-
WannaCry hits Honda car plant in Japan
A vulnerable machine WILL get infected. Only, if the block is accessible, the worm will exit immediately after infecting it…. and, according to Reuters, they shut the plant down.
The automaker shut production on Monday at its Sayama plant, northwest of Tokyo… Production at other plants operated by the automaker had not been affected, and regular operations had resumed at the Sayama plant on Tuesday, she said.
The story doesn’t sound right. Anybody know what really happened?
Interesting. Vess Bontchev just tweeted an explanation:
They probably just discovered the infection. They were not encrypted, because of the block. The block doesn’t prevent infection… A vulnerable machine WILL get infected. Only, if the block is accessible, the worm will exit immediately after infecting it… A vulnerable machine WILL get infected. Only, if the block is accessible, the worm will exit immediately after infecting it… they were running vulnerable, unpatched. They probably got infected repeatedly during the month. Just nobody noticed until now, because the encryption didn’t trigger, due to the block. A more interesting question is how did they discover the problem? The DoublePulsar backdoor remains, not sure if AV detects it.
There’s another good discussion kicked off by Mikko Hypponen here.
-
Viivo End Of Life Just Announced
PKWARE’s Viivo data encryption has just announced it will be shutting down from the end of the month, with their servers ceasing to operate a year later.
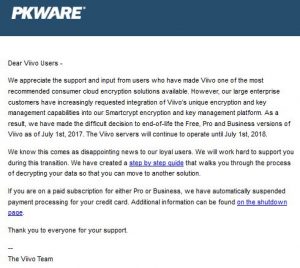
Viivo’s free and paid services have added to the security of cloud storage over recent years, giving extra peace of mind to users of offerings like Dropbox, OneDrive, Google Drive and Box. These users will now be looking at their options, so they can decrypt their Viivo files within the given time. Find out more on https://viivo.com/shutdown
PKWARE are also known for their zip products, as well as encryption.
-
IFIXIT gives the new Surface Laptop 0/10 repairability score
Microsoft’s new Surface Laptop starts at $999.00 in the Microsoft Store.
That price will get you a 3.1GHz i5 Intel Sky Lake processor, 4GB RAM, a 128GB SSD and Win 10 S. The top-of-the-line Surface Laptop runs $2199.00 for a 4.0GHz i7 Sky Lake processor, 16GB RAM, a 512GB SSD, and Win 10 S.IFIXIT recently tore down the new Surface Laptop with its Alcantara fabric-covered keyboard to determine its repairability. They gave it a score of 0/10. Yes, 0 (zero).
Verdict: The Surface Laptop is not a laptop. It’s a glue-filled monstrosity. There is nothing about it that is upgradable or long-lasting, and it literally can’t be opened without destroying it.
It would seem Microsoft has created a $1000.00 (minimum) disposable laptop. Read the teardown notes on IFIXIT.com
-
Acrobat Reader XI Now Offered Upgrade to Acrobat 2017 Reader
This month, Adobe has started upgrading Reader XI to 2017, which was released this month. This comes with new options for upgrading, and EULA changes.
You can read about this over on Browser & Desktop Software:
Acrobat 2017 is now being rolled out -
Microsoft confirms problems with June 2017 security patches for Outlook, provides workarounds
Microsoft has acknowledged that the June 2017 security patches for Office Outlook can cause Email attachment blocking problems. This affects Outlook 2007 (KB 3191898), Outlook 2010 (KB 3203467), Outlook 2013 (KB 3191938), and Outlook 2016 (KB 3191932). The description of the Security Updates comes with this warning about known issues:
If an email message includes an attached email message, and the attached email message’s subject line ends with an unsafe file name extension as listed in the Blocked attachments in Outlook page, the email attachment will be blocked for recipients. To fix this issue, save the email message to the computer and rename its subject line so that it does not end with an unsafe file name extension. Then, attach it to the email message to be sent.
The blocking of attachments with file extensions that are on the list is meant to protect against opening files that could be harmful to your computer. However there have been reports that other attachments such as Rich Text (.rtf) and Word and Excel are also being blocked. Microsoft has issued several workarounds for this.
For Office 2007 and 2010 Rich Text attachments (.rtf)
- Forward the email to yourself and then open the attachments from the forwarded email.
- Change the email format to HTML, or Text format.
- Save the attachments to your computer, using one of the following methods, then open them from the saved location:
- Drag and drop the attachments to your desktop.
- Go to File > Save Attachments.
- Copy and paste the attachment to your computer.
For Outlook 2007, Outlook 2010, Outlook 2013, and Outlook 2016 attachments containing consecutive periods (…) or exclmation mark (!).
If you’re sure the attachment was sent from a trusted source, proceed to Open or Save the attachment.For Outlook 2013 and Outlook 2016
If you set ShowLevel1Attach to allow Outlook to display Level 1 attachments, you may see the error: “One or more objects in this file have been disabled due to your policy settings”- Change the email format to HTML, or Text format.
- Save the attachments to your computer, using one of the following methods, then open them from the saved location:
- Drag and drop the attachments to your desktop.
- Go to File > Save Attachments.
- Copy and paste the attachment to your computer.
For a complete description of the warning messages, and the workarounds Microsoft has issued, see You receive an error when opening attachments in Outlook
@gborn is also reporting issues with Outlook after installing June 2017 security patches on Born’s Tech and Windows World
-
Sign up for the Windows Server beta program now
If you’re in to on-premises Windows Server you can now sign on to beta test the twice-a-year product updates.
Server’s going to a twice-a-year update schedule, just like Win10 and Office, and the process has the same familiar ring to it, “Semi-annual Channel releases.” Shortly Server will have its own Insider Program as well.
I can’t think of any better way to kill on-prem Server, than to force it into a twice-a-year upgrade cadence.
Sign up here.
-
XP SP3/Server 2003 Security Patches Released June 2017
In a most unusual Patch Tuesday (Full details in Woody on Windows blog, which has just moved from InfoWorld to Computerworld), Microsoft announced in a June 2017 security update release that it was releasing additional security patches for older platforms. Microsoft security advisory 4025685 was released in tabular form, with references to the security bulletins that each patch addressed for each of the non-supported older platforms. To make for easier downloads, here is the list or the patches needed for Windows XP/Server 2003.
NOTE: These links are set to open in additional tabs. After the download, remember to close the extra tab(s).
XP SP3
- KB958644 — you may already have this 2008 update installed.
- KB2347290 — you may already have this 2010 update installed.
- KB4012598
- KB4012583
- KB4022747
- KB4018271 for IE8
- KB4018466
- KB3197835
- KB4024323
- KB4025218
- KB4024402
- KB4019204
Server 2003 SP2 64-bit
- KB958644 — you may already have this 2008 update installed.
- KB2347290 — you may already have this 2010 update installed.
- KB3011780
- KB4012598
- KB4012583
- KB4022747
- KB4018466
- KB3197835
- KB4024323
- KB4025218
- KB4024402
- KB4019204
Server 2003 32-bit or Home Server 2003 original release
If you need additional patches for other older platforms, they can be downloaded from the Microsoft Update Catalog by entering the patch number in the search box.
-
The Dangers of Posting Your X-Rays to Social Media
Malwarebytes Labs published a post by William Tsing on June 9, 2017, explaining the problems that can occur when x-rays are shared online.
The problem stems from the private details of both the patient and the hospital that are shown on x-rays. Most contain the patient’s full name, date of birth, and sometimes their Social Security Number, and will often contain the name of the medical facility that took the x-ray.
The information can be used together to enable either identity theft or doxing, but it could also be used to jeopardise the security of the network of the medical facility. Personally, the name of the hospital would give your location, to add to your name and date of birth, and could be used to access property tax, tax or voting records. For the hospital, a networked x-ray machine connected to the internet could be identified in the x-ray details, which could be used to access the system. Malwarebytes were able to gain a lot of information from one x-ray they checked.
“Yikes. Medical infrastructure security has problems. A lot of problems. But while the responsibility for an insecure network lies with the organization running it, posting photos that have exploitable information is also not a great thing. Given that vulnerabilities in the medical space can have catastrophic consequences, we should take extra care before exposing any data from inside a hospital or doctor’s office.”
If you really must share an x-ray online, crop it first, so no identifying information remains. Read the full article on blog.malwarebytes.com
-
Win7 Monthly Rollup KB 4022719 triggers printing problems in Internet Explorer
EverWilli, posting on the Microsoft Answers forum, describes a problem with the latest Win7 Monthly Rollup, KB 4022719:
After installing KB4022719 our users cannot print certain items from Internet Explorer 11. If a users opens a page in a *frame and attempts to print they only get a blank page.
We have tired all the basic fixes, resetting IE, cleaning temp files, printer files, checking for a low folder but the only solution at this time is to uninstall KB4022719. Thus far we have only uninstalled on 2 pc’s with the issue and that fixed the printing on both machines.
There are now reported sightings of the bug with the Win7 Monthly Rollup KB 4022719, as well as the standalone IE security patch KB 4021558.
Only solution so far is to roll back the security patch.
UPDATE: The problem now appears on the Edge Developer’s forum, marked by Microsoft as “Won’t Fix.” More than a few people are aghast. It’s not clear if that’s Microsoft response to a bug of its own creation – or if it’s an indicator that the Edge folks really don’t care much about IE 11.
-
Microsoft’s new anti-Chromebook ads show that you really need to consider buying a Chromebook
I’ve been saying it for years now. Unless you have an overarching need for a specific Windows application, you should consider getting a Chromebook. True, Google will snoop on your activities. But Microsoft does, too.
The latest ads from Microsoft — detailed by Paul Thurrott today — prove the point. Even Microsoft can’t come up with convincing arguments for sticking with Windows.
Windows is an old gray mare who ain’t what she used to be. At least Chromebooks work well, easily, securely and reliably.
-
June 2017 Adobe Flash Player & Shockwave Player security updates
EP advises:
New Adobe Flash Player and Shockwave Player security updates released on Tuesday June 13, 2017-
Adobe Flash Player security bulletin APSB17-17:
https://helpx.adobe.com/
security/products/flash- player/apsb17-17.html This updates Flash Player to version 26
Adobe Shockwave Player security bulletin APSB17-18:
https://helpx.adobe.com/
security/products/shockwave/ apsb17-18.html This updates Shockwave Player to version 12.2.9.
-
Yep, KB 4020732 and KB 4020733 were released early
Last week, there were reports that two Lync 2010 security patches had appeared on Windows Update servers. It wasn’t clear if they were intentional early arrivals, or if somebody just screwed up.
It looks like the latter’s the case. See the KB 4020732 article.
Security Update for Lync 2010 X86/X64 (KB4020732)
Security Update for Lync 2010 Attendee – Administrator level installation (KB4020733)


