|
In this issue PUBLIC DEFENDER: The best tech secrets of 2022: AirTags, TikTok, Twitter, oh my Additional articles in the PLUS issue • Get Plus! MICROSOFT 365: Microsoft 365: Year in review FREEWARE SPOTLIGHT: Firewall App Blocker — Make the Windows firewall usable ON SECURITY: Finding good security information
PUBLIC DEFENDER The best tech secrets of 2022: AirTags, TikTok, Twitter, oh my
By Brian Livingston Amid my efforts to help you protect yourself against some rather aggressive technologies, I’m glad to report that there’s been at least some progress this year on the worst aspects of our “labor-saving” devices. Please note: I’m not claiming that my columns by themselves caused any of the changes I describe below. I just report the problems. We can all celebrate when bad tech is improved, whoever may have developed a particular solution. If you don’t use an iPhone, choose a tracker for Android phones instead
I reported earlier this year that Apple’s new AirTag tracking devices had weak security features. Specifically, the button-sized, wireless key-ring finders are being used by criminals to track people and trail high-value vehicles to steal. (These uses ignore the devices’ legitimate purpose: helping you find your bicycles, travel luggage, and other possessions). The Positive Security consultancy, using only three inexpensive pieces of tech hardware, was able to defeat all of the fairly limited anti-stalking features that Apple’s AirTags do include.
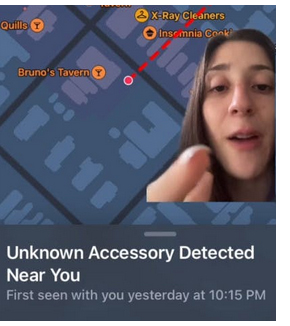
These problems have been shouted about by many people. One of them, TikTok poster Erika Torres, published in a Daily Dot blog a video showing that someone had planted an AirTag on the underside of her car. After using her iPhone to connect to Apple’s AirTag server, she found that the device had been reporting her location to an unknown stalker when she was at a bar, while driving, and at her home. (See screen capture at left.) Tracking devices have been available for decades, of course. But they generally required a GPS service, the payment of a monthly fee, and some technical savvy. Apple’s release of $29 AirTags in 2021 changed all that. For the first time, any criminally minded person with enough skill to turn on an iPhone could track anyone or anything by hiding an AirTag in a victim’s vehicle, purse, etc. A study of crime reports from eight major US police departments was recently revealed in a Vice blog post. One-third of the AirTag-linked files involved women being illegally tracked by men. Fewer than half of the complaints mentioned AirTags being used to locate and steal cars, bicycles, and other valuables. While current and former suitors and husbands are the stalkers in most cases, that’s not always true. Police in Indiana arrested a 26-year-old woman in June for allegedly using an AirTag to track her estranged boyfriend to a bar, where she killed him (USA Today). In an attempt to quell criticism of the AirTag’s lax security, Apple released last December a notification app called Tracker Detect for Android phones. But that app doesn’t work automatically, the way the app for iPhones does. You must run Tracker Detect manually every time you suspect that an AirTag may have been planted on you. (For automatic notification on Android phones, my column recommended the free AirGuard app from Google Play.) Apple could easily fix most stalking problems. But at this writing, the Cupertino tech giant hasn’t implemented in AirTags even the most basic precautions:
More on these recommendations and other concerns can be found in a Tech Wellness blog post. The problem of people being stalked — as opposed to tracking devices being used to harmlessly locate lost key rings and so forth — can be largely eliminated. Apple, Google, and other smartphone makers should include automatic tracker notification in iOS, Android, and all other mobile operating systems. Google was rumored to be adding universal tracking notification into Android beta version 22.12.13 back in March. The feature will hopefully allow you to halt alerts of non-worrisome AirTags that a friend traveling with you may be carrying. But the capability is apparently not yet installed, much less turned on by default (9to5Google). Until automatic warnings are included in all smartphones, the global editor in chief of Tom’s Guide says, “AirTags should be pulled from the market.” If you don’t own an iPhone, what’s your best bet to automatically get notifications that you’re being stalked, as well as to use these tiny devices to legitimately locate your belongings? Purchase a technology that works with Android devices (which now comprise 72% of the smartphones in the world, according to StatCounter):
In addition to the reviews I link to above, read my January 10 and March 7 columns for information on the security (or lack thereof) of AirTags. TikTok is still as bad as before, but now it’s in even more hot water
I reported this year that TikTok, the hugely popular short-video app, collects users’ passwords, crypto wallet addresses, and much more, transferring all this information to servers that are accessible by officials in Beijing, China.
Efforts to ban TikTok in the United States go back to a July 31, 2020, address by former President Donald Trump. In the absence of a ban, he said, he would attempt to force the app to be sold to an American company. (See Figure 2.) I wrote that legal challenges had frustrated those goals. But the incoming Biden administration subsequently prohibited TikTok’s use on devices employed by the US military, the Department of Homeland Security, and the Transportation Security Administration (TSA). The government of India also banned TikTok and several other Chinese-developed programs from the devices of that country’s 1.4 billion people, calling the apps a threat to national security. TikTok has only gotten into more trouble since then. In the US, TikTok’s use by government agencies, employees, and contractors is banned as of this writing in 16 states: Alabama, Florida, Georgia, Idaho, Iowa, Maryland, Nebraska, New Hampshire, North Dakota, Oklahoma, South Carolina, South Dakota, Tennessee, Texas, Utah, and Virginia (Wikipedia). The controversy has barely dented TikTok’s popularity among the general public, however. It was the most sought-after app in the world in 2021, with 656 million downloads, ahead of Instagram’s 545 million (Business of Apps). See the exposé of TikTok in my July 11 column. Nonfungible tokens (NFTs) are worth only what someone will pay for them
Early this year, nonfungible tokens were a hot commodity in the cryptocurrency world. Now, NFTs have come down to earth — along with the values of most crypto coins themselves. I warned in a column at the time that NFTs were vulnerable to a collapse of value. Specifically, the price of the biggest crypto token — bitcoin — has crashed 53% to 93% seven times in the past 11 years. Every time new buyers flowed in, excited by social-media hype, they were taken to the cleaners by insiders who sold. The sellers got their money out of bitcoin while the getting was good.
One colorful user of NFTs is Sky Mavis, a Vietnam-based game-development company that runs the multiplayer world called Axie Infinity. Players must purchase the company’s own crypto coin, Axie Infinity Shards (symbol: AXS), to obtain game animals. Each animated creature is associated with its own NFT, theoretically making each character unique. In August 2021, the tiny Sky Mavis endeavor was enjoying revenue of $15 million per day as more and more gamers discovered its play-to-earn-rewards system (paid in crypto, of course). Unfortunately, hackers said to be from North Korea managed to make off with $620 million worth of Sky Mavis’s assets last March (CNET). On January 1, 2022, one AXS coin was trading for more than $94. By December 19, with players’ faith in the company shattered, the price people were willing to pay had ground down to only $6.92 per AXS — a loss of 93% (CoinMarketCap). Game animals that players once purchased for more than $300 each are now worth less than $10. Even without any specific hacker exploits, the dollar values of bitcoin and other crypto tokens — including most NFTs — have crashed hard this year. Since bitcoin’s all-time high on November 11, 2021, the digital token has lost 76% of its value, as I reported in my December 5 column. NFTs have fared even worse. The co-founder and former CEO of Twitter, Jack Dorsey, auctioned an NFT that theoretically represented the first-ever tweet. A crypto whale based in Malaysia, Sina Estavi, “won” the auction with a bid of $2.9 million. Estavi intended to flip the NFT for even more, but the crypto crash was already dragging values down. In October 2022, the latest bid for his token on OpenSea, the largest NFT auction site, was only $132 — an inconceivable loss of 99.995%. Estavi has decided to hold onto his NFT for now (Entrepreneur). OpenSea itself found in a January 2022 study that more than 80% of the NFTs its users were creating were outright frauds. Promoters simply made digital copies of artworks that actually belonged to the original artists. The starry-eyed buyers didn’t receive the art or anything of value for the money they invested. For details on this and other aspects of NFTs, see my February 7 column on the subject. Are 80% of Twitter accounts really bots, and does anyone still care?
A hot topic this year was whether most of the accounts on Twitter, the short-message phenomenon, weren’t human users but were merely automated bot traffic. I reported that more than 80% were bots, based on a study by the head of intelligence at F5, a global network-security firm.
The number of Twitter accounts that were just bots acting like real users was a main bone of contention between the CEO of Tesla, Elon Musk, and Twitter executives who were fighting off Musk’s efforts to buy the company. Musk was eventually forced by a court order to follow through on his buyout promises. On October 27, Musk purchased Twitter for $44 billion, much of that consisting of borrowed money. Installing himself as Twitter’s CEO, Musk fired the website’s executives and laid off (or lost to resignations) 4,800 of Twitter’s 7,500 employees and terminated its 5,000 contract workers. The story is related in my December 19 column, along with details on the other companies in the Great Tech Layoff. With the website’s content-moderation group mostly gone, its advertisers largely suspended their ad campaigns — eliminating the money their ads had been paying into Twitter’s budget. Musk himself told an all-hands meeting of the remaining staffers that bankruptcy was a possibility for the once-enormous presence that was Twitter. Finally, Musk posted a poll on December 18 asking whether Twitter users thought he should step down as CEO, saying he’d abide by the vote. An astonishing 17.5 million people voted, and Musk was crushed. More than 57% gave him the thumbs-down (The Guardian). The evidence that 80% of supposed Twitter accounts were simply bots was explained in my September 12 column. Illegitimi non carborundum (Wikipedia). Have a wonderful 2023!
The PUBLIC DEFENDER column is Brian Livingston’s campaign to give you consumer protection from tech. If it’s irritating you, and it has an “on” switch, he’ll take the case! Brian is a successful dot-com entrepreneur, author or co-author of 11 Windows Secrets books, and author of the new fintech book Muscular Portfolios. Get his free monthly newsletter.
The AskWoody Newsletters are published by AskWoody Tech LLC, Fresno, CA USA.
Your subscription:
Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, AskWoody.com, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody Tech LLC. All other marks are the trademarks or service marks of their respective owners. Copyright ©2022 AskWoody Tech LLC. All rights reserved. |
|||||||||||||||||||||||||