
|
There are isolated problems with current patches, but they are well-known and documented on this site. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
Data-encryption alternatives to TrueCrypt
In this issue
- TOP STORY: Data-encryption alternatives to TrueCrypt
- BEST HARDWARE: Devices for Win8, cloud storage — and your car
- LOUNGE LIFE: How to keep pieces of the Web for later
- WACKY WEB WEEK: Because of how you look: Through Google Glass
- LANGALIST PLUS: More on better data/boot security for Windows
- PATCH WATCH: Patch Watch update: Hyperbole about an IE update
Data-encryption alternatives to TrueCrypt
It seems as if everyone who kept sensitive files secure did it with TrueCrypt. Edward Snowden depended on it. So did I.
But now that the popular disk-encryption app is effectively dead — at least for the foreseeable future — it’s time to look for a replacement.
In last week’s (June 12) Top Story, “The life and untimely demise of TrueCrypt,” Susan Bradley reviewed the application’s history and stated, “It’s a mystery that we gave TrueCrypt such an extraordinary level of trust. It had dubious legal foundations, its developers were unknown, and its support was primarily relegated to forums that are now missing.”
In this follow-up article, I’ll discuss my own approach to protecting sensitive files, and I’ll explain why I — unlike Susan — typically don’t recommend Microsoft’s BitLocker. I will recommend two file-encryption programs that might take TrueCrypt’s place.
How safe is safe enough — and for what?
Let’s use your home as an analogy. You probably keep your front door locked — at least at night and when you’re away. You might have an alarm system or even bars on the windows. But your security system most likely doesn’t match those used by New York’s Metropolitan Museum of Art or the Getty Center in Los Angeles.
Why? Well, for one thing, you can’t afford it. But mostly, it would be overkill. Few of us have anything in our homes that would attract the sort of professional thieves who might steal a Van Gogh.
To a large extent, the same rules apply to data. It takes a lot of time and skill to crack encryption, and most criminals are looking for an easy score. Even the NSA, which has the ability to crack all but the best encryption, probably won’t bother. It might soak up everyone’s cellphone metadata because that’s relatively easy. But it reserves the hard work for the few people of interest.
That doesn’t mean you shouldn’t take precautions. Going back to that house analogy, encrypting sensitive files is like locking your front door — a reasonable and generally sufficient line of defense. (And you must ensure that unprotected bits of those files don’t remain on your hard drive.) You also need to protect the encryption key with a long, complex password that’s extremely difficult to crack — and be wary of phishing scams and other deceits that might trick you into handing over the key.
Which files should be encrypted and where?
You don’t need to encrypt every file. We’ll assume that neither the NSA nor criminals are really interested in your collection of cat photos or your daughter’s term papers.
Obviously, you do need to protect files containing bank statements, credit-card information, and Social Security numbers — basic data about your personal identity. But you also might want to encrypt any information that you don’t want others to see — and anyone else’s personal information you might possess. The simple rule: If in doubt, encrypt it.
Your work might dictate different encryption procedures. For example, a small construction company might need to encrypt just a few financial and customer files, whereas nearly every file an accountant handles probably needs encryption.
The safest place for sensitive files is on an encrypted (and fully backed-up) partition or drive. File-by-file encryption can leave temporary, unencrypted copies on the hard drive. But if every sector on the drive is encrypted, these temporary copies will be unreadable as well.
I’m partial to using a virtual drive/partition — what TrueCrypt called a volume. This is typically a single, often quite large, encrypted file. When you open it with the correct password, Windows sees it as a standard drive from which you can launch files, manage them with Windows Explorer, and so on. When you’re done, you close the volume and all files inside are once again inaccessible. Temporary and “deleted” files stay within the volume, so they, too, are encrypted.
You can, of course, encrypt real partitions. In fact, you can encrypt all partitions — including C:. Booting and signing in to Windows automatically opens these encrypted, physical partitions. But if someone boots the system from a flash drive or connects your hard drive to another computer, nothing will be accessible.
Arguably, this is the safest type of data protection. Because your entire hard drive is encrypted, even Windows’ swap and hibernation files are locked. But full-drive encryption has its own problems. For example, you won’t be able to pull files off an unbootable system by using other boot media.
Also, with full-drive encryption, all data files are accessible whenever you’re signed in to the PC. They can be stolen by a remote cyber thief via malware or by a co-worker while you’re on a coffee break. By contrast, you have to consciously open an encrypted volume, which can remain locked when you’re in a not-so-safe environment — such as on a public Wi-Fi network.
Bottom line: Full-drive encryption makes the most sense if you work primarily and continuously with sensitive information — as in accounting. In most cases, an encrypted partition makes more sense; it’s nearly as secure as full-drive encryption and offers more flexibility. File-by-file encryption is the least secure but is worth considering if you can’t use drive/partition encryption, as discussed in the May 15 Top Story, “Better data and boot security for Windows PCs,” and in a follow-up in this week’s LangaList Plus.
BitLocker best for corporate environments
For many, Windows’ own BitLocker encryption tool is the obvious TrueCrypt replacement. Susan Bradley put it at the top of her short list, and the infamous TrueCrypt warning on the SourceForge download page provides extensive directions for setting it up.
BitLocker comes with Windows 7 Ultimate and Enterprise plus Windows 8 Pro and Enterprise. It can encrypt real and virtual partitions or the entire drive. In my view, BitLocker has its place — primarily when managed by a PC expert in an office scenario. BitLocker is sort of set-and-forget; non-techie office workers can simply sign in and out of Windows in the normal way without even knowing (or caring) whether their files are encrypted.
But for personal use, BitLocker’s password/key system can be overly complex or confusing. For example, when you set up BitLocker, you create an unlock password. (You can also have a BitLocker-encrypted drive unlock automatically when users sign in to Windows — or they can use a smartcard or PIN.) But you must also create a separate key-recovery password that’s stored on the system if the PC has a Trusted Platform Module (TPM; more info) chip, or on a flash drive if it doesn’t. Setting up BitLocker on a system without a TPM chip can take some time and admin skills.
Basically, if you don’t have a newer PC and an advanced version of Windows, BitLocker is simply not a viable option. For an individual maintaining his or her PC, it’s just another layer of complication.
Here are two better data-encryption applications for personal PCs.
DiskCryptor: For drives and partitions
Like TrueCrypt, DiskCryptor (info) is free. It’s also open-source, though I’m not as confident as I once was that being open-source is an advantage. (As Susan pointed out last week, “There’s even debate whether TrueCrypt qualifies as open-source.”
DiskCryptor is designed to encrypt partitions. According to the DiskCryptor site, Windows 8 isn’t supported. But it seemed to work fine encrypting a separate, nonboot partition on a fully updated Win8.1 Update system.
DiskCryptor’s user interface is somewhat unattractive, but it’s relatively easy to figure out. The program offers industry-standard AES, Twofish, and Serpent encryptions (see Figure 1). If you’re really paranoid, you can combine them, encrypting first one way and then another.
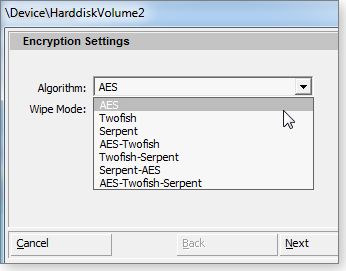
Figure 1. DiskCryptor lets you combine encryption technologies for extra security.
A simple wizard helps you quickly encrypt any partition — including C:. If you encrypt C:, you’ll have to enter your DiskCryptor password before Windows will load. (If C: is your only partition, you’ve effectively encrypted the entire drive. Note: As with all current, third-party encryption apps, you can’t use DiskCryptor on a Win8 system’s boot [C:] drive that has Secure Boot enabled. For more info, see “Reader disagrees with data-encryption advice” in this week’s LangaList Plus [paid content].)
Although DiskCryptor doesn’t support TrueCrypt-like virtual partitions, you can use a real partition for a similar result. Use Windows’ Disk Management program or a third-party partition tool to create a small, separate partition for your sensitive files. Then use DiskCryptor to encrypt that partition (see Figure 2). The result is much like a TrueCrypt volume, except that it’s a real partition.

Figure 2. DiskCryptor's main menu for managing drive encryption
But using a real partition has some disadvantages. For example, the encrypted partition is clearly visible in Windows’ Disk Management, though it’s labeled as unformatted.
And backups can be tricky. The only way to back up the files when the partition is closed is with image-backup software. Using the default settings for EaseUS Todo Backup resulted in an error message, as shown in Figure 3. After selecting the sector-by-sector backup option, both the backup and the restore worked.

Figure 3. Backing up an encrypted partition with EaseUS default settings generated an error message.
You can also open the partition and use a conventional file-backup program. But make sure it’s one that has its own built-in encryption to secure your files.
On the other hand, backup is very simple with a virtual partition, which to Windows is simply another (really big) file. Keep the file in a standard folder — such as Documents — and it’ll get backed up automatically and regularly.
Cryptainer LE: The tool for virtual partitions
If, like me, you prefer a virtual partition, Cryptainer LE (also called Cypherix LE; site) is the better option. The free version doesn’t let you create a volume greater than 100MB (see Figure 4), but if you’re judicious about what you encrypt, it might be enough.
And if it isn’t enough, you can shell out U.S. $30 and get Cryptainer ME, which comes with a 2.5GB-file limit. Shell out $70, and you can create terabyte-sized volumes. But if you’re going that big, you may as well encrypt the whole drive.
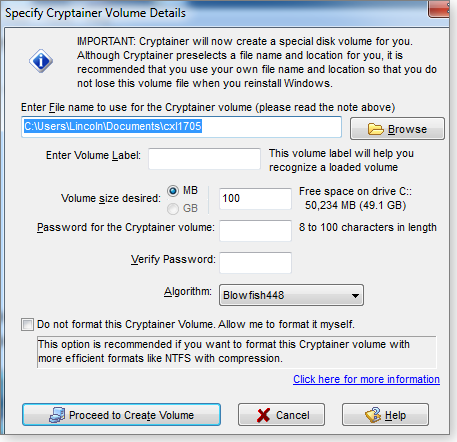
Figure 4. The free Cryptainer LE lets you set up small encrypted volumes.
Cryptainer is easy to set up and use; the buttons are big and colorful, and — more importantly — they’re easy to understand. Tabs help you use and control multiple volumes (see Figure 5).

Figure 5. Cryptainer LE has a simple menu system for creating and managing encrypted volumes.
When you set up a volume, the free version appears to offer AES 256-bit and Blowfish 488-bit encryption — but you actually get only 128-bit Blowfish. Again, for most people, that’s sufficient. Blowfish 488-bit and AES 256-bit encryption are, obviously, enabled in the paid versions.
The choice: Stay with TrueCrypt or move on
If you don’t already have TrueCrypt, either DiskCryptor or Cryptainer should do; it just depends on how you prefer to work with encrypted files. (Or, if your encryption needs are relatively simple, use file-by-file encryption as detailed in the May 15 Top Story.)
On the other hand, if you’re already using TrueCrypt, you can probably stick with it — at least for a while. As Susan pointed out, a formal code review of TrueCrypt showed that it “does not have any back doors and still provides secure encryption that can’t be easily cracked.” (Note: There’s still a downloadable version of TrueCrypt, but it’s read-only — i.e., you can open encrypted volumes to remove files, but you can’t create new ones.)
Currently, I’m still using TrueCrypt. But I don’t know for how long. TrueCrypt, like many other public encryption applications, can be cracked with some effort and the right tools. With no updates, it might become more vulnerable over time. If a new version of TrueCrypt doesn’t rise from the ashes relatively soon, I’ll seriously consider moving over to Cryptainer LE or ME.
Devices for Win8, cloud storage — and your car
Windows 8 got off to a rough start, mostly because of Microsoft’s misguided attempt to move all Windows users to touch-and-swipe.
Fortunately, new devices help us live comfortably in both old and new Windows. Plus: New products that keep your data safe and your mobile devices running.
Classic mouse meets Windows 8 touch gestures
It’s a safe bet that the majority of Windows 8 users have not migrated to — nor become comfortable with — touch-enabled 8 computers. Sure, that fancy new notebook has a massive touchscreen, but it’s likely you’re mostly navigating with the standard touchpad or an external mouse. There are significant ergonomic issues with using a touchscreen, but aside from that, most of us have spent too many years mousing around with XP and Win7. That said, there are times when Win8’s touch gestures make working with Windows just a bit faster: scrolling through webpages, for example.
Bowing to the obvious, both Logitech and Microsoft offer hybrid touch-enabled mice. In theory, you get the best of both worlds. I reviewed Logitech’s Ultrathin Touch Mouse T630 in the Dec. 12, 2013, Best Hardware column. And though I could appreciate Logitech’s approach to gesture-based navigation, the device still lacked the familiar buttons and scroll wheel of a typical mouse.
That’s not the case with Logitech’s new Wireless Mouse M560 (U.S. $40; more info); it’s obviously designed for Win8 users who prefer the shape and function of a traditional pointing device.
Available in black or silver, the nicely sized M560 (Figure 1) is, according to Logitech, configurable for both lefties and righties. But with thumb buttons on only the left side, this mouse still favors righties. To reduce hand fatigue, it has sculpted sides lined with soft rubber grips. Along with the standard left-click/right-click buttons and center scroll wheel, the M560 includes a small Windows 8 button, located just behind the scroll wheel.

Figure 1. Logitech's Wireless Mouse M560 combines a traditional mouse form with a few Windows 8–specific controls. Source: Logitech
The Win8 button gives quick click-and-slide access to the Charms bar and the App Bar. It’s a handy addition; a standard mouse annoyingly requires you to hover the cursor in the corner until the Charms bar opens.
The M560 includes two buttons on the left side, and you can customize button/scroll functions via Logitech’s SetPoint software (free download; see Figure 2). The package comes with Logitech’s thumbnail-size Unifying USB Receiver, which can connect multiple keyboards and pointing devices.

Figure 2. Logitech's SetPoint software lets you customize the M560's buttons and scroll wheel to your preferences.
Unlike the T630 mouse, this model isn’t giving you the full range of touch-gesture support. But for the typical desktop user, it doesn’t need to. You can find the M560 online for about $25. Try it out — at that price, if you don’t like it, you won’t feel bad passing it along to someone else.
Roadside assistance for cars and mobile devices
The proliferation of mobile devices has, not surprisingly, created a burgeoning market for portable recharging power packs. They come in sizes as small as lipstick cases and as large as car batteries. Everyone seems to have a particular spin on portable power packs — including Cobra, best known for radar detectors. It’s come up with a box that will charge your cellphone — and jump-start your car, too.
About the size of a large cell phone, the $130 Cobra JumPack (info) weighs 10.5 ounces and delivers 7,500 mAh from its lithium-cobalt battery. The box might look like any other power pack with a USB port until you pull out the two jumper cable–size alligator clips (Figure 3). Cobra claims that the JumPack has enough power to jump-start a car several times on a single charge.

Figure 3. The versatile Cobra JumPack both charges portable electronics and jump-starts cars. Source: Cobra
True to its automotive roots, the JumPack includes a built-in LED flashlight with three settings: full beam, emergency strobe, and S.O.S. flasher.
As luck would have it, right after receiving my test unit, a friend left his car’s interior lights on overnight, effectively killing the battery. “Aha!” I thought, “Here’s a convenient test for the JumPack and a way to avoid calling AAA.”
The process proved brain-dead simple. First, press the Power/Flashlight button to check the current battery capacity. With all four LEDs lit, I confirmed the JumPack was fully charged. Next, as with any jumper cable, connect the red clamp to the positive post on the car battery and the black clamp to an unpainted bolt or body part as far from the battery as the short cables will allow (to prevent a possible battery explosion). Finally, connect the cables to the JumPack port.
When my friend turned on the ignition, the engine started and I removed the cables. While he went on his way, I checked the JumPack’s remaining power. Two lit LEDs meant there was still 40 to 65 percent battery capacity, some of which I then used to charge my iPhone. (The LED power-capacity lights stay illuminated during a charging session.)
The possible knock on the JumPack might be its own charging options. You can plug it into AC or into a car’s 12-volt cigarette-lighter plug. But unlike many other small, portable power packs, there’s no option for plugging it into the USB port of some other device or adapter.
Fail-safe data backups in a personal cloud
In the Oct. 10, 2013, Best Hardware column, I lavished praise on Western Digital’s personal-cloud hard drive — the WD My Cloud. I noted that the box sat near my desk — not at some remote site — yet still provided Wi-Fi and Internet connectivity.
I concluded that “Given its cost, the $135 2TB device is an ingenious solution that frees me from monthly cloud storage fees, bandwidth limitations, and the remote possibility of cyber attacks on my data stored on someone else’s remote server.” Moreover, its Wi-Fi let me stream a variety of media to my smartphones and tablets, saving space on their limited internal storage.
Now, to make our data even more secure, Western Digital has released the dual-drive My Cloud Mirror (info) in 4TB, 6TB, and 8TB capacities. The Mirror (Figure 4) uses the same desktop and mobile app-management software of the original My Cloud, including the built-in ability to connect to Dropbox and other cloud-based storage sites.

Figure 4. Western Digital's My Cloud Mirror has dual hard drives that can be set up as either RAID 1 (mirror) or RAID 0.
By default, the drive is set up with RAID 1; all data on one internal hard disk is mirrored on a second disk. If the one disk fails, your data is preserved on the other disk. The box is designed so that you can replace a failed drive yourself.
If you’re more interested in performance and capacity, you also have the option of reformatting the drive as RAID 0, in which case data is spread across both disks.
Western Digital has made setting up the My Cloud Mirror a quick, five-minute task. With Gigabit Ethernet and a 1.2GHz processor, file transfers go at a fast clip and videos stream without hiccups. The box’s software lets you easily back up data on mobile devices such as phones and tablets.
The 4TB My Cloud Mirror I tested weighs in at a hefty five pounds — it’s not designed to be portable storage. It’s compatible with Windows, from XP SP3 on, and with most OS X systems. The 4TB unit costs $350; add $100 for the 6TB unit and $200 for 8TB.
The need for speed: A quick and portable SSD
Using solid-state drive technology and possessing both USB 3.0 and Thunderbolt interfaces, LaCie’s upgraded Rugged hard drive (info; Figure 5) delivers blazing data-transfer speeds — especially when compared to the still all-too-common, platter-based, USB 2.0 drives. (Although an Intel creation, Thunderbolt is still primarily the domain of Macs; Thunderbolt-enabled PCs are few.)

Figure 5. LaCie's upgraded Rugged drive has a shock-proof case and fast USB and Thunderbolt ports.
Although LaCie offers ruggedized models from 120GB to 2TB, only those below 1TB are solid-state. Thunderbolt provides the fastest speeds (up to 387 megabytes per second), but USB 3.0 is no slouch, either. I copied a 3.6GB file to an SSD model via USB 3.0 in 12 seconds. For comparison, copying the same file to a USB 2.0 hard drive took 11 minutes.
USB 3.0 also means that a single cable supports both data and power. The drive will work with USB 2.0 ports but not efficiently.
Wrapped in a removable, rubber-like case, the drive can weather, according to LaCie, a 6.6-foot drop — as well as dust and moisture (it’s not waterproof). So whether the drive accidentally falls off your desk or falls out of your pack on some desert Jeep track, your data should be protected and accessible.
Ruggedized electronics are never cheap — and neither is exceptional performance. The three SSD models cost $220 for 120GB, $300 for 250GB, and $500 for 500GB.
I asked a LaCie representative whether consumers could opt for a color less conspicuous than the bright orange casing. Apparently, the company had considered this but ultimately honored the concept of logo designer Neal Poulton. At least you’ll probably never lose sight of an electric-orange device.
How to keep pieces of the Web for later
Lounge member Olleym had been accustomed to copying into a Word doc the parts of webpages he wanted to read later. But technological times have changed; many sites don’t allow that anymore.
Posting in the Other Applications forum, he asked for help from fellow Loungers; they responded with some interesting solutions.
The following links are this week’s most interesting Lounge threads, including several new questions for which you might have answers:
 starred posts: particularly useful
starred posts: particularly useful
If you’re not already a Lounge member, use the quick registration form to sign up for free. The ability to post comments and take advantage of other Lounge features is available only to registered members.
If you’re already registered, you can jump right into today’s discussions in the Lounge.
Because of how you look: Through Google Glass
 |
When Jason Jones of the Daily Show reviewed Google Glass recently, he interviewed six Glass Explorers (the official term for Google Glass early adopters). It would be fairer to say he mocked them to their Glass-bedecked faces, from start of the segment to the end of it. The comedy might have been broad, but it nicely identified more at issue for Glass critics than the look: the fancy glasses are cameras (and phones and browsers and so on). Naturally, the Glass Explorers defend their position at the head of the technology pack. They might be subject to muggings in the street and assaults in bars (“hate crimes,” asserts one of the evangelists). But in another year, they sincerely believe, everyone will be wearing Glass. Based on this amusing — and thought-provoking — skit, we can only hope that’s not the case. Click below or go to the original video. |
| Post your thoughts about this story in the WS Columns forum. |
More on better data/boot security for Windows
TrueCrypt has been discontinued — at least for now — but that unhappy news simplifies the choice of whole-disk versus file-and-folder encryption.
Plus: An old partition question arises anew, Internet Explorer opens only blank pages, and using permanent markers aids warranty claims.
Reader disagrees with data-encryption advice
The May 15 Top Story, “Better data and boot security for Windows PCs,” generated some interesting reader mail.
Soon after that article’s publication, the developers of TrueCrypt — possibly the world’s most popular third-party, whole-disk encryption tool — unexpectedly and rather mysteriously announced they were shutting down operations. Effectively, the TrueCrypt project was dead. (Susan Bradley wrote about the apparent end of TrueCrypt in the June 12 Top Story, “The life and untimely demise of TrueCrypt.”)
Though shocking, TrueCrypt’s demise strengthens some of the arguments I made in the May 15 story — as the following exchange with reader Jon C illustrates.
- “I usually appreciate the depth and perspective of Fred Langa’s articles, but I feel that there were some major omissions in the ‘Better data and boot security for Windows PCs’ article.
Apart from a brief reference to whole-disk encryption being ‘the gold standard,’ he seemed to be saying that a BIOS-based password plus encrypted files/folders is basically just as good [as whole-disk encryption] — and is the better choice in the UEFI environment. A combination of BIOS passwords and file encryption might be more reliable, but it’s certainly not ‘better security.’
“I think that any article on this subject should at least address data in the page and hibernation files on the hard disk, not to mention temp files like those created by apps such as MS Word. To my knowledge, whole-disk encryption is the only way to protect against attacks on these disk-based files. Granted, attacking these files is more work for malware or a hacker, but it seems no different than digging through raw memory on a server exploited by Heartbleed.”
You’re correct in stating that file-and-folder encryption is not intrinsically as thorough as whole-disk encryption. That’s why I called whole-disk encryption the “gold standard.”
But third-party, whole-disk encryption currently doesn’t work properly on Windows 8. It might never work correctly, because it’s fundamentally at odds with Secure Boot and Unified Extensible Firmware Interface (UEFI).
So arguments about the theoretical advantages of whole-disk encryption become moot with Windows 8. For the foreseeable future, whole-disk encryption simply is not an option.
Yes, BitLocker is an option with some editions of Windows (more info), but BitLocker has its own problems. See, for example, the Sept. 13, 2012, Top Story, “Rethinking the process of hard-drive sanitizing.” Skip down to the section titled “Windows’ built-in encryption-tool limitations.”
That might change. Perhaps Microsoft will improve BitLocker. Or maybe some third-party, whole-disk encryption option will come along that doesn’t run afoul of Windows 8’s UEFI-based Secure Boot. Also, it’s been reported that the Linux Foundation will take over the TrueCrypt code; perhaps that group will produce a Win8-compatible version of TrueCrypt.
But until then, Windows 8 users have no better option than file-and-folder encryption.
A new slant on an old partitioning question
Christopher Sirr asks a question that crops up with some regularity in reader mail:
- “I have a chance to start clean with a replacement PC, due to arrive in a few weeks.
“It will have over 5TB of disk space on two hard drives (3TB and 2TB) plus a 128GB SSD.
“Can and should I try to partition as follows:
- 1st drive: Windows 8.1 only
- 2nd drive: Programs only
- 3rd drive: Files only
“Or do the programs need to reside in the same partition or drive as Windows?
“Also, should I request Windows 8 to be installed on the SSD drive? Everything I’ve read so far doesn’t quite answer the questions.”
I’ll make suggestions as to how to use your abundant drive capacity in a moment. But first I must state that I no longer recommend changing Windows’ default file locations.
The full explanation appears in the Dec. 19, 2013, LangaList Plus article, “Why relocating default folders is no longer wise.” But the bottom line is this: if you place files in nonstandard locations, you’re working against Win8’s ability to back itself up.
Win8 has a pretty good, automated, near-real-time backup feature called File History that’s turned on by default. But it normally backs up only standard locations; if you place files elsewhere, File History might not “see” the files and thus not back them up. (For more info, see the July 11, 2013, Top Story, “Understanding Windows 8’s File History.”)
So with that in mind, here’s what I recommend:
The SSD is, of course, your fastest drive. Put the files you access most frequently on that drive. That includes Win8, all regularly used third-party programs, plus all your routine user files. With 128GB to play with, you shouldn’t have any problem fitting it all in.
Next, I’d suggest using the 3TB drive to store bulky files that don’t change often — and consequently don’t need regular backups. For example, store your movies, music, and photos there.
You could also use that drive to store copies of the installation files for your important software. (Those files might be in an as-downloaded format such as .msi or similar format, or they might be .iso-based copies of the installation CDs/DVDs.) Group each program’s installation files within separate folders: for example, an Office Install Files folder, a Photoshop Install Files folder, and so on. To each folder, add a .txt file containing any related application keys.
Creating this kind of software library on a local hard drive will simplify and speed any future software reinstallations — it will also let you tuck away your original CDs or DVDs in a location where they won’t get scratched, lost, or otherwise rendered unusable.
Finally, I’d use the 2TB drive for backups. Assign that drive to Win8’s File History, but also use it to store periodic system images in their own separate folders. (See “Creating customized recovery images for Win8” in the Oct. 10, 2013, Top Story.)
With the above setup, or something along those lines, you’ll be well organized and working with — not against — Win8’s built-in backup mechanisms.
With over 5TB of space, you’ll have plenty of room to grow — probably for years to come!
Internet Explorer launches with blank pages
Mike Clauson’s copy of IE is malfunctioning.
- “I have a newish, fully updated, Win8 notebook.
“I am not sure what happened recently, but I am unable to open Internet Explorer. When I click on the IE icon, it tries to open but just displays a blank page.
“I can use other browsers, but this IE issue has vexed me for two weeks! Can you assist me in restoring functionality?”
Sure, Mike!
But I interpret your browser’s symptoms a little differently than you do:
I think Internet Explorer actually is working; it launches and opens a page. But something — a setting, an add-on or extension, malware, etc. — is preventing IE from loading and displaying your normal homepage or whatever page you’re trying to see.
This might be easy to fix by just resetting your browser.
You can revert IE to its default, just-installed state with a few clicks. The process removes all add-ons, third-party toolbars, and extensions, plus it restores the browser’s default settings. It usually returns a browser to full operation. IE also lets you choose whether the reset should delete or retain personal data (history, cookies, passwords, and so forth) stored within the browser. You don’t have to lose your browser data — unless you want to!
For complete instructions in resetting IE, see the Jan. 6, 2011, LangaList Plus article, “Return IE to its just-installed state with ease.” Microsoft also offers an automated tool and manual instructions on MS Support page 923737, “How to reset Internet Explorer settings.”
(Note: Every major browser offers similar ways to revert to its default state. Check the browser’s help file.)
If resetting the browser doesn’t help, then I’d suspect malware. Something might be trying to hijack your homepage settings.
Fixing that takes a little time but usually isn’t very difficult. You can deep-scan and thoroughly clean your PC of infections with one or more of the tools discussed in the April 11, 2013, Top Story, “A dozen tools for removing almost any malware.”
With known-good settings, and no malware at play, your copy of IE should work normally again.
Permanent markers aid warranty claims
Louis Schenfeld offers this useful tip:
- “I’ve never run across a recommendation to label hard drives with their purchase date and source. I have two identical hard drives that were purchased at different times. One just failed, and I don’t recall when and where I purchased it. From now on, though, I am going to label each drive I install with the date of purchase.”
Nice idea!
I suggest, however, not writing directly on the part itself. Instead, write the info on a small slip of paper and tape it to the part in question. Or apply a strip of tape to the part and use a permanent marker to write the warranty info on the tape. Using removable tape or paper would ensure that a vendor couldn’t void your warranty claim simply because your labeling “altered the case” — or some such excuse.
On the other hand, marking the case is sometimes the point. I use permanent markers to help identify my laptops, tablets, cameras, and other portable electronic devices. I write my name and phone number on the device and then cover the writing with a piece of clear tape to prevent the ink from wearing off.
And, of course, I use permanent markers to write labels for DVDs and CDs. (Use a felt-tip marker; it’s the safe way to write on optical discs.)
But I’d never thought of writing purchase dates and warranty info on hard drives and similar gear. Good idea. Thanks!
| Reader Louis Schenfeld will receive a gift certificate for a book, CD, or DVD of his choice for sending the tip we printed above. Send us your tips via the Windows Secrets contact page. |
Patch Watch update: Hyperbole about an IE update
An article on Windows patching included the startling headline that Microsoft is restricting security patches for IE 11 on Windows 7.
What particularly caught my eye was the report that Win7 users would not be receiving the June Internet Explorer patch in Windows Update.
Much ado about Internet Explorer updating
A June 16 InfoWorld headline proclaimed, “Microsoft strips some Windows 7 users of IE 11 patch privileges.” The patch in question was KB 2957689, the June cumulative IE update that fixed (as I noted in the June 12 Patch Watch) a whopping 59 vulnerabilities.
The InfoWorld story caught my attention mostly because I distinctly remember seeing KB 2957689 offered in my Windows 7 machines. And though it’s true that the June IE 11 for Win7 patch requires you to have an April IE cumulative update installed, that doesn’t mean Microsoft is suddenly changing the rules and making it difficult for Win7 users to update IE 11.
According to MS Support article 2957689, “All future security and nonsecurity updates for Internet Explorer 11 require you to have update 2919355 [Win8.1 Update] or update 2929437 [Win7 SP1] installed in order to receive updates.”
Here’s why that’s not a cause for concern.
Microsoft is currently maintaining many different patching branches. That’s hard to do, and it’s mostly Microsoft’s own fault. Back in April, Microsoft released two versions of MS14-018, April’s IE security update. That seemed a bit odd at the time. KB 2936068 was just the security update; KB 2929437 included the security fixes plus Enterprise Mode and an update to IE WebGL renderer. You could actually install both without a problem, as I did on my home machine.
Ideally, every cumulative IE update would include all previous patches, so we wouldn’t have to play the game of adding patch on top of patch — which some Windows 8.1 users are now struggling with as they try to install Windows 8.1 Update (KB 2919355). Unfortunately, an all-inclusive update is probably impractical.
But though Win9.1 Update is a true hardship for more than a few Win8.1 users, requiring KB 2929437 isn’t. That InfoWorld article left me scratching my head. I’d had no problems installing the April IE updates on any of my Win7 systems, nor had I seen any reports of problems. In truth, it was a rather routine update, and there was no reason not to install it. Keeping IE patched against new vulnerabilities is always important.
An Office Click-to-Run error truly is worrisome
June was not so trouble-free for Office 2013 users who get silent updates via Click-to-Run. (See the Dec. 4, 2013, On Security story for more info on Click-to-Run.)
Click-to-Run acts like an Application Virtualization (App-V; more info) deployment: it streams down the entire program rather than installing individual updates.
According to an MS Office Sustained Engineering Team blog, there were reports, after the June updates had gone out, that some Office Click-to-Run users were unable to open their Office apps (see Figure 1). The blog goes on to state that less than one percent of the users were affected.

Figure 1. A relatively small number of Office 2013 Click-to-Run users received this error message after the June updates had been released.
At this time, to correct the problem, Click-to-Run users have to uninstall and then reinstall Office, as noted in a Microsoft Community thread.
As with Windows Update patches, I recommend disabling automatic updating in Click-to Run for now. To do so, click on any Office 2013 app and then click File/Account. On the right side of the screen, click Update Options and then select Disable updates. That will stop automatically streamed updates. I’ll revisit this issue in the next Patch Watch, at which time I’ll probably recommend turning automatic Click-to-Run updating back on.
Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com).
Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners.
Your email subscription:
- Subscription help: customersupport@askwoody.com
Copyright © 2025 AskWoody LLC, All rights reserved.

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Windows Update orchestration platform to update all software
by
Alex5723
4 hours, 28 minutes ago -
May preview updates
by
Susan Bradley
27 minutes ago -
Microsoft releases KB5061977 Windows 11 24H2, Server 2025 emergency out of band
by
Alex5723
6 hours, 14 minutes ago -
Just got this pop-up page while browsing
by
Alex5723
4 hours, 9 minutes ago -
KB5058379 / KB 5061768 Failures
by
crown
1 hour, 5 minutes ago -
Windows 10 23H2 Good to Update to ?
by
jkitc
16 minutes ago -
At last – installation of 24H2
by
Botswana12
20 hours ago -
MS-DEFCON 4: As good as it gets
by
Susan Bradley
52 minutes ago -
RyTuneX optimize Windows 10/11 tool
by
Alex5723
1 day, 8 hours ago -
Can I just update from Win11 22H2 to 23H2?
by
Dave Easley
1 day, 1 hour ago -
Limited account permission error related to Windows Update
by
gtd12345
1 day, 21 hours ago -
Another test post
by
gtd12345
1 day, 21 hours ago -
Connect to someone else computer
by
wadeer
1 day, 16 hours ago -
Limit on User names?
by
CWBillow
1 day, 19 hours ago -
Choose the right apps for traveling
by
Peter Deegan
1 day, 9 hours ago -
BitLocker rears its head
by
Susan Bradley
17 hours, 13 minutes ago -
Who are you? (2025 edition)
by
Will Fastie
16 hours, 10 minutes ago -
AskWoody at the computer museum, round two
by
Will Fastie
1 day, 11 hours ago -
A smarter, simpler Firefox address bar
by
Alex5723
2 days, 8 hours ago -
Woody
by
Scott
2 days, 17 hours ago -
24H2 has suppressed my favoured spider
by
Davidhs
16 hours, 49 minutes ago -
GeForce RTX 5060 in certain motherboards could experience blank screens
by
Alex5723
3 days, 7 hours ago -
MS Office 365 Home on MAC
by
MickIver
3 days, 1 hour ago -
Google’s Veo3 video generator. Before you ask: yes, everything is AI here
by
Alex5723
3 days, 21 hours ago -
Flash Drive Eject Error for Still In Use
by
J9438
16 hours, 34 minutes ago -
Windows 11 Insider Preview build 27863 released to Canary
by
joep517
4 days, 16 hours ago -
Windows 11 Insider Preview build 26120.4161 (24H2) released to BETA
by
joep517
4 days, 16 hours ago -
AI model turns to blackmail when engineers try to take it offline
by
Cybertooth
3 days, 20 hours ago -
Migrate off MS365 to Apple Products
by
dmt_3904
3 days, 21 hours ago -
Login screen icon
by
CWBillow
3 days, 11 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.

