|
ISSUE 17.3.0 • 2020-01-20
The AskWoody PLUS Newsletter
In this issue WINDOWS 7: Closing the book on Windows 7 BEST OF THE LOUNGE: Tools of the trade — PC edition LANGALIST: Win10’s default lock screen is a wasted opportunity PATCH WATCH: 2020 patching starts with a bang! WOODY’S WINDOWS WATCH: Say hello to the latest and greatest Microsoft Edge Windows 7 Closing the book on Windows 7
We’ve finished the last chapter for the storied Windows 7 operating system — at least for almost all home users. With all the various notifications, can there be a Win7 user who doesn’t know that the last general patches were sent out this past Tuesday (January 14)? If so, it’s time to come out from under your rock. On the other hand, Microsoft has given businesses a bit more time for upgrading to a current version of Windows — or some other fully supported OS of their choice. As we’ve reported in several articles, such as “Hunting for an elusive Win7 ESU license” (2019-12-23 AskWoody Plus newsletter), businesses of any size can purchase Win7 Extended Security Updates licenses — for up to three years. Each ESU is good for one year, and each succeeding year’s license has a higher fee. Unfortunately, Microsoft did not make acquiring just one or two ESU licenses especially easy for small businesses. So as a service to all AskWoody small-business readers, we’ve posted an application form. Simply enter your contact information, and you should hear from Amy Babinchak’s Harbor Computer Services. (Note: The cost will be slightly higher than the first year’s base U.S. $61 ESU license fee. Harbor Computer Services doesn’t make any revenue from this offer, so it must pass along an additional charge-card fee.) Again, the licenses need to be renewed once a year, and the cost escalates — Microsoft really wants you off Win7 as soon as possible. That three-year deadline will sneak up on you sooner than you think. So start planning immediately for a new platform. (And keep in mind that we have only three more years of support for Win8.1 and Server 2012 R2.) Keeping Win7 users in the EoL loop
As you can imagine, the end of support for Windows 7 is a hot topic on the AskWoody forums. I’ve started an online FAQ. Here are some of the more-frequently asked questions — and my short answers:
Here’s a series of questions from an AskWoody Plus member — along with my answers. They cover a lot of Win7 EoL territory. (Our reader graciously let me re-post the Q&As here. They are edited for clarity.)
[Susan’s reply] I understand perfectly. I have one Windows 7 machine that I’m keeping in the platform mix at my office.
At a minimum, you must install the October Win7 monthly rollup (not just the security patch). But you can also opt for either the November or December rollups. Microsoft released a new servicing-stack update for January, but — following our usual practice — I’d defer all of this month’s patches. For now, concentrate on last year’s fixes. (If you want to live a bit dangerously, you can, of course, install the January updates — you’ll then be able to install extended-security patches just fine. Given that you historically installed security-only updates — including November’s — you won’t see rollups offered. So when running your next manual update using files from the Microsoft Update Catalog, be sure to pick the rollup and not the security-only patch. Again, you can install any monthly rollup from October (KB 4519976) on.
I would install the November servicing-stack update (KB 4523206) first and then install whatever rollup is offered. Again, Microsoft has released January’s servicing-stack update (KB 4536952), but I recommend deferring it for a while. Bottom line: You can install any servicing-stack update released after September.
To be rid of the nag, you can use the registry-key trick (more info) — or merely click a button to hide the nag when it first appears. That said, if your computers are in a domain, you won’t see this most recent upgrade warning.
Yes, the form was produced by Amy and Ted. And no, you don’t need any sort of Office 365 account. But acquiring an ESU from another source might involve adding Office 365. I see no reason why an Office 365 account should be needed for an ESU. It’s just Microsoft red tape. I’m assuming that because the Office 365 team is small/medium business–focused, they shouldered the burden of sponsoring extended support. This is the first time that small businesses have been able to participate in ESUs — previously, the service was limited to Enterprises. So regardless of any hurdles you might have to cross, this is a big win for all small firms.
Yes, that Harbor Computer services form is where we recommend small-business AskWoody readers go to purchase the ESU product keys. Note that the activation key is the same for all of us — only the product key is different for each customer. Furthermore, that product key will be the same for your two computers.
You can buy licenses at any time. However, to stay secure, it would be best to have them in place before February’s Patch Tuesday. But you don’t have to purchase an ESU before adding the preparation updates discussed above. Putting it all together
We went on to summarize the process:
When you are fully updated through December, and you have the product keys Amy or Ted emailed to you, do the following steps:
If you have any issues with the process, please visit us on the AskWoody forum. We’ll be there to help.
In real life, Susan Bradley is a Microsoft Security MVP and IT wrangler at a California accounting firm, where she manages a fleet of servers, virtual machines, workstations, iPhones, and other digital devices. She also does forensic investigations of computer systems for the firm. Best of the Lounge Tools of the trade — PC edition
Are you handy with small tools? Do you have some knowledge of PC guts and a propensity to DIY when it comes to repairing your machine? In a PC hardware post, MVP MrJimPhelps tells us what’s in his DIY pro-level tool box, complete with mirrors, magnifying glasses, and other essentials. And find out what other tools forum members suggest that will help with any computer-repair task — even if you’re not a technician. Windows 10 Plus member richw42’s computer is behaving restlessly. The Win10 1903 machine now refuses to go to sleep — it won’t even shut down gracefully. Puzzled, richw42 turned to other AskWoody Loungers for an explanation and a cure. The answer is still in the wind. Windows 7 After years of use, Plus member cellsee6’s HP 470 G3 laptop started blue-screening for no apparent reason. The WhoCrashed report points to a hardware malfunction, and cellsee6 heads to the forum for help with deciphering the memory dump. Fellow members suggest instead that checking disk-drive health is a good place to start. Linux New year, new problem for Plus member Slowpoke47. For some reason, Linux-based Firefox started rendering text like a really bad print job. Loungers walk Slowpoke47 through various possible causes and different solutions. Windows 1909 MVP MrJimPhelps remotely upgraded two computers to Windows 1909. One upgrade was flawless, the other not so much — the video was severely distorted. Read along as MrJimPhelps takes us through a guided troubleshooting tour. Windows 10 Plus member CorKam revisits an often-asked question: How to transfer software and data from an old Win7 portable to a new Win10 machine. Using transfer software is tempting, but simply reinstalling applications might be the better path. Windows10 Plus member berniec had a problem diagnosing a driver issue that prevented Wi-Fi from restarting after the laptop emerged from hibernation. Tired of running Windows’ built-in troubleshooter, berniec turned to forum members for a better solution. PowerShell, anyone? If you’re not already a Lounge member, use the quick registration form to sign up for free. LANGALIST Win10’s default lock screen is a wasted opportunity
By Fred Langa The default Win10 lock screen is awful — a cluttered mess of ads, random impersonal images, and vanilla system information. But all three of those elements are easily customized; you can make the lock screen truly your own, with the information you need, the images you want — and with no ads! Easy ways to make the Win10 lock screen more useful
Reader Brandon Na asked:
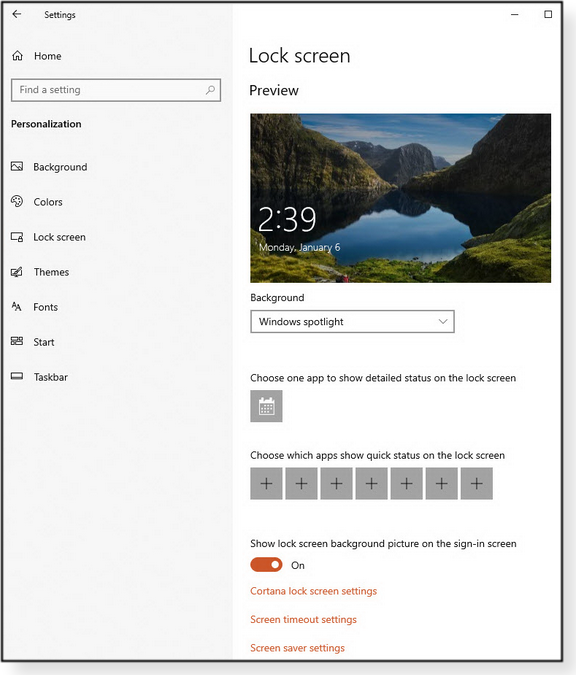
I like the concept of a pleasant-looking lock screen, but the default Win10 implementation is simply too generic. The lock screen is, of course, the combination of image and information displayed by Windows after startup but before you sign in. It also shows up anytime the PC has been “software-locked” (automatically or when you press Winkey + L). In many older Win10 setups, the default lock screen is basically just a glorified clock with a never-changing image of a seaside cave (Figure 1).
In truth, the default generic layout of the Win10 lock screen is intended to be a placeholder: a fairly attractive screen that would eventually be “personalized” (in Microsoft-speak) by users. Unfortunately, few users know of or utilize the many available lock-screen customizations. The result is that millions of PCs — maybe yours! — show the same boring and almost-useless lock screen forever. To me, it seems counterproductive to have potentially useful system information displayed on a screen that’s so static and dull, no one really pays attention to it anymore. I suspect that’s one of the reasons why newer versions of Win10 usually default to a series of randomized images generated by the “Windows Spotlight” service. These images are overlaid with some basic system information and icons — which I find perfectly fine. But you also get several floating text links for what Microsoft calls “fun facts, tips, and more.” I call them ads. Figure 2 shows a typical default lock screen on newer versions of Win10. I’ve superimposed yellow numbers and arrows to highlight the three separate elements of this type of screen: (1) a random, Microsoft-selected background image; (2) several ad links; and (3) system icons and information.
The Windows Spotlight stock images vary widely in quality. Some are acceptable (the one shown above isn’t bad), but many are, to my eyes, just awful — with garish, oversaturated colors and far-from-realistic dynamic ranges. (My guess is that many of these images were originally meant to be printed — thus the over-processed colors — rather than to be displayed on a bright screen.) My reaction is more often “ugh” than “wow.” But even if the images were fabulous, shouldn’t your lock screen show something you’d prefer to see, day in and day out? As for the ads (masquerading as “interesting tidbits”), does anyone besides Microsoft like them? To me, they add visual clutter and distraction while failing to provide an offsetting benefit. I can’t think of a single time when I found the links useful — not once, ever! The lock screen’s standard system-information text and icons are generic, minimal, and generally inoffensive. But did you know that the screen can display much more information? That includes detailed status data for one app (from a list Windows provides) plus quick-view (iconized) info for seven more (from among 11 choices). And all those lock-screen elements — background image, ad links, and system information/icons — are completely user-controllable. On my personal-use PC, I’ve turned off the ads and substituted the stock images with my own family photos. I’ve also explored the alternative system-information options to see whether the defaults are best for me — which, in fact, they are. Figure 3 shows the result. Compare that lock screen to those in Figure 1 or 2. I know which one I’d rather look at every day!
Changing lock-screen elements is easy. Here’s how:
The exact mix of lock-screen customizations available to you depends on your PC’s software setup. But every system should support at least the major elements. You’ll find everything you need on a single settings page. To get there, click Settings/Personalization/Lock screen — or type lock screen into the Windows search box and select “Lock screen settings” when it’s offered. The settings page will look similar to Figure 4.
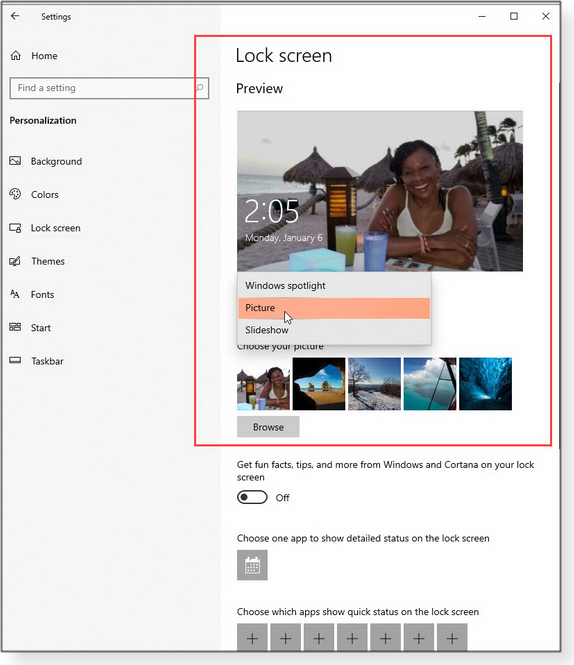
To change lock-screen background image: Click the box below Background (just below the thumbnail of the current image) to open a drop-down list of options. Select Picture if you want to show your choice of a single, static image (see Figure 5). Select Slideshow to display a series of images. Or choose Windows spotlight if you want to let Microsoft stay in control.
If you choose Picture or Slideshow, you next select the image or images of your choice. For Picture, click Browse and navigate to the image’s location; for Slideshow, click one of the listed folders — or choose Add a folder and click though to a folder of photos. Also click the “Advanced slideshow settings” link to enable/disable other options. Locations on the C: drive work best because it’s always available to Windows, even before you’re signed in. (Lock-screen photos on networks and some other locations might not become available until after you sign in.) Kill the lock screen’s ad links: If you have the background set to “Windows spotlight,” you get the ad links whether you like them or not. On the other hand, if you picked “Picture” or “Slideshow,” you’ll see a switch labeled Get fun facts, tips, and more from Windows and Cortana on your lock screen (see Figure 6). Click the toggle to turn this “feature” off.
Control lock-screen system information/icons: Your PC’s customization options live just below the Background settings. For the “detailed information” option, click the icon below Choose one app to show detailed status on the lock screen. (See Figure 7.) Pick the app of your choice from the displayed list. The Calendar/clock is the default, but you can change to whatever alternate choices your setup offers. (Typically, this includes apps such as 3D Viewer, Messaging, Mail, Xbox Console Companion, Weather, and some third-party apps such as Dell’s SupportAssist.) You can also select None. Next, under Choose which apps show quick status on the lock screen, select up to seven additional “quick status” icons from the available choices. These typically include 3D Viewer, Messaging, Mail, Xbox Companion, Weather, Clock/Alarms, Skype, the Microsoft Store, Microsoft Content, and possibly others — plus, again, None.
Don’t waste your lock screen!
With lock-screen personalization changes this easy to make, why stick with the boring, cluttered, and (sometimes) ugly default options? Make your lock screen uniquely your own — with attractive images and just the system info that’s most useful to you. And no ads!
Fred Langa has been writing about tech — and, specifically, about personal computing — for as long as there have been PCs. And he is one of the founding members of the original Windows Secrets newsletter. Check out Langa.com for all Fred’s current projects. PATCH WATCH 2020 patching starts with a bang!
Patch Tuesday arrived on January 14, and it was not an auspicious start to the new year. An NSA warning about a newly revealed Windows vulnerability isn’t the only newsworthy event for January. Let’s recap: As we’ve discussed thoroughly on askwoody.com, millions of Windows users are saying goodbye (sort of) to the beloved Windows 7. For consumers, January’s updates are the last they’ll receive — barring some extraordinary event. Businesses still relying on Win7 machines (and there are possibly millions) get a three-year reprieve — if they take advantage of Microsoft’s Win7 Extended Security Updates (ESU) offering. (Remember, you can buy an ESU, a year at a time, by filling out our application form, as noted in the 2019-12-23 article “Hunting for an elusive Win7 ESU license.”) Those future Win7 security updates are crucial for businesses. To underscore that point, the National Cyber Security Centre (part of the U.K. Government Communications Headquarters intelligence agency) put out a warning to not use Windows 7 for online banking — unless you continue to receive security fixes after January 14. I know of too many people who say they’re comfortable with running this obsolete OS without updates. I’m not one of them. So consider exactly where and how you plan to use your no-longer-secure copy of Win7. Don’t use it for online banking, for filing your taxes, for managing medical accounts, or on any other site that involves sensitive personal information. The phishers and scammers are extremely adept, and an unpatched Win7 system is, as they say, low-hanging fruit. On the browser front, Chromium-based Edge is now out (more info). I rarely install beta products on production machines, but I made an exception this time. It’s running just fine, and it’s probably more secure than the original Edge. Better yet, it works on Windows 7 and macOS. According to a Microsoft Windows Blogs post, the company will slowly roll out the new version over several months — in other words, it’ll eventually show up in Windows Update. Not surprisingly, the initial release is not without hiccups: there are reports that the update is set to a language different from the local system’s default. Rules for patching
For this Patch Watch, I’ve broken down patching guidance into two sections: one for Windows consumers (effectively anyone not connected to a domain) and the other for small-business PC admins. Personal Windows users: Managing January patching works just as in any other month. Defer all updates for at least a couple of weeks, unless we say otherwise. I’ve not heard of nor seen any major issues with January’s fixes, but we’re still freshly past Patch Tuesday. Bad things could still pop up. And as I’ve mentioned numerous times, Win10 Pro gives you more control over when updates are installed than will the Home edition. Also, Woody now recommends that Win10 1809 users move up to Version 1903. (If you’re still on Version 1803, you’re pushing your luck.) Administrators: January is somewhat complicated. If you manage Windows Server platforms — or you’re more paranoid than most — I’m going to bend the standard patching rules and strongly suggest that some of you install January updates relatively soon. Why? It starts with the recently disclosed Windows vulnerability you’ve no doubt read about. Ironically, on January’s Patch Tuesday, the U.S. National Security Agency (aka the NSA) posted an advisory about a “critical” flaw in Windows: crypt32.dll (or, officially, CVE-2020-0601). I don’t see this vulnerability as a serious threat to individuals, small businesses, and other smaller organizations. By my reading and interpretation of the NSA advisory, the organization found it while either trying to get into someone else’s computer or investigating how the bad guys got into government systems. The vulnerability must not have been all that useful to the NSA, because it passed on information about the flaw to Microsoft. Moreover, any related exploits would most likely target infrastructure, governmental institutions, and all sorts of other large and scary entry points. The good news? Even without patching, Microsoft and other antivirus vendors are putting protections in place to thwart bad actors. The vulnerability is connected to certificate validation in Win10, Server 2016, and Windows Server 2019. Attackers exploit the vulnerability by crafting certificates that appear to have been legitimately signed. Here’s how the bad guys might use the vulnerability. It’s a bit scary to read.
Fortunately, the following Windows components are not impacted because they rely on a different certificate process:
Moreover, Windows Defender will sense when a maliciously signed certificate is being used, which is good news for Win10 users who use the default anti-malware system. However, the fact that the threat seems limited to Windows 10, Server 2016, and Server 2019 proves once again that newer isn’t always better. So … if you just happen to be in charge of, say, a nuclear power plant, and you’re running the aforementioned Windows versions, you might want to add January’s updates sooner rather than later. As for the rest of us? We can kick back and wait to hear that the updates are sound. A more worrisome threat? In truth, I’m more concerned about two other recently revealed vulnerabilities — CVE-2020-0609 and CVE-2020-0610 — that center on Remote Desktop (used on the client side) and Remote Desktop Gateway, which many large and small businesses use to allow remote staff access to company systems. Of the two, the latter is the more troubling. On Remote Desktop Gateways, the vulnerabilities show up as a pre-authorization flaw — meaning the attacker doesn’t have to authenticate to servers that have RDgateway installed. (This feature isn’t installed by default.) However, if you happen to be running Small Business Server Essentials 2012 or 2016, you’re vulnerable to this potentially wormable bug. I was so concerned about this potential threat to my Windows Server installations, I applied the January updates the same day they were released. The good news is that Microsoft has since updated its security advisory with more specifics: an attacker would have to come in through a typically unexposed port (UDP 3391). So the threat is probably not as bad as I thought. For those of you still running Small Business Server 2011, 2008, or even 2003, be comforted that none of those platforms is vulnerable to this bug. That said, all three of those platforms are no longer supported, so you’ll need to migrate to the formerly vulnerable systems soon. Bottom line: If you have RDgateway installed, you’ll probably want to fast-track the January patches. Another bug that gave me pause, but not sleepless nights, impacts Remote Desktop. CVE-2020-0611 is not a great threat unless you have a habit of connecting to the office from often-unsecure locations such as coffee-house hotspots and hotel Wi-Fi. This threat has almost no impact on home systems. A successful attack would require tricking a user into connecting to a malicious site via social engineering, DNS poisoning, or man-in-the-middle techniques. But those who travel and use Remote Desktop are vulnerable. So you might immediately approve January’s patches for them. Patching summary
Again, we are less than a week past January’s Patch Tuesday. Things are looking good so far, but we want to remain cautious. The exception is, as discussed above, Windows Server updates.
Windows 10
Reminder: We recommend that most Win10 users now have Version 1903 installed. If you’d prefer to bump up to Win10 1809, see PKCano’s post. Servicing-stack updates
Cumulative updates
.NET Framework This month’s .NET updates include security patches for several vulnerabilities — so they’re important. Note that Win10 1809 has three updates listed. But you should see only one to be installed. (Typical .NET confusion!)
Windows 8.1/Server 2012 R2
If you’re running Win7 and not interested in Win10, consider upgrading to Windows 8.1. It still has the monthly rollup or security-only cadence that Windows 7 had. (Future Win7 ESUs will be security-only.) Windows 7/Server 2008 R2 SP1
Remember: These updates include a time-to-update nag message. Block it with registry-key changes or check the “Don’t remind me …” box. Windows Server 2012
These updates still have the Cluster Shared Volume flaw. Windows Server 2008 SP2
Office security and non-security updates
January’s security updates fix a remote-code-execution vulnerability. Office 2016 Office 2013 SP1 Office 2010 SP2 The following Office non-security enhancements and fixes were released January 7, 2020. Office 2016
Office 2013 and 2010 There are no new non-security updates for Office 2013 and Office 2010. Refresher: Patch Watch rules for updating
It’s a new month of patching. Once again, here are our current recommendations for patching Windows and Office. They may change as Microsoft evolves its updating process.
Stay safe out there.
In real life, Susan Bradley is a Microsoft Security MVP and IT wrangler at a California accounting firm, where she manages a fleet of servers, virtual machines, workstations, iPhones, and other digital devices. She also does forensic investigations of computer systems for the firm. WOODY’S WINDOWS WATCH Say hello to the latest and greatest Microsoft Edge
By Woody Leonhard Will Microsoft’s last-ditch effort to reinstate its Internet-browser hegemony succeed? There’s plenty to like about the new Chromium-based Edge — but plenty of shortcomings, too. Almost as soon as Microsoft won the Internet-browser race in the 2000s, its hold on that hard-fought market began to erode. By May 2007, Firefox was running on roughly a quarter of all Windows PCs. In 2009, Google’s Chrome burst onto the scene in a big way — and for Microsoft, it’s been all downhill ever since. So in 2015, Microsoft tried to replace the old and vulnerability-ridden Internet Explorer with the shiny new Edge. Over the past four years, the new browser has gone exactly … nowhere. Edge shipped as the default browser with every version of Windows 10 — an advantage once considered antitrust-worthy. For many new Win10 users, it was known mostly as the best way to download Firefox or Chrome, a bit of notoriety it holds to this day. I’ve never used Edge consistently; I do play with it from time to time to see what’s new (typically, not much). I’m just not willing to run another snooping Microsoft product. If you use a browser other than Edge (and there’s over a 95 percent chance you do), you probably feel the same way. Many factors contributed to the demise of Edge as we currently know it: incompatibility, sluggishness, a paucity of add-ons, and the ABM (anything but …) movement. With that situation unlikely to improve, Microsoft decided to take a different tack. Starting around a year ago, it gave Edge a radical rendectomy — which is to say, MS tore out the old, proprietary rendering engine that powered the beast and replaced it with Chromium, the open-source code that’s the foundation for Google Chrome. Last week, Microsoft formally released the new Chromium-based version of Edge, making it available for Windows 7, 8.1, 10, and related versions of Windows Server. There are even editions of the new Edge for Android, Apple iOS, and macOS. You can download and install it manually — if you’re feeling lucky — or you can just wait; it’ll show up on your PC sooner or later. Normally, the new Edge will simply install itself on top of the old Edge and display its fabulous and unmistakable icon, shown in Figure 1. (The classic “e” icons of Internet Explorer and old Edge are annoyingly similar.)
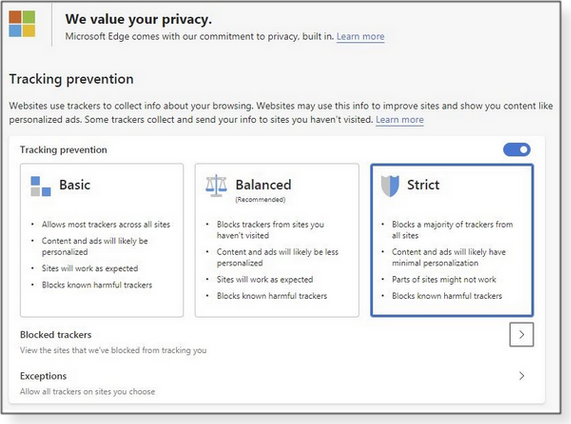
To run both old and new Edge simultaneously, you must make some changes to the Windows registry or Group Policy (MS info). What shall we call this rebuilt beast? Microsoft fluctuates between calling it the “new Microsoft Edge,” “Chromium-based Edge,” “Edge Chromium,” and “that browser with the cool blue swirl icon.” ZDNet’s Mary Jo Foley started calling it Chredge — which suits me just fine! And what label do we slap onto the original Edge? Microsoft has started calling it “Legacy Edge” or “Edge Legacy.” I think I’ll call it “Better Off Forgotten.” Putting aside the “Collections” feature (see Martin Brinkmann’s explainer) — which I figure I’ll use exactly … never — the item that struck me as worthwhile is something called “Tracking prevention” (see Figure 2).
The intent of this feature seems pretty clear: you can tell Chredge that you want to allow all, some, or no tracking cookies. The documentation has more explicit details, but you can reasonably expect that “Strict” will work as well as some third-party ad blockers. You can also expect that Google’s Chrome, in particular, will try to match the appearance of the feature — if not the intent. If you decide to give Chredge a whirl, try Tracking prevention on some of your favorite webpages. One well-known computer site that shall remain nameless runs almost a hundred trackers — on just the first page. AskWoody.com, I’m happy to report, has just two trackers: one for “Automattic” (the WordPress site that dishes up avatar pictures on users’ posts) and one for Google (necessary for CAPTCHAs, unfortunately). You’ll be hearing a lot more about Chredge. If nothing else, Microsoft fanbois will finally have a browser to talk about without being ridiculed. Give it a shot if you feel so inclined, and let us know how it goes on askWoody.com.
Eponymous factotum Woody Leonhard writes lots of books about Windows and Office, creates the Woody on Windows columns for Computerworld, and raises copious red flags in sporadic AskWoody Plus Alerts. Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com). Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners. Your email subscription:
Copyright © 2020 AskWoody LLC, All rights reserved. |


 By Susan Bradley
By Susan Bradley






 What to do: Windows consumers should stick to the usual plan and defer this month’s updates until further notice. Admins might want to test the patches and then apply them as soon as they’re ready to.
What to do: Windows consumers should stick to the usual plan and defer this month’s updates until further notice. Admins might want to test the patches and then apply them as soon as they’re ready to.