
|
Patch reliability is unclear. Unless you have an immediate, pressing need to install a specific patch, don't do it. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
Microsoft’s six free desktop security tools
In this issue
- TOP STORY: Microsoft's six free desktop security tools
- WACKY WEB WEEK: Ice cubes bigger than chunks of Manhattan
- LOUNGE LIFE: How to share big video files privately
- LANGALIST PLUS: Are both PC and router firewalls necessary?
- BEST PRACTICES: Two ways to put Windows 7 and 8 on the same PC
- ON SECURITY: Working with the real Microsoft Support
Microsoft's six free desktop security tools
These free utilities can prevent or cure trouble caused by viruses, worms, spyware, keyloggers, and other kinds of unwanted software.
Whether you’re keeping your PC free from malware or cleaning up a PC that’s already infected, one or more of these tools should get the job done!
Most Windows users probably don’t know that Microsoft offers an array of free security tools. Some are included with Windows, others available by download.
At one end of the spectrum is a simple, lightweight utility — the Malicious Software Removal Tool — that protects against some of the most common malware in circulation. At the other end of the spectrum is a heavy-duty system-scanning tool — Windows Defender Offline — that operates from its own bootable medium. It operates completely outside the installed Windows, allowing the scanner to find and remove some forms of malware that standard Windows-based security tools might miss.
As is all too common with Microsoft, some of these tools (and their features) are somewhat difficult to find. Some tools are poorly explained; some tools’ functions overlap with those of other tools. Two of these tools even have the same name — but are totally different products!
This article should sort out the confusion; it briefly explains what the six tools are, what types of malware they target, how they work, how to access and use them, and other important facts. You’ll also find links to more detailed information — and, of course, links to the free downloads.
Let’s dive in!
The target: Malware, as Microsoft defines it
Microsoft divides malware into two broad loosely defined terms: malicious software and potentially unwanted software. The first category covers mostly self-replicating Trojans, viruses, worms, and similar code that infects your PC (typically for some evil purpose) and then seeks to infect other PCs.
The second category — potentially unwanted software — includes undesirable (and often hidden) apps such as spyware that surreptitiously tracks you, keyloggers that capture everything you type, and adware that force-feeds you popup ads. The somewhat clumsy phrase “potentially unwanted” is meant to suggest that you might not want the software if you knew what it really did.
These two categories aren’t precisely mutually exclusive. For example, some potentially unwanted spyware is also self-propagating, like a virus. What’s more, Microsoft sometimes uses the terms interchangeably. Still, these two categories will help you understand the main purposes of Microsoft’s security tools.
The Microsoft Malicious Software Removal Tool
What it is: Microsoft’s Malicious Software Removal Tool (MSRT; more info) is a basic antivirus program. It comes in all current versions of Windows — XP, Vista, Windows 7, and Windows 8. When you install Windows, MSRT is enabled by default.
What it does: MSRT automatically removes malicious software (viruses, worms, etc.) that, based on Microsoft’s internal research, is considered especially prevalent and dangerous to Windows users. MSRT currently targets about 200 of the most common malware types. You’ll find a list of them on the MSRT download page.
How it works: Windows Update automatically refreshes MSRT once a month (it’s always KB 890830), usually on the second Tuesday (aka Patch Tuesday). After updating, MSRT automatically runs, scanning your PC once and removing any active malware infections it finds. No user intervention is required.
One scan a month isn’t especially good malware protection, but you can also run MSRT manually any time you wish (see Figure 1). Simply enter mrt.exe in the XP/Vista/Win7 Start menu Search box or Win8’s Search window and press Enter. Once open, MSRT gives you a choice of quick, full, or custom scans. As you’d expect, the full scan is the most thorough.
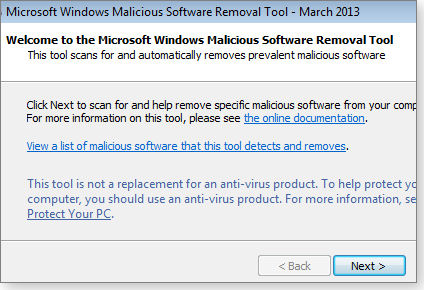
Figure 1. The Malicious Software Removal Tool is built into your copy of Windows, and provides basic protection against a selection of common malware threats.
If you want or need a fresh copy of MSRT, it’s available via download pages for the 32-bit or 64-bit versions.
Important to know: MSRT is a strictly post-infection tool. It detects and removes malicious software from already-infected computers — and only if the malware is active and running at the time of the scan. But as MSRT Support article 890830 clearly states, the list of malware it detects represents only “a small subset of all the malicious software that exists today.”
MSRT can’t prevent new malware infections. It also doesn’t target potentially unwanted software (again: spyware, adware, etc.).
Bottom line: MSRT is a “better than nothing” anti-malware tool. There’s no real downside to keeping it on your system — its footprint is small, its impact on system operations is negligible, and it can serve as a kind of last-ditch defense against some very common malware types, should they somehow make it into your system.
But you certainly shouldn’t depend on MSRT as your only or primary defense against malicious software; it’s an incomplete anti-malware solution.
Windows Defender (XP, Vista, Win7 version)
What it is: Windows Defender is a basic tool for guarding against potentially unwanted software. Windows Defender is installed by default in Vista and Win7, and it’s a free download for XP.
What it does: Windows Defender provides always-on, real-time protection against spyware, adware, keyloggers, and so on. It self-updates and runs automatically.
How it works: Windows Defender continually monitors your PC’s files and browsing activity. When it detects potentially unwanted software, it opens a dialog box and lets you decide whether to proceed with the installation. (For more information, see the related Microsoft support article or TechNet’s Windows Defender Guide.)
You can also trigger Windows Defender (shown in Figure 2) manually whenever you want to scan your PC for spyware and other potentially unwanted software, as a Defender support article explains.
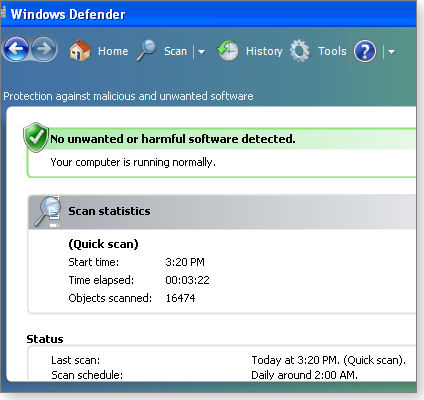
Figure 2. Windows Defender for XP, Vista, and Win7 offers real-time protection against adware, spyware, and similar potentially unwanted software.
XP users can download either 32-bit or 64-bit versions.
Important to know: Windows Defender doesn’t detect or remove viruses, worms, and similar malicious software.
Bottom line: Windows Defender complements Microsoft’s Malicious Software Removal Tool. And just like MSRT, it’s better than nothing. Together, MSRT and Defender are a sort of last line of defense — potentially helpful if no other anti-malware tools are active. Fortunately, superior tools are readily available (see next sections).
The all-in-one Microsoft Security Essentials
What it is: Microsoft Security Essentials is Microsoft’s all-in-one, consumer-security tool. It targets both types of malware — malicious software and potentially unwanted software. It’s a free download (site) for XP, Vista, and Windows 7.
What it does: MSE provides always-on, real-time protection for your PC. It detects and removes a wide range of malware. It’s also highly automated, operating with little or no user intervention (see Figure 3).
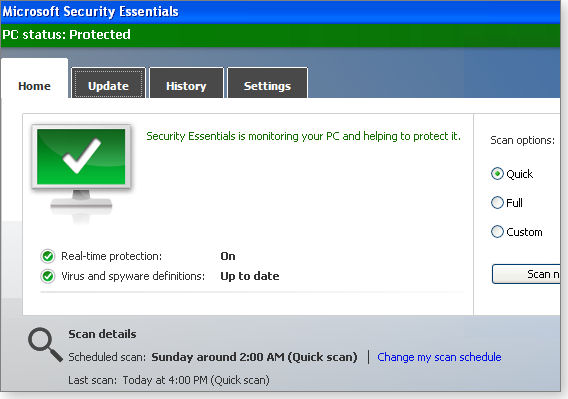
Figure 3. Operating almost entirely automatically, Microsoft Security Essentials (MSE) provides real-time protection against malware and potentially unwanted software.
How it works: By default, MSE runs continuously in the background whenever your system is on. It updates itself every day. Along with its real-time protection, it also runs scheduled scans of your PC’s memory and files. If you use its default settings, MSE requires almost no user input. But it’s also highly configurable, should you want to change its standard routines.
Important to know: MSE must be manually installed; it’s not built into any version of Windows. On MSE’s MS Download Center page, you’ll find 32- and 64-bit versions for XP, Vista, and Win7.
Typically, to avoid conflicts between AV products, a PC should run only one real-time, anti-malware/anti-spyware tool at a time. In other words, you can run MSE or Windows Defender, but not both at the same time. In fact, when MSE is installed, it disables Windows Defender.
In a similar vein, if you’re running some other always-on, anti-malware tool, you should disable or uninstall that tool before installing MSE. (MSE can’t disable non-Microsoft AV scanners.)
MSE’s principal weakness? It’s not especially adept at guarding against user error, as detailed in the April 7, 2011, Top Story, “LizaM*n infection: a blow-by-blow account.” If you click past security warnings raised by Windows, your browser, and/or MSE itself, MSE will step aside and let malware install. Moreover, based on recent antivirus testing, MSE is currently not among the top-performing AV products.
All of which means that MSE is not the ideal choice for casual or inexperienced Windows users, who are often more easily tricked into installing malware.
In addition to the aforementioned Top Story, Windows Secrets has extensively covered MSE — including its advantages and deficits — in previous issues. Use these links if you’d like to read more:
- “The 120-day Microsoft security suite test drive,” May 6, 2010, Top Story
- “Security Essentials test drive — month 6,” Sept. 16, 2010, LangaList Plus
- “Two great security tools get free updates,” Jan. 13, 2011, Top Story
- “Is your free AV tool a ‘resource pig?’,” Feb. 16, 2012, Top Story
- “MS Security Essentials: Poor showing in new test,” Dec. 20, 2012, LangaList Plus
Bottom Line: In the right hands — primarily experienced Windows users — MSE is a fine, free security tool. I use it on my XP, Vista, and Win7 machines, and I’ve never run into trouble with an infection.
Windows Defender: Win8’s built-in security tool
What it is: Microsoft has a long history of confusing product names. In this case, the Win8 version of Windows Defender is nothing like the original Windows Defender for XP, Vista, and Win7. It is, in fact, effectively a renamed version of Microsoft Security Essentials.
What it does: In Microsoft’s own words, the Win8 version of “Windows Defender provides the same level of protection against malware as Microsoft Security Essentials.”
How it works: Win8 Defender is virtually identical to MSE in both appearance (see Figure 4) and function.
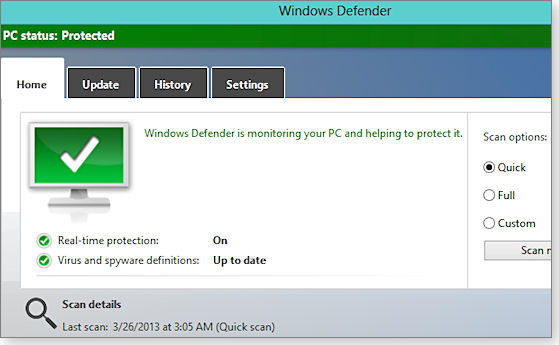
Figure 4. Despite its name, Win8's built-in Windows Defender is really just a renamed and minimally altered version of Microsoft Security Essentials.
Important to know: Unlike MSE, Win8 Defender is built into the OS — so there’s nothing to download or install.
Bottom Line: Because Win8 Defender is really a rebranded version of MSE, I don’t recommend it for novices and inexperienced users. But it’s probably fine for anyone who takes the entire process of PC security seriously. I use it on my Win8 systems.
Two special-purpose cleanup tools
No software is perfect — that includes all anti-malware tools, from all vendors. Should your AV product fail and your system become infected, you need a powerful cleanup tool to find and remove the malware.
It’s also good practice to verify that Windows is truly free of malware — even if your full-time scanner appears to be working — by periodically running an AV tool that operates completely on its own.
Microsoft offers two such special-purpose, cleanup/verification tools. Microsoft Safety Scanner is exceptionally simple to use — just click and run. Windows Defender Offline is harder to use, but it employs the best possible techniques for detecting malware hidden at even the deepest levels of your system.
Microsoft Safety Scanner is a Windows security utility that thoroughly scans your PC (see Figure 5) to find and remove both malicious and potentially unwanted software. A standalone application, it’s active only when it’s actually running a system scan. (It’s not constantly on in the background.) That lets it coexist peacefully with whatever full-time anti-malware software you’re using.

Figure 5. Microsoft Safety Scanner works independently of your other security tools and can clean an infected system — or verify that no malware is present.
Microsoft Safety Scanner is compatible with all current Windows versions: XP, Vista, Win7, and Win8. Its info/download page includes 32- and 64-bit versions.
Safety Scanner is extremely easy to use; simply download and launch it, and then select whether you want a quick, full, or custom scan. At the end of the scanning process, you’ll get a report of what Safety Scanner found and removed.
Windows Defender Offline (WDO) is Microsoft’s most powerful anti-malware tool for consumers. It’s a self-contained, downloadable utility that operates completely outside Windows. After you’ve downloaded and launched WDO, it steps you through the process of creating bootable media (CD, DVD, flash drive, etc.) and installing the WDO files. You then restart the PC with the bootable disc/drive.
Because WDO is both operating system and AV scanner, neither the Windows installed on the system hard drive nor any other software is active. Everything on the hard drive is effectively inert. This lets WDO detect malware that is in one way or another well hidden in the Windows system. Because it’s completely standalone, WDO can’t conflict with other security tools you normally use.
WDO targets a wide range of malicious and potentially unwanted software. In operation, it looks and functions almost exactly like Microsoft Security Essentials or the Win8 version of Windows Defender.
If WDO has a weakness, it’s in the task of creating the WDO media. If your system is having difficulty running because of an infection, you’ll need either a working system to build the WDO media or you’ll need to have media you created before the infection (in which case you might not have the latest virus signatures). If you have only one PC, I recommend putting the latest version of WDO on a flash drive once a month or so.
You’ll find both 32- and 64-bit versions of WDO for all current Windows versions (XP through Win8) on its info/download page.
Putting it all together
The following table (Figure 6) is your one-stop reference for Microsoft’s six desktop security tools. It concisely summarizes which Windows versions they’re for, which kinds of malware they target, and whether they’re for prevention or cleanup/verification.
Take your pick: they’re all free!
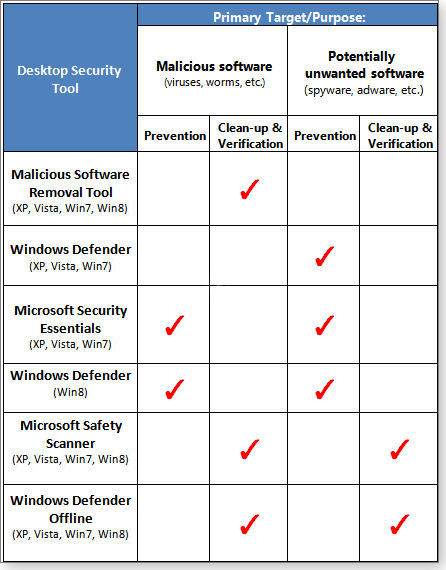
Figure 6. Microsoft's six desktop-PC security tools
Ice cubes bigger than chunks of Manhattan
 |
By Kathleen Atkins In May 2008, filmmakers were on hand to witness a calving event in western Greenland — the largest ever recorded on video. The retreat of the Ilulissat Glacier roiled the ocean for 75 minutes and momentarily sent chunks of ice twice the height of Manhattan skyscrapers into the air. This footage is part of the award-winning film, “Chasing Ice,” presently playing in theaters. It puts a whole new spin on the phrase “on the rocks.” Play the video |
How to share big video files privately
We’re long past the old days of shared dinners and long nights of vacation slides.
Now when you want to assemble trip memories, it could easily be a video that you make available to your companions. But how to share a big file securely? That’s what Larry98765Ottawa asked the Lounge members in the Graphics/Multimedia forum. He was happily surprised by the workable suggestions he received there.
The following links are this week’s most interesting Lounge threads, including several new questions for which you might have answers:
 starred posts: particularly useful
starred posts: particularly useful
If you’re not already a Lounge member, use the quick registration form to sign up for free. The ability to post comments and take advantage of other Lounge features is available only to registered members.
If you’re already registered, you can jump right in to today’s discussions in the Lounge.
Are both PC and router firewalls necessary?
Running two firewalls — in Windows and in a router — might seem redundant, but there are good reasons to do so.
Plus: Security concerns about Windows Error Reporting, advice on differential copying/synching software, and getting a balky browser add-in to work.
Concerned about outbound, ‘phone-home’ activity
Reader Harry M. Ward is trying to sort out some firewall issues.
- “I’ve read your excellent Feb. 28 article, ‘Using multiple layers of security — an update.’ I’ve also read the March 11, 2010, LangaList Plus item, ‘Let’s put your firewall to the test.’
“I just tested my router’s firewall, using the sites recommended in those stories. The tests that check the firewall’s ability to stop inbound connections found all of my ports ‘stealthed’ and invisible from the outside. But the firewall failed the leak tests — it doesn’t stop outbound connections. Should I be worried?
“Also, I’ve been told I don’t need a PC-based firewall because all ports are stealthed by the router. Is that true? (I run XP Pro SP3 on one computer and Windows 7 Pro SP1 on another.)”
Good questions, Harry. Let me answer them in reverse order:
I believe every PC should have its own internal firewall, even if a router or other external device has an operating firewall. Often there’s no obvious indication that an external firewall is working. If it fails and leaves you unprotected, you’re none the wiser.
Windows, on the other hand, constantly checks for a working PC-based firewall. If that firewall fails or is turned off by accident, malware, or some other cause, Windows alerts you via a security message in the notification area.
Although this monitoring works with various user-installed, third-party firewalls, it works best with Windows’ own firewall. I recommend — and use — the firewalls included with Vista, Windows 7, and Windows 8. They’re efficient and free, they add minimal overhead to the PC’s operation, and they have a negligible impact on network speed.
XP’s firewall, on the other hand, is 13-year-old technology that’s relatively primitive by current standards. For XP users, I recommend a third-party product such as Comodo Firewall (site; free and commercial versions). A Web search will yield many alternative choices as well.
As for inbound/outbound blocking, I believe a firewall’s main purpose is guarding against inbound attacks — attempts by unauthorized persons to find and access your PC from some external location on the Internet or other connected network. These inbound attacks are a real and persistent threat.
I’m far less concerned about a firewall’s ability to monitor and block malicious outbound connections — for example, malware phoning home. If malware is trying to phone home, you’ve already lost the battle! Your PC is infected and might already be thoroughly compromised.
If you have strong defenses that prevent malware infections and your PC stays clean, outbound/phone-home protection is effectively irrelevant.
With that said, you are, of course, free to use outbound blocking. You can use a third-party firewall that provides outbound blocking, or you can enable it in Windows’ built-in firewall. The March 17, 2011, LangaList Plus article, “Outbound blocking for Windows Firewall,” provides a description of tools and techniques.
Here’s an update to that article: The recommended Sphinx Software tool, Firewall Control, now comes in various free and commercial versions (with, of course, differing capabilities) and supports all versions of Windows from XP through Win8. See the Sphinx Software site for more information.
Bottom line: I definitely recommend using a PC-based firewall; don’t worry about outbound blocking.
Is ‘Windows Error Reporting’ a security threat?
John Whalley wonders whether sending crash reports to Microsoft constitutes a potential security threat.
- “About once every seven to 10 days, I get a popup that says, ‘Microsoft Windows has encountered a problem and must close {application}.’ The popup gives me the option to report the problem to Microsoft. In the past, I’ve always opted to do so.
“First question: Should I continue to let Microsoft receive the reports? Is it possible these reports could be part of a support scam?
“Second question: What does Microsoft do with this information?”
Windows Error Reporting (WER) is a technology that’s been in every version of Windows from XP onward. It captures data about software crashes and hangs when they occur in end users’ PCs. With a user’s approval, the information gathered about a particular software crash/hang is sent to Microsoft, where it’s crunched to see what’s crashing, how often, and why.
In theory, this lets Microsoft identify and possibly fix the bugs that need the most attention — those that are impacting large numbers of users out in the real world. If there’s a fix of a particular bug, it should eventually show up as a Windows Update item. (For more information, see the MSDN article, “Windows Error Reporting: Getting started,” or the TechNet article, “Windows Error Reporting.”)
WER’s upside is clear: It helps Microsoft find and quash real-life bugs we might encounter. But there are also potential downsides.
For example, Microsoft permits some third-party software vendors to use WER data to learn why and how their software crashes in Windows. These are not the repair-service scam companies that make those cold calls: “Hello. We see you’re having trouble with your PC. We can fix it for a small fee. …”
Still, access to WER data by selected third-party companies means that the reporting system is not a completely closed loop — it doesn’t include just you and Microsoft. So there’s a small possibility of abuse.
Another issue: Although WER doesn’t intentionally collect personal data, a crash dump (a listing of what was in RAM at the time of the crash) could conceivably contain some scraps of personal information.
So whether to submit those reports to Microsoft comes down to a judgment call. I believe WER is pretty harmless. In most cases, I let the system send crash reports to Microsoft. But if you’re uncomfortable sending in the data, just say, “No!”
Software that backs up but doesn’t compress data
Keith Pauli is looking for a way to sync his PC’s drives with a network-attached storage (NAS) device.
-
“I’m looking for software that will keep my documents, scans, pictures, etc. in sync between my main [PC-based] hard drive and my NAS device. It must keep track of modified/added files on my main hard drive and update them on the NAS drive.
“I’m not looking for the typical backup solution, which compresses or encrypts backup data and stores it on my NAS. I want exact copies on the NAS because I can access the device remotely when traveling. Can you help? “
Sure, Keith. Your situation is similar to a folder-synching question that came up a couple of months back. And the same answer applies.
I know of two free programs that can sync files, folders, or entire drives between a PC and various other accessible devices — PCs, USB drives, networked drives, phone-based storage (e.g., for music files), and so on — in other words, any device that can be accessed via Windows Explorer or through Windows Networking. Neither application adds any compression or encryption to the copied data. All they do is clone data from a source device to a target device.
The first is Microsoft’s SyncToy (site); the other is a tool I use every day — the late Karen Kenworthy’s Replicator (site).
For more information (and screen shots), see the Feb. 7 LangaList Plus item, “Seeking a viable replacement for Live Mesh.”
Solving problems with browser add-ins
Ulf Smith’s specific problem is between Internet Explorer 9 and RoboForm. But the answer for Ulf applies to other troublesome browser add-ins as well.
-
“In Fred’s articles, he often refers to the use of RoboForm for safely storing many passwords under one master password.
“I’ve used RoboForm for a long time, but the combination of RoboForm and IE 9 is annoying. Every time I start IE 9, I have to go into its Manage Add-ons tool and enable RoboForm.
“I’ve contacted RoboForm, but their advice has not led to a solution. Any suggestions?”
If you try a browser add-in and it doesn’t work, here are three possible solutions.
- Start by working the problem from the add-in vendor’s side of things — checking its support forums or contacting tech support.
- Since you tried RoboForm’s suggestions and they didn’t work, try resolving the problem from the browser side. Simplify your browser setup by returning it to its just-installed state. By removing all third-party add-ons, plugins, etc., you start with a clean setup. You then rebuild the browser with just the add-ons you really need and want.
Resetting a browser is easy. For example, with IE 8, 9, and 10, simply select Tools/Internet Options/Advanced. Next, click the Reset button under Reset Internet Explorer settings. Restart IE, and you’ll have a fresh slate on which to install RoboForm — or whatever other add-ons you desire. (For more details, see the Jan. 6, 2011, LangaList Plus item, “Return IE to its just-installed state with ease.”)
- If that doesn’t work, you’re really left with just one option: finding an alternative product that does work.
There are some excellent, alternative password-keeper utilities available. For example, take a look at Password Safe (free; site) and KeePass (free; site). Surely one of them will work with your setup, and — unlike RoboForm — they’re both 100 percent free!
Good luck, Ulf!
Two ways to put Windows 7 and 8 on the same PC
For numerous reasons, you might want to have Windows 8 and Windows 7 on the same PC.
There are two common techniques for installing multiple operating systems on one machine. Here’s how to choose between the two.
Living in a dual-Windows environment
Take a poll of experienced Windows users, and you’ll find few who are ambivalent about Microsoft’s newest operating system. Typically, there’s one group that loves the new “Modern” (née Metro) interface and another that dislikes it intensely. Love it or hate it, many veteran Windows users are simply trying to learn to live with it.
If you’re still in the discovery phase with Windows 8 — still trying to decide whether to commit to it — or you’re making a slow and careful migration to the new OS, having both operating systems on the same system makes good sense. And there are two ways to do it: install one Windows on a virtual machine or create a dual-boot system with each Windows on a separate partition. (Yes, some PC users might want to install Windows 7 on a machine that already has Win8.)
Whether you use a virtual machine or dual-boot, each technique has its particular pros and cons. For example, using a virtual machine is typically less risky. As far as the host Windows (the one that boots when you power up your system) is concerned, you’re just installing another application. On the other hand, virtual machines can have daunting compatibility problems.
A dual-boot approach usually provides better compatibility, but setting it up entails resizing partitions and changing how your PC boots.
In this first article of a two-part series, I’ll explain what you need to know before choosing either a dual-boot setup or a virtual machine. The descriptions assume you’re adding Windows 8 to an existing Win7 system. But the instructions apply to the other way around, too — or if you’re adding Windows 8 to a Vista Computer.
Installing Windows 8 on a virtual machine
Think of a virtual machine (VM) as a computer inside another computer — except that the virtual computer’s “hardware” is completely emulated by software. Though the virtual machine looks like just another application to the host system, the OS running inside the VM sees its own computer — with its own unique storage, RAM, graphics subsystem, and so on. And the guest OS runs just as it would on real hardware: you install it, boot it, launch applications from the Start menu, and shut it down when you’re done.
The complex part of a virtual machine is the guest OS’s need to communicate with the real world. For example, it needs a connection to the network and the Internet, to physical USB ports, and possibly to real optical drives. To do all that, the guest OS communicates with the host OS via the virtual machine’s software.
Two of the most popular free VM programs are VMware’s VMware Player (site) and Oracle’s VirtualBox (site). VMware Player is a stripped-down, intentionally limited version of a U.S. $250 professional program. VirtualBox is strictly free — there’s no “professional” version with more features.
Of the two applications, VMware Player (Figure 1) was the easier one to set up. On the other hand, VirtualBox has features that VMware intentionally left out of VMware Player. For example, VirtualBox lets you take snapshots of the current virtual machine state so you can save multiple versions of a VM, restore one you want to use, go back to an older one, or delete the VMs you’ll never use again.
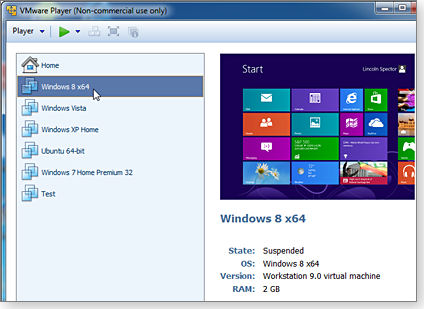
Figure 1. VMware Player is the less richly featured, free version of VMware's Fusion Professional.
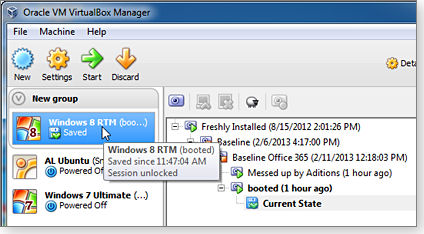
Figure 2. Oracle's VirtualBox is a bit harder to set up than VMware Player but has more features.
Based on my experience, VMware Player also has fewer compatibility issues than does VirtualBox. More on that below.
Whichever program you use, when setting up a virtual machine, you don’t have to alter your hard drive — or your installed version of Windows 7 — in any significant way. If something goes decidedly wrong while you’re setting or running Windows 8 inside a VM, your primary Windows 7 system should be unaffected. (That said, it’s always good policy to make a system backup before installing any major software such as a virtual machine app.)
Another significant advantage of virtual machines: You’re running both host OS and guest OS simultaneously. That means you can quickly switch from one to the other and, with the addition of special software, copy or move files between the two.
Unfortunately, file sharing is not as easy as it should be. For the most part, a virtual machine is an isolated system. The guest OS can typically access only selected folders on the host system via a virtual network.
Enabling sharing is usually an additional setup process, after you’ve set up the guest OS. When it goes smoothly, it’s no great challenge. But that’s not always the case: I’ve yet to successfully make Windows 8, running inside VirtualBox, share files and folders with my host Win7 system.
Sharing in VirtualBox requires the installation of VirtualBox Guest Additions software — which can present some real challenges. Some users find that Guest Additions installs easily; many others — including me — are not so lucky. And when I finally did get the software installed, it messed up the VM’s video beyond use. Fortunately, VirtualBox’s snapshot feature let me restore a working environment — but without sharing.
Other problems with a virtual machine include the tax on system resources, display resolutions, and peripheral sharing. For example, when it’s running, a virtual machine consumes a significant amount of system resources — especially RAM. You’re not going to want to run a VM on a PC with only 1GB of system memory. 2GB will work, but 4GB is better. (I use 8GB.) Also, that virtual hard drive you set up takes up real hard-drive space.
Often you’re viewing a virtual machine as a window on your desktop. Sometimes, the screen resolution for the virtual desktop never seems quite right. Moreover, you might have to enable and disable communication between the guest OS and one or another of the physical peripherals as you switch between guest and host operating systems.
If you’re checking how well Windows 8 works with your hardware, running the OS in a VM won’t give you a true answer. In a virtual machine, the emulated hardware is not the same as the PC’s actual hardware. That means that Win8 (the guest OS) is operating in a different environment — with different drivers — than it would if installed directly on the PC.
Finally, when you create a virtual machine and install Windows 8 into it, the installation process assumes you’re setting up a virgin computer — one free of any operating system. That means you have to use a full OEM version of Windows 8; there’s no option for using the somewhat less expensive upgrade version. That’s a particularly expensive choice if you purchased the upgrade for $40 during the brief time Microsoft sold it at that price.
Installing Windows 8 on the real machine
Installing Windows 8 as a dual-boot alongside Windows 7 eliminates many of the compatibility issues of a virtual machine but imposes its own set of problems and limitations. For example, in a dual-boot setup, you’re running one OS or the other, but not both. Switching from Windows 7 to Windows 8 — or from Windows 8 to Windows 7 — requires a full reboot.
Setting up a dual boot also requires changing your PC environment in some significant ways — including repartitioning your hard drives. More on that in Part 2.
On the plus side, a dual-boot system gives you two complete operating systems that are set up for your existing hardware. If you decide that Windows 8 is your future, you’ll know precisely how it will work with your PC, and you can simply kill off the Win7 setup.
When you install Windows 8 on your real computer, the installation process sees Windows 7 and treats the Win8 install as an upgrade — even if you’re installing it onto another partition, which you should. That means you can use a cheaper Windows 8 Upgrade instead of a full OEM version.
Part 2: Setting up a Win7/Win8 dual-boot system
For the most part, setting up Windows 8 in virtual machines is relatively simple and intuitive. Setting up a dual-boot system takes more work and, as mentioned above, typically requires significant changes to your hard-drive configuration. It’s not something inexperienced Windows users should tackle.
In Part 2 of this topic, I’ll cover how to set up a Win7/Win 8 dual-boot machine. Stay tuned.
Working with the real Microsoft Support
With so many stories about bogus Microsoft Support calls, it’s a sure bet many Windows users wonder what an official Microsoft Support experience is like.
Here’s what you will — and won’t — experience if you contact Microsoft for Windows, security, and application support.
Before we start, one caveat: This article was written on a computer located in the United States. That means all the support/security offerings discussed are U.S.-based. They don’t reflect the links and experiences you might receive if you’re residing in another country. Microsoft makes varying support offerings for each geographic region and language (click the country/language name at the bottom of the MS support options page to see the entire list). Thus my experiences will not necessarily match yours.
Microsoft doesn’t have your phone number
It seems that every week we hear of someone getting a phone call from some scammer pretending to be a technician from Microsoft Support. Fred Langa detailed one Windows Secrets reader’s experience in the Feb. 28 Top Story, “Security alert: Bogus tech-support phone calls.” These “techs” have various malicious goals including: tricking you into giving them direct access to your computer, giving them money to “fix” problems that don’t really exist, and/or letting them plant malicious software on your system.
In a moment, I explain what to expect from a real Microsoft Support case. But first, here are two important facts:
- Microsoft does not have beacons on your machine that report back to MS Support when you’re infected by malware. Yes, your system checks in with Microsoft servers, but it does so primarily for updates or activation, or when Windows Genuine checks that you have a valid key code.
- If Microsoft does have your phone number — provided by you for purchases or previous support, or when signing up for a Microsoft (e.g., Hotmail) account — the company doesn’t associate the number with your PC. Again: Any contact a PC has with MS servers is not linked to the owner’s phone number.
As someone who buys Microsoft software licenses, I get calls from Microsoft’s marketing department about new Windows Server 2012 offers or the latest on Office 365, and about other products of interest to business. But I’ve never had anyone from Microsoft call me and claim that my computer has been flagged with a virus. It just never happens! Microsoft phone support always starts with a call from a user.
There are two types of support Microsoft offers to customers: consumer-level support for individuals and IT Professional, a business category. This article focuses on consumer support; a future story will discuss options for small- and medium-size businesses.
Recently, Microsoft began pushing its product support away from phone calls and toward fixits, automated tools, forums, and chats. Not long ago, the bottom of every Microsoft security-support bulletin displayed a phone number — 1-866-pcsafety — and the recommendation that users call the number for Windows/Microsoft Update help. Now, security bulletins give a list of support resources — including a link to a Windows Update fixit that resets the Windows Update components.
(The fixit is actually a good starting point if you run into Windows Update errors. Start by running the fixit as is. If that doesn’t work, try the more aggressive mode that clears out the software distribution folder, resets the Windows Update history, and reregisters all Windows Update files.)
Different paths to different support offerings
Finding help online for Microsoft product updates can be unpredictable, to put it kindly. Depending on the update or product, using the Support information links in Windows Update takes you to different support sites. For example, when I clicked the Support information link (bottom-right on the available-updates window) for a Silverlight update, I was sent to a simple Support Options page. The page briefly states there’s free uninstall-and-install support available for Silverlight; a following page provides a support phone number and hours of operation. (It doesn’t give the time zone.)
The point? If I have a problem with a Silverlight update, Microsoft won’t call me — I have to call Microsoft and initiate a support incident. But I can get a specific support phone number for the problem.
Selecting the Support information link for KB 2553501 — a security update for the Microsoft Filter Pack 2.0 — directs you to a landing page that’s less helpful. In fact, it’s a generic support page with options such as: “Find it myself” (with linked icons for various MS products), “Ask the community” forums (again, with links to specific MS products), and “Get Live Help.”
The support link for Internet Explorer 10 takes you to an entirely different support page: a generic Top Solutions troubleshooting site with such topics as “Upgrading to Windows 8” and “Why my Hotmail account was upgraded to Outlook.com.” It also contains a Windows RT FAQ — but nothing on IE 10.
Getting live help from Microsoft Support
Because the focus of this story is walking you through a contact with Microsoft Support, I’ll start with the “Get live help” option (see Figure 1) on the home MS Support page and walk through the following steps:
- Under Contact Microsoft, click Microsoft Customer Service.
- On the Contact page, click Microsoft Support — help for products and services to expand its list of options.
- At the top of the list is Microsoft Technical Support — Submit a technical support request.
That’s the real starting point for contacting MS Support.
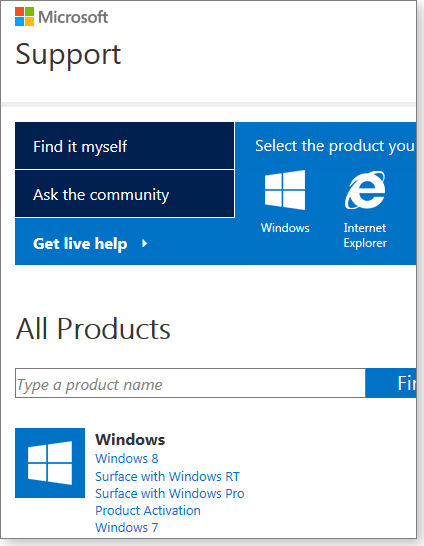
Figure 1. Microsoft Support offers three ways to get help. Get live help could take you to the MS Answer Desk, a free/paid online chat service.
The next page displays a list of supported products. The product you choose will send you to a specific MS Support division. For this walk-through, let’s say we’d like to know why KB 2807986 is shown in Windows Update but isn’t checked for installation. (For the record, this is a bit of a trick question. To my knowledge, Microsoft has not posted an official reason why KB 2807986 is currently unchecked on many computers, though the question has been asked in the MS forums. My theory? Microsoft is watching for issues with kernel updates.)
To find an answer, we start by clicking the Windows 7 link. We’re then presented with a list of Win7 versions. The product we pick determines the type of support we’ll receive. If we choose a business version of Windows 7 (Win7 Pro, Enterprise, or Ultimate), we’ll end up with the IT Professional division, which typically handles problems unique to networking domains. If we choose Windows 7 Pro, we’ll be asked whether the OS is in a home or business. Choosing I use it for my own personal use moves you to the consumer-support offerings.
We’ll choose Windows 7 Home Premium to move on to the next screen.
The next page — Product and Problem (Figure 2) — has a drop-down list of support topics, ranging from Virus issues to Internet Explorer. We’ll choose Windows Update issues and click Continue.
Figure 2. Windows Update Issues is one of the options in the Support topic list.
We now arrive at the MS Support Answer Desk page, shown in Figure 3, a relatively new chat desk with Microsoft-trained and outsourced technical support personnel. The service is not necessarily free. Also, be aware that the Microsoft Answer Desk techs are not employees of Microsoft. As stated in the service’s Service Agreement, “Always use caution when giving out any personally identifiable information about yourself or your family members when interacting with Answer Techs.”
Figure 3. Microsoft's Answer Desk sign-in page.
The Microsoft Answer Desk experience
To start a chat, we need to have or create a Microsoft account — or sign up as a guest. We’ll continue on as a guest. The sign-in process requires that we give a phone number and email address. As you’ll recall, I’ve said that Microsoft doesn’t connect your phone number with your computer. But the Answer Desk service could. (You could, in theory, enter a bogus phone number and email address at this stage of the support process.)
After we accept the terms of agreement, an Answer Desk tech begins the chat session. If you prefer that the tech call you, there’s a button for that option in the chat window. (The tech will call you only if you click the link.)
If your problem is relatively simple, your Answer Desk session might be free. As detailed in a 2011 PCWorld article, more complicated answers will bump you over to paid support — typically U.S. $99 per hour (not per incident).
Problems with OEM PCs (where support is normally provided by the vendor) are more likely to push you into the paid service. To determine warranty status, the Answer Desk technician might ask for an MS Product ID number to verify whether you’re obtaining support for an OEM computer or a retail Windows purchase.
My copy of Windows is past the 90-day, retail product–support window. So I’d have to pay the $99 fee. (They would most likely use a remote-control app to examine my machine and fix the problem.) If I had an OEM version of Windows, I could also contact the hardware vendor using an MS Support Computer Manufacturers’ Contact Information page.
If we had an MS Signature PC — a system purchased from the Microsoft Store (site) — we’d also have a 90-day, phone-support subscription. (Signature PCs are specifically built for Microsoft and typically have the usual OEM crapware removed.) You can use the 1-800-Microsoft number to access phone support. But the aforementioned vendor contact page also gives a phone number for the Microsoft Store Online.
The Answer Desk tech I chatted with could not answer my question. (I didn’t expect him to.) But to his credit, he didn’t push me to pay for additional support. Instead, he asked me for my email address, indicating that he had access only to my name. (Recall that I gave an email address during sign-in.) He then sent me a recap of the courtesy support chat with a download link for the update.
If I’d had a problem that required access to my system via remote control, the Answer Desk interface would have asked for a credit-card number and that $99 payment. (Checks, obviously, aren’t accepted — just credit and debit cards.
For any online support, I recommend using a temporary credit card to eliminate or reduce possible losses from fraudulent online transactions.
Taking our question to MS Support forums
Back at the MS Support home page: If I choose “Ask the community,” click the Windows icon, and then select Windows 7, I’m taken to the Ask Windows 7 Community page. Pressing the Go button then sends me to Windows forums. In the Windows Topic and Apps drop-down box, I pick Windows Update and Show All in the Windows Version box. That takes us to topics related to Windows Update.
Like most forums, the Microsoft Community has knowledgeable people who might answer your question. But most of them are not Microsoft employees. As noted on the Who’s who in the forums section of the MS Community FAQ, most of the people answering questions are volunteers. (The same is true for the Windows Secrets Lounge, by the way.) That said, it appears that MS support engineers will unofficially provide answers or ask for more information to get to the root of an issue.
I believe Microsoft’s forum support is best for easily fixed problems, where both the issue and its resolution are already known. Forums are not as useful for early reports or solutions to a problem security update. (It’s one of the reasons for holding back on some security updates. You want to allow time for reports of update problems to surface and be checked.)
The Microsoft Community lacks a feature that’s basic to most forums: the ability to easily upload images of problems displayed on your computer screen. There’s a convoluted process, documented on a forum thread.
A hidden way into MS Support for security issues
You can get additional help for security questions, but it’s not well documented and not posted on any official MS page that I’ve seen. If you call 1-800-Microsoft and state clearly that you have a problem with a security update (giving the specific update number), you might get a support-call router who will open a support case without requiring a credit card. (You might also have to give a credit-card number, knowing that as long as the issue concerns a security update, you won’t be charged.)
As noted, unlike those tech-support scammers, Microsoft will never call you proactively about a security problem. But there’s some irony in the fact that it’s nearly impossible to find an MS support number for security issues.
Consumer support: A bit of an eye-opener
After using Microsoft’s IT Professional support for years, I encountered some surprises while doing the research for this article on consumer support. It’s no wonder that many Windows users head over to Google and search for information on problems such as a mysterious error code — hoping to find a forum or a site that has an understandable solution. Even Googling Microsoft support isn’t of much help: the search results displayed two bogus Microsoft Support offerings (see Figure 4) in the ads located at the top of the page. Microsoft’s Bing was no better.
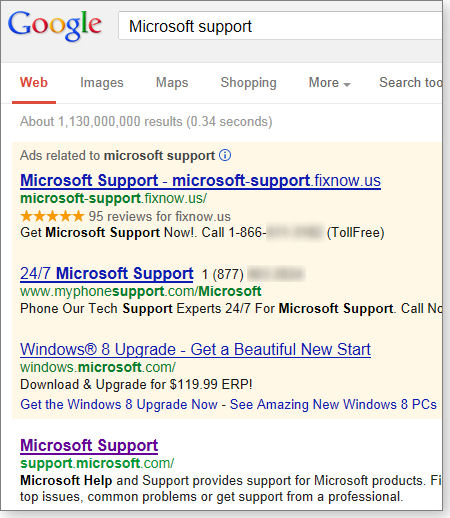
Figure 4. Searching Microsoft support on Google returned two bogus sites.
Bottom line: Once you’re past your 90 days of free Microsoft support, your best option for free consumer-product support is MS Community and other forums, where you must depend on the kindness of strangers. You’ll find me there from time to time, watching for patching issues and helping out where I can. But remember: The forums are small help for those really nasty patching and security issues that crop up all too often.
There’s another valuable resource I recommend: The Windows Secrets Lounge has helpful, technically savvy folks — and it’s easy to attach images to your posts.
Small businesses and IT Professional subscribers generally get a much better support experience. But they pay for it. I’ll be discussing how their experience is vastly different in an upcoming Windows Secrets article.
Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com).
Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners.
Your email subscription:
- Subscription help: customersupport@askwoody.com
Copyright © 2025 AskWoody LLC, All rights reserved.

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
AMD : Out of Bounds (OOB) read vulnerability in TPM 2.0 CVE-2025-2884
by
Alex5723
3 hours, 31 minutes ago -
Totally remove or disable BitLocker
by
CWBillow
2 hours, 25 minutes ago -
Windows 10 gets 6 years of ESU?
by
n0ads
14 minutes ago -
Apple, Google stores still offer China-based VPNs, report says
by
Nibbled To Death By Ducks
14 hours, 18 minutes ago -
Search Forums only bring up my posts?
by
Deo
14 hours, 31 minutes ago -
Windows Spotlight broken on Enterprise and Pro for Workstations?
by
steeviebops
1 day, 2 hours ago -
Denmark wants to dump Microsoft for Linux + LibreOffice
by
Alex5723
18 hours, 37 minutes ago -
How to get Microsoft Defender to honor Group Policy Setting
by
Ralph
1 day, 2 hours ago -
Apple : Paragon’s iOS Mercenary Spyware Finds Journalists Target
by
Alex5723
1 day, 12 hours ago -
Music : The Rose Room – It’s Been A Long, Long Time album
by
Alex5723
1 day, 13 hours ago -
Disengage Bitlocker
by
CWBillow
1 day, 3 hours ago -
Mac Mini M2 Service Program for No Power Issue
by
Alex5723
1 day, 15 hours ago -
New Win 11 Pro Geekom Setup questions
by
Deo
14 hours, 27 minutes ago -
Windows 11 Insider Preview build 26200.5651 released to DEV
by
joep517
1 day, 23 hours ago -
Windows 11 Insider Preview build 26120.4441 (24H2) released to BETA
by
joep517
1 day, 23 hours ago -
iOS 26,, MacOS 26 : Create your own AI chatbot
by
Alex5723
2 days, 3 hours ago -
New PC transfer program recommendations?
by
DaveBoston
7 hours, 58 minutes ago -
Windows 11 Insider Preview Build 22631.5545 (23H2) released to Release Preview
by
joep517
2 days, 7 hours ago -
Windows 10 Build 19045.6029 (22H2) to Release Preview Channel
by
joep517
2 days, 7 hours ago -
Best tools for upgrading a Windows 10 to an 11
by
Susan Bradley
1 day, 19 hours ago -
The end of Windows 10 is approaching, consider Linux and LibreOffice
by
Alex5723
23 hours, 30 minutes ago -
Extended Windows Built-in Disk Cleanup Utility
by
bbearren
1 day, 8 hours ago -
Win 11 24H2 June 2025 Update breaks WIFI
by
dportenlanger
3 days, 2 hours ago -
Update from WinPro 10 v. 1511 on T460p?
by
CatoRenasci
2 days ago -
System Restore and Updates Paused
by
veteran
3 days, 4 hours ago -
Windows 10/11 clock app
by
Kathy Stevens
2 days, 15 hours ago -
Turn off right-click draw
by
Charles Billow
3 days, 7 hours ago -
Introducing ChromeOS M137 to The Stable Channel
by
Alex5723
3 days, 11 hours ago -
Brian Wilson (The Beach Boys) R.I.P
by
Alex5723
18 hours, 3 minutes ago -
Master patch listing for June 10, 2025
by
Susan Bradley
3 days, 13 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.

