
|
Patch reliability is unclear. Unless you have an immediate, pressing need to install a specific patch, don't do it. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
Activate Windows’ hidden, master admin account
In this issue
- TOP STORY: Activate Windows' hidden, master admin account
- LANGALIST PLUS: Virtual PC install kills host PC's networking
- PATCH WATCH: Duplicate patches add to the usual update confusion
- LOUNGE LIFE: Cookies can do more than make you fat
- FIELD NOTES: Insights and interesting news on computing
- WACKY WEB WEEK: Peculiar forces converge in Portland, Oregon
Activate Windows' hidden, master admin account
Windows’ user rights can be confusing and frustrating. Whether signed in with an administrator-level user account or evoking the Run as administrator setting, you can still run into insufficient-rights warnings.
But Windows’ built-in, separate Administrator account gives you unfettered access to virtually all parts of your system setup — once you know how to access it.
Many Windows users don’t know this account exists, primarily because it’s usually hidden and inactive by default. Here’s how to enable the “master” administrator account — and use it to streamline heavy-duty system repairs, problem-solving, and maintenance tasks in Win8, Win7, and Vista.
One master account to rule them all
Most operating systems have some sort of special-purpose master account: one that lets you control the OS with virtually no restrictions. This type of account has various names: “superuser,” “root,” “supervisor,” and so forth. Windows calls it Administrator.
Windows’ master account doesn’t simply enhance a standard admin-level user account or serve as an elevated version of the Run as administrator option. Administrator operates much like a normal user account, except it has virtually unlimited permissions.
Once activated, Administrator (or Admin for short) is a separate account, complete with its own private desktop and user files. You can set it up with its own themes, background, and other customizations, and you can install software that’s not shared with non-admin-level users.
The unfettered, full-permission access offered by the Administrator account is ideal when you need access to the deepest parts of Windows — for example, when you’re trying to resolve really thorny system problems. But clearly, that level of control can also be dangerous. There’s no safety net, so a misstep could royally screw up your system.
That’s why Microsoft hides the Admin account by default. It’s not intended for full-time, routine use — the risks are simply too great — but it’s there for knowledgeable users to employ when needed.
A review of Windows’ admin-level access options
As noted, Windows offers three ways to access admin-level permissions and functions. They are, from simplest to most powerful:
- Run as administrator: This option is typically used to temporarily access limited admin-level rights from within a non-admin-level (standard) account. In some cases, tasks that require administrator-level permissions can be run by simply right-clicking the name of an app or function and selecting the “Run as administrator” option.
The process has a couple of speed bumps: a user account control (UAC) prompt must be acknowledged, and you must also enter an admin-level password. This two-step process can cause problems with complex and multi-step admin-level tasks. Also, depending on the account type (standard, guest, or child), some admin-level tasks are simply off-limits.
- Assign a user account as an administrator: Admin-level user accounts are subject to UAC controls. A warning will pop up whenever a potentially dangerous system change is about to start — for example, when installing new software or making system-level changes that might affect other users. The task won’t proceed until the user explicitly grants permission via a UAC prompt.
This one-step speed bump lets most admin-level tasks run to completion. However, some complex, multi-step tasks might fail. This can happen when a task requires several admin-level tools working in series or uses command lines or scripts. The process could stop because only the first tool or task received the necessary permissions.
- Sign in as Administrator: The master Admin account — the focus of this article — has full permissions and operates with virtually no restrictions. It has none of the restrictions or drawbacks of the first two administrator-access methods.
When you’re in the Admin account, you’ll likely never see a UAC prompt — any system-level task you initiate is carried out immediately. Not only is this UAC-free operation convenient, it will also let you complete complex tasks that would otherwise fail. Within an Admin account, you can sequentially run multiple tools and tasks without the problem of repeatedly confirming elevated privileges.
In practice, I’ve found that the Admin account gives the best shot at overcoming otherwise unsolvable Windows-permissions issues. Many tasks that can’t be completed via an admin-level user account or the run-as-administrator option will generally work in the Admin account.
How to reveal and activate the Admin account
There are various ways to enable the Administrator account, but two are probably the simplest: an easy point-and-click process and a quick command-line entry.
(All the following instructions assume you’re starting from an admin-level user account.)
Point and click
This method uses the Local Users and Groups feature (or plugin) in Windows’ Microsoft Management Console (MMC). It’s available on all but the most limited editions of Windows, such as Windows Basic and Windows Home.
Here’s how to enable the Admin account via the MMC:
- Win8: From the desktop, right-click the Start icon, click Run, and then enter lusrmgr.msc (or open the Search charm and enter lusrmgr.msc there).
- Win7/Vista: Click Start, enter lusrmgr.msc into the run or search boxes, and then press Enter.
- In all three versions of Windows, if a UAC prompt appears, click Yes to accept the warning.
- With the Management Console open, click Users in the left pane.
- In the center pane, right-click Administrator and then select Properties. The Administrator Properties dialog box will appear.
- In Administrator Properties, under the General tab, clear (uncheck) the Account is disabled box (Figure 1).

Figure 1. Account is disabled checkbox reveals and enables the master administrator account.
- Click OK and close the MMC.
Command line
This method works in every version and edition of Windows that I tried it on — all the way back to Vista Basic!
- Open an administrator-level (aka elevated privilege) command prompt. In Win8, type Windows key + X and select Command Prompt (Admin). For older Windows versions, enter command prompt into the start menu search box. When it appears in the search results, right-click it and select Run as administrator. (For more on the command prompt, see the MS how-tos for Win8, Win7, and Vista.)
- Type or copy/paste the following command (also shown in Figure 2), which reveals and enables the Administrator account.
net user administrator /active:yes

Figure 2. Activating the Administrator account in an admin-level command window
- Press Enter and then close the command Window.
Accessing the Administrator account
Once you’ve enabled the Administrator account via either of the preceding methods, reboot your system, sign out of your currently open account (or select Windows’ Switch user option) — the Admin-account icon should now appear on your sign-in screen. (For more info, see the MS FAQ item, “How can I switch to a different user account?” for Win8, Win7, and Vista.)
Figure 3 shows the Administrator account added to a Win7 sign-in screen. Win8 and Vista look somewhat different, of course, but work the same way. To access Administrator, you simply click its icon, just as you would any admin- or standard-user account.
Figure 3. Once activated, the master Administrator account appears as a normal sign-in option (Win7 shown).
The first time you access the new Admin account, Windows will take some time to set it up. Again, Administrator has its own desktop, user files, and settings, so Windows needs to create a new user folder (C:\Users\Administrator) with the standard subfolders: Contacts, Desktop, Documents, Downloads, and so forth. Fortunately, the setup is a one-time event; once completed, accessing the Administrator’s account will take no more time than accessing any other account.
Important: When the Administrator account is first set up, there’s no password for it. But this fully privileged account is, obviously, too dangerous to leave unguarded. So once Windows completes the setup process and you have full access, your first task should be to establish a really secure password.
You can use the normal method: click Control Panel/User Accounts/User Accounts and use the appropriate prompts/links that let you add or change a password. You can also change the sign-in picture and so on.
Checking whether the Administrator account works
It’s easy to verify that your new Admin account is fully privileged. Simply put, with a properly working Admin account, you should almost never see a UAC warning.
To test this, simply begin any task that would normally trigger a UAC prompt. For example, the full Management Console normally requires a UAC confirmation to launch from a typical user account. But once you’re in Administrator, simply entering mmc into the Windows search or run box will take you straight to the Management Console — with no intervening UAC speed bump.
Similarly, any command window you open within Administrator automatically includes admin-level rights — no further steps are needed to elevate the command windows’ privileges.
You’re now free to perform virtually any system-level task, with no worries about having the right permission levels and without UAC interference.
Remember: When you’re running as Administrator, you’re working without a figurative safety net — there’ll be no warnings to remind you that you’re about to undertake potentially dangerous actions. So before making any significant system changes with the Admin account, carefully think through any actions you’re about to perform — and always, always, always make sure you have full, current, working backups. (Please don’t send me an email stating that you tried Administrator, severely damaged your system, and have no backup to restore!)
When you’re finished with a task that required the use of the Admin account, sign off (or reboot) and then sign back in to your normal user account. (Another reminder: Many, if not most, standalone Windows users run continuously on an admin-level user account, which can make it easier for malware to take full control of the system. It’s safer to use a standard user account for your day-to-day computing activities.)
How to put Administrator back in the closet
Again, for security’s sake, you should use the Admin account only when you really need it. When you disable and hide the account, its icon will no longer appear on the sign-in screen. Think of it as removing temptation.
Fortunately, the steps for putting Administrator away are nearly identical to those you use to enable it. There are, again, two simple methods; perform either from your regular user account.
Point-and-click: Follow the same steps described above to access the Administrator properties via the MMC. But now, simply tick the Account is disabled box (Figure 4); then click OK and exit the console.
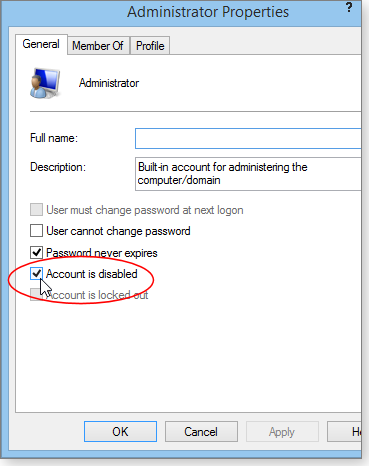
Figure 4. One click quickly disables and hides the Administrator account.
Command-line: Open an admin-level command prompt and then type or copy/paste the following command (shown in Figure 5).
net user administrator /active:no
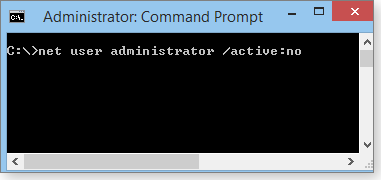
Figure 5. Disabling the master Administrator account via a command-line window
Press Enter and close the command window.
Whichever method you use, it’s really just that simple!
Automate the enable/disable-Admin process
If you think you might need to pop in and out of Administrator regularly, you can save yourself some time by automating the command-line method.
In your normal user account, type or copy/paste the enabling command (net user administrator /active:yes) into Notepad. Click File/Save As and navigate to the location where you want to keep the file. In the Save as type drop-down menu, select the All Files option. Give the file an obvious name and assign it a .bat extension instead of .txt. For example, you might call the enabling file EnableAdminAcct.bat (see Figure 6).
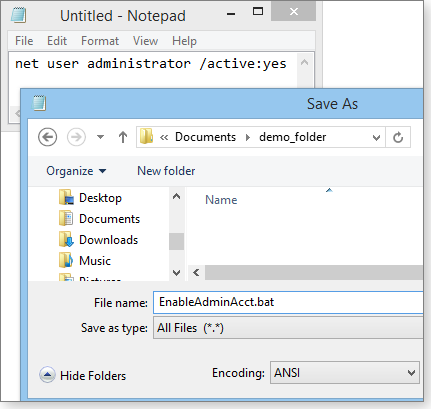
Figure 6. Creating command files makes it easy to enable/disable the Administrator account.
Now click New in Notepad and do the same thing for the matching disabling command (net user administrator /active:no). Once again, click File/Save As, select All Files, give this file an equally obvious name, and assign it a .bat extension (for example, DisableAdminAcct.bat).
When you want to enable or disable the Administrator account, right-click on the appropriate .bat file and select Run as administrator. Accept any UAC warnings that appear; a command window will flash on the screen as the command executes — and then vanish.
You can then reboot, sign off, or use the Switch user command: the Admin account’s icon will be either present or absent on the sign-in screen — depending on whether you ran the enable or disable command.
Ultimate power requires ultimate caution
Once again, the Administrator account is hidden by default for a very good reason: it can be dangerous if misused. In fact, an MS TechNet page suggests that Administrator is aimed at IT-level activities such as operating-system deployment and software auditing.
But with care, caution, and good backups, the master admin-level account can be used for complex repair and maintenance tasks as well as to resolve stubborn permissions problems that “Run as administrator” or an admin-level user account simply can’t handle.
Virtual PC install kills host PC's networking
When any sort of software activity torpedoes networking connections, it’s usually easy to restore normal operations. Here’s how.
Plus: Questioning whether cloud-storage services are completely reliable, and possible IP-address hijacking gets a reader into legal trouble.
VirtualBox install takes host PC offline
Reader Rene Lopez de Arenosa Jr. tried testing Win10 on a virtual machine, but the setup caused a serious networking failure on the main system.
Fortunately, the fix is quick and easy; it’s also applicable to other, similar networking glitches.
- “I read your article, “How to safely test-drive Win10 — step by step” [Oct. 16, 2014, Top Story].
“When I installed VirtualBox 4.3.26 to load Windows 10 Technical Preview, I lost all network access — Internet, printer, and so forth. I couldn’t find a way to contact Oracle about the problem. Any suggestions?”
Rene, I’m very surprised you had a networking failure. I’ve been using VirtualBox for years, and I’ve never run into that problem.
In any case, I’m sure I can get you back online in minutes.
Here’s what probably went wrong. During setup, VirtualBox ties its network subsystem to your PC’s main networking components. Technically, VB is creating a semi-isolated subnetwork (info) that your virtual PCs will use to go online. VirtualBox also sets up a network address translator (NAT; info) to help keep the VPCs’ online activities safely separate from your main (host) PC’s.
When VirtualBox first sets up its subnet, it briefly shuts down networking on the host system. That’s why you typically see a warning similar to that shown in Figure 1.
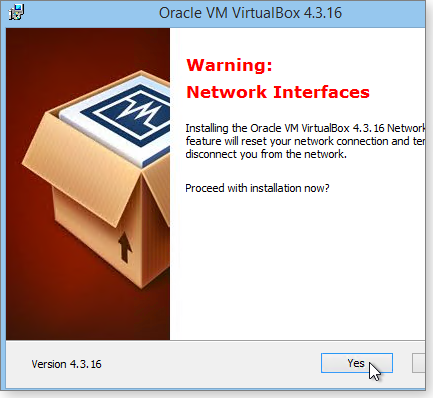
Figure 1: During a normal VirtualBox installation, the application momentarily disables the host PC's networking system.
This is almost surely where your PC encountered trouble — the host PC’s network interfaces shut down and now won’t restart. Somehow, the system’s network settings became scrambled and need to be reset.
The fix should be easy, using the following steps:
- Step 1. Exit or suspend any software that uses the network.
- Step 2. Launch Windows’ Device Manager by opening the Control Panel and typing device manager into its search box, then click the Device Manager icon when it appears.
- Step 3. Expand Device Manager’s console tree to show all network adapters in your system. Right-click the first adapter and select the Uninstall option, as shown in Figure 2. Don’t worry; this process is harmless and will temporarily disconnect the related driver software.

Figure 2. Hardware problems can sometimes be fixed by a temporary soft uninstall.
- Step 4. When the confirmation dialog appears (Figure 3), do not check the box labeled Delete the driver software for this device. In other words, leave the drivers in place as is. Click OK.

Figure 3. For a short-term, soft uninstall, leave the 'Delete the driver …' checkbox empty.
- Step 5. Repeat for all network adapters on your system. (Note: After each change, Device Manager might rescan your hardware; your monitor could blink as it’s probed — that’s normal.) When you’re done, all network adapters will be inactive — you’ll effectively have no network setup.
- Step 6. Reboot your host system or, on the Device Manager toolbar, click Action/Scan for hardware changes. (I prefer to reboot; it’s a more certain way to obtain a clean start.) Either way, Windows will “discover” the existing networking components and set up a fresh, from-scratch networking system — without whatever mangled network settings were causing the problem.
For more details, please see the item, “VirtualBox networking (and other) problems,” in the Oct. 23, 2014, LangaList Plus column.
A final word about tech support: VirtualBox’s main components are open-source and distributed for free. Oracle contributes generously to maintaining the VirtualBox application and website, but it doesn’t own the VirtualBox code and can’t be expected to offer extensive tech support.
As with most open-source products, VirtualBox support is provided mainly via online documentation (site) and the VirtualBox “community” (site), made up of forums, chats, and mailing lists.
Most VirtualBox problems can be resolved through those resources.
Is it necessary to back up cloud-stored files?
Writing from Canada, Jean-Guy Heon wonders whether he can trust his cloud-storage providers to not lose his files.
- “I find it extraordinary that we can store files on various cloud services. The ability to sync PCs, laptops, tablets, and smartphones is quite impressive to me.
“[The services] all claim to be reliable, but should a periodic [local] backup of cloud-stored files be necessary? Or are the services so reliable that we should feel safe with the data kept out there?”
Cloud-storage reliability comes down to two factors:
- Are your files present and intact on the cloud-based servers?
- Is the service connected to the Net when you need access to your files?
Generally speaking, the major cloud-storage services and Web-based email services (which also store your mail in the cloud) have very good track records when it comes to preserving user files. For example, most of the larger services store your files on redundant servers and use their own professional-quality backup and archiving methods.
But a good record isn’t the same as a perfect one. From time to time, we’ve seen stories about some cloud or email service wiping out some users’ files. These glitches are extremely rare and typically affect a relatively small number of users. But that’s small consolation if you’re one of the unlucky ones whose files were lost.
More often — but still relatively rarely — a service might go offline. Obviously, having your files safely stored on a cloud server isn’t very helpful if you can’t access them. A data center might experience a major power or network outage, an Internet trunk cable might get ripped up by a backhoe (as happened recently in Seattle), some natural or man-made disaster might damage essential infrastructure, or some other, previously undreamed-of disruption might afflict the cloud.
No cloud-storage provider can guarantee 100 percent “uptime,” and the numbers they do quote can be a bit deceiving. For example, an advertised uptime of “99 percent” sounds great — until you do the math. Given 8760 hours in a typical year, a cloud service could be down for 87.6 hours — more than two work weeks! — and still meet the 99 percent-uptime promise.
Some services claim 99.9 percent uptime; while that’s better, it’s still 8.76 hours offline a year — more than a full business day.
If these outages happen in dribs and drabs — a few seconds or minutes here and there — you might not notice them. But outages over several hours or days can obviously be troublesome.
An inability to access your cloud-based files can also originate on your end. Your local Internet connection might go down, your ISP might have an outage, and so forth. Again, the files might be safe and intact, but if you can’t get at them, what good are they? (Synching across devices adds another layer of complexity. Was a particular device connected to the Net long enough to have its local files updated as needed?)
So when you ask whether you need local backup of your cloud-stored files, I have to answer your question with two other questions:
- How important are your cloud-stored files?
- Is it critical that you have quick and reliable access to the files?
Again, there’s a remote possibility of losing some files and a somewhat less-remote possibility of service interruptions. If you can live with that, you don’t need local backups.
If not, you definitely do need complete, current, local backups of your cloud-stored data.
You can use whatever means you wish for the backups, but Win8 users have it easy — you can set up automatic cloud/local backups with just a few clicks. See “Mastering Windows 8’s backup/restore system” in the Jan. 15 Top Story.
Legal trouble from misused IP address
Barry Kirwan got an unpleasant warning from his Internet service provider.
- “My ISP has sent me a legal notice of infringement — copyrighted content was being downloaded to my PC’s IP address. But I didn’t do that!
“Around the time of the illegal downloads, I found and removed three Trojans after running a full virus scan.
“I didn’t think much of it at the time, but the notice from the ISP makes me very concerned. Is it possible for a Trojan to utilize my IP address as a cover for downloading copyrighted material?”
In a word: yes!
Your PC (or your router) is assigned an IP address when it first connects to an ISP. All data traffic sent to the Net from your system — or from other devices attached to the same router — carries the same, basic IP address.
If malware phones home from your PC, its data packets will be tagged with your IP address — just like your legitimate Internet traffic.
And the problem isn’t limited to malware. Some legitimate software also can be problematic. For example, BitTorrent software (info) and similar peer-to-peer file-sharing tools can use your PC as a way station — downloading files from distant servers as a background task, storing those files on your hard drive, and then redistributing them to other torrent users. It all happens automatically, with no direct action or involvement on your part. But again, all the data packets emanating from your PC — whether you’re aware of them or not — will carry your PC’s IP address.
Although BitTorrents (and their ilk) have legitimate uses, they’re also a popular way to distribute illegally copied material. So if you set up your PC as a peer on a torrent, illegal software or content might flow through your PC as a background activity, even if you personally never touch the stuff.
I suggest that you tell your ISP you found malware on your system — that gets your reply on the record. Then uninstall any and all file-sharing or torrent software on your system. Also, beef up your anti-malware defenses to keep your PC clean of future infections.
Bottom line: If you don’t use torrent-style peer networking, if you keep malware off your PC, and if you protect your Wi-Fi router with a strong password, then your PC, router, and IP address should be safe from unauthorized — and potentially illegal! — online activity.
Duplicate patches add to the usual update confusion
Sorting through Patch Tuesday releases is hard enough. But posting new patches in multiple security bulletins just makes the update process even harder.
Adding to the chore of keeping our systems safe, some April nonsecurity fixes are showing up again in May.
A warning about Windows Update getting stuck
As reported in a Reddit post and other sites, some systems are getting stuck at Stage 3 of 3 while processing a batch of updates. Apparently, Windows Update is having trouble coping with patches superseding other patches. At this time, the specific update or updates causing the problem isn’t known.
 What to do: Reportedly, the solution is simple: just enter the standard Ctrl + Alt + Del.
What to do: Reportedly, the solution is simple: just enter the standard Ctrl + Alt + Del.
MS15-043 (3049563), MS15-053 (3050945)
Time for the regularly scheduled browser review
May’s cumulative update for Internet Explorer tackles 22 vulnerabilities, including some in the JScript and VBScript. Rated critical, KB 3049563 applies to all supported versions of IE, from IE 6 on. Windows 10 Technical Preview users will also see this update. (It’ll be interesting to see whether Microsoft’s next browser, Edge — more info — will require fewer fixes.)
The updates in MS15-053 also address vulnerabilities in the JScript and VBScript scripting engines that could allow bypassing Windows’ ASLR security feature. Rated important, KB 3050945 is for Vista systems; admins running Server 2003 and 2008 should see KB 3050946 and/or KB 3050945.
If you have Firefox installed, check that it’s on Version 38.0; Chrome should be on release 42.0.2311.152, which includes the latest Flash update. Standalone versions of Flash should be up to Version 17.0.0.188.
 What to do: Install KB 3049563 (MS15-043) and all other browser updates as soon as possible.
What to do: Install KB 3049563 (MS15-043) and all other browser updates as soon as possible.
MS15-044
A messy fix for malicious TrueType fonts
The numerous patches in MS15-044 resolve vulnerabilities in the way Windows DirectWrite library handles OpenType fonts. The issue affects a number of Microsoft components and applications including Windows, .NET Framework, Office, and others listed below. The most egregious of the vulnerabilities could allow remote code execution if you open a malicious document or webpage.
The following patches are all rated critical.
- 2881073 – Office 2010
- 2883029 – Office 2007
- 3039779 – Skype for Business
- 3045171 – Windows Server
- 3048068 – .NET 3.0 SP2
- 3048070 – .NET 3.5.1
- 3048073 – .NET 3.0
- 3048074 – .NET 4.0
- 3048077 – .NET 4.0, 4.5, 4.5.1, and 4.5.2
- 3051464 – Lync 2010
- 3051465 – Lync 2010 Attendee
- 3051467 – Microsoft Live Meeting
- 3056819 – Silverlight 5
Some of these updates will show up again in items below because of shared code. That sharing is why I’ll err on the side of caution and watch for possible side effects with third-party programs.
 What to do: Delay installing this blockbuster font update for a couple of weeks.
What to do: Delay installing this blockbuster font update for a couple of weeks.
MS15-045 (3046002)
Journal files lead to attacks
Windows Journal is an application for taking notes (more info). It was introduced in the XP Tablet PC Edition and is still found in editions of Vista, Win7, and Win8. But a malicious Journal file could give a hacker remote access to your system. The fix, KB 3046002, is rated critical and impacts all supported versions of Windows, including Win10 Preview.
On server platforms, you’ll see the update only if you’ve installed the Desktop Experience role. There are early reports that a few users have run into an error 0x80080005 message when trying to install the update. You might need to install KB 30496002 separately from all other patches.
 What to do: Install KB 30496002 (MS15-045) when offered.
What to do: Install KB 30496002 (MS15-045) when offered.
MS15-046
A whopper of an Office security update
MS15-046 replaces last month’s MS15-033, which included a slug of Office security fixes. Although some of the vulnerabilities could allow a remote hack, all these patches are rated just important.
- 2956140 – Office Web Apps 2010
- 2956193 – Office Web Apps 2010
- 2956194 – SharePoint Server 2010
- 2956195 – PowerPoint Viewer
- 2965233 – SharePoint Server 2010
- 2965237 – Word 2010
- 2965240 – Excel 2010
- 2965242 – Office 2010
- 2965282 – Office 2007
- 2965307 – Word 2013
- 2965311 – Office 2010
- 2975808 – Office 2013
- 2975816 – PowerPoint 2013
- 2986216 – Excel 2013
- 2999412 – Office 2010
- 2999420 – PowerPoint 2010
- 3023055 – SharePoint Server 2013
- 3039725 – SharePoint Servers 2013
- 3039748 – Office Web Apps 2013
- 3062536 – Office for Mac
 What to do: Install the updates included in MS15-046 as soon as possible.
What to do: Install the updates included in MS15-046 as soon as possible.
MS15-048 (3057134)
The usual round of .NET Framework fixes
The patches in MS15-048 fix two vulnerabilities in .NET Framework: one for an XML decryption denial-of-service threat and the other for a possible elevation-of-privilege attack via Windows Forms. All of the following patches are rated important. The list looks long, but you’re likely to receive only a subset of the patches.
- 3023211 – .NET 1.1 SP1
- 3023213 – .NET 2 SP2
- 3023215 – .NET 3.5.1
- 3023217 – .NET 3.5
- 3023219 – .NET 3.5
- 3023220 – .NET 2 SP2
- 3023221 – .NET 4
- 3023222 – .NET 4.5/4.5.1/4.5.2
- 3023223 – .NET 4.5/4.5.1/4.5.2
- 3023224 – .NET 4.5/4.5.1/4.5.2
- 3032655 – .NET 3.5.1
- 3032662 – .NET 4
- 3032663 – .NET 4.5/4.5.1/4.5.2
- 3035485 – .NET 2 SP2
- 3035486 – .NET 3.5
- 3035487 – .NET 3.5
- 3035488 – .NET 2 SP2
- 3035489 – .NET 4.5/4.5.1/4.5.2
- 3035490 – .NET 4.5/4.5.1/4.5.2
Also, last month’s KB 3037580 — .NET 4.5, 4.5.1, and 4.5.2 for Windows 8 and Server 2012 — has been revised and needs to be reinstalled. According to a MS TechNet Forums thread the problems with the original patch showed up primarily with server platforms.
 What to do: Since the retirement of XP, installing .NET updating is no longer an object of dread. Install any of the updates in MS15-048 when offered.
What to do: Since the retirement of XP, installing .NET updating is no longer an object of dread. Install any of the updates in MS15-048 when offered.
MS15-049 (3058985)
Silverlight: A case of use-it-or-lose-it
This is the first of our déjà-vu updates. KB 3056819 is the Silverlight update listed above in Security bulletin MS15-044. And here it is again in MS15-049. To add to the confusion, it was listed as critical in the first bulletin and important in MS15-049.
Confused? I am. Before accepting this update, step back and ask yourself whether you really need Silverlight. Netflix no longer relies on it. I recommend going to Windows’ Programs and Features applet and uninstalling Silverlight. Then see if any of your applications or services asks for Silverlight.
 What to do: If you must have Silverlight installed, feel free to install KB 3056819 (MS15-049).
What to do: If you must have Silverlight installed, feel free to install KB 3056819 (MS15-049).
MS15-050 (3055642)
Nearly the end of road for an aging server OS
A flaw in the Windows Service Control Manager (SCM) could lead to elevation-of-privileges attacks. SCM is used to communicate with remote systems (more info). It’s rated important for all supported Windows platforms — except Server 2003.
In a sign that Server 2003 is nearing its end of life, Microsoft didn’t offer the update to Version 2003. The company indicated that it was unable to architect a workable patch for a decade-old OS.
 What to do: Install MS15-050, KB3055642 as soon as possible.
What to do: Install MS15-050, KB3055642 as soon as possible.
MS15-051 (3045171)
Déjà vu, take 2: A kernel update
As with the Silverlight update, KB 3045171 is listed in two bulletins. We saw it above in MS15-044, and here it is again in MS15-051. And as with Silverlight, this kernel-mode driver update is rated both critical and important. The update fixes both the TrueType font issue and a vulnerability in the Windows kernel that could allow elevation of privileges.
If you understand all this, you might earn extra points in a Windows updates trivia contest. (Okay, so maybe I’m the only person in the universe who thinks a game of updates trivia might be fun.)
 What to do: Same recommendation as above: Wait a couple of weeks before installing KB 3045171 (MS15-051).
What to do: Same recommendation as above: Wait a couple of weeks before installing KB 3045171 (MS15-051).
MS15-052 (3050514)
An exploit that bypasses Windows-kernel security
Another Windows kernel update, KB 3050514, patches a vulnerability that could let an attacker bypass Windows’ Kernel Address Space Layout Randomization (KASLR) security component. The patch changes how Windows validates memory addresses.
Rated important, this update affects only editions of Windows 8 and Server 2012. Note: If you manually installed this update onto Win8, it will be superseded by KB 3061518 (MS15-055). That process is automatic if you install from Windows Update.
 What to do: Install KB 3050514 (MS15-052) soon.
What to do: Install KB 3050514 (MS15-052) soon.
MS15-054 (3051768)
Using the MMC for denial-of-service attacks
Many server admins use the Microsoft Management Console to manage their systems. But the MMC can also be used for advanced tasks on Windows workstations — for example, when configuring hard drives or enabling Windows’ master Administrator account, as described in this week’s Top Story.
A flaw in the MMC could allow a denial-of-service exploit if a hacker tricks a user into sharing a malicious .msc file. This avenue of attack is more often seen in an enterprise setting than on standalone PCs.
Impacting all supported versions of Windows, the fix, KB 3051768, is rated important.
 What to do: Install KB 3051768 (MS15-054) when offered.
What to do: Install KB 3051768 (MS15-054) when offered.
MS15-055 (3061518)
Leaking information from unsecure links
May’s last security update, KB 3061518, fixes a Windows flaw that could allow data theft. It changes the Secure Channel (Schannel) security system to disallow weak Diffie-Hellman ephemeral (DHE) keys — keys will have to be a minimum of 1024 bits. That’s important, because our SSL protocols are under heavy attack, and weakly encrypted links make easy targets.
 What to do: Install KB 3061518 (MS15-055) when offered.
What to do: Install KB 3061518 (MS15-055) when offered.
MS15-047 (2760412, 2956192, 3017815)
A SharePoint Server vulnerability
Microsoft’s server-based Web-sharing platform is vulnerable to remote attacks via the W3WP service. Because the attacker must be authenticated by the system, the update is rated just important. The update is for all supported versions of SharePoint Server (2007 SP3, 2010 SP2, and 2013 SP1), including versions of the service running on Small Business Server 2008 and 2011. Admins should remember to run the psconfig command on SBS 2011 in order to complete the update process (as noted on an SBS Blog post).
 What to do: Install KBs 2760412, 2956192, or 3017815 (MS15-047) after backing up your server.
What to do: Install KBs 2760412, 2956192, or 3017815 (MS15-047) after backing up your server.
May’s monumental list of nonsecurity fixes
If you didn’t install the nonsecurity updates offered in the latter half of April, they might be offered again in May’s Patch Tuesday release.
Here’s the list of nonsecurity updates you might see. It doesn’t include numerous Project and SharePoint Server updates. For a more complete list, see the May MS Office Sustained Engineering Team post.
Windows 7, 8, 8.1 and Windows Server 2008/2012
- 3013531 – Transferring .mkv files to Windows Phone
- 3020370 – Cmitrust.dll enhancement and Server 2008 R2 fix
Win8, Win 8.1, Win8.1 RT and/or Server 2012 R2
- 3013538 – Automatic brightness failure
- 3015696 – InputPersonalization.exe crashes
- 3022345 – Enables Diagnostics Tracking Service
- 3033446 – Wi-Fi connectivity issues on CHT systems running Win8.1
- 3036216 – Compatibility update
- 3037924 – System Image Backup to Blu-ray media issue
- 3038002 – Allows UHS-3 memory-card detection on Surface devices
- 3038562 – DPAPI data-access failure after password reset on Server 2012 R2–based domain controller
- 3038701 – Custom Media Size entries missing
- 3042216 – Shortcut-menu issues with multiple monitors and high resolutions
- 3043812 – Cambria font issues in Word
- 3044673 – No Android image-date information shown in Windows Explorer
- 3045717 – Narrator doesn’t stop when Ctrl key pressed
- 3045719 – Microsoft Project Siena gallery crashes
- 3045992 – “Description cannot be found” displayed in Event Viewer
- 3046737 – Korean translation error when Bluetooth devices disconnected
- 3047254 – Stop error “0x0000009F” with Bluetooth
- 3047255 – Stop error “0x0000009F” with two USB devices connected
Windows 8.1 RT only
- 3046743 – Reduces Office servicing footprint
Windows Server 2012 R2 only
- 2998097 – “Specified account does not exist” error message on password change
Office 2007/2010
- 2965291 – Office 2010; error when pasting HTML content
- 2965301 – Office 2010; SharePoint Workspace issue
- 2986252 – Outlook 2007 junk-mail filter
- 2986257 – Office 2010
- 2999439 – Office 2010; corrupted images that contain transparency
- 3015585 – Outlook 2010; various fixes
- 3015642 – Outlook 2010 junk-mail filter
Office 2013
- 2881017 – Office; garbled text in Word tables
- 2956152 – Office; improved OneDrive compatibility
- 2956164 – Outlook print-preview displays box in subject line, with Thai system locale set
- 2965253 – Office; error when pasting HTML content
- 2965259 – Office; improved OneDrive compatibility
- 2965269 – Office; improved OneDrive compatibility
- 2965271 – Office; compile error when using DAX with Power Pivot add-in
- 2965277 – Office; OneDrive synchronizing and Excel close error
- 2975869 – Office; Access crashes on VBA update
- 2975901 – OneNote; “Set Picture as Background” failures
- 2986156 – Office; Office Add-in issues
- 2986171 – Office; update for Yoruba proofing tools
- 2986209 – Outlook junk-mail filter
- 3039700 – Office; various fixes
- 3039711 – Outlook; Facebook compatibility
- 3039799 – Outlook; various fixes
- 3054782 – Outlook; Facebook compatibility
Other updates
- 2553251 – Project 2010; baseline values rollup failures
- 2767882 – SharePoint and SAP: Duet Enterprise 1.0
- 2881006 – Office Audit and Control Management Server 2013 or Spreadsheet Compare
- 2881076 – Office Audit and Control Management Server 2013 or Spreadsheet Compare
- 2899503 – Office Audit and Control Management Server 2013 or Spreadsheet Compare
- 2986209 – SharePoint Server 2010
- 2965292 – Visio 2010; org chart failure with duplicate names in Global Address Book
- 2975855 – Visio 2013; Shape geometry-feature failure
- 2986244 – OneDrive for Business
- 2986246 – Project 2013; various fixes
 What to do: Wait on these updates until the end of the month, when I’ll discuss any reported issues. April’s nonsecurity Office updates are safe to install, if you haven’t done so already.
What to do: Wait on these updates until the end of the month, when I’ll discuss any reported issues. April’s nonsecurity Office updates are safe to install, if you haven’t done so already.
Regularly updated problem-patch chart
This table provides the status of recent Windows and Microsoft application security updates. Patches listed below as safe to install will typically be removed from the table about a month after they appear. Status changes are highlighted in bold.
For Microsoft’s list of recently released patches, go to the MS Security TechCenter page.
| Patch | Released | Description | Status |
|---|---|---|---|
| 3045171 | 05-12 | Windows kernel-mode drivers; also in MS15-044 | Wait |
| 3056819 | 05-12 | Silverlight | Wait |
| 3057110 | 05-12 | Microsoft font drivers; see MS15-044 for full patch list | Wait |
| 3002657 | 03-10 | Windows Netlogon; for Windows Server | Install |
| 3030377 | 03-10 | Windows Task Scheduler | Install |
| 3030398 | 03-10 | VBScript; also KB 3030403 | Install |
| 3032323 | 03-10 | Adobe font driver | Install |
| 3032359 | 03-10 | IE cumulative update | Install |
| 3033889 | 03-10 | Windows Text Services; also KB 3039066 | Install |
| 3034344 | 03-10 | Windows kernel-mode driver | Install |
| 3035017 | 03-10 | Remote Desktop Protocol; also KB 3036493 (Win7) | Install |
| 3035126 | 03-10 | Windows Photo Decoder | Install |
| 3035131 | 03-10 | Windows kernel | Install |
| 3035132 | 03-10 | PNG image processing | Install |
| 3038999 | 03-10 | Microsoft Office; see MS15-022 for full list | Install |
| 3040856 | 03-10 | Microsoft Exchange Server | Install |
| 3046049 | 03-10 | Windows Schannel; combats FREAK exploit | Install |
| 2965219 | 04-14 | SharePoint Server; also KB 2965302 and 2965278 | Install |
| 3038314 | 04-14 | Internet Explorer cumulative update | Install |
| 3042553 | 04-14 | HTTP.sys in Windows | Install |
| 3045685 | 04-14 | Impersonation events; also KB 3045999 | Install |
| 3045711 | 04-14 | Active Directory Federation Services; servers only | Install |
| 3045755 | 04-14 | Security advisory; PKU2U enhancement | Install |
| 3046269 | 04-14 | Windows Task Scheduler | Install |
| 3046306 | 04-14 | Windows Graphics Component | Install |
| 3046482 | 04-14 | Windows XML Core Services | Install |
| 3047234 | 04-14 | Windows Hyper-V; Win8.1 and Server 2012 R2 | Install |
| 3048010 | 04-14 | .NET Framework; see MS15-041 for full patch list | Install |
| 3048019 | 04-14 | Word; see MS15-033 for full patch list | Install |
| 3046002 | 05-12 | Windows Journal | Install |
| 3049563 | 05-12 | IE cumulative update | Install |
| 3050514 | 05-12 | Windows kernel | Install |
| 3050945 | 05-12 | JScript and VBScript; also KBs 3050941 and 3050946 on servers | Install |
| 3051768 | 05-12 | MS Management Console file format | Install |
| 3055642 | 05-12 | Service Control Manager | Install |
| 3057134 | 05-12 | .NET Framework; see MS15-048 for full patch list | Install |
| 3057181 | 05-12 | Office; see MS15-046 for full patch list | Install |
| 3058083 | 05-12 | SharePoint Server; KBs 2760412, 2956192, and 3017815 | Install |
| 3061518 | 05-12 | Schannel | Install |
Status recommendations: Skip — patch not needed; Hold — do not install until its problems are resolved; Wait — hold off temporarily while the patch is tested; Optional — not critical, use if wanted; Install — OK to apply.
Cookies can do more than make you fat
Lounge member wavy was surprised to find himself redirected from the Microsoft webpage he’d expected to land on — he ended up on an MS sign-in page.
He was using Firefox as his browser, and — unless he used private browsing — he got this unwelcome result every time.
This problem engaged a few active and experienced minds in the Third-Party Browser forum. It turns out that enabling third-party cookies can take you places you might not have planned on going to.
The following links are this week’s most interesting Lounge threads, including several new questions for which you might have answers:
 starred posts: particularly useful
starred posts: particularly useful
If you’re not already a Lounge member, use the quick registration form to sign up for free. The ability to post comments and take advantage of other Lounge features is available only to registered members.
If you’re already registered, you can jump right into today’s discussions in the Lounge.
Insights and interesting news on computing
A recent trip to Hawaii shows that there is still plenty of room for computing innovation — and better help on the Web.
Plus: A reminder that email is never a good medium for venting thoughts best kept to oneself.
A new WS column on general computing
As we hope most Windows Secrets subscribers now know, our newsletter recently became part of Penton, a rapidly growing media company that addresses a wide range of markets such as technology, agriculture, transportation, and more. This change will undoubtedly be a good thing for Windows Secrets. The design and format haven’t changed in many years, and an upgrade is overdue.
With this acquisition, there will be some changes in the newsletter, designed to make our information even more useful and timely. One of those changes will be a regular column by yours truly, the editor of Windows Secrets. There will be no set theme, topic, agenda, or particular rant for the column — which, for want of an acutely clever label, I simply call Field Notes.
The title reflects over 30 years of using and covering technology every day. That experience is not limited to Windows; I have deep appreciation and interest in all technology. (For example, I hope to find some time to explore drone photography.) Still, I’ll try to keep the topics relevant and interesting to most PC users.
I invite your feedback in the Windows Secrets Lounge on topics to consider and useful information you’d like to see in the column — and useful changes you’d like to see in the newsletter. Let’s keep it constructive. (Use the link at the bottom of the column.) To kick things off, here are two recent observations.
Wanted: A good solution for uploading images
As you know, the editors of Windows Secrets took a week off at the end of April. My time off was spent visiting my son in Hawaii. (What Seattleite could resist an excuse to travel to somewhere warm and sunny?)
To a dedicated photographer, the islands offer endless opportunities to create images. But in my case, it also presented a dilemma — how to download and safely store potentially hundreds of bulky RAW photos. It was, of course, a problem I didn’t thoroughly consider until I was on my way to Oahu.
To travel as light as possible, I’d left my notebook computer at home and taken my iPad Air. My plan seemed simple and obvious: download images to the iPad and upload them to Dropbox. That procedure is relatively simple — if you have lots of free space on the iPad, which I didn’t. After some research over a beer or two, the only solution seemed to be to download the day’s images to the tablet, let Dropbox sync them to the cloud, and then delete them from the iPad. But it’s a cumbersome process on a simple touchscreen device.
Eventually, I gave up and simply kept the hundreds of photos on my memory cards and hoped the shots were not overwritten nor the small SD Cards lost.
I assume there is a solution out there. (Looking for help on the Internet demonstrated what we already know: for the most part, the Web is light-years wide and an inch deep.) If you know of one, post it in the Lounge. If there isn’t one, here’s a great opportunity for a clever programmer. Write an app that lets digital-camera users directly download images from camera to cloud, using a tablet as a bridge.
What we put down in email can bite us
TV shows rarely get technology right, but a recent episode of The Good Wife scripted a humorous reminder of a basic computing rule: treat everything you put in email as information that might end up on the front page of the New York Times.
In the episode, a hacker cracks the law firm’s email servers and publicly posts hundreds of messages online, airing much of the firm’s dirty laundry — primarily snide remarks associates and partners have made about each other. You can easily imagine the results.
In the real world, the key lessons are that email is never completely secure from hacks: deleting a message is not like burning a letter (it might live on, inside other servers), and it can easily go astray. You might recall reports of some unfortunate employee who wrote a snarky response intended for a fellow worker but who stupidly hit the reply-to-all button.
I followed another security rule while I was out on the islands: if you’re leaving an empty house at home, resist the temptation to post travel photos on Facebook. As with ill-considered email, careless social-media sharing can bring you grief.
Peculiar forces converge in Portland, Oregon
 |
A campaign to “Keep [My City] Weird” might have originated in Austin, Texas, but we in the Northwest region of the country have no doubt that the people of Portland, Oregon, are the most enthusiastic competitors in the odd contest. And many Portlanders are proud of this reputation. They promote it. This week’s video illustrates the case of a flame-shooting bagpiper playing the “Star Wars” theme while balancing on a BB-8 droid. Would such an event be regarded (benignly) as unremarkable in your town? We think not. Next question: How did that BB-8 droid go off-script from its as-yet-unreleased Star Wars 7 film “The Force Awakens” and show up in Portland? Weird. Click below or go to the original YouTube video. |
| Post your thoughts about this story in the WS Columns forum. |
Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com).
Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners.
Your email subscription:
- Subscription help: customersupport@askwoody.com
Copyright © 2025 AskWoody LLC, All rights reserved.

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Suggestions for New All in One Printer and a Photo Printer Windows 10
by
Win7and10
4 hours, 56 minutes ago -
Purchasing New Printer. Uninstall old Printer Software First?
by
Win7and10
5 hours ago -
KB5060842 Issue (Minor)
by
AC641
9 hours, 33 minutes ago -
EchoLeak : Zero Click M365 Copilot leak sensitive information
by
Alex5723
12 hours, 5 minutes ago -
24H2 may not be offered June updates
by
Susan Bradley
1 hour, 14 minutes ago -
Acronis : Tracking Chaos RAT’s evolution (Windows, Linux)
by
Alex5723
1 day ago -
Turning off OneDrive
by
CWBillow
1 day, 5 hours ago -
June 2025 updates are out
by
Susan Bradley
46 minutes ago -
Mozilla shutting Deep Fake Detector
by
Alex5723
1 day, 15 hours ago -
Windows-Maintenance-Tool (.bat)
by
Alex5723
1 day ago -
Windows 11 Insider Preview build 26200.5641 released to DEV
by
joep517
1 day, 17 hours ago -
Windows 11 Insider Preview build 26120.4250 (24H2) released to BETA
by
joep517
1 day, 17 hours ago -
Install Office 365 Outlook classic on new Win11 machine
by
WSrcull999
1 day, 17 hours ago -
win 10 to win 11 with cpu/mb replacement
by
aquatarkus
1 day, 9 hours ago -
re-install Windows Security
by
CWBillow
1 day, 21 hours ago -
WWDC 2025 Recap: All of Apple’s NEW Features in 10 Minutes!
by
Alex5723
2 days ago -
macOS Tahoe 26
by
Alex5723
1 day, 19 hours ago -
Migrating from win10 to win11, instructions coming?
by
astro46
6 hours, 16 minutes ago -
Device Eligibility for Apple 2026 Operating Systems due this Fall
by
PKCano
1 day, 9 hours ago -
Recommended watching : Mountainhead movie
by
Alex5723
1 day, 10 hours ago -
End of support for Windows 10
by
Old enough to know better
17 hours, 56 minutes ago -
What goes on inside an LLM
by
Michael Covington
1 day, 4 hours ago -
The risk of remote access
by
Susan Bradley
13 minutes ago -
The cruelest month for many Office users
by
Peter Deegan
12 hours, 25 minutes ago -
Tracking protection and trade-offs in Edge
by
Mary Branscombe
1 day, 14 hours ago -
Supreme Court grants DOGE access to confidential Social Security records
by
Alex5723
2 days, 23 hours ago -
EaseUS Partition Master free 19.6
by
Alex5723
1 day, 23 hours ago -
Microsoft : Edge is better than Chrome
by
Alex5723
3 days, 12 hours ago -
The EU launched DNS4EU
by
Alex5723
4 days, 1 hour ago -
Cell Phone vs. Traditional Touchtone Phone over POTS
by
280park
3 days, 15 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.

