|
BEN’S WORKSHOP: Finding the Achilles’ heel of TPM PUBLIC DEFENDER: Social-media apps are killing our kids. Do adults care? MICROSOFT 365: Escape from the clutches of OneDrive ON SECURITY: Security information for an end-of-life operating system is lacking BEN’S WORKSHOP Finding the Achilles’ heel of TPM
By Ben Myers • Comment about this article Eclypsium, a security firm, recently discovered a vulnerability in the system-board firmware supporting the Trusted Platform Mode (TPM) for a wide range of Intel processors. As described by an Eclypsium blog entry, it is “a high impact vulnerability (CVE-2024-0762 with a reported CVSS of 7.5) in the Phoenix SecureCore UEFI firmware that runs on multiple families of Intel Core desktop and mobile processors.” Interpreting further, the modern UEFI (Unified Extensible Firmware Interface) has long replaced the earlier BIOS (Basic Input Output System). Both are sets of hardware instructions burned into the flash memory chip on a system board, and they are responsible for starting up a computer, thereafter establishing communication with all the attached devices. CVE-2024-0762 is an identifier assigned to security vulnerabilities by the Information Technology Laboratory of the National Institute of Standards and Technology (NIST), a federal agency. The CVSS (Common Vulnerability Scoring System) rating of 7.5 makes this vulnerability high, but not critical, on a scale from zero to ten. A rating of 9.0 or above is critical. The NIST dictionary of security vulnerabilities is freely accessible to all. The Mitre Corporation, long a government contractor, maintains a website that shadows the NIST information, as with its CVE entry for this vulnerability. CVE information is also available from Mitre to the public at no charge. An interesting chronology with sounds of silence
Okay! So we have a high vulnerability, but in which families of Intel CPUs? In fact, many families. The Eclypsium webpage identifies the Lenovo ThinkPad X1 Carbon 7th Gen and X1 Yoga 4th Gen, both using the latest Lenovo BIOS updates and found to have the original firmware vulnerabilities. The NIST citation for CVE-2024-0762 was updated on May 29 and includes many families of Intel processors. But it stops short of earlier processor families, such as Intel 4th Gen, that do not meet Microsoft’s requirements for running Windows 11. A Lenovo security webpage has seen regular updates of the information about its list of vulnerable systems across all product lines — desktop, workstation, laptop, and all-in-one computers — starting on May 20 and last updated June 20. A Phoenix Technologies security webpage, dated May 14, states that “Mitigations for CVE-2024-0762 were made available in April of 2024.” Figure 1 shows a rough chronology of events — rough because the various websites do not show absolutely accurate information about when these webpages were created.
I have shown the approximate dates when information about this vulnerability was made public, because I remain perplexed as to why both the computer industry and the wider world of journalism have been so quiet about CVE-2024-0762, which was identified at least two months ago. Maybe the vulnerability is simply too complex for major print and online media to digest and then explain clearly? Phoenix and Lenovo are out in front here, because Phoenix’s credibility is at stake and Lenovo has quickly and diligently identified all its systems with the vulnerability. Other computer players have clammed up — disappointing, given that millions of computers are potentially at risk. Intel and its strategic UEFI partner, Phoenix, have unintentionally created a firmware defect in some of the most intricate computer instructions — ones that need to be absolutely perfect. Intel gets to sit on the sidelines, finger its worry beads and watch. And, yes, this took me more than a few minutes to sort out. What this vulnerability means to all of us
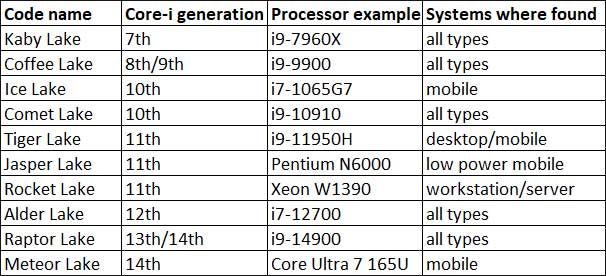
Here is the vulnerability reduced to its simplest terms. NIST states that the vulnerability is present in the last ten families of Intel i-series processors and all their related companion processors including Xeon, Celeron, Pentium, and others. This is an old bug, most likely as old as the very first Phoenix UEFI firmware. For each Intel “Lake” code name, Figure 2 summarizes the Intel i-generation, a processor example, and in which types of systems these processors are found. This table should help all to understand the scope and breadth of the vulnerability.
If you have a system with an Intel CPU in one of these families — and who doesn’t? — what should you do? The reality here is that Phoenix UEFI firmware shows up in millions of computers sold with an Intel processor. American Megatrends International (AMI), with its APTIO and AMIBIOS brands of firmware, is one competitor of Phoenix. Insyde, with its InsydeH2O® UEFI BIOS, is the other. Figure 3 shows but one afflicted chip.
In a world where brand names reach out beyond their own silos to their customers, one would expect statements from other computer brands to allay concerns about a serious vulnerability. They might say, for example, “Our excellent XYZ computers use only InsydeH2O® UEFI BIOS, so our computers are safe.” What you can do and — sometimes — cannot do
Perhaps most important, if your computer has an AMD processor, breathe easy. There is nothing to do. Sorry, Intel. If your computer has AMI APTIO, AMIBIOS, or InsydeH2O® firmware, you are also in the clear. The name of the UEFI firmware is shown when you boot into UEFI or BIOS instead of the operating system. The process usually involves turning the PC on and repeatedly hitting a specific key. The key varies from manufacturer to manufacturer but is often F2, Esc, F10, or Del. A quick Web search will usually provide the right answer for you. Once in, the firmware maker is displayed. If you can’t find the firmware maker this way, ask the manufacturer of your system. You have a right to know, especially with this vulnerability at large. Did you fail both tests above? You’re in the danger zone. I should note at this point that a computer compromised by this vulnerability can be infected only via hands-on access. Make sure all your computers are physically secure from intrusion by others. In a business setting, secure all computers after work hours. Apply a small dose of paranoia to your thinking about letting anyone other than trusted members of your circle touch your computer. If you have any Lenovo computer, head to the Lenovo webpage cited above to find the UEFI firmware update for your system. If you find one, read the accompanying description telling you why the update is important. Download it and install it. Lenovo BIOS updates are as simple and foolproof as possible, as long as you follow the on-screen instructions. For example, do not unplug your computer while the UEFI firmware update is running. Don’t try to do the update during a powerful thunderstorm or hurricane. Basic common sense prevails. For any other brand of computer or motherboard, check with the manufacturer’s website for an UEFI firmware or BIOS update, and proceed as described for Lenovo computers. If an UEFI firmware update is not available for your computer, check the manufacturer’s website again after a few weeks. Check repeatedly until there is an update to mitigate this firmware risk. Applying Phoenix mitigations to branded UEFI firmware, or vice versa, is not a simple task for the name-brand computer or motherboard manufacturer, and the testing required for its firmware update must be comprehensive so that a computer will not fail or become infected in your hands. It may take time for the manufacturer to sort things out. If your computer has an earlier processor not on the list of Intel Lakes above, do not expect an UEFI update. The industry is concerned only about TPM in computers that meet Microsoft Windows 11 requirements, including a very few processors released late in the Intel 7th-gen Kaby Lake epoch. Phoenix UEFI firmware first appeared more or less with the Intel third-generation Ivy Bridge processors, not the earlier second-gen Sandy Bridge processors (a conclusion based upon my quick test of two older laptops). Somewhere along the way, Intel’s generational naming went off the Bridges and into the Lakes. Wait and see
Nobody has stated which generations of UEFI firmware will see updates first. My wild-but-calculated guess says that Phoenix UEFI firmware mitigation will begin with the latest Intel generations of processors and continue on back to older generations, one by one. To date, there are no known reports of in-the-wild exploits of CVE-2024-0762, so we can still rest a bit easy.
For over 20 years, Ben Myers has offered “cradle-to-grave” computer services for small businesses and individual computer owners — including building, upgrading, refurbishing, testing, repairing, and recycling of computer and network gear, primarily with Windows, a bit of MacOS, Linux, and — wait for it — MS-DOS. PUBLIC DEFENDER Social-media apps are killing our kids. Do adults care?
By Brian Livingston • Comment about this article Rates of suicide and self-harm among teens and preteens in the US and other countries have doubled, tripled, and even quintupled in the past dozen years. Now we may finally know why. An explosive front-page article in The Wall Street Journal on June 21, 2024, revealed that Instagram — with more than 2 billion monthly active users — feeds disturbing videos to viewers who register as minors. The website’s Reels stream, the newspaper said, feeds to teenagers three times as many sex videos as it sends to adults over the age of 30, 1.7 times as much violence, and 4.1 times as much bullying. In extensive testing from January to June, the Journal and computer-science assistant professor Laura Edelson of Northeastern University registered numerous accounts, identifying themselves in profiles as 13-year-old users. Each account was then used to monitor Instagram’s media feed. The study’s testers were instructed to skip past most clips but watch to the end those videos that included any female character. Within 30 minutes, the accounts configured as age 13 “began being served video after video about anal sex,” the Journal reported.
A separate story — headlining page one of The New York Times on June 24, 2024 — charged that Mark Zuckerberg, the CEO of Instagram parent Meta Platforms, has declined since 2019 to fund software engineers who wanted to address “problematic use/addiction and teens.” Meta is currently being sued by the attorneys general of 45 US states as toxic to children. Perhaps surprisingly, neither the Journal nor the Times found the same problems with TikTok or Snapchat that were typical of Instagram. That doesn’t mean every social-media company is blameless. It could just mean similar algorithms weren’t detected by these particular studies. It’s not just X-rated videos that drive social-media users to despair
The US Surgeon General, Dr. Vivek Murthy, said in an op-ed on June 17, 2024, “Legislation from Congress should shield young people from online harassment, abuse and exploitation and from exposure to extreme violence and sexual content that too often appears in algorithm-driven feeds.” He categorized it as an emergency: “Adolescents who spend more than three hours a day on social media face double the risk of anxiety and depression symptoms.” In an Education Week report, Murthy called youth mental health “the defining public-health crisis of our time.” As shown in Figure 1, suicides by US girls aged 10 to 14 now represent more than 2 per 100K population. For boys, the rate is more than 3 per 100K. Girls and boys aged 15 to 19 (not shown) are committing suicide at even higher rates: 5 and 16 per 100K. For comparison, heroin overdoses at all ages in 2022 represented only 1.8 deaths per 100K (National Institute on Drug Abuse statistics page). Why would Instagram or any other social-media site program an algorithm to feed hardcore sex videos and violent content more often to 13-year-olds than to adults? Here’s a possible answer: because it works. As Murthy explained in a Guardian interview:
The surgeon general compares today’s anything-goes social-media apps to manufacturers who sold cars with no seat belts, airbags, or other safety features before they were required by law. As Alexander Tin reported in a CBS News segment on February 13, 2023: Around 1 in 3 high school girls in the US have seriously considered attempting suicide, according to new results from a Centers for Disease Control and Prevention survey from 2021, up from less than a fifth of teen girls in 2011. And more than half of teen girls, 57%, reported feeling “persistently sad or hopeless” — a record high number.
Both boys and girls are stressed by threats and pressure
Young males aren’t immune to social-media dangers. There’s been a massive increase since 2020 in the number of boys who’ve fallen victim to “sextortion,” according to NBC News coverage. The unfortunate youths had been persuaded to send nude photos of themselves to someone posing as a teen who wanted a relationship. But the hotties turned out to be hackers who blackmailed the boys, saying the images could be sent via Instagram or other media to their parents, principals, and other figures of authority. In some cases, the “nudes” were merely AI-generated fakes — but they can still subject worried teens to existential crises. In the US, FBI special agent Mark Civiletto estimated in an ABC News story that “well over 100,000 cases” of sexploitation occurred in 2022, only 7,000 of which were reported. Numerous suicides have resulted from these humiliating and threatening situations, he added. Meanwhile, teenage girls often feel they can never be as beautiful, buxom, or popular as the adult women they see in social-media feeds. The result is often depression — or worse.
The photo at left (from a Wikipedia article) shows the healed scars of a distressed young woman who was treated in an emergency room after making shallow cuts on her arm — an example of intentional but nonsuicidal self-harm. According to a presentation by Vanessa Horta, a North Carolina–based filmmaker and media producer, 1 in 5 teen girls and 1 in 7 teen boys in the US commit self-harm including cutting, burning, or bruising themselves. Why would tweens or teens cut or burn their arms? I’m a few years past teenage status myself, but I clearly remember what a horrible pressure cooker middle-school and high-school life was. And that was way back in prehistoric times (before social media controlled billions of eyeballs). Kids who resort to self-harm are feeling hyperstressed, overwhelmed, numb, lost, disconnected, or unreal, according to an analysis by LifeSIGNS, a British charity. Injuring oneself may give a teen or preteen a feeling of relief, being in control, or even just being able to function. But is it truly social media that’s making young persons overstressed? Today’s huge rise in teen suicides and self-harm could merely be what adults have always called “kids these days.” Rather than speculate on just how depressed young people may be, let’s use an objective measure: the number of teens and preteens who harm themselves so badly that they must be rushed to an emergency room. (See Figure 3.)
Jean Twenge — a San Diego State University psychology professor and the author of several books about young people’s use of social media — wrote on June 19, 2024, in the Institute for Family Studies blog: Since 2009, more than twice as many 15- to 19-year-old girls and young women have been admitted to the ER for self-harm behaviors in the U.S. Even more shocking, five times more 10- to 14-year-old girls were admitted to the ER for self-harm in 2022 than in 2009 … . That’s 5 times more families taking their 4th to 9th grade daughters to the hospital because they have intentionally harmed themselves. The relationship between social media and harm shows evidence of cause and effect, not simply coincidence. Instagram launched on October 6, 2010. Within just its first 24 hours, the app garnered 25,000 signups, an astonishing uptake, according to a Britannica history. With its 2 billion users today, Instagram’s impact is monumental. Twenge herself has examined 13 possible origins — other than social media — for the “mental health crisis” of today’s Internet users. Pundits have proposed that students now live in fear of school shootings, or suffer from excessive homework, or are depressed by climate change. But Twenge shows in her analysis that none of these correlates in any way to the rise of youth depression and self-harm. Her work has been repeated and confirmed in a Zach Rausch article, a Jon Haidt blog post, and by several other researchers. Their studies show that depression and suicides are rising in many Western countries, not just the US. (Rausch and Haidt both contribute to a substack named After Babel, a follow-up to a book with the same title, says The Fulcrum Newsletter.) The emergency is real. Based on 2024 Gallup polling of every major country in the world, youthful North Americans now report being less happy than those over 60. “In many but not all regions, the young are happier than the old,” explains a summary. “But in North America happiness has fallen so sharply for the young that they are now less happy than the old.” Today, the US and Canada have the second- and third-largest gaps of any country in the world between their indexes of youthful misery and elderly satisfaction, according to a Visual Capitalist article. Bummer, dude. Will anyone actually do anything about ‘the crisis of our time’?
In addition to the lawsuits by the 45 states mentioned above, a campaign has been started by more than 250 grieving parents who lost children as young as 8 to suicide, adulterated substances, and more. In February 2024, they placed a full-page ad in the Journal addressed to US Senate Majority Leader Chuck Schumer. The group, Parents for Safe Online Spaces (ParentsSOS), implores Congress to pass a Kids Online Safety Act. It would require social-media companies to rein in sexploitation, bullying, violent content, and other harmful content. More information is available at the ParentsSOS website. While awaiting legislative action, school districts scattered across some 21 countries have banned smartphones during classroom time. Many of these educational institutions require students’ phones to be secured in a locking fabric pouch called Yondr, as an Axios article describes. (The pouches don’t interfere with message reception.) At the end of the school day, teachers unlock everyone’s pouches. This approach is endorsed by the new Phone-Free Schools Movement (website). The pouches are also favored by musicians and other performers who ban calls and photos during their gigs. If you or someone you know has suicidal feelings, call or text 988 in the US or Canada for confidential support. To find the number in other countries, see a listing by OpenCounseling. Just as there was an era when people died because cars lacked seat belts, we now live in a time when the addictive drug known as social media lacks common-sense protections for mental health. I wish I could say that the solution will come quickly. But if we do nothing, the world’s kids will soon become even more stressed and depressed than they already are today.
The PUBLIC DEFENDER column is Brian Livingston’s campaign to give you consumer protection from tech. If it’s irritating you, and it has an “on” switch, he’ll take the case! Brian is a successful dot-com entrepreneur, author or co-author of 11 Windows Secrets books, and author of the fintech book Muscular Portfolios. MICROSOFT 365 Escape from the clutches of OneDrive
By Peter Deegan • Comment about this article Saying that Microsoft pushes OneDrive on customers is putting it mildly. It’s more like ramming OneDrive down the throats of customers by means of all those many direct and passive-aggressive tricks. I’ll explain how OneDrive, as well as other cloud and email stores, is reorienting how we think about computer storage. I’ll discuss how Windows changes when OneDrive is enabled, and how to undo it. Finally, I’ll show how to get the best of both worlds by making a mixed — cloud and local — file-storage system. OneDrive: the central location for all files
Those of us who have been around computers for a long time think of our computer as the main store for everything (docs, files, photos, and so forth), with the cloud and other locations as offshoots. But with the cloud, we must reorient our thinking not — only for files but also for email, calendars, and contacts. In this new paradigm, the main store is online (in the cloud), with copies on computers and devices. It’s the reverse of how we’ve done things for decades. And it applies to all major cloud stores – OneDrive, Dropbox, Google Drive, and others.
OneDrive lets you choose what is synchronized to each device. Files and folders can be copied (synchronized) to a device for offline use or left as a placeholder file until needed, via an “on-demand” download. An entire online folder can be hidden from a local computer. Microsoft is pushing OneDrive in Windows
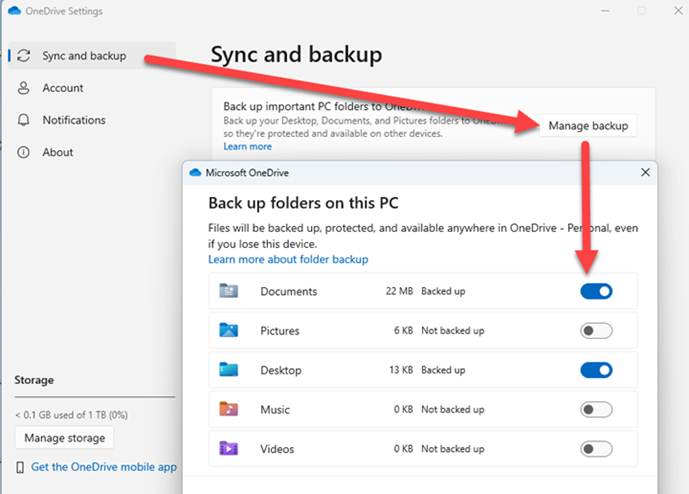
If you set up OneDrive in Windows, it will likely change some “Known folders” to sync with OneDrive. In my recent tests, it did this without any warning, much less asking! Known folders is what Microsoft calls Desktop, Documents, Downloads, Pictures, Music, and Videos. Go to Explorer Home to see where Windows is storing files (Figure 2), which is how a new Windows 11 PC plus OneDrive is automatically configured.
The Desktop, Documents, and Pictures folders are set to be synced to OneDrive. The name “OneDrive” doesn’t appear — just the first name on the OneDrive account (“Van,” in this case) — plus the type of OneDrive account (Personal or Business). The outlined cloud icons mean files are downloaded to the computer when needed (“on demand”). “Stored locally” means files are saved to that computer only. Change back to local folder
To move a Known folder from OneDrive back to local storage only is quite simple, but not in a location you might expect. In OneDrive settings, select Sync and backup | Manage backup. See Figure 3.
Note Microsoft’s little wording trick — calling this option “backup,” as if it’s the only backup option available on Windows. Changing any Known folder to “Not backed up” will actually change the folder location back to its usual local folder under \users\<user name>\. For locally saved Known folders, you can check the folder used by right-clicking the folder, clicking Properties, and then clicking the Location tab. See Figure 4.
That’s the simple “all or nothing” answer. But the real world isn’t that simple. Mixed OneDrive and local storage
There’s a way to have the best of both worlds — a mixed or hybrid setup with some files on OneDrive and others (the majority) stored on the local computer. OneDrive can be extremely useful for sharing files among your devices and with other people. And it can provide other benefits. But it’s not suitable for all files, no matter what Microsoft says. There are many documents I do not want placed into cloud storage, for legitimate concerns about putting private or confidential information online. Microsoft had its own troubles with hackers stealing customers’ data earlier in 2024. I mostly use OneDrive to share documents with myself on my various devices. Some pictures are good to have online for various reasons (such as the invaluable Camera Roll), but my main image and video storage could overwhelm the OneDrive quota. Note: My locally stored files have backups, naturally. Windows File History is always there, with key folders synced across devices directly, using Resilio Sync. Now set up the Quick Access list to pin both folders, in this case Documents. Right-click on the OneDrive folder and choose Pin to Quick access. See Figure 5.
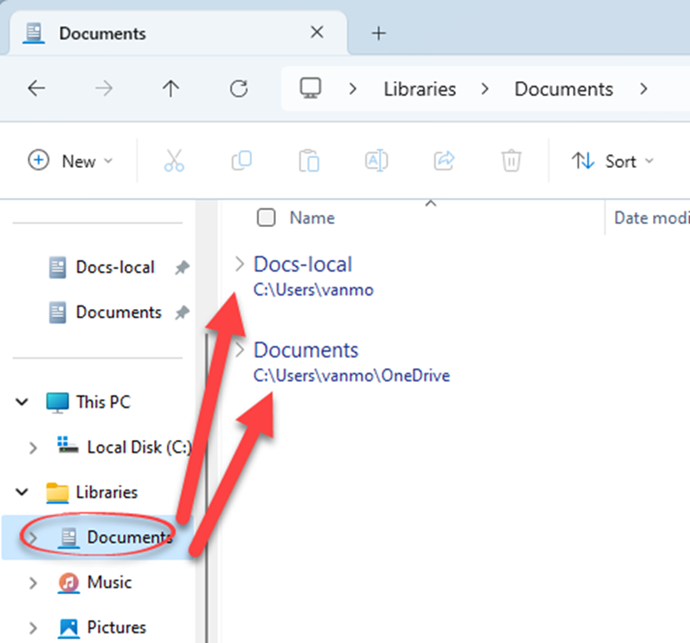
Having two folders with the same name can be confusing, so I usually change the local-folder name to “Docs-local.” Navigate to c:\users\<user name>\, then right-click on the Known folder and choose Rename (Figure 6). Most likely you’ll have to sign out of Windows, then log in again to make the name change appear in the Quick Access list.
It’s safer to rename the local folder, because trying to rename the OneDrive folder might have unintended consequences. Use Libraries
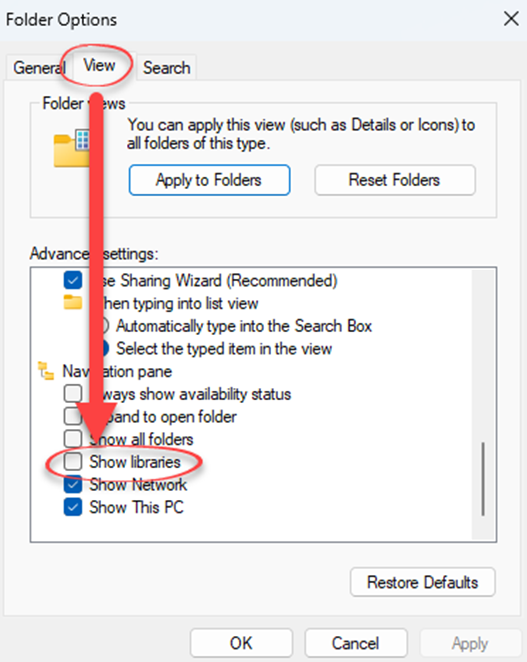
Libraries provide a way to bring multiple folders together into a single view for searches and also trigger backups via File History. Microsoft used to promote the use of Libraries, until it conflicted with its strategy of getting customers to save everything in one place, namely OneDrive. Libraries don’t suit Microsoft’s latest corporate agenda, so it’s hidden the feature in Explorer. The first thing to do is reveal Libraries in Explorer Options. Select the View tag and under Navigation pane, check Show Libraries. See Figure 7.
There’s a Library to match each of the Known folders (you can make more). Each Library can be linked to multiple folders, in this case both Documents folders — local and OneDrive.
In Microsoft Office
Modern Office defaults to saving via OneDrive, if available. Change that by going to File | Options | Save | Save to Computer by default. This setting is applied to all Office apps, though that’s not clear in the dialog (Figure 9). Of course, you can choose another folder for any document.
The Office AutoSave scam
Microsoft uses every trick it can think of to push people into storing everything on its OneDrive storage system. One of the most annoying and unjustified is the crippling of AutoSave. AutoSave is a feature to regularly save the file as you’re working. In Microsoft 365 (Windows or Mac) and Office 2021, it’s available only to documents saved on OneDrive. There’s no good technical reason for that limitation. Microsoft has done it just to push customers into saving on OneDrive. Just in case you don’t get the unsubtle hint, there’s an unnecessarily large label with a slider on the Quick Access Toolbar. If you try to turn on Autosave for a locally saved file, there’s a prompt to choose a OneDrive location.
Local vs. OneDrive isn’t the binary choice that Microsoft is selling to their customers. A smarter way is to save to OneDrive only the files that need it, leaving the rest on your computer.
Peter Deegan is the author of Windows 11 for Microsoft Office Users, Microsoft 365 for Windows: Straight Talk, Eye-Catching Signs with Word, Christmas Cheer with Office, and others. He has been the co-founder and editor in chief of the Office Watch site and newsletters since they started in 1996. ON SECURITY Security information for an end-of-life operating system is lacking
By Susan Bradley • Comment about this article Lately, I’ve been working on painting the trim on my house. We have old-fashioned caulked windows. To make sure that the caulk doesn’t crack with the weather, maintenance is required. That means painting. I like doing it because it gets me off the computer and thinking of other things. Painting the house is great for appearances and — more importantly — protects it from weather and other damage. I’ve been concerned about how the security industry has changed over the years. It is not giving the best information to people using everyday technology, especially if that tech is a bit older. There is far too much attention-getting clickbait masquerading as headlines. Just as Ctrl+Alt+Del was a common remedy more than a decade ago, contemporary advice seems to have morphed into turning on automatic updates without acknowledging that side effects can be riskier than the vulnerabilities themselves. Often it calls for backups — not of your entire systems but only of your data. Manufacturers are building in obsolescence and reducing reparability. And the latest trend? AI, of course. It’s being pushed into everything, usually without our permission and often in ways difficult to remove. I could move into a new house with freshly painted trim, but I like where I live. Why should I move my technology just, because I’m told that the trim is brighter? Anything wrong with painting my own trim? Getting vendors to explain precisely how a vulnerability can be exploited is sometimes difficult. It’s useful to know that because a long-standing theory maintains that attackers can code up exploits in a matter of minutes — and do the same after a given vulnerability has been patched. But here’s an important question: Just because an exploit has been discovered, does that mean it’s actually being used in active attacks? We don’t get many answers to that sort of question. I’m not saying fixing the exploits is a waste of time. It’s necessary. It would just be nice to easily understand what’s going on. We’re a year away from the end of the road for Windows 10. Many of you must determine the true risk of continuing with it. Will Microsoft tell us, clearly, how the update strategies for Windows 10 and Windows 11 differ? Will Windows 10 gradually become more vulnerable than Windows 11? Just the other day, I spotted the YouTube video What happens if you connect Windows XP to the Internet in 2024? Eric Parker wondered how fast such a PC would be compromised. The video garnered many views and was cited in — you guessed it — clickbait headlines. I don’t want to spoil it for you, because it’s sometimes interesting to check out this sort of thing, but I noticed a problem — he turned off the firewall. That’s not a real-world scenario. Most of us would have the Windows firewall turned on, would perhaps have set up a firewall on our gateway, and would most definitely be behind the firewall of our Internet service provider (ISP). And there’s another quiet thing. Despite the fact that XP, Vista, 7, and 8 are well out of support, sometimes Microsoft will release a patch anyway if the vulnerability could be massively disruptive. I don’t anticipate that Microsoft will start releasing vulnerability notices for Windows 10. It will be on us to make inferences from the Windows 10 extended updates that are released as well as from watching vendors such as 0patch, who will support Windows 10 for at least five years. What’s the risk?
Many ask me about the risk of running an operating system without updates. You know what I’m about to say: it depends. For example, suppose a system is completely off the grid? Part of our own Ben Myers’s business involves repair and update of process-control systems running very old software. In such cases, the status quo ante is vastly more important than the risk of an OS change that breaks the software. Then there’s the fact that some updates fix bona fide security issues, yet others proactively roll out feature updates. Sometimes those updates fix security issues, sometimes the updates proactively roll out changes to the operating system. Ignoring updates can create Internet-connectivity issues. For example, build a Windows XP (or even Windows 7) PC from scratch, and I guarantee that you will have to jump through many hoops to get it connected. Why? Because over time, Microsoft has changed the base security protocol. TLS 1.1 and 1.2 are now the de facto standards for connecting to the Web, assuring that money transactions and other sensitive interactions will remain secure. Yet those versions of TLS were not the default in Windows XP and 7. The computer would boot and be useful for local work, but it would have been very unwise to use either for surfing. Similarly, Windows 10 will continue to work into the near future, after its official end of life. But inevitably, sooner or later there will be something new in accepted security profiles, the way the Web works (Web 3.0? 4.0?), or the way financial transactions are handled. If such things require any sort of major work on Windows 10, you should assume it won’t happen. And once updates stop for good, things that you expected to work forever, such as printing, go all goofy on you. Just last month, Microsoft released fix for a Wi-Fi vulnerability (CVE-2024-30078). After reading articles on the Web (some behind clickbait headlines), you might have thought that we had a worm and we should immediately patch. Microsoft didn’t help by informing us how to analyze the risk. Instead, Redmond put out vague phrases such as “Exploiting this vulnerability requires an attacker to be within proximity of the target system to send and receive radio transmissions” and “An unauthenticated attacker could send a malicious networking packet to an adjacent system that is employing a Wi-Fi networking adapter, which could enable remote code execution.” Some theorized that the vulnerability was so severe that merely scanning for an SSID will be enough to compromise systems. Microsoft still hasn’t added any useful information, including additional guidance to help us determine how vulnerable we really are. In the absence of good guidance from the Pacific Northwest, it’s no surprise that many would rely on headlines such as Update Now! New Windows Wi-Fi Flaw Lets Hackers Infiltrate Your PC Without You Even Clicking Anything. However, a researcher on X investigated, narrowing down the true risk of the vulnerability. He stated: You need to share the same network as the target, need to brute force a specific memory layout, and still need extra information to perform anything other than a DoS. Why couldn’t Microsoft tell us that? You’d think they’d know. What about the cloud?
Microsoft announced that it will be releasing vulnerability information for Cloud services. As the company noted just the other day: In the past, Cloud service providers (CSPs) refrained from disclosing information about vulnerabilities found and resolved in cloud services, unless customer action was required. The common understanding was that if the customer didn’t need to install updates then no additional information was necessary to help them stay secure. However, as the industry matures, we recognize the value of transparency. Therefore, we are now announcing that we will issue CVEs for critical cloud service vulnerabilities, regardless of whether customers need to install a patch or to take other actions to protect themselves. There will be a new column in the Security Update Guide Vulnerabilities tab to indicate whether customer action is required. Apple vulnerabilities
Apple is another vendor that often doesn’t release detailed information about vulnerabilities until a later date. It’s important to remember that if you are a politician, journalist, or other public figure, attacks via smartphones (including Android) are targeted at you. The rest of us, not so much. We lesser mortals are more likely to be tricked by scam text messages or phishing. And in some cases, such as the recent vulnerability (CVE-2024-27867) with Apple AirPods, the risk is low because they are automatically updated when paired, reducing the likelihood of compromise. Edge vulnerabilities
I don’t mean the browser here; I mean the generic term for devices at the “edge” of your network (home or business) that connect you to the Internet and usually provide intrusion protection. More and more attackers are able to exploit the edge to launch attacks against businesses. If you visit CISA’s Known Exploited Vulnerabilities Catalog, you will find many examples of vulnerabilities in D-Link equipment. I urge consumers and businesses alike to focus more attention on the edge, especially because it tends to be out of sight and thus out of mind. If your edge devices are your own, work with the vendor to make sure firmware is up to date. Consumers have less flexibility, but you may have noticed that occasionally your gateway router goes offline for a brief period. Sometimes that’s due to electrical problems, but sometimes updates are being delivered. If you have any concerns about the state of security with a gateway router, discuss it with your ISP. Sometimes, a newer model is available and can be swapped out (by you) for free. Businesses should also review the firewall rules. Ensure that there are no misconfigurations or additional ports that have inadvertently opened up. Checklist:
Bottom line: Review your edge devices and ensure they are not only up to date, but also configured as you intend them. It pains me to say that no vendor these days is giving good, current, and actionable information. They seem content to allow all that scary clickbait, without challenge or other response. This is not an idle matter; we all rely upon the vendors to help us make good decisions regarding risks to our devices, especially when they are older. I’m hoping that, as more and more devices reach end of life, security news providers will increasingly step up to the plate and provide this vital information that is currently lacking. You can be sure that I’ll be doing my best to provide actionable intelligence.
Susan Bradley is the publisher of the AskWoody newsletters. The AskWoody Newsletters are published by AskWoody Tech LLC, Fresno, CA USA.
Your subscription:
Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, AskWoody.com, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody Tech LLC. All other marks are the trademarks or service marks of their respective owners. Copyright ©2024 AskWoody Tech LLC. All rights reserved.
|