
|
Patch reliability is unclear, but widespread attacks make patching prudent. Go ahead and patch, but watch out for potential problems. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
Eliminate Flash-spawned ‘zombie’ cookies
In this issue
- INTRODUCTION: It's been 20 years of investigative journalism
- TOP STORY: Eliminate Flash-spawned 'zombie' cookies
- LOUNGE LIFE: Keep your computer cool in the summer heat
- WACKY WEB WEEK: Goat calls for help in a most human way
- LANGALIST PLUS: Are the benefits of defragmentation overblown?
- PATCH WATCH: Microsoft releases critical out-of-cycle patch
- BEST PRACTICES: Forecast for cloud-based servers is hazy
It's been 20 years of investigative journalism
 By Brian Livingston
By Brian Livingston
When I started writing articles for technology magazines 20 years ago, I wondered whether the principles of investigative journalism could be applied to the computer industry.
Little did I know then that there was an endless supply of dirt to be dug up.
As I look ahead, changes are coming that I’d like you to know about. Looking back, I see that some of the stories I followed as a contributor to various publications are still having an impact on our lives today:
InfoWorld, 1991 to 2003. To great fanfare, Microsoft in early 1993 released MS-DOS 6.0 featuring DoubleSpace, a newfangled disk compression scheme. Headaches for pioneers soon arose. In a May 3, 1993, column, I reported “problems running Windows with DOS 6.0.” That same day, InfoWorld published a cover story revealing disk corruption caused by the new disk operating system.
Unfortunately, Microsoft forced InfoWorld to print a partial retraction on May 10 because the magazine could not replicate every case of corruption. Other computer magazines reviewed DOS 6.0 and said they didn’t see any problems.
To my knowledge, I was the first journalist to reveal precisely how DOS 6.0 created “La Brea tar pits” that wiped out files. In a series of columns on Aug. 23, Aug. 30, and Sept. 6 (see Figure 1), I publicized a free utility called Jeopardy Detector that turned the border of a PC monitor bright red when DOS 6.0 was in this condition.
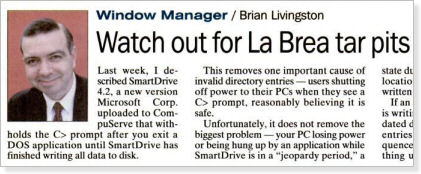
Figure 1. Revealing exactly how Microsoft’s software was corrupting disk files was the first step in getting Redmond to fix its operating system.
With the technical details made clear, other magazines were able to confirm the problem. Within months, Microsoft was forced to renounce DOS 6.0. Because IBM had released a competing product named PC-DOS 6.1, Microsoft’s upgrade was called MS-DOS 6.2. In an unprecedented move, the software giant released the upgrade as a free download, as reported at the time by computer writer Alan Zisman.
►How it affects you. Whether because of the financial expense or the sheer embarrassment, Microsoft never produced another standalone DOS after version 6.22, a minor upgrade. As soon as Windows 95 was released in mid-1995, users no longer had to first install a separate product called DOS. Microsoft’s conversion to graphical operating systems was complete — a momentous shift. Good riddance to character mode.
CNET News, 2000 to 2001. In the weekly Wired Watchdog column for CNET, I sought to expose fraud on the Web. One of my biggest finds was the “youth filter” that the AOL online service was promoting in 2000.
I found that the filter had a hidden but severe political agenda. AOL’s filter would allow users to visit the site of the Republican Party but not the Democratic Party or the Green Party. Promotions of guns were available at sites such as Colt, Browning, and the National Rifle Association — but AOL blocked such well-known gun-safety organizations as the Coalition to Stop Gun Violence and the Million Mom March, as I wrote on April 24, 2000. (See Figure 2.)
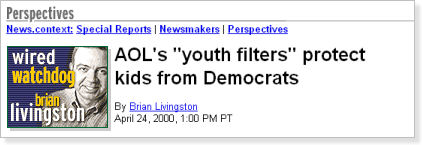
Figure 2. Youth filters such as the ones AOL used were found to have an explicit political agenda.
►How it affects you. AOL soon discontinued its use of the filter, which had been provided by the Learning Company, a firm that the toy giant Mattel had acquired in 1999 for $3.5 billion. Mattel divested itself of the subsidiary by the end of 2000 at a near-total financial loss. Today, there’s less emphasis on trying to prevent teens from seeing some skin and more emphasis on filtering out true security threats. Making security our first priority benefits us all.
Windows Secrets Newsletter, 2004 to 2010. One of the newsletter’s longest-running stories was the fact that Windows Vista included a built-in procedure that allowed its cheaper “upgrade” version to perform a clean install. This was something that only the more-expensive “full” version was supposedly able to do.
As I reported on Feb. 1, 2007, using the feature required no hacking — Microsoft had knowingly programmed the trick in. Vista’s “full” version could be seen as merely an overpriced head fake designed by the company to make the price of its “upgrade” version seem reasonable by comparison. (The clean-install procedure was outlined to me by my Windows Vista Secrets co-author Paul Thurrott, who wrote a short blog update about it.)
Various low-level Microsoft executives berated us publicly, claiming that the technique should never have been revealed. But Microsoft made sure the trick remained in Vista Service Pack 1, as reported by WS associate editor Scott Dunn on April 3, 2008. And Windows 7 even enhances the procedure, incorporating a new command to make the steps more user-friendly, as Woody Leonhard wrote on Nov. 2, 2009.
►How it affects you. Microsoft’s pricing games with its products may be coming to an end. With the release of Office 2010 this year, Redmond is offering simplified pricing for its office suite, below 2007’s “upgrade” price and “full” price, according to Woody’s June 16 story (paid content). To be sure, there are still different prices for home, business, and professional editions of Office 2010. But setting one low base price for each edition — without consumers needing to prove they previously owned a particular product — is a step toward rationality by Microsoft.
It’s time for a transition. Since my first real column — for Systems Integration, a glossy monthly (1990 to 1991) — I’ve also been a contributing editor over the years for PC World, eWeek, PC/Computing, Windows Sources, and Windows Magazine. By my count, I’ve written more than 1,000 articles, sold more than 2.5 million copies of 11 books (nine with remarkable co-authors like Davis Straub, Bruce Brown, Bruce Kratofil, and Paul Thurrott), and hammered out a million e-mails, ranging from the mundane to the maddeningly technical. I’m ready for that change I mentioned above.
I’m retiring from Windows Secrets today and turning the reins over to new hands. As the newsletter has grown from 0 to 400,000 subscribers over the past several years, the demands on my time gradually shifted from writing to more-sedate managerial duties. As a result, I haven’t written any content for the paid section of the newsletter since December 2005. No loss: senior editors Fred Langa and Woody Leonhard, plus all the other contributors who bring you Windows Secrets, have more collective knowledge to give you than I could ever hope to match.
 As my last official act, I’ve promoted Tracey Capen (left) from technical editor to editor in chief. Truth be told, he’s been performing the top editorial job on the Windows Secrets Newsletter for months. Tracey’s experience as executive editor of reviews for PC World for 10 years, preceded by stints as a senior editor of InfoWorld and Corporate Computing magazines, makes him extremely qualified to bring you fresh information on Windows.
As my last official act, I’ve promoted Tracey Capen (left) from technical editor to editor in chief. Truth be told, he’s been performing the top editorial job on the Windows Secrets Newsletter for months. Tracey’s experience as executive editor of reviews for PC World for 10 years, preceded by stints as a senior editor of InfoWorld and Corporate Computing magazines, makes him extremely qualified to bring you fresh information on Windows.
To ensure that Tracey has the resources he needs to grow the newsletter, Windows Secrets is joining the iNET Interactive network. iNET Interactive is an online media company operating a portfolio of services dedicated to tech professionals and enthusiasts.
You may recognize many of iNET’s services, including Hot Scripts (resources for Web developers), Web Hosting Talk (the Internet’s largest Web-hosting information site), DB Forums (resources for database administrators), and Overclockers (a community focused on performance computing). For more information, see iNET Interactive.
My one regret during my career is that it was impossible for me to reply personally to every e-mail from thousands of readers seeking help with Windows problems. One of my greatest satisfactions, therefore, has been the 2009 integration of the WS Lounge (formerly Woody’s Lounge) into WindowsSecrets.com.
Very soon, the Lounge will work side-by-side with a network of discussion boards such as DB Forums and Overclockers. The flow of ideas between the complementary communities can only make them even better places for computer users to exchange information.
After two decades in which I’ve tried to unveil for you the mysteries of Windows, I hope you’ll allow me to take a long vacation, get a lot of sleep, dream big dreams, and refresh myself. I’ll probably do a bit of consulting. Maybe I’ll start an airline.
If you need to reach me, you can always send e-mail via the Windows Secrets contact page. Your message will be forwarded to me whether I’m in Mogadishu, Machu Picchu, or anywhere in between.
My thanks to everyone who’s ever read my words, contributed a hot tip, or both. Keep on enjoying Windows Secrets and keep sending in your findings, so your tireless columnists can keep researching them, writing them up, and raising hell.
| Have more info on this subject? Post your tip in the WS Columns forum. |
Brian Livingston is co-author of 11 books in the Windows Secrets series (Wiley Publishing).
Eliminate Flash-spawned 'zombie' cookies
 By Woody Leonhard
By Woody Leonhard
Way back in a 2008 column, I spotlighted one of the most insidious and least-known features on the Internet: Adobe Flash cookies that were not subject to the usual cookie rules.
Almost two years later, these special Flash cookies are still living in our PCs, and enterprising privacy-busters now use them to create zombie cookies — regular cookies that come back from the dead.
My Oct. 23, 2008, column, “Flash cookies are putting your privacy at risk,” described how data stored by Adobe’s Flash Player is beyond your browser’s control and how it could store more personal data than you’d suspect.
Flash cookies have now landed their manipulators in troubled waters. Last week, two well-known privacy attorneys, Dallas-based Joseph Malley and California-based David Parisi, filed a lawsuit in U.S. District Court for the Central District of California against Quantcast, a Web page–ranking and audience-statistics firm. (A July 27 Wired Threat Level story on the lawsuit includes a link to a PDF copy of the filed court documents.)
The lawsuit claims class action status and lists additional defendants — a Who’s Who of online players including MySpace, ABC, ESPN, Hulu, JibJab, MTV, NBC Universal, and Scribd.
In the class action complaint, Quantcast “and websites affiliated individually with Quantcast, referred collectively to as, ‘Quantcast Flash Cookie Affiliates,'” are accused of “setting [F]lash cookies on their user’s computers to use as local storage within the [F]lash media player to back up browser cookies for the purposes of restoring them later.”
The complaint goes on to accuse the defendants of setting online tracking devices that let them access and disclose personal information. But while the complaint is complex, the technology that spawned it is surprisingly straightforward.
Flash cookies are the all-pervasive app
In order to understand zombie cookies (yes, that’s the technical name), you need to know about Flash’s Local Shared Objects, or LSOs — the formal name for Flash cookies. My 2008 column goes into detail about LSOs, but the upshot is this: Adobe Flash Player LSOs work much like the cookies maintained by our browsers — they are files that live in our computers and are updated and read by Web pages that we visit.
Since Flash Player runs on more computers than even Windows (!), Flash Cookies are as close to universal as anything on the Internet. Steve Jobs won’t let Flash run on iPads and iPhones, but for just about everything else, there’s a version of Flash.
Like standard cookies, LSOs usually fly under the radar. But they can store significantly more data than the usual cookie. Regular old browser cookies are limited to 4KB in size; LSOs can go up to 100KB. Regular cookies are completely controlled by your browser — you can use your browser to turn them on or off, to delete them, to block them. Not so LSOs. They are controlled by Adobe’s Flash Player, and it’s notoriously difficult to get at them.
While you may not have easy access to Flash LSOs, Web sites do. If you have Adobe Flash installed on your computer, Web pages can set and read Flash cookies — whether the page you’re viewing has a visible Flash animation or not. So while you think you’ve blocked a site’s cookies, it’s entirely possible for the site to use an LSO for the same purpose.
And it’s all hidden under the covers and difficult to turn off unless you run a Flash Cookie blocker (more about which later) or jump through some major hoops.
Cookies that return from the cookie-crusher
Most PC users know the basics of Web cookies. Most have their computers set up to block cookies, block third-party cookies, or delete all cookies when they end a browsing session. It’s all based on your level of paranoia. You may have a spyware scanner that looks for and deletes various types of cookies, particularly from marketing companies such as Doubleclick. Even those of us who allow cookies free rein still delete them from time to time, if only to clear out the cobwebs.
Here’s how zombie cookies reappear.
When you visit Web sites, they often plant cookies on your computer, if they can. But some sites will also stick duplicate cookies into the Flash LSO. When you go back to these sites, they check whether you have their standard cookies stored in your browser. If none are found, they then check whether there’s any doppelgänger cookies in the Flash LSO. And if they find any, the sites reconstruct their original cookies and stick them back into your PC. Very clever.
Zombie cookies are scary because they provide online companies with a secret way to keep tabs on people and their Web-surfing proclivities. Unless you check your browser’s list of cookies regularly, you may never know that these resurrected tracking cookies are back in business.
Where companies like Quantcast come into play
Data-gathering companies such as Quantcast make money selling information about people who visit Web sites. According to Quantcast’s own site, “Millions of Web site owners, including two-thirds of the Online Publisher’s Association, use Quantcast’s measurement service to create demographic, geographic, and affinity-based audience profiles.” And the cookies placed on your PC can be used as sophisticated monitoring tools.
Curious about what’s gathered? You can take a free ride with the Quantcast demo.
I ran a Quantcast analysis for U.S.-based visitors to our site, windowssecrets.com, in May of this year. The results appear in Figure 1. You should take the results with a grain of salt, of course.

Figure 1. According to Quantcast, 86% of those who visit the Windows Secrets site have no kids under 18; 19% make more than $100,00 per year; and 17% at least walked through part of grad school.
It’s in the best interest of these companies to continually gather data about Web-site visitors. Cookies, as already mentioned, are a key part of that process. Zombie cookies undoubtedly contribute to keeping these tracking cookies alive for as long as possible.
Take control of Flash cookies with PC cleaners
Controlling Flash LSOs, and thus eliminating zombie cookies, is a pain in the neck if you use the Adobe method, which involves futzing around with a very unfriendly Web site. I talk about the official method in my October 2008 article.
For Firefox users, an add-in can now help. To control Flash cookies, just download (page) and install the BetterPrivacy add-in for Firefox.
For cleaning Internet Explorer, there are two products — both free — you can try: CCleaner, available for download on Piriform’s home page, and Flash Cookies Cleaner 1.2, offered as a free download on Softpedia’s site.
Certainly, the zombie cookie approach to subverting a user’s direct commands — reinstating a cookie after the user has explicitly deleted it — constitutes some sort of privacy invasion. Whether it’s actionable in court is anybody’s guess.
Should be quite interesting.
| Have more info on this subject? Post your tip in the WS Columns forum. |
Woody Leonhard‘s latest books — Windows 7 All-In-One For Dummies and Green Home Computing For Dummies — deliver the straight story in a way that won’t put you to sleep.
Keep your computer cool in the summer heat
By Keely Dolan
It’s the peak of summer, and staying cool isn’t just a question of comfort: it can mean survival.
In homes and offices without air conditioning, that fact can be just as pertinent to personal computers as it is to us.
A hot day can tax the cooling system in most personal computers. In his thread titled “Cooling a PC in a high heat environment” Lounge member William Edwards posed the question of how to keep his system adequately cool in an observatory, where temperatures reach over 100 degrees Fahrenheit.
Helpful suggestions ranged from removing a side panel and angling a fan directly into the CPU to simply limiting usage during the hottest times of the day. More»
The following links are this week’s most-interesting Lounge threads, including several new questions that you may be able to provide responses to:
☼ starred posts — particularly useful
If you’re not already a Lounge member, use the quick registration form to sign up for free. The ability to post comments and take advantage of other Lounge features is available only to registered members.
If you’re already registered, you can jump right in to today’s discussions in the Lounge.
The Lounge Life column is a digest of the best of the WS Lounge discussion board. Keely Dolan is a Windows Secrets Lounge administrator.
Goat calls for help in a most human way
 |
By Stephanie Small
When someone cries for help, it strikes at core of our humanity. Only the most heartless of us could ignore the pleas of someone in distress. But what if the call for help arises from an unexpected source? Would you respond the same way if the cry came from, say, a goat? Watch this amusing clip of a beast’s clever technique for getting attention fast. Play the video |
Are the benefits of defragmentation overblown?
 |
By Fred Langa
One of the never-ending, always-simmering debates between PC users is whether defragging modern hard drives provides any measurable benefits to PC performance. Unfortunately, the answer is not an absolute yes or no but instead depends on how you defrag your system. |
There’s clear logic behind defragmentation
Reader Martin Hack asks a legitimate question regarding some advice given recently in this column: Is the recommendation to “Defrag, defrag, and defrag again” actually founded in fact?
- “In his July 22 column, Fred makes the following statement: ‘Defrag, defrag, and defrag again. Hard-drive files neatly packaged into long, unbroken chains load faster than those whose segments are scattered all over the drive.’
“I have yet to see this shown to be the case. And if he has any proof, I’d like to see it. Thanks.”
It’s always good to question conventional wisdom, Martin. Sometimes it’s dead wrong! But I can show you the benefits of defragmentation in two ways.
I admit the first is anecdotal and subjective, so you’re free to disregard it. That said, I’ve seen the benefits of defragging many, many times when I’ve cleaned up PCs crippled by serious performance issues. Such PCs’ drives are almost always severely fragmented, and they almost always perform noticeably better after a thorough defrag.
But that’s a fuzzy argument, so let me give you the underlying logic:
Files are stored on a hard drive in small chunks called clusters. On an NTFS drive, for example, the default cluster size is 4KB. Large files are stored in a series of 4KB clusters.
Let’s look at the example of a common file — Excel.exe. It occupies 17.5MB (17,924KB or 18,354,176 bytes) of disk space on my system. Do the math (17,924KB divided by 4KB), and you’ll see that this one file occupies approximately 4481 clusters.
Current hard drives have an average nonsequential seek time (the time needed to move the drive heads from one place on the platters to another) of around 7 milliseconds (ms); server drives can be faster, laptop drives slower, but 7ms is a reasonable average.
A little more math (4481 clusters multiplied by the 7ms average seek time) shows you that loading a completely fragmented Excel.exe would require over 31 seconds just in mechanical head-movement time. Note that this doesn’t count the actual read-in time nor any processing or setting up of Excel — it’s 31 seconds lost in just getting the drive’s heads in position to read the file’s pieces!
Too extreme an example? Maybe. Few files are that badly fragmented, and I’m using Excel only for illustrative purposes. But even if the file is only half-fragmented, it would add at least 16 seconds to the time it takes to launch Excel. And that’s just one file. Multiply that by the hundreds of files launched and saved in a typical day, and it adds up to significant time.
For example, my advice about defragging was in reference to a reader question about system startup — when all of Windows and every startup program (hundreds of megabytes in all) must be read from the disk into memory. On a badly fragmented disk, this can add tens of thousands of unnecessary head seeks — needless minutes of purely mechanical work by your hard drive!
Defragmentation eliminates that wasted time by putting all of a file’s clusters into a sequential order. A fully defragmented file requires just one nonsequential seek (the one that moves the head to the start of the file).
A good defragger will also go a step further, ordering your startup programs so they, too, are lined up one after the other on the hard drive. That way, your drive’s heads can glide through one startup program after another in a long, unbroken read — instead of jittering and jumping all over the disk, gathering tens of thousands of scattered file fragments.
Thorough defragging can eliminate virtually all unnecessary disk-head movements. Good defragging tools are either free or built into Windows, and running them is point-and-click simple. So, why wouldn’t you defrag?
Trust me on this. Defragging makes a difference!
Another method for completely uninstalling Flash
Bill McGarry offers some additional information with regard to my July 22 item, “Fix Flash Player with a complete uninstall.”
- “You’re right. When Flash won’t work (or won’t install), sometimes you need to completely uninstall all Flash versions. Adobe has a special program to uninstall Flash Player. I had a problem a while back where Flash was not working. One Web site recommended using the Adobe Flash uninstaller, and that did the trick!
“The instructions are on an Adobe Web-site page. The notes say that you should exit all programs, including all browsers.
“The site also says that Internet Explorer users need to select Show Details after running the Flash uninstaller, then look for the Delete on Reboot lines in the log. That will determine whether you need to restart your computer to complete the uninstall process. (Not too user-friendly, is it?) But on the same Web page, it says that if you mistakenly leave any program open, close the program and run the uninstaller again.
“I would recommend running Task Manager before running the uninstaller, then killing any iexplore.exe instances that are still running. (The Task Manager is also a good way to check that there are no Chrome or Firefox components running.) I would still check the uninstaller log to see whether there are any other programs that need to be stopped, and I would keep running the uninstaller until the log says that everything was removed successfully.”
Thanks, Bill! The Adobe tool is worth trying, but all your caveats and additional warnings about it are why I prefer manual deletion. If you track down and delete all Flash files everywhere on the disk and remove all references to Flash in the Registry, there’s no way that Flash can survive. It will be gone for certain — no caveats, no quibbles, no doubts.
But options are good, and the Adobe tool could be useful for people who aren’t comfortable with the admittedly harder manual methods.
Install 64-bit Windows 7 over 32-bit Vista?
Don Lathem wanted to do a major system upgrade but ran into a snag.
- “I am running 32-bit Vista Home Premium. My machine is 64-bit capable (determined two different ways). I want to install Windows 7 Home Premium x64 as a custom installation. But I keep getting the message ‘Setup was unable to create a new system partition or locate an existing system partition.’ Of course, I’m trying to install it right onto the existing system partition. Any ideas?”
You’re trying what Microsoft calls a “cross-architecture, in-place upgrade.” You’re not only trying to change the edition of your OS (from Vista to Windows 7) but also its bittedness: from 32- to 64-bit. I’m sorry to report that it won’t work. It’s just too much to change all at once.
The Technet article, “Windows 7 upgrade paths,” explains what upgrade combinations are acceptable.
Your best bet, Don, is to back up everything and do a clean Win7 install in a new, empty partition.
AV suite implicated in horrible boot time
Charles Rathbun wrote in with some useful information related to my July 22 item, “Horrible four-minute boot resists easy fixes.”
- “I installed Trend Micro Internet Security 2010 on some of my clients’ computers.
“I noticed significant performance and Web-browsing sluggishness (especially with Vista). Once TMIS 2010 was removed, the performance greatly increased.
“This unpleasant discovery makes me want to get rid of what I once thought was good software.
“Personally I’d recommend ESET’s NOD32, as I have been both using it and reselling licenses for it since 2005 and have never had any significant compatibility or performance issues. Their software is written entirely in assembly language instead of the bloated C++ used for Norton and McAfee.”
Thanks, Charles. AV tools and security suites are notorious system hogs, and feature-bloat is common.
For example, Trend Micro lists 13 major features and subsystems in its security suite, McAfee lists 14, and Symantec lists 33!
Many of these features duplicate abilities already built into Windows and the major browsers. For example, Internet Explorer and Firefox have built-in link-checkers, pop-up-blockers, parental controls, and more. Windows itself (especially Win7) has a capable firewall built in.
So the large security suites are including features you probably already have, and all of these redundant features consume memory and CPU time.
In contrast, the small, more nimble security packages offer just the essentials. For example, ESET lists just six major features for NOD32.
And my current favorite security tool, Microsoft’s free Security Essentials (site), lists just two major functions: antivirus and anti-malware protection. When used with Windows’ built-in firewalls and a fully current browser (say, IE8 or Firefox 3.6.x), you end up with essentially the same capabilities provided by the huge commercial security suites.
What’s even better, it’s all free!
On any system that’s suffering a slowdown, it’s well worth the time and trouble to at least temporarily swap out a large commercial security suite with a small and lithe AV tool.
You just may recover some of the performance you thought your system had lost forever!
| Have more info on this subject? Post your tip in the WS Columns forum. |
| Readers Bill McGarry and Charles Rathbun will each receive a gift certificate for a book, CD, or DVD of his choice for sending the tip we printed above. Send us your tips via the Windows Secrets contact page. |
Fred Langa is a senior editor of the Windows Secrets Newsletter. He was formerly editor of Byte Magazine (1987–91), editorial director of CMP Media (1991–97), and editor of the LangaList e-mail newsletter from its origin in 1997 until its merger with Windows Secrets in November 2006.
Microsoft releases critical out-of-cycle patch
 |
By Susan Bradley
When Microsoft releases a patch outside its normal twice-monthly cycle, it’s usually not one to ignore. Hackers are already attacking PCs, using the vulnerability fixed by the out-of-cycle patch in Security Bulletin MS10-046. |
MS10-046 (2286198)
Patch fixes security flaw in Windows shortcuts
MS10-046 details a critical patch to the Window Shell (the user interface) in all versions of Windows. It fixes a flaw which allows the shortcuts on your desktop to be used as attack vectors.
It started as a USB flash drive–based exploit which can infect your system simply by opening a flash drive in Windows Explorer. Now, there’s a potential threat whenever Windows loads shortcut icons for display — typically when a user browses Web sites, network drives, or flash drives.
If you are running ESET’s NOD32 antivirus, make sure you have the latest definition file. ESET’s Knowledgebase article NEWS94 details a known conflict between its product and the patch in MS10-046 which may cause your PC to bog down or drop into a BSOD.
► What to do: Accept the update as soon as it’s offered, or go to Support Bulletin MS10-046 and download the patch as soon as you can.
For those running XP SP2, I have bad news: there will not be an update. Instead, your only safe option is to install the Microsoft Fix it in Support article 2286198 and reboot your system.
When you log back into XP, you find that all your icons are now nondescript white boxes, which makes it hard to navigate your way around your desktop. So I urge you again to upgrade to Windows XP SP3 as soon as possible. Then you can properly patch your systems with the KB 2286198 update when it’s offered.
| Have more info on this subject? Post your tip in the WS Columns forum. |
The Patch Watch column reveals problems with patches for Windows and major Windows applications. Susan Bradley has been named an MVP (Most Valuable Professional) by Microsoft for her knowledge in the areas of Small Business Server and network security. She’s also a partner in a California CPA firm.
Forecast for cloud-based servers is hazy
By Susan Bradley
Home-office and small-business users once had few network server options, but now we’re awash in offerings.
With a bewildering number of choices such as data centers, storage in the cloud, and new local-server hardware, deciding what is right for your business is harder than ever.
Vendors hard-selling online business servers
As a small-business owner who manages her own IT and as a regular columnist for Windows Secrets, I’m well versed in server and security issues. But even I have been overwhelmed by the hype over cloud-based services and the number of vendors pushing this relatively new form of data storage.
These vendors make the enticing pitch that my life will be so much easier once I’m no longer maintaining my own servers. They tout advantages such as better data security, better backups, and easier updates and upgrades — since they’ll do those tasks for me.
But with tech journals and forums telling tales of downtime problems and other woes, I’m inclined to tread carefully — especially when looking at business solutions. In his blog, CloudBzz pundit John Treadway called the overabundance of cloud-service providers the era of the red ocean, in which many of these vendors will not survive a future shakeout.
When I’m looking for a safe place to store my firm’s data, I need a high level of confidence that my cloud-services provider will not fold up and vanish in the night. I also need to know that, should this happen, I can quickly and easily move my data to another vendor.
Internet connection speed a reason for worry
How fast data moves over the Internet is the highest hurdle for a workable cloud-based server solution. Slow or unpredictable connections won’t cut it. For example, although cable provides the fastest connections in my area, I’ve run into one of those wacky problems that have dogged telecommunications companies for years: even though the business office for the local cable company is right across the street from my offices, I’m unable to get business-quality service.
In my case, the viable alternative was to speed up my existing DSL connection. I’m using a Linksys RV042 (info page), which combines two DSL lines into one faster connection. That would be fine, except that banks and many other Web sites using secure sockets layer (SSL) security can’t work with my router’s dual-line capability. So I end up running SSL sites through one DSL connection, putting me back to square one.
This problem extends to any cloud-server services I might consider, because they use SSL to protect data as it flows between their servers to my PCs.
MS Aurora server puts the cloud in your office
The problems with cloud-server services have not been lost on vendors, some of which now offer hybrid solutions combining the speed of a local server with the backup and maintenance advantages of a Web-hosted solution.
Microsoft, for example, recently released a beta version of its new Small Business Server, code-named Aurora. It combines an on-site file server with cloud-based e-mail services and SharePoint — Microsoft’s Web-based, document-management platform. Designed for small firms with under 25 workstations, Aurora supports both Windows and Apple workstations.
While many businesses are comfortable with online e-mail services, they’re not ready to keep their financial data in the cloud. With Microsoft’s hybrid service, the local server acts as both the backup system for local workstations and the file server for data that companies want to keep local.
Information on the Aurora beta is available on Microsoft’s Windows Small Business Server site. Based on my informal look at the product, the blend of cloud-based e-mail with local file storage looks promising.
Other vendors offer variations on that theme. Intel’s Hybrid Cloud Pilot Program (info page) combines on-the-premises servers with remote management tools. Customers pay a monthly subscription fee, and Intel partners handle server maintenance and management remotely.
Prominently placed at the Cloud Security Alliance conference (held in conjunction with the Black Hat security conference), Amazon’s EC2 offerings make it a major player in cloud services (info page). But as a traditional brick-and-mortar small-business owner, I find EC2 well above my needs — it’s used by the vendors (such as Intuit) that I use.
Interestingly, Apple and Open-Source solutions trail behind in cloud-based solutions. Apple has no hybrid-cloud offering at this time, but if you have a significant number of its computers, you should take a look its small-business solution. Consisting of the Mac mini with Snow Leopard Server (info page), it blends a small computer with the basic tools a small firm needs to share information, files, and e-mail.
Still interested in a free, open-source solution, even if it’s not natively in the cloud? Check out ClearFoundation’s ClearOS (info page), a network server that includes Internet gateway tools, file serving, an e-mail system, and more. Be aware, however, as with other open-source solutions, you’ll need to pay for ClearFoundation’s support offerings if you need professional help.
Before investing in any of these solutions, ensure that they support your key business applications or that you can add a Windows box to the system to run the mission-critical apps.
Pushing toward pure-cloud computing solutions
At Microsoft’s Worldwide Partner Conference in Washington, D.C., it was obvious that Microsoft is taking aim at Amazon’s and Google’s cloud services. Microsoft gave more details on future versions of its pure-cloud-based operating system Azure, which will include ready-to-use, server-based, big-box appliances that can be shipped immediately to data centers.
But to be clear: just like Amazon’s EC2, Microsoft’s Azure operating system will be used more by application vendors to build software we will all use in the cloud — it’s not an application system small businesses like mine will rent or use directly.
For individuals and small businesses, Google docs is the reigning online-only platform for creating and sharing documents. Small firms can use Google docs for word processing, spreadsheets, presentations, and more. (See Figure 1.) And they can share their docs within the firm and with outside collaborators. Although convenient, that capability is not without its hazards. Over a year ago, a TechCrunch story took Google to task for information leaks on the Google docs platform.
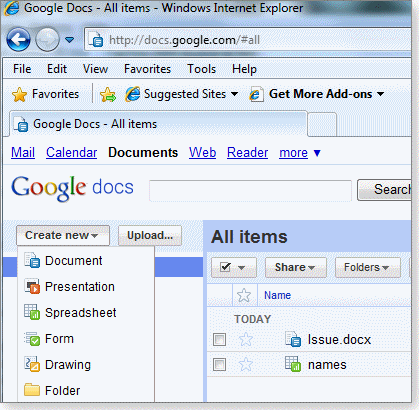
Figure 1. Google docs lets individuals and small firms create and share many types of common business documents.
Microsoft may be facing similar concerns as it pushes PC users onto its online Windows Live Office and Skydrive platforms, which allow members to compose and share documents, entirely online. (See Figure 2.) Windows Secrets has reported on Windows Live security flaws in several recent stories, such as Woody’s April 22 Top Story, “Hotmail’s social networking busts your privacy,” and Yardena Arar’s July 1 column, “Office 2010’s Web tools raise security questions.”

Figure 2. Microsoft’s cloud-based apps and its Skydrive online storage provide business applications, documents storage, and sharing online.
Businesses needing more secure document management can use SharePoint 2010 and Office Web apps, installed on local Web-hosting servers. But there’s a catch: to host your own version of Office Web Apps and replicate what Microsoft’s Skydrive offers consumers, you’ll need to have an Office 2010 volume license in addition to the SharePoint 2010 server.
Microsoft plans to offer hosted versions of Office applications you can use through your browser — without requiring locally installed copies of Office. But before it can do that, it will have to upgrade its own Business Productivity Online service to the latest versions of SharePoint 2010.
Keep your business data storage solutions mobile
If you choose a hybrid server solution or one that has just hosted server maintenance, make sure you can move your data easily and quickly. The hallmark of a successful small business is agility, and you need to ensure that your data management is just as flexible. Review the vendor policies for exporting data or obtaining backups, or use third-party products such as Archiver (info page) to move your hosted data back down to a local location for peace of mind.
Conversely for those that have local servers, you may wish to investigate cloud-based backup solutions that allow you to move the local data up to cloud storage or even have fall-over to a cloud-based copy of your server. But make sure you get a solution that isn’t just a consumer desktop solution; get one that will back up servers fully. Online backup services such Evault, Doyenz, and Symform are just three among many services offering Internet backup solutions for servers.
Bottom line: The small-business server solutions are varied and rich — and quite confusing. But with some research, you can find a solution that will work perfectly with your particular needs.
| Have more info on this subject? Post your tip in the WS Columns forum. |
Susan Bradley has been named an MVP (Most Valuable Professional) by Microsoft for her knowledge in the areas of Small Business Server and network security. She’s also a partner in a California CPA firm.
Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com).
Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners.
Your email subscription:
- Subscription help: customersupport@askwoody.com
Copyright © 2025 AskWoody LLC, All rights reserved.

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Updates seem to have broken Microsoft Edge
by
rebop2020
2 hours, 13 minutes ago -
Wait command?
by
CWBillow
1 hour, 22 minutes ago -
Malwarebytes 5 Free version manual platform updates
by
Bob99
5 hours, 8 minutes ago -
inetpub : Microsoft’s patch for CVE-2025–21204 introduces vulnerability
by
Alex5723
11 hours, 44 minutes ago -
Windows 10 finally gets fix
by
Susan Bradley
20 hours, 37 minutes ago -
AMD Ryzen™ Chipset Driver Release Notes 7.04.09.545
by
Alex5723
21 hours, 57 minutes ago -
Win 7 MS Essentials suddenly not showing number of items scanned.
by
Oldtimer
16 hours, 30 minutes ago -
France : A law requiring messaging apps to implement a backdoor ..
by
Alex5723
1 day, 11 hours ago -
Dev runs Windows 11 ARM on an iPad Air M2
by
Alex5723
1 day, 11 hours ago -
MS-DEFCON 3: Cleanup time
by
Susan Bradley
6 hours, 50 minutes ago -
KB5056686 (.NET v8.0.15) Delivered Twice in April 2025
by
lmacri
3 hours, 31 minutes ago -
How to enable Extended Security Maintenance on Ubuntu 20.04 LTS before it dies
by
Alex5723
1 day, 23 hours ago -
Windows 11 Insider Preview build 26200.5562 released to DEV
by
joep517
2 days, 3 hours ago -
Windows 11 Insider Preview build 26120.3872 (24H2) released to BETA
by
joep517
2 days, 3 hours ago -
Unable to eject external hard drives
by
Robertos42
13 hours, 34 minutes ago -
Saying goodbye to not-so-great technology
by
Susan Bradley
1 hour, 15 minutes ago -
Tech I don’t miss, and some I do
by
Will Fastie
7 hours, 8 minutes ago -
Synology limits hard drives
by
Susan Bradley
3 days, 7 hours ago -
Links from Microsoft 365 and from WhatsApp not working
by
rog7
2 days, 9 hours ago -
WhatsApp Security Advisories CVE-2025-30401
by
Alex5723
3 days, 13 hours ago -
Upgrade Sequence
by
doneager
3 days, 6 hours ago -
Chrome extensions with 6 million installs have hidden tracking code
by
Nibbled To Death By Ducks
1 day, 12 hours ago -
Uninstall “New Outlook” before installing 2024 Home & Business?
by
Tex265
2 days, 5 hours ago -
The incredible shrinking desktop icons
by
Thumper
4 days, 10 hours ago -
Windows 11 Insider Preview Build 22635.5240 (23H2) released to BETA
by
joep517
4 days, 11 hours ago -
Connecting hard drive on USB 3.2 freezes File Explorer & Disk Management
by
WSJMGatehouse
1 day, 11 hours ago -
Shellbag Analyser & Cleaner Update
by
Microfix
1 day, 4 hours ago -
CISA warns of increased breach risks following Oracle Cloud leak
by
Nibbled To Death By Ducks
4 days, 21 hours ago -
Outlook 2024 two sent from email addresses
by
Kathy Stevens
6 hours, 57 minutes ago -
Speeding up 11’s search
by
Susan Bradley
2 days, 9 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.

