
|
There are isolated problems with current patches, but they are well-known and documented on this site. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
A refresher course on Facebook privacy controls
In this issue
- TOP STORY: A refresher course on Facebook privacy controls
- LOUNGE LIFE: Don't know what you've got till it's gone
- WACKY WEB WEEK: Eight bits of animal lore — contradicted
- LANGALIST PLUS: No-reformat reinstalls for all Windows versions
- WOODY'S WINDOWS: Zapping System Progressive Protection
- BEST PRACTICES: Devices to give Wi-Fi networks a boost
- PATCH WATCH: Microsoft releases critical patch for IE
A refresher course on Facebook privacy controls
With over a billion active users recording the minutiae of their activities, purchases, travel plans, and other personal information, Facebook is a potential treasure trove for hackers and marketers trolling for data.
Facebook’s privacy settings seem to be a constantly moving target, so it’s important to review them from time to time. Here’s what you need to know.
The challenge of understanding Facebook privacy
Since its inception, Facebook has been — and often still is — criticized for its privacy controls. Well-publicized hacks of Facebook pages belonging to founder Mark Zuckerberg and the French president back in January 2011 didn’t help. For many users, Facebook privacy controls were either lacking or too difficult to wade through.
Fortunately, Facebook’s latest privacy-control enhancements are more accessible to the social site’s users. Unfortunately, many of the controls are disabled by default or set at their lowest threshold. And there’s still a bewildering array of privacy settings, scattered in different locations, that determine who can access information you’ve posted.
There’s one other frequently misunderstood fact about Facebook privacy: Because friends of your friends can see some of the things you post and tag — even if you’ve set more restrictive settings — you’re never sure just who is seeing what.
Review and change privacy via Privacy Shortcuts
Reviewing your Facebook privacy settings is important for understanding and controlling what personal information others — individuals and companies — can access on your page. The basic privacy settings are now easily accessed via the new Privacy Shortcuts tools, found under the lock icon to the right of your sign-in name.
Click the lock, and you’ll get a drop-down list of options, starting with one of the most basic settings: Who can see my stuff? Click its down-arrow, and the first configuration option is Who can see my future posts? (see Figure 1).
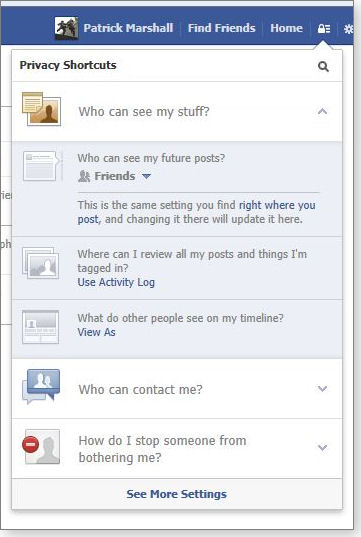
Figure 1. Facebook's Privacy Shortcuts gives you quick access to basic privacy settings.
The default (or current) setting is clearly displayed. If you want to change it, just click the down arrow and choose Public, Friends, Only Me, a custom setting, or other listed choices (see Figure 2).
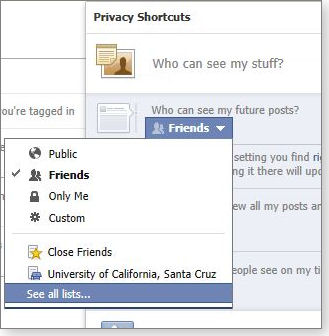
Figure 2. Facebook's options for choosing who sees your future posts
Although it’s not well explained, selecting the “Custom” option (see Figure 3) lets you choose specific people or lists of people who won’t be able to see your postings. You’re also reminded that anyone tagged in your photos will be able to see those postings, regardless of the privacy settings you have in place.
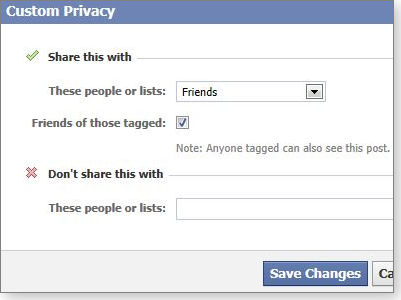
Figure 3. The Custom Privacy tool gives finer control over who sees your future posts.
Curiously, if you want to change the audience for all of your old posts, you have to go to the Configuration menu, accessed via the gear icon next to the Private Shortcuts icon.
Managing your timeline posts, likes, tags, etc.
The next item under Who can see my stuff? is Where can I review all my posts and things I’m tagged in? Clicking this option takes you to the Activity Log page. (You can also access the log from the Privacy Settings option under the configuration menu.) Facebook’s activity log lets you scan your likes and postings as well as photos in which you have been tagged. In each case, you can see who is able to see these items by hovering over the people icon next to the item. Click the pencil icon, and your options depend upon the type of item.
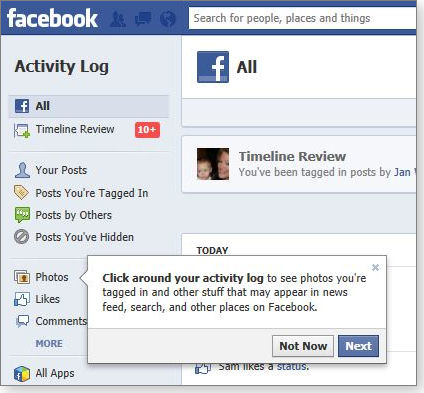
Figure 4. As you work with Facebook's privacy settings, popup dialog boxes can walk you through the log-review process.
For example, if the item is something you liked, clicking on the pencil icon will let you unlike it. For posts, the pencil lets you delete the posting. For photos in which you’re tagged, options include hiding it on your timeline or requesting that the author of the tag or the photo remove it (see Figure 5). If it’s a status update or a photo that has been posted to your wall by someone else, you can delete it, hide it on your timeline, or highlight it.
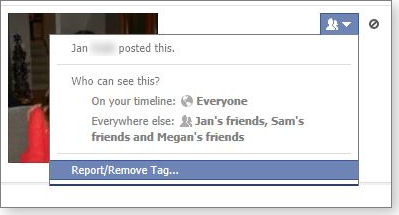
Figure 5. If you don't like being tagged in a photo, you can ask that the tag or photo be removed.
Viewing how your timeline looks to others
The last option under Who can see my stuff? is What do other people see on my timeline? Click it, and your timeline pops up with a black bar across the top and a control that states: This is what your timeline looks like to: — followed by “View as Public” or “View as Specific Person.” A Tip box also pops up, stating, “Remember: Things you hide from your timeline still appear in news feed, search, and other places on Facebook.” Confused? Me, too! One of the most daunting features of Facebook is trying to keep track of all the places your information can be seen.
Controlling who can send you messages
The next section of the Privacy Shortcuts menu — Who can contact me — has two options. The first — Whose messages do I want filtered into my Inbox — offers Basic Filtering (Mostly your friends and people you may know) and Strict Filtering (Mostly just friends — you may miss messages from other people you know). The use of the terms “mostly” and “may” leave me wondering who is really in charge here.
Next, you can choose whether to receive friend requests from any Facebook user or only from friends of friends, as shown in Figure 6.
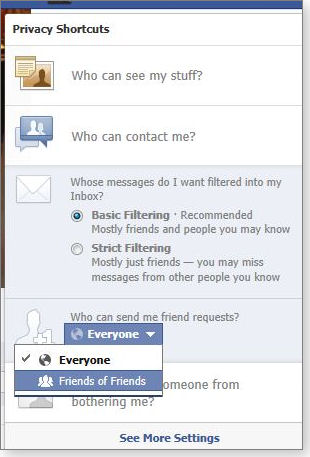
Figure 6. Facebook's friend-request control
Locking down access to your previous posts
The third item on the Privacy Shortcuts menu, How do I stop someone from bothering me?, is simply a quick way to unfriend someone. Just enter the individual’s name or e-mail address, and that person can no longer initiate conversations with you or see your timeline.
Clicking See More Settings at the bottom of Privacy Shortcuts takes you to the Privacy Settings and Tools screen, which is also accessible by clicking on the configuration (gear) icon next to the Privacy Shortcuts lock.
You’ll find a lot of repetition here. As with Privacy Shortcuts, you can specify who can see your future posts, and you can access the Activity Log. However, an additional option — Limit Past Posts — restricts who can see previous posts. It changes posts shared with the public or friends of friends to just friends — and to people who are tagged plus their friends. (Gee, it’s still kind of hard to know who is actually open to seeing what, isn’t it?)
The next item specifies who can look you up using your e-mail address or phone number — everyone, friends of friends, or just friends — and whether or not search engines can link to your timeline (see Figure 7).
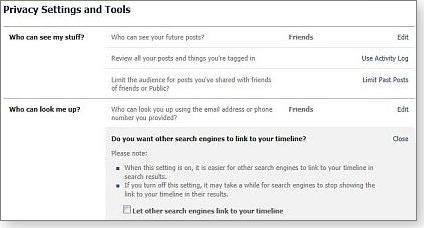
Figure 7. The Who can look me up? control also lets you control search-engine access to your Facebook timeline.
Just under the Privacy option in the left-hand navigation panel, you’ll find an entry for Timeline and Tagging. This screen, too, repeats much of the controls available in the Privacy Shortcuts. You can, for example, specify who can view your posts. But there are some additional tools; for example, the Review posts friends tag you in before they appear on your timeline option. Although that sounds useful, it won’t prevent your tagged image from appearing on other people’s timelines.
At the bottom of the Timelines and Tagging Settings page, you’ll find three options for configuring how tags are handled. With the first option, you can opt to review and approve or reject tags others want to add to posts in your timeline. The second option determines who else can see a post you’re tagged in. (This one seems really confusing.) The options are the usual Friends, Only Me, and Custom.
The final setting in Timelines and Tagging Settings (shown in Figure 8) is Who sees tag suggestions when photos that look like you are uploaded? The only two options are you or your friends. (Does your head hurt now? Mine does.)
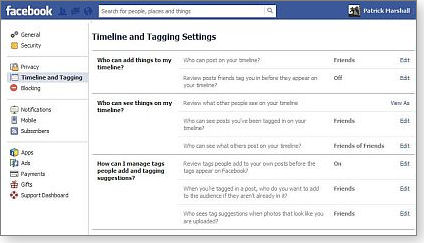
Figure 8. Facebook's Timeline and Tagging Settings
The last privacy-settings category (in the left-hand navigation panel below Timeline and Tagging) is Blocking. The first blocking option — Restricted List — lets you create a list of friends who can see only those posts you make public. There’s also a note that “Facebook does not notify your friends when you add them to your Restricted list.” This might be a good option for business contacts and others with whom you’re only sorta friends.
There are four other blocking options, shown in Figure 9. For each, you just type in the names of those you want blocked. You can block users, application invitations, event invitations, and applications. The last item will prevent applications from contacting you or collecting nonpublic information. Unfortunately, the onus is on you to manage the lists.
(Of course, the best Facebook privacy policy is to refrain from downloading and using Facebook applications in the first place.)
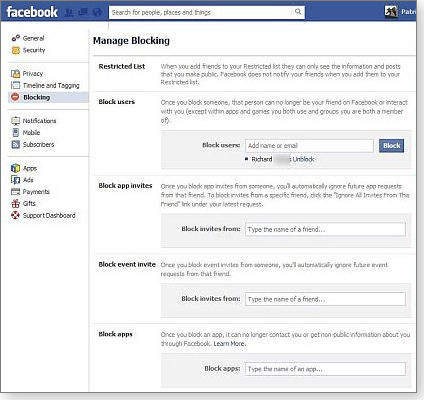
Figure 9. The blocking controls include the ability to restrict applications from using your personal information.
Finally, it’s worth noting that, although Facebook has added many privacy controls and simplified some existing ones, it has recently removed a major option: users can no longer hide themselves from Facebook searches. Small wonder some Facebook users have decided to unfriend themselves from the world’s largest social network.
Don't know what you've got till it's gone
It should be no surprise to learn that people love some fonts and hate others.
Oddly, it turns out that people can be just as particular about their screen cursors. In the Windows 7 forum, Lounge member Gromek laments the paucity of cursor-icon choices. He’s looked everywhere, he thinks, for a better cursor — one he knows used to exist in XP. Fellow Loungers offer their insights.
The following links are this week’s most interesting Lounge threads, including several new questions for which you might have answers:
 starred posts: particularly useful
starred posts: particularly useful
If you’re not already a Lounge member, use the quick registration form to sign up for free. The ability to post comments and take advantage of other Lounge features is available only to registered members.
If you’re already registered, you can jump right in to today’s discussions in the Lounge.
Eight bits of animal lore — contradicted
 |
What do lemmings, daddy longlegs, ostriches, baby birds, goldfish, dogs, bats, and frogs have in common? They all are victims of widely shared misconceptions professed by millions of human beings. Setting the record straight, this rapid-fire mini-lecture begins with the persistent myth of the suicidal lemming. Fortunately, the truth is far more interesting than the fable. Play the video |
No-reformat reinstalls for all Windows versions
When Windows goes badly wrong, rebuilding the operating system without reformatting and reinstalling apps and data can save hours of work.
A fast, nondestructive Windows reinstall is a manual process in XP, Vista, and Win7, but it’s built in and fully automatic in Windows 8.
Reader seeks no-reformat reinstall for Win8
A nondestructive Windows reinstall completely refreshes the operating system but retains your user accounts, data, passwords, and/or installed programs. This type of repair takes a fraction of the time required for a standard, full reinstall — and it’s much, much easier to do.
I’ve covered nondestructive reinstalls for previous versions of Windows in several earlier stories. See, for example, the July 14, 2011, Top Story, “Win7’s no-reformat, nondestructive reinstall.” The process for Vista is nearly identical. For Windows XP, check out the 2006 InformationWeek article, “XP’s no-reformat, nondestructive total-rebuild option.”
Reader William Searle wondered about this capability in Windows 8.
- “Is there a Win8 version of the ‘no-reformat, nondestructive reinstall?'”
Indeed there is, William. Microsoft made it easier than ever and built it right into the operating system; it’s nondestructive for your settings and user data and for native Win8 apps downloaded through the app store. (From-disc apps, however, might still have to be reinstalled the old-fashioned way.)
Here’s how to access the Win8 version of the reinstall process.
Open the Win8 Charms bar and click Settings (the gear icon). At the bottom of the Settings bar, click Change PC settings. On the PC Settings page, select General and then click the Get started button under Refresh your PC without affecting your files (as shown in Figure 1).
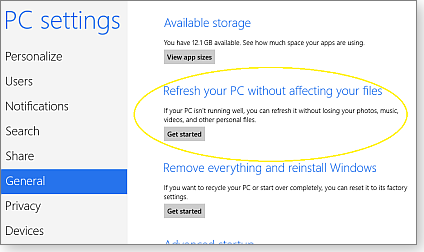
Figure 1. Win8's built-in version of a no-reformat, nondestructive reinstall is always just a few clicks away in the PC Settings menu.
The next screen tells you exactly what the refresh will do. Read it carefully. For example, it notes that applications you installed from disc or the Web will be removed. (Apps downloaded from the Windows Store are retained.)
It’s taken a long time for this capability to become a standard item in Windows, but it’s great that it’s finally there!
Secure Internet use in public places
Gerald Gibson wonders about wireless security when on the road.
- “When I travel, I like to use the wireless Internet available at hotels and motels.
However, I use unsecured public connections only for general research — not for personal banking or credit-card accounts.“What software can I use, or connection can I make, to securely check my accounts?”
Gerald, a virtual private network (VPN) will improve online security on public nets. A VPN connection uses a form of encryption to establish a secure, private channel between your PC and a VPN provider’s server. That private channel is often metaphorically referred to as a VPN tunnel because data passes directly and securely (via dedicated connections and/or encryption) through any and all intervening networks, even if they’re public and insecure. (For more, see Wikipedia’s VPN article.)
A VPN-tunnel provider becomes a trusted man in the middle for private connections to sensitive sites such as that of a bank or credit-card company.
To set up a secure VPN connection, start by establishing an encrypted link to a VPN server, usually using software supplied by a reputable VPN provider. This private connection is separate from any other connections you might have with the local Wi-Fi/Internet provider (ISP). This makes your VPN communication quite reasonably secure from any local snoops on the public (hotel, motel, cafe, etc.) network.
At the VPN-server end, your data is decrypted and passed along to its intended destination — such as your bank’s site. This leg of the connection is no more, or less, secure than, say, the connection from your home ISP to the bank. But it’s well beyond the reach of any snoops on a public net.
There’s an added benefit to using a VPN connection: your retransmitted data packets arrive at their destinations carrying the VPN provider’s IP addresses and localization data (rather than yours). This means the site you’re communicating with won’t know your actual, originating IP address, location, or other identifying information — unless you specifically reveal it. Thus, a VPN tunnel can be useful if you want to surf or visit sites anonymously.
The only catch to using VPN is that you have to trust your VPN provider. As the man in the middle, the provider knows who you are and where you are. An unscrupulous VPN provider could easily snoop your decrypted data. So it’s important to use only reputable companies.
The various free VPN providers are fine for lightweight, anonymous surfing. But for sensitive communications, where a security breach could have serious repercussions, it’s best to use an established commercial VPN provider with a good reputation. There are many to choose from, but here are a few to get you started:
- openvpn.net: 100MB of free data transfer, with commercial accounts available for larger data volumes.
- VPNreactor.com: free use for up to 30 minutes at a time, with paid accounts for unlimited use.
- VPNmaster.com: unlimited data transfer for U.S. $3.95 a month and up.
A Web search will show you many more VPN providers. But take your time and choose carefully!
An open discussion of Windows 8’s usability
B.R. Black would like to start a discussion on Win8’s overall usability, especially Microsoft’s decision to put tablet-centric functions on the desktop version of the OS.
- “I’ve been reading Jakob Nielsen’s Alertbox newsletters almost as long as I’ve been reading Windows Secrets. His analysis of Windows 8 provides a serious look at why Win8 has usability issues for various users. Check out his article on the Nielsen Norman Group site.
“Nielsen didn’t comment on Gnome 3’s new desktops or the several generations of Ubuntu’s Unity desktop, but several of the same usability issues apply. So the use of a tablet interface on a desktop computer is not just a Windows issue. There are several attempts underway to combine elements of the desktop and tablet interfaces into a one-size-fits-all interface. In most cases, these efforts are misguided.
“I recently purchased a few extra copies of Windows 7, which I’ll continue to use as my desktop or laptop OS for as long as I can — or until something better is released. I’ll also continue to use a Debian- or Ubuntu-derivative OS for my day-to-day activities. And I’ll monitor Windows Secrets so I can help others when they get into problems with Windows.”
I agree that Win8’s user interface is a major issue. It’s a stumbling block for many potential users, despite the fact that Win8 has some very nice technology under the covers. (See, for example, the lead item in this column.)
To crib from Lord of the Rings, Win8 tries to be “the one (interface) to bind them all” — phones, tablets, and desktops. But it ends up being awkward and confusing for many Windows users. For example, some parts of Win8’s hybrid interface use the tile format; other parts reside within the traditional desktop environment. Win8 makes you constantly shift mental gears, making even expert Windows users feel like noobs again — at least at first.
There are also ergonomic issues. Although Win8 on the desktop is fully mouse-compatible, using that familiar input device involves lots of ergonomically dubious, large-scale arm movements. Previous Windows versions could be managed without moving your arms much from an ergonomically correct, near-resting, neutral position. (In fact, working with Win8 on a desktop might be more effective if you take some time to memorize some of its common keyboard shortcuts, as detailed in the Nov. 1, 2012, Best Practices story. Or use a small touchpad or touch-capable mouse, as described in that same issue’s Best Hardware review.)
It can be even worse with Win8 tablets. When using the OS in a pseudo-notebook setting (such as a Microsoft Surface with its snap-on keyboard), you have to constantly move your hands from the keyboard to the touchscreen, then back to the keyboard. It’s both tiring and inefficient — and ergonomically unsound, because you can’t sit and use the tablet in a correct computing posture (as shown in an Office Details diagram).
Handheld use of Win8 brings its own ergonomic woes. Win8 tablets are really designed for use in wide-screen, landscape mode. Although Win8 can shift to portrait (vertical) mode, some apps work only in a horizontal format. (Every Win8 print and TV ad I’ve seen shows Win8 only in landscape mode.)
Landscape mode is great for movies, but it’s awkward and uncomfortable for many routine, handheld uses; you more or less have to use two hands to hold the tablet. Moreover, you often have to use exaggerated arm movements for some commands, such as swiping the full width of the tablet to get to an off-screen tile. It’s annoying and tiring over long periods of use.
In contrast, iPads and most Android tablets are meant to be held and used primarily in portrait mode — as you would hold a smartphone or book. This makes one-handed operation easy. (Yes, landscape mode is available in Android; you need only turn the tablet sideways when you’re doing something that needs the full screen width, such as watching a movie. But the default orientation is usually portrait mode.)
There’s more, but the upshot is this: I find Win8 pretty solid under the hood but otherwise disappointingly confusing, hard to use, and ergonomically unsound.
I really hope that Windows 9 — whenever it arrives — retains the many good points of Win8 while scrapping the stuff that simply doesn’t work well.
Samsung-specific, Android/Outlook synching
David Putnam offers this info for Samsung phone owners. (I don’t often discuss vendor-specific apps, but Samsung makes more Android phones than any other manufacturer. So this applies to an unusually large number of smartphone users.)
- “How about Samsung’s Kies? It just had an update (I downloaded it today) and actually comes close to working now. I was impressed and now have all my Outlook contacts (I think) in my Galaxy phone.”
Thanks, David! As the Kies help file states, it can “synchronize contacts, schedules [i.e., calendars], memos, or the to-do list with Outlook” as well as “synchronize contacts with Web accounts (Google, etc.)”
That’s all good, but I find Kies to be somewhat rough — it feels like a beta version to me. I originally installed it because it can back up, restore, and upgrade the phone’s firmware. But I’ve never needed Kies for that task; so far, I’ve received all my system updates automatically and effortlessly over the air.
So I’ve come to prefer native-Android apps for the stuff that Kies can do. That said, Kies is a free download from the Samsung site.
Zapping System Progressive Protection
Over the holiday break, three people sent me panic messages asking about an antivirus product that was demanding money to fix their computers.
If my admittedly small sample is any indication, the venerable and virulent “System Progressive Protection” rogueware is back with new infection methods to delight us all. Oh boy.
System Progressive Protection’s persuasive ways
System Progressive Protection — SPP to its friends — presents some truly scary statistics to personal-computer users unfortunate enough to fall under its sway. It reports finding dozens — even hundreds — of Trojans, dialers, pernicious autoruns, spyware, and the like on a system. In truth, it’s probably the only thing infecting the machine. Of course, your only “solution” is to send money to the purveyors of System Progressive Protection so their bogus program can “activate” and rid the computer of the creepy-crawlies it “found.”
That’s the scam. In practice, if you send money, you’re giving the con artists both your credit-card number and the keys to your PC.
Yes, it’s the old rogue-anti-malware shtick. But recently, SPP’s infection vectors have become considerably more subtle — and the demands more outrageous. It’s particularly galling to see an SPP scan flag dozens of rogue applications on a completely clean machine (a bit of the pot calling the kettle black).
Less sophisticated rogue-malware scanners typically perform an ersatz scan and threaten fire and brimstone if you don’t activate the “scanner” by sending money. Most bogus scanners turn belly-up when confronted by a quick run of Microsoft Security Essentials, Malwarebytes, or some other legitimate AV product.
That’s not the case with this new version of SPP. It digs deep into Windows, making it resistant to nearly every type of malware-scanning software I’ve used. Manual disinfection methods that work on earlier versions of SPP might be ineffective with the latest incarnation. I haven’t yet seen a detailed analysis of this new version, but it appears to burrow in and run as a rootkit (Wikipedia definition) — a particularly tenacious type of infection.
Just to add to your woes, SPP can also disable other Windows programs. Try to run, say, Notepad or WinWord, and you might get a popup notification similar to the one in Figure 1. Run your browser, and it might pop up more bogus malware warnings. On some systems, it knocks out antivirus and/or firewall programs, or it might disable legitimate AV software, Windows Update, some parts of Windows Defender — or even the Windows Security Center.
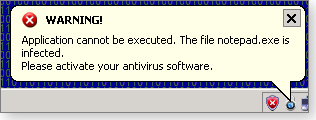
Figure 1. System Progressive Protection can hijack common .exe files and display a bogus security warning.
It gets worse. Some versions of SPP take over your Internet connection, making it impossible to run online AV scanners. To establish a Web connection, you have to boot Windows into Safe Mode and manually override the SPP proxy setting. There are also reports that the malware reappears after users manually clean their systems.
A Microsoft Malware Protection Center page identifies SPP as a variant of Win32/Winwebsec (more info), a family with a long list of aliases, such as AntiSpyware Pro 2009, MS Removal Tool, Security Shield, Total Security, and (just to stay timely) Win 8 Security System. Microsoft is especially sensitive about Winwebsec because several variations use Microsoft names and/or trademarks to make them appear legitimate.
Nobody seems to know who’s behind System Progressive Protection. It’s fair to assume that there’s a group at the core of it — typically, lucrative Internet scams involve dozens of people, both on the technical end and on the distribution and money side. We can also assume that law-enforcement agencies all over the world, along with teams at Microsoft and other organizations, are working hard to bring the perpetrators down.
For now at least, the dark side is winning.
The various ways SPP infects Windows systems
Of the three people who contacted me, one had been infected via an attachment on a bogus UPS-delivery email. The victim is an experienced computer user, but he wasn’t watching closely. The attachment was an .exe file with a plausible explanation; he double-clicked to “open” the file, clicked once more — and his PC was, as the hackers say, pwned.
The second person confessed (in hushed tones) that he’d been visiting video sites, some of which required downloading and installing video decoders (codecs) specific to the type of video he was trying to view. Bad dog; bad, bad dog. My advice was to install and use VLC Media Player (site) for viewing online videos. I added this warning: If VLC doesn’t have a codec for the type of file you’re trying to view, stop! — move on to another video.
The third victim had a less common — and much more interesting — story. While he was surfing the Web, one of the visited sites stated that he needed to update Adobe Flash Player. He followed the instructions on the popup, downloading and installing “Flash Player,” and bang — he was infected. He received no unusual warnings during the download or installation.
All three victims were running the latest version of Microsoft Security Essentials — and blamed Microsoft for shoddy protection. MSE was decertified by the highly regarded AV-Test in its latest report, as noted in a Softpedia story. I’ve been recommending MSE for years now, and that news hurt. But it’s hard to pin the blame on MSE.
In the case of the bogus UPS notification, the recipient essentially shot himself in the foot by clicking twice through unambiguous warnings. He just wasn’t paying attention. That’s not MSE’s fault.
The second infection — the dodgy codec — also required several deliberate clicks, over Windows 7’s objections. (Even XP would’ve been smart enough to warn a couple of times.) Video downloads are especially likely to end in difficult consequences, if one is not paying careful attention.
However, the third infection should have drawn a warning from MSE. It should have scanned the downloaded file, caught the SPP infection, and sent up red flags when the user tried to install it. MSE missed the boat on that one.
I was all set to get on my high horse (as, I’m sure you know, I’m wont to do) and wail about the sorry state of MSE, when I bumped into a post on the Malwarebytes Newest Rogue Threats forum. Poster BornSlippy uploaded a file that identified itself as an Adobe Flash Player update. He ran the file through VirusTotal (site), a malware-scanning service that checks submitted files against every major antivirus package. Out of 46 tested packages, only six flagged the file as being infected — and no two agreed on which malware resided in the file.
Although it’s not known whether BornSlippy’s file held SPP, it’s quite sobering that a presumably infected file identifying itself as an Adobe Flash Player update could get through the majority of AV scanners — including most of the big-name ones. Avast, AVG, BitDefender, Comodo, F-Secure, Kaspersky, Malwarebytes, McAfee, Microsoft, Panda, Sophos, Symantec, TrendMicro, and VIPRE all missed the malicious payload. BornSlippy posted the file on December 22, which is just about the time my third victim got hit with the infector disguised as a Flash update. Bottom line: Beware of random Flash Player update offers. A new release of Flash Player was released last week; get it from the Adobe site.
Protect yourself from SPP and similar threats
The “prevention” steps given on Microsoft’s Win32/Winwebsec (which, again, includes System Progressive Protection) site are a rehash of admonitions we’ve heard a thousand times. Specifically, we’re told to:
- Enable a firewall on your computer.
- Get the latest computer updates for all your installed software.
- Use up-to-date antivirus software.
- Limit user privileges on the computer.
- Use caution when opening attachments and accepting file transfers.
- Use caution when clicking on links to webpages.
- Avoid downloading pirated software.
- Protect yourself against social-engineering attacks.
- Use strong passwords.
Gag me with an EPROM.
All three of the aforementioned victims were using the built-in Windows firewall. It didn’t help, not even a little bit. They all had the latest updates. However, one victim was tricked into believing he was one update behind on Flash. They were all using Microsoft Security Essentials — and it didn’t squeal. Limiting user privileges (i.e., running with a “standard” account) is great in principle, but few PC users do it in practice. In any case, it’s not clear whether running a standard account would’ve made any difference in the outcome of these three SPP attacks. In this case, pirated software had nothing to do with anything. Ditto strong passwords.
That leaves us with two obvious admonitions: Use caution when opening links and attachments, and protect yourself against social-engineering attacks. That’s a bit like saying, “Don’t run with scissors” (which, as noted in a 2007 MS article, was another Microsoft admonishment, years ago).
I believe that protecting yourself from attacks such as SPP is really a question of constant and consistent mindfulness. It’s easy to become inured to our click-click-click (or, increasingly, tap-tap-tap) responses to computer dialog boxes and prompts. Unfortunately, with most of today’s threats, that inattention is what gets you infected. You really do need to think before you click. Easier said than done, I know.
The flip side of that observation is: Don’t automatically accept whatever demands pop up on your screen. In this age of constant phishing and malicious mimicry, just because a website says you need a new version of Flash doesn’t mean you really do. No matter how legitimate the site looks, go to the source (e.g., the Flash Player site) and check for yourself. (Or, preferably, wean yourself off Flash as much as you can.) Be suspicious if a site requires downloading a new codec just to view a movie. And for heaven’s sake, don’t run an .exe file to check your UPS delivery status (especially if you are not expecting a package).
I’m convinced that a strong driver of the upswing in SPP infections over the holidays (based, admittedly, on my tiny, anecdotal sampling) is simply PC users’ letting their guard down. It’s a sad commentary on today’s computing environment that you have to stay vigilant — all the time!
Happy New Year, everybody. Just remember that there are Grinches everywhere.
Devices to give Wi-Fi networks a boost
One of the common challenges of Wi-Fi is getting good coverage throughout your home or small business.
There are numerous devices for extending a Wi-Fi network, but picking the best device can be confusing.
Most of the confusion stems from terminology — different devices have different applications, but their names are often used interchangeably. For example, an access point is often thought of as an open wireless modem or router, accessed by the public. But the term is also applied to devices that supply wireless connectivity to a modem that doesn’t natively support it. “Access point” can also be used to describe a device that simply extends the range of a wireless network.
To help sort through this labeling morass, I’ll take you through the common wireless devices and software options, and I’ll describe how each can help get you a better Wi-Fi signal.
Bridges, boosters, access points, and more
The typical home or small-business net is made up of various devices performing one or more tasks. To make things more confusing, a single device can play different roles in a network, depending on how it’s configured. Here are some key elements in a small network:
- Wireless bridge: This device provides a link between wired and wireless network segments. In a small network, the bridge is built into the router, which typically has both a wireless transmitter and Ethernet ports. In corporate/enterprise applications, wireless bridges can be standalone devices used to divide a large network into segments for better management.
Windows has a built-in bridging option that lets you link different connections through your PC. You could, for example, use the bridge to connect two PCs via an Ethernet cable, giving Internet access to both through one system’s Wi-Fi transceiver.
Setting up bridging within Windows is relatively easy. In the Control Panel, select Network and Sharing Center. Click the Change adapter settings link in the left sidebar (see Figure 1). Next, you’ll see a list of available wired and wireless connections. Select the two segments you want to bridge; right-click. Select Bridge Connections; a new listing — Network Bridge — should appear, as shown in Figure 2.

Figure 1. The Change adapter settings link takes you to a list of available network connections.

Figure 2. When two network segments are bridged in Windows, a new Network Bridge listing should appear.
- Range extender: Range extenders (also known as wireless repeaters or cascading routers) are relatively simple devices that receive Wi-Fi data and send it out exactly as received. As their name implies, extenders are excellent for expanding the range of a small network. Unlike an access point, no Ethernet cabling is needed; you just need power for the device.
There are downsides to using a range extender: they repeat everything, including interference. You might also notice a slight decrease in network performance, despite having a stronger signal. Range extenders can take some time to set up properly. Their placement is every bit as important as that of the primary router.
You can purchase a single-function, dedicated range extender, but you can also use that spare wireless router you might have sitting in the closet. A popular solution for turning an old router into a repeater is to use the open-source DD-WRT (site) firmware upgrade. DD-WRT adds new capabilities to the common router. Some versions are free, others require purchasing an activation. The site’s router database page will tell you whether your router is compatible and whether activation is needed. Keep in mind that you upgrade the firmware at your own risk.
- Access point: A wireless access point is useful when your small-network modem/router does not have wireless capabilities, the modem/router is using an older network protocol such as 802.11g, or you want to add wireless capabilities to an otherwise wired network. You attach an access point via its Ethernet port. Again, you can use a spare wireless router as an access point by turning off its DHCP server (more info).
-
Wireless booster: Wireless boosters are typically replacement antennas for your existing router. Depending on the booster, the construction of your home or office, and various other factors, inexpensive boosters can extend your Wi-Fi range up to 600 percent, according to Hawking Technology info. Larger antennas can extend a router’s range well beyond that, but at a fairly high cost. This isn’t your Pringles-can Wi-Fi antenna; boosters amplify the power of your wireless transceiver. Examples include products from Hawking Technology and Amped Wireless (site).
Wireless boosters are especially useful when you’re looking for connectivity outside the house. Your garage, for example, might not be the best place for a wireless repeater. In most cases, wireless boosters are plug-and-play — simply remove the antenna that came with the router and plug in the booster. Hawking’s products let you adjust the devices output, so you’re not giving Wi-Fi to the entire neighborhood. Also, the performance decrease associated with repeaters isn’t an issue.
Software-based Wi-Fi enhancement solutions
I’d be wary of any application that claims to boost a wireless signal. However, there are a number of apps that help you detect and analyze Wi-Fi signals. Smartphones are rapidly becoming jack-of-all-trades devices, so it should be no surprise that they make excellent tools for identifying and troubleshooting faulty network connections.
I use a free app — Wifi Analyzer for Android (site) — that reports signal strength in a given place and the amount of channel noise present on the network. If you live in an apartment or a crowded office complex, Wi-Fi interference can be a major problem. By identifying which channels any surrounding routers are occupying, you can set your router to a cleaner channel.
A few analyzers are offered for iPad and iPhone users. One popular choice is Network Analyzer Lite (site).
inSSIDer (site) is an excellent solution for Windows users who wish to analyze surrounding Wi-Fi signals from a PC. (For more on Wi-Fi analyzer tools, see the Sept. 9, 2010, Best Hardware, “Spectrum-analysis tools cure Wi-Fi headaches.”)
General tips for optimizing Wi-Fi networks
Placement of your primary router is essential to maintaining a good, consistent signal. Often, apartment complexes and Internet home-service providers have a habit of sticking routers into a closet at the far end of the home. This does get the network equipment out of sight, but it might not provide a good connection when you’re using your notebook at the other end of the house and the signal has to pass through multiple walls.
Keep your router as centrally located as possible, preferably without confining walls and doors. Also keep in mind that the electrical cables running through your home’s walls present interference, as do appliances such as microwaves and cordless phones that work within the frequencies allocated for public use. And resist the temptation to put your wireless transceiver on top of or next to your PC.
If you have an older wireless router in use, the best way to enhance your network is to upgrade to dual-band, 802.11n. “N” offers more than faster speed — it typically has better signal strength than 802.11 Versions a, b, or g. (Virtually every 802.11n router presently sold is also a/g.)
Keep your wireless router’s firmware updated. Consult your owner’s manual or online resources to find out how. A firmware update can improve connectivity and add updated security features, as noted in Fred Langa’s Dec. 13, 2012, Top Story, “Routers using WPS are intrinsically unsafe.”
Microsoft releases critical patch for IE
When there’s an out-of-cycle update from Microsoft, it’s almost always one we want to install quickly.
This special edition of Patch Watch has two critical fixes that should be added to Windows workstations without delay.
MS13-008 (2799329)
Critical zero-day patch for Internet Explorer
In the Jan. 10 Patch Watch, I recommended that Internet Explorer 6, 7, or 8 users install fixit 50971 to block a new exploit that’s already attacking PCs. At that time, there was no patch available. But there is now; this past Monday, Microsoft released an out-of-cycle patch, KB 2799329, rated critical for all client versions of Windows using IE 6 through 8. PCs running IE 9 and 10 are unaffected.
An important note: According to the FAQ in MS Security Bulletin MS13-008, cumulative update KB 2761465 (MS12-077) must be installed before installing KB 2799329. In Windows Update, click the View update history link, look for KB 2761465, and confirm it’s on your system.
 What to do: Install KB 2799329 (MS13-008 ) as soon as possible. If you installed fixit 50971, remove it after installing the patch by running its companion fixit: 50972. Removing it should restore any lost browser speed you might have encountered.
What to do: Install KB 2799329 (MS13-008 ) as soon as possible. If you installed fixit 50971, remove it after installing the patch by running its companion fixit: 50972. Removing it should restore any lost browser speed you might have encountered.
Java: Use it if you must; lose it if you can
Like browsers, Java is one of those apps you really need to keep updated. But, unlike a browser, you might be better off living without Java. So before installing Java 7 Update 11, consider whether any of your applications or computing tasks needs Java to run. If you’re not sure, uninstall Java completely from your Windows workstation and see whether anything breaks.
In some cases, you can keep Java on your system but disable it in your browser. An easy way to do this is through the Java Control Panel, which should reside in your Windows Control Panel. If you don’t see Java’s control panel, it’s because you’re not running Java 7 Update 10 or 11. Proceed to the Oracle Java download page and install Version 7 Update 11. Be sure to untick any offered — but unwanted — accessory apps, such as the McAfee security software Oracle tried to foist on me.
Now go into the Java control panel and look for the Security tab. Initially, it appeared incomplete (see Figure 1) in my Java control panel because I had both Java 7 Update 9 and Java 7 Update 11 installed. Once I removed Java Update 9, the complete security tab appeared, as shown in Figure 2.
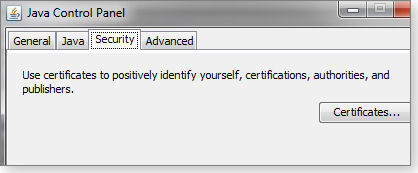
Figure 1. My Java Security tab as it appeared when I had Updates 9 and 11 installed
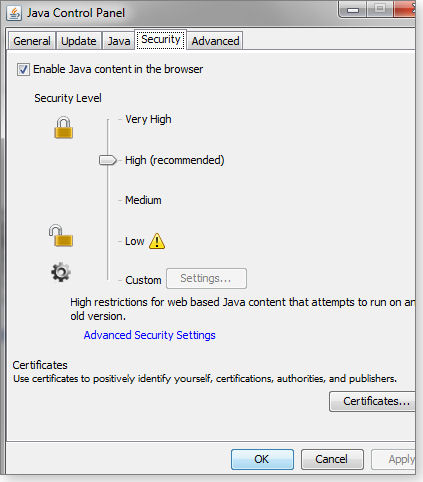
Figure 2. The complete Java Security tab with a check box at the top for enabling or disabling Java in browsers
At the top of the Java Security section is a check box labeled “Enable Java content in the browser.” Make sure it’s unchecked and click Okay. According to the Java help page, “How do I disable Java in my web browser?,” unchecking the box disables Java in all installed browsers. (That page has other useful links for managing Java.)
Oracle released Java Update 11 in response to a zero-day threat. But the patch ensures only that the Security Level in the Java control panel is set to high. It doesn’t really fix the root cause of Java’s overall security problems. Again, see whether you can live without it.
 What to do: If you must run Java, check your installed version and download (site) Java 7 Update 11 if you don’t already have it. If you still have earlier versions of Java installed, now’s a good time to remove them.
What to do: If you must run Java, check your installed version and download (site) Java 7 Update 11 if you don’t already have it. If you still have earlier versions of Java installed, now’s a good time to remove them.
Regularly updated problem-patch chart
This table provides the status of problem patches reported in previous Patch Watch columns. Patches listed below as safe to install will be removed from the next updated table. For Microsoft’s list of recently released patches, go to the MS Safety & Security Center PC Security page.
| Patch | Released | Description | Status |
|---|---|---|---|
| 2553272 | 08-14 | Office 2010 stability/performance fixes (status change) | Skip |
| 2598289 | 08-14 | Office 2010 stability/performance fixes (status change) | Skip |
| 2592687 | 10-23 | Windows RDP 8.0 update for Win7 SP1 | Skip |
| 2574819 | 10-23 | Adds DTLS support to Win7 SP1 | Skip |
| 2750841 | 11-13 | MS/OpenDNS IPv6 conflict | Skip |
| 931125 | 12-11 | Root certificates | Skip |
| 2506143 | 12-11 | PowerShell 3 | Skip |
| 2779562 | 12-11 | Time-zone fix | Skip |
| 2735855 | 09-11 | Windows Filtering Platform: Potential third-party firewall impact | Wait |
| 2553402 | 10-09 | MS FAST Search Server 2010 for SharePoint SP1 | Wait |
| 2731771 | 10-09 | Time-zone conversion | Wait |
| 2739159 | 10-09 | Windows 7 encryption | Wait |
| 2754849 | 10-09 | SQL Server; see MS12-070 for complete patch list | Wait |
| 2756822 | 10-09 | Cumulative time-zone update | Wait |
| 2745030 | 11-13 | .NET updates; see MS12-074 for complete patch list | Wait |
| 2769324 | 01-08 | Numerous .NET updates; see MS13-004 for complete patch list | Wait |
| 2769327 | 01-08 | .NET updates; see MS13-007 for complete list | Wait |
| 2647753 | 10-09 | Printing core components — timestamp reissue | Optional |
| 2732487 | 10-09 | Segoe font — timestamp reissue | Optional |
| 2770816 | 10-23 | Install only if KB 2756872 fails; check MS Support site for details | Optional |
| 2753842 | 12-11 | Windows kernel; also KB 2779030 | Install |
| 2758857 | 12-11 | Unicode file names | Install |
| 2760410 | 12-11 | Word 2010 | Install |
| 2760416 | 12-11 | Office Compatibility Pack (might be offered) | Install |
| 2760421 | 12-11 | Word 2007 | Install |
| 2760497 | 12-11 | Word 2003 | Install |
| 2761465 | 12-11 | Internet Explorer cumulative update | Install |
| 2770660 | 12-11 | DirectPlay | Install |
| 2756145 | 01-08 | XML Core Services; see MS13-002 for compete patch list | Install |
| 2769369 | 01-08 | Print Spooler for Windows 7 | Install |
| 2778930 | 01-08 | Kernel-Mode | Install |
| 2785220 | 01-08 | Secure Sockets Layer Version 3 | Install |
| 2799329 | 01-14 | Critical out-of-cycle IE update | Install |
Status recommendations: Skip — patch not needed; Hold — do not install until its problems are resolved; Wait — hold off temporarily while the patch is tested; Optional — not critical, use if wanted; Install — OK to apply.
Publisher: AskWoody LLC (woody@askwoody.com); editor: Tracey Capen (editor@askwoody.com).
Trademarks: Microsoft and Windows are registered trademarks of Microsoft Corporation. AskWoody, Windows Secrets Newsletter, WindowsSecrets.com, WinFind, Windows Gizmos, Security Baseline, Perimeter Scan, Wacky Web Week, the Windows Secrets Logo Design (W, S or road, and Star), and the slogan Everything Microsoft Forgot to Mention all are trademarks and service marks of AskWoody LLC. All other marks are the trademarks or service marks of their respective owners.
Your email subscription:
- Subscription help: customersupport@askwoody.com
Copyright © 2025 AskWoody LLC, All rights reserved.

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Attack on LexisNexis Risk Solutions exposes data on 300k +
by
Nibbled To Death By Ducks
2 hours, 20 minutes ago -
Windows 11 Insider Preview build 26200.5622 released to DEV
by
joep517
8 hours, 11 minutes ago -
Windows 11 Insider Preview build 26120.4230 (24H2) released to BETA
by
joep517
8 hours, 13 minutes ago -
MS Excel 2019 Now Prompts to Back Up With OneDrive
by
lmacri
11 hours, 19 minutes ago -
Firefox 139
by
Charlie
10 hours, 35 minutes ago -
Who knows what?
by
Will Fastie
3 hours, 18 minutes ago -
My top ten underappreciated features in Office
by
Peter Deegan
8 hours, 56 minutes ago -
WAU Manager — It’s your computer, you are in charge!
by
Deanna McElveen
3 hours, 20 minutes ago -
Misbehaving devices
by
Susan Bradley
11 hours, 4 minutes ago -
.NET 8.0 Desktop Runtime (v8.0.16) – Windows x86 Installer
by
WSmeyerbos
1 day, 14 hours ago -
Neowin poll : What do you plan to do on Windows 10 EOS
by
Alex5723
8 hours, 22 minutes ago -
May 31, 2025—KB5062170 (OS Builds 22621.5415 and 22631.5415 Out-of-band
by
Alex5723
1 day, 13 hours ago -
Discover the Best AI Tools for Everything
by
Alex5723
12 hours, 39 minutes ago -
Edge Seems To Be Gaining Weight
by
bbearren
1 day, 3 hours ago -
Rufus is available from the MSFT Store
by
PL1
1 day, 11 hours ago -
Microsoft : Ending USB-C® Port Confusion
by
Alex5723
2 days, 14 hours ago -
KB5061768 update for Intel vPro processor
by
drmark
14 hours, 26 minutes ago -
Outlook 365 classic has exhausted all shared resources
by
drmark
13 hours, 8 minutes ago -
My Simple Word 2010 Macro Is Not Working
by
mbennett555
2 days, 10 hours ago -
Office gets current release
by
Susan Bradley
2 days, 13 hours ago -
FBI: Still Using One of These Old Routers? It’s Vulnerable to Hackers
by
Alex5723
4 days, 3 hours ago -
Windows AI Local Only no NPU required!
by
RetiredGeek
3 days, 11 hours ago -
Stop the OneDrive defaults
by
CWBillow
4 days, 3 hours ago -
Windows 11 Insider Preview build 27868 released to Canary
by
joep517
4 days, 13 hours ago -
X Suspends Encrypted DMs
by
Alex5723
4 days, 16 hours ago -
WSJ : My Robot and Me AI generated movie
by
Alex5723
4 days, 16 hours ago -
Botnet hacks 9,000+ ASUS routers to add persistent SSH backdoor
by
Alex5723
4 days, 16 hours ago -
OpenAI model sabotages shutdown code
by
Cybertooth
4 days, 17 hours ago -
Backup and access old e-mails after company e-mail address is terminated
by
M W Leijendekker
4 days, 5 hours ago -
Enabling Secureboot
by
ITguy
4 days, 12 hours ago
Recent blog posts
Key Links
| S | M | T | W | T | F | S |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | 6 | 7 |
| 8 | 9 | 10 | 11 | 12 | 13 | 14 |
| 15 | 16 | 17 | 18 | 19 | 20 | 21 |
| 22 | 23 | 24 | 25 | 26 | 27 | 28 |
| 29 | 30 | |||||
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.

