In this issue ON SECURITY: The basics of security WINDOWS 11: The new PC Health Check app is here (almost) Additional articles in the PLUS issue LANGALIST: Should you activate Win10’s optional Application Guard? PUBLIC DEFENDER: Apple plans to break its end-to-end encryption HARDWARE: Breaking and entering with Linux HARDWARE DIY: Opal: How I planned my new build
ON SECURITY The basics of security
By Susan Bradley What are the basics you need to secure your computers and devices? The needs of consumer and business users are different, but the foundation of security is the same for both. We all need an operating system we can trust, a means to surf the Internet in a trustworthy fashion, and a way to save and store passwords securely. And I’ll add a fourth to this list, increasingly important: we need an application or device to allow us to effectively and efficiently use multi-factor authentication. Recommendations for consumer and home users There are four major things that your Windows computer must have. The first is an up-to-date browser. It doesn’t matter which browser you prefer — just make sure you’re always using the most current version. I can’t emphasize this enough, especially given the recent furor over Firefox’s new Proton UI. Some users have resolved to keep their version of Firefox “pre-Proton,” a dangerous move. This can be especially dangerous where e-commerce, banking, finance, health, or other sensitive activity is concerned. Avoiding Proton at the expense of security is risky. But if you are anti-Proton, use a userchrome.css process to change the look back to the classic Firefox rather than staying on an older, unpatched version. Second, and this may surprise you, don’t use a third-party antivirus product. In this era of zero-day vulnerabilities and phishing, all antivirus solutions are reactionary, not proactive. That being the case, using a program that doesn’t interfere with Windows updates or feature releases is a better idea. And that means using Windows Defender, which provides good, unobtrusive performance with less likelihood of problems. Over the years, Microsoft’s antivirus offerings have gone from less-than-stellar protection to ones that hold their own in comparison tests. Microsoft’s security products are used at the enterprise level more than you might guess. Next, I strongly recommend using a password program in lieu of storing passwords in your browser. Stealing passwords stored in your browser is trivial, and writing down passwords on paper doesn’t force you to choose good passwords. Using a tool to generate complex passwords is highly recommended. Look for a password tool that is platform-agnostic and will allow you to log in to sites across all your devices. Once you set up a password program, go back to your browser software and remove the saved passwords. Over time, as you log in to your key websites, change the passwords on these sites to more complex, secure ones. Last but not least, ensure that you have a good two-factor authentication process — and use it on a regular basis. The most common choice for a second authentication factor is text messages to a phone; even though the news is full of SIM-card attacks, any second factor makes it much harder for attackers. The bad guys will move on to easier targets. Also consider using a two-factor authentication platform such as Authy or Microsoft Authenticator for additional protection. For those of you with Chromebooks, carefully watch the state of support for your device. These inexpensive computers will not be provided with security updates for as long as Windows will receive them. Google originally supported versions for five years but then changed to a 6.5-year program called Auto Update Expiration (AUE). That unfortunate choice of names warns you that after six years, your Chromebook may still work but won’t be secure. And because Chromebooks are almost useless without connecting to the Web, outdated security means danger. Recommendations for business users The US Cybersecurity & Infrastructure Security Agency (CISA) describes business bad practices that lead to cybersecurity issues and ransomware attacks. Not surprisingly, the basics are similar to those I’ve mentioned above for consumers:
In business, the danger might be greater due to third-party business applications, or apps built in-house, that contain embedded credentials, often in clear text. If an attacker can gain access to the system and read any file, it can find those credentials and then use them. Another vulnerability, often overlooked, is a failure to change the default passwords associated with networking equipment, such as firewalls, routers, and managed switches. Those credentials should be strong, securely stored, and changed instantly any time a person previously entrusted with them is no longer associated with the business. Microsoft’s bad defaults
Recently Microsoft released a cloud computer platform called Windows 365. It allows businesses of any size to have a hosted Windows 10 (and soon Windows 11) instance in the cloud but otherwise act like a desktop operating system. I signed up for the beta and was surprised (and a bit shocked) to find it configured with what I consider to be less-than-ideal defaults. I found that Windows was deployed to the assigned end user with local administrator rights! In my test case, the Windows 365 instance was a trial tied to a Microsoft 365 subscription that does not have the additional control platform provided by Microsoft Endpoint Manager (formerly called Intune). Thankfully, the operating system was not connected to the local domain and resources of my local computer. But it still concerned me that after years of recommending to businesses that they deploy workstations with least privilege rights, Microsoft bypassed its own best-practice advice. I was not the only one who thought this unusual; several security researchers also questioned this approach. Clearly, Microsoft heard that feedback and recently advised in a blog post how better to deploy Windows 365 to users without local administrator rights. Microsoft uses the excuse that “This is similar to what happens in many small businesses: users purchase a physical PC themselves from a retailer and they retain local admin rights for that device.” Microsoft goes on to state that “standard IT security practices” are to set users as standard users. And then it recommends that you use Microsoft Endpoint Manager to better control the users and the operating system — but this is provided only with higher Microsoft 365 Business subscriptions and not the basic one that many small businesses often start with. Furthermore, Microsoft just announced that all Microsoft 365 subscription plans are going up in price — with the exception of the highest plan, which features the best security features (called the E5 license). This makes it harder to ensure that Windows 365 has the “basic” security it needs from the get-go. Microsoft 365 E5 includes actionable guidance for workstations to make them more secure. It includes security-threat information and guidance that allow you to gain insight into how attacks occur. It exposes a timeline analysis, so you can go back in time and review what has happened to your system and how it got owned by an attacker. It provides the ability to know whether an attacker was able to open and review an email (called MailItemsAccessed — an audit technique exposed only in the E5 license). But all these security features come at a price tag of US $57 per user per month. To put that in perspective, Windows Professional edition costs $200, once, and is often part of the cost of the computer you buy. Office for business use can be purchased for around $250. An E5 license costs $684 per year, per person. That’s a lot for a small business on a tight budget. You can purchase a single Microsoft 365 E5 license in order to review the features, or you can try out Office 365 E5 (just the Office part of the suite) for free, or you can set up a simulated test lab. Test it out and see whether there are situations or users that might need this extra protection; you don’t have to cover all users. I’m hoping that Microsoft makes this license cheaper so that it can be utilized by more customers. To me, the items in the E5 license are “basic” needs of auditing and security especially when I’m in the cloud. I just can’t justify $57 monthly per person. References
In real life, Susan Bradley is a Microsoft Security MVP and IT wrangler at a California accounting firm, where she manages a fleet of servers, virtual machines, workstations, iPhones, and other digital devices. She also does forensic investigations of computer systems for the firm.
WINDOWS 11 The new PC Health Check app is here (almost)
By Will Fastie Hallelujah! Sorry. That might be a little over the top. Rejoicing may be too early. And maybe unjustified. On August 27, Microsoft posted an Supported processors
The blog post spends a lot of time patting Microsoft on the back for carefully researching the processor landscape and adding selected CPUs to the list. That’s fine, but the most significant addition was the Intel Core i7-7820HQ. Wait, a seventh-generation chip? That’s right. Oh, in case you didn’t realize it, the i7-7820HQ is the processor in Microsoft’s most expensive Surface device, the Surface Studio 2. Its addition comes with a very substantial footnote, but it’s hard not to think how self-serving this is. Now all Surface devices in Microsoft’s online store are compatible with Windows 11. How convenient. No other seventh-generation chips were added. The line in the sand remains intact — you’ll need an eighth-generation Intel chip. No additional processors were added to the AMD or Qualcomm lists. Along with the update on processors, Microsoft wrote a lot about security. Pushback about TPM has been almost as loud as pushback about processors, so I think Microsoft was trying to do a better job explaining this than it did back on June 24. My conclusion in Windows 11 announced (2021-06-28), that Microsoft would not back off on its system requirements for Windows 11, remains accurate. PC Health Check app re-released
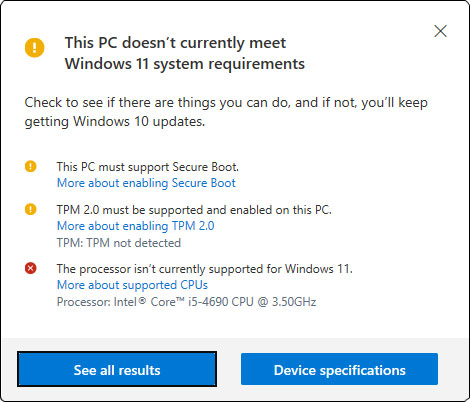
One of the most embarrassing parts of Microsoft’s June 24 event was its announcement of the PC Health Check app that determines whether a system is compatible with Windows 11. The app was instantly and universally panned, including by me, because it failed to provide a full analysis of compatibility and instead simply stopped at the first non-compliance detected. The app was pulled from Microsoft’s site within 24 hours, along with a statement that it would return closer to general availability of Windows 11. That statement was panned, too, because the app (really an applet) is relatively simple and should have been repairable quickly. Let me stop for a moment to reflect on that point. Obviously, the original version of the app was built with all the checks because otherwise it would have been completely useless. The objection we all had was that the app didn’t list all the conditions — it simply stopped on the first item detected. It took Microsoft two months to fix that. I’m sure you’re as impressed as I am. It is fixed, as the figures below will attest. Even so, Microsoft is still being timid. Instead of getting it right and releasing it to everyone, it was released only to Windows Insiders. The blog post said that Microsoft would await feedback and then probably release it generally in a couple of weeks. I’m sure you’re as impressed as I am. Anyway, here are a couple of screen clips showing the updated version of the PC Health Check app at work. Figure 1 shows the incompatibilities detected on Onyx, my current PC with the i5-4690 CPU.
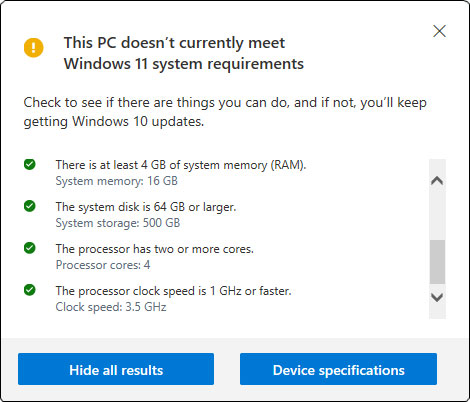
Figure 2 shows what happens if the “See all results” button is clicked. Then both the checks that failed as well as the checks that passed are shown.
The truth is that the new version of the PC Health Check app is what it should have been two months ago. Microsoft should still be embarrassed, but at least the app is here.
Will Fastie is editor in chief of the AskWoody Plus Newsletter.
You’re welcome to share! Do you know someone who would benefit from the information in this newsletter? Feel free to forward it to them. And encourage them to subscribe via our online signup form — it’s completely free!
Publisher: AskWoody Tech LLC (sb@askwoody.com); editor: Will Fastie (editor@askwoody.com). Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody Tech LLC. All other marks are the trademarks or service marks of their respective owners. Your subscription:
Copyright © 2021 AskWoody Tech LLC, All rights reserved. |