|
In this issue PATCH WATCH: KB5034441 has led us astray, in a horrible way Additional articles in the PLUS issue PUBLIC DEFENDER: Microsoft is pushing Copilot AI out to you LEGAL BRIEF: The hidden cost of WFH COMMENTARY: Bing Chat is sorry PATCH WATCH KB5034441 has led us astray, in a horrible way
By Susan Bradley • Comment about this article What’s with this Windows recovery partition thing? If you’ve been following along, you know we’ve been discussing the update associated with a BitLocker vulnerability (described in KB5034441) that may require a resizing of the Windows recovery partition to resolve. Microsoft’s handling of this problem has been so terrible that I was driven to raise the MS-DEFCON level to 1, just the fifth time I’ve considered it necessary. It turns out that the underlying problem is an update to the Windows Recovery Environment (WinRE). The problem surfaces when the existing recovery partition does not have enough space to hold the updated WinRE. More on that in a second. First, a caveat. I do not believe that consumer users should be installing KB5034441 in the first place. This update fixes a vulnerability that allows attackers to boot into the recovery partition, then access a drive protected with BitLocker. Most consumers don’t have BitLocker enabled through their own actions, so I think very few consumers are affected. However, some PC manufacturers enable BitLocker out of the factory. Some caution is called for (MS-DEFCON 1, after all), but my recommendation is that consumers block the update until the dust settles. Meanwhile, Microsoft’s handling of this update has been horrific. This is a classic one-size-fits-all update, but the risk associated with the vulnerability is not the same for all. For example, my computers at home do not have BitLocker enabled, nor do they have the hardware (TPM) necessary to support BitLocker’s encryption. The vulnerability requires the attacker to physically (not remotely) access the PC. Physical attacks against consumer PCs are highly unlikely, whether BitLocker is enabled or not. So my home machines do not meet the criteria for the vulnerability, yet the patch is being pushed to me anyway. And when it runs, it fails. Why it fails
The problem is space in the recovery partition. It’s a bit hard to grasp the details here (thanks again, Microsoft), but the update apparently requires 250MB of free space in the existing recovery partition. If that space is available, and even if your machine does not have BitLocker enabled, the update should install without error. One of my home computers had not one, but two, recovery partitions. The second of the two was the one that the system identified as the active recovery partition. Because it had less than 250MB free, the update failed. How did I know it had less free space than needed? It’s a two-task process. The first is to discover which partition is the recovery partition, tricky on my PC with two recovery partitions. Here are the steps I used to make that determination, the same steps you can use to check yours:
REAgentC is a command-line interface in PowerShell for WinRE. As shown in Figure 1, REAgentC identified the active recovery partition as partition 5 on disk 0.
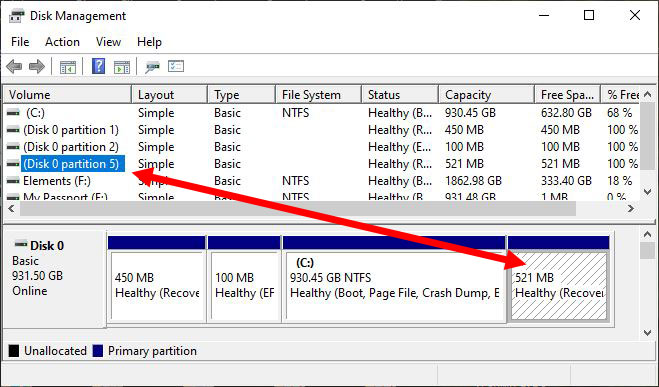
The next task is getting the details about that partition. The easiest way is to use the Disk Management tool. You can launch it by pressing WinKey and typing Disk Management, then clicking the app name; or by right-clicking the Start button and selecting Disk Management from the menu. Figure 2 shows that result on the same computer:
When either the volume name or partition in the visualization is clicked, both highlight and thus establish the relationship. In other words, the gray hatching means that the 521MB partition is partition 5. Unfortunately, there’s still a loose end and a huge point of confusion. In the Volume list in Figure 2, look to the far-right column with the heading % Free and notice that partition 5 is shown with 100% of the space free. It isn’t. To discover that, I resorted to one more tool, which gave this result:
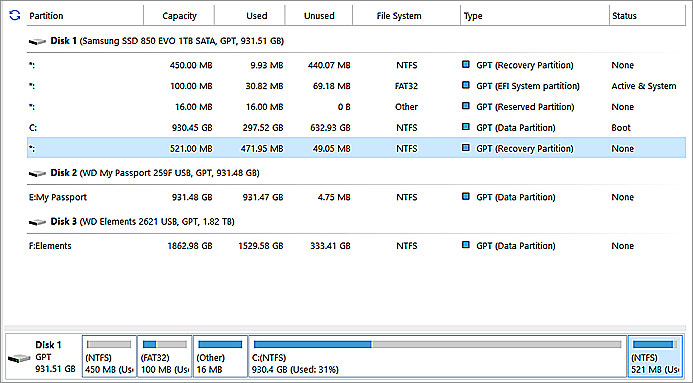
In Figure 3, the fifth partition highlighted in light blue is partition 5, which we can tell only because it’s listed last of five. But the report does show us that the partition has 49MB free, not enough for the WinRE update to complete successfully. The tool I used was MiniTool Partition Wizard Free (at OlderGeeks.com). The full extent of this program is shown in Figure 4.
It’s a tool I’ve mentioned before, most recently in a post from December 2022. That post argues that Microsoft should be providing a built-in tool for partition tasks. That’s brought home even more forcefully as a result of the WinRE update failure. Perhaps Microsoft will finally change its mind and provide such a tool, because Redmond’s solution is not easy to use. Microsoft did provide PowerShell scripts in its support post Updating the WinRE partition on deployed devices to address security vulnerabilities in CVE-2024-20666 (KB5034957); those scripts are clearly intended for IT administrators. But they may require the use of a somewhat obscure process to disable PowerShell security before the script is run, which is far from user-friendly. Because of this complexity, I opted not to attempt the update on my second home PC — I’ll keep KB5034441 blocked. Because BitLocker problems are not likely to affect either of my two PCs, I’d rather wait and demand that Microsoft provide a consumer-friendly resolution to this mess. I should add a personal note about this experience. I’m not easily confused about patches and updates, as you know. I handle IT admin tasks all the time. But I was frazzled by this experience. It was beyond confusing, and it burned at least one full day of my weekend. Then Will spent more time trying to figure out exactly what I was talking about, despite the fact that we’ve written about KB5034441 several times. If we get tangled up like this, what’s the average user to do? There’s more fallout. I have no explanation for why my drive has two recovery partitions. I have no idea how the second one got there, so that means more research. I am not comfortable advising you to resize your partitions. If you click on the wrong thing, you could accidentally delete your entire working hard drive. So I’m still going to strongly recommend that if you are not comfortable with resizing your partitions or using a partition tool to help, skip this update on your Windows 10 PCs. Fortunately, it’s a separate patch — you can use the BlockAPatch tools to hide the update. Don’t worry if you can’t stop the update before it attempts to install. It will do no damage. It will merely attempt to install and fail. That doesn’t mean we can ignore it indefinitely; at some point, a future update may require this one. My hope is that Microsoft will step up between now and then. So why are we patching WinRE, and what is it?
WinRE is the Windows Recovery Environment, which can be used to repair unbootable operating systems. It consists of the core booting elements so you can boot under the operating system. That’s a valid reason for wanting it on your computer. That’s the good thing. The bad thing is that over the years, the recommended size needed for this core OS has changed. If your recovery partition is the last one on your drive, you are all set to adjust its size and give it more room. That’s because you can safely trim the end of the OS partition to come up with the extra space needed for a recovery partition. That task is more difficult when the recovery partition precedes the OS partition. It’s important to remember that updates for WinRE can be included in cumulative updates, as they currently are for Windows 11. When that is the case, and the conditions for the installation of the WinRE update are not met, the entire cumulative update may fail to install. Unfortunately, that means you will eventually need to resize the recovery partition. Again, I’m not recommending that now. When it becomes clear that this is an essential task, and Microsoft has not provided automation that allows mere mortals to apply the fix, I’ll have the details to you promptly. To further reinforce my advice not to resize yet, I used a free partition tool on one of my impacted computers. After it ran, the recovery partition was no longer recognized. I fixed that by extracting WinRE.wim from a Windows 10 ISO, then forcing the system to repair itself with a fairly complex process. I’m not going to describe it because I don’t recommend you try it, but it illustrates the danger associated with the problem. Patching recommendations for consumers
Having the WinRE on your system is wise, because it allows you to repair the booting of the computer. Without it, you will need to reinstall your operating system or restore from an image. So, to repeat: I do not recommend this update for consumers. Just wait. One thing I do recommend is a check of Windows 11 PCs to determine whether BitLocker is enabled. It may have been activated inadvertently. As you may be aware, I purchased a Windows 11 home laptop as a testbed computer. I installed it with the no@thankyou.com trick to get a local user and set it up without a password. BitLocker was not enabled. Then I let someone borrow the machine — who logged in using their Microsoft account. That was enough to trigger drive encryption, with the side effect that their BitLocker key was stored in their Microsoft account. Logging in to check their email on the Web would not trigger encryption, but if they logged in to the Microsoft store or added another Microsoft–account-based user, that would do it. This is a rare occurrence, to be sure. It does happen when a consultant or technician may need apps or tools from the Microsoft store and uses their credentials to get them. Then, after the fact, the owner of the PC may be asked for the BitLocker keys during an update process, all the while insisting that they never enabled BitLocker. That’s why I always urge you to explicitly disable device encryption on a Windows 11 PC — unless you do it deliberately and have made a permanent record of the keys or know they are stored in your Microsoft account. Patching recommendations for businesses
Businesses must review how large the WinRE partition is for the PCs in their firm. Many admins are now recommending 1GB for the recovery partition, as a way of future proofing against update problems. So you’ll need to inventory your PCs to find any that have this problem. Then those PCs must go through the partition-resizing process so that updates will proceed without error. The easiest detection method may be to attempt to install the update and let it fail. But here’s the head-scratcher: This update is pushed only on Windows update, not on WSUS or in the Microsoft catalog site. In short, it’s not IT-friendly, either. I can’t fathom the reason Microsoft would release this update to the very users with the least resources for dealing with it — consumers and very small businesses. If you do plan to roll out this update, remember that for Windows 10, the WinRE fix is separate, whereas in Windows 11 it is included in the cumulative update. While I’ve not seen issues with Windows 11, I have seen issues with Windows 10. For IT pros, I can recommend a PowerShell script named WinRE-Customization by Martin Himken to assist you in rolling it out. Patching recommendations for Apple users
You may think that Apple is without its patching trials and tribulations. You would be wrong. I’ve been following two issues without resolution. First, some Mac users are being pushed to the Sonoma release before they want to install it. Even users in our forums have been complaining about this unwanted push. You can restore back, but not without time and energy. Second, you may have an iPhone that is not giving you the normal texting tone. It’s unclear whether the recent upgrades to iOS 17 are triggering this or whether 17.2.1 will fix the issue. Some have reported turning Bluetooth off or disabling iMessage so that texting will be over SMS. Needless to say, this is frustrating for Apple users. Any time you have an issue with your phone, try to recall whether updates were recently installed. If so, turn your phone off and then on again. Then check the Apple discussions forum, looking for recent complaints. It may not fix your issues, but at least you will know you are not alone. Resources
Susan Bradley is the publisher of the AskWoody newsletters.
The AskWoody Newsletters are published by AskWoody Tech LLC, Fresno, CA USA.
Your subscription:
Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, AskWoody.com, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody Tech LLC. All other marks are the trademarks or service marks of their respective owners. Copyright ©2024 AskWoody Tech LLC. All rights reserved. |
|||||||||||||||||||||