|
In this issue PATCH WATCH: Vulnerabilities everywhere Additional articles in the PLUS issue WINDOWS: Sadly, Windows 11 still isn’t great at multiple monitors MICROSOFT: More Microsoft Rewards tips and tricks FREEWARE SPOTLIGHT: Folder Size Analyzer — What’s using up your hard drive?
PATCH WATCH Vulnerabilities everywhere
By Susan Bradley Another month, another series of updates for seemingly everything on the Windows platform. But this isn’t just any month. Patch Tuesday once again coincided with the week of the annual security conference, Black Hat. The Windows-based topics range from “Hacking Bing.com (and much much more) with Azure Active Directory” to a briefing titled “Defender-Pretender: When Windows Defender Updates Become a Security Risk.” In addition, there is a talk called “Single Instruction Multiple Data Leaks in Cutting edge CPUs aka Downfall.” Better known as CVE-2022-40982, the flaw is a transient execution side-channel issue and impacts all processors based on Intel microarchitectures from Skylake through Ice Lake. Not to be left out, Apple and Android bugs have their own talks. Technology will always — unfortunately — need patching. But lately, patches have been getting more complicated, to the extent that merely patching your device isn’t enough. Remediation steps are necessary, which for the consumer or home user may be complicated or cause side effects. In a business setting, especially for someone tasked with patching and protecting healthcare, you may want to do everything you can to protect your network. Bottom line: In the last few months, we’ve seen more and more of these complicated patches that don’t fully protect you. It’s up to you to determine how vulnerable you think you are, or whether you feel the thing that makes you stop, click, and think is good-enough protection. Patching recommendations for consumer and home users
The biggest surprise for me this month is a benefit that consumer and home users using the old-fashioned Office 2013 version will receive. Office 2013 was supposed to be at its end of life back in April. Yet every Office 2013 product got a proactive “defense in depth” update. Excel, OneNote, Outlook, PowerPoint, Project, Publisher, Visio, Word — did we forget anything? All of them received an update to not exactly fix a vulnerability, but to “stop the attach chain leading to the Windows Search Remote Code Execution Vulnerability (CVE-2023-36884).” That vulnerability was patched in July’s updates, but for older Office, it apparently needed additional protection. In its recent support post Outlook emails open next to web links in Microsoft Edge, referencing Microsoft 365 Personal and Family subscribers, Microsoft noted that it is: … striving to improve and streamline our product experiences — offering a new way to use the classic Microsoft Outlook app on Windows and the Microsoft Edge web browser. Or, in other words, to find new ways for us to ask “who changed what now?” The post goes on: … browser links from the Outlook app will open in Microsoft Edge by default, right alongside the email they’re from in the Microsoft Edge sidebar pane. And: Ultimately though, if this experience isn’t right for you, you can turn off this feature the first time it launches in Microsoft Edge, and then in Outlook settings at any time after that. I have yet to see this in action, but I’m hoping that it will be an obvious thing that you can stop — not one of those jarring events where you notice that something did change, but you have no idea why. Note this will not change your default browser settings, just where the links go. If this annoys you, go to the Microsoft Edge Settings page, click on Sidebar, and then turn off Automatically open Outlook email context in the side pane. Don’t just patch Windows
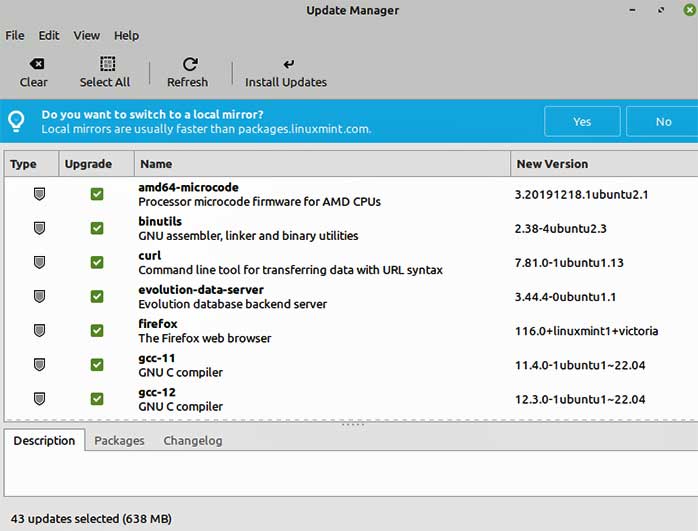
For those running Ubuntu, don’t forget to check for updates, especially security updates. It’s estimated that nearly 40% of the installed versions of Ubuntu may be vulnerable to GameOver(lay), which is actually two vulnerabilities (CVE-2023-2640 and CVE-2023-32629). Updates were released in July but may still be dribbling down to your version, so keep checking. The vulnerabilities are unique to Ubuntu kernels because they stemmed from Ubuntu’s individual changes to the OverlayFS module. Just as with many Windows vulnerabilities, this one is designed to give attackers more rights on the system, but they still must trick you or get onto your system first. Use the command line or the Software Updater GUI tool to apply updates. Invariably, the Ubuntu forums tell you that the command line interface (CLI) is amazingly simple, but I never can remember one operating system’s command from another. I prefer the GUI methods (Figure 1).
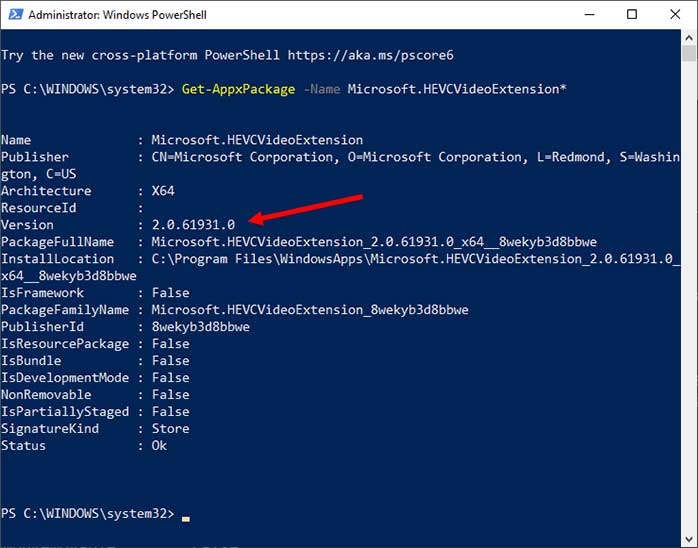
Whichever method you use, ensure you are up to date. For those of you who are fans of Linux Mint Cinnamon, Version 21.2 (aka Victoria) was released at the end of July. For upgrade instructions, you can follow the steps on the Linux Mint forums. For that platform, I recommend using the GUI method by clicking on the Edit | upgrade option. Just as with any other platform, ensure that you’ve backed up your computer. In Linux Mint, the built-in backup software is called TimeShift, and it allows you to take a system snapshot before the upgrade. Make sure your preferred browser is up to date, as with any operating system. Canon announced that over 200 models of inkjet printers can expose your Wi-Fi details. The Canon advisory recommends that, before sending a printer to be recycled, you reset all settings to the factory defaults. This is probably not a bad idea for any printer or any tech device, for that matter. Ensure that you always know how to erase, reset, or — if need be — take a hammer to that device, destroying the hardware to ensure your sensitive information isn’t inadvertently obtained by someone else. If you’ve disabled the Microsoft Store, be aware that HEVC video extensions may need to be manually patched. Use PowerShell to check the version (Figure 2).
If the package version is 2.0.61931.0 and the package was installed by your device’s manufacturer, or the version is 2.0.61933.0 and the package was obtained from the Microsoft Store, you have the update. To update manually, you must re-enable the Microsoft Store, download and install the updated version, then disable the store again. There is a method using WinGet, but it is very complex and I do not recommend it. Patching recommendations for business users
Microsoft’s mail-server platform seems to be constantly at risk from something. If it’s not attackers wanting to gain control of the email platform, it’s Exchange patching that is fraught with issues. This month’s Exchange updates appear to be causing installation issues for German language installations. But even if you don’t have issues getting the patch installed, be aware that your patching job is not done. For those on Exchange 2016 and 2019, run a PowerShell script to fully protect yourself from CVE-2023-21709. In addition, if you run Exchange and use either Azure or the AD Rights Management Service (RMS), you’ll need to complete another step. If you do not know what Azure or RMS is, Exchange Online CBC encryption changes should not apply to you. But if you do, you will need to follow this post to enable support for AES256-CBC mode of encryption in Exchange Server. It allows you to use secure AES256-CBC mode to encrypt email messages and attachments in Exchange Online and decrypt such email messages and attachments in Exchange Server. If Microsoft wanted to drive you insane, so that you’d voluntarily move to Microsoft 365 no matter the cost, this month may just do it. Hang in there, Exchange administrators — this is going to be a fun month. Teams is the next software that should be on a fast track for updating this month. It’s continuing to be regarded by attackers not only as a means to phish their way into an organization through email lures, but also as a weapon in attacks. This month’s vulnerabilities include “allowing an attacker to gain code execution on a target system by convincing someone to attend a malicious Teams meeting set up by the attacker.” If you are still in testing mode, warn staff to be aware of malicious Teams invites. Note that the only way you can push out a new Teams deployment in an emergency and not wait for auto-updating is to use a bulk installer and create a script to remove the old version and deploy the new one. Also note that the Teams spellchecker appears to be broken with this release. In my recent MS-DEFCON 2 alert, I mentioned CVE-2023-32019 and Microsoft’s support post KB5028407: How to manage the vulnerability associated with CVE-2023-32019, which stated that the resolution introduced a breaking change. That post has been updated: IMPORTANT The resolution described in this article has been released enabled by default. To apply the enabled by default resolution, install the Windows update that is dated on or after August 8, 2023. No further user action is required. The key here is “enabled by default.” Previously, the update was installed but disabled, with Microsoft recommending testing before deployment. Still, there has not yet been any communication regarding what breaking change we’re supposed to be looking for. I haven’t seen anything in my early testing, but I don’t know if I’m looking in the right places for side effects. A little more communication from Microsoft would be much appreciated. Although Microsoft recommends installing the patch, remember that the current MS-DEFCON level is 2. Give this one a bit more time to settle. CPU patching
As a patching administrator, I’ve gotten more used to remotely patching firmware in workstations and laptops. I’ve had to. From Intel to AMD, more and more information-leak bugs are being found in these CPUs’ firmware. My advice: Ensure that you identify riskier servers, workstations, and laptops that are likely targets. Identify which CPUs have patches now, and which will be coming out in future releases. AMD has a recap of its upcoming releases that you’ll need to keep an eye on. Some won’t be out until October. At the recent Black Hat security conference, researchers released information about Downfall — vulnerabilities in Intel chips. If you don’t have a mechanism to patch and maintain firmware, you’ll need to ensure your patching routine can handle this going forward. It remains to be seen whether this will have performance impact. Stay tuned. I’m sure we’ll be squishing these bugs for a long time. Resources
Susan Bradley is the publisher of the AskWoody newsletters.
|
|||||||||||||||||||
| Know anyone who would benefit from this information? Please share! Forward the email and encourage them to sign up via the online form — our public newsletter is free! |
|
Enjoying the newsletter? Become a PLUS member and get it all! |
|
 |
Don’t miss any of our great content about Windows, Microsoft, Office, 365, PCs, hardware, software, privacy, security, safety, useful and safe freeware, important news, analysis, and Susan Bradley’s popular and sought-after patch advice. PLUS, these exclusive benefits:
We’re supported by donations — choose any amount of $6 or more for a one-year membership. |
  |
|
The AskWoody Newsletters are published by AskWoody Tech LLC, Fresno, CA USA.
- Publisher: Susan Bradley (publisher@askwoody.com)
- Editor: Will Fastie (editor@askwoody.com)
Your subscription:
- Subscription help: CustomerSupport@askwoody.com
Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, AskWoody.com, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody Tech LLC. All other marks are the trademarks or service marks of their respective owners.
Copyright ©2023 AskWoody Tech LLC. All rights reserved.