
|
Patch reliability is unclear. Unless you have an immediate, pressing need to install a specific patch, don't do it. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
Free first aid for a wide range of Windows ills
In this issue
- LANGALIST PLUS: What to do when Windows Update fails
- TOP STORY: Free first aid for a wide range of Windows ills
- LOUNGE LIFE: Protecting passwords on multiple devices
- ON SECURITY: Ways to encrypt sensitive data in Windows
- WACKY WEB WEEK: Versatile Finnish cover band also plays hockey
- PATCH WATCH: No summer break from MS Office updates
What to do when Windows Update fails
Update problems can leave your PC vulnerable to hackers, malware, and other security threats. Here’s how to overcome Windows Update failures.
Plus: How to remove Windows 8 from a Win7/8 dual boot; why OneDrive should not be your only backup mechanism; and a new, free, small-footprint OS.
How to reset and restart Windows Update
John Mitzi’s Windows-based updating system has failed, leaving him unable to install the new patches needed to keep his system safe from emerging security threats.
- “My Windows Update isn’t working. Is it possible to uninstall this application and reinstall it?
“So far, I’ve been unable to fix this problem. Any suggestions?”
Windows Update is a critical component of the Windows OS; it can’t be uninstalled, but it can be repaired — usually quite easily!
Sorting out Windows Update’s many possible failure points used to be a major hassle, involving some deep spelunking techniques such as resetting the local Update database, stopping and restarting the patch engine, killing and restarting hung Background Intelligent Transfer Service (BITS; info) downloads, and so on.
Happily, those days are mostly done. Microsoft now offers an impressive range of Update-specific repair tools that can correct most problems.
In addition to the automatic tools, Microsoft also details several manual repair methods for those rare (one hopes) instances where the point-and-click fixes don’t work.
Here’s what to do when you have Windows Update trouble:
Start by running a thorough and deep malware scan. Some types of viruses can actually disable Windows Update.
Next, browse to Microsoft Support document 971058, “How do I reset Windows Update components?” — it offers two fully automated fixit tools, one for Win8/7 and another for Vista and XP. It also includes instructions for manually resetting Windows Update.
(Note: The fixits included in KB 971058 are examples of automated repair tools that are not easily found in Microsoft’s Fix It Solution Center. See this week’s Top Story for more information.)
If the fixit doesn’t work, try the automated and manual repairs offered on the “Fix Microsoft Windows Update issues” page, which can resolve still more problems with Win8, Win7, and Vista.
Still no luck? Try the “Troubleshoot problems with installing updates” pages for Win8, Win7, and Vista. These pages have some overlap with the aforementioned sites, but they’re still worth a visit if Windows Update is resisting repair.
Finally, Windows 7 users can try the Win7-specific Windows Update Troubleshooter (download link).
One of these automated or manual options mentioned above should be able to correct just about any problem with Windows Update — and get your system fully up to date again!
Removing Win8 from a dual-boot Win7/Win8 system
Reader Keith Irvin is looking for the exact opposite of what I covered in the April 23 LangaList Plus column, “Remove Windows 7 from a Win7/8, dual-boot PC.”
Rather than removing Win7, he wants to remove Windows 8 and return his PC to a wholly Windows 7 system.
- “I’m looking down the road toward Windows 10. I have a standard Win7/Win8.1 dual-boot machine that has worked fine for a long time. Win8.1 now fails to boot — I don’t care, I don’t need it and there’s nothing on it to save. When Win10 becomes available I’d like to replace Win8.1 with Win10.
“More specifically, I’d like to wipe Win8.1’s partition to make room for Win10, and dual-boot it with my current Win7. How would you go about this? Should I fix Win8.1 first? Delete the Win8.1 partition — and if I do, will the boot loader still launch Win7?”
You’re in luck, Keith. That’s a surprisingly easy task. You should be able to remove Win8 from your dual-boot setup in just a couple of minutes, using only tools built into Windows tools.
Of course, before you begin, the standard precautions apply. Make sure your current setup is fully backed up. Also, because you’re about to wipe out the Win8 installation, take a moment to confirm that your Win7 setup is fully functional.
When you’re ready, here’s how to remove Win8 with just a few clicks.
- Boot normally to Windows 7.
- In an admin-level account, open the start menu and enter msconfig in the Search programs and files box. Press Enter; the System Configuration tool will open.
- Click the Boot tab and then select Windows 7 in the list of installed operating systems.
- Click the Set as default button, then click Apply.
- Select the Windows 8 listing and click the Delete button. Click Apply.
- Close the dialog box by clicking OK.
- You’ll now be prompted to reboot. You can do that now or later — it’s your choice.
That’s all it takes to disable Win8! Your PC is now single-boot, with Win7 as the only active OS.
You can use the partition-management tool of your choice to recover the space used by the now-inert Win8 setup. Win7’s built-in disk management tool is fully up to the task; just launch diskmgmt.msc from the start menu’s search box. In the Disk Management tool, select the Win8 partition and delete it.
You can leave the deleted partition as unallocated space — in anticipation of reusing it when Win10 becomes available — or use the extend command to merge the space with an adjacent partition.
See? Quick and easy!
Is it okay to use OneDrive for all backups?
Kevin Lemke currently uses Win8’s built-in tool for backups but wonders about using OneDrive instead.
- “Fred, thanks for your recent article, “Mastering Windows 8’s backup/restore system” [Jan. 15 Top Story).
“I currently use Win8’s File History and custom images for my backups. However, I’d rather back up my files to OneDrive. Is there an easy way to have the files use OneDrive as an online backup?” (I’ve never used OneDrive.)
Yes, you can use OneDrive as your sole backup — but I don’t recommend doing so. I’ll explain why in a moment. But here’s how you’d do it, if you still want to.
Simply put, you move whatever folders you want OneDrive to back up into the OneDrive folder on your hard drive. For example, you could move your entire Documents folder and all its subfolders to C:\Users\{username}\OneDrive\Documents (or, on some systems, to C:\Users\{username}\SkyDrive\Documents).
You can then use the relocated Documents folder as you always have, just as if it were in its original location. Any files you save, alter, or create within the OneDrive\Documents folder will be automatically synched to your online OneDrive account in the cloud.
That might sound secure, but here’s why it’s a bad idea. Your OneDrive account will always contain a single copy of your files — the most recent version. Currently, you can’t use OneDrive to roll back all types of files to earlier versions. (Many third-party services such as Dropbox support versioning for all file types; OneDrive currently supports a form of versioning only for Office files.)
So for the most part, if you inadvertently save a bad version of a file (say, one with errors), that’s all you’ll end up with — you’ll have the same bad file on your hard drive and in the cloud. You’d have no way to recover a previous, better version.
In contrast, File History saves multiple versions of all personal files and lets you easily roll back to a good version and pick up from where you left off.
File History and OneDrive actually work best together. You can use File History to create incremental, versioned, local backups, and OneDrive to provide safe, offsite storage for selected copies of your most important files.
If you set up and use File History and OneDrive as described in the “Mastering Windows 8’s backup/restore system” article, you’ll automatically save your files to three separate locations: a current copy on the primary data drive, a current copy in the OneDrive cloud, and multiple previous versions on the external File History drive — all in near-real time. This virtually guarantees that you’ll never lose an important file again!
My recommendation to you: Use the Win8 backup pieces together, as they’re designed to work. Don’t try to force OneDrive into a role it’s not particularly well-suited for.
A new OS that’s small, free, and complete
MenuetOS is a technical tour-de-force — a wholly new OS that’s coded from the ground up in pure assembly language. It looks and acts like Windows or Linux, but it’s astonishingly compact. The complete download is around 845KB — yes, that’s kilobytes, not megabytes or gigabytes. The OS and the apps it ships with can fit onto a single floppy disk, should someone still use floppies.
The Menuet site describes it this way:
“MenuetOS is a pre-emptive, real-time, and multiprocessor operating system in development for the PC written entirely in 32/64-bit assembly language. Menuet64 is released under license and Menuet32 under GPL. Menuet supports 32/64-bit, x86 assembly programming for smaller, faster, and less resource hungry applications.”
Available free at the above site, the Menuet package includes the base OS plus 3DS Viewer, midi player; FTP client and server, HTTPS client, draw tool, and several games.
To try the OS, I downloaded a compressed floppy image, available as an 845KB ZIP file or Windows-based, .exe floppy-disk writer. I then extracted the image — M6410000.img — and set up a generic VirtualBox VPC.
I used VirtualBox’s Storage menu to add a virtual floppy controller to the new VPC; I then added a virtual floppy drive to the new controller. Its dialog box has a “Choose disk” option, which I selected, pointing VirtualBox to the uncompressed floppy .img file. I also opened the virtual PC’s System settings and ensured that “Floppy drive” was first in the boot order.
(If you have trouble setting up a VPC to boot from a floppy image, eHow.com details an alternate method. VirtualBox help files also cover the topic in more technical detail.)
Figure 1 shows what appeared.
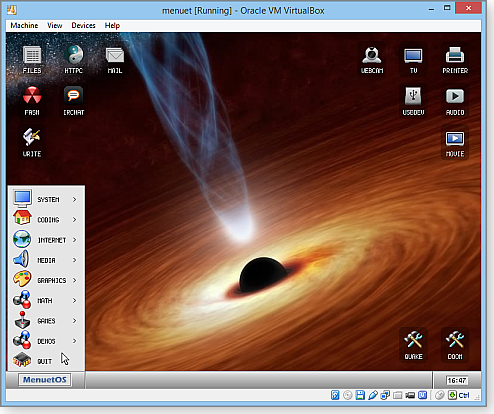
Figure 1. MenuetOS running in a virtual machine from its 1.44MB floppy-disk image.
As of this writing, Menuet is only at version 1.1, so there’s not a lot of third-party support for it. I found some free games and a separately licensed media player (a TV tuner plus MP3/DVD player) that costs $11.
Whether or not you have a practical use for Menuet, it’s a fabulous example of assembly-language expertise — interesting and fun to see in itself, and quite a counterpoint to the gigabyte-scale bloat of the mainstream Windows, Linux, and Apple OSes!
Free first aid for a wide range of Windows ills
Did you know that Microsoft offers over 500 automated, online solutions for common problems you might encounter with Windows software and hardware?
And that’s on top of the dozens of always-available troubleshooting tools built into Windows 7 and Windows 8.
I’m sure most Windows users are unaware of the breadth and depth of fix-it apps and troubleshooters available for free from Microsoft. As the LangaList Plus columnist, I thought I was on top of that topic. But even I had no idea that there are now over 500 solutions at our fingertips. Wow!
These extremely useful tools can provide 24/7 self-help fixes for problems with printing, audio, security, and networking along with many other hardware and software issues.
But (there’s always a “but”) not all fix-its and troubleshooters are easily found. In fact, following Microsoft’s system for searching for help can sometimes lead to dead ends, wrong answers, or missed solutions!
The information that follows will help you find the automated repair/diagnostic tools you need. Use it as a quick reference for what’s available, how Microsoft organizes its tools, and the best way to search for the solution to a particular problem. So let’s get started.
Under the covers: Microsoft’s SDP and MATS
Fix-its and troubleshooters are user-friendly implementations of two advanced Microsoft technologies: the Support Diagnostics Platform (SDP) and the Microsoft Automated Troubleshooting Service (MATS).
SDP is a mechanism to collect diagnostic information such as Registry data, configuration files, and application event logs. MATS can analyze SDP data to see whether the conditions fit a known pattern — and if so, suggest or implement automated repairs that are likely to resolve the detected problem. (Want more details? See the MS Support article 2598970, “Information about Microsoft Automated Troubleshooting Services and Support Diagnostic Platform.”)
In their native form, MATS and SDP services are aimed at programmers and IT/PC professionals. They’re offered via Microsoft Diagnostic Services, described in MS Support article 2672837, “Microsoft Diagnostics Services — Self-help diagnostic portal.” You can access the SDP/MATS tools for free on the Support Diagnostics sign-in page; your Microsoft Live ID and password will let you in.
For most individual PC users, those pro-level MATS/SDP offerings are overkill. So instead, I’ll focus on Microsoft’s far-easier-to-use — but still highly effective — automated fix-it and troubleshooter tools.
Start with Microsoft’s fix-it library
Microsoft has collected most of its fix-it solutions in the Fix it Solution Center site. It’s available to all — no Microsoft sign-in required.
The site’s deceptively simple homepage (see Figure 1) is in fact the portal to some 500 solutions, accessed by simply pointing and clicking.

Figure 1. The online Fix it Solution Center is the front end for fixes for hundreds of common PC problems.
The page is divided into three sections, which Microsoft clearly wants you to step though in a 1-2-3 order. I actually disagree with this approach, and I’ll explain why later. But for now, here’s what Microsoft has in mind:
- Step 1: Select a problem area.
Choose from the six major application categories the one that’s closest to what’s causing trouble. They include Windows, Internet Explorer, Windows Media Player, Entertainment (which includes Xbox, Zune, and — oddly — Windows Phone), and Office (including Project, InfoPath, and Live Meeting). There’s also “Other,” a catch-all category that includes Streets and Trips, Windows Server, SQL Server, Forefront, Dynamics, SharePoint, and other enterprise/server products.
A seventh category — Top Solutions — is a shortcut to the most common fix-its and troubleshooters from the other six categories.
- Step 2: What are you trying to do?
This section attempts to narrow your search by listing specific kinds of trouble. Depending on what you chose in Step 1, you’ll get anywhere from one to eight Step 2 subchoices. In some cases, a second submenu of additional choices will appear, offering up to eight or so more options.
- Step 3: View or run solutions.
After Step 2 has been completed, suggested solutions — such as a click-to-run fix-it or related information — appear in the Step 3 text box. Fix-its are accompanied by a Run Now button, which is a little misleading: Clicking the button doesn’t run the selected fix-it but instead downloads the fix-it file (usually, an .exe) to your PC. You then navigate to the file on your hard drive and click to run it.
Microsoft’s three-step method seems straightforward and might work for inexperienced users — anyone who enters the site with little or no clue as to why their system is malfunctioning or what might need to be fixed.
However, that 1-2-3–step process has led me down blind alleys, causing me to miss the correct solution.
If you already have at least a general idea of what the trouble is, or what the needed repair is, you can often do much better with a more direct approach.
A better way to search for solutions
I use an example to show how different paths don’t necessarily lead to the desired solution.
Let’s say you’re trying to remove an old or malfunctioning program, but it simply won’t uninstall properly. Perhaps you get an error message when you run the program’s normal uninstaller, or maybe data is left behind on the hard drive or in the Registry — data that makes your system think that the software is still present on your system.
You could work this problem three ways — I’ll start with the one-step, direct-search method I recommend:
- Skip Microsoft’s Steps 1 and 2 and go directly to Step 3. Type “uninstall” into the Filter Solutions box and then press Enter; the listing “Fix problems that programs cannot be installed or uninstalled” immediately appears along with a “Run Now” fix-it. (See Figure 2.) That’s all it takes: You get the correct solution in one quick step.

Figure 2. A good keyword in Step 3's Filter Solutions search box (highlighted) can let you zero in on the correct solution in one step.
Microsoft’s recommended three-step process is a lot less straightforward. It involves more clicks and some guesswork — and produces far less certain results. See for yourself!
Microsoft’s three-step method, option 1:
- In Step 1, select Top Solutions.
- In Step 2, look for anything related to uninstalls. (Spoiler alert: Nothing will be listed.)
- Still in Step 2, select the only thing listed that mentions installations at all: “Install or upgrade hardware or software.”
- Start reading the proposed solutions listed in Step 3. The top-recommended fix-it is for Zune — clearly not what you’re looking for.
Keep reading. You’ll find solutions for printers, CD/DVD drives, USB, undetected hardware devices, audio recording problems, audio playback problems, and the rest. Somewhere among the incorrect solutions (it’s the eighth-listed choice on my system), you’ll find the correct “Fix problems that programs cannot be installed or uninstalled.”
Microsoft’s method, option 2:
- In Step 1, Select Windows. (No, the uninstall problem isn’t really with Windows itself, but that’s the closest Step 1 item that might apply.)
- In Step 2, look for anything related to uninstalls. Again, nothing will be listed.
- Still in Step 2, select the only thing listed that mentions installations at all: “Install or upgrade hardware or software.” A new selection box will open.
- In the new selection box, find the closest match to an uninstallation problem: “Install or remove programs.”
- In Step 3, the correct “Fix problems that programs cannot be installed or uninstalled” should appear — at the top of a list of 19 incorrect items.
You can see why I prefer the one-step, direct-search method. If you have a reasonably good idea of what the trouble is, you can likely zero in on the correct fix-it faster and more surely simply by entering one or more good keywords in the “Filter solutions” text box.
Running Windows’ built-in troubleshooters
Some problems are common enough that Microsoft built the relevant fix-it right into Windows itself — there’s no need to go online. Microsoft calls the built-in fix-its “Troubleshooters.”
Built-in troubleshooters aren’t just handy, they could be vital if a problem prevents the PC from going online. (Obviously, a Web-based fix-it is of no use at all if you can’t access it.)
Windows 8 and Windows 7 each have about 30 troubleshooters built in; Vista, alas, has but one.
You can see available troubleshooters by opening Control Panel and typing the word “troubleshoot” into the search box — the category list Troubleshooting will appear. You can then open each subcategory to drill down to the individual troubleshooters.
Figure 3 shows the Win7 Troubleshooter category list. Win8’s is very similar.
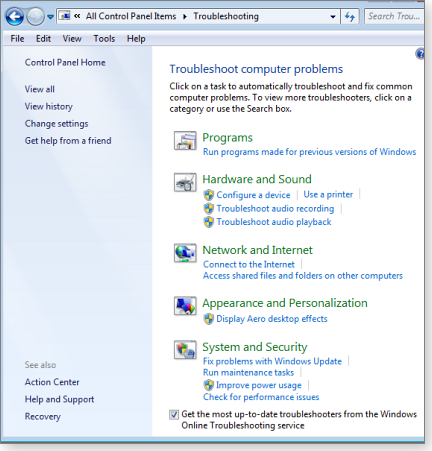
Figure 3. Each troubleshooting category can be opened to reveal the specific troubleshooters inside.
When you find an appropriate troubleshooter, just click to run it.
When local and online solutions don’t work
Combined, the local troubleshooters and the online Solution Center offer hundreds of solutions — but, oddly, not all of the automated solutions are offered by Microsoft. Sometimes, you have to search elsewhere.
For example, let’s say you’ve made some networking changes to a Win7 system. Suddenly, all the network connections — including the Home (local) network — are now stuck in the limited “Public” mode, which is preventing you from properly sharing files and devices. Surprisingly, it’s not a rare problem at all, as noted in the May 12, 2011, LangaList Plus item, “The ‘Make all future networks public’ debacle.”
None of the built-in networking troubleshooters addresses this problem. And strangely, the online Solution Center yields a response of “No matching results,” regardless of whether you use Microsoft’s three-step search or go straight to Step 3 and directly enter appropriate keywords — such as “stuck public connection,” “stuck public network,” “change public network,” “change network connection type,” “stuck connection,” and so on.
But there is an excellent, fully automated solution: Microsoft fix-it 50725, described in and accessed by MS Support article 2578723, “Windows 7 Network connections are stuck in Public mode.”
Although the Solution Center can’t find that particular fix-it, a general Web search can. For example, entering the same keywords — e.g., “stuck public network” — into Google or Bing yields a listing for KB 2578723/fix-it 50725 within the first few search results. In fact, Google usually lists the correct Support article and fix-it as the very first result.
(For another example of a fix-it that’s not easily found via the Solution Center, see this issue’s LangaList Plus column. [Paid content])
So don’t give up if your initial searches of Troubleshooters and the Solution Center come up dry. Your favorite search engine might help you find additional automated repair tools that Microsoft didn’t include in those two resources.
Three options can save untold frustration
Putting all the preceding information and methods together suggests an easy, three-step approach to solving common Windows problems.
- First: Check out the Troubleshooters built into your copy of Windows.
- Second: If a local troubleshooter isn’t available or didn’t help, check out the Fix it Solution Center site. Start with my direct-search method for the surest results.
- Third: If you still can’t find a solution, expand your search via Google, Bing, or other preferred search engine.
With hundreds of automated and semi-automated repair tools available, odds are you’ll find one that will give you the kind of fast and almost effortless self-help “first aid” that your malfunctioning Windows needs!
Protecting passwords on multiple devices
Lounge member Trev has used KeePass happily for years on his Windows PC.
These days, he’s branched out into other devices, so he asks Loungers in the Non-Microsoft OSes forum to recommend a KeePass-compatible app for his Android tools.
They come through — in detail. You’ll be well advised to read the research.
The following links are this week’s most interesting Lounge threads, including several new questions for which you might have answers:
 starred posts: particularly useful
starred posts: particularly useful
If you’re not already a Lounge member, use the quick registration form to sign up for free. The ability to post comments and take advantage of other Lounge features is available only to registered members.
If you’re already registered, you can jump right into today’s discussions in the Lounge.
Ways to encrypt sensitive data in Windows
We all have something to hide. No, not those embarrassing party photos; I’m talking about sensitive documents such as medical records, financial statements, work files, and so forth. (Okay, and maybe those embarrassing photos, too.)
Encryption is the best way to protect important data from those who might do us harm. Here’s a rundown of encryption options.
If you think that your Windows sign-in password is going to protect you from data thieves, you’re sadly mistaken. In most cases, it’s relatively easy to read what’s on a hard drive that’s been stolen or compromised by malware — especially if your primary system is a notebook or some other mobile device.
Theft aside, our privacy is at stake. Who doesn’t have information that we’d just rather not reveal to co-workers, friends, or family members? And it’s not just the primary files on our hard drive we need to worry about. Protecting our data extends to backups and cloud storage.
Encryption is the only way to truly secure sensitive personal and work files. At the bare minimum, you should encrypt anything that might prove useful to identity thieves. Files that contain your bank-account number, credit-card number, social-security number, and similar information need to be encrypted. Whatever else you want kept secret is up to you — or possibly up to the people who pay you.
I’m going to discuss four approaches to encryption and suggest software for each.
Note: Encryption can protect you only if you use a secure password. Make sure your passwords are long and difficult to guess. And don’t lose your password — or all your secure data will be permanently secure from you, too.
Tools for encrypting a small number of files
If your life is simple, you probably have relatively few sensitive files that need protection from theft or from data snoops. These can be encrypted individually; the process is fast and simple. But it has limitations.
One tool readily at hand is Windows’ built-in Encrypting File System (EFS). Built into professional versions of Windows, it’s easy to set up: simply right-click a file, multiple files, or a folder; select Properties. Then click the Advanced button at the bottom of the General tab. In the Advanced Attributes dialog box, enable “Encrypt contents to secure data” (see Figure 1). Encrypted file/folder names are shown in green text.
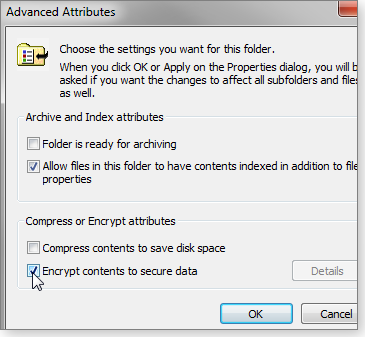
Figure 1. Windows' built-in file/folder encryption system, EFS, is quick and easy to apply.
If you encrypt a folder in this way, any files you create in — or drag to — this folder will be encrypted automatically.
EFS’s apparent simplicity is also its drawback. You gain access to EFS-protected data when you sign in to Windows with your regular password. The encryption/decryption keys are kept in an encryption certificate stored by Windows. If that certificate is damaged, you’ll no longer have access to your EFS-protected data. For that reason, it’s strongly recommended that you back up the certificate or create a recovery certificate (more info).
EFS recommends that you not encrypt specific files but instead encrypt the enclosing folder or folders. It does so because opening an encrypted file creates a temporary and unencrypted file in the same folder. If that temporary file is left in an unencrypted folder, it’s accessible by anyone.
To my mind, all that makes this form of protection beyond the comfort zone of an average Windows user. I think it makes sense only in an office environment with a professional IT staff to offer assistance.
For personal use, the more user-friendly and flexible option is the free and extremely popular compression program 7-Zip (site), which has been mentioned many times in Windows Secrets. Like most compression programs (and unlike Windows’ built-in compression tool), 7-Zip supports highly secure AES-256 encryption for classic .zip. (7-Zip can also be used to compress files without encryption.)
7-Zip also supports AES-256 encryption for its own highly efficient .7z compression format. (For backward compatibility, 7-Zip also supports the ancient and insecure ZipCrypto encryption method, but I don’t recommend using it for new archives.) Unlike a .zip file, .7z can hide the names of files inside an encrypted archive.
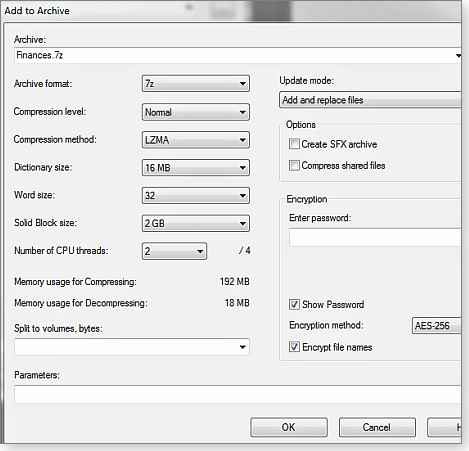
Figure 2. 7-Zip combines compression with strong file/folder encryption.
7-Zip is a bit cumbersome if you simply click a file to open it. You’ll have to either open 7-Zip’s File Manager (Figure 3) or extract the file and then re-zip it when you’re done making changes. If you’re regularly working with .7z compressed/encrypted files, it’s easier to simply work within File Manager. When you’re done with a file, it will be automatically re-encrypted.

Figure 3. The easiest way to work with .7z-encrypted files is through the 7-Zip File Manager application.
Note that by default, 7-Zip does create unencrypted temporary files (as do many other encryption products). For example, when you edit a document in Word, 7-Zip creates an unencrypted copy of the encrypted file. When you close the file, the temporary file overwrites the original encrypted version. It’s possible that those temporary files might not be removed when a file is re-encrypted. A good temp-file cleaner can help reduce this problem.
What’s more, 7-Zip hasn’t been updated since 2010 — too long a time for security software. That said, AES-256 encryption is still current and considered very secure. (A new version is currently in beta.)
Encryption vaults: TrueCrypt and its offspring
To my mind, this is the best way to protect your sensitive files. Encryption vaults (or “containers”) emulate drives, so any temporary files will almost certainly end up encrypted. Vaults also avoid the complexities (described below) of an encrypted drive or partition.
When not in use, an encrypted vault is just a big file that no one can read. (You set the vault’s size when you create it.) When you mount a vault with your password, Windows sees it as a standard drive or partition — with a drive letter. You can use files in an open vault just as you would if they were in your Documents folder. When you’re done with the file in the vault/drive, close the vault and the “drive” disappears.
At one time, the most popular vault system was TrueCrypt (site), a much-beloved, open-source, and free encryption program that suddenly closed up shop, as reported in the June 12, 2014, Top Story, “The life and untimely demise of TrueCrypt.” There was some concern about TrueCrypt because it had not been updated in a while.
Oddly, at the time that TrueCrypt’s anonymous developers abandoned the program, the code was going through a rigorous technical audit. This past April, the audit was completed and TrueCrypt was deemed still reasonably safe. Matthew Green, one of the auditors, reported in a blog post that “TrueCrypt appears to be a relatively well designed piece of crypto software. The NCC audit found no evidence of deliberate backdoors or any severe design flaws that will make the software insecure in most instances.” Instead, they found minor flaws that in extreme and unusual cases could have compromised security.
TrueCrypt’s code is still available — officially, so that users can access encrypted vaults and migrate data to other encryption applications. Some developers are trying to resurrect TrueCrypt (site), while others have created TrueCrypt derivatives (called forks).
One of these, VeraCrypt (site; Figure 4), is now my new favorite encryption tool. Unlike TrueCrypt, we know who made — and continues to update — VeraCrypt: French IT security consultant Mounir Idrassi.
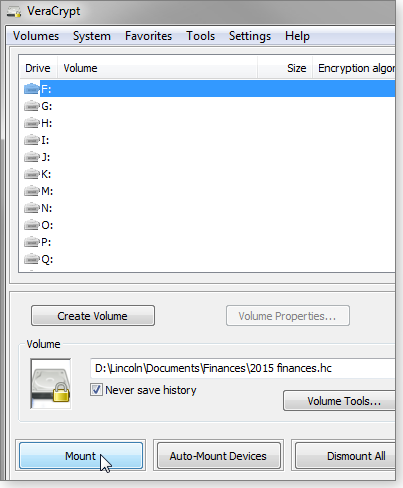
Figure 4. When VeraCrypt mounts an encrypted container, it's assigned a standard Windows drive letter.
VeraCrypt is probably more secure than TrueCrypt. Idrassi made changes that should add greater protection against brute-force attacks. Moreover, VeraCrypt includes some handy features borrowed from TrueCrypt. For instance, you can hide one vault inside another. The downside: Opening a VeraCrypt container can take longer than opening one in TrueCrypt.
Another TrueCrypt fork — CipherShed (site) — is currently in pre-alpha.
Since the vault/container is just a file, it’s as easily backed up as any other file (assuming you’re backing up as you should). Your backup program doesn’t have to support your encryption program. And since the file is encrypted, the backup is encrypted as well.
Add encryption to an entire data partition
If you have large collections of sensitive data that you access frequently, another option is to encrypt an entire drive or partition. It works best if you’ve placed your system files (Windows, etc.) and data on separate drives or partitions (more info).
If you’re using Win7 Ultimate, Win7 Enterprise, Win8 Pro, or Win8 Enterprise, you can use the built-in BitLocker tool. Just right-click the drive you want to encrypt and select “Turn on BitLocker.”
As with the file/folder-based EFS, BitLocker works best in an office environment, where the IT staff keeps careful records of where the keys are kept and the worker bees don’t need to know what the word encryption means. For more on BitLocker, see the MS TechNet page, “BitLocker drive encryption in Windows 7: Frequently asked questions.”
The other option is to use VeraCrypt — as long as you’re not encrypting a system drive or partition. Start as if you were creating a regular VeraCrypt vault, but on the first page of the Volume Creation Wizard, select Encrypt a non-system partition/drive (Figure 5). From this point on, everything should be obvious.
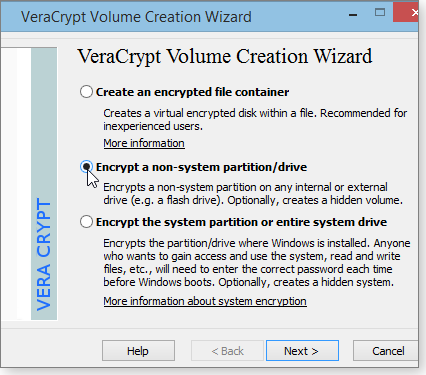
Figure 5. VeraCrypt can encrypt an entire drive or partition — as long as it doesn't contain Windows or other system files.
Note: Be careful what you pick on the wizard’s Volume Creation Mode page. If you already have files on the partition you want to encrypt, be sure to select Encrypt partition in place. The transition will take hours, but your files will be there when it’s done.
After the transition, your data partition will appear to be useless. Try to open it via Explorer, and you’ll be told you need to format the disk. Do not format that disk! Instead, open VeraCrypt and click Auto-Mount Devices (Figure 6). You’ll be asked to enter your password and open the encrypted partition; it will then be assigned an unused drive letter.
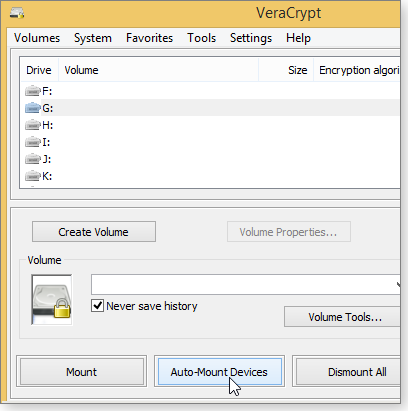
Figure 6. Use VeraCrypt's Auto-Mount Devices option to open an encrypted data partition
Note: In theory, a vault’s unencrypted files live only in system memory. But theory isn’t reality. Bits of your sensitive files can turn up in a swap file and other places. It’s extremely unlikely that a criminal will have the time and skills to recover this data — if it even exists — but it’s a possibility.
Finally, encrypt the whole dang thing
If every sector of every drive is encrypted, there’s no possible way that a stray remnant of a file could be accessed by a thief or a data snoop. But I doubt that anybody not on the NSA’s short list needs to worry about going this far.
Encrypting a system has its own issues, including boot problems and data-recovery complications. In a recent article, I recommended keeping encrypted stuff encrypted while you’re on a public network. But that’s impossible if everything is encrypted. I once bricked a PC while testing a full-drive encryption program. (I didn’t recommend that program.)
If you feel that you absolutely must do this, go with Windows’ BitLocker. If your version of Windows doesn’t support BitLocker, upgrade to one that does.
VeraCrypt might be safe if your drive tracks partitions with the old master boot record (MBR) technology, but I’m not confident enough to recommend it. VeraCrypt, wisely, refuses to encrypt the system partition of a drive using the newer GUID Partition Table (GPT) system.
Bottom line: You need data encryption, just as you need a lock on your front door. But that lock doesn’t have to be as secure as the one at Fort Knox. Consider what you need to encrypt and then match it with the most suitable type of encryption — recognizing how much hassle you’re willing to put up with. For more on encryption, see the Dec. 12, 2013, Top Story, “Pre-encryption makes cloud-based storage safer,” and the May 15, 2014, Top Story, “Better data and boot security for Windows PCs.”
Versatile Finnish cover band also plays hockey
 |
When the members of the band Steve ‘n’ Seagulls cover a song and make a video, they don’t leave many of their ideas unexpressed. When was the last time you watched musicians clear an ice rink, sharpen their skates, and invite Finland’s Women’s National Ice Hockey Team to play a match with them? The band added to this a soundtrack of themselves singing “You Shook Me All Night Long” — enunciating the lyrics (in English) clearly, by the way. You might enjoy watching the women beat the daylights out of the guys and then kindly help them off the ice when the game is over. Click below or go to the original YouTube video. |
| Post your thoughts about this story in the WS Columns forum. |
No summer break from MS Office updates
It’s a relatively light month for security updates, but Office 2010 and 2013 both get a slew of nonsecurity fixes.
June’s Patch Tuesday release was also bulked up with a bunch of reissued security updates for Office 2010 and some patches that prepare Win7 and Win8 machines for Windows 10.
MS15-056 (3058515)
Regularly scheduled browser update review
The days immediately following Patch Tuesday (the second Tuesday of the month) are always a good time to ensure that all installed browsers are up to date. Even Opera (site) received a recent update. It’s also a good time to review your browser’s add-ons and extensions — some may no longer work after a browser update, others could need updating themselves, and those you no longer use should be removed.
As noted in a Windows Blog post, Microsoft has added HTTP Strict Transport Security (HSTS; more info) to IE 11 on Windows 8.1 and 7. June’s cumulative IE update, KB 3058515, among other things, adds support for HSTS to IE clients. But actually implementing this security feature will be up to individual site developers.
Rated critical, KB 3058515 patches over 20 IE vulnerabilities. It also includes seven nonsecurity fixes — among them, one that improves HTML table display speed and another that solves an issue with slow or crashing Web apps.
Of the other browsers, Firefox is now up to Version 38.0.5 (more info); Chrome is on Version 43.0.2357.124, as noted on a Chrome release post. (Along with security updates, Mozilla is apparently very busy adding new features to Firefox.)
IE isn’t the only app to get a heavy load of security fixes. According to Adobe’s June 9 security bulletin, Flash Player 18.0.0.160 addresses 13 vulnerabilities, some of which have already been used in ransomware attacks. (In my recent “Ransomware” session at last month’s MVP Virtual Conference, I discussed about how Flash is used for ransomware attacks.)
 What to do: Install KB 3058515 (MS15-056) as soon as possible.
What to do: Install KB 3058515 (MS15-056) as soon as possible.
MS15-057 (3033890)
Playing the latest pop hit can be hazardous
While Apple users are getting a new streaming service this month, Windows Media Player users are receiving a patch that prevents remote code-execution exploits. Rated critical, KB 3033890 is for Vista, Win7, Server 2003, and editions of Server 2008.
With this exploit, a PC can become infected if malicious media content is downloaded from a website, which could then let a hacker take complete control of your system.
 What to do: There’s a high probability that this avenue of attack will be seen soon. Install KB 3033890 (MS15-057) as soon as possible.
What to do: There’s a high probability that this avenue of attack will be seen soon. Install KB 3033890 (MS15-057) as soon as possible.
MS15-059 (2863812, 2863817, 3039749, 3039782)
New threats from malicious Office docs
May’s MS15-046 update included a huge number of security fixes for all supported versions of Office. The updates in June’s MS15-059 also cover Office 2007, 2010, and 2013 — but thankfully, the number of fixes is small. Office 2007 users will see just KB 2863812; Office 2010 will get KB 2863817; and Office 2013 gets KB 3039749 and KB 3039782.
An attacker who successfully exploits one or more of the three Office vulnerabilities patched by MS15-059 could run malicious code with the same rights as the current user.
 What to do: Install KB 2863812, KB 2863817, KB 3039749, and/or KB 3039782 (MS15-059) when offered.
What to do: Install KB 2863812, KB 2863817, KB 3039749, and/or KB 3039782 (MS15-059) when offered.
MS15-060 (3059317)
Using IE’s developer tools to compromise Windows
As anyone who likes to poke behind the curtains of IE knows, pressing F12 on the keyboard pops up a set of developer tools. It’s handy for reviewing page-formatting code. But a relatively obscure vulnerability in the Microsoft Common Controls component of Windows could let an attacker take remote control of systems. For the exploit to work, a user must click a malicious link and then click F12. Not surprisingly, this update is rated just important.
KB 3059317 applies to all supported versions of Windows, including Windows 10 Technical Preview. (Note that updates in Win10 Preview are not optional.)
 What to do: Even if you never use IE’s F12 developer tools, install KB 3059317 (MS15-060) when offered.
What to do: Even if you never use IE’s F12 developer tools, install KB 3059317 (MS15-060) when offered.
MS15-061 (3057839)
Run some code; become an administrator
Next to IE and Office, a favorite hacker target seems to be the Windows kernel. Nearly every month, we see one or two kernel mode–driver fixes. This month’s KB 3057839, for example, removes several Windows vulnerabilities that could give an attacker full rights to a system. However, the hacker must first be able to sign in to the machine.
Rated important, this update impacts all supported versions of Windows.
 What to do: It’s always good to be cautious about kernel updates. Put KB 3057839 (MS15-061) on hold until the end of the month.
What to do: It’s always good to be cautious about kernel updates. Put KB 3057839 (MS15-061) on hold until the end of the month.
MS15-063 (3063858)
Using a malicious DLL to take control
KB 3063858 would seem to be déjà vu; it, too, fixes a vulnerability in the Windows kernel that could allow unauthorized elevated rights. But in this case, the attacker must place a malicious .dll file on the local machine or shared network resource and then wait for a user to run an app that loads the DLL. (More proof that there are many ways to attack an OS.)
The update is rated important for Vista, Win7, Win8, Server 2008, and Server 2012.
 What to do: As with the aforementioned kernel update, uncheck KB 3063858 (MS15-063) until the end of the month, by which time we should have heard about any unexpected side effects or incompatibilities with third-party apps.
What to do: As with the aforementioned kernel update, uncheck KB 3063858 (MS15-063) until the end of the month, by which time we should have heard about any unexpected side effects or incompatibilities with third-party apps.
MS15-046
Office 2010 security updates get a do-over
It’s not, however, déjà vu for some Office 2010 security updates. Microsoft has reissued numerous patches in MS15-046 to fix vulnerabilities that were missed in the May release. (Note that these updates have new KB numbers.)
To be reinstalled are:
- 3054833 – SharePoint 2010
- 3054834 – Office 2010
- 3054835 – PowerPoint 2010
- 3054838 – Excel Web App
- 3054839 – SharePoint 2010
- 3054841 – Office 2010
- 3054842 – Word 2010
- 3054843 – Web Applications 2010
- 3054845 – Excel 2010
- 3054840 – PowerPoint Viewer 2010
- 3054847 – SharePoint Foundation 2010
- 3054848 – Office 2010
 What to do: Install any of the above updates in MS15-046 if offered.
What to do: Install any of the above updates in MS15-046 if offered.
MS15-062 (3062577)
An ADFS security update for server admins
Using a malicious URL, a hacker could exploit a vulnerability in Microsoft Active Directory Federation Services that might lead to elevated privileges on servers. But this cross-site scripting attack also requires some unintended help from a user — thus KB 3062577’s important rating. The update impacts Windows Server 2008, 2012, and 2012 R2.
 What to do: This exploit works only on systems with ADFS enabled. Deploy KB 3062577 (MS15-062) only after it’s been tested on your network environment.
What to do: This exploit works only on systems with ADFS enabled. Deploy KB 3062577 (MS15-062) only after it’s been tested on your network environment.
MS15-064 (3062157)
Exchange 2013 gets elevation-of-privilege attacks
It’s rare that only one version of a Microsoft product has a security issue. But KB 3062157 impacts only MS Exchange 2013. Left unpatched, three vulnerabilities in Exchange could give an attacker access to other systems behind a firewall, target services running on the server, and exploit authentication services.
What to do: Exchange admins should deploy KB 3062157 (MS15-064) after testing it.
Another bulky month of nonsecurity updates
Among the long list of Windows and Office nonsecurity updates are several for Win7 and Win8 to prepare systems for upgrading to Windows 10. I’ll review these soon in an upcoming Windows Secrets issue.
For the full list of Office security and nonsecurity updates, see MS Support page 2971668.
The June nonsecurity updates are as follows:
Windows optional updates
- 3050265 – Win7; Windows Update scan performance, Win10 prep
- 3050267 – Win8; various Windows Update fixes, Win10 prep
- 3068708 – Win7/8; customer experience and diagnostic telemetry, Win10 prep
Office 2007/2010
- 2553308 – Outlook 2010; Social Connector
- 2965296 – Office 2010; English proofing
- 2965297 – OneNote 2010; SharePoint synching
- 3054875 – Office 2010; various fixes
- 3054881 – Outlook 2010; various fixes
- 3054883 – Outlook 2010; junk-mail filter
- 3054891 – Outlook 2007; junk-mail filter
Office 2013
- 2889863 – Office; MS Query import crash
- 3023054 – Office; bullet-list formatting problems
- 3039755 – Word; Track Changes, HTML table display
- 3039761 – Office; hyperlink conversion issues with Skype for Business
- 3039791 – Office; English proofing
- 3039764 – OneNote; notebook access for students and teachers
- 3054774 – Office; IRM features in Azure RMS
- 3054783 – Office; Error 1706 with standalone Office apps
- 3054786 – Outlook junk-mail filter
- 3054794 – Excel; various fixes
- 3054795 – Access; database-splitting failure
- 3054797 – Office; various fixes and enhancements
- 3054853 – Office; various fixes and enhancements
- 3054854 – Outlook; Facebook compatibility
- 3054855 – Outlook; numerous fixes
- 3054856 – Outlook; Facebook compatibility
- 3023058 – PowerPoint; various fixes
(Current versions for Office Click-to-Run are 14.0.7151.5001 and 15.0.4727.1002.)
Other updates
- 2956196 – Microsoft FAST Search Server 2010; OpenSSL
- 3017816 – Project 2010; incorrect assignments, lost start dates
- 3039729 – Visio 2013; various fixes
- 3054789 – SharePoint Server 2013; InfoPath performance
- 3054791 – Lync; adds Skype for Business client
- 3054825 – OneDrive for Business; memory leaks
- 3054830 – Project; numerous fixes
- 3054857 – SharePoint Server 2013; English proofing
- 3054859 – SharePoint Server 2013; various fixes
- 3054860 – SharePoint Server 2013; SQL reports, scorecard formatting, Excel exports
- 3054863 – Office Web Apps Server 2013; List Level missing
- 3054865 – Project Server 2013; cumulative update
- 3054869 – Project Server 2013; various fixes
- 3054874 – SharePoint Server 2010; English proofing
- 3054877 – Project Server 2010; cumulative update
- 3054866 – SharePoint Server 2013; cumulative update
- 3054864 – SharePoint Foundation 2013; cumulative update
- 3054867 – SharePoint Foundation 2013; document library navigation, REST-call error
- 3054871 – SharePoint Foundation 2013; multi-language terms for time zones
- 3054880 – SharePoint Server 2010; cumulative update
- 3054884 – SharePoint Server Office Web Apps; English proofing
 What to do: Put off all nonsecurity updates for a couple of weeks.
What to do: Put off all nonsecurity updates for a couple of weeks.
Regularly updated problem-patch chart
This table provides the status of recent Windows and Microsoft application security updates. Patches listed below as safe to install will typically be removed from the table about a month after they appear. Status changes are highlighted in bold.
For Microsoft’s list of recently released patches, go to the MS Security TechCenter page.
| Patch | Released | Description | Status |
|---|---|---|---|
| 3057839 | 06-09 | Windows kernel | Wait |
| 3063858 | 06-09 | Windows kernel | Wait |
| 3045171 | 05-12 | Windows kernel-mode drivers; also in MS15-044 | Install |
| 3046002 | 05-12 | Windows Journal | Install |
| 3049563 | 05-12 | IE cumulative update | Install |
| 3050514 | 05-12 | Windows kernel | Install |
| 3050945 | 05-12 | JScript and VBScript; also KBs 3050941 and 3050946 on servers | Install |
| 3051768 | 05-12 | MS Management Console file format | Install |
| 3055642 | 05-12 | Service Control Manager | Install |
| 3056819 | 05-12 | Silverlight | Install |
| 3057110 | 05-12 | Microsoft font drivers; see MS15-044 for full patch list | Install |
| 3057134 | 05-12 | .NET Framework; see MS15-048 for full patch list | Install |
| 3057181 | 05-12 | Office; see MS15-046 for full patch list | Install |
| 3058083 | 05-12 | SharePoint Server; KBs 2760412, 2956192, and 3017815 | Install |
| 3061518 | 05-12 | Schannel | Install |
| 3033890 | 06-09 | Windows Media Player | Install |
| 3058515 | 06-09 | IE Cumulative update | Install |
| 3059317 | 06-09 | MS Common Controls | Install |
| 3062157 | 06-09 | MS Exchange Server | Install |
| 3062577 | 06-09 | Active Directory Federation Services (servers only) | Install |
| 3064949 | 06-09 | Office; KBs 2863812, 2863817, 3039749, 3039782 | Install |
Status recommendations: Skip — patch not needed; Hold — do not install until its problems are resolved; Wait — hold off temporarily while the patch is tested; Optional — not critical, use if wanted; Install — OK to apply.
Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com).
Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners.
Your email subscription:
- Subscription help: customersupport@askwoody.com
Copyright © 2025 AskWoody LLC, All rights reserved.

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Turn off right-click draw
by
Charles Billow
14 minutes ago -
Introducing ChromeOS M137 to The Stable Channel
by
Alex5723
3 hours, 45 minutes ago -
Brian Wilson (The Beach Boys) R.I.P
by
Alex5723
4 hours, 56 minutes ago -
Master patch listing for June 10, 2025
by
Susan Bradley
5 hours, 22 minutes ago -
Suggestions for New All in One Printer and a Photo Printer Windows 10
by
Win7and10
11 hours, 20 minutes ago -
Purchasing New Printer. Uninstall old Printer Software First?
by
Win7and10
11 hours, 24 minutes ago -
KB5060842 Issue (Minor)
by
AC641
15 hours, 57 minutes ago -
EchoLeak : Zero Click M365 Copilot leak sensitive information
by
Alex5723
18 hours, 29 minutes ago -
24H2 may not be offered June updates
by
Susan Bradley
53 minutes ago -
Acronis : Tracking Chaos RAT’s evolution (Windows, Linux)
by
Alex5723
1 day, 7 hours ago -
June 2025 updates are out
by
Susan Bradley
7 hours, 10 minutes ago -
Mozilla shutting Deep Fake Detector
by
Alex5723
1 day, 21 hours ago -
Windows-Maintenance-Tool (.bat)
by
Alex5723
1 day, 7 hours ago -
Windows 11 Insider Preview build 26200.5641 released to DEV
by
joep517
2 days ago -
Windows 11 Insider Preview build 26120.4250 (24H2) released to BETA
by
joep517
2 days ago -
Install Office 365 Outlook classic on new Win11 machine
by
WSrcull999
2 days ago -
win 10 to win 11 with cpu/mb replacement
by
aquatarkus
1 day, 16 hours ago -
re-install Windows Security
by
CWBillow
2 days, 3 hours ago -
WWDC 2025 Recap: All of Apple’s NEW Features in 10 Minutes!
by
Alex5723
2 days, 7 hours ago -
macOS Tahoe 26
by
Alex5723
2 days, 1 hour ago -
Migrating from win10 to win11, instructions coming?
by
astro46
12 hours, 40 minutes ago -
Device Eligibility for Apple 2026 Operating Systems due this Fall
by
PKCano
1 day, 16 hours ago -
Recommended watching : Mountainhead movie
by
Alex5723
1 day, 16 hours ago -
End of support for Windows 10
by
Old enough to know better
1 day ago -
What goes on inside an LLM
by
Michael Covington
1 day, 10 hours ago -
The risk of remote access
by
Susan Bradley
6 hours, 37 minutes ago -
The cruelest month for many Office users
by
Peter Deegan
18 hours, 49 minutes ago -
Tracking protection and trade-offs in Edge
by
Mary Branscombe
1 day, 21 hours ago -
Supreme Court grants DOGE access to confidential Social Security records
by
Alex5723
3 days, 5 hours ago -
EaseUS Partition Master free 19.6
by
Alex5723
2 days, 6 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.

