-
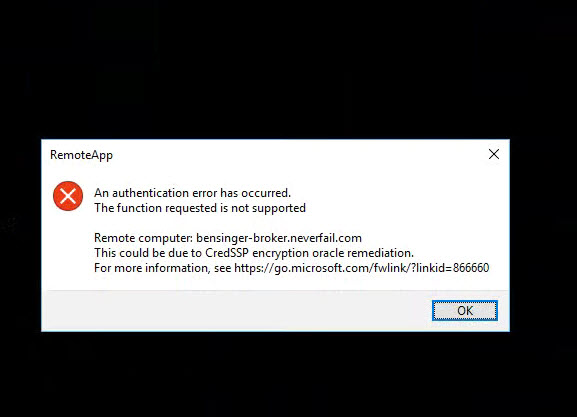
Problems with CredSSP updates CVE-2018-0886 breaking RDP connections
Yet another mess.
@GeekDiver reports:
Looks like CVE-2018-0886 was included in the cumulative update and is breaking RDP connections and App feeds. No backward compatibility in CredSSP right now we are dealing with 100 Windows 10 PCs that are affected. Anyone else seeing this?
The CVE-2018-0886 article lists every current version of Windows as falling under this patch’s spell.
Microsoft has an extensive list of errors generated by this update in KB 4093492, which mentions this error and offers a link to https://go.microsoft.com/fwlink/?linkid=866660 — which, in turn, links back to the same article.
Kinda like chasing your tail. Windows is the productivity OS, right?
Susan aka Patch Lady note as of 5/9/2018: Please note the problem is NOT with the update. Rather the issue is that there’s a mismatch of patching levels. In March Microsoft released an update that began the process of rolling out an update to CredSSP used in Remote Desktop connection. In May the updates mandate that a patched machine can’t remote into an unpatched machine. If you dig into the KB there is a registry workaround to [TEMPORARILY] disable the mandate, but the better and wiser move is to update the server or workstation you are remoting into. Make sure the “thing” you are remoting into has an update. Also note that for consumers and home computers you probably won’t see this issue. This only has impact if you use Remote Desktop connection to remote into another computer.
-
Multiple reports that Windows Update is overriding the “metered connection” setting
I’m seeing reports from many different places that Microsoft’s long-standing (unspoken) policy of bypassing cumulative updates on machines with “metered connections” has been broken.
Specifically, it looks like yesterday’s Win10 1709 cumulative update KB 4103727 — the one that brings Win10 up to build 16299.431 — is being applied on machines that have their internet connections set as “metered.”
It’s not clear if that’s the case with both Wi-Fi and Ethernet (wired) internet connections.
It’s also not clear if Win10 1703 is similarly afflicted.
If true, Win10 Home customers are going to get hit hard — the metered connection approach was the only easy, reliable method I know about for avoiding updates.
Home users may be forced to disabling wuauserv and/or running third-party cumulative update blockers.
If you know of someone who’s experiencing a forced cumulative update, please post here and let me know which version of Win10, and whether the metered connection is Wi-Fi or Ethernet.
-
Windows and the inexorable downward slide
Horace Dediu (Asymco) has a new blog post that you should read, as we’re shuffling deck chairs and playing “Nearer, My God, to Thee.”
-
Microsoft blocking the Win10 version 1803 update on some PCs with Intel solid state drives
Details are sketchy, but there’s a post on the Microsoft Answers Forum from “Microsoft Agent” Lonnie_L:
When attempting to upgrade to Window 10 April 2018 Update select devices with certain Intel SSDs may enter a UEFI screen reboot or crash repeatedly.
Microsoft is currently blocking some Intel SSDs from installing the April 2018 Update due to a known incompatibility that may cause performance and stability issues. There is no workaround for this issue. If you have encountered this issue, you can roll back to Windows 10, version 1709 and wait for the resolution before attempting to install the April 2018 Update again.
Microsoft is currently working on a solution that will be provided in a near future Windows Update, after which these devices will be able to install the April 2018 Update
That’s a whole lot of warning with a teeeny-tiny amount of useful information.
Paul Alcorn at Tom’s Hardware has picked up the scent:
The errors are surprising given that Intel’s SSDs use industry-standard protocols, such as SATA and NVMe, that ensure broad compatibility. We also don’t know if these issues pertain only to SSDs that use a certain protocol. Intel does deliver its own custom drivers for some products, so there is a chance that the fix may require a combination of a new Intel driver along with changes from Microsoft.
There are good reasons to hold off on version 1803.
Thx @sb
-
May 2018 Patch Tuesday has arrived
The May Security Updates have been released for all versions of Windows. Today, Windows 10 v1803 becomes officially available.
As usual, Martin Brinkman has his amazing overview available on the ghacks site. The updates according to operating system:
- Windows 7: 11 vulnerabilities of which 2 are rated critical, 7 important, and 1 low.
- Windows 8.1: 11 vulnerabilities of which 2 are rated critical, 7 important, and 1 low
- Windows 10 version 1607: 18 vulnerabilities of which 3 are rated critical, 14 important and 1 low.
- Windows 10 version 1703: 19 vulnerabilities of which 3 are rated critical, 15 important and 1 low.
- Windows 10 version 1709: 20 vulnerabilities of which 3 are rated critical, 16 important and 1 low.
- Windows 10 version 1803: 16 vulnerabilities of which 3 are rated critical, 12 important and 1 low.
Windows Server products
- Windows Server 2008 R2: 11 vulnerabilities which 2 are rated critical, 8 important, and 1 low.
- Windows Server 2012 and 2012 R2: 11 vulnerabilities which 2 are rated critical, 8 important, and 1 low.
- Windows Server 2016: 18 vulnerabilities of which 3 are rated critical, 14 important, and 1 low.
Other Microsoft Products
- Internet Explorer 11: 9 vulnerabilities, 6 critical, 3 important
- Microsoft Edge: 18 vulnerabilities, 13 critical, 5 important
Security Updates for Microsoft Office are available, including Office 2010, 2013 and 2016.
There are also .NET Rollups and Security-only patches for Win7/8.1 this month.
Unless you have a specific reason to install updates, you should wait until Susan Bradley (Patch Lady) has had time to evaluate them and/or Woody gives the DEFCON go-ahead. Patch reliability is unknown at this time.
-
Our newest forum: Tech Accessibility
I’ve just opened up a new forum that’s long overdue, quite frankly. Tech Accessibility covers topics and concerns about making computers accessible to everyone, everywhere.
Thanks to @Lori for suggesting it, and @Elly for fleshing it out.
-
Time to block automatic updates UNLESS you’re on Win10 version 1803
I can’t recall the last time I recommended that folks allow Windows to install updates automatically, but if you got stuck with Win10 1803 — and you want to keep it — you’d better get the Patch Tuesday patch as soon as you can.
Computerworld Woody on Windows.
-
Turning the ratchet up to MS-DEFCON 2
I’ll have full instructions on Monday, but most of you know the drill.
I’m changing it now because I suddenly realized that some of you may be running Win10 1709 and clicking on “Check for updates.” (Thx, JL!)
If you did get pushed onto 1803, real quick, roll back to 1709 — Start > Settings > Update & security, on the left choose Recovery, on the right click to Roll back to previous version.
We’re at MS-DEFCON 2: Patch reliability is unclear. Unless you have an immediate, pressing need to install a specific patch, don’t do it.