
|
Patch reliability is unclear. Unless you have an immediate, pressing need to install a specific patch, don't do it. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
Mastering Windows 8’s backup/restore system
In this issue
- TOP STORY: Mastering Windows 8's backup/restore system
- LANGALIST PLUS: Emergency access to your PC's UEFI settings
- PATCH WATCH: Easing into a new year of Windows updating
- LOUNGE LIFE: Fine print: Bigger is not always easier to read
- WACKY WEB WEEK: Cat graciously accepts ride from French bulldog
- DIGITAL ENTERTAINMENT: A geek survives her first CES experience
Mastering Windows 8's backup/restore system
Windows 8 has easily the most comprehensive backup-and-recovery system ever seen on a personal computer.
With little user effort, and when applied correctly, Win8’s built-in backup tools provide automatic, frequent, triple-data redundancy.
Inexplicably, however, Microsoft tends to describe each tool more or less in isolation. It doesn’t provide a simple, comprehensive explanation of how the backup components work together — and do so extremely well.
This article rectifies that deficiency; it describes how to use File History, OneDrive, and other options as a complete system for near-bulletproof backups.
You’ll also find numerous links to articles that provide detailed how-to information — and operational tips on backing up Windows 8 systems.
An overview: Win8’s three-part backup system
Here are the main components:
- File History — Local backups of user data: Win8’s File History tool makes continuous, near-real-time, incremental backups of selected user files. It then stores these backups on a networked or USB-attached external drive. If the primary copy (the working file) is damaged or accidentally erased, it can be quickly and easily restored from the local File History backups.
- OneDrive — Remote user-data backup: Local backups are critical, but they have a potentially fatal flaw: any event that damages your PC or the drive containing your working files might also eliminate your local backups. Fires, floods, thefts, electrical surges, and similar catastrophes might result in the loss of all local copies. The answer for that possibility is cloud storage/backup, which maintains copies of your files on fully protected data servers, far removed from your PC.
Microsoft’s cloud-based storage service started out as the relatively simple SkyDrive. But over the past few years, Microsoft has steadily improved the service’s capabilities, including tightly integrating it with Office 2013 and building it into Windows 8. (In fact, one of the early complaints about Office 2013 was its preference for storing files in SkyDrive.) Because of a trademark dispute, the service was renamed OneDrive in early 2014.
There are, of course, many other cloud storage and backup services that will let you restore lost files. (A Nov. 20, 2014, Best Practices [paid content] discusses the differences between cloud-based synching and backup.) But — as is hardly discussed at all by Microsoft — OneDrive and File History can work cooperatively to provide automatic, double backups of all your important files.
With almost no effort on your part, files can be automatically saved to three separate locations — the primary data drive, the external File History drive, and the OneDrive cloud — in near-real time. It virtually guarantees that you’ll never lose an important file again!
Why “important” files? By default, OneDrive users get 15GB of free online storage. Yes, you can put copies of all your data on OneDrive — but only if it amounts to fewer than 15GB or you’re willing to pay for additional storage space. (Note: Office 365 subscribers get essentially unlimited storage [more info].)
- OS backups and system imaging: Windows 8 includes separate tools to back up and restore the operating system. Refresh lets you perform a nondestructive reinstall of the operating system while leaving most of your user files alone. However, not all user-installed, desktop applications will survive the process; you must use the custom imaging option to preserve your specific software setup. Reset does a full, clean-slate, factory restore.
With that foundation, we’re ready to take a closer look.
How File History creates reliable local backups
As mentioned above, Win8’s File History (Figure 1) is a highly automated, set-and-forget, near-real-time, archiving system. It does, however, require a drive other than the primary Windows (typically C:) drive. The backup drive can be a second internal disk, an external USB storage device, or a networked drive.

Figure 1. It's easy to access, configure, and fine-tune Win8's File History.
By default, File History automatically backs up everything in your Windows libraries — typically Documents, Music, Pictures, and Videos. But it can also back up other files and folders if you simply add them to a Windows Library. Likewise, you can exclude files and folders from File History by removing them from a library.
File History also automatically backs up four standard Windows user folders: Desktop, Favorites, Contacts, and anything stored in your local OneDrive folder (which I’ll come back to in the next section).
To get up to speed quickly on File History’s configuration, customization, and use, see the following:
- “Understanding Windows 8’s File History” – July 11, 2013, Top Story
- “Windows 8: File History explained” – TechNet article
- “Set up a drive for File History” – MS how-to
- “Customize File History’s backups with ease” – Oct. 9, 2014, LangaList Plus (paid content).
Keep in mind that File History makes incremental backups every hour, by default. But you can have it run as often as every 10 minutes. As a result, File History can consume a lot of disk space. The advanced settings (Figure 2) let you control how often File History runs and how long it should save backup files. For more on this, see the July 11, 2013, Top Story listed above and the Nov. 6, 2014, LangaList Plus column, “How to shrink huge File History backups.”
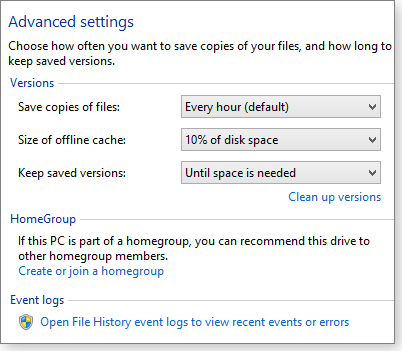
Figure 2. File History's advanced settings let you configure the frequency of backups, how much disk space they consume, and how long they're kept.
(A related article discusses how to work around a rare but annoying bug that can cause File History to back up every file, every time. See the Aug. 15, 2013, LangaList Plus column, “Solving File History’s ‘excessive saves’ bug” [paid content].)
File History can also have connection issues with multiple external drives. If you routinely connect and disconnect various external drives, check out the March 6, 2014, LangaList Plus item, “How to make File History retain drive IDs.” Your hard drive’s sleep and suspend cycles can also interfere with File History’s ability to make backups. See the Nov. 28, 2013, LangaList Plus, “A warning regarding Win8’s File History.”
With File History properly configured, Win8 will make reliable and automatic local backups of whatever files you’ve set it to maintain.
How OneDrive adds another layer of data security
All Windows 8 users should be familiar with Microsoft’s OneDrive online service. Again, it’s built into the operating system and automatically gives Win8 users 15GB of free, cloud-based storage. (Additional storage is surprisingly inexpensive; see MS info.)
But OneDrive does more than store copies of your data files. By default, Win8 automatically backs up seven types of personalization/customization settings to your associated OneDrive account: Start screen layout, color scheme, theme and background, language preference, browser history, browser favorites, and the settings for any apps you obtained from the Windows Store. (For more on this, see the Dec. 11, 2014, LangaList column, “Controlling Win8’s auto-synching of settings.”)
Anything you or your software saves or adds to OneDrive is automatically stored in the cloud on Microsoft servers. But OneDrive does much more — though Microsoft does a terrible job of explaining those capabilities.
For example, the local OneDrive folder on your C: drive normally stores only snippets and partial copies of any files you’re working on; the full copies reside in the cloud. But OneDrive also offers a Make available offline option. Any files or folders to which you apply the option are fully available for offline access; OneDrive automatically stores a second complete copy of the file or folder on your hard drive.
That’s the key to Win8’s outstanding data redundancy. If you store your important files and folders in OneDrive and then use the Make available offline option, OneDrive makes two complete copies. When combined with File History, you end up with:
- A live copy in the OneDrive folder on your hard drive
- A backup copy stored in the cloud on the OneDrive servers
- A local backup saved by File History on a second (typically external) drive.
That’s about as bulletproof and automatic as a backup system gets!
Moreover, because File History makes frequent, incremental backups, the Make available offline option provides a form of versioning for your OneDrive-based files. Your local OneDrive folder and the OneDrive servers will always contain the most recent copy of any included file, and File History will contain as many previous iterations of the file as you’ve configured it to capture.
The Make available offline option is easy to implement: in File Manager, open your OneDrive folder and right-click any included file or folder. Then select Make available offline, as shown in Figure 3. It’s that simple.

Figure 3. Selecting Make available offline gives any OneDrive file or folder three-way redundancy: hard drive, cloud, and File History.
For me, the “Make available offline” — combined with OneDrive in the cloud and local File History — is the best feature of the Win8 backup system. It should be enough to protect your data against almost any imaginable form of loss.
OneDrive is generally easy to access and use; but if you’d like more information, see these Microsoft sources:
Note: There’s a potential OneDrive issue that Microsoft does not cover well. The service is linked to your Microsoft account, which you also use when signing in to Win8 systems. But Win8 also allows for other types of sign-ins — seven in all — and not all of them allow for automatic access to OneDrive.
If you have trouble accessing your OneDrive account — or for tips on how to prevent access trouble in the first place — see the Jan. 8 LangaList Plus column, “Taming Win8’s seven-way sign-in hassles.”
Security Note: It’s always wise to encrypt your most sensitive folders or files to prevent snoops from being able to access them — especially if the data will be transmitted over the Internet or stored in a cloud-based server. I use 7-Zip (free; site) to apply 256-AES encryption to sensitive files and folders stored in my local OneDrive folder. The encrypted files are then automatically replicated to the cloud and to my File History backups.
A refresher on Win8 OS and software restorations
File History and OneDrive deal mostly with user files and data. But as mentioned above, Win8 provides separate mechanisms for backing up and restoring operating-system files and installed software.
Refresh: Windows 8’s ‘Refresh your PC without affecting your files’ feature returns system files to their original condition while leaving the users’ accounts, data, passwords, and personal files largely untouched. But there are limitations. For example, Refresh removes any non-native Windows 8 (typically, desktop) apps that you’ve installed. For full information, see the Aug. 15, 2013, Top Story, “A ‘no-reformat reinstall’ for Windows 8.”
Reset: If a refresh doesn’t work. Win8’s ‘Remove everything and reinstall’ option wipes out your existing setup and rolls Windows back to its initial, out-of-the-box state. For details on this process, see the Sept. 12, 2013, Top Story, “A clean-slate reinstall for Windows 8.”
Microsoft doesn’t stress this, but I will: Reset is designed to work with File History. After a system reset, File History can automatically repopulate your Documents, Music, Pictures, Videos, Desktop, Favorites, Contacts, and any other folders or files you’ve added to File History — such as OneDrive items you’ve made available offline. Depending on how your system is set up, the post-Reset file-restoration process might be fully automatic, or it might require a few clicks to get started. (See the Win8 how-to, “Restore files or folders using File History.”) Either way, it’s an almost effortless way to get back all your user files and data after an operating system reset.
Customized system recovery images: Win8’s built-in Recimg.exe tool (Recimg, for short) is a command-line option that creates custom system images (see Figure 4). When needed, custom images can return Win8 to a user’s specific configuration — including all applications installed when the custom image was made (not just native Win8 apps). For detailed instructions, see the Oct. 10, 2013, Top Story, “Creating customized recovery images for Win8.”

Figure 4. A typical Recimg progress screen
Once Windows is fully restored from a custom system image, use File History to restore the latest copies of your files.
Note: If you use encryption products such as TrueCrypt, VeraCrypt, or Boxcryptor that create “containers” with assigned drive letters, you can’t make custom system images. If you try it, Recimg will simply fail with a generic error message. For more information and a workaround, see the Dec. 11, 2014, LangaList Plus, “Why VeraCrypt won’t work with Windows 8.”
Make sure you can access your backups
Obviously, backups are worthless if you can’t get to them. You should be able to access your backups regardless of the circumstances — even if Windows won’t run or your PC won’t boot from its hard drive. Be sure you have a working bootable emergency-repair disk or drive. These articles can help:
- “Emergency repair disks for Windows: Part 1” – April 10, 2014, Top Story.
- “Emergency repair disks for Windows: Part 2” – April 17, 2014, Top Story
If you have trouble booting your system from the emergency disc, see:
- “How to solve UEFI boot and startup problems” – Dec. 11, 2014, Top Story
- “Emergency access to your PC’s UEFI [boot] settings”– in this issue’s LangaList Plus section (paid content).
Third-party backup/restore alternatives
Nothing’s perfect. Although Win8’s backup/restore system works well in most circumstances, it might not be a good fit for your particular configuration. Or you might simply not want to trust your data to the cloud.
If that’s the case, there are numerous third-party backup tools that can produce traditional backups and images of your Win8 system. Some of the more popular products include:
- Macrium Reflect – free and paid (with free trial) versions
- Paragon Backup & Recovery – 30-day demo and paid versions
- Acronis True Image – paid with 30-day free trial (site)
- EaseUS Todo Backup – free and paid versions.
For some Windows 8 setups, an automated cloud-based backup service might be more suitable. See Lincoln Spector’s Nov. 20, 2014, Best Practices story, “Cloud data protection: Synching versus backup” [paid content]. You can find more alternatives by doing a Web search for “windows 8.1 local backup.”
Win8 backups: Significantly different but arguably better. Microsoft did a poor job of documenting backup and recovery in Win8, and getting used to the process does take some effort. But it’s well worth taking some time to understand and implement Win8’s built-in backup-and-restore tools.
Once configured, Win8’s backup system offers automated, redundant, near-real-time data security that most traditional backups simply can’t match.
Try the Windows 8 way — you’ll probably never go back!
Emergency access to your PC's UEFI settings
If Windows won’t boot, you still can access its UEFI/BIOS settings to start repairs — if you know the trick.
Plus: Overcoming Windows-homegroup networking hassles and the pros and cons of using third-party printer cartridges.
UEFI access when Windows isn’t available
Reader Bob H. was one of several readers who had questions after reading the Dec. 11, 2014, Top Story, “How to solve UEFI boot and startup problems.”
- “Your article on the UEFI contained all the information needed, if — and only if — the computer will successfully boot Windows. Your methods won’t work when Secure Boot is on and only UEFI boot is enabled.
“Here’s a trick that brings up the ‘Choose an option’ menu, letting you then boot the UEFI setup.
“When the boot-up process starts and you see the progress icon, hold down the power button until the PC shuts down completely (or simply unplug the system’s power cord).
“Doing this two to three times in relatively fast succession should bring up the needed troubleshooting menus on a subsequent startup.”
Your way might work, Bob, but it sounds a little tough on the hardware — and it requires multiple attempts before it succeeds.
As mentioned toward the end of the “How to solve UEFI boot and startup problems” article, almost all PCs offer a built-in, hardware-based method for accessing the UEFI settings, even if Windows won’t boot normally.
For example, to directly access the UEFI on one of my PCs, I simply power-on the system with the F2 key already pressed. This brings up the UEFI settings every time, without stressing the hardware.
You can find your PC’s UEFI-access method by searching the vendor’s help/support pages for your specific brand and model and adding search terms such as “uefi,” “bios,” “access,” or “boot.”
You can also run a general Web search using, for example, {your PC brand} {your PC model} uefi bios access boot.
Security warning: Accessing the BIOS or UEFI is a kind of back door into your PC and its contents. With the proper key combination, anyone with direct access to the machine might alter its BIOS/UEFI settings and potentially gain full access to your local files.
It’s relatively easy to do. A snoop might simply alter the system’s boot order and load Linux from a flash drive. He could then access your C: drive — and possibly all other attached hard drives.
To block this type of unauthorized access, establish an administrator/supervisor password for the BIOS or UEFI, as shown in Figure 1.

Figure 1. Setting a password will protect your PC's BIOS/UEFI from unwanted configuration changes such as boot order.
For more information on BIOS/UEFI passwords, head over to the Feb. 28, 2013, LangaList Plus article and look for the subsection titled “Protecting against local/physical threats”; then scroll down to the heading “Hardware-level passwords.”
Solving homegroup issues on networked Win7/8 PCs
Michael Borgstrom experienced an all-too-common frustration.
- “Hi guys! I have one desktop running 32-bit Win8.1, a laptop running 64-bit Win7, and a desktop running 64-bit Win7.
My problem: The Win8.1 PC cannot ‘see’ the Win7 homegroup.
“Win8.1 invites me to create a homegroup but then puts up a message that a homegroup can’t be created on the computer.
“If I try to join the homegroup running on the Win7 machines, I receive a similar message.
“Any ideas?”
Sure, Michael!
Homegroups are a mixed blessing. When they work, they offer an exceptionally simple way to network Windows PCs.
On the other hand, when they don’t work, troubleshooting can be difficult because many homegroup settings are hidden from easy access — and correction.
Also, if you get a homegroup working, it can be noticeably slower than conventional Windows networking — up to 12 percent slower, in my tests (more on this in a moment).
As a first step to resolving homegroup hassles, try running Microsoft’s automated fixit, available on a Microsoft webpage. Manual repair options are also described on that page.
If that doesn’t solve your problem, the most reliable repair method I know is to wipe out the existing networking setup and let the network rebuild itself from scratch. It’s not hard and takes only a few minutes.
Follow the steps in the May 12, 2011, LangaList Plus item, “The ‘Make all future networks public’ debacle.” (Yes, that’s a different networking problem, but the process of restoring a clean-slate networking setup is the same.)
Work on your Win8 PC first and then repeat the steps on your other PCs.
Along the way, ignore any offers to establish a homegroup.
At the end of the rebuild process, Windows should automatically establish standard, classic, non-homegroup networking.
You can then retry homegroups — or just leave the standard Windows network as is.
In my experience, standard Windows networking can be better at connecting dissimilar Windows versions — and it’s typically faster. For complete information, see the Oct. 14, 2010, Top Story, “Simple change in settings pumps up Win7 networks.” Although I haven’t repeated the formal timing tests for Win8, the speed difference feels about the same to me.
Either way — with a homegroup or with standard networking — a from-scratch rebuild of your networking setup should iron out your connection problems.
Wondering about remanufactured ink cartridges
Long-time reader Elaine M. is pondering ways to reduce the high cost of original-equipment printer consumables. Her question is specifically about toner cartridges, but the answer also applies to inkjets.
- “I keep hearing that printer manufacturers and repair people claim that most printer problems are caused by not using OEM toner cartridges.
OEM cartridges are typically very pricey. Significantly less expensive are remanufactured cartridges, which fall somewhere between OEM and generic ‘compatible’ cartridges.
“I’d like to know whether remanufactured cartridges are different from compatible cartridges (as I think they are). If so, are remanufactured cartridges safe to use? Or must we accept that purchasing toner cartridges means taking out a second mortgage on the house?”
You’re right; OEM supplies for printers seem obscenely expensive. Unfortunately, it’s hard to find accurate information on alternatives.
Some OEM cartridge sellers insist that using a remanufactured cartridge will reduce your printer to slag. On the other hand, sellers of remanufactured or “compatible” cartridges claim that there’s no difference between OEM and refilled or third-party products.
As is so often the case, the truth lies somewhere in between these extremes.
High-quality, non-OEM supplies can give excellent service. But not all third-party supplies are of high quality.
Some laser cartridge vendors — often those with the lowest prices — merely refill a used cartridge with fresh toner powder, slap on a new label, and then ship it. With laser cartridges, this approach usually works for a refill or two — if the vendor is using high-quality toner.
After too many refills, a cartridge can fail. Seals, springs, sliding shutter mechanisms, wiper blades, and other parts simply wear out (see the Clover Technologies article, “Inside a toner cartridge”).
Obviously, an overused cartridge might not perform to factory specs; it can even damage the printer itself.
Better third-party toner manufacturers disassemble the cartridge and inspect all components, reusing only those that are still within factory tolerances. These remanufactured cartridges can perform as well as originals.
Here’s your best bet: Write down the brand names of available remanufactured cartridges. Visit each brand’s site and look for a description of the remanufacturing process. Pay attention to the words they use — for example, refilling versus remanufacturing. The better vendors are quite transparent about the techniques they use.
As an example (no endorsement implied), Laser Connection sells both OEM and remanufactured cartridges, so it appears to have no particular axe to grind. Its site does a fairly good job of explaining the differences among available toner cartridge types: OEM, remanufactured, refilled, recycled, compatible, and others.
Knowing the differences among types lets you make a more informed choice. (Keep in mind that Laser Connection’s descriptions might not apply to other vendors.)
Inkjet cartridges are an entirely different matter. With most inexpensive inkjet printers, the tiny nozzles that spray ink are on the cartridge. Refilling becomes far more problematic. For a fuller discussion on the merits of OEM vs. non-OEM inkjet cartridges, see the Dec. 19, 2013, LangaList Plus item, “Is cut-rate printer ink worthwhile?”
Easing into a new year of Windows updating
We’re not sure whether it’s good news or bad, but January’s Patch Tuesday has few Windows updates and no Office patches.
Our only official critical security update is for servers; for the first time in months, there’s no update for IE.
3024663
A patch for Adobe Flash/IE vulnerabilities
Not among January’s official list of Patch Tuesday releases is KB 3024663, which first showed up as KB 2755801 this past September and was sent out as an IE 10 and IE 11 update for Win8 and Server 2012 systems. The patch includes vulnerability fixes for Adobe Flash Player, now built into IE Versions 10 and 11.
 What to do: There’s no official rating associated with this update. But given past weaknesses in Flash, Windows 8 users should install KB 3024663 as soon as possible.
What to do: There’s no official rating associated with this update. But given past weaknesses in Flash, Windows 8 users should install KB 3024663 as soon as possible.
MS15-002 (3020393)
Telnet pokes security holes in servers
Wikipedia defines Telnet as a network protocol used to “provide a bidirectional, interactive text–oriented communication facility, using a virtual-terminal connection.” Which is to say, it’s an early form of text messaging and remote access.
Telnet isn’t used much anymore; server administrators might enable it to test email communications between servers or between clients and servers. But more often, admins now use Microsoft’s Remote Connectivity Analyzer (site) to troubleshoot communication problems with MS Exchange (Microsoft’s email server) or Office 365.
It’s no surprise that an old protocol would have security flaws. KB 3020393 patches a privately reported vulnerability in Windows that could lead to remote-control attacks. The attacker would send malicious packets to a server that has Telnet enabled.
The update is rated critical for all currently supported versions of Windows, both workstations and servers. KB 3020393 is the only update listed as critical among January’s Patch Tuesday releases, but its rating would seem to overstate the threat. By default, Telnet isn’t even installed in Windows, starting with Vista. It was included with Windows Server 2003 but not enabled by default. Given that only hardcore, grizzled server admins are likely to use Telnet, you’d probably be hard-pressed to find a server — much less a workstation — that’s vulnerable to a Telnet exploit.
 What to do: Admins should consider installing KB 3020393 (MS15-002) if there’s a chance that Telnet might be enabled on their servers. In the unlikely chance that the patch shows up on a workstation, it can be safely ignored.
What to do: Admins should consider installing KB 3020393 (MS15-002) if there’s a chance that Telnet might be enabled on their servers. In the unlikely chance that the patch shows up on a workstation, it can be safely ignored.

Figure 1. The refreshingly short January Windows Update list on a typical Win8.1 system
MS15-001 (3023266)
Google and Microsoft duke it out over patch
KB 3023266 is the fallout from a vulnerability-patching fight between Google and Microsoft. Google found a flaw in Windows and privately reported it to Microsoft. Google also gave Microsoft essentially an ultimatum: Microsoft had 90 days to come up with a patch, after which Google would make the vulnerability public.
That 90-day window expired on Dec. 29, 2014, and Google, true to its word, posted detailed information about the flaw. That prompted Senior Director Chris Betz to post a long rejoinder on the Microsoft Security Response Center site.
The actual threat is relatively mild. Rated important, KB 3023266 patches a flaw in Windows that might give an attacker additional rights to a system. But to do so, the attacker has to sign in to Windows and run a malicious application. (The flaw lets an attacker avoid security checks in Windows’ Application Compatibility component.)
Vista users are off the hook; the update applies to Win7 and Win8, plus Windows Server 2008 R2 and newer.
 What to do: Install KB 3023266 (MS15-001) when offered.
What to do: Install KB 3023266 (MS15-001) when offered.
MS15-003 (3021674)
User profiles lead to attacks
KB 3021674 is another update with its roots in Google. Google found a bug in the Windows User Profile Service and reported it to Microsoft — again with a 90-day deadline attached. On Jan. 11, details of the vulnerability were released to the public on the Google Security Research site.
Here, too, an attacker must sign in to a system and run a malicious application to gain additional user rights. For that reason, KB 3021674 is rated important, but it applies to all current versions of Windows.
 What to do: Install KB 3021674 (MS15-003) when offered.
What to do: Install KB 3021674 (MS15-003) when offered.
MS15-004
Remote desktop components lead to attacks
Malicious-application exploits seem to be a theme this month. The patches in MS15-004 fix a privately reported vulnerability that could result in an elevated-privileges attack. In this case, the attacker must convince a PC’s user to run malicious software. The updates are all rated important and apply to all current versions of Windows.
Windows 7 and Server 2008 R2 systems with Remote Desktop Client 8.0/8.1 installed might receive multiple updates for this vulnerability. They can be installed in any order. MS15-004 includes:
- Vista – KB 3023299
- Win7 – KBs 3019978, 3020387, and/or 3020388
- Windows 8/8.1 – KB 3019978
- Server 2008 R2 – KBs 3019978, 3020387, and/or 3020388
- Server 2012 and 2012 R2 – KB 3019978
 What to do: Install any MS15-004 updates offered.
What to do: Install any MS15-004 updates offered.
MS15-005 (3022777)
Starbucks Wi-Fi users might be at risk
If you routinely connect to public Wi-Fi networks and rarely think about whether they can be trusted, you’ll want to expedite the installation of KB 3022777.
When connecting to a wireless network and remote servers, your system will initiate a connection with a Domain Name System (DNS; more info) server and possibly an LDAP server (more info). Both systems are essentially public network directories. (Both allow a client computer to talk to servers.)
But a vulnerability in Windows’ Network Location Awareness Service could allow an attacker to send back spoofed DNS/LDAP responses. These malicious packets might then be used to drop your firewall’s defenses. For you fellow Trekkies, it would be like the Starship Enterprise hailing a star base. But a cloaked Romulan warship intercepts the communications and tricks the Enterprise into lowering its shields.
KB 3022777 is rated important and applies to all supported Windows systems except Server 2003. It’s extremely doubtful that anyone would connect Server 2003 to a wireless network, but per Microsoft, “It’s infeasible to build the fix for Windows Server 2003.”
 What to do: Install MS15-005, KB 3022777 when offered.
What to do: Install MS15-005, KB 3022777 when offered.
MS15-006 (3004365)
A flaw in Windows’ error-reporting component
KB 30004365 impacts only the various editions of Windows 8 and Server 2012. It patches a vulnerability in the Windows Error Reporting system that could let an attacker poke into a system’s working memory, bypass Windows security, and potentially access other systems.
Here again, the attacker must be able to sign in directly; he must also have admin rights. That was once a high bar, but it’s possible that this vulnerability could be combined with other exploits. The update is rated important.
 What to do: Install KB 3004365 (MS15-006) soon.
What to do: Install KB 3004365 (MS15-006) soon.
MS15-008 (3019215)
Updating the Windows kernel — with caution
KB 3019215 patches a potential malicious-application exploit of the Windows kernel-mode driver. This is yet another elevation-of-privileges threat.
The patch applies to all supported versions of Windows and is rated important. The attacker must sign in to a system locally.
I’m sticking with my kernel-patching policies from previous years. Delay installing this patch for a while so your third-party security software can catch up with the changes. KB 3019215 updates the mrxdav.sys file — which hasn’t, to my knowledge, been a problem in the past. But that’s not to say it can’t happen.
 What to do: Hold off on installing KB 3019215 (MS15-008) until I report back in the next Patch Watch.
What to do: Hold off on installing KB 3019215 (MS15-008) until I report back in the next Patch Watch.
MS15-007 (3014029)
A final January security patch for servers
KB 3014029 applies to all supported Windows Server versions, including Server 2003. Using malicious username strings, an attacker could exploit a flaw in the Windows Network Policy Server or Internet Authentication Service. The update is rated important.
 What to do: Deploy KB 3014029 (MS15-007) after testing.
What to do: Deploy KB 3014029 (MS15-007) after testing.
A few leftovers from December’s Patch Tuesday
We might finally be done with all our leftover food from the holidays, but a few December patching problems remain.
After installing IE cumulative update KB 3008923, some users reported problems with IE 9 crashes. Microsoft offered hotfix KB 3025945 on its MS Update Catalog, a site primarily used by administrators. (As with most hotfixes, you should only download and install this fix if you need it.) To find the fix, go to the Update Catalog and enter KB 3025945 into the search box; then manually download the file to your PC and install it.
If you’re running IE 10 on Windows 8 or Server 2012, you’ll see KB 3029449 (MS14-080) again, a security update for VBScript 5.8. In general, you can install any update that is reoffered.
Finally, the patches in MS14-082, an Office security fix, are still causing problems for some Excel users. The MS Excel Support Team Blog posted some workarounds. Bottom line: If you use complex macros in Excel, don’t install this update yet.
 What to do: Look for updates on problematic security patches in the next Patch Watch.
What to do: Look for updates on problematic security patches in the next Patch Watch.
The nonsecurity-update list is refreshingly thin
Surprisingly, the only nonsecurity updates (so far) in January are for .NET Framework. .NET 4.5.2 should be unchecked in Win7 Windows Update; it might or might not be checked in Win8.1. My philosophy on .NET updates: Install them when an application needs them. January’s .NET updates include:
Windows 7
- 2901983 – .NET 4.5.2
Windows 8.x
 What to do: Leave these .NET updates alone unless an application requests them.
What to do: Leave these .NET updates alone unless an application requests them.
Regularly updated problem-patch chart
This table provides the status of recent Windows and Microsoft application security updates. Patches listed below as safe to install will typically be removed from the table about a month after they appear. Status changes are highlighted in bold.
For Microsoft’s list of recently released patches, go to the MS Security TechCenter page.
| Patch | Released | Description | Status |
|---|---|---|---|
| 2977292 | 10-14 | EAP security advisory | Optional |
| 3003743 | 11-11 | RDP access logging; possible connection issues | Optional |
| 3020393 | 01-13 | Telnet service | Optional |
| 3019215 | 01-13 | Kernel-mode driver | Wait |
| 3009712 | 12-09 | MS Exchange Server; KBs 2996150, 3011140, and 2986475 (reissued) | Install |
| 3008923 | 12-09 | IE; also KB 3029449, fixit KB 3025945 for IE 9 crashes, fixit KB 3025390 for IE 11 issues | Install |
| 3013126 | 12-09 | MS Graphics Component | Install |
| 3016711 | 12-09 | VBScript; KBs 3012168, 3012172, and 3012176 | Install |
| 3017301 | 12-09 | MS Word and Office Web Apps; see MS14-081 for full list | Install |
| 3017347 | 12-09 | Excel; KBs 2910902, 2910929, 2920790, and 2984942 | Install |
| 3017349 | 12-09 | MS Office; see MS14-082 for full list (Excel users: Install with caution; see fixit KB 3025036) | Install |
| 3004365 | 01-13 | Windows Error Reporting system; Win8 and Server 2012 | Install |
| 3014029 | 01-13 | Network Policy Server, Internet Authentication Service | Install |
| 3021674 | 01-13 | Windows User Profile Service | Install |
| 3022777 | 01-13 | Network Location Awareness Service | Install |
| 3023266 | 01-13 | Windows Application Compatibility system | Install |
| 3024663 | 01-13 | Flash update for IE 10/11; Win8 and Server 2012 only | Install |
| 3025421 | 01-13 | Windows Components; see MS15-004 for full list | Install |
Status recommendations: Skip — patch not needed; Hold — do not install until its problems are resolved; Wait — hold off temporarily while the patch is tested; Optional — not critical, use if wanted; Install — OK to apply.
Fine print: Bigger is not always easier to read
Forum member billrice wants a new and bigger monitor.
To make a better-informed decision, he asked for help from Lounge members in the Hardware forum.
One of the happy side effects of a forum is that someone is apt to point out an issue you forgot to consider. The original poster appreciates the perspective; you might, too.
The following links are this week’s most interesting Lounge threads, including several new questions for which you might have answers:
 starred posts: particularly useful
starred posts: particularly useful
If you’re not already a Lounge member, use the quick registration form to sign up for free. The ability to post comments and take advantage of other Lounge features is available only to registered members.
If you’re already registered, you can jump right into today’s discussions in the Lounge.
Cat graciously accepts ride from French bulldog
 |
A cat of any appreciable experience can judge within seconds the threat level posed by a puppy. But a young dog often has to work hard to fathom its (low) standing in a canine-feline hierarchy. As is usually the case, the subtle cat in this video leaves almost all the labor, physical and mental, to the puppy. Click below or go to the original YouTube video. |
| Post your thoughts about this story in the WS Columns forum. |
A geek survives her first CES experience
The massive 2015 Las Vegas International CES was awash in new high-tech TVs, drones, iPhone cases, selfie sticks, digital wearables, 3D printing, and other digital gadgetry.
Tired feet aside, I had a successful first trip to the Consumer Electronics Show. Reportedly, it was the same for another show newbie, the Girl Scouts.
A show for those who sell tech to consumers
CES is primarily a showcase for what’s hot and what’s coming in consumer electronics. It’s not officially open to end users; it’s targeted at electronics retailers. Huge and easily overwhelming, CES is a place to see both the practical and the just plain wacky — plus everything in between.
Attending as a member of the press had its advantages. Before the show even opened, I started receiving press releases about new services and products. This was a helpful preview of what I would see on the show floor.
For example, I received a press release for a “smart pill box” that alerts caregivers when someone isn’t taking his or her medicine on schedule. Another press release touting Whoosh!, yet another screen-cleaning product, noted that most cell phones are disgustingly dirty.
I should say here that my reasons for attending CES weren’t completely frivolous. My true mission (or excuse, if you like) was to attend the show’s first-ever Personal Privacy and Cyber Security Marketplace exhibits (more info). I also wanted to see whether Microsoft and Windows had a significant presence at CES. Microsoft is still struggling to develop its consumer-electronic credentials; what better place than CES?
That said, I was eager to find interesting gadgets that will show up in retail in the year ahead. Many of the products shown aren’t even in production yet; they’ll arrive in stores sometime in 2015. Most surprising was the vast section of overseas manufacturers who are ready to build and mass-produce nearly anything and everything you might want to sell.
I’d call CES the Business of Consumer Electronic Show rather than just the Consumer Electronic Show.
A disappointing display of consumer security
Given the importance of computing safety, the Personal Privacy and Cyber Security sections of the show were underwhelming. There should have been many more security vendors.
Those I did see included Private Internet Access (site), an online VPN service; HYPR, a company offering biometric protection for credit cards and bitcoins; and iWallet), whose product is a digitally secured, armored wallet for your cards and cash.
As I walked around other sections of the show floor, I ran across more vendors with security solutions. One of these products was so impressive, I purchased one online from the comfort of my hotel room that evening. The myris (Figure 1) is a biometric device that replaces the need for passwords. It uses a video camera to scan your eye’s iris and confirm your identity. Any website that supports Fast IDentity Online (FIDO; more info) should accept the myris biometric token. (I plan to discuss various ways to avoid passwords in an upcoming article.)

Figure 1. I was so impressed with the myris eye-authentication security device that I purchased one.
Apps for finding the nearest Girl Scout cookie
Though consumer security was disappointing, I was delighted to see the Girl Scouts at CES. Real Girl Scouts were talking up their Digital Cookie program (more info) — and doing a better job of it than many of the official spokesmodels hawking products in other booths. Those of us addicted to Girl Scout cookies can now order them via websites and mobile apps.
It was great fun to see girls embracing technology. I promised to digitally order my annual batch of Thin Mints from my local chapter.
Has anyone seen Microsoft or Apple in the house?
The lack of any meaningful Microsoft presence was all too obvious at CES. Steve Ballmer gave the keynote speech in past shows, but there’s been no presentation by Microsoft in recent years that I can recall. Microsoft had a booth at Tech West in the Venetian, but it was hard to find products running Windows on the main CES floor.

Figure 2. Products running Windows were somewhat hard to find at CES.
Any official Apple representation was also noticeably absent from the show floor, but the company’s influence was far more obvious than was Microsoft’s. Just the number of manufacturers showing off iPhone and iPad cases was astounding. Interestingly, some of those cases included integrated batteries for keeping mobile Apple devices charged. I confess that, by the end of day two, I was eyeing purses that included a built-in power brick. Jill-e, for example, nicely combines styling with the problem of keeping your aging iPhone powered all day.
Here and there, I found a few products showcasing Microsoft technology — for example, Windows 8 tablets and small-form-factor PCs. The company’s new wearable, the Band, showed up in the Qualcomm booth. But most devices I saw in the robotics, wearables, and drones sections of the show are based on versions of Android.
A theme running through CES is the “Internet of Things” — or rather the “Internet of Everything.” It supposes that all kinds of devices — washers, dryers, refrigerators, cars, etc. — are connected to the Internet. Most of these connected products will run versions of Linux, not Windows.
As I wandered through row upon row of “Internet of Things” products, security came to mind. How are we going to maintain and patch all these Web-connected devices? Who’s going to ensure that everything connected to the Net gets the needed firmware updates? Will we be hacked through our microwave ovens? It’s something we’ll have to seriously ponder.
The rise of the digital wearables
Another theme of CES was digital devices that we wear. This goes well beyond Google Glass. Exercise monitors, for example, were a hot item. They ranged from simple clip-on sensors to monitors disguised as Swiss watches.
One issue with wearables is incompatibilities. For example, my Jawbone UP exercise band communicates with my Nest thermostat, letting it know when I’m in the house. Thus, when I leave the house, the Nest automatically lowers the inside temperature. But the two devices don’t always work perfectly together. The Jawbone kept setting the thermostat at too high a temperature. I had to disable the Jawbone/Nest integration and reset the thermostat to override the Jawbone. (Yes, I know this sounds awfully geeky, but it’s where we’re all headed.)
The upshot? Before you purchase a digital band or similar device to help you keep that New Year’s fitness resolution, go online and check the device’s “works with” section. See whether it’s compatible with other, related applications you might want to purchase — for example, the yet-to-be-released Apple Watch. At this point, we don’t know whether it will need to live within the Apple ecosystem or whether Apple will follow competitors such as Fitbit and allow the Watch to share information with non-Apple applications.
With all these interconnected products and services, you’d be smart to review their privacy policies, ensuring that information shared among the apps is always under your control. You probably don’t want your exercise stats shared with everyone on Facebook.
Of the fitness-device vendors at CES, iFit had the most entertaining presentation; it featured dancers wearing iFit bands and showcased how their bands interacted with other locations and devices. But I think Fitbit wins the prize for connecting with third-party apps and services. Exercise bands are the current rage, but I suggest taking your time picking one. Ask your friends what they like and dislike about theirs.
Is this finally the year of bitcoin?
Bitcoin is traveling a rough road to legitimacy. Perhaps one indication that it’s becoming mainstream was the bitcoin section at CES, where many vendors displayed tools for working with the digital currency. (Last year, bitcoin was a poor investment; it lost more value than most mainstream currencies.)

Figure 3. Bitcoin and vendors who support the controversial currency were prominent on the show floor.
I still don’t use bitcoin because I feel it continues to be tainted by the dark side of the Web. But based on the number of vendors supporting the currency, it’s clear that bitcoin is here to stay.
The wacky: Tools for making better selfies
It seemed as if there were almost as many selfie sticks at CES as iPhone/iPod cases. What’s a selfie stick? If you want to take a picture of yourself but can’t find a random nearby person to snap the shot, you can now cart around a golf club–like extension stick that lets you hold your smartphone at the proper distance. There’s even a Bluetooth-connected button on the stick’s handle to trigger the phone remotely.
Future tech: Cars, planes, and 3-D printing
Three consumer categories rapidly on the rise are smart cars, three-dimensional printing, and personal aerial drones.
CES has a sizable automotive section. This year, Mercedes showed off a self-driving concept car. In the immediate future, we’ll see self-parking cars from Volkswagen and Audi. Having grown up with the Jetsons, I’m still holding out for my personal, bubble-topped, flying car.
Not surprisingly, three-dimensional printing was out in full force at the show. The printer vendors showed how easy it was to replicate a digitized object. More accurately described as small-scale, fluid-based, many-layered construction, the process is fascinating to watch and will no doubt eventually find many applications in both consumer and business markets.
A booth surrounded by netting was a sure sign of an aerial-drone display. Most of the demos showed how a single person with a remote control could precisely move a drone through the air. But Parrot went a step further: its droid flew in a ballet set to music. Each time I walked by one of these flying demonstrations, it definitely caught my attention.

Figure 4. Aerial drones were a popular category at CES.
A French-based company, Parrot’s booth included a touching reminder of the recent events in Paris. On the final day of CES, it posted a tribute to the lives lost in the Charlie Hebdo tragedy — reminding me that, no matter how much we get wrapped up in technology, the important thing is what we do with that technology.
Takeaways from a mega consumer-electronic event
I’m a veteran of many technology events, but I’ll admit I was a bit overwhelmed by my first CES. The number of products was astounding. So it shouldn’t be surprising that I found a few products that I want to purchase (and that I could afford).
I’ve already ordered the myris security device. Unfortunately, the cool Parrot plant-watering gadget won’t be available until later this year. But I could not resist the first-edition plant monitor (more info) that alerts you when a plant needs water, requires fertilizing, or has other needs.
I’m definitely thinking about other automation devices for my house. I’ll keep an eye out for Zigbee and Z-Wave devices, as well as the Iris products featured in the Lowe’s (site) exhibit.
I’ll also be interested in following the fitness-wearables market and seeing how those products compare with Apple’s upcoming devices.
CES 2015 reportedly had more than 170,000 attendees. I’m sure there were that many pairs of tired feet. Had I not gone with friends who were CES veterans, I’d probably still be trying to find my way out of the North Hall and out onto the acres of space on the main floor.
Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com).
Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners.
Your email subscription:
- Subscription help: customersupport@askwoody.com
Copyright © 2025 AskWoody LLC, All rights reserved.

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
WinRE KB5057589 fake out
by
Susan Bradley
2 hours, 10 minutes ago -
The April 2025 Windows RE update might show as unsuccessful in Windows Update
by
Susan Bradley
2 hours, 18 minutes ago -
Firefox 137
by
Charlie
5 hours, 1 minute ago -
Whisky, a popular Wine frontend for Mac gamers, is no more
by
Alex5723
8 hours, 29 minutes ago -
Windows 11 Insider Preview build 26120.3863 (24H2) released to BETA
by
joep517
8 hours, 41 minutes ago -
Windows 11 Insider Preview build 26200.5551 released to DEV
by
joep517
8 hours, 44 minutes ago -
New Windows 11 PC setup — can I start over in the middle to set up a local id?
by
ctRanger
1 hour, 49 minutes ago -
Windows 11 Insider Preview Build 26100.3902 (24H2) released to Release Preview
by
joep517
12 hours, 15 minutes ago -
Oracle kinda-sorta tells customers it was pwned
by
Nibbled To Death By Ducks
18 hours, 17 minutes ago -
Global data centers (AI) are driving a big increase in electricity demand
by
Kathy Stevens
1 day, 4 hours ago -
Office apps read-only for family members
by
b
1 day, 7 hours ago -
Defunct domain for Microsoft account
by
CWBillow
1 day, 4 hours ago -
24H2??
by
CWBillow
18 hours, 16 minutes ago -
W11 23H2 April Updates threw ‘class not registered’
by
WindowsPersister
12 hours, 31 minutes ago -
Master patch listing for April 8th, 2025
by
Susan Bradley
12 hours, 44 minutes ago -
TotalAV safety warning popup
by
Theodore Nicholson
3 hours, 32 minutes ago -
two pages side by side land scape
by
marc
3 days, 5 hours ago -
Deleting obsolete OneNote notebooks
by
afillat
3 days, 7 hours ago -
Word/Outlook 2024 vs Dragon Professional 16
by
Kathy Stevens
2 days, 10 hours ago -
Security Essentials or Defender?
by
MalcolmP
2 days, 12 hours ago -
April 2025 updates out
by
Susan Bradley
7 hours, 46 minutes ago -
Framework to stop selling some PCs in the US due to new tariffs
by
Alex5723
2 days, 6 hours ago -
WARNING about Nvidia driver version 572.83 and 4000/5000 series cards
by
Bob99
1 day, 20 hours ago -
Creating an Index in Word 365
by
CWBillow
2 days, 22 hours ago -
Coming at Word 365 and Table of Contents
by
CWBillow
1 day, 10 hours ago -
Windows 11 Insider Preview Build 22635.5170 (23H2) released to BETA
by
joep517
4 days, 2 hours ago -
Has the Microsoft Account Sharing Problem Been Fixed?
by
jknauth
4 days, 5 hours ago -
W11 24H2 – Susan Bradley
by
G Pickerell
4 days, 7 hours ago -
7 tips to get the most out of Windows 11
by
Alex5723
4 days, 5 hours ago -
Using Office apps with non-Microsoft cloud services
by
Peter Deegan
7 hours, 9 minutes ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.

