|
In this issue PUBLIC DEFENDER: Did hackers buy Roku devices — using your credit card? Additional articles in the PLUS issue OFFICE: Understanding Office document formats FREEWARE SPOTLIGHT: SmartContextMenu — Computing for lazy people like me PATCH WATCH: Time for 23H2
PUBLIC DEFENDER Did hackers buy Roku devices — using your credit card?
By Brian Livingston • Comment about this article In a pair of serious security breaches in the past two months, hackers tried username-password combinations found on the Dark Web. They attempted to log on to more than half a million accounts at Roku. Hundreds of users who had unwisely stored their full credit-card numbers with Roku were exploited by the hackers. The victims’ credit-card numbers on file enabled the perps to buy anything in the Roku store. Roku is a large enterprise. The company controls 51% of the global market for streaming-TV products and services, according to an Advanced Television article. With more than 80 million active Roku subscribers around the world, it’s likely that you or someone you know has been affected by the hack or the restrictive measures Roku has imposed to fight off future breaches. A huge target, with hundreds or even thousands of credit cards at risk
Roku revealed the two exploits in a blog post on April 12, 2024. The company also released a data-breach notice that it mailed to the affected subscribers, as required by law (PDF).
With that information — and other details I’ve pieced together from security sources — allow me to explain these two massive data breaches. They could easily affect you and any of your friends who subscribe to Roku or its streaming services:
(Disclosure: I myself used Roku’s streaming-TV operating system for several weeks in 2020. The service was included with my rental of an Airbnb apartment, where my family stayed in between selling one home and moving into another.) Accounts with stored credit-card numbers were sold for 50 US cents
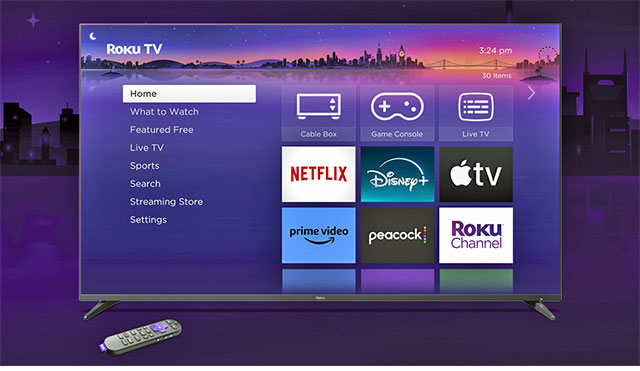
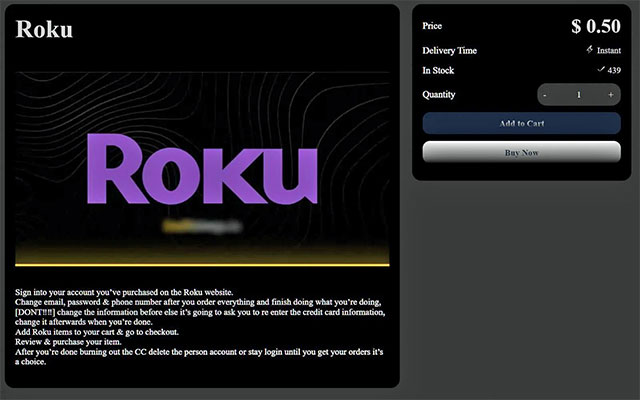
What did the hackers want with hundreds or thousands of accounts that had credit-card numbers stored in Roku’s servers? After all, the CC numbers on file could be used only to buy hardware and services from Roku’s own website. A perp could buy a Roku TV (see Figure 1) or a Streaming Stick 4K (see Figure 3). But you need only one TV to watch whatever you like. It turns out that there are many people around the world who would love to get a free-use credit card. With it, they could buy Roku TVs, streaming sticks, and premium channels such as Netflix, Peacock, and many others. Ethically challenged persons could purchase from the hackers a credential with credit-card privileges for as little as 50 US cents (see Figure 2).
The image in Figure 2 was copied from a Dark Web marketplace that offered stolen Roku CC-enabled credentials and much more. For your purchase price of $0.50, the hackers included a helpful set of instructions on the best way to buy stuff from the Roku store without revealing yourself or alerting the victimized user. Below, I paraphrase the instructions shown in small type in Figure 3. I’ve lightly edited the wording for readability, while retaining some of the hackers’ grammatical errors: Sign in on the Roku website to the account you’ve purchased. Change the user’s email, password & phone number after you order everything and finish doing what you’re doing. DON’T change the information beforehand, or else the site is going to ask you to re-enter the credit card information. Change the info afterwards, when you’re done. Add Roku items to your cart & go to checkout. Review & purchase your items. After you’re done burning through the credit card, delete the person’s account OR stay logged in until you get your orders. It’s your choice. In the second, the hacker’s exhortation to change the legitimate user’s email address, password, and phone number is intended to prevent the victim from receiving any confirmation emails about the bogus purchases. In the final paragraph, the instruction to delete a victim’s entire account after maxing out the stored credit card is pure maliciousness. However, the buyer of the stolen credentials may have purchased several Roku streaming-TV services and wanted to prevent the legitimate subscriber from streaming at the same time. Interestingly, Roku claims that fewer than 400 subscribers were the victims of bogus credit-card charges. But the Dark Web promotion shown in Figure 2 boasts that 439 CC-enabled sign-ins were “in stock.” We may never know the total number of misused accounts. How to protect yourself from credential-stuffing exploits
It’s obvious that weak passwords — and poor security at the websites that allowed their passwords to be hacked — make us vulnerable to hacker sign-in attempts at many sites, not just Roku’s.
To insulate yourself as much as possible from hackers discovering your username and password and signing in as you at various websites, take the following steps:
Our passwords don’t all have to be ‘123456’
It’s a fact of our modern, silicon lifestyles that hackers are assembling faster and faster computers to crack our credentials. Unfortunately, more and more of our accounts are protected only by a username and a password, which can be broken by determined criminals.
The most common password people choose is 123456, according to a Wikipedia article. We’re far past the point that such trivial strings will defend our finances against intruders. In this column, I’ve tried to give you the armor you need to protect yourself and your loved ones — and your credit cards. Stay safe out there!
The PUBLIC DEFENDER column is Brian Livingston’s campaign to give you consumer protection from tech. If it’s irritating you, and it has an “on” switch, he’ll take the case! Brian is a successful dot-com entrepreneur, author or co-author of 11 Windows Secrets books, and author of the fintech book Muscular Portfolios.
The AskWoody Newsletters are published by AskWoody Tech LLC, Fresno, CA USA.
Your subscription:
Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, AskWoody.com, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody Tech LLC. All other marks are the trademarks or service marks of their respective owners. Copyright ©2024 AskWoody Tech LLC. All rights reserved. |
||||||||||||||||||||||||||||