notified Microsoft on Nov. 17. Project Zero has an automatic 90-day disclosure deadline: If the vendor (in this case Microsoft) doesn’t fix the hole that’s discovered, it will be automatically disclosed 90 days later.
Sure enough, 90 days passed and, on Feb. 14, the timer rang and the full disclosure popped out, including exploit code.
This isn’t a huge bug. The bad guy has to get access to your computer before it can be exploited. Once logged on to your machine, the interloper can open a bad EMF file and use it to sneak a peek at system memory that isn’t theirs.
It seems that security bulletin MS16-074 didn’t fix the problem entirely.
Yuhong Bao (whom I’ve mentioned before, many times) sent a provocative message to the Project Zero folks. He said:
I wonder if this was supposed to be part of the cancelled February Patch Tuesday.
Something to ponder over the upcoming three-day US holiday.


