
|
Patch reliability is unclear. Unless you have an immediate, pressing need to install a specific patch, don't do it. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
Ending UAC headaches, once and for all
In this issue
- TOP STORY: Ending UAC headaches, once and for all
- LANGALIST PLUS: PC crashes when waking from sleep mode
- LOUNGE LIFE: Diagnosis: It just might take a village
- WACKY WEB WEEK: Canadian bear cub takes an interest in golf
- BEST SOFTWARE: Taking another look at Microsoft's Outlook.com
- PATCH WATCH: A heaping helping of Windows and Office updates
Ending UAC headaches, once and for all
Windows’ User Account Control (UAC) helps keep us safe from unwanted system changes — but it can also get in the way of routine operations.
With the right tools and techniques, you can fine-tune UAC so that commonly used programs don’t trigger UAC prompts.
By controlling UAC on an application-by-application basis, you’ll no longer be bothered by unnecessary alerts, but it will still warn you when it should!
A review of UAC’s intents and limitations
Microsoft introduced User Account Control in Vista, and it’s been part of every version of Windows since Vista (including, so far, Windows 10). Simply put, UAC alerts you whenever a potentially significant change is about to be made to your PC or its settings. Its basic task is to protect against malware or system changes that could give a hacker access to your local data.
UAC is a good concept, but it got off to a rocky start. In Vista, its too-frequent warnings irritated users, contributing to the general distaste for that version of Windows. In fact, Vista’s UAC became the central joke in one of the famous “I’m a PC/I’m a Mac” TV ads (YouTube video) featuring John Hodgman and Justin Long.
Adding to UAC’s early woes, the tool had notoriously few user controls. For example, Vista Starter, Home Basic, and Home Premium allow only one all-or-nothing choice (shown in Figure 1): turn UAC on or off! (For more on this limited version of UAC, check out the related MS Windows help page.)
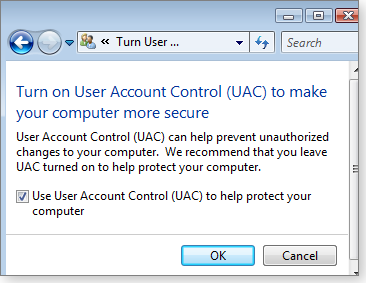
Figure 1. In consumer versions of Vista, the UAC setting is limited to just on or off.
Vista Business, Enterprise, and Ultimate offer a bit more UAC flexibility, but making adjustments isn’t easy. For the details, see the “Scenario 3: Configure User Account Control” subsection in the MS TechNet article, “User Account Control step-by-step guide,” and the TechNet reference pages, “Understanding and Configuring User Account Control in Windows Vista.”
Given Vista’s UAC limitations, it’s no surprise that third-party vendors filled the void with simple utilities. For example, WinAbility’s TweakUAC (Figure 2) adds a quiet mode that helps reduce the number of UAC alerts. TweakUAC (info page) is free, but you’ll have to provide a valid email address and agree to receive marketing emails from WinAbility.
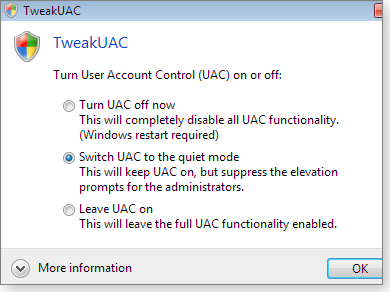
Figure 2. Third-party tools such as TweakUAC enhanced Vista's basic UAC on/off choices.
With Windows 7, Microsoft took into account the many complaints from Vista users about UAC. The company made UAC more flexible and less prone to unnecessary alerts. In both Win7 and Win8, UAC offers four levels of sensitivity, ranging from full off (“Never notify me”) to full on (“Always notify me”). The four levels are briefly described within the UAC control itself (see Figure 3) and are discussed more fully in the Windows information page, “What are User Account Control settings?”
To access Win7/8’s UAC controls, open Control Panel and type “uac” into its search box; then click the Change User Account Control settings link.
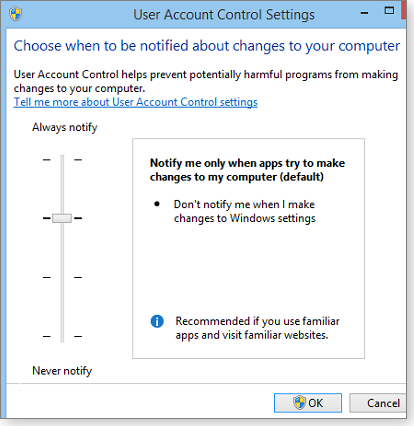
Figure 3. Win7's and Win8's four levels of UAC sensitivity
Win7’s and Win8’s UAC is an improvement over Vista’s, but it still has a glaring omission: all UAC settings are system-wide — they affect all software the same way. You can’t, for instance, disable UAC for one program you know is safe but leave it enabled for everything else.
If you want to adjust UAC activity on a per-application basis, you have to make some system adjustments or install additional free software.
Tuning UAC, application by application
Typically, I’d begin a how-to by showing the standard Windows method. But the built-in steps for making application-by-application UAC changes are rather convoluted. So I’ll start with a far simpler and easier way to modify UAC behavior — using free, third-party, add-on tools.
Winaero.com’s ElevatedShortcut, for example, lets you set up a custom UAC-suppressing shortcut for any program. The shortcut launches the app in a way that won’t trigger a UAC alert.
ElevatedShortcut (site) is a tiny, standalone program that doesn’t require installation. It runs on Vista, Windows 7, and Windows 8, and it’s free (voluntary donations accepted). Despite its “ElevatedShortcut for Windows 7 and Windows 8” name, I successfully used it on Vista systems — even on the notoriously hamstrung Vista Home Basic!
Warning! ElevatedShortcut’s download page displayed distracting “Download now!” buttons for unrelated and potentially unwanted software. Be careful where you click! As of this writing, the correct download link is toward the bottom of the download page — look for a gray box just above the donation link. The correct download file is labeled elevatedshortcut.zip.
(If you need a ZIP extraction tool, I recommend the free, open source 7-Zip [site].)
The ZIP file contains two subfolders: one for Win7 systems — which also runs on Vista — and another for Win8. Drag, move, or copy/paste the appropriate folder to the location of your choice and then open the folder.
To run the program, simply click the ElevatedShortcut file. Again, the program is standalone (self-contained); it doesn’t need to be installed. Running the app opens a simple, self-explanatory dialog box.
To create a new “elevated” shortcut, start by clicking New shortcut (shown in Figure 4). In the next dialog box, use the Target path setting to navigate to an executable file for the software you want to launch with UAC suppression. You can leave everything else blank, if you wish. If you do so, the elevated shortcut will be created in the same folder where elevatedshortcut.exe resides. If you want the shortcut to appear elsewhere, use the Folder to store shortcut field.
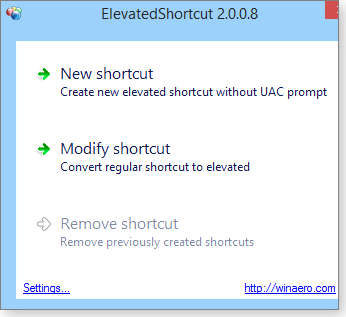
Figure 4: ElevatedShortcut sets up a custom shortcut that bypasses UAC alerts for specific programs.
For example, as shown in Figure 5, I created a custom “elevated” shortcut for Windows’ Registry Editor (Regedit) and told ElevatedShortcut to place the shortcut on my desktop. Clicking OK created the new shortcut’s icon, shown on the right in Figure 5. Note that the shortcut’s name was automatically appended with “(elevated).” That makes it easy to always know when I’m clicking the shortcut that will bypass the UAC prompt.
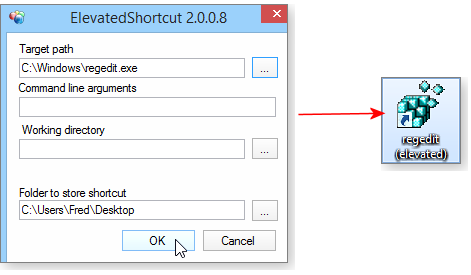
Figure 5. On the left, I created an elevated shortcut to launch the Windows Registry Editor (regedit.exe); on the right, the new shortcut icon on my desktop.
Use your new UAC-bypassing shortcut as you would any standard shortcut — simply double-click it to launch the desired application. In the example above, launching the elevated shortcut opens Regedit immediately — with no UAC prompt.
That’s pretty slick, but ElevatedShortcut won’t work every time with every application. Here’s another option.
A second free tool for bypassing UAC prompts
ITknowledge24’s UAC Trust Shortcut 1.0 (free; site) worked fine on my Vista, Win7, and Win8 test PCs. It’s available in 32- and 64-bit versions, and it installs in the normal Windows way (i.e., unlike ElevatedShortcut, it’s not a standalone program). ITknowledge24’s download page is refreshingly straightforward, containing no possibly misleading links to potentially unwanted software. Simply download the ZIP file and launch “setup” — installation is quick and easy.
When you run UAC Trust Shortcut, you’re presented with the dialog box shown in Figure 6. To begin setting up a UAC-bypassing shortcut, click the Add another program button.
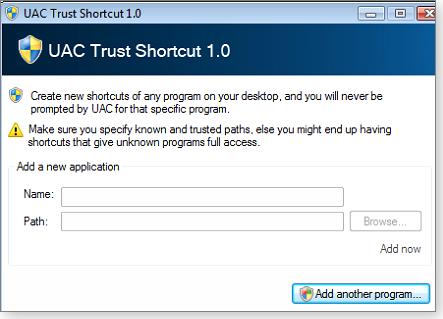
Figure 6. UAC Trust Shortcut's simple dialog box for creating a UAC-bypassing shortcut
Click the add another program button. In the next dialog box, give your shortcut a name and enter the path to the trusted application’s location. Here again, I created a UAC-bypassing shortcut for Regedit (see Figure 7).
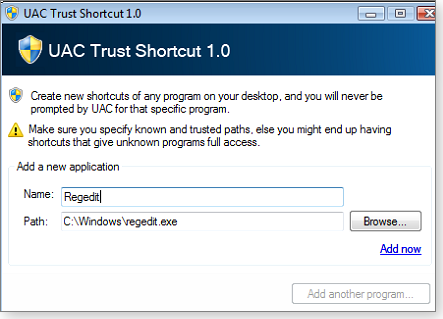
Figure 7. In this example, I named the elevated shortcut Regedit and set the path to the tool's location.
When you’re done entering the required information, click the Add now link — the new shortcut will be automatically placed on your Windows desktop. (Note: In my example, the shortcut is labeled just “Regedit.” You might want to give the shortcut an addendum such as “NoUAC” that makes it clear you’re bypassing User Account Control.)
Two UAC-bypassing methods from Microsoft
Microsoft provides both built-in and add-on methods for suppressing UAC warnings with specific applications. Both techniques work with Vista, Win7, and Win8.
The add-on option — Application Compatibility Toolkit (ACT) — is a heavy-duty tool you can use if all other methods fail. I’ll discuss it in a few moments.
The classic, built-in method is somewhat fussy to implement, but it doesn’t require any add-on or third-party tools. You’re basically using a Windows Task Scheduler script that’s launched via a custom shortcut. Here are the steps:
- In an admin-level account, open Task Scheduler. To do so, enter taskschd.msc into the Run (Vista), Start (Win7), or Search (Win8) box.
- In Task Scheduler’s left-hand pane, select Task Scheduler Library and then right-click it. Click New Folder from the drop-down menu (see Figure 8).

Figure 8. Creating a new Task Scheduler Library folder
- Give your new folder an obvious name. In this example, I’ll use NoUAC.
- In the left-hand pane, select the new folder you just created.
- Next, in the right-hand pane, click Create Task. Figure 9 shows my new NoUAC folder in Task Scheduler’s left pane and the Create Task link on the right.

Figure 9. Select your new folder (NoUAC in this example) and then click Create Task.
- When the Create Task dialog opens, make sure you’re on the General tab.
- Enter the following information, as highlighted in Figure 10:
Name: Give your Task a simple, obvious name without any spaces in it. For my example of launching Regedit without a UAC prompt, I’ve entered Regedit_NoUAC into the name field.
Description: This field isn’t mandatory, but it’s good practice to add a description so you can better identify the task’s purpose at some later date.
- Now, still within the Create Task dialog box, switch to the Actions tab and click the New button. Make sure that Start a Program is selected in the Action field. In the Settings section, click the Program/script Browse button and navigate to the application that you want the task to launch (see Figure 11). Click OK when you’re done.

Figure 11. The New Action dialog box lets you define what the Task will do — in this case, launch Regedit.
- Switch to the Settings tab and ensure that Allow Task to be run on demand is checked (Figure 12).

Figure 12. Ensuring that the Regedit task runs only when needed
- Close out the dialog by clicking the OK button. Your new task should appear in the middle pane of the main Task Scheduler window.
- Test your new task by right-clicking it and selecting Run. (Figure 13.) The program you selected should run without triggering a UAC prompt.

Figure 13. Before leaving Task Scheduler, test the new Regedit task.
Run with highest privileges: Check the box here to assign your new task admin-level privileges.
Configure for: Use the pull-down menu to select the operating system you’re currently using (Win7, in the example shown).

Figure 10. Fill out or select these four fields for the new task.
You’re finished with Task Scheduler. You’re now ready to create a custom shortcut to quickly and easily launch the new “Regedit_NoUAC” task!
- Right-click anywhere on the classic Windows desktop and choose New/Shortcut from the drop-down menus, as shown in Figure 14.

Figure 14. Create a new shortcut by right-clicking the Desktop and selecting New/Shortcut.
- In the Create Shortcut dialog box, enter the location of the new task. The path should be something similar to that shown below, with “{NameOfNewFolder\NameOfNewTask}” replaced with your new task’s folder and task names.
C:WindowsSystem32schtasks.exe /RUN /TN “{NameOfNewFolderNameOfNewTask}“
In my example, I entered:
- Click Next. In the next dialog box, “What would you like to name the shortcut?,” enter a simple, intuitive name. Following my conventions, I named it RegeditNoUAC. Click Finish. The new shortcut will appear on your Desktop.
C:\Windows\System32\schtasks.exe /RUN /TN “NoUACRegedit_NoUAC”
If all went well, clicking on the shortcut will launch your targeted program, bypassing the UAC.
If you can’t get this built-in technique to work, either fall back to the free tools mentioned earlier or roll out the following heavy artillery.
Microsoft’s Application Compatibility Toolkit
Microsoft’s free Application Compatibility Toolkit (ACT) and the related Windows Assessment and Deployment Kit (ADK) are professional-level tools that let you adjust how different programs interact with Windows. The Toolkit contains a preconfigured database of many popular programs. You can, of course, add new entries to the database. ACT even comes with a demo program (a fake stock-tracking app, shown in Figure 15) with which you can experiment.
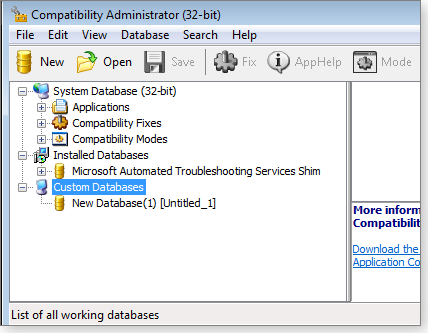
Figure 15. Microsoft's advanced Application Compatibility Toolkit lets you modify how programs interact with Windows.
Simply put, you use the database to whitelist whatever program you wish. Programs on the list should not trigger a UAC warning whenever you run them.
The Application Compatibility Toolkit and the Windows Assessment and Deployment Kit are complex — well beyond what I can cover here. But there’s plenty of information available online. See, for example:
Windows 7 and Vista:
- “Microsoft’s Application Compatibility Toolkit” – free download on MS site
- “ACT 5 Step by Step Guides” – MS Download Center page
- “Application Compatibility Toolkit (ACT) Technical Reference” – TechNet page
- “Introduction to the Application Compatibility Toolkit (ACT) Version 5.6” – TechNet page
Windows 8:
- “Windows Assessment and Deployment Kit (ADK) for Windows 8” – free download on MS site
- “Windows Assessment and Deployment Kit” – MS info page with supplemental links
- “Windows 8.1 Application Compatibility” – TechNet reference page
Many paths to the same User Account Control end
As with most Windows tools and options, you have numerous ways to solve PC problems. The above methods and techniques range from point-and-click simple to professional-level power and complexity, and from nearly automatic operation to fine-grained manual controls.
One of those options should make Windows’ User Account Control behave just the way you want it to. You’ll have UAC’s protective benefits — but not its annoyances!
PC crashes when waking from sleep mode
Sleep mode trouble (along with related hibernate and hybrid sleep problems) can be hard to cure. Here’s help.
Plus: Solving upgrade problems with two different Win8 systems, and how to use an ordinary PC touchpad for handwriting input.
PC enters sleep normally but then can’t wake up
Like many PC users, reader Biagio Vella lets his machine enter sleep mode when idle — both to save electrical energy and to reduce system wear and tear. But he’s encountered problems in getting his system to awaken properly. It’s a problem that’s not especially rare.
Biagio’s using a Win8 system, but similar problems can occur on Win7 and Vista setups — and the same solutions apply.
- “Dear Mr. Langa. I have a fairly new (2012) mainstream PC with Windows 8.1 installed and fully updated. My PC used to wake up from sleep as soon as I moved the mouse or pushed a keyboard key.
“But since upgrading to Win8.1, the PC crashes when I wake it up. I have to fully shut down by pressing the power button and then reboot.
“I have updated the chipset drivers from the vendor’s site and disabled the network adapters’ power-management setting — but all in vain.
“Here’s the strange thing: When I use the dedicated sleep key on the keyboard, Windows goes to sleep normally and wakes up immediately. The system crashes only when it goes to sleep on its own.
“I don’t know whether it’s a bug that came along with the Win8.1 update. I’ve tried the tips I’ve found on the Internet, but it was all a waste of time.
“Do you have any information that I can try to troubleshoot this issue? It’s so annoying — especially when I forget to click the sleep key and the PC goes to sleep automatically.”
You’ve already tried the best solution for sleep-mode and other power-control issues: You’ve updated your drivers from the vendor’s site (not from Windows Update).
So we have to look a little deeper.
One clue: Your PC behaves differently, depending on how it enters sleep mode. A manually triggered sleep mode works fine, but automatic sleep mode triggers a crash upon wake-up. Let’s work through what’s going on in those different instances.
On PCs with standard hardware: Vista, Win7, and Win8 typically offer three related power-saving modes: sleep, hibernation, and hybrid sleep.
In standard sleep mode (sometimes called “suspend”), your PC goes into a low-power state. The system consumes just enough electricity to keep the RAM contents intact, monitor for system events (such as a key- or mouse-click, or when the lid is closed on a laptop), and run other essential low-power processes.
Most users prefer sleep mode because, when awakened, the PC almost instantly picks up from where it was when last put to sleep. But there’s a downside to standard sleep. If anything interrupts the power to the sleeping system, the contents of RAM — including any unsaved files — will be lost. The system won’t be able to resume normally upon wake-up.
Hibernation mode writes the entire contents of RAM and the exact state of your PC’s CPU into a hidden hibernation file (hiberfil.sys) on the hard drive. Power is then shut off completely. When a PC starts up from hibernation, Windows uses the contents of the hibernation file to put the system RAM and CPU back into its last active state. But because this typically means reading several gigabytes of data from the drive, the process is not instantaneous — it usually takes at least a few seconds to a minute or more.
Hibernation is more reliable than sleep because the PC is totally off. The data and PC state are safe, even if you unplug the PC or remove its battery.
Hybrid sleep mode combines standard sleep and hibernation in a three-step process. First, the system prepares as if it were going to hibernate; the RAM and CPU contents are fully written to the hard drive. However, in the second step, the PC then goes into low-power sleep mode instead of completely shutting down. This combines the near-instant access of standard sleep with the reliability of hibernation. If there’s an interruption of power or a total shutdown, you won’t lose an unsaved file or have to completely restart applications.
The third step kicks in if the system remains in hybrid sleep for some set length of time. Sleep mode terminates, and the PC enters full power-off hibernation mode.
Most desktop PCs use hybrid sleep as their default for automatic sleep operations.
When Biagio manually triggers sleep mode by pressing the sleep button, his PC is most likely entering standard sleep mode. Things work as they should — the system goes to sleep and awakes normally. But when the PC goes to “sleep” on its own, it’s likely using the default hybrid-sleep mode — and that’s when things go awry.
For hybrid sleep to work properly, the PC’s power-management drivers must be correct, the hard drive must have space for the hibernation file, and the hibernation file must be written and read correctly.
Biagio has already checked the drivers, so there’s no help forthcoming from that quarter. So the next step is to check the hibernation file.
A hibernation file is roughly 20 to 25 percent smaller than the amount of installed RAM. Assuming the drive has sufficient space, the simplest option is to wipe out the hidden hiberfil.sys file and then rebuild it from scratch. You can do this by disabling hibernation, which deletes the current hibernation file; then re-enable hibernation, which creates a fresh hibernation file.
Microsoft offers fully automated fixits (site) that disable/enable hibernation. You also get instructions for manually doing the same thing. (The page doesn’t mention Win8 compatibility, but everything worked fine on my Win8 test system.)
After completing the disable-/enable-hibernation process, run chkdsk (TechNet info) to ensure that your hard drive is error-free.
With good drivers and an error-free hiberfil.sys file, hibernation and hybrid sleep should both work correctly.
If the crash-on-wake problem persists, the drivers are once again the prime suspects. Unfortunately, driver troubles aren’t something an end user can remedy. You can use only the drivers the vendor offers — even if they’re flawed.
If you suspect bad drivers, your only option might be to disable hybrid sleep. In an admin-level account, open the Control Panel and click System and Security/Power Options. For each Power Plan, click the Change plan settings and Change advanced power settings links. Next, click the Change settings that are currently unavailable link. Scroll down to the Sleep category, expand it, and look for Allow hybrid sleep. Change its setting to Off. (As shown in Figure 1, laptops typically have two settings.)
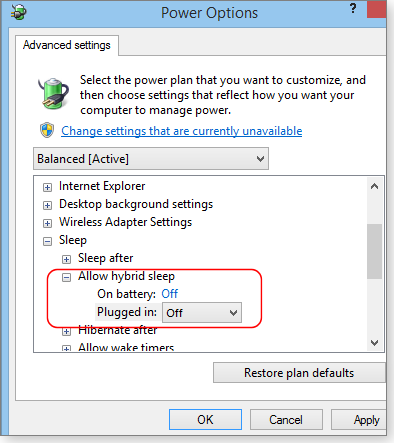
Figure 1. The option for disabling hybrid sleep is in Windows' advanced power settings.
You can disable hibernation entirely with the aforementioned fixit or with manual methods. With hibernation disabled, a PC will use only standard sleep mode — which, in Biagio’s case, apparently works fine.
For more information, see:
- “Sleep and hibernation: frequently asked questions” – Microsoft Windows 7 help page
- “Sleep mode” – general Wikipedia topic
Upgrade problems with two Windows 8 PCs
Thomas Savage is one of many who’ve had problems with Windows 8.x upgrading.
- “I have two Win8 computers that keep failing attempted upgrades.
“One is stuck at Win8.0; the other came with Win8.1. But when I try to upgrade either, both display the message ‘reverting changes’ and warn me not to turn off the power. They then confiscate my computer for up to an hour.
“Any idea how to debug these?”
Sure, Thomas!
The most common problem with Win8 upgrades is low-level (i.e., system-level), add-on software that fundamentally alters how Win8 works.
For example, some popular, third-party anti-malware applications do not play nicely with Win8. Checking online discussion boards, you’ll see reports that products such as Comodo and AVG might not work reliably on Win8 setups — even though they worked perfectly on previous versions of Windows.
Another common problem is with disk- or volume-level encryption — i.e., tools that encrypt entire drives or that create encrypted “containers.”
You can probably solve your upgrade troubles by (at least temporarily) uninstalling whatever low-level/system-level add-ons you have installed — especially any third-party encryption and anti-malware tools. When your PCs are closer to their initial states, they’ll probably upgrade just fine.
Note: If you remove a third-party anti-malware tool, don’t run unprotected. At least temporarily, use Win8’s built-in Windows Defender; it’s essentially the same as Microsoft Security Essentials on Vista and Win7. For more information, see the April 4, 2013, Top Story, “Microsoft’s six free desktop security tools.”
If you still can’t upgrade after manually simplifying your setups, take things up a notch with Win8’s built-in “no-reformat reinstall” option; it’s called Refresh your PC without affecting your files. And if you still can’t upgrade, your final option is to bring out the big gun: Use Win8’s Remove everything and reinstall Windows option.
These last two options are discussed in the Aug. 15, 2013, Top Story, “A ‘no-reformat reinstall’ for Windows 8.”
One of these three options will likely set things right.
When your systems are working correctly and are fully upgraded, consider replacing the third-party, system-level software (anti-malware, encryption, or whatever) you’ve been using. Look for different tools that won’t muck up Win8’s works!
Handwriting input via a standard touchpad
Rick McCoo is looking for help with handwritten input.
- “I am trying to find software that’ll let me use the touchpad on my standard (non-touchscreen) laptop for handwriting recognition. Since the touchpad can follow my finger for mouse operations, shouldn’t it be able to follow it when writing? My search did not turn up anything obvious for an ordinary laptop. There seemed to be lots of software for touchscreen products. Any ideas?”
Sure, you can use the touchpad for handwriting input. But keep in mind that there are limitations, mostly caused by the relatively low resolution of the typical PC touchpad.
Here are two easy ways to check whether it’s practical on your system.
The more refined approach is to use Alvin Wong’s TouchPad Handwriting app, which works on PCs that are equipped with a Synaptics touchpad (one of the most common types in use).
The free, open-source software (Figure 2) is available on a SourceForge page.
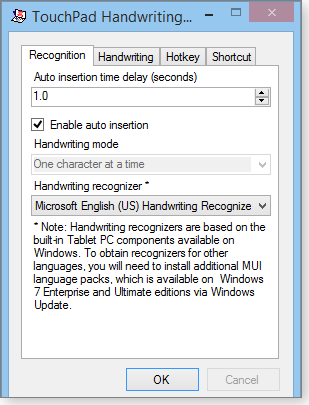
Figure 2. The free TouchPad Handwriting app enables an ordinary touchpad to capture handwriting — but with limitations.
The software’s easy to set up and use. But if you need help, AddictiveTips has a brief online tutorial.
Note that the TouchPad Handwriting app was originally designed to allow direct input of ideograms (e.g., Chinese characters), so it’s geared to one-character-at-a-time operation. Also, as previously mentioned, basic touchpads usually have fairly low resolution — you’re not going to get high-quality results.
The second approach is ultra-simple and works on any normal, touchpad-equipped Windows PC. Use a graphics application such as Paint to capture handwriting via your touchpad. For example, open Paint and select the Pencil tool. Position the cursor where you want it, and then press and hold the left touchpad button with one hand while you write on the touchpad with the other. Your motions will leave a trail on-screen. Release and re-press the left touchpad button to start a new stroke, word, or character.
This approach works, but you’ll instantly see the problems caused by the low resolution of most touchpads — the results are often comically crude!
If you need serious handwriting capture and recognition, you’ll get far better results with a separate graphics tablet or dedicated handwriting-entry device. They can capture handwriting as entered — just like writing on paper — or can work with handwriting-recognition software to convert your handwritten input into standard text. A basic Wacom input tablet currently costs around U.S. $65.
But if your handwriting-input needs are modest, tools such as Paint or the free TouchPad Handwriting app may be all that’s required. And, if nothing else, they’re free and fun to try!
Diagnosis: It just might take a village
Lounge member ggmcbreen, a graphics designer, relies heavily on graphics properties of certain tools such as thumbnails, which suddenly were not showing up in her folders.
Instead, she saw mainly blank icons.
She described her problem to Loungers in the Windows 7 forum, who gamely offered promising but ultimately ineffective advice. But all those suggestions must surely have helped the anti-malware technician who eventually restored ggmcbreen’s computer to working order. It always helps to rule out the wrong possibilities.
The following links are this week’s most interesting Lounge threads, including several new questions for which you might have answers:
 starred posts: particularly useful
starred posts: particularly useful
If you’re not already a Lounge member, use the quick registration form to sign up for free. The ability to post comments and take advantage of other Lounge features is available only to registered members.
If you’re already registered, you can jump right into today’s discussions in the Lounge.
Canadian bear cub takes an interest in golf
 |
A Calgary golfer’s game took a sudden turn toward interesting on a green in the back nine of a British Columbian golf course. A foursome of bears — a mama with three cubs — preceded the human visitors to the green. One of the cubs took a particular liking to the flag. Now video viewers everywhere can see a style of play we might never have imagined witnessing on a golf course. Click below or go to the original YouTube video. |
| Post your thoughts about this story in the WS Columns forum. |
Taking another look at Microsoft's Outlook.com
Hotmail’s replacement, Outlook.com, has slowly improved since its release in mid-2012.
Microsoft’s webmail viewer now provides a good selection of filtering tools for organizing your mail and protecting yourself from spam and other potentially dangerous mail.
Moving from client-based email to webmail
I was never a big fan of Web-based email programs. I preferred to stay on top of my electronic mail by downloading it to my desktop-based Outlook client, where I could read messages offline, organize them into folders, and send replies when convenient. It was a system I could manage relatively easily — until recently.
Over time, the volume of inbound mail grew until it hit unmanageable levels. Most of these messages flooding my inbox are from spambots and people or companies I don’t personally know. A more organized person might have set up multiple filters, white lists, junk-mail lists and other tools for removing the chaff. But like many email users, I suspect, I was habituated to simply scanning my mail quickly, reading the ones I needed, and moving on. (As a result, I had over 11,000 unread messages.)
With my client-based email system becoming choked with junk, webmail started to look more attractive. If I was getting barraged with unwanted mail, at least it would be sitting in someone else’s servers and not mine.
As an author of numerous books on Office, I naturally gravitated to Microsoft’s webmail service, Outlook.com. I’d looked at it when it was first released and wasn’t impressed. But with a steady stream of improvements, Outlook.com has matured into a relatively robust email app. It now offers some advanced features that enable users to import and manage other email accounts, filter incoming email, and apply and manage security features.
Outlook.com still doesn’t have the breadth of organizational tools found in Gmail, but I actually prefer Outlook.com’s somewhat simpler, more streamlined interface. Outlook.com’s “folders” seem more intuitive to a long-time Windows user than does Gmail’s “labels.” And though Outlook.com has privacy issues of its own, I’m more concerned by the many privacy questions surrounding Google.
So here’s a summary of Outlook.com’s more advanced features. It might be all you need to get a grip on email overload.
Importing messages from other email accounts
Keeping multiple email accounts has become standard practice. At a minimum, many email users want to keep business mail accounts separate from personal accounts. But having more than one account is also a good strategy for reducing junk mail. You can set up one or more disposable email accounts for use with online services that you don’t completely trust.
Managing multiple accounts does, of course, take a bit more work. Checking each account separately several times a day is simply impractical. The best solution is to set up your webmail or email-client app to consolidate all your various accounts, where you can check all your mail in one place. (It can also help to reduce junk mail because messages might pass through more than one junk-mail filter.)
The process of importing other, external email accounts into Outlook.com is relatively simple. Start by clicking the gear icon (settings), located in the upper-right corner of the Outlook.com window. In the drop-down menu, choose Options. Next, click the Import email accounts link under the Managing your account section.
The Import email accounts window gives you four options: Google, Yahoo, Other email provider, or Email apps on your PC. For the first three, Outlook.com asks for the external account’s email address and password. Before clicking the Import button, click the Options link to select how your imported messages are organized (see Figure 1). If you choose Email apps on your PC, Outlook.com prompts you to install the Mail Migration add-on that manages the import for you. (Click Install in the message bar to download and launch the add-on.)
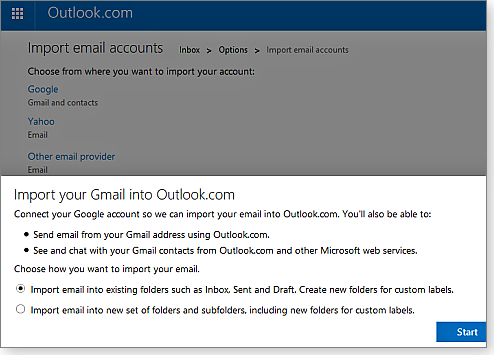
Figure 1. Outlook.com makes importing your email from Google, Yahoo, or other services quick and easy.
As soon as you click Start, Outlook.com begins importing the mail from the external account. The full import can take a few seconds or a few minutes, depending on the number of messages stored by the other account. During the import process, Outlook.com pops up a help screen for setting up mail forwarding from the external account. You’ll want to have mail automatically forwarded if you plan to import that account.
Mail imported from the external account appears in Outlook.com as a separate heading — including the external account’s inbox. Any folders you had created in the external email account appear in Outlook.com’s Folders panel. However, any new messages forwarded by the external account (those received after the initial import process) show up in Outlook.com’s main inbox. By default, Outlook.com combines all new messages, from all accounts, in the inbox. Unfortunately, there’s no easy way to tell which account a particular message came from, except by opening it.
Managing spam and setting up message filtering
Outlook.com now gives you a number of ways to control the types of messages that show up in the inbox. Outlook.com seems to do a good job of filtering out unwanted messages, but you can increase its vigilance with added filtering.
Click the gear icon and then Options. In the Preventing junk mail section, click Filters and reporting. The default standard junk email filter sends mail recognized as junk to the Junk Mail folder. The optional Exclusive setting is far more aggressive: it classifies as junk all mail that does not come from someone in your contacts list, safe-senders list, or alerts that you signed up for. (This setting weeded out most of my 11,000 unread messages.)
If you manually classify a message as junk, an optional Filters setting — Ask the sender to remove you from mailing lists and automatically block spammers (see Figure 2) — can help reduce your junk-mail load. Obviously, spammers will ignore the request, but it can reduce unwanted mail from “legitimate” senders. The option will also send reports about possible spammers to Microsoft to improve future junk-mail filters. Keep in mind that junk-mail filtering isn’t foolproof. The more aggressive the filtering, the more often you’ll want to check that legitimate mail hasn’t fallen into the Junk folder.
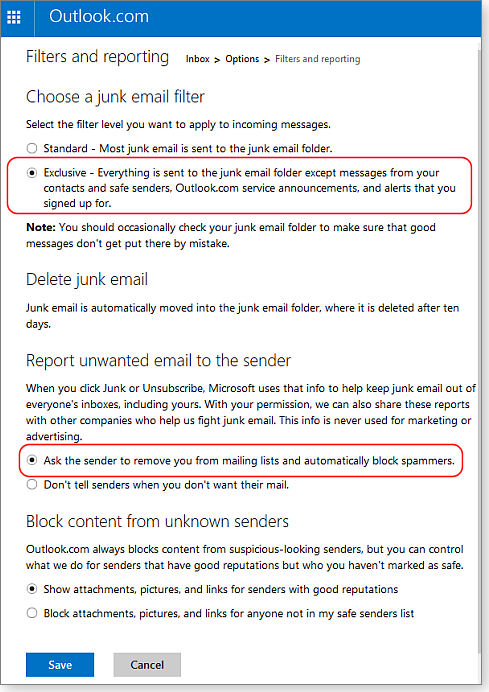
Figure 2. The two options highlighted above provide more aggressive junk-mail filtering.
Block content from unknown senders gives you added control over the display of email elements that commonly contain malicious code. By default, Outlook.com displays attachments, pictures, and links included in emails from senders with good reputations — according to Microsoft. But for added safety, Outlook can block those elements in all emails except those from senders in your safe-senders list. That’s probably a good option for those who tend to click before thinking about possible consequences.
Increasing overall security
Several months ago, Microsoft announced that Outlook.com would include encryption to help protect your emails from “electronic snooping and theft.” This came on the heels of the Snowden incident and after public outcry about companies providing customer data to the U.S. National Security Agency (the infamous NSA). According to Microsoft Trustworthy Computing president Matt Thomlinson, encryption helps “reinforce that governments use appropriate legal processes, not technical brute force, if they want access to that data.” This policy is similar to what’s offered by most companies that store and transfer user data in the cloud. You’ll have to judge whether that’s sufficient protection for your comfort level.
You don’t need to do anything to enable Outlook.com encryption protection. All messages sent and received via Outlook.com are now automatically protected with standard Transport Layer Security and Forward Secrecy encryption (more info). It should help ensure that messages reach their destinations without interference from those with nefarious intent.
No longer a bare-bones webmail utility
Outlook.com has numerous other tools for tailoring email management to your needs. A May 13 Office blog notes new features such as advanced rules, a quick undo button, faster replies, and enhanced chat. Standard Outlook users should be able to adapt to Outlook.com relatively easily. And who knows — a few Gmail users might find Outlook easier and faster to use.
In any case, moving at least some of your expanding inbox to the Web can cut down the time spent separating the mail you want from the spam you don’t. I invite you to join the conversation about online email by clicking the Windows Secrets Lounge link below.
A heaping helping of Windows and Office updates
It seems that Microsoft is honoring Thanksgiving with a platter full of security and nonsecurity fixings for both Windows and Office.
As with big holiday meals, this batch of updates should not be digested in one sitting. Focus on security updates, for now.
MS14-065 (3003057)
Reviewing your Browser security
A regular chore for Patch Tuesday is reviewing browser security. KB 3003057 is the monthly roundup of Internet Explorer security fixes. For November, the patch covers 17 privately reported vulnerabilities. (“Private” typically means the vulnerability was discovered by security researchers, who reported the flaw directly to Microsoft.) The update applies to all versions of Internet Explorer from IE 6 to IE 11 and is, of course, rated critical for workstation systems. If you’re running Windows 10 Technical Preview, you’ll probably get this update, too.
Our monthly review of browser security always includes Adobe Flash, Java, and the browsers we have installed. Adobe Flash users should now be on Version 15.0.0.223 (and Version 15.0.0.356 for Adobe Air), as documented in the Nov. 11 Adobe security bulletin. The latest Java is Version 7 Update 71. (If you want to check that you have the latest version, head over to the “Verify Java Version” site and click the big red button.)
Google’s Chrome and Mozilla’s Firefox typically upgrade automatically. You should now be on Chrome 38.0.2125.122 and Firefox 33.1. Check any other browsers you might have installed.
With the basics done, it’s time to make sure that other add-ons are up to date. For example, I’m glad to see that out-of-date Microsoft Silverlight versions will be added to IE’s ActiveX Control blocking feature that was introduced a few months ago. As noted in a recent IEBlog post, you’ll be notified when trying to load any Silverlight older than Version 5.1.30514.0. (If you need Silverlight, say, to run Netflix, check that you have KB 2977218 — the most recent Silverlight update — installed.) If none of your media apps requires Silverlight, uninstall it and ignore any future offers to install it on your system.
Windows 8.1 users running EMET 5 should either install Version 5.1 (more info) or temporarily disable EAF+ mitigation for IE 11 in your installed version of EMET. This vulnerability impacts all supported versions of Windows; expect to see it offered for Windows 10 Technical Preview, too.
 What to do: Install KB 3003057 (MS14-065) immediately, along with the usual Adobe Flash, Java, and browser updates.
What to do: Install KB 3003057 (MS14-065) immediately, along with the usual Adobe Flash, Java, and browser updates.
MS14-064 (3006226, 3010788)
Choking off a zero-day threat to OLE
Last month, I reported on an Object Linking and Embedding (OLE) zero-day vulnerability. By definition, zero-days are newly discovered vulnerabilities that are waiting for a patch. The two updates in MS14-064 are those patches for the OLE subsystem. KB 3006226 is rated critical and KB 3010788 is rated important.
Although the vulnerability is in Windows, a few targeted attacks used Office documents to exploit the flaws in OLE. So Microsoft has also released three nonsecurity updates — KB 2597972, KB 2878251, and KB 2889936 — to harden and protect files such as PowerPoint documents.
 What to do: Install security updates of KB 3006226 and KB 3010788 (MS14-064) as soon as offered, but leave the related nonsecurity patches for later in the month.
What to do: Install security updates of KB 3006226 and KB 3010788 (MS14-064) as soon as offered, but leave the related nonsecurity patches for later in the month.
MS14-066 (2992611)
Adding more protection to Web connections
Cipher suites are combinations of security code and authentication used in network communications (more info) and the Web. They support encryption used in Transport Layer Security (TLS) and Secure Sockets Layer (SSL). An enhanced version of networking encryption is called Perfect Forward Secrecy (PFS; more info), and it was included in Windows 8.1, as noted in a Microsoft Cyber Trust Blog post.
KB 2992611 fixes a flaw in TLS encryption and also enhances Windows’ security suites, providing more robust encryption to protect customer information. As discussed in the aforementioned Cyber Trust blog, these new suites all operate in Galois/Counter Mode (more info) — a popular combination of encryption and authentication — and two of the suites backport PFS protection to Windows 7.
The update is rated critical for both Windows servers and workstations. Without the patch, an attacker can take over a server by sending malicious data packets. Any Windows server hosting webpages, including Windows Small Business Server and Windows Server Essentials, is at risk. (Apparently, the vulnerability is not present in the Windows 10 Technical Preview.)
 What to do: Install KB 2992611 (MS14-066) on all supported Windows systems — and especially Web servers — as soon as possible.
What to do: Install KB 2992611 (MS14-066) on all supported Windows systems — and especially Web servers — as soon as possible.
MS14-067 (2993958)
MSXML used in malicious webpage attacks
Microsoft XML Core Services (MSXML) allows Web- and XML-based applications — written with JScript, Visual Basic Scripting Edition (VBScript), or Microsoft Visual Studio 6.0 — to work across platforms and within Web browsers. That makes those services irresistible targets, when their vulnerabilities are revealed. KB 2993958 fixes a privately reported flaw in Windows’ XML Core Services.
The update impacts all supported versions of Windows operating systems — including, most likely, Windows 10 Technical Preview. The update is rated important for servers and critical for workstations.
 What to do: Install KB 2993958 (MS14-067) soon.
What to do: Install KB 2993958 (MS14-067) soon.
MS14-069 (2899526, 2899527, 2899553)
Quashing remote attacks on Office 2007
The three updates in MS14-069 patch three privately reported flaws in Microsoft Office 2007. An exploit using the vulnerabilities could allow an attacker to acquire the same rights to a PC as the current user. (If the user is running in administrator mode, the attacker could take over the PC.)
KB 2899526 is for Office Compatibility Pack SP3, KB 2899527 is for Office 2007 SP3, KB 2899553 patches Word Viewer. You might see this third patch if you’re not running Office 2007 but you have Compatibility Pack installed. The three patches are all rated merely important because an exploit will work only if the current PC user opens an attachment or clicks a webpage link.
In a recent blog post, U.K.-based Security MVP Derek Knight warns that malicious Word documents are common. As I’ve said many times: open attachments only from trusted senders — and even then, be cautious. Sender addresses and notices from businesses are easily spoofed by malicious hackers. Always ask yourself whether you were expecting a document, and consider opening unknown files in a virtual machine or an alternative platform.
 What to do: Install KBs 2899526, 2899527, and 2899553 (MS14-069) when offered.
What to do: Install KBs 2899526, 2899527, and 2899553 (MS14-069) when offered.
MS14-071 (3005607)
Windows Audio Service component goes rogue
One sometimes gets the feeling that Windows has too many components to ever be truly secure. KB 3005607 patches a vulnerability in Windows Audio Service that could lead to an elevation-of-privilege attack. By itself, the vulnerability is not especially threatening — the update is rated merely important — but it could be added to blended exploits to enable remote attacks. And as with many current exploits, an attacker need only trick a user into browsing a malicious webpage or clicking on a bogus link.
The update is for all current versions of Windows except, apparently, Windows 10 Technical Preview.
 What to do: Install KB 3005607 (MS14-071) when offered.
What to do: Install KB 3005607 (MS14-071) when offered.
MS14-072
.NET used in elevation-of-privilege attacks
.NET Framework updates are about as common — and nearly as important — as Internet Explorer fixes. The various updates in MS14-072 impact all current versions of Windows, and they’re all rated important.
Last month, while I was installing .NET updates, two patches failed to install on the first attempt. But I had no difficulties on the second try. With XP out of the lineup, updating .NET is getting easier, but it’s still not foolproof. If one or more of your updates fails to install, simply try again — the odds are good it will work. (Many administrators prefer to install .NET updates separately.)
You might see one or more of the following .NET patches:
Server 2003
- KB 2978114 – .NET 1.1
- KB 2978124 – .NET 2.0 SP2
- KBs 2978124 and 2978124 – .NET 4
Vista and Server 2008
- KB 2978116 – .NET 2.0 SP2
- KB 2978125 – .NET 4
- KB 2978128 – .NET 4.5, 4.5.1, and 4.5.2
Windows 7 and Server 2008 R2
- KB 2978120 – .NET 3.5.1
- KB 2978125 – .NET 4
- KB 2978128 – .NET 4.5, 4.5.1, and 4.5.2
Windows 8, 8.1 and Server 2012, 2012 R2
- KBs 2978121 and 2978122 – .NET 3.5
- KB 2978127 – .NET 4.5, 4.5.1, and 4.5.2
- KB 2978126 – .NET 4.5.1 and 4.5.2
 What to do: I no longer recommend delaying .NET updates; install any of the above patches (MS14-072) when offered.
What to do: I no longer recommend delaying .NET updates; install any of the above patches (MS14-072) when offered.
MS14-074 (3003743)
RDP logging silenced
Remote Desktop Protocol is often used to remotely connect to one computer from another. RDP should not be used by itself over the Web. Businesses typically combine it with VPN software for making secure connections between remote workstations and local servers. Obviously, keeping those connections secure is extremely important. But a vulnerability in Windows could let someone sign in to a server without that event being logged. That could leave network administrators unaware of unauthorized access.
KB 3003743 closes that privately reported vulnerability. It’s rated important for all supported versions of Windows. Note that there are reports that the patch, as with an October RDP patch, breaks concurrent connections — and possibly App-V deployments. If you use any thin client programs, you’ll want to put this KB 3003743 on hold.
 What to do: The vulnerability is a threat only to Windows systems that have RDP enabled. (It’s disabled by default.) For those who don’t have RDP enabled, KB 3003743 (MS14-074) is optional. But as a precaution, I recommend installing it.
What to do: The vulnerability is a threat only to Windows systems that have RDP enabled. (It’s disabled by default.) For those who don’t have RDP enabled, KB 3003743 (MS14-074) is optional. But as a precaution, I recommend installing it.
MS14-079 (3002885)
Kernel-mode-driver denial-of-service attacks
Kernel updates have always been somewhat problematic, but more so lately, it seems. Often these updates conflict with third-party anti-malware software or other applications that tie deep into Windows.
Impacting all supported versions of Windows, KB 3002885 is a kernel fix for potential denial-of-service attacks that use malicious TrueType fonts.
 What to do: Because this update is rated only moderate, and the cure might be worse than the disease, leave KB 3002885 ( MS14-079) for the end of the month. That will give us plenty of time to see whether there are problems with the update.
What to do: Because this update is rated only moderate, and the cure might be worse than the disease, leave KB 3002885 ( MS14-079) for the end of the month. That will give us plenty of time to see whether there are problems with the update.
MS14-070 (2989935)
For admins: TCP/IP used for attacks on servers
In Windows, the TCP/IP stack is used for basic communication between workstations and servers. By exploiting a vulnerability in Windows’ TCP/IP component during input/output control (IOCTL) processing, hackers could gain access to Windows Server 2003 systems. (IOCTL is a function that lets applications access device drivers directly.)
To initiate the attack, a hacker needs to run (or trick a user into running) a malicious application on the target system. For that reason, the update is rated important, and it applies only to versions of Windows Server 2003. But here again, the vulnerability could be used in a blended attack. So it should not be ignored.
 What to do: Update Server 2003 systems as soon as possible with KB 2989935 (MS14-070).
What to do: Update Server 2003 systems as soon as possible with KB 2989935 (MS14-070).
MS14-073 (2889838), MS14-076 (2982998), MS14-077 (3003381), MS14-078 (2991963)
Admins get even more security update helpings
November’s Patch Tuesday saw numerous security fixes for servers. They include:
- KB 2889838 (MS14-073) for SharePoint 2010
- KB 2982998 (MS14-076) for Internet Information Services on Win8, Win8.1, Windows Server 2012, and Server 2012 R2
- KB 2991963 (MS14-078) for Japanese Input Method Editor
- KB 3003381 (MS14-077) for Active Directory Federation Services
Admins must also contend with delayed updates for MS Exchange servers. The patches were pulled at the last minute due to quality issues, as noted in the Nov. 11 Exchange Team Blog post. Reportedly, the updates will be released again in December.
 What to do: Be sure to test these updates before deployment.
What to do: Be sure to test these updates before deployment.
The usual monthly menu of nonsecurity updates
So far, I’ve not run across any reports of problems with these nonsecurity updates. But it’s early in the cycle — leave them for the usual end-of-the-month patch cleanup. (There were several ill-behaved nonsecurity patches in October.)
Windows 7 users might see KB 2952664 among the optional updates in Windows Update. This patch was to ease the upgrade process from Windows 7 to Windows 8. I suggest hiding the update (right-click the update and select “Hide update”) if you have no plans to move to Windows 8. A Patch Watch reader reported system slowdowns after installing KB 2952664.
Here’s November’s list of nonsecurity fixes. For more information on Office updates, see MS Support article 3012392. (It includes numerous updates for MS SharePoint Server.)
Windows 7
Windows 8 and 8.1
- 2976536 – Windows Defender update
- 2976978 – Windows 8 and 8.1 compatibility
- 3000853 – November rollup update
- 3003663 – Camera formats
- 3003667 – Camera formats
- 3003727 – USB 3.0 debugger fix
- 3008188 – Cumulative fixes and improvements
- 3008627 – Unexpected UAC prompt after KB 2918614
Office 2007
Office 2010
- 2589386 – Office: PDF text display
- 2687275 – Office: Pivot-table issue
- 2837602 – Office: Server linking
- 2878251 – PowerPoint: User experience with OLE objects
- 2889828 – Office: German and French proofing tools
- 2889935 – Excel: Pivot-table issue
- 2899521 – Outlook: Junk-mail filters
Office 2013
- 2837654 – Office: Searching Help issue
- 2863859 – Access: Crashes when using Portuguese (Brazil) language setting
- 2881008 – Office: Improved language localization
- 2889857 – Office: German, French, and Russian proofing tools
- 2889936 – PowerPoint: Several improvements
- 2899493 – Office: Inkjet error messages; Offline Address Book downloading; other fixes
- 2899500 – Word: Document Inspector
- 2899504 – Outlook: Certificate errors; Offline Address Book fix
- 2899506 – Outlook: Junk-mail filter
- 2899509 – Excel: Multiple issues when using pivot tables
- 2899510 – Office: Various OneDrive issues
Other updates
- 2899497 – Visio: Error messages; slow responses
- 2899507 – Lync: Various issues; check known issues and prerequisites
- 2899513 – OneDrive for Business: Various improvements
 What to do: Wait until the end of the month to install nonsecurity updates.
What to do: Wait until the end of the month to install nonsecurity updates.
Regularly updated problem-patch chart
This table provides the status of recent Windows and Microsoft application security updates. Patches listed below as safe to install will typically be removed from the table about a month after they appear. Status changes are highlighted in bold.
For Microsoft’s list of recently released patches, go to the MS Security TechCenter page. See our “Windows Secrets master Patch Watch chart” post for a more extensive list of recent updates.
| Patch | Released | Description | Status |
|---|---|---|---|
| 2982378 | 09-09 | Credentials protection | Optional |
| 2977292 | 10-14 | EAP security advisory | Optional |
| 3003743 | 11-11 | RDP access logging; possible connection issues | Optional |
| 2949927 | 10-14 | Recalled by Microsoft; SHA-2 support | |
| 3002885 | 11-11 | Kernel-mode driver; denial-of-service attacks | Wait |
| 2987107 | 10-14 | Internet Explorer cumulative update | Install |
| 2990942 | 10-14 | ASP.NET MVC for servers; see MS14-059 for full list | Install |
| 2993254 | 10-14 | Server 2003 kernel | Install |
| 2998579 | 10-14 | FAT32 disk-partition driver | Install |
| 3000061 | 10-14 | Windows kernel; possible issue for Win7 to Win8 upgraders | Install |
| 3000414 | 10-14 | .NET updates; see MS14-057 for full list | Install |
| 3000434 | 10-14 | Word 2007 and 2010; see MS14-061 for full list | Install |
| 3000869 | 10-14 | Windows kernel | Install |
| 2899526 | 11-11 | Office 2007; also KBs 2899527 and 2899553 | Install |
| 2982998 | 11-11 | Internet Information Services on Win8 and Server 2012 | Install |
| 2989935 | 11-11 | TCP/IP; Windows Server 2003 systems | Install |
| 2992611 | 11-11 | Cipher suites | Install |
| 2992719 | 11-11 | Japanese Input Method Editor | Install |
| 2993958 | 11-11 | MSXML Core Services | Install |
| 3000431 | 11-11 | SharePoint 2010 | Install |
| 3003057 | 11-11 | IE monthly rollup | Install |
| 3003381 | 11-11 | Active Directory Federation Services | Install |
| 3005210 | 11-11 | .NET Framework; see MS14-072 for full list | Install |
| 3005607 | 11-11 | Windows Audio service | Install |
| 3006226 | 11-11 | OLE zero-day; also KB 3010788 | Install |
Status recommendations: Skip — patch not needed; Hold — do not install until its problems are resolved; Wait — hold off temporarily while the patch is tested; Optional — not critical, use if wanted; Install — OK to apply.
Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com).
Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners.
Your email subscription:
- Subscription help: customersupport@askwoody.com
Copyright © 2025 AskWoody LLC, All rights reserved.

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Microsoft : Edge is better than Chrome
by
Alex5723
1 hour, 28 minutes ago -
The EU launched DNS4EU
by
Alex5723
7 hours, 1 minute ago -
Cell Phone vs. Traditional Touchtone Phone over POTS
by
280park
5 hours, 7 minutes ago -
Lost access to all my networked drives (shares) listed in My Computer
by
lwerman
12 hours, 28 minutes ago -
Set default size for pasted photo to word
by
Cyn
18 hours, 30 minutes ago -
Dedoimedo tries 24H2…
by
Cybertooth
6 hours, 36 minutes ago -
Windows 11 Insider Preview build 27871 released to Canary
by
joep517
1 day, 17 hours ago -
Windows 11 ad from Campaign Manager in Windows 10
by
Jim McKenna
1 day, 14 hours ago -
Small desktops
by
Susan Bradley
8 hours, 8 minutes ago -
Totally disable Bitlocker
by
CWBillow
11 hours, 2 minutes ago -
Phishers extract Millions from HMRC accounts..
by
Microfix
1 day, 15 hours ago -
Windows 10 22H2 Update today (5 June) says up-to-date but last was 2025-04
by
Alan_uk
2 days, 21 hours ago -
Thoughts on Malwarebytes Scam Guard for Mobile?
by
opti1
16 hours, 10 minutes ago -
Mystical Desktop
by
CWBillow
3 days ago -
Meta and Yandex secretly tracked billions of Android users
by
Alex5723
2 days, 6 hours ago -
MS-DEFCON 2: Do you need that update?
by
Susan Bradley
21 hours, 58 minutes ago -
CD/DVD drive is no longer recognized
by
WSCape Sand
3 days, 15 hours ago -
Windows 11 24H2 Default Apps stuck on Edge and Adobe Photoshop
by
MikeBravo
3 days, 18 hours ago -
North Face and Cartier customer data stolen in cyber attacks
by
Alex5723
3 days, 16 hours ago -
What is wrong with simple approach?
by
WSSpoke36
1 day, 14 hours ago -
Microsoft-Backed Builder.ai Set for Bankruptcy After Cash Seized
by
Alex5723
4 days, 4 hours ago -
Location, location, location
by
Susan Bradley
2 days, 18 hours ago -
Cannot get a task to run a restore point
by
CWBillow
4 days, 5 hours ago -
Frustrating search behavior with Outlook
by
MrJimPhelps
3 days, 20 hours ago -
June 2025 Office non-Security Updates
by
PKCano
4 days, 16 hours ago -
Secure Boot Update Fails after KB5058405 Installed
by
SteveIT
5 hours, 16 minutes ago -
Firefox Red Panda Fun Stuff
by
Lars220
4 days, 16 hours ago -
How start headers and page numbers on page 3?
by
Davidhs
5 days, 2 hours ago -
Attack on LexisNexis Risk Solutions exposes data on 300k +
by
Nibbled To Death By Ducks
4 days, 5 hours ago -
Windows 11 Insider Preview build 26200.5622 released to DEV
by
joep517
5 days, 11 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.

