|
ISSUE 17.10.0 • 2020-03-09
The AskWoody PLUS Newsletter
In this issue ON SECURITY: How small businesses are easy ransomware targets BEST OF THE LOUNGE: Deleting a stubborn file in Windows 7 LANGALIST: Is your deleted cloud data really gone? APPLE MAC: Switchers: Taking a bite of the Apple – Part 1 UTILITIES: Updates to the Askwoody Ultimate Utilities List ON SECURITY How small businesses are easy ransomware targets
Yes, they really are out to get us. Recent trends in malicious attacks mean that small businesses need to be more vigilant than ever. As exploits rapidly evolve, we face the threat of falling behind in the battle to protect ourselves. On the latest front, simply keeping backups of our data isn’t enough. Ransomware: Your backups won’t protect you
Ransomware attacks could now be the biggest digital threat to small businesses and organizations. At one time, keeping complete archives of your data was considered the best defense. No more. It’s now possible that malicious hackers know more about your backup system than you do. Increasingly, ransomware attacks are targeting not just live data but backup files, too. Those critical archives are being deleted, encrypted, or otherwise damaged as part of an attack. Think the cloud is safe? Ransomware attacks are also targeting cloud-stored archives, as reported in a Bleeping Computer article. Recently, a malicious hacker brazenly revealed that they possessed one business’s online-backup credentials as proof they could access everything on the company network. In a recent post (PDF download), the U.S. Federal Bureau of Investigation (FBI) warned: “Between January 2014 and October 2019, the Internet Crime Complaint Center (IC3) received complaints totaling over $2.1 billion in actual losses from business email–compromise [BEC] scams targeting Microsoft Office 365 and Google G Suite.” The FBI still recommends that you do not pay ransomware. But if both your active files and your backups are encrypted by the attackers, you may not have any other viable option. So what should small businesses do to protect their backups, too? In short, a lot more than we’re doing now. Sadly, I have to ask: Do you actually have thorough and recent backups of your critical business data? If you can’t confidently answer “Yes,” stop reading this article and get your archiving procedure in order — right now! Determining a safe place to store your backup files
First and foremost for protecting yourself from ransomware attacks is the location of your archives. Are you comfortable simply storing your data on an external hard drive? How about cloud-based backup services? How about both? The safest solution is to store copies of your backups in multiple locations. Remember the old saying that you can never be too rich or too thin? Small businesses can never have too many backups — especially when it comes to ransomware threats. Here’s the key to a complete backup strategy: sign up for OneDrive or Google Drive, plan on keeping several external hard drives dedicated to backups, and, most important by far, always have at least one of the drives offline at all times. Finally, educate your staff on how ransomware starts. A Microsoft Doc article has a quick and simple summary. Eliminate direct access to backups
That might sound like a silly or excessive requirement to some of you, but if you can easily browse through your archived files, a malicious hacker can, too — and then encrypt them. As an additional layer of defense, use a backup software/service that signs in to your network under a special account — one that’s not connected to an individual. For example, the paid version of Macrium Reflect includes this extra protection via its Macrium Image Guardian feature. Other backup vendors have similar capabilities — but always in their paid versions. When you run a backup on Windows Server, the process takes the drive offline so that it’s hidden from the file system. Another option for small businesses is using Microsoft Azure or Microsoft 365 Business. MS 365’s combination of SharePoint and OneDrive for Business lets you use the services’ recycle-bin features and versioning to recover files deleted in a ransomware attack. Don’t plan on finding a decryption key online
Regularly at small-business forums and venues, I run across folks asking about a magical de-encryption key that will unlock their data. No two ways about it, there is no magic key! Sites such as nomoreransomware.org can sometimes help decrypt a compromised system — but only if the attackers used a previously cracked encryption system. (White-hat hackers attempt to take over locked systems and reveal the encryption method and keys.) If you’re really stuck, security experts recommend that you not pay the ransom. Instead, they suggest contacting the FBI or your antivirus vendor first; they might be working on a take-over project and have decryption keys that have not been publicly posted. If you do contact whoever encrypted your data, you might try negotiating for a lower price to get your data back. Cyber insurance for small businesses
Yes, there is such a thing — and it’s not an unreasonable cost for smaller businesses. Like all insurance, hopefully you’ll never need it. But if you fall prey to ransomware, cyber-insurance reps can provide you with guidance and information on how to best proceed with the attacker — for example, how to obtain bitcoins. They can provide other tools for remediating the crisis and help determine whether you need to contact your customers. But possibly most important, a cyber-insurance rep can be a calming presence when you’re freaking out over your now inaccessible data. Ask your normal insurance broker if they can point you to cyber-insurance vendors. Adding a pound of prevention
First and foremost, add two-factor authentication to everything that requires a password. It’s another critical line of defense should a password be stolen. As noted in the aforementioned FBI alert, cyber criminals develop and use phishing kits specifically targeting Google G Suite and especially Microsoft Office 365, due to its vast market share. If you have an Office 365 Business subscription, the alert recommends that IT admins take the following steps. (Some of these recommendations will require additional licenses for security add-ons.)
The upshot? If you currently access your Office 365 email account with merely a username and a password, you’re potentially a sitting duck. Attackers can employ various techniques to steal your credentials. Also, if you use a consultant to help with your small-business email configuration, recommend that they visit Alex Fields’s excellent ITProMentor site and download his MS 365 Business security guide. I follow the recommended steps in my business. Also, send your consultant the link to Alex’s Best practices checklists. Ask whether they are using similar techniques to help protect your network. Keep this in mind: Anyone can be tricked
Along with ransomware, wire-transfer fraud is another significant threat. Shark Tank’s Barbara Corcoran found out the hard way (CNN article), when scammers got authorization for a wire transfer by changing one letter of an email. Barbara was fortunate to recover her funds; you might not be so lucky. Put in place some old-fashioned analog precautions for wire transfers or other financial transactions. Use a standard verification process that does not include email. For example, pick up the phone! Barbara’s staff got nailed by one of the newest oldest tricks in the book. The FBI alert explains how it’s done:
The FBI’s recommendation:
Bottom line: It’s not easy to stay one step ahead of ever-evolving malicious hacks and scams. Making sure you’ve built strong cyber-defense walls is a never-ending task. But it’s well worth the effort for keeping your business safe.
In real life, Susan Bradley is a Microsoft Security MVP and IT wrangler at a California accounting firm, where she manages a fleet of servers, virtual machines, workstations, iPhones, and other digital devices. She also does forensic investigations of computer systems for the firm. Best of the Lounge Deleting a stubborn file in Windows 7
Many Win7 users are thumbing their noses at Microsoft and sticking with the beloved OS — despite the end of free support. But that doesn’t mean they won’t run into computing problems from time to time. Win7 is still Windows. Case in point: Plus member opti1 ran into a pesky Malwarebytes popup on a Win7 Home Premium machine. After making several attempts to delete the popup’s associated file and getting only “File Access Denied” messages, opti1 turned to AskWoody forum members for help. As was suggested, running the Malwarebytes Support Tool came to the rescue. PC buying Plus member AusJohn is having a custom computer built and wants to know which edition of Win10 — the retail version or an OEM copy — is best. The crux of the discussion is differences in licensing. Fortunately, fellow members weigh in with solid advice. Browsers Denied access to common news sites — whether using Chrome, Firefox, or Edge — Plus member magicspeller needs help looking for an offending ad blocker. Disabling uBlock Origin and Ad Muncher did not help. And online news sites are notorious for preventing or severely limiting access when ad blockers are enabled. Suggestions abound, but the issue remains. Upgrading Plus member WSClouddancer has a question we often see in the Lounge. To wit: Will transferring personal data from Win7 to Win10 have any impact on the operation of the newer OS? The answer is relatively simple: With an in-place upgrade, incompatible files and apps won’t be transferred. WSClouddancer is pleased with the responses and plans to share them with the tech managing the upgrade. Win7 EoL An anonymous reader wants to know whether a Win7 PC that’s not connected to the Internet will last indefinitely without updates. The computer will be used only for music and photos. In theory, an Internet-free system is safe. But USB drives, Wi-Fi, and software upgrades are all potential threats. Share your thoughts on protecting Win7 machines. Backups What can you do when a system image written to an external drive won’t work? That’s the dilemma for Plus member mpw. Fellow Loungers offer various tips to solve the problem. But ultimately mpw finds the fix: changing Windows’ backup settings. Browser DaBoss Microfix has found possibly the perfect Web browser. The challenge to fellow Loungers? Hunt down and “name that browser!” If you’re not already a Lounge member, use the quick registration form to sign up for free. LANGALIST Is your deleted cloud data really gone?
By Fred Langa Most Windows users know that clicking “delete” does not actually erase local files. The same holds true for your data stored in the cloud. Those files can remain in remote backups or in online services’ logs for a very long time. Fortunately, there’s an easy way to keep your left-online data protected, even when it’s no longer under your full control. Here’s how. Plus: More on the demise of Windows’ screen saver. Worries deleted cloud-based data getting left behind
Dinesh Bheda asked:
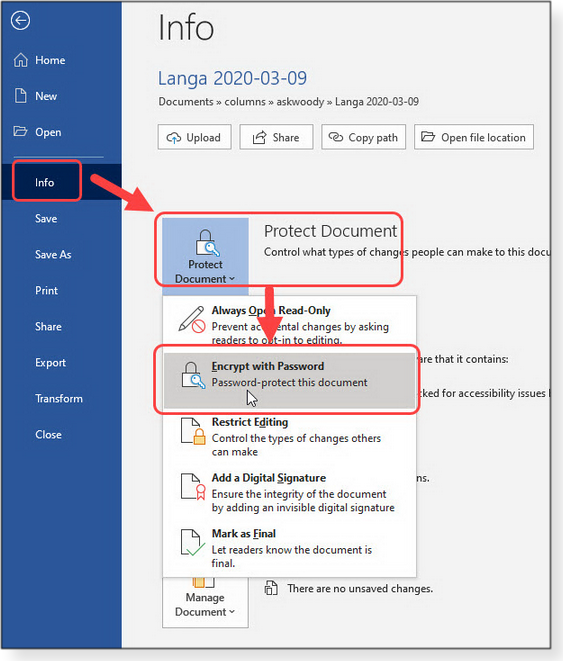
That’s an excellent question! And the unsatisfactory answer is “You can’t!” There’s no way you, as an end user, can guarantee deletion/erasure of anything you post online or save in the cloud. Your files are on someone else’s server — and only they control the for-real data retention/deletion rules. Even deleting your entire online/cloud account won’t necessarily delete your files. Some of your previous files and data will almost surely live on in your ISP’s or cloud provider’s backups and logs — at least for a while. The retention period might be weeks or months, especially if the service has a “previous versions” or “recover your accidentally deleted account” feature. (Obviously, if you can recover deleted data, there must be backups somewhere.) These backups should eventually age out and get overwritten, but there’s no way for users to know how long that will take. And in some cases, the data might be retained literally for years — for example, in jurisdictions where ISPs and/or cloud-service providers believe they need to hang on to old user data should there be future legal actions. There’s just no way to really know. So, what can you do? How can you make sure that the contents of online files will never fall into the wrong hands? Use encryption! If you encrypt your files before you upload them, it won’t matter at all where they end up or who might have access to them. With quality encryption (say, AES-256 or better) and a strong password, the contents of your online/cloud-based files will be completely secure. Let your files sit on the cloud-based server forever — who cares? No one will be able to read them! File encryption is easy, and there are many tools available. Some cloud-service providers offer their own built-in encryption. For example, OneDrive offers a “Personal Vault” (MS info) that applies BitLocker encryption to selected cloud-based OneDrive files. Some applications, such as the MS Office suite, offer good built-in encryption (i.e., “password protection”) for files, although you must enable it on a file-by-file basis. For example, within Word, click File/Info/Protect Document/Encrypt with Password (see Figure 1).
But cloud-based and built-in encryption options still force you to trust the skills and policies of the provider. The encryption isn’t truly under your control. That’s why I prefer to use a third-party encryption app to scramble files before they’re uploaded. When the encryption and decryption happen locally, on your PC, the remote-cloud provider never sees your password or the unencrypted contents of your files. You’ll know that only you hold the keys! I use the venerable 7-Zip (free/open source; site). It’s not tied to any one app, file type, or service — it can encrypt literally any file or folder on your machine. And as a bonus, it efficiently compresses There are many other free and paid encryption options, as this example Google search shows. Good file encryption is really the only way to keep your private files stored online truly private — even when they’re no longer in your possession or under your control! More on Windows’ screen-saver demise
After reading how Microsoft is deprecating Windows’ classic screen-saver feature (“Say goodbye to Windows’ screen-saver app,” AskWoody Plus newsletter 2020-02-24), several readers wondered whether dropping the built-in screen saver also meant that add-on, third-party screen savers would no longer work. For example, Bernie Cosell asked:
As far as I know, separate apps should continue to operate normally. It’s only the built-in screen saver that’s going away. John Matenkosky added:
Thanks, guys!
Fred Langa has been writing about tech — and, specifically, about personal computing — for as long as there have been PCs. And he is one of the founding members of the original Windows Secrets newsletter. Check out Langa.com for all of Fred’s current projects. Apple Mac Switchers: Taking a bite of the Apple – Part 1
With the end of free support for Windows 7, many users are looking at alternatives to Windows 10. And some are considering jumping to Apple’s Mac platform. This two-part series is an introduction to the world of Mac for those thinking about making the switch from a Windows PC. (A more-detailed verion of this article can be found in the AskWoody forum.) In this installment, we’ll cover the various types of Mac desktops and notebooks. We’ll also give tips for setting up a new Apple system. Part 2 will provide a general tour of the macOS operating system, discuss keyboard differences, and delve into Mac security concepts. Purchasing a Mac
Buying an Apple product is a bit different from purchasing a Windows PC. With the latter, you pick from numerous hardware vendors such as Acer, Dell, HP, Lenovo, and possibly even Microsoft (e.g., Surface portables). But Apple is Apple. Anything running the macOS or iOS operating system is going to be Apple hardware. That said, you’ll have numerous models to choose from among desktops, all-in-ones, and notebooks. There are plenty of places to pick up a Mac, including Best Buy, Newegg, Amazon, and even Costco. However, if you’re new to this platform, I strongly recommend visiting an Apple Store. There, you can ask questions and kick the tires, so to speak. You should also browse the various Mac models’ specifications via Apple’s online comparison page. I’ve found that purchasing directly from Apple offers some excellent perks — such as dedicated product specialists. Even as a seasoned Mac user, I’ve always walked away having learned something new. Prices should be about the same, no matter where you shop. But Apple does offer discounts for education customers (students and teachers), along with other benefits for business customers. (Ask the product specialist about any extras you might qualify for, plus any deals when combining Apple products and the company’s credit card.) Apple also offers trade-in and recycling programs. Moreover, Apple stores hold free sessions on using Apple products — from the basics to specialized topics such as photography, video, music, coding, and art. Desktop machines: Apple currently offers four major classes of desktop Macs. Note that none of these systems includes an optical-disc player.
Notebooks: Apple’s portables fall into two groups:
Before buying an Apple notebook, there are a few things to consider. First and foremost, none of these machines has the standard USB ports you find on Windows PCs. Apple has moved completely to USB-C (aka Thunderbolt 3) ports. Smaller notebooks typically have two ports, while the larger models may come with four. If you have lots of legacy USB gear, you’ll want to invest in Thunderbolt-style cables or USB C-to-Type A adapters. (There are dozens of the adapters offered on Amazon for under $10. But you might also want to consider an inexpensive after-market USB-C hub that’ll provide a variety of ports (example). Apple’s notebooks also don’t have a standard HDMI or Ethernet ports. If you want to connect an external display, you’ll need another USB-C adapter. (The aforementioned hubs will often include an HDMI port, and some models will have a standard Ethernet port.) Apple never adopted the touch-screen concept for its portables — and for some good reasons. Do you have a standard Windows notebook (not a tablet or convertible) with a touch screen? How often do you actually use it? Instead, Apple developed its somewhat controversial Touch Bar across the top of the keyboard. (Among other things, it replaces the classic function keys.) Some Mac users like this feature, others find it gimmicky. Another item you’ll want to check out at an Apple retail store is the feel of the portables’ keyboards. Most models use a butterfly-style mechanism for smooth typing. The top-end MacBook Pros use Apple’s “Magic Keyboard,” which offers more key travel and provides an experience closer to good desktop keyboards. Key backlighting is standard. All new Apple notebooks come with an expansive and responsive trackpad. They also have the “Force Touch” feature that first appeared on iPhones. There are many other features you’ll want to learn about. Check them out on Apple’s online Mac info pages — or better yet, take a test drive. One of the more challenging decisions when purchasing Apple products is whether to add the AppleCare+ extended warranty. Apple’s standard policy is one year for repairs and 90 days for tech support. AppleCare extends that another two years and also includes reduced fees for repairs due to accidental damage (up to two occurrences). I recommend buying the extra coverage. I give my Macs the white-glove treatment, but AppleCare+ has still paid for itself over the years — especially when I’ve run into deep tech issues. AppleCare+ prices vary; as you might expect, they’re higher for notebooks. But if you schlep your portable around frequently, the chances of damage are high. If you run into a problem with your Mac, I suggest taking it down to an Apple retail store and not using the mail-in repair option. One of the store reps might be able to resolve the issue while you wait. Setting up a new Mac
The initial setup process is handled by Setup Assistant (more info) — it’s generally easy and takes little time. It will, however, require that you set up a new Apple account or use an existing account. (If you already have an Apple product such as an iPhone, iPad, or even iTunes on Windows, you almost surely have an Apple account.) Setup Assistant includes Migration Assistant, which you can use to move content from a Windows machine to a new Mac. (It can also be launched later — look for it in the Applications/Utilities folder.) Another option is to use one of the various cloud-storage services to migrate user files. There’s even a macOS version of Microsoft’s OneDrive. One of the steps in Setup Assistant is configuring iCloud, Apple’s cloud-based storage (iCloud Drive) and synching service (more info). You get 5GB of online storage free, and Apple offers 50GB, 200GB, and 2TB paid subscriptions. You might be surprised to know that you can install iCloud on Windows machines, via the Microsoft Store. It’s one more way to share your data between Mac and Windows devices. Setting up applications that will work with your files will be the highest hurdle. Macs come with an excellent selection of useful software. But there are also macOS editions of many apps you currently use in Windows — MS Office 365, for example. You might want to read Apple’s related article on Mac/Windows compatibility. You can even run Windows 10 on your Mac, via Apple’s Boot Camp utility or virtual-machine software such as VirtualBox. Once you’ve installed additional apps, migrated your personal files, and become comfortable working with the macOS environment, you’ll want to open the System Preferences app and do a bit of personalization. More help online: You’ll find more on all things Apple … on AskWoody! To start, check out the macOS forum.
Nathan Parker has been using Apple devices since 2006, when he purchased a PowerBook G4 running Mac OS X Tiger. He has worked in various IT consulting roles and is currently an IT Consultant for Earth Networks (formerly WeatherBug). In addition to his contributions on AskWoody, Nathan also blogs weather updates at WeatherTogether. And he’s working on his PhD. UTILITIES Updates to the AskWoody Ultimate Utilities List
This past October, I introduced my occasional Ultimate Utilities List to the AskWoody newsletter. Readers returned the favor by offering some of their favorites in the AskWoody Lounge. Here’s an assortment of apps you might want to try out. GPSoftware’s Directory Opus: DennyB submitted this entry as an excellent substitute for Windows’ File Explorer. The one catch? It’s not cheap. The “Light” version is priced at AUD $49, or about USD $33, while the “Pro” edition is AUD $89 (about USD $59). You can try it free for up to 60 days. Backup Outlook: Michael Austin suggested this backup utility. As its name indicates, the app is targeted at keeping Outlook data and settings safe and easily recoverable. Backup Outlook costs USD $39.95, but you can try a limited edition for 14 days. ccPortable (OlderGeeks.com download): Many long-time Windows users have lamented their loss of trust in the once immensely popular CCleaner. Back in the Windows 7 era, it was the go-to utility for safely scanning and cleaning PCs. But all is not lost: several forum members recommended the free and portable version of CCleaner as a good alternative. If it’s posted on the OlderGeeks site, you know it’s safe from malware and unwanted add-ons. Microfix suggested BleachBit as yet another portable and free cleaning utility. Its focus is reducing disk clutter and enhancing privacy. RVAUser wondered at the recommendation for paid ACDSee Photo over the venerable IrfanView. Make no mistake, IrfanView is a fine free photo editor. I still have it installed on my PCs. It has a tool for many image-editing tasks. But if you’re trying to rapidly process large numbers of photos — especially RAW images from Canon or Nikon cameras — ACDSee is simply a more professional-level product. RVAUser also recommended Startpage as a substitute for DuckDuckGo (listed below). Startpage touts itself as the most private search engine in the world. It basically works as a privacy bridge between your browser and Google Search. Which means you won’t be tracked, but the top results will still contain lots of ads. One correction provided by RVAUser: The previous Ultimate Utilities List had TeamViewer as “trial/paid.” As its website clearly states, it’s free for personal use. BByg3223 suggested Greenshot as another excellent and free screen-capture app. We’ve mentioned it in the Windows Secrets editions of the list. But frankly, I’ve used Windows 10’s now built-in Snip & Sketch for all my recent screen-clipping needs. Our own Deanna McElveen has reviewed many great utilities in her regular Freeware Spotlight column. One app that I use often is Folder Painter (see also the 2019-12-23 AskWoody newsletter). It lets me quickly and easily change the color of folders in File Explorer. I use it mostly to highlight the current newsletter issue I’m working on. But it could also be a great way to tag specific image folders that are organized simply by date. Finally, I’ve replaced ACDSee with JAM Software’s TreeSize Free on the list of top utilities. Don’t get me wrong: I use the photo-editing app every day to put out the newsletter. But TreeSize Free is one of those highly recommended and indispensable tools for investigating what’s using up your storage. Do you have another utility or app you can’t live without? Tell us about it via the link at the bottom of this article. Share the wealth. A free-utilities caution: Here are a couple of important reminders about installing and using utilities that delve deep into Windows: Always be sure you have a full and current system backup before running the app. That’s especially true of “system cleaners” and “performance enhancers.” Next, watch out for those annoying and potentially dangerous software offers that often come with free utilities. The Adobe Acrobat Reader installer, for instance, has included pre-checked offers for Google Chrome and McAfee. (The various utilities hosted by our OlderGeeks friends are guaranteed to be free of tagalong software and viruses. A future Ultimate Utilities article will list apps reviewed in our Freeware Spotlight columns.) Without further delay, here are our recommendations. Our list of must-have utilities
When we set up a new machine, we install these apps first.
For browser security, I also set DuckDuckGo as my default search engine. Other recommendations
Here’s the long list of utilities we’ve suggested and discussed over the years. Let us know which ones you still use. General Utilities
Media applications
Browsing security
Drive diagnostics and management
Mobility
Password vaults
Online password checkers
On-demand antivirus scanners
Encryption
Firewall checkers
Networking
TB Capen is editor in chief of the AskWoody Plus Newsletter. Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com). Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners. Your email subscription:
Copyright © 2020 AskWoody LLC, All rights reserved. |


 By Susan Bradley
By Susan Bradley
 By Nathan Parker
By Nathan Parker By T B Capen
By T B Capen
