|
In this issue BEN’S WORKSHOP: Finding the Achilles’ heel of TPM Additional articles in the PLUS issue PUBLIC DEFENDER: Social-media apps are killing our kids. Do adults care? MICROSOFT 365: Escape from the clutches of OneDrive ON SECURITY: Security information for an end-of-life operating system is lacking BEN’S WORKSHOP Finding the Achilles’ heel of TPM
By Ben Myers • Comment about this article Eclypsium, a security firm, recently discovered a vulnerability in the system-board firmware supporting the Trusted Platform Mode (TPM) for a wide range of Intel processors. As described by an Eclypsium blog entry, it is “a high impact vulnerability (CVE-2024-0762 with a reported CVSS of 7.5) in the Phoenix SecureCore UEFI firmware that runs on multiple families of Intel Core desktop and mobile processors.” Interpreting further, the modern UEFI (Unified Extensible Firmware Interface) has long replaced the earlier BIOS (Basic Input Output System). Both are sets of hardware instructions burned into the flash memory chip on a system board, and they are responsible for starting up a computer, thereafter establishing communication with all the attached devices. CVE-2024-0762 is an identifier assigned to security vulnerabilities by the Information Technology Laboratory of the National Institute of Standards and Technology (NIST), a federal agency. The CVSS (Common Vulnerability Scoring System) rating of 7.5 makes this vulnerability high, but not critical, on a scale from zero to ten. A rating of 9.0 or above is critical. The NIST dictionary of security vulnerabilities is freely accessible to all. The Mitre Corporation, long a government contractor, maintains a website that shadows the NIST information, as with its CVE entry for this vulnerability. CVE information is also available from Mitre to the public at no charge. An interesting chronology with sounds of silence
Okay! So we have a high vulnerability, but in which families of Intel CPUs? In fact, many families. The Eclypsium webpage identifies the Lenovo ThinkPad X1 Carbon 7th Gen and X1 Yoga 4th Gen, both using the latest Lenovo BIOS updates and found to have the original firmware vulnerabilities. The NIST citation for CVE-2024-0762 was updated on May 29 and includes many families of Intel processors. But it stops short of earlier processor families, such as Intel 4th Gen, that do not meet Microsoft’s requirements for running Windows 11. A Lenovo security webpage has seen regular updates of the information about its list of vulnerable systems across all product lines — desktop, workstation, laptop, and all-in-one computers — starting on May 20 and last updated June 20. A Phoenix Technologies security webpage, dated May 14, states that “Mitigations for CVE-2024-0762 were made available in April of 2024.” Figure 1 shows a rough chronology of events — rough because the various websites do not show absolutely accurate information about when these webpages were created.
I have shown the approximate dates when information about this vulnerability was made public, because I remain perplexed as to why both the computer industry and the wider world of journalism have been so quiet about CVE-2024-0762, which was identified at least two months ago. Maybe the vulnerability is simply too complex for major print and online media to digest and then explain clearly? Phoenix and Lenovo are out in front here, because Phoenix’s credibility is at stake and Lenovo has quickly and diligently identified all its systems with the vulnerability. Other computer players have clammed up — disappointing, given that millions of computers are potentially at risk. Intel and its strategic UEFI partner, Phoenix, have unintentionally created a firmware defect in some of the most intricate computer instructions — ones that need to be absolutely perfect. Intel gets to sit on the sidelines, finger its worry beads and watch. And, yes, this took me more than a few minutes to sort out. What this vulnerability means to all of us
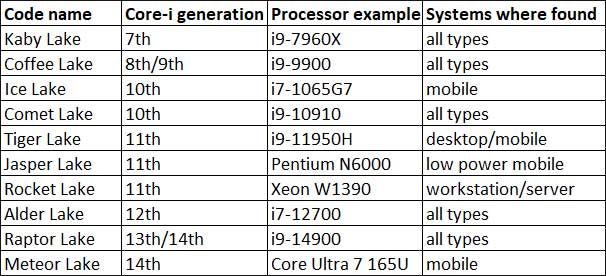
Here is the vulnerability reduced to its simplest terms. NIST states that the vulnerability is present in the last ten families of Intel i-series processors and all their related companion processors including Xeon, Celeron, Pentium, and others. This is an old bug, most likely as old as the very first Phoenix UEFI firmware. For each Intel “Lake” code name, Figure 2 summarizes the Intel i-generation, a processor example, and in which types of systems these processors are found. This table should help all to understand the scope and breadth of the vulnerability.
If you have a system with an Intel CPU in one of these families — and who doesn’t? — what should you do? The reality here is that Phoenix UEFI firmware shows up in millions of computers sold with an Intel processor. American Megatrends International (AMI), with its APTIO and AMIBIOS brands of firmware, is one competitor of Phoenix. Insyde, with its InsydeH2O® UEFI BIOS, is the other. Figure 3 shows but one afflicted chip.
In a world where brand names reach out beyond their own silos to their customers, one would expect statements from other computer brands to allay concerns about a serious vulnerability. They might say, for example, “Our excellent XYZ computers use only InsydeH2O® UEFI BIOS, so our computers are safe.” What you can do and — sometimes — cannot do
Perhaps most important, if your computer has an AMD processor, breathe easy. There is nothing to do. Sorry, Intel. If your computer has AMI APTIO, AMIBIOS, or InsydeH2O® firmware, you are also in the clear. The name of the UEFI firmware is shown when you boot into UEFI or BIOS instead of the operating system. The process usually involves turning the PC on and repeatedly hitting a specific key. The key varies from manufacturer to manufacturer but is often F2, Esc, F10, or Del. A quick Web search will usually provide the right answer for you. Once in, the firmware maker is displayed. If you can’t find the firmware maker this way, ask the manufacturer of your system. You have a right to know, especially with this vulnerability at large. Did you fail both tests above? You’re in the danger zone. I should note at this point that a computer compromised by this vulnerability can be infected only via hands-on access. Make sure all your computers are physically secure from intrusion by others. In a business setting, secure all computers after work hours. Apply a small dose of paranoia to your thinking about letting anyone other than trusted members of your circle touch your computer. If you have any Lenovo computer, head to the Lenovo webpage cited above to find the UEFI firmware update for your system. If you find one, read the accompanying description telling you why the update is important. Download it and install it. Lenovo BIOS updates are as simple and foolproof as possible, as long as you follow the on-screen instructions. For example, do not unplug your computer while the UEFI firmware update is running. Don’t try to do the update during a powerful thunderstorm or hurricane. Basic common sense prevails. For any other brand of computer or motherboard, check with the manufacturer’s website for an UEFI firmware or BIOS update, and proceed as described for Lenovo computers. If an UEFI firmware update is not available for your computer, check the manufacturer’s website again after a few weeks. Check repeatedly until there is an update to mitigate this firmware risk. Applying Phoenix mitigations to branded UEFI firmware, or vice versa, is not a simple task for the name-brand computer or motherboard manufacturer, and the testing required for its firmware update must be comprehensive so that a computer will not fail or become infected in your hands. It may take time for the manufacturer to sort things out. If your computer has an earlier processor not on the list of Intel Lakes above, do not expect an UEFI update. The industry is concerned only about TPM in computers that meet Microsoft Windows 11 requirements, including a very few processors released late in the Intel 7th-gen Kaby Lake epoch. Phoenix UEFI firmware first appeared more or less with the Intel third-generation Ivy Bridge processors, not the earlier second-gen Sandy Bridge processors (a conclusion based upon my quick test of two older laptops). Somewhere along the way, Intel’s generational naming went off the Bridges and into the Lakes. Wait and see
Nobody has stated which generations of UEFI firmware will see updates first. My wild-but-calculated guess says that Phoenix UEFI firmware mitigation will begin with the latest Intel generations of processors and continue on back to older generations, one by one. To date, there are no known reports of in-the-wild exploits of CVE-2024-0762, so we can still rest a bit easy.
For over 20 years, Ben Myers has offered “cradle-to-grave” computer services for small businesses and individual computer owners — including building, upgrading, refurbishing, testing, repairing, and recycling of computer and network gear, primarily with Windows, a bit of MacOS, Linux, and — wait for it — MS-DOS.
The AskWoody Newsletters are published by AskWoody Tech LLC, Fresno, CA USA.
Your subscription:
Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, AskWoody.com, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody Tech LLC. All other marks are the trademarks or service marks of their respective owners. Copyright ©2024 AskWoody Tech LLC. All rights reserved. |
|||||||||||||||||||||||