In this issue PUBLIC DEFENDER: The first Google search result often leads to a virus Additional articles in the PLUS issue LANGALIST: PC refuses to upgrade to newer version LINUX: Preparing for your move to Linux ON SECURITY: Preparing for your move to Linux Not a Plus Member yet? Join today!
PUBLIC DEFENDER The first Google search result often leads to a virus
By Brian Livingston The top search result in Google is all too often a link to a website that’s been hacked to infect visitors’ devices with a virus. The culprit behind these infections is called “Gootloader,” a descendant of years-old malware that just keeps getting worse on Google — the only search engine that’s being targeted. The hackers have found ways to control the content management systems (CMSes) of legitimate websites that happen to rank highly in Google on certain search terms. The hacked sites are made to display fake webpages that can infect users who click a link. The websites’ owners are usually unaware that anything evil is happening. The virus authors insert search-engine optimization (SEO) tricks to enhance a hacked website’s chances of showing up as the No. 1 result in specific Google searches. The “improved” websites often rise to the top in searches, because Google’s ranking algorithm boosts websites that match the exact wording of a user’s search. Warning: Don’t do any of the Google searches or try to visit any of the websites that are mentioned in the screen shots below, unless you’re a professional security researcher with special defensive software. I’m deliberately not rendering in a clickable format any of the hyperlinks shown in the illustrations. Routine searches match legitimate-sounding websites
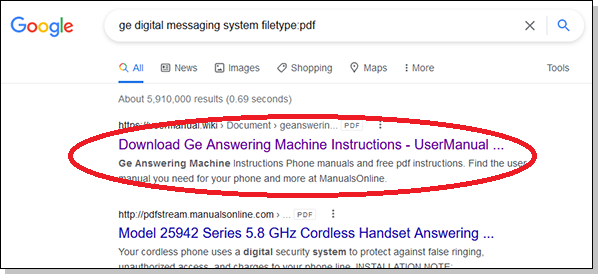
As an example of how the hackers work, imagine that you maintain a landline in a small office to get better audio quality than a cellphone. To screen out nuisance calls, your phone line is initially picked up by a popular answering machine, the GE Digital Messaging System. Let’s say you need to change the device’s configuration or greeting one day. So you search in Google, looking for a PDF that contains the product’s out-of-print user manual. The top Google hit is shown in Figure 1.
Google’s No. 1 listing is a website that has “UserManual” in its name, which sounds legitimate. You click the link to download the PDF and open it. Then you see your first clue that something is seriously wrong. The words match your search, but the link is malicious
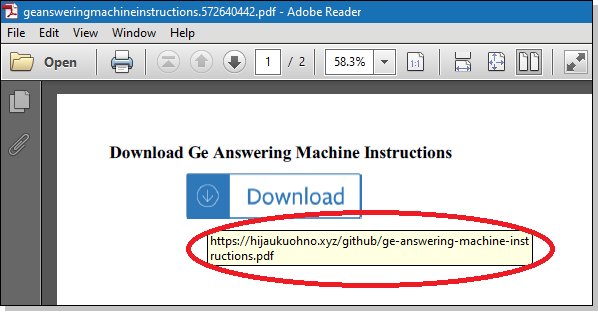
The downloaded PDF is not a user manual, but only a short document containing little more than a button to “download the manual.” At this point, if you’re wise, you’ll hover your mouse over the button to see where it goes. In this case, an Adobe Reader tooltip reveals that the website you would be taken to is called (I swear I’m not making this up): ◼ Hijack You Oh No (dot) xyz Actually, the hacker can’t spell “hijack,” so the literal domain name, as shown in Figure 2, is: ◼ hijaukuohno (dot) xyz
What kind of hacker is so stupid as to pick a domain name that sounds like “Hijack You Oh No”? I’m showing you this dopey example only to prove how even lame, second-rate hackers are able to get Google to do their bidding. The real problem isn’t inexperienced “script kiddies.” It’s sophisticated hacker gangs that are employing these same techniques to lure millions of Web surfers, using Google’s search results as the bait. A well-known malware kit has morphed this year into ‘Gootloader’
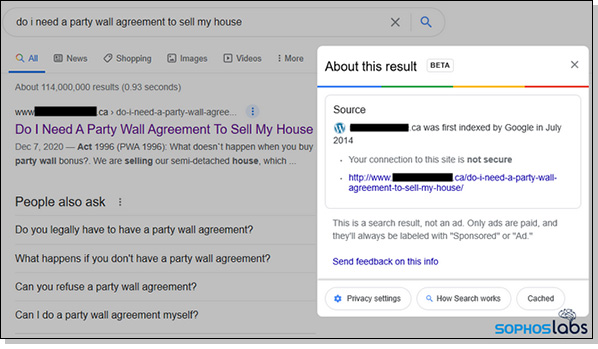
Security researchers have sounded a warning for years against Gootkit, a family of malware that exploits weaknesses in the Windows operating system. This year, researchers at Sophos Labs identified an outgrowth of Gootkit called Gootloader. It uses elaborate methods to get into Google search results and deliver viral packages. Figure 3 is an example of a longer search string — in this case, a search for a type of real-estate contract known as a party wall agreement.
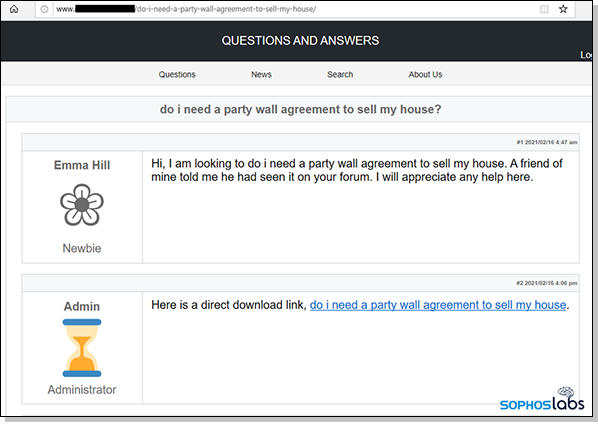
Google’s No. 1 recommendation — out of 114 million websites — is a Canadian medical-services site. Curious users who check the “About this result” sidebar see that Google considers the site legitimate and not an ad, and that the site has been indexed since 2014. Everything sounds on the up-and-up. Google, however, does not warn the user that the website has been hacked by Gootloader. The tool controls the site’s CMS and delivers a fake webpage that looks like an actual discussion forum, as shown in Figure 4. To lure the visitor into clicking a link, the page and its links use the same words that were in the user’s Google search.
I wish that the average user’s immediate reaction were, “It’s very unlikely that a website would have a page title, a hyperlink, and a document name using the exact words that I searched on, so I’m not going to click this link.” Unfortunately, it’s our human nature to think, “This website perfectly matches what I’m looking for, and Google vouches for it, so I’m going to download and open the file it’s offering me.” If you use the link, you receive a ZIP file that contains a JavaScript file with a .js extension. Both files bear the same filenames as the original search terms you entered into Google.
Sometimes, you get lucky. Gootloader checks with a master server known as the mothership before it does any damage. The malware is known to operate only in affluent countries, including the United States, Canada, France, Germany, and South Korea. The website information is delivered in the user’s language, such as Korean in the case of South Korea. There’s no point in the gang wasting resources on countries that are not specifically targeted. Using Google’s own ranking algorithm against it — and you
The hackers don’t seem to focus on the most-popular searches, such as weather and news. It would be hard to rise to the top on such terms, which fit well-established, branded sites. Instead, the hackers’ computer time is spent processing thousands of longer search strings that, obscure as they may be, still match what millions of Web surfers are entering into Google: things such as digital messaging, sell my house, and on and on. The scheme works because of Google’s particular method of ranking websites. It’s hard to remember the dawn of the Web, but the dominant search engine back in 1995 was AltaVista. It was a wild success — Google wouldn’t get popular enough to attract a single advertiser until 2000 — but if you used AltaVista to search on general motors, you’d see listings for engines used by Army officers. AltaVista’s search results were heavily based on the number of times a keyword appeared on a page. The genius of Google’s founders, in addition to counting how many backlinks a website had, was recognizing that phrases could have different meanings than their individual words. It seems obvious today that General Motors is a major corporation and probably the topic that a searcher is actually looking for. AltaVista never adapted, and it was merged into Yahoo in 2003. Gootloader turns Google’s very love of phrase-matching against the search giant. A hacked site will never show up as Google’s No. 1 choice on a common search, such as money — which has 21 billion hits — but feed Google an esoteric string such as party wall agreement, and Gootloader’s SEO work gives the hackers a very good chance of topping the search results. Google tries, but is it successful or half-hearted in protecting users?
I asked Google for comment on the ways it eliminates malware-infested websites from its search results. A Google spokesperson responded: We aren’t able to share all the specifics about how we fight malware, because if we did, bad actors could use that information to try and work around our systems. But we’re always working to keep people safe on Search from bad actors. Google Safe Browsing, for instance, displays warning messages letting you know that the site you are trying to enter might be unsafe, protecting you and your personal information from potential malware and phishing scams. We also alert webmasters if we believe they have been hacked and work with them to secure their sites. In 2020, we detected 40 billion pages of spam every day – including sites that have been hacked or deceptively created to steal your personal information – and blocked them from appearing in Search results. There are no more than 55 billion webpages in Google’s indexes, according to WorldWideWebSize statistics. So if Google blocks 40 billion of them 365 days a year, the search giant may already be blocking 73% of all the webpages in the world. To which I say, “That’s great — now do better.” It’s unacceptable that a handful of hackers can ever get Google to display malware in the top 10 results, much less the No. 1 result, on any type of search. OK, Google, show us that you’re smarter than these miserable crooks. For a start, merely alerting webmasters that their sites are spreading viruses doesn’t seem to be 100% effective. It would be better to notify the operators that their hacked sites will be removed from search results starting today, until the affected servers are clean. That would get webmasters’ immediate attention while actually giving Google’s billions of ordinary users the protection they deserve. For more information, the Google spokesperson recommended a blog page on safe search. How to protect yourself against viruses in Google search results
First of all, read Sophos Labs’ excellent August 12 analysis of Gootloader and its “mothership” server. That article links to the labs’ first description of Gootloader back in March, which is also a good read. A separate Sophos article recommends four steps you can take to avoid malicious websites:
Windows Vista and later versions hide file extensions by default. With just a few clicks, you can force File Explorer and other programs to display these extensions, as explained in a CNET article. You can also submit questionable files or entire websites to free sandbox services, such as Hybrid Analysis (also known as Reverse It). I submitted the URL that’s circled in Figure 2. The resulting report told me that the download would have installed a 61KB cabinet file, patched its running process in memory (a trick malware uses to avoid detection), and had two other “suspicious indicators.” Nice try, Mr. Hijack You Oh No. All of the above is a lot to expect PC users to do to protect themselves against the search results of a tech giant with $182 billion of revenue in 2020 (Statista stat). Sophos Labs’ original description of Gootloader recommended a simpler solution: In the end, it’s up to the search engines, whose algorithm the malware games to get a high search result, to address the initial attack vector. Users can be trained to do things like enable visible file suffixes in Windows, so they can see they’re clicking a file with a .js extension, but they can’t choose which search results appear near the top of the list or how those sites get manipulated by threat actors. Here’s an even easier fix: Stop using Google, since it’s the only search engine large enough for the Gootloader gang to bother exploiting. Think the search engine is irreplaceable? Critics say the company is a danger to your privacy, as explained in articles in Wikipedia and CPO Magazine. “To google” has long been a verb — it was added to the Merriam-Webster and Oxford dictionaries way back in 2006 — but a new candidate is “to degoogle.” The term has its own subreddit with 55,000 members, who post a handy sidebar of alternatives. Another good source of guidance is a RestorePrivacy review that focuses on the security of user data. Remember how AltaVista wound up …
The PUBLIC DEFENDER column is Brian Livingston’s campaign to give you consumer protection from tech. If it’s irritating you, and it has an “on” switch, he’ll take the case! Brian is a successful dot-com entrepreneur, author or co-author of 11 Windows Secrets books, and author of the new book Muscular Portfolios. Get his free monthly newsletter.
You’re welcome to share! Do you know someone who would benefit from the information in this newsletter? Feel free to forward it to them. And encourage them to subscribe via our online signup form — it’s completely free!
Publisher: AskWoody Tech LLC (sb@askwoody.com); editor: Will Fastie (editor@askwoody.com). Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody Tech LLC. All other marks are the trademarks or service marks of their respective owners. Your subscription:
Copyright © 2021 AskWoody Tech LLC. All rights reserved. |




 In Windows, the .js file looks like the image at left, according to Sophos Labs. Running this program can infect your device in ways that might not be at all apparent. You may not learn until days or weeks later that your computer is acting strangely or your files have been encrypted and you’re a victim of a ransomware attack.
In Windows, the .js file looks like the image at left, according to Sophos Labs. Running this program can infect your device in ways that might not be at all apparent. You may not learn until days or weeks later that your computer is acting strangely or your files have been encrypted and you’re a victim of a ransomware attack.






