|
ISSUE 17.11.0 • 2020-03-16
The AskWoody PLUS Newsletter
In this issue LANGALIST: Hard drive runs almost continually BEST OF THE LOUNGE: Is FTP really a thing of the past? SECURITY: Conference showcases a tsunami of security products PATCH WATCH: Win10 cumulative update gets an update. Don’t panic! APPLE MAC: Switchers: Taking a bite of the Apple – Part 2 FROM THE EDITOR AskWoody Plus newsletter spring break
The AskWoody editorial department is taking a week off from publishing. It gives us time to catch up on some newsletter housekeeping. The next issue will arrive in your email inbox on March 30. During the break, you might still receive one or more AskWoody Alerts. We hope all our readers are staying safe and well during this uncertain time. Thanks for your continuing support. — TB Capen, editor LANGALIST Hard drive runs almost continually
By Fred Langa An AskWoody Plus subscriber’s new PC is bogging down from hard-drive saturation … but why? A little spelunking with Task Manager will usually identify the problem. Plus: Another reason for “PC screen continually goes dark” Yikes! A new PC is super slow
Writing from Virginia, Stan Palen requests help with a hard drive that’s continually busy.
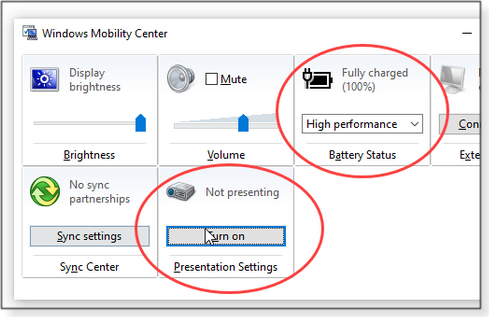
Here’s the good news: Hard drive– and SSD-related problems can usually be tracked down and solved fairly quickly. But that’s not always the case. Before you do anything else, protect yourself from any serious malfunction the PC might be experiencing. Ensure you have a current and reliable backup or system image safely stored off the PC — i.e., on an external drive or in the cloud. When you know your data is safe, start the process of diagnosis and repair. You said you used Task Manager — that’s great! It can usually point you toward what’s behind system slowdowns. Task Manager came into its own in Windows XP, but Win10 includes a nicely enhanced version. (If you’re not familiar with Task Manager, here’s a quick recap: Start by typing task manager into the Windows search box and then select the app when it’s offered. If all you see is a simple list of apps, click the More details link. Next, widen the Task Manager window until you see all columns displayed. For more Task Manager info, see “A visual tour of Win8’s new Task Manager” [Windows Secrets Newsletter 2014-06-12]. The Win10 version is functionally the same, but it includes a few handy new features.) Stan said that his Task Manager didn’t show anything “out of the ordinary.” But I’d first have to ask this: Under the Performance tab, was Task Manager’s Memory graph maxed out? In other words, was all or almost all system RAM in use? If so, the PC may simply be RAM-starved, and the disk thrashing is due to excessive pagefile activity (i.e., Windows is constantly swapping code and data between the drive and the too-limited RAM). In that instance, there’s really nothing wrong with the disk. The solution is to install more RAM. That will reduce the need for paging activity and result in a quieter and more-responsive PC. If excessive memory use isn’t evident, the next step is to isolate and examine the software — apps, system tasks, and processes — that are causing inordinate disk activity. Task Manager makes it relatively easy: Under the Process tab, clicking the Disk heading will sort that column so that the most disk-intensive apps are listed at the top. (You might have to click the heading again to see the information in descending order.) Now read across to the Name column to see what’s creating the most disk activity. Is it a third-party app? If the disk-churning application is something you added to the system (as opposed to something that’s part of core Windows or your PC’s OEM setup), try closing it. Right-click the name and select End task. If the disk problem resolves, you should probably consider uninstalling the app and picking an alternative that has better coding. Once that’s done, your disk-churn problem should be gone. Another solution — especially on older systems — is to install a faster drive. Consider swapping out a slow spinning-platter drive for a quick solid-state drive. Is it Microsoft/OEM software? Native Windows and OEM-installed apps, processes, and/or services might be the disk-eating culprit. Disk-centric activities such as defragging/optimizing, cleanup, anti-malware scanning, search indexing, software updating, and so forth could be transient maintenance activities that are unable to run to completion — at least within a reasonable amount of time. This is especially true if (as in Stan’s case) the new PC, or its current Windows version, is relatively new; the system might require a lot of initial busywork. For example, a new PC will need to index all restored or carried-over user files. This can take quite a while on a large HDD with lots of data, especially if other tasks are simultaneously competing for attention. One easy way to get past all deferred/delayed/backlogged maintenance is to let the PC run full throttle, unattended, for several hours — or, better yet, overnight. That should provide ample time for most automatic system maintenance to run to completion — as long as you prevent the system from automatically dropping into sleep or hibernate mode. You can set this up in literally seconds. Right-click the battery or electrical plug symbol in the Win10 notification area (normally the lower-right corner of the screen) and select Windows Mobility Center. (If it’s not there, type “windows mobility center” into Search and select it when offered.) With the Mobility Center open, select High performance from the drop-down list in the Battery Status section. Next, click the Turn on button in the Presentation Settings section (see Figure 1). This will suppress all the normal system throttling and time-out settings, letting your PC work as hard as it can until you tell it to stop.
Leave your PC set to those two Mobility Center settings for several hours or overnight. When you come back, all deferred and pending maintenance should be finished. Once your system has finished its work, go back into the Windows Mobility Center and change the two settings back to their defaults (or your preferences) — i.e., click Turn off in Presentation Settings and select Balanced in Battery Status. Again, see whether the disk-churn has stopped. If the PC is now operating normally, it was just backlogged self-maintenance — and you’re now done. It’s something else: At this point, you’re probably left with two possibilities, neither of them good: a malware infection or a major issue with the drive itself (such as impending hardware failure). The 2020-01-13 LangaList column “Let your PC start the new year right!” has information and links that can help in both cases. For example, the Check Your PC’s Defenses section lists resources for known-good and thorough antivirus/anti-malware tools you can use to ensure the PC is clean. The section Check drive health discusses how to thoroughly examine (via S.M.A.R.T.) — and maybe improve — your hard drive’s overall fitness. And the section Take out all the trash can help ensure that your drive isn’t choked with needless junk files. As a last resort, consider trying the techniques discussed in Removing bloatware and OEM mods from new machines (LangaList 2019-12-09). It provides details on the various ways Windows can semi-automatically reinstall itself, giving you a pristine and hopefully error-free Windows setup. Another reason for “PC screen continually goes dark”
In the 2020-02-10 AskWoody Plus newsletter, I described a laptop problem that caused unpredictable and repeated partial screen-blanking. Only a reboot would restore normal operation. The oddest symptom was that the cursor would remain visible on an otherwise black screen. After reading my suggested approaches to isolating and correcting the problem, AskWoody subscriber Gordon Insley wrote:
I replied: “Maybe, but why would some graphics (the cursor) display properly if any of the fundamental graphics hardware components was broken? I think if the interface or LCD/backlight were dead, nothing at all would display. Weird failure!” To which Gordon replied: ” I have known cursors to show up in such circumstances because they require little to no processing by the graphics components. We are not necessarily saying failure — just a malfunction. With a partially faulty inverter board, all manner of unexpected stuff can result. “However, as you noted in your article, my first call, too, would be lack of heat dissipation, then a display/video graphics driver problem. I’d consider hardware (display and display inverter) malfunctions by a process of elimination. Again, a poorly performing or slow-running fan would be a starting point. “I speak from experience — not just speculation. One of my laptops, a vintage (2005) IBM ThinkPad, is still up and running as a result of both preventative and corrective maintenance.” Thanks for that input, Gordon!
Fred Langa has been writing about tech — and, specifically, about personal computing — for as long as there have been PCs. And he is one of the founding members of the original Windows Secrets newsletter. Check out Langa.com for all of Fred’s current projects. Best of the Lounge Is FTP really a thing of the past?
In the 2020-02-17 AskWoody Plus Newsletter article “RIP FTP: There’s a better way to share files,” Amy Babinchak states: “Microsoft finally got its OneDrive cloud-storage service right” — and hints this may be the final nail in FTP’s coffin. Some members of the AskWoody Lounge respectfully disagree, believing that the task of transferring files will never be a one-size-fits-all proposition and that FTP is still alive and well. Windows 10 1909 Lounger Wildstar was surprised to see “Remote Registry” enabled after upgrading from Windows Pro 1903 to 1909. It set off an alarm bell. However, as ominous as this might sound, it doesn’t mean that pending doom from malicious hackers might be forthcoming. Windows 10 Plus member John782 took the plunge and upgraded his older Toshiba Satellite from Win7 to Win10 1909. John describes the experience as relatively trouble-free. Fellow members chime in with their own stories of migrating up to the latest Windows. MVP Nathan Parker occasionally receives winmail.dat files on his Mac. But they don’t open, even in Outlook. Naturally, he turned to the forum, seeking help from the same members to whom he often provides advice. The needed how-to help was quick — and accompanied by an answer as to why this problem happens. Excel Lounger WSMartinM has a VBA routine used in Excel 2010 to show font colors. The problem? The test routine keeps returning an error message. With help from fellow Loungers and a small change in the script, WSMartinM is now coloring between the lines. Browsers Plus member Alex5723 provides a link to a story reporting that the Waterfox browser — a privacy-centric offshoot of Firefox — has been sold to a pay-per-click online advertising company. Readers respond with the usual “Oh, no!” and discuss the rise of Waterfox and where it’s heading now — along with what alternatives still remain. Windows10 After trying several “fixes” to get System Restore to create a restore point, Plus member WarningU2 turned to AskWoody readers for a solution. That led to a round of brief trial-and-error attempts. The solution? Change ownership at the administrator level. If you’re not already a Lounge member, use the quick registration form to sign up for free. SECURITY Conference showcases a tsunami of security products
If you needed proof that Web security has become a major industry, you need only to have walked the acres of booths at the RSA Conference 2020. More than 36,000 attendees, 704 speakers, and 658 exhibitors gathered at San Francisco’s Moscone Center this past February to explore the “Human Element” in cyber security. The conference included hundreds of keynotes, track sessions, tutorials, seminars, and special events. Protecting the Internet has become a veritable military-industrial complex. Some of the most interesting and timely topics included privacy, machine learning and artificial intelligence, policy and government, applied cryptology, and block chains. The vendors hawking hardware and software security solutions ranged from heavyweights such as Microsoft, Cisco, McAfee, and IBM to clusters of small players in phone booth–sized stalls. But no matter what their size, all exhibitors had a common mission of selling their wares to corporate IT professionals — not to end users. Nevertheless, some of that enterprise-security technology eventually trickles down to the rest of us. Thus, as one of the “human elements,” I explored the hundreds of booths to find security products that might more immediately apply to end users. One clearly prevalent theme from this year’s conference was the Internet’s growing impact on all economies. That, in turn, only increases the need for more-vigilant — but also consumer-friendly — security protocols and services. Two examples apply biometric security in quite different ways. Yubico‘s easy-to-use USB keys provide two-factor or passwordless authentication for both individuals and businesses. Nuance, on the other hand, adds security to corporate voice-recognition systems that we consumers frequently interact with. Security on your keyring
Two-factor authentication is now standard for securely signing in to our various online accounts. Even Facebook recommends using two forms of sign-in credentials. Let’s face it: with the many reports of corporate breaches, the chances are high that our passwords are floating around in multiple hacker databases. Currently, our smartphones are the most popular tool for second-factor authentication. Responding to a text message is quick and easy, and we have our phones close at hand — most of the time. But what if your phone is stolen or damaged? Or you no longer have access to the company phone that is the device of record? Two-factor sign-ins suddenly become a pain in the neck. Yubico offers a simple alternative that can be used with or without passwords. I first reviewed this company’s USB security dongle back in 2017 for Windows Secrets. At that time, the device came in only a couple of physical formats, and it worked with just a few selected online services. Its main authentication and cryptographic protocol was Universal 2nd Factor (U2F, more info) — which is still in use today, along with numerous other protocols such as FIDO, WebAuthn/FIDO2, and OpenPGP. Over the years, Yubico has expanded and enhanced its products. For example, the company’s thumbnail-size YubiKey 5 Series dongles now include the tiny USB-C Nano, the YubiKey 5 NFC with built-in near-field communication for mobile devices, and the YubiKey 5Ci that’s outfitted with both standard USB and Apple Lightning connectors. (See Figure 1.) Prices for these keys range from just USD $20 to $70.
(Not familiar with near-field communication [NFC; more info]? The most common applications are credit cards that can be simply “tapped” for retail payments, and the tap-and-go security ID cards for employees.) You don’t need any special software for using a Yubico key; they’re easily linked to any compatible website, application, or browser — of which there are now many. The devices are also battery-free. The initial setup is as simple as signing in to “www.yubico.com/start.” You then register the key with each application or online service it’ll secure. Yubico has an online catalog of supported services. Note that all required credentials are stored on the Yubico dongle. So it will work with multiple devices without any additional configuration. Dare I say it? Attached to our keyrings, the Yubico dongles are literally the key to our digital security. It has you at ‘Hello’ — voice authentication
Nuance (site) is a great name for a company whose forte is detecting the nuances in human voices. The company’s biometric solution goes well beyond the security options you’ll find in Windows 10 (i.e., fingerprints, facial recognition, and so forth). Instead, it specializes in enterprise solutions that provide authentication and fraud detection across interactive voice-response systems (IVR; more info). Early applications of IVR include call centers — as in those annoying voice-based call-routing systems. Today, think Amazon’s Alexa and other speech-centric technologies that detect, listen, and learn. You might be familiar with Nuance indirectly. Through a series of corporate acquisitions, Nuance Communications also owns Dragon Speech Recognition software, perhaps the most popular speech-to-text program for consumers and businesses. Nuance’s IVR systems are embedded in contact centers such as bank and airline customer-service operations, mobile apps, and the Web. The primary purpose of Nuance’s software is to detect who’s on the other end of a voice call; in other words, to determine whether the caller is actually who they say they are. Simply put, the end game is to catch phone-based acts of fraud. In a demo at the RSA Conference, I could see … er, hear … the three key features of the Nuance platform:
This algorithmic, conversational artificial intelligence is activated as soon as a phone call connects. It might detect who you are right at “Hello.” Even with a faked Caller ID number, cyber criminals are no longer guaranteed anonymity — and neither are legitimate callers. It might be an excellent application for “security,” but it could also be a case of “Say hello to Big Brother.”
Michael Lasky is a freelance writer based in Oakland, California. He has over 20 years of computer-magazine experience, most recently as senior editor at PC World. PATCH WATCH Win10 cumulative update gets an update. Don’t panic!
Even in the best of times, we almost always expect to get Windows-updating surprises. And these are far from normal times. Still, it was a bit shocking that two days after Microsoft released the expected March cumulative update for Windows 1903 and 1909, it released another cumulative patch. Posted March 12, KB 4551762 effectively replaces the original cumulative update KB 4540673. If you’ve delayed March patching, you’ll get only the newer version. The change-up applies only to Win10 Versions 1903 and 1909 plus Windows Server Core installations (which do not have the Windows GUI.) In other words, servers with a GUI are not impacted. So what does the new cumulative update actually do? It has only one change: a fix for Windows SMB 3.1.1, aka SMBv3. (Server Message Block is a networking protocol for shared files, printers, and other resources.) The flaw, CVE-2020-0796, could allow remote-code-execution exploits. Its description states: “To exploit the vulnerability against a server, an unauthenticated attacker could send a specially crafted packet to a targeted SMBv3 server. To exploit the vulnerability against a client, an unauthenticated attacker would need to configure a malicious SMBv3 server and convince a user to connect to it.” Reportedly, the SMBv3 bug does not impact Azure, Microsoft’s cloud platform. Also, if your Win10 1903 or 1909 workstations are connecting to an older Windows Server platform such as Server 2012 R2 (as I am at the office), you are running SMB 3.0.2, which is not vulnerable. In short, it all depends on what your workstations are linked to. (Tip: If you want to see what version of SMB your computer is using, enter “PowerShell” into the Windows search box and select “Run as Administrator.” In the blue box that opens up, type in Get-smbconnection and hit Enter. You might be surprised — I was. Turns out one of my home computers is connecting to a Western Digital My Cloud external hard drive using SMB 3.1.1 — whereas at the office, I am connecting to older SMB platforms.) Bottom line: I don’t see this as a serious threat to those of us with Windows 1903 and 1909 workstations. I’m more worried about the other updates out this month. Keep this in mind: The cumulative-update/rollup-update model bundles all security fixes into one patch. So you can’t opt to not install all updates. The current system is convenient, but it effectively hides just how many security issues are truly being patched. For example, included in this month’s Windows 7 ESU updates is a pile of fixes for remote-code-execution, elevation-of-privilege, information-disclosure, and tampering threats. (Many of these Win7 patches also impact Windows 10.) Here are the threats you could be facing if you don’t have Win7 ESU updates in place. It’s a very long list, but fortunately, there are only a few I’m really concerned about — mostly the “information-disclosure” exploits that can target random Web surfing. The good news is that none of the following has been used in active attacks — yet! Elevation of privilege: These vulnerabilities in Windows allow malicious hackers to acquire admin rights to targeted machines. However, in most cases, the attacker needs to sign in to a system, install a bogus application, and then trick a user into running the app. Typically, the highest risk is to large businesses — not to astute, and maybe a bit paranoid, AskWoody readers.
Information disclosure: In most cases, these vulnerabilities allow attackers to acquire information stored in a computer’s memory. That stolen information can then be combined with other exploits to thoroughly compromise a system. Typically, the malicious hacker has to trick users into opening a malicious file or going to an untrusted webpage. Anyone who surfs the Web indiscriminately is at greatest risk. It’s far safer to do your general Web activities on a Chromebook or smartphone. With the two exceptions noted below, all these vulnerabilities are in the Windows Graphics Device Interface (GDI) component.
Remote code execution: CVE-2020-0881 and CVE-2020-0883 are additional vulnerabilities in the Windows GDI. In both cases, the attacker must trick a legitimate user into opening a malicious file or website.
Tampering
Whew! That’s a huge list of Win7 bugs. My point is to show the potential exposure of using the Web with an out-of-date Win7 installation. Either sign up for Extended Security Updates or move to a supported OS. Again, although I’ve not seen reports of these threats being used in the wild or tagged in the Exploit database, using an unpatched machine will get only more dangerous. Malicious hackers love easy targets. March patching summary
I’ll be testing the Win10 replacement cumulative update KB 4551762. Given that it supersedes KB 4540673, I’ll likely recommend installing the newer update in a week or two. UPDATE: According to an AskWoody post, there are already reports of problems with KB 4551762. Note: On Win7 systems receiving ESUs, remember that you must install February’s servicing-stack update KB 4537829 before attempting to install the March patches. A warning to Win7 users and Server 2008 R2 admins planning to go without new patches (i.e., you’ve not signed up for extended support): There are in-the-wild attacks on SQL Server and on-premise Exchange. These systems are really vulnerable if they don’t have the February updates (more info). Moreover, in the public databases of freely available exploits, only a patched December bug is listed. What does that mean to you and me? Active exploits that appeared in February or March for Windows 7 can be difficult to track. That said, here’s what I think is a more immediate threat: COVID-19 scams and phishing, along with fake COVID-19 maps I see popping up on websites. Note that the AskWoody site has a special section where you can ask questions about COVID-19 cons. I’m also concerned about small businesses struggling to quickly set up secure remote access. I suggest you read CIS Controls’ article “Telework and Small Office Network Security Guide” before making any decisions on significantly reconfiguring your network.
Windows 10
Servicing-stack updates Cumulative updates
.NET Framework Microsoft has not released March .NET Framework updates at this time. Stay tuned. Windows 8.1/Server 2012 R2
Windows 7/Server 2008 R2 SP1
Extended Security Updates (ESU) reminder: Be sure to install KB 4538483 from the Microsoft Update Catalog download site before attempting to add new security fixes. If you do not have this February servicing-stack patch, you won’t see March’s updates. Also be sure to install March servicing-stack update KB 4550735 to prepare your machine for April’s fixes. Server 2012
Windows Server 2008 SP2
Office security and non-security updates
March’s Office security updates fix a remote-code-execution vulnerability. As usual, defer these updates until we give the all-clear. Office 2016
Office 2013 SP1
Office 2010 SP2 The following Office non-security enhancements and fixes were released March 3 and 10. Office 2016
Office 2013 and 2010 There’s one update for Skype.
These days, more than ever, stay safe out there.
In real life, Susan Bradley is a Microsoft Security MVP and IT wrangler at a California accounting firm, where she manages a fleet of servers, virtual machines, workstations, iPhones, and other digital devices. She also does forensic investigations of computer systems for the firm. Apple Mac Switchers: Taking a bite of the Apple – Part 2
By Nathan Parker With the end of free support for Windows 7, some users are weighing whether it might be a good time to jump to Apple’s Mac. If you’re thinking about making the switch but are new to Apple, we’ve provided a two-part quick guide to the Mac environment. In Part 1 (2020-03-09 AskWoody Plus Newsletter) we discussed the various types of Mac desktops and notebooks. We also included an overview on setting up a new Mac. In Part 2, we’ll examine the macOS desktop, provide a brief description of the Mac keyboard, and discuss system backup and security. As noted in Part 1, this series is a condensed version of an AskWoody post. Look online for more details about all things Mac. Touring the Mac’s user interface
Apple desktops and notebooks all come with the macOS operating system — known until recently as OS X. Once you get past some labeling differences, many aspects of macOS will feel familiar to Windows users. For example, Windows’ File Explorer becomes Apple’s Finder. And just like Explorer, Finder has lists of files and folders and other easily recognizable navigation tools. To help with the transition, Apple offers some handy online tips for Windows-to-Mac switchers. Also, check out the “What’s it called on my Mac” article. Here is a very brief tour of the macOS user experience, as it compares to Windows:
Mac’s keyboard peculiarities
With a few exceptions, Mac and Windows keyboards are quite similar. (Even Windows keyboards vary from model to model.) What might trip you up initially are two modifier keys: Command and Option. Of the two, you’ll use Command extensively for keyboard shortcuts. Think of it as simply a renamed Windows Ctrl key. (Which is why Apple came up with the phrase “Lose Control, gain Command.”) So instead of pressing Ctrl + C to copy, you press Command + C; Ctrl + V becomes Command + V (paste); and so forth. The Alt key on Windows is also known as the Option key on the Mac. Apple has published an extensive list of keyboard shortcuts. As long as you remember to substitute the Command key for Ctrl, you’ll quickly pick up the most important ones (Cut, Copy, Paste, Undo, Find, and so on). On Mac notebooks, the trackpad works much as Windows users would expect. It’s actually one of the most comfortable and responsive trackpads you’re likely to work with. But you’ll also want to learn its gestures for quick zooming, scrolling, right-clicking, and more. Newer Macs with Magic Trackpads also support Apple’s Force Touch, first introduced on iPhones. For the uninitiated, this feature allows additional gesture controls when you press down harder on the trackpad. (We suspect that many iPhone users still don’t understand it.) Backing up and securing the new system
When you purchase your new Mac, I strongly suggest also buying a 2TB USB-connected hard drive for storing backups. There are many to choose from for under USD $70. In macOS, backups are handled by the included Time Machine app. It’s easy to set up and largely automatic. The app lets you exclude specific files and folders from the backup process. For example, you can avoid the redundancy for archiving data on the external drive and in the cloud — i.e., iCloud, Dropbox, OneDrive, etc. (On the other hand, you might like that additional data security.) While an external drive is easiest to set up, you can also store archived data to network-attached storage or even another Mac. And if the machine has a major OS failure, you can boot up from the Time Machine drive. For other options, please see my Mac Security article. Other security tools include the built-in firewall (more info) and FileVault, macOS’s full-system encryption. Both are found under System Preferences/Security & Privacy. (On a new machine, you’ll want to ensure that the firewall is turned on.) An Apple info page has a good overview on Mac security. For a deeper dive into the topic, see my Mac Security articles on firmware and Wi-Fi security. It’s also a good idea to check for macOS updates shortly after setting up a new Mac. It will ensure that you have the latest security fixes. (No, Macs are not immune to malware.) You can also configure your system to automatically install new patches. I keep an ongoing list of Apple updates on the AskWoody forum — think of it as a Mac-focused Patch Watch. macOS includes a built-in password manager: Keychain. Saved user names and passwords can be shared with other Apple devices through iCloud. Note that I also use the third-party password manager 1Password because it offers additional features and works with non-Apple web browsers. For Macs that support them, setting up Touch ID and Apple Pay help increase sign-in security — and makes it easier to pay for online purchases. Finally, you’ll want to review macOS’s suite of privacy features. Two computing worlds — with a lot of overlap
Transitioning from Windows to Mac is a bit like moving to a different make or model of car. The basic controls may have other names and be in different places, but they mostly do the same things you’re used to. (Now where did they put that ignition-key slot?) Again, you’ll find more on all things Apple … on AskWoody! To start, check out the macOS forum.
Nathan Parker has been using Apple devices since 2006, when he purchased a PowerBook G4 running Mac OS X Tiger. He has worked in various IT consulting roles and is currently an IT Consultant for Earth Networks (formerly WeatherBug). In addition to his contributions on AskWoody, Nathan also blogs weather updates at WeatherTogether. And he’s working on his PhD. Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com). Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners. Your email subscription:
Copyright © 2020 AskWoody LLC, All rights reserved. |



 By Michael Lasky
By Michael Lasky
 By Susan Bradley
By Susan Bradley What to do: You’ve probably got enough on your mind without worrying about threats to Windows. Defer updating for now. I’ll report back toward the end of this month.(See our online
What to do: You’ve probably got enough on your mind without worrying about threats to Windows. Defer updating for now. I’ll report back toward the end of this month.(See our online