|
ISSUE 17.19.0 • 2020-05-18
The AskWoody PLUS Newsletter
In this issue SOCIAL NETWORKING: Zoom: Is it safe? BEST OF THE LOUNGE: Whether to clean or not to clean the registry LANGALIST: How USB booting leaves a digital trail PATCH WATCH: .NET Framework oddities and ESU issues highlight May patching BEST UTILITIES: Freeware Spotlight — Open Hardware Monitor SOCIAL NETWORKING Zoom: Is it safe?
By Lincoln Spector Have you noticed that the start of every article about Zoom suggests that it has quickly turned into the most needed app on the planet? Thanks to the pandemic, what was created as a business-conferencing tool has become the de facto means for ordinary people to connect to each other. My wife, a faculty member at the San Francisco Conservatory of Music, uses Zoom to teach her students miles away. Family get-togethers, schools, charity events, remote concerts, and even television hosts now depend on the service. But while Zoom’s stock was exploding, the programmers who built the platform seemed to be tripping over their shoelaces. Problems kept popping up, often followed by official apologies. And then came the reports of questionable privacy policies and online trolls crashing meetings. With good reason, people started asking, “Is Zoom safe?” In a previous article about Zoom and similar services (2020-04-06 AskWoody issue), I concentrated on video-conferencing etiquette and ease of use (or lack thereof). I wrote that article in March, just as we were getting used to the new world of stay-at-home socializing. We were all learning as we went along. Thus I ignored one of the more difficult questions about these services: To what degree are Zoom and its competitors spying on us? Because I ultimately recommended Zoom as the easiest video-conferencing service for users of any technical skill — yes, even Uncle Fred could get it working — I’m going to focus on its failings. Both accidentally and intentionally, the company has put your privacy at risk. Much has been written about these problems in recent weeks, so I’ll give you a summary of what you really should know about the service — and others. A potential threat to school kids
In early April, New York City banned Zoom for school use — even though “thousands of teachers and students began using it for remote learning,” according to an article penned by Chalkbeat’s Alex Zimmerman. It went on to say: “The education department received reports of issues that impact the security and privacy of the platform during the credentialing process … .” A month later, the city lifted the ban after Zoom made security changes. Quoted in a Spectrum News NY1 article, New York DOE Schools Chancellor Richard Carranza stated: “The security of our students and staff is paramount, and we’ve worked with Zoom to create a tailored platform that provides the safety and functionality schools need to engage in remote learning.” In a Zoom blog post, the company claims to be hard at work providing a safer environment. Are these real and significant fixes? Or are they little more than the digital equivalent of slapping on some new paint? We just don’t know yet. But based on the aforementioned blog, Zoom does seem to be taking its issues seriously. Party crashing and other bad behavior
As with all major events, the current pandemic has created its own vernacular. One of the more unique additions is Zoombombing — which I sincerely hope you’ll never experience. This is the Internet version of crashing a party, starting fights, and painting offensive epitaphs on walls … except you’ll never know who ruined your fun. As noted in a CNET article, it’s horribly easy to Zoombomb a meeting. If you search for URLs containing zoom.us, you might get hundreds of vulnerable Zoom-enabling sites. Fortunately, the article provides some tips for blocking Zoom hooligans. But not all the service’s problems are as visible or caused by outside actors. As reported in a Vice article, the iOS edition of Zoom was for some time sending personal data to Facebook — even if the user was not a Facebook subscriber. At the time, there was no mention of Facebook in Zoom’s privacy policy. Privacy Matters activist Pat Walshe called that policy “shocking.” Once the information came out, Zoom, not surprisingly, stopped sending information to Facebook. When I researched my earlier article, I skimmed through Zoom’s 3,855-word privacy policy. Among numerous worrisome points was the statement that it “covers all Personal Data that you affirmatively provide during your interactions with us, information that we automatically collect when you interact with our Products, and information that we collect about you from third parties.” That sounds intrusive, but it’s hard to know whether that’s any worse than, say, Facebook, Windows, or macOS. The latest version of the statement, dated March 29, claims that “We do not sell your personal data.” I haven’t studied the entire statement — it has ballooned to 5,225 words — and probably wouldn’t understand it all if I did. But you might want to read the top bullet points and judge for yourself. Just how bad is this?
Given its history and recent news coverage, it’s not surprising that people describe Zoom as “fundamentally corrupt” and “malware.” Nevertheless, it’s still extremely popular; it has become the Google of personal video conferencing. So whether to use it mostly comes down to what you’re willing to tolerate. Even Windows has been dubbed “malware” (Computer World article). Zoom used to claim that its service had end-to-end encryption — an assertion made by redefining the concept. When it turned out not to be so, the company had to eat crow. Zoom acknowledged “a discrepancy between the commonly accepted definition of end-to-end encryption and how we were using it.” In a May 7 Zoom blog post, the company announced that it had acquired an encryption startup called Keybase — I assume to improve the service’s privacy problems. That might help small gatherings, but it’s unlikely today’s technology can handle simultaneous end-to-end encryption for 100 or more nodes. Most troubling, Zoom’s technology exposed personal devices to malware. Last year, a security researcher discovered that the program installed hidden and potentially vulnerable Web servers onto Macs. Soon after that became public knowledge (July 2019), Zoom reported that it had removed the code via an update. Why not simply use another service?
There are, of course, alternatives to Zoom — Cisco’s Webex, Google Meet, and Microsoft Teams, to name just a few. (I discussed Webex and Google Duo in my April 6 article.) Sure, there might be better choices, but we’re up against the Facebook dilemma — i.e., you might prefer a less intrusive social network (MeWe, for example), but all your friends, family, and business associates are glued to Godzilla. Zoom is now the behemoth of both business and non-business video conferencing. For a Consumer Reports Digital Lab article, privacy researcher Bill Fitzgerald took on the arduous task of examining the policies of several video-conferencing platforms. The conclusion: “While there are differences … on balance, the differences aren’t enormous … from a privacy point of view, none of these options is great.” So even if you could convince your acquaintances to move to another meeting service, it probably wouldn’t remove the underlying privacy problems. Am I sticking with Zoom?
Probably. Until the virus is under control, we need a way to socialize without endangering our lives or those of others. I’m not willing to take the risk of shopping in public without a mask, but I am willing to possibly lose some privacy in order to continue connecting with friends and family. And there really isn’t a significantly better option. Whether you’re using Zoom or one of its competitors, assume that someone untrustworthy might be recording what you’re saying. So don’t read out your personal bank account number, or proprietary business info, or the secret family recipe for gefilte fish in a Zoom meeting. If you really need to keep something private, use an encrypted email service such as Sendinc — or just use the phone!
Lincoln Spector writes about computers, home theater, and film and also maintains the blog Bayflicks.net. His articles have appeared in CNET, InfoWorld, The New York Times, The Washington Post, and other publications. Best of the Lounge Whether to clean or not to clean the registry
It’s likely you’ve used Windows’ built-in tools and/or third-party apps to remove leftover bits of defunct programs and other junk from your PC. But what about cleaning the Windows registry? Windows doesn’t offer its own registry clean-up tool — Microsoft would prefer that users leave that OS component alone. But that doesn’t necessarily mean that there’s no benefit to sweeping out the accumulated detritus. With that in mind, MVP Rick Corbett explored the registry’s exponential growth from Windows 7 to Windows 10 — and gives his thoughts on the “cleaning” question. Fellow Loungers chime in with their views — of course! Windows 10 When Plus member WillFastie recently lost the ability to customize the Start menu on a Win10 Pro 1909 PC, he asked others in the forum whether they had run into the problem. Installing the latest Windows updates proved fruitless — the right-click context menu would still not function properly. WillFastie found the fix: removing or resetting a registry key called NoChangeStartMenu. The only unanswered question was how it got there. Browsers Two different computers, two different approaches to saving downloaded files. Plus member Ron M ‘s machine lets him decide where to put files brought down from the Internet. But his wife’s computer offers only the “Downloads” folder as a destination. Ron wants his wife’s system to match his. The issue is quickly solved with a simple change in browser settings. If only all problems were this easy to fix! Security An anonymous reader wonders whether there’s a better and cheaper security suite than Kaspersky’s Total Security. What’s running on your setup? Windows 10 After air dusting the motherboard and fans on an ASUS M4A88-TD3 PC, Plus member Lil88reb discovered that the machine refused to enter sleep mode automatically. It would sleep when prodded by a manual power selection. Worse yet, the problem would come and go on three different systems. So was the cleaning just coincidence? Fellow Loungers offered suggestions, but Lil88reb is still on square one. Can you diagnose the problem? MS Office Upgrades can be really frustrating. Plus member LH had no problems with email when using Office 2010 on a Win7 machine. But then came the new Win10 system with Office 365. After some back-and-forth in the forum, LH arrived at a solution: changing a security setting in Gmail. UTILITIES An anonymous reader prods the forum for a WinPatrol alternative. The tool takes a snapshot of critical system resources and reports any changes. But it reportedly hasn’t been updated or supported since 2017. Anonymous is still looking for suggestions. Post yours! If you’re not already a Lounge member, use the quick registration form to sign up for free. LANGALIST How USB booting leaves a digital trail
By Fred Langa In all but the most extraordinary circumstances, every PC boot — even one that’s using an operating system installed on a USB flash drive — leaves some digital footprints behind. Here are the factors involved … and some of the unexpected places where booting activity might be recorded. Plus: Good and not-so-good duplicate file–finding software. Leave-no-trace PC startup?
Without explaining the no doubt interesting context for his question, reader M.R. asked:
Usually, yes. But it depends on how the PC and the bootable USB were set up — and how hard someone wants to look for those “footprints.” Most PCs built in the last decade use the Unified Extensible Firmware Interface (UEFI; info) for initial startup. And by default, every boot of a UEFI-based PC touches some low-level portions of the installed operating system — even when booting from external devices. That’s just how UEFI works. (For additional UEFI information, see “How to solve UEFI boot and startup problems,” Windows Secrets 2014-12-11.) These low-level actions are usually recorded in system-event logs and other areas, leaving behind a record every time a PC starts up. But here’s another complication: For additional security, UEFI might actively block external booting. The feature is designed to prevent potentially hostile access to your PC’s contents by an unauthorized or unrecognized operating system. Normally, to launch a Windows PC from an external, nonnative OS, you must first disable UEFI booting and enable Compatibility Support Module (CSM) — a built-in “legacy” or “compatibility-mode” system that bypasses or suppresses many UEFI features. Switching to CSM startup isn’t a subtle change. For one thing, it must be set up before attempting an external boot. That process usually takes several minutes, involves at least two system reboots, and requires at least a Windows admin-level password. It could also require a second, firmware/OEM-level password to alter the deepest boot settings. In short, switching to CSM booting is not the sort of change someone can apply on the fly — or via a blink-and-you-missed-it drive-by hack. Typically, using CSM also requires disabling a PC’s Fast Boot — the speedy and default UEFI-controlled startup method now employed by most PCs. Without Fast Boot, a system will almost always take far longer to launch. So as you can see, there’s nothing subtle about any of this. Setting up CSM booting takes some time, effort, and reboots; and the resulting startup sequence will have obviously changed. Sure, these effects might escape the notice of a casual or novice user, but they’d be blatant to anyone who was paying attention. I’d sure notice if my PC’s boot sequence suddenly changed and got significantly longer, wouldn’t you? That leaves you with nonstandard or legacy PCs using the classic BIOS (or equivalent). Those systems might let you boot from USB with little or no trace. But they’re now rare — and usually very, very old. (UEFI started way back in 2005. By 2007, it was becoming nearly ubiquitous.) But even if you do successfully boot a PC without any involvement of the native OS, you may still leave some footprints. For example, many kinds of bootable USB sticks (e.g., flash drive–based Linux) use the PC’s hard drive as temporary swap space for better speed. Although the PC’s OS might not be involved in this action, those “foreign” swap files (or their residue) might be detected afterward. To ensure that nothing’s left behind, you’d have to take pains to guarantee that the external OS won’t interact with the PC’s hard drive in any way whatsoever. There are other possible records, too. Consider the local network: the router or server might record when the PC went online. And your ISP might log when the PC connected to the Internet, what sites were visited, and so on. This information is generally not retained on the PC itself, but it’s still a recoverable record — a trace — of PC operation. So, the fantasy of someone just walking up to a random PC that hasn’t been specially prepped, popping in a thumb drive, and taking over the hardware with absolutely no trace left behind is pretty much just that — a fantasy. That said, there are some exotic techniques for obtaining a PC’s contents without leaving an obvious footprint. For example, RAM freezing, which I described in my 2019-11-11 column. And then there’s the newly discovered Thunderbolt hack. But these attacks require hardware modifications to the PC’s innards — and even then, they still do not allow you to use USB-booting without leaving some evidence. Bottom line: On current PCs, a leave-no-trace startup from a USB drive requires significant advance preparation, alterations to the PC’s basic setup (i.e., switching to CSM boot), specialized knowledge and skill on the part of the perpetrator, and a victim who’s not paying much attention! So although it’s technically possible to boot and use a PC without leaving any record, its exceptionally difficult to pull off. Duplicate Duplicate Finder Finder Apps Apps
Subscriber Roland Swirsky writes:
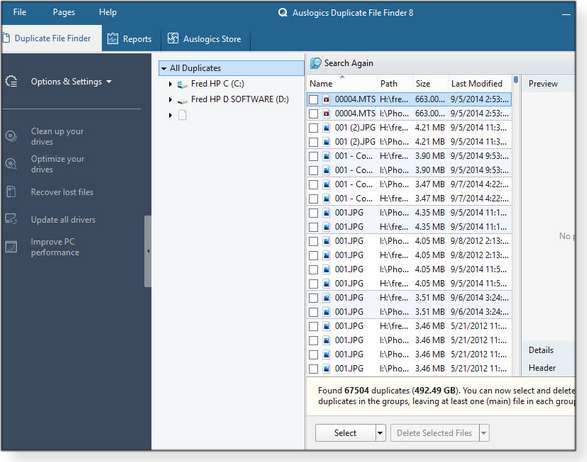
Oh, man; there’s a ton to choose from. In a moment I’ll list four duplicate-file finders I’ve used — one that was very good, two that were OK, and one that was a slug. But in the spirit of full disclosure, I must first say I rarely use this type of software. That’s mainly because disk space costs almost nothing, and the contents of files can be priceless. So I deliberately and consciously retain many, many duplicate files scattered across multiple internal, external, and cloud-storage locations. It’s cheap insurance. For example, some of my most irreplaceable digital files are photos of events that can never be re-created — places I’ll never see again and people I care about. Losing these files would be heartbreaking. Typically, I move the raw, original, full-resolution, unedited photos from my camera to a cloud account and to two local HDDs — one usually live and the other normally disconnected. This way, it’s extremely unlikely that any single calamity would wipe out all three originals. When I want to work on a photo (cropping, straightening, adjusting lighting, and so forth), I’ll make an additional working copy — yet another duplicate — and work on that version. I even save interim copies after each major editing step so I can easily revert to the last-good copy, should — as often happens — my photo-editing experiments go badly awry. By the end of the process, I can easily have a half-dozen different files of a single photo. So that’s why I’m personally not a huge fan of duplicate-file finders. I’d rather soak up a little inexpensive disk space than potentially lose an irreplaceable original or a live working copy. That said, on those rare occasions when I’ve needed to search for unintentional duplicates, my go-to tool is Auslogics’ Duplicate File Finder (free; Figure 1). It can thoroughly search for a variety of duplicate types — files with the same name, files with the same content regardless of name, and so on. As an all-around, general-purpose duplicate finder, I’ve found it hard to beat.
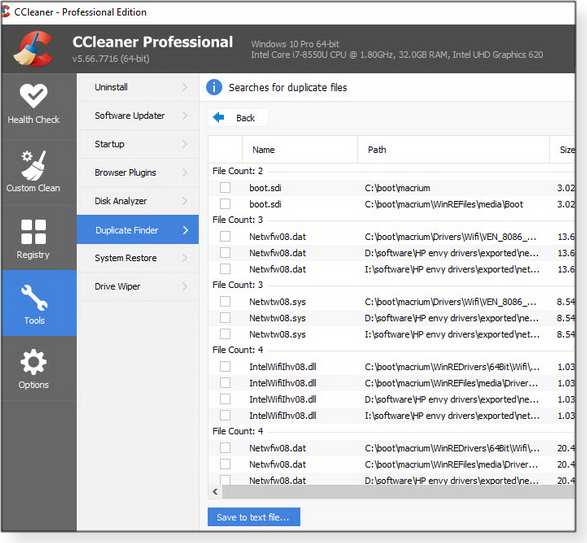
For quick, minor cleanups, I’ll sometimes use the lightweight Duplicate Finder tool built into CCleaner (free/paid; Figure 2). It’s very fast but seems to be driven mostly by simple filename-matching, which typically finds only the most obvious duplicates.
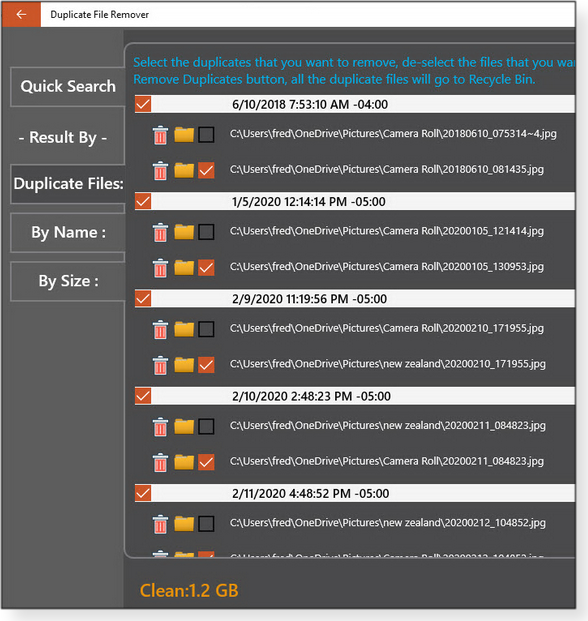
Videopix’s Duplicate File Remover is an easy-to-use, lightweight, native Windows 10 app (free/paid; Figure 3), meaning that it can be auto-reinstalled by Windows after an automated reset or upgrade.
I’ve tried — but can’t recommend — Duplicate Files Finder. (Note the “s” on Files, distinguishing this app from Auslogics’ similarly named product.) It’s an open-source offering, but I found it simplistic, hard to use, and slow. About the only good thing I can say about the app is that it’s free. But there are literally dozens — maybe hundreds— of other similar utilities and services. Just search Google for remove+delete+find+duplicate+files+windows+10. Whether you want to aggressively find and remove all duplicates or just zero in on specific types and locations, there’s definitely a tool out there for you. Try one of the above offerings to get a feel for how this class of software works — and then have at it with the tool of your choice!
Fred Langa has been writing about tech — and, specifically, about personal computing — for as long as there have been PCs. And he is one of the founding members of the original Windows Secrets newsletter. Check out Langa.com for all of Fred’s current projects. PATCH WATCH .NET Framework oddities and ESU issues highlight May patching
For some Windows 7 users, May’s .NET Framework security updates proved to be a patching speed bump. On Patch Tuesday (May 12), Microsoft released .NET fixes for three new vulnerabilities. CVE-2020-0605 is a remote-code execution threat, CV-2020-1066 might allow elevation of privileges, and CVE-2020-1108 could result in denial-of-service attacks. But soon after the updates appeared, Win7 users reported installation failures. The upshot? The patches generally worked fine on systems with genuine (paid) and up-to-date Extended Security Updates (ESU) subscriptions. On the other hand, they failed if you were using the ESU bypass script (more info) — a somewhat controversial technique that can let Win7 users receive ESUs without paying for them. If you’ve gone the “script” route, even downloading the patches from the Microsoft Update Catalog (MUC) site will prove fruitless. This is yet another example of why you should purchase Windows7 ESU keys to keep your systems fully protected. As a reminder, anyone with Win7 Pro can still buy an ESU from Amy Babinchak by filling in the Harbor Computer Services Windows 7 ESU application form. (Home editions are not eligible for an ESU. It’s one of the reasons I continue to recommend that Win7 Home users upgrade to the Pro edition.) Yes, there are some workarounds for installing the .NET fixes without having a paid ESU, as noted on the My Digital Life site (sign-in required). But they make my head hurt, and I think it’s much easier —and it feels a bit more honest — to purchase an ESU subscription. Microsoft might find other ways to enforce ESU licensing down the road. Remember: In order to receive May’s Win7 updates, you must have April’s servicing-stack update KB 4550738 installed. If you need to download it manually, head over to its MUC download page. You should also receive KB 4538483 — released on May 9, it’s a new version of an earlier special ESU installer patch. You can find it on its MUC page. Changes to Patch Watch: For the upcoming second May Patch Watch column, I’ll be making a few modifications. Because Microsoft is pausing its optional updates, I’ll add specific tips for individuals — and I’ll include some server-patching suggestions as well. I’ll also showcase new patching options for Office 365 that will be coming out in May and June. May’s list of Windows 7 vulnerabilities
Here is my regular reminder to Win7 users who are living with unpatched systems: Without current patches, the threats to Win7 systems grow larger with each passing month. To give some perspective on the threats, I’ve started an evolving list of Win7 vulnerabilities; look for the links on our online Master Patch List. If your boss is too cheap to purchase ESUs for the company’s Win7 systems, I suggest you show him or her the list. Also, keep this in mind: The growing list of vulnerabilities gives malicious hackers more and more tools for use in future ransomware and phishing attacks. Popular exploits include older vulnerabilities (more info), Office 365, and flaws in VPNs used by home-based workers. So here are the latest threats that are patched in May: Denial of Service: This form of attack keeps a system so busy that it can’t complete normal processes.
Elevation of privilege: This Windows vulnerability lets malicious hackers acquire admin rights on targeted machines. Typically, the attacker must sign in directly, install a bogus app, and then trick a user into running it. Large businesses have the highest risk.
Information disclosure: Used by attackers to steal information stored in a computer’s memory. That data can then be combined with other exploits.
Remote-code execution: The most dangerous form of exploit, it lets an attacker take complete control of a system. In many cases, the attacker must trick a user into opening a malicious website, image file, font, etc.
Security feature bypass: Typically exploited by malicious hackers in blended attacks. It’s often used for ransomware or other lateral attacks that target networks.
Bottom line: If you must use Win7 — especially in a business setting — you should already have an ESU subscription (more info). Or at the very least, use the 0patch service. May patching summary
For anyone running Windows 10, now is the time to download a copy of Version 1909‘s ISO and tuck it away in a safe place. As Woody noted, Microsoft just posted Windows 10 2004 on MSDN and will start rolling out the new “feature” release in the coming weeks. Like Woody, I recommend deferring major releases until we’re sure Microsoft has ironed out the major wrinkles. You should see Version 2004 offered in Windows Update. But, thankfully, it won’t automatically install — until you give the OK! Of the to-be-patched vulnerabilities, I predict CVE-2020-1048 (Print Spooler elevation of privilege) will be exploited sooner rather than later. There’s already chatter on various websites and Twitter postings about how it’s relatively trivial to type in a command and gain more rights on a system. Although we’re still a ways away from active exploits, we’re keeping an eye on it.
Windows 10
Servicing-stack updates
Cumulative updates
.NET Framework for Windows 10
Windows 8.1/Server 2012 R2
Windows 7/Server 2008 R2 SP1
ESU reminders: I was offered KB 4538483; it’s essentially a re-issue of a special ESU licensing update. It needs to be installed in order to obtain Win7 updates. If you didn’t receive it, download it from the Microsoft Update Catalog site. Be sure you have April’s servicing-stack update KB 4550738 installed (grab it from an MUC download page). Otherwise, May’s patches won’t show up. You’ll also need May’s servicing-stack update KB 4555449 in place to receive June fixes. (It should show up after installing the May updates.) Server 2012
Windows Server 2008 SP2
Office security and non-security updates
May’s Office security updates impact only Excel! Office 2016
Office 2013 SP1
Office 2010 SP2
The following Office non-security enhancements and fixes should also be deferred on production systems until further notice. Office 2016
Office 2013 and Office 2010
These days, more than ever, stay safe out there.
In real life, Susan Bradley is a Microsoft Security MVP and IT wrangler at a California accounting firm, where she manages a fleet of servers, virtual machines, workstations, iPhones, and other digital devices. She also does forensic investigations of computer systems for the firm. Best Utilities Freeware Spotlight — Open Hardware Monitor
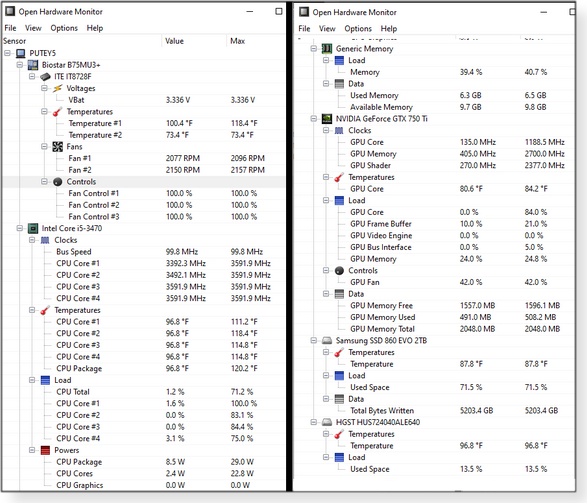
Some of the most difficult computer problems to diagnose and resolve are random errors — those inconsistent blue screens, those arbitrary freezes and shutdowns, those odd Windows glitches. A common cause of random system failures is overheating — one or more hardware components running at higher-than-safe temperatures. Sure, spring might bring warmth and fresh flowers, but it also delivers shedding pets and lots of other airborne particles that clog up PC fans and put additional stress on CPUs, power supplies, and video cards. So how do you know whether something is overheating? Michael Möller’s Open Hardware Monitor (OHM) can help provide an answer. This small, completely portable, open-source utility has a deceptively simple function: it reads and displays the various temperature and fan-speed sensors in your PC, providing a real-time report on system cooling. In fact, on my relatively modest system, it gave so much info that two screenshots were required to show the stats (see Figure 1). Your list might be somewhat shorter, depending on the PC’s components.
Starting from the top of my list, OHM shows system voltage, temperature, and fan speed readings from the ITE IT8728F (system-monitoring) chip located on my motherboard. Next is the data from the machine’s Intel Core i5 processor, showing clock speeds and temperatures for individual cores. It also gives each core’s load and power usage. Under Generic Memory, OHM lists the system’s current level of RAM use and memory load. (In tests, it matched up closely with the numbers reported by Windows’ Task Manager.) Up next is video stats. My NVIDIA GeForce GTX 750 Ti card provides a boatload of information, including clock speeds, temperature, load, fan speed, and memory use. (If you have dual screens, keep OHM open on one display and run a stress-inducing video game on the other.) For hard drives, OHM is showing my SSD’s temperature — plus the amount of space used and bytes written. My HGST (good ol’ spinner drive) provides only temperature and consumed space. In short, OHM can display nearly any information a system component audits and reports. Advanced options
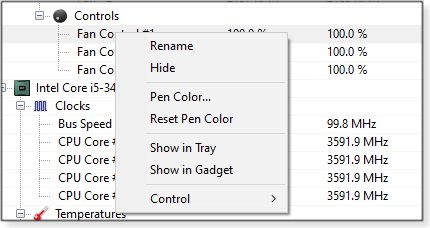
Is there a statistic you want to pay particular attention to? Right-click it to open the context menu shown in Figure 2.
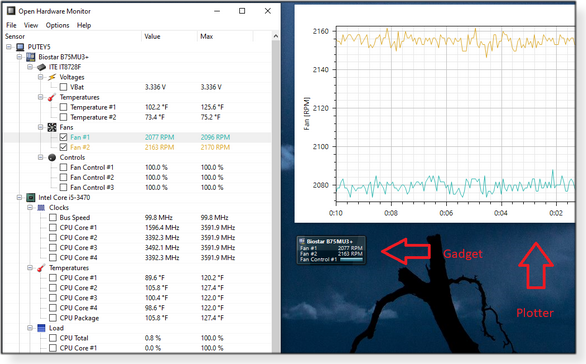
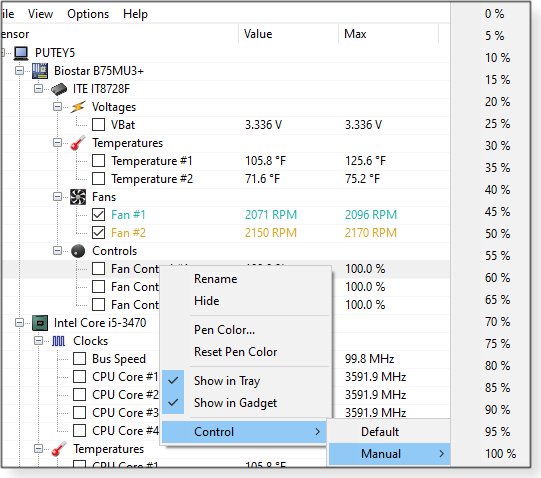
You can rename an item to something more descriptive, such as “That dying fan” or “MrFannyMcFanFace.” If you want to see its changing stats on a plot, click View in the top toolbar and then check Show Plot; next, click the checkbox to the left of the item’s name. That will start a live graph of one or more components’ monitored data. For example, in Figure 3, I’m keeping an eye on fans #1 and #2. Use the context menu’s Pen Color option to further highlight a component. Other options in the context menu include Show in Gadget, which appears as a small box on the Windows desktop (Figure 3) and View in Tray, which shows up in the Windows taskbar (Figure 4). Note: Show in Gadget won’t show up until you click View/Show Gadget in the top toolbar.
My PC also allows user control over fan speed, as shown in the Controls group (under ITE IT8728F). Here, the context menu for Fan Control #1 offers the Control option. Selecting Manual lets me set a percentage of maximum fan speed (see Figure 5).
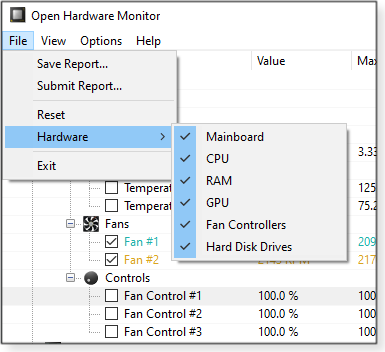
You can further filter information that OHM displays by clicking File/Hardware from the top toolbar. As shown in Figure 6, you can select or deselect a variety of system components.
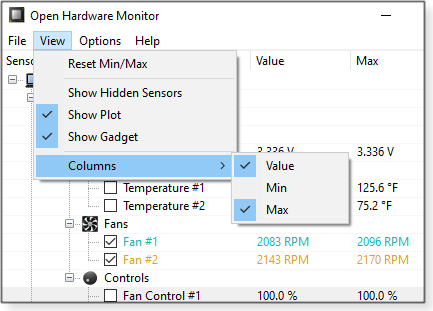
Other options under File include reports of a system’s environmental activity — or reports submitted to the OHM project to help it build a better product. You can also reset settings with one click. Under View, clicking Reset Min/Max simply changes those numbers to the current Value. (By default, the minimum-value column is not displayed — see Figure 7 — but you can restore it via View/Columns.)
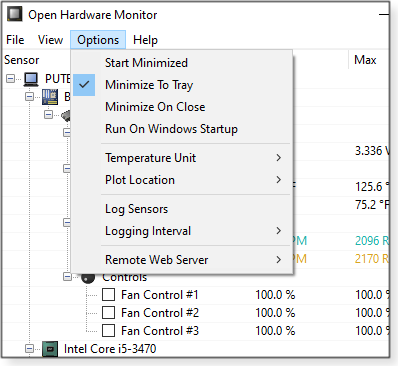
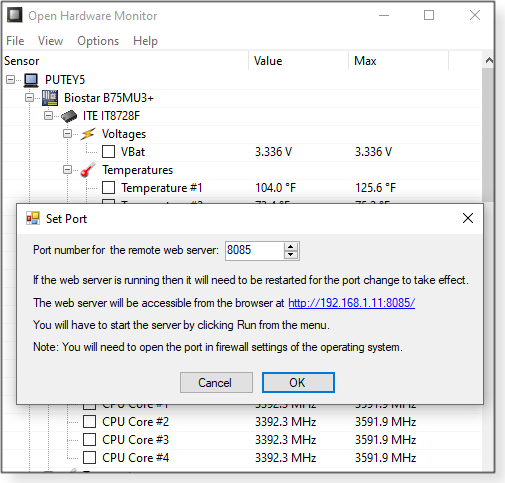
With the toolbar’s Options, you get control over other aspects of OHM: temperature units, startup, plot location, and more (see Figure 8). You can even set up the utility so it can be monitored over the Internet! (See Figure 9.)
A couple of final notes: OHM is technically in beta — and has been for about a decade. (Now that’s some beta testing!) As such, there’s no real documentation, no users’ guide. Fortunately, it’s not all that difficult to figure out — for the most part. For instance, I could find no information on the app’s somewhat opaque Parameters option (included with some context menus). That said, this is an excellent tool for eliminating overheating as a cause of system failures. It’s a must-have for your troubleshooting kit. Go grab a copy from OlderGeeks’ Open Hardware Monitor page. Happy Computing!
Deanna and Randy McElveen are celebrating over 20 years in the computer business, ten years running OlderGeeks.com, and more than 26 years of putting up with each other. Their computer store is in a small town in the Missouri Ozarks. Believing that happy customers are always the best advertisement, they hope to do it for another 20 years. Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com). Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners. Your email subscription:
Copyright © 2020 AskWoody LLC, All rights reserved. |




 By Susan Bradley
By Susan Bradley What to do: We’re officially in the patch wait-and-see period. Confirm that you have Windows Update paused on production systems. Use the next couple of weeks to check out May’s fixes on test machines only! Windows 7 users should make sure they have all the needed servicing-stack updates in place. As always, you can find a recap of past patches on our online
What to do: We’re officially in the patch wait-and-see period. Confirm that you have Windows Update paused on production systems. Use the next couple of weeks to check out May’s fixes on test machines only! Windows 7 users should make sure they have all the needed servicing-stack updates in place. As always, you can find a recap of past patches on our online  By Deanna McElveen
By Deanna McElveen