|
ISSUE 17.6.0 • 2020-02-10
The AskWoody PLUS Newsletter
In this issue WOODY’S WINDOWS WATCH: Important developments in the world of Windows BEST OF THE LOUNGE: Isolating Internet connections on a LAN LANGALIST: PC screen continually goes dark SMALL BUSINESS: How we automated the Win7 ESU-purchase process BEST UTILITIES: Freeware Spotlight — security.txt WOODY’S WINDOWS WATCH Important developments in the world of Windows
By Woody Leonhard This past week saw some major changes in Windows as we know it — from remarkable bugs in Win7 to frightening discoveries about Win10. Microsoft is (once again!) reorganizing the Windows team. Do we have reason for hope … or does it presage doom and gloom? My magic eight ball says: ‘Doom and gloom!’
I try to avoid repeating news items in the AskWoody Plus newsletter, but this past month has been a real barn burner. Indulge me for a moment. The Windows 7 crowd saw the official end of free patches on January 14 — then discovered that the final January updates broke the “Stretch” wallpaper setting and turned the background black on some Win7 systems (Computerworld article). Piling on, there was a string of reports that Win7 was suddenly sprouting warnings that “You don’t have permission to shut down this computer.” Add Susan Bradley’s ongoing efforts to bring Win7 Extended Service Updates (ESUs; Computerworld) — a three-year, U.S. $70-per-year patching reprieve — to individuals and small businesses, and we’ve had more important Win7 news in the past few weeks than in the preceding few years. Then we heard rumors that a certain group of Office users — mostly folks whose companies subscribe to Office 365 ProPlus — are going to get their default search engine in Firefox and/or Google Chrome switched to Bing. It’s browser hijacking, pure and simple — something that Microsoft has railed against for years. Only this time, Microsoft’s doing the hijacking. If all of that weren’t enough news for one lifetime, we discovered last week that Microsoft’s using an undocumented back door (Computerworld) in the Windows 10 Search function to beta-test buggy code. The immediate fallout was millions of machines with black Search boxes. But the root cause appears to be much, much more distressing. And this litany of missteps and changes is playing out against a backdrop of yet another Windows reorg. Many of you think that Windows — being an enormous cash cow for Microsoft, to the tune of billions of dollars a quarter — is being steered by an MS executive who has Windows’ reputation at heart. Not true. Back in April 2018, Microsoft and Windows chief Terry Meyerson parted ways. Microsoft then broke Windows into two pieces (Computerworld): the Windows Core team takes care of the internals, while the Windows Experience team deals with the parts of Windows that you and I can interact with. The Windows group has long had a similar division of labor internally, but the big change in April 2018 came when Microsoft split the two groups into two completely separate operating divisions within the company. The Core team went with Jason Zander, whose Azure and Windows group reports to Scott Guthrie. The UI, er, Windows Experience team went with the legendary Joe Belfiore and was placed, along with Office 365 and Panos Panay’s Surface group, under Rajesh Jha. At that point (nearly two years ago) Windows no longer had a single guiding light. It also didn’t have a seat on the MS Senior Leadership Team. This, in spite of all the money it was — and still is — making. (We don’t know how much because of some very creative accounting. But that’s a beef for another time.) This past week we saw another shift in Microsoft’s Windows management. ZDNet’s Mary Jo Foley posted the details, but the upshot is that Joe Belfiore’s heading off with his family for another months-long cruise and the Windows Experience group will soon report to Panos Panay. Yes, the guy who brought us the MS Surface’s legendary customer-support debacle (Computerworld) is about to take charge of the part of Windows that you and I live with. Scott Guthrie? I don’t know where he is. Haven’t heard from him in many months. Jason Zander’s still in charge of Windows Core, apparently, but he has a lot of eggs on his plate — his LinkedIn profile says he “leads the core teams building Microsoft’s intelligent cloud and intelligent edge — from silicon to cloud to the edge. This purview includes Azure strategy; product management; engineering and operations of cloud product lines including IaaS, PaaS, Microservices, Networking, Storage, IoT, SQL Server, Big Data & Analytics stacks, Quantum Computing, global expansion, and more.” Did you see Windows in that list? Me neither. We’ve seen some significant improvements in Windows lately. For example, the “Pause updates …” feature in Win10 versions 1903 and 1909 alone was a remarkable advance in putting patching control back into the hands of Windows users. But in the past few weeks we’ve seen a back door, a threatened browser hijacking, and Windows management forking again. I don’t feel comfortable about this. Not one whit.
Eponymous factotum Woody Leonhard writes lots of books about Windows and Office, creates the Woody on Windows columns for Computerworld, and raises copious red flags in sporadic AskWoody Plus Alerts. Best of the Lounge Isolating Internet connections on a LAN
Local-area networks (LANs) are indispensable for sharing an Internet connection and stored files between multiple computers. But suppose you want to block one computer’s access to the Web but still allow some file sharing? And dual-booting Windows 7 and Mint — which does need access to the Web — adds even more complications. AskWoody Plus member Slowpoke47 posted this problem in the Lounge. The solution? Accept some connectivity compromises. Linux Plus member Bill C just finished a new Linux Mint–based machine and seeks opinions on configuring a second data drive. What file system is best? Solid-state drive (SSD) or standard hard drive? We expect sometimes wildly different “what’s best” points of view in the AskWoody forums, but in this case, there’s a surprising level of consensus. Linux With Win7 having passed its end of life, many Windows users are pondering Linux as an alternative. Plus member RMeijer turns to the Lounge for opinions on this approach — and fellow members oblige. Cloud storage Lounger Ian uses the free version of OneDrive and is puzzled about the service’s three-file limit. Fellow Loungers quickly come up with an easy solution: ZIP files. SECURITY Microsoft regularly adds, removes, and changes functions in Windows — and not always for the better. So Plus member 280park asked for the forum’s take on how Microsoft’s Windows Defender stacks up against the many third-party alternatives. Share your thoughts on this critical security necessity. Most of us feel the pain of spam clogging up our email inboxes. Plus member dmt_3904 is looking for tips on how to stanch the flood. One partial solution is to create rules that automatically send unwanted mail to the trash. Help us all out … share techniques that have worked for you. Linux As support for Win7 ends, Linux has become a hot topic in the forums. Many Loungers have migration questions, so Plus member Alex5723 started a Win7-to-Linux discussion with a link to an Ubuntu blog. That post highlights the installation process, hardware considerations, and getting to know Linux. Join the discussion — and bring a Linux appetite! If you’re not already a Lounge member, use the quick registration form to sign up for free. LANGALIST PC screen continually goes dark
By Fred Langa A laptop suffers unpredictable and repeated partial screen-blankings, requiring a reboot to restore normal operation. Is it hardware? Software? Both? The approaches outlined in this article should help to isolate and correct this and similar problems. An unreliable screen makes laptop worthless
AskWoody member Alvaro Mera writes:
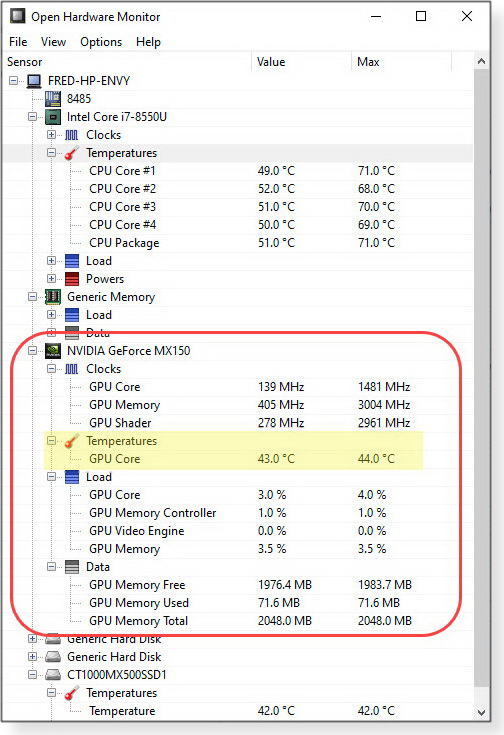
Sure! There’s clearly some kind of graphics issue, but there’s also a reassuring sign: the cursor remains visible while the rest of the screen goes dark. This suggests there’s no fundamental hardware failure such as a dying graphics chip, screen, or backlight — any one of which would cause the screen to go totally dark. So although the laptop isn’t working properly, its basic hardware is probably still okay. What’s causing the malfunction? When a PC component runs normally for a while and then fails, it’s often a thermal issue — i.e., it’s overheating. This type of problem goes something like this: When you first turn on the PC, all the hardware is at room temperature, so everything starts and runs fine. But after some random time — until you’ve used the system for a while, or the room warms up, or you start a task that’s really demanding — some component begins to overheat and shuts itself off for self-preservation. But after cooling a bit (such as in the minute or two it takes to reboot), the temperature can drop back within spec. Everything works again … until the next overheating episode. To see whether heat is the culprit, keep an eye on your laptop’s internal temperatures as it runs. That should show whether overly high temps are causing the transient hardware failures. Ideally, in tracking down a suspected graphics-system thermal problem, you’d focus on the GPU itself — the graphics processing unit. But many midrange, mainstream PCs (such as the Inspiron N5110) use integrated graphics, where everything’s on the mainboard. There’s no separate, isolated GPU to monitor. In these cases, you’ll need to monitor the mainboard and CPU (central processing unit) temperatures instead. In some systems, Windows’ Task Manager will display temperatures for you. Open Task Manager/More details and click on the Performance tab. If Windows can display your GPU’s temperature, the readings will be shown right next to the GPU’s thumbnail performance graph. Don’t worry if your PC’s Task Manager doesn’t show temperatures; many — including mine — do not. (It’s usually an OEM/vendor design decision and not under user control.) If your PC doesn’t show temperatures on its own, use a third-party app such as Open Hardware Monitor (free/open source; site). This app also displays fan speeds, voltages, load levels, and clock speeds (see Figure 1).
There are many similar temperature-monitoring apps to choose from, as the Google search “windows+GPU+hardware+temperature+monitor” will illustrate. In any case, the idea is to leave a temperature-monitoring app open and visible on your PC’s desktop while you go about your business. Keep an eye on temperature changes as you work. Take note of any temperature spikes, especially if they’re soon followed by one of those mostly blank-screen episodes. That scenario would almost certainly confirm a thermal issue! What temperatures are acceptable? You may be able to look them up online. Check the tech-spec pages on your system’s support site to see whether they list maximum allowable temperatures for the PC and its components. Alas, not all do. For example, my HP laptop has a separate NVIDIA graphics subsystem, but neither NVIDIA nor HP lists a maximum allowable temperature for the GPU in this configuration. In cases like this, where no specific temperature is given, you have to fall back on less-precise rules of thumb to gauge safe PC operating temperatures. For example, many current GPUs and CPUs will typically idle at temperatures around 100-125F (37-52C); will operate under load at around 175-185F (80-85C); might reach 200F (93C) or so under sustained, full-throttle operation; and will usually auto-shutdown (to prevent thermal damage) as temperatures approach 212F (100C). Again, these are just general guides — use them only in the absence of better, specific information from the maker. In all cases, lower temps are better. If your PC shows high temperatures, especially just before an anomaly (such as the screen going dark), it’s reasonable to assume there’s a thermal problem that needs correction. In PCs that have been in use for a while, thermal problems often have a very simple cause: reduced airflow due to dust and dirt accumulating inside the PC’s internal airways, heat exchangers, and fan/fans. (See Figure 2.)
The cure for this kind of overheating is as simple as keeping the insides of your machine clean. See, for example, the Oct. 13, 2011, Top Story “Take your PC’s temperature — for free!,” which offers more detail on how to detect and correct PC overheating. (It’s an older article, but the basics of air-cooled PCs haven’t changed at all.) If the problem persists after cleaning, or if high temperatures weren’t the problem in the first place, then the culprit most likely lies in the software setup. This is especially true in Alvaro’s case, as he said his PC “also has Win7.” A second OS installation on a drive always complicates matters due to the possibility of cross-contamination and interference. Moreover, if his Win10 system was upgraded from Windows 7, something from that original Win7 setup might have been carried over and incorporated into the new setup. For example, a bug in the recent January Win7 update caused black screens when the wallpaper was set to “Stretch.” (See the Jan 27, 2020, Computerworld Woody on Windows article.) It’s possible that this screen-saver flaw made its way into Alvaro’s hybrid Win7/Win10 setup, causing it to generate a black screen when the screen saver kicks in. Similarly, old Win7 graphics drivers may be causing trouble, especially if they were carried over into the current Win10 setup. The easiest fix for these kinds of mixed-OS issues is to simplify and “purify” the setup by reinstalling Windows from scratch using installation media on a DVD or a flash drive. Unlike the Reset and Fresh Start options built into Windows, using DVD- or flash drive-based installation media lets you repartition or reformat your system drive, wiping out any old OS installations or dual-boot setups and ensuring that no settings or software of any kind gets carried over into the new setup. A total, bare-metal, Win10 reinstallation is fast, free, and easy. After making a complete backup of the malfunctioning system, go to Microsoft’s Download Windows 10 page. Skip the Update now link near the top of the page; instead, click the Download tool now button under Create Windows 10 installation media to download the Media Creation Tool. (See Figure 3.)
Next, following the instructions listed under Using the tool to create installation media (USB flash drive, DVD, or ISO file) to install Windows 10 on a different PC, run the tool and burn the installation files to a DVD or flash drive. Boot your malfunctioning PC from the flash drive or DVD and use the standard Win10 setup/installation routine to install a fresh, from-scratch copy of Win10 — a setup uncontaminated by any remnants of the old setup. Once the new and completely clean copy of Windows is up and running, visit the laptop maker’s support site to download and install any special drivers you might need. With a clean copy of Windows, and the PC running within thermal specs, your screen-blanking problems should be a thing of the past!
Fred Langa has been writing about tech — and, specifically, about personal computing — for as long as there have been PCs. And he is one of the founding members of the original Windows Secrets newsletter. Check out Langa.com for all of Fred’s current projects. SMALL BUSINESS How we automated the Win7 ESU-purchase process
By Amy Babinchak At Harbor Computer Services, we specialize in providing IT services to small businesses with between one and 100 computer users. An important part of those services is helping customers modernize their business processes by effectively using applications and tools provided with their Microsoft 365 subscription. Often, this entails automating repetitive office tasks — an approach we also apply in our own business. Here’s an example. As you are no doubt aware, we’ve set up a process by which AskWoody newsletter readers may obtain Windows 7 Extended Support Updates (ESU) licenses. We knew that many small businesses still depended on Win7 systems; we also knew that it’s not easy to obtain small numbers of ESU licenses through local MS Cloud Solution Provider IT firms. When we set up our ESU offer, I had no idea how many requests we’d see. Quite a few, as it turned out. It soon became clear that we had to help ourselves by automating as much of the purchase process as possible. (As mentioned in previous articles, there is no markup for this service — the only additional cost is for credit-card fees.) On the surface, making an ESU purchase sounds like a simple task. But when you break it down, there is really a whole bunch of small steps that take someone’s time. Complete processing of an ESU license–purchase goes like this:
When we see repetitive tasks such as those listed above, we look for ways to make them simpler and quicker — using tools we already own. In this case, we didn’t automate the entire process but did take some big bites out of it. Here’s what we do now to make it less time-consuming. 1. Set up a separate email address and folder for correspondence
We started out by creating an email alias (HarborESU@harborcomputerservices.net; see Figure 1) in MS Exchange to manage any questions we might receive about ESU licensing. In this instance, an alias is just another email address that is associated with an individual (i.e., my colleague Ted, who is managing ESU licensing). We often use an alias for special purposes such as this.
In Outlook, we created a folder for ESU inquiries, then used the Outlook Rules Wizard to have the emails automatically placed into the new folder, where they could easily be reviewed and answered. (See Figure 2.)
2. Create an application form
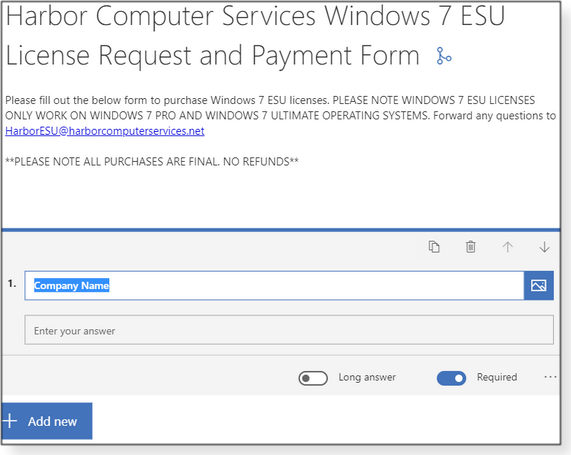
We used Microsoft Forms (more info) to create the simple application where ESU customers enter all the information needed to make an ESU purchase. Using Microsoft Forms is super simple: you just create fields selected from the various available question types. (See Figure 3.)
Your custom forms can be as simple or as complex as needed. (See Figure 4.) The app even handles branching.
Once a custom form is finished, you share it either internally or publicly. For example, you can see our final ESU-application form, shared online with anyone who has the URL created by MS Forms. The service will notify you automatically whenever someone has completed a shared form. We tend to purchase ESU licenses in small batches. To help us manage application information and purchases, we set up a simple data table as an alternative to keeping track of multiple completed forms. 3. Deliver Forms data to SharePoint
We used a pre-made template in Microsoft’s Power Automate (formerly known as Flow) to connect Forms and the SharePoint-based table, as shown in Figure 5.
Setting up the template is a simple process of associating Forms fields with those in SharePoint via a drop-down list. With that step done, our SharePoint list is automatically populated for us (see Figure 6).
3. Send data to MailChimp
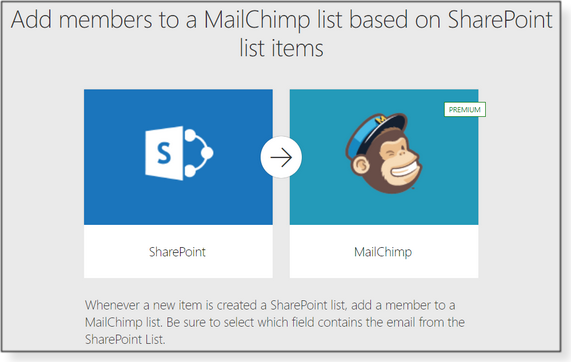
At the end of 2020, we want to remind ESU customers that they need to re-subscribe for another year. (Actually, we hope they don’t renew their ESU licenses in hopes they’ve moved along to Windows 10.) To simplify that notification process, we again used a Power Automate template (Figure 7) to automatically add any customer email addresses tagged with “Win7” to MailChimp (the same service used to send out AskWoody Plus newsletters).
It’s fantastic that we can move data between various cloud services via Power Automate. And Microsoft has made the process surprisingly easy. Microsoft expects process-automation tasks such as those we set up to be built and managed by “citizen developers.” In other words, we all have the power to create processes that would once have required complex and expensive custom applications. Now, we can just use tools at hand to create forms and work flows from pre-built templates. Again, we didn’t automate the entire ESU-purchase process, but we did eliminate a good bit of data entry, email sending, and organization headaches that can eat up an employee’s time. In our case, these tools helped defray uncompensated expenses. But for many small businesses, a cloud-based Microsoft 365 subscription can add to the bottom line. That’s always our goal, too. We believe that IT should never be an expense — it should be a valuable tool that lets people get more things done.
Amy Babinchak is the owner of three IT-related businesses: Harbor Computer Services, Third Tier, and Sell My MSP. She has been working in the IT field with small and medium businesses for more than 20 years. She’s also a Microsoft MVP and has received numerous leadership awards. Best Utilities Freeware Spotlight — security.txt
Just when you thought you knew everything about the Internet … Remember Easter eggs — digital-style? Those hidden gems embedded in applications? Alas, few exist anymore; The Easter Egg Archive lists past and present examples. Here’s one: In Firefox, enter about:mozilla in the URL bar. There’s a sort of Internet equivalent to the Easter egg — though not as charming. Many websites are adopting two “hidden” venues designed to provide a bit of inside information. Security.txt provides a standardized place where websites and software authors can define their security policies (more info). And security researchers can use the information on a security.txt page to responsibly report newly discovered vulnerabilities to website or software owners. Humans.txt is a less formal initiative for posting information about a website’s authors (info) — or just something fun. Again, security.txt and humans.txt are typically hidden; to see them, you must know where to look. For example, if I want to watch something on Netflix, I simply go to netflix.com. But if I want to get more info about the staff and maybe employment information, I must enter netflix.com/humans.txt into my browser. I’ll then see this (Figure 1):
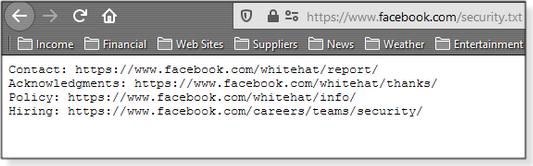
Let’s suppose a security researcher finds a vulnerability in a company’s software or website and wants to report it — and possibly score a nice bounty. She could simply look for a security.txt file on the site. For example, type facebook.com/security.txt into any browser and you’ll see the helpful information shown in Figure 2. You’ll now know where to report discovered security flaws, see acknowledgments of valid reports, find other related information, and apply for a job — because you outsmarted the company’s current security team!
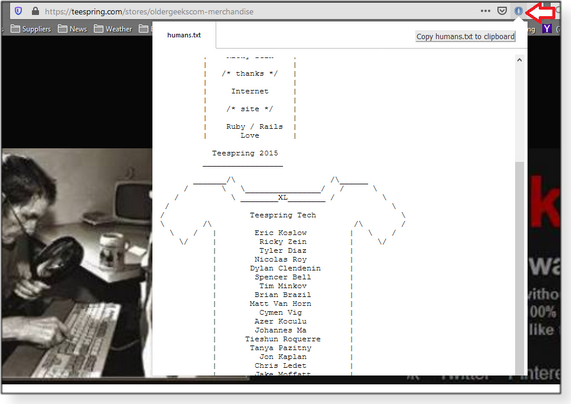
Unfortunately, finding a site’s security.txt or humans.txt info can be a shot in the dark. Wouldn’t it be cool if your browser just notified you when these pages are present? It can! (Did you really think I wouldn’t show you how to make this happen?) Harmless Systems’ security.txt app is a browser extension for Firefox, Chrome, Chromium, and Microsoft Edge. (An Opera edition is coming soon.) Head over to our OlderGeeks site to download it. Using this extension is nearly effortless, and it’ll automatically find both security.txt and humans.txt files. I’m using Firefox for the following examples, but it works the same in any of the other supported browsers. So let’s just start surfing and see what we find. It’s kind of like hunting for very bland treasure! Okay, I found something … We sell t-shirts and stuff on Teaspring (shameless plug). So if I go to our (ahem) store at https://teespring.com/stores/oldergeekscom-merchandise, I get an alert from the security.txt icon at the right end of the address bar (see Figure 3). Although the .txt file is in the root of the website’s folder structure, the extension still finds it, no matter where I am on the website.
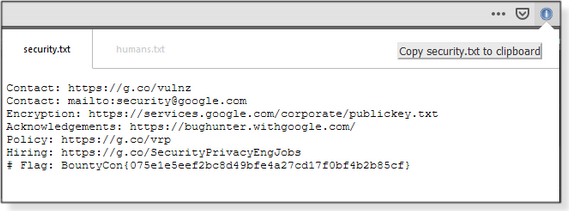
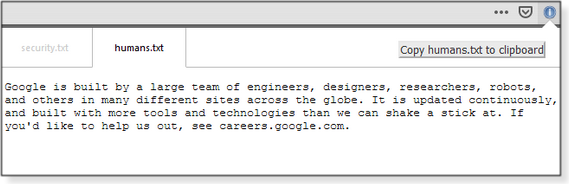
Next, I’ll try Google. Here, I’m notified of both security.txt and humans.txt files under two tabs (Figures 4 and 5).
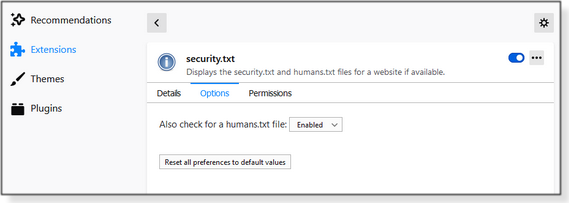
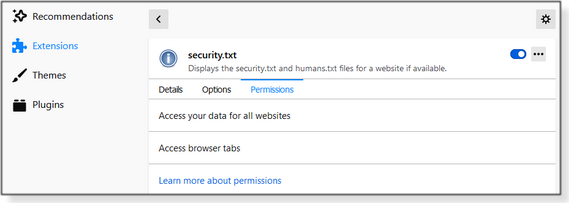
The security.txt extension has just a few options. In your browser, open the add-ons or extensions section and click on “security.txt.” When it opens, you’ll see three categories: Details, Options, and Permissions (Figures 6, 7, and 8).
The Permissions section reports that you’re allowing the extension to read all data on any webpages you open as well as any data you enter (including, possibly, user names and passwords). Fortunately, it’s easy to turn the extension on or off, as needed. In fact, it might be instructive to read what your browser’s permissions mean. (It might make you squeamish about allowing most extensions.) See, for example, the Permission request messages for Firefox extensions page. It’s somewhat scary that most extensions have access to your Web-based data. It comes down to whom you trust. So there you have it: something you probably didn’t know about the Internet. Many websites are using security.txt and humans.txt to provide some “insider” or background information. And sometimes these special pages are quite entertaining. See if you can find some good ones, then share them in the AskWoody Lounge. And if you happen to go on an Easter egg hunt, let us know what you find! It’s a disappearing part of personal-computer history. Happy Computing!
Deanna and Randy McElveen are celebrating over 20 years in the computer business, ten years running OlderGeeks.com, and more than 26 years of putting up with each other. Their computer store is in a small town in the Missouri Ozarks. Believing that happy customers are always the best advertisement, they hope to do it for another 20 years. Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com). Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners. Your email subscription:
Copyright © 2020 AskWoody LLC, All rights reserved. |










 By Deanna McElveen
By Deanna McElveen