-
Yes, Microsoft says Win10 has hit 800 million devices
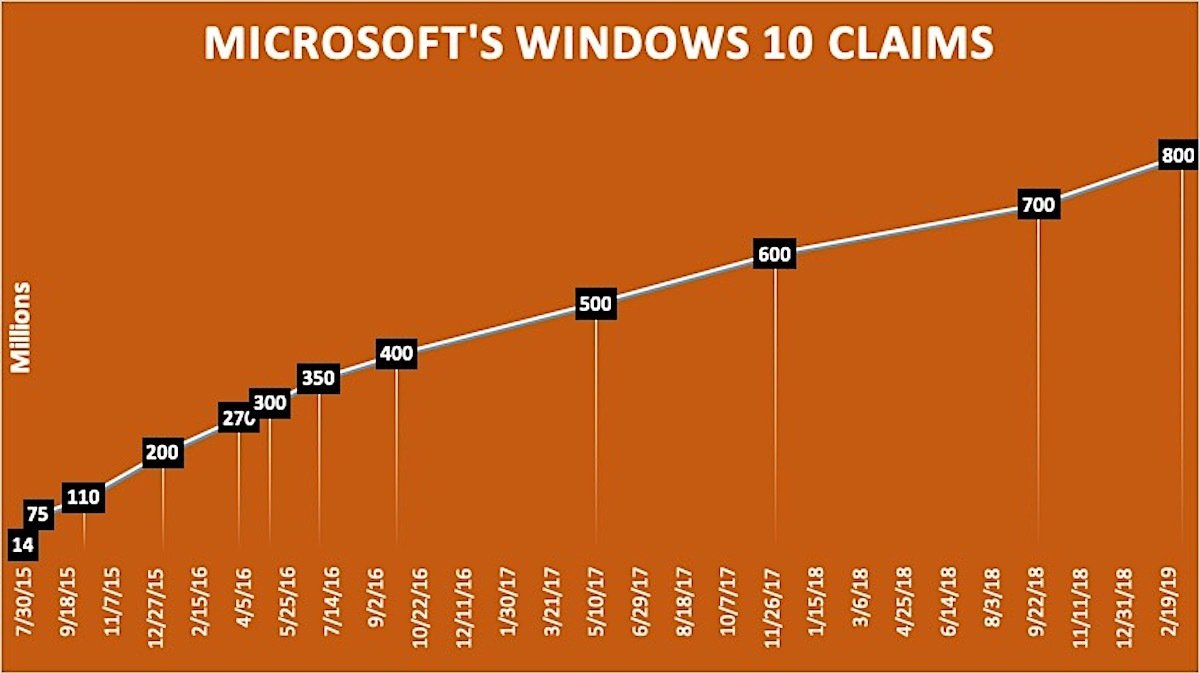
Gregg Keizer has a solid – and suitably skeptical – summary in Computerworld:
Microsoft on Thursday said that 800 million devices are now running Windows 10, a 100 million increase in less than six months.
Microsoft has regularly touted numbers for Windows 10, most of the time, although not always, by citing the active monthly devices, or those personal computers, tablets and other systems used within the last month.
The 800 million number is sufficiently fuzzy that it’s hard to say if that’s monthly active devices, or just installs and/or activations, or some other metric. Microsoft’s number page says, simply, “There are more than 800 million devices running Windows 10,” dodging the definition quagmire. Says Keizer:
Using the 12-month average change in user share, Computerworld recently forecast that nearly 41% of all Windows PCs will be running Windows 7 at the moment it falls off Microsoft’s support list.
That’s an astonishing number.
-
They’ll have to pry Win7 from my cold, clutched claws – Seven Semper Fi
I think it’s kismet.
On the day that Microsoft announced it had installed Win10 on 800 million devices (yep, even refrigerators!), I went the other way.
I’ve kept several Windows 7 virtual machines running for many years. But I finally decided to plunk down some hard cash ($125, to be precise) and bought a refurbished Lenovo ThinkCentre M82 small form factor PC, with a genuine, crisp copy of Windows 7 Pro. I figured it’d be better experiencing the demise of my old friend first-hand, rather than vicariously through a virtual machine.
So I’m busy setting up the new/old/off-lease Seven Semper Fi.
A couple of things struck me during the from-scratch installation…. aside from having to clear away the junk (why would they install AVG Free and Adobe Reader on a refurb? no, don’t answer, I know, I know) the install brought back fond memories — remember how you had to actually CHOOSE to activate automatic update, and how the “Check for updates” button actually, you know, checked for updates, instead of installing everything in the swamp?
Anyway, I’m forging ahead with a minimalist machine, to commiserate with you folks as the inevitable approaches. I got it updated (took about 30 minutes, starting with the updates installed by the refurb company). Restarted three times to finish the process. Installed Firefox (still debating about Chrome). Got rid of AVG Free and installed Microsoft Security Essentials (knowing that it’ll die early next year, too). Added VLC Media Player, 7 Zip, speccy (all from oldergeeks.com, of course) and I’ll install Office 2013 shortly.
What else would you like me to try?
The machine works great, by the way. Intel i5-3470, onboard graphics card, 4 GB memory, 250 GB hard drive. It can be leisurely at times, but I don’t mind. Five years ago it would’ve been a contendah.
-
Google comes clean on that “emergency” security patch – and shows how it was used to trigger a Windows 7 0day
Now I understand.
Google releases patches for its Chrome browser all the time. As @b explained about 36 hours ago, Google sent out a special alert to get Chrome updated specifically to head off a 0day attack.
I didn’t get too excited about it because Chrome automatically updates itself quite reliably, and because the threat didn’t seem to be all that great.
A few hours ago, Clement Lecigne of the Google Threat Analysis Group added some key details:
On Wednesday, February 27th, we reported two 0-day vulnerabilities — previously publicly-unknown vulnerabilities — one affecting Google Chrome and another in Microsoft Windows that were being exploited together.
To remediate the Chrome vulnerability (CVE-2019-5786), Google released an update for all Chrome platforms on March 1; this update was pushed through Chrome auto-update. We encourage users to verify that Chrome auto-update has already updated Chrome to 72.0.3626.121 or later.
The second vulnerability was in Microsoft Windows. It is a local privilege escalation in the Windows win32k.sys kernel driver that can be used as a security sandbox escape. The vulnerability is a NULL pointer dereference in win32k!MNGetpItemFromIndexwhen NtUserMNDragOver() system call is called under specific circumstances.
We strongly believe this vulnerability may only be exploitable on Windows 7 due to recent exploit mitigations added in newer versions of Windows. To date, we have only observed active exploitation against Windows 7 32-bit systems.
Pursuant to Google’s vulnerability disclosure policy, when we discovered the vulnerability we reported it to Microsoft. Today, also in compliance with our policy, we are publicly disclosing its existence, because it is a serious vulnerability in Windows that we know was being actively exploited in targeted attacks. The unpatched Windows vulnerability can still be used to elevate privileges or combined with another browser vulnerability to evade security sandboxes. Microsoft have told us they are working on a fix.
As mitigation advice for this vulnerability users should consider upgrading to Windows 10 if they are still running an older version of Windows, and to apply Windows patches from Microsoft when they become available. We will update this post when they are available.
Google’s vulnerability disclosure policy says, to a first approximation, that it gives software manufacturers 90 days to fix a security hole, and if no fix appears, they disclose the details.
It’ll be interesting to see how Microsoft reacts.
UPDATE: Catalin Cimpanu has a thorough timeline on ZDNet.
-
Fred Langa: “My 500 GB hard drive has one bad sector; what does that really mean?”
Short answer: Not a heckuvalot.
Yet another insightful piece from the master.
On Langa.com.
-
The highest customer satisfaction in the history of Windows
I’m just going to drop this here, gently, and tip-toe away without comment.
Thank you to all our customers and partners for helping us achieve 800 million #Windows10 devices and the highest customer satisfaction in the history of Windows. https://t.co/G3CRdkFoPT pic.twitter.com/je9kvBvYhj
— Yusuf Mehdi (@yusuf_i_mehdi) March 7, 2019
-
Windows Blog: “Data, insights and listening to improve the customer experience”
Yesterday, Rob Mauceri and Jane Liles published a white paper on the Windows Blog that talks about using telemetry to figure out if a patch is ready for deployment:
We approach each release with a straightforward question, “Is this Windows update ready for customers?” This is a question we ask for every build and every update of Windows, and it’s intended to confirm that automated and manual testing has occurred before we evaluate quality via diagnostic data and feedback-based metrics. After a build passes the initial quality gates and is ready for the next stages of evaluation, we measure quality based on the diagnostic data and feedback from our own engineers who aggressively self-host Windows to discover potential problems. We look for stability and improved quality in the data generated from internal testing, and only then do we consider releasing the build to Windows Insiders, after which we review the data again, looking specifically for failures.
In other words, MS looks at the telemetry from dog food runs and, if all looks copacetic, the Insiders get it.
I’m not going to snark about it (you folks can do that better than I). It’s obvious that the people involved have advanced tools at their disposal, they’re good at what they do, and they know the statistical analysis cold.
But you have to ask yourself… If the model’s so great, why did Destiny 2 and CoD get hit so badly last week?
Why do we continue to get solid, acknowledged bugs with almost every Windows patch on Patch Tuesday?
And… how on earth did Win10 version 1809 get let out of its cage?
-
Blue screens acknowledged with the latest Server 2016 second February cumulative update, KB 4487006
Microsoft has just acknowledged a Blue Screen error in Server 2016 if you install the “optional non-security” February patch, KB 4487006:
In some cases, Windows Server will stop working and restart when hosting multiple terminal server sessions and a user logs off. The faulting driver is win32kbase.sys.
Microsoft is working on a resolution and will provide an update in an upcoming release.
Yet another reason why you should avoid the second monthly cumulative updates until they’ve been vetted and rolled into a “real” Patch Tuesday cumulative update.
Thanks to an anonymous AskWoody poster.
-
Welcome to Windows Secrets Lounge transplants
We haven’t yet “swallowed the whale” — moved the 40,000 Windows Secrets user accounts and 1 million posts over to AskWoody — but (I’m assured) it’ll be happening soon.
In the interim, hundreds of Windows Secrets Loungers have already signed up here with AskWoody accounts, and hundreds of additional Windows Secrets Newsletter subscribers have made the leap. Just a reminder: If you’re trying to log on to this site with a username that’s also your email address, you need to go through the (easy!) steps to set up a “proper” AskWoody account. Your old subscriptions will come across with you. You have my word on that — and you know where to reach me.
If you’re new to AskWoody, check out the Welcome! tab at the top. Some of the information there may help you make the transition.
So dive in and post away. We have a large group of very helpful people here who just love taking on new challenges.


