-
Patch Lady – Defender makes a change
 So earlier I was helping on a thread in the forum about some issues with failing defender updates on Small Business Server 2011 platforms. [For anyone who is interested, SBS 2011 was once a featured small business platform that provide file server and email services for small businesses – this was pre-cloud, you know]. The symptoms that was reported that defender updates were failing. Well first I was scratching my head because Defender wasn’t installed by default on Server platforms back then. While Server 2016 now ships with Windows Defender enabled, Server 2008 R2 – of which SBS 2011 was based – didn’t have Defender installed. I realized after doing some searching and confirming with the people in the forum that Defender COULD get on Server 2008 R2 if one enabled the Desktop Experience role. And that role would be wanted if you wanted to run disk cleanup on Server 2008 R2 (note you also get this on Server 2008 R2 by copying some files to get it to work as well).
So earlier I was helping on a thread in the forum about some issues with failing defender updates on Small Business Server 2011 platforms. [For anyone who is interested, SBS 2011 was once a featured small business platform that provide file server and email services for small businesses – this was pre-cloud, you know]. The symptoms that was reported that defender updates were failing. Well first I was scratching my head because Defender wasn’t installed by default on Server platforms back then. While Server 2016 now ships with Windows Defender enabled, Server 2008 R2 – of which SBS 2011 was based – didn’t have Defender installed. I realized after doing some searching and confirming with the people in the forum that Defender COULD get on Server 2008 R2 if one enabled the Desktop Experience role. And that role would be wanted if you wanted to run disk cleanup on Server 2008 R2 (note you also get this on Server 2008 R2 by copying some files to get it to work as well).So the question came up as to what exactly changed in Windows defender to suddenly make the definition updates fail on Server 2008 r2 whereas before it once worked? And then in the dark recesses of my mind it hit me. Yes. Defender HAD made a big change. And quite recently in fact, thus triggering this failure.
As noted back in January,
Starting March 1, 2018, Windows Defender Antivirus and other Microsoft security products will classify programs that display coercive messages as unwanted software, which will be detected and removed. If you’re a software developer and want to validate the detection of your programs, visit the Windows Defender Security Intelligence portal.
AH HA, that explains the recent change.
If you happen to be a Small Business Server 2011 admin and notice that defender updates are failing, I would honestly just disable the service and then look for a third party antivirus to install on your server, as I stated in the forum, and I truly mean no disrespect, SBS 2011 is in extended support and defender was not meant in that era to be installed on Server 2008 R2. Getting a fix would not be what I expect from Microsoft’s support policies for this product.
For the rest of us on windows 7, 8.1 and 10, be aware that effective March 1, 2018, if you happen to be running Windows defender on Windows 10 or Microsoft Security Essentials, any software that tries to trick you will be detected and removed.
As defined by Microsoft:
Software that coerces users may display the following characteristics, among others:
- Reports errors in an exaggerated or alarming manner about the user’s system and requires the user to pay for fixing the errors or issues monetarily or by performing other actions such as taking a survey, downloading a file, signing up for a newsletter, etc.
- Suggests that no other actions will correct the reported errors or issues
- Requires the user to act within a limited period of time to get the purported issue resolved
So look for more alerts on your system as these software programs get detected.
-
So how DO you block the upgrade to Win10 1709
More than a few people have asked, what with Win10 1703’s new-found ability to upgrade to 1709 all by itself — no Windows Update required — what does it take to make sure Microsoft doesn’t change its mind again and pushes you onto whatever version it likes?
@abbodi86 has an interesting observation:
Windows Update in Windows 10 is a lost cause without intervention
some steps are obligatory to keep the current version:
– set connection to metered
– set Automatic Update policy to disabled or notification
– disable UpdateOrchestrator and WindowsUpdate schedule tasks
– use wushowhide.diagcab or WUMT to check for updates and hide the upgrader-updateswhich seems to be a whole lot of work just to stay with what you have.
Comments?
-
Microsoft releases new single-purpose patch for Win10 1703, KB 4092077, to fix a bug in an earlier patch
It just started rolling out. I don’t see it yet on Windows Update, but the KB article is up:
March 8, 2018—KB 4092077 (OS Build 15063.936)
Addresses issue where, after installing this update, some localized devices have incorrect strings or unusual behavior in different areas of the user interface (UI) that make the UI unusable.
That appears to be something of a circular reference. No idea what the KB article means. But note that the build number for this patch, 15063.936, is the same as the build number for last month’s Win10 1703 cumulative update, February 22, 2018—KB 4077528 (OS Build 15063.936)
Which version are you running? Your guess is as good as mine.
-
Report: Win10 users being pushed onto 1709 even if they have Feature Updates deferred
UPDATE: See Computerworld Woody on Windows.
Hey @woodyleonhard , it seems Microsoft is now forcing Windows 10 1607 and 1703 users to upgrade to 1709, even if Feature Updates have been deferred. This notification just popped to my laptop, which is running 1703.
Couldn't stop it upgrading.
More info:https://t.co/9hgphP7QI9 pic.twitter.com/IYBouieDl0— Juzu Operatzija (@juzuo) March 8, 2018
-
Will Win10 1803 be called (yuck!) Spring Creators Update (/yuck!)?
WalkingCat (@h0x0d) asked someone with a copy of the next-next version of Win10 (the Skip Ahead build 17618, presumably leading to version 1809) to run a PowerShell command that lists VMHost supported versions.
The result isn’t going to make any Windows fans happy.
https://twitter.com/warnelidl/status/971692964694188032
The last listed version is “Microsoft Windows 10 Spring Creators Update/Server 1803.”
Pardon me while I try to keep my breakfast down.
-
Patch Lady – sounds great until we think about the updates
 Susan here, getting ready for that time of year that makes me for a sleepy Susan… aka Daylight savings. I just spotted in the news tonight that Florida is considering opting to stay in daylight savings. So what has that got to do with computers? Plenty. Computers are creatures of time. They have to be on the right time or near it otherwise all sorts of bad things occur. Like for example.. updating. You have to be no more than a few minutes off of the real time otherwise Windows update will totally fail. Because your machine depends on computer certificates, which have date/time stamps and if your computer comes back with the message that the certificate chain is invalid because the date and time is off…well you get the idea.
Susan here, getting ready for that time of year that makes me for a sleepy Susan… aka Daylight savings. I just spotted in the news tonight that Florida is considering opting to stay in daylight savings. So what has that got to do with computers? Plenty. Computers are creatures of time. They have to be on the right time or near it otherwise all sorts of bad things occur. Like for example.. updating. You have to be no more than a few minutes off of the real time otherwise Windows update will totally fail. Because your machine depends on computer certificates, which have date/time stamps and if your computer comes back with the message that the certificate chain is invalid because the date and time is off…well you get the idea.In a network a workstation cannot be more than 2 to 5 minutes off of the time set by the domain controller otherwise it will cause Kerberos log in problems.
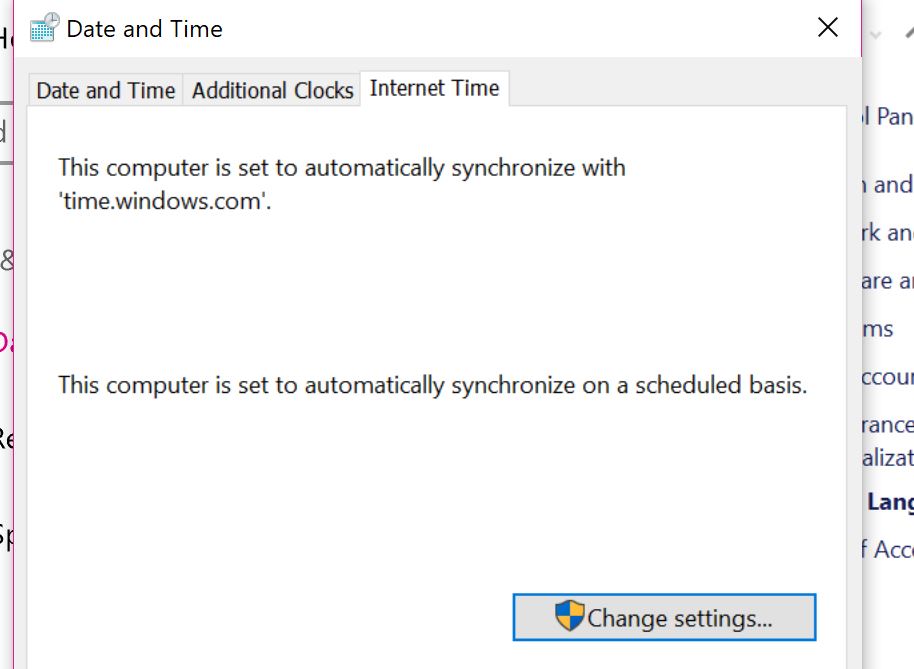 On standalone computers your computer is typically sync’d up to time.windows.com. This is a time server provided by Microsoft. But you can use an alternative time server.
On standalone computers your computer is typically sync’d up to time.windows.com. This is a time server provided by Microsoft. But you can use an alternative time server.NIST.gov provided the definitive list of all of the time servers. NTP or Network Time protocol is one of those old foundational protocols used in computers. So foundational that attackers have even found ways to do denial of service attacks on NTP servers. But on workstations, your machine only goes outbound to get it’s time information and isn’t open to attack.
Time is so foundational to how our computers talk to one another that it’s one of the reasons the DST updates are pushed out on a regular basis because time is sooo important. The DST blog showcases how often countries mess with time. It always amazes me how much countries mess with time.
By the way, trivia here…. do you know why we have time zones in the first place? As I understand it you can thank the English and the introduction of trains for the introduction of “Railway time” which was needed to standardize when it was expected that the train would arrive. Prior to travel everyone just set their own clock.
With the use of cloud technology I’m seeing some organizations go to a Universal time or UTC and not depend on the local time zone. One of the key things to establish in computer forensics is what time was set for all devices – that is – was the time set correctly in the firewall/modem/router that is logging events, in the computer event log and so on so the forensic investigator can prepare a timeline of events and correlate activity.
So many times (get it — a pun on time) we’d skip over that time zone update as being optional because we didn’t live in the area of the time zone change. But we’d often end up with computers that couldn’t handle when we DID have a time zone change. Everyone here remember when the USA moved the time zone change dates and how much we were running around trying to get things updated? It’s one of the reasons Windows 10’s updates are all inclusive and those time change updates come automatically.
So, if Florida opts out of changing it’s clock, a ton of developers in Redmond will be working around the clock to roll out updates.
Fun to look forward to if the bill goes through.
And now it’s my bedTIME.
-
Patch Lady – so where’s the Server patches?
 As a follow up to Woody’s “where the Windows 7 32bit patch updates” remember there are a couple more missing in action:
As a follow up to Woody’s “where the Windows 7 32bit patch updates” remember there are a couple more missing in action:As noted in this post, we’re still missing Server 2008 and Server 2012 updates. In case it helps all of you Windows 7 32 bit folks to know that you are not alone.
Q3: Why aren’t Windows Server 2008 and Windows Server 2012 platforms getting an update? When can customers expect the fix?
A3: Addressing a hardware vulnerability by using a software update presents significant challenges, and some operating systems require extensive architectural changes. Microsoft is continuing to work together with affected chip manufacturers to investigate the best way to provide mitigations. -
So, where’s the 32-bit Windows 7 Meltdown patch?
Just got this from LB:
Hey Woody,
What do you think about doing a story on the missing Windows 7 32-bit meltdown fix? Or maybe mentioning it in next week’s update writeup (unless it finally hits.)
It seems very odd that it’s taken microsoft so long to issue a fix when the problem, and the solution (kpti), are clear cut (as opposed to the much tougher spectre problems.) 32-bit Win7 should still be getting security fixes until Jan 2020, last I knew.
Anyway, just a thought. Thanks for all the work you do to keep us informed!
take care,
Anybody out there have some insight? Microsoft was slow to get the 32-bit Meltdown patches to Win10. Surely they wouldn’t just give up on Win7, would they?
Er, would they?


