-
WSb1rd
AskWoody LoungerOriginally Posted by Dammer
Have since been running other scanners but have not found anything else.If things seem fine, and if you don’t have already it, this might be a good time to download MalwareBytes and do a direct install to the computer / update and do full scan. I think these two programs that I mentioned are the only two free ones, that I’m aware of that rids this thing.
Also, you did a system restore it sounds like. I just wonder if any of these variations include a time bomb, which simply means set to trigger on a certain date. I doubt it at this time, as I’ve never ready anything about that as of yet, however I did have a program that did that.
Anyhow, glad to hear it appears you got things fixed. This one can be a pain to work with.
I would seriously look at Paragon Back-up & recovery 2011 Free .It’s free and when things get really bad, it might be a good way to get things back to normal. Again, I’ve only made archives, never a restore, as I’m a big believer in Acronis TrueImage, which has saved my several times.
b1rd
-
WSb1rd
AskWoody LoungerI was able to get rid of it through SafeMode. I installed MalwareBytes from a flash drive while in SafeMode, then ran it while still in SafeMode.
Several people have had success with renaming the file from .exe to .com (renaming it, not changing the file extension) Both during the download, as well as within the programs folder.
Another option I found some place was a portable version of SuperAnti Spyware. It assigns the file a random name, and can be both downloaded directly to a flash drive, then run from it as well. I would still suggest running either in Safemode, or if you can boot, then hit Run> type msconfig and select diagnostic start up, which is basically the same, just easier to get to on many systems.
Edit:
I did do some quick checking and there were a couple people saying not to start this in Safemode, but did not indicate why. They suggested to bring up the task manager Run > msconfig and get to the start up tab ASAP, and quickly uncheck it if you can find it. Personally, I’ve removed several of these, however different variations, and that has never worked for me. Also, I can’t see why running the fix in Safemode would be any problem at all.
-
WSb1rd
AskWoody LoungerMalwarebytes is available in a free version. There is no need to pay for it, unless you want the frilly, fancy, unnecessary features of the paid version.
I think he was referring to the “real-time” protection aspect and perhaps the automated updates, thus blocking the problem rather than trying to fix it.
COMODO is decent, however it’s only a snapshot. Also, it does insert itself into the Master Boot Record, so if there’s a problem with it- that can be a problem (However I do use it with no problems)
Another FREE option is PargaonBackup & Recovery 2011 (Advanced) Free It’s a free mirroring program in the event you can’t boot. (You need to make an ISO image media which the initial installation will prompt you to do)
I have made several archives, however I have yet to try and restore my system using this program, so I have no comments on that part. I did see it received decent ratings though. Also, if you can boot, you can still use the restore feature without the boot media, but remember it will bring your entire system back to the date of the archive, thus taking away anything you’ve saved as of that time period.
Personally, I use COMODO / TrueImage / and Paragon to back things up.
Paragon is defaulted to save the archive on the main drive, but I would suggest saving it to an external drive (Or another internal dive if you have one) if possible, to reduce the chances of a corrupted archive file, not to mention the longer defrag lag time on a the main drive as well.
b1rd
-
WSb1rd
AskWoody Lounger…but to bring up Task Manager and kill the current browser session
Thanks, that’s been my practice too.
In fact, this popped up on my personal computer just last week. Pretty impressive UI, however I was already familiar with this, and I have two internal hard drives, which this one failed to imitate.
I might add that this was the initial page that showed up, unlike what Fred Langa had, so I’m guessing it’s a different variation. This was an actual screen shot I took prior to shutting down the browser.
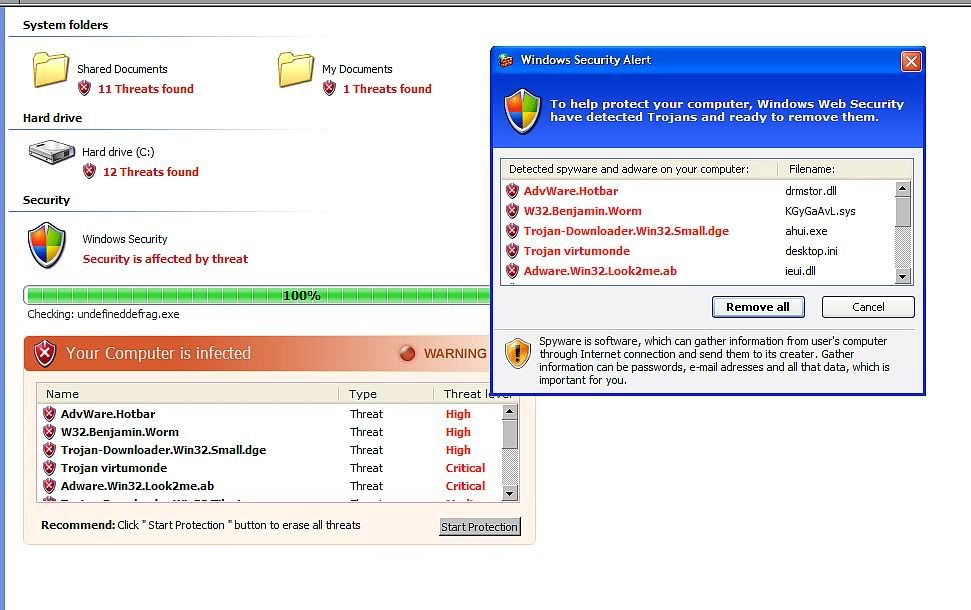
-
WSb1rd
AskWoody LoungerI actually sent the editor a letter asking the same, and I was directed to come here to post.
Also I’m new, so I also wanted to say hello!
PS- I already tried to post this, but I’m not sure if it needs to go through a moderator first, so if this a repeat, my apologies.
Regards,
b1rdMy letter:
Hi, and thanks for taking the time to read this.
I was reading Fred Langa’s article about the “LizaMoon” infection in the Windows Secrets Newsletter • Issue 283 and I noted he made the below statement, and I was wondering about a possible problem with this.
“Typically, when you encounter any suspicious webpage dialog, the correct procedure is to immediately dismiss it via the red-X close box in the upper-right corner of the dialog box or to simply close the browser. (If needed, you also can use Windows’ Task Manager to kill offending software or its processes.)”
I’ve always been under the impression that these types of rouge malware should be closed, via right-clicking the tab on the taskbar, or bringing up the Task Manager and closing the entire browser. I’m not sure if he meant close the page via the red X on the browser, or on the rouge dialog box itself.
The reason I’m asking is that is it not possible that the programmer has the ability to create the user interface so that anywhere that one clicks on it actually initiates the install command? I don’t know enough about programming, but I can’t see why the install command can’t be disguised as a red X.
Also, I’ve removed a few of these from some computers. (Different variations, but the same type of scare tactic) The last one I did for a friend would not even allow me to install MalwareBytes from a flash drive and disabled his ability to go online. I was finally able to install MalwareBytes through SafeMode, then scanned it and everything was eventually fixed.
Thanks, and thanks for a great newsletter.

|
Patch reliability is unclear, but widespread attacks make patching prudent. Go ahead and patch, but watch out for potential problems. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Dev runs Windows 11 ARM on an iPad Air M2
by
Alex5723
22 minutes ago -
MS-DEFCON 3: Cleanup time
by
Susan Bradley
17 seconds ago -
KB5056686 (.NET v8.0.15) Delivered Twice in April 2025
by
lmacri
2 hours, 58 minutes ago -
How to enable Extended Security Maintenance on Ubuntu 20.04 LTS before it dies
by
Alex5723
11 hours, 36 minutes ago -
Windows 11 Insider Preview build 26200.5562 released to DEV
by
joep517
15 hours, 34 minutes ago -
Windows 11 Insider Preview build 26120.3872 (24H2) released to BETA
by
joep517
15 hours, 36 minutes ago -
Unable to eject external hard drives
by
Robertos42
15 hours, 12 minutes ago -
Saying goodbye to not-so-great technology
by
Susan Bradley
8 hours, 53 minutes ago -
Tech I don’t miss, and some I do
by
Will Fastie
3 hours, 30 minutes ago -
Synology limits hard drives
by
Susan Bradley
1 day, 19 hours ago -
Links from Microsoft 365 and from WhatsApp not working
by
rog7
22 hours, 13 minutes ago -
WhatsApp Security Advisories CVE-2025-30401
by
Alex5723
2 days, 1 hour ago -
Upgrade Sequence
by
doneager
1 day, 19 hours ago -
Chrome extensions with 6 million installs have hidden tracking code
by
Nibbled To Death By Ducks
47 minutes ago -
Uninstall “New Outlook” before installing 2024 Home & Business?
by
Tex265
18 hours, 1 minute ago -
The incredible shrinking desktop icons
by
Thumper
2 days, 22 hours ago -
Windows 11 Insider Preview Build 22635.520 (23H2) released to BETA
by
joep517
3 days ago -
Connecting hard drive on USB 3.2 freezes File Explorer & Disk Management
by
WSJMGatehouse
1 day, 19 hours ago -
Shellbag Analyser & Cleaner Update
by
Microfix
1 day, 9 hours ago -
CISA warns of increased breach risks following Oracle Cloud leak
by
Nibbled To Death By Ducks
3 days, 9 hours ago -
Outlook 2024 two sent from email addresses
by
Kathy Stevens
2 days, 14 hours ago -
Speeding up 11’s search
by
Susan Bradley
22 hours, 3 minutes ago -
HP Pavilion Will Not Wake Up After Being Idle for Longer Period
by
WSwalterwood44
1 day, 10 hours ago -
Make a Windows 11 Local Account Passwordless
by
Drcard:))
3 days, 23 hours ago -
Ubuntu 25.04 (Plucky Puffin)
by
Alex5723
4 days, 7 hours ago -
24H2 fixed??
by
CWBillow
2 days, 23 hours ago -
Uninstalr Updates
by
jv16
4 days, 12 hours ago -
Apple zero days for April
by
Susan Bradley
9 hours, 6 minutes ago -
CVE program gets last-minute funding from CISA – and maybe a new home
by
Nibbled To Death By Ducks
3 days, 10 hours ago -
Whistleblower describes DOGE IT dept rumpus at America’s labor watchdog
by
Nibbled To Death By Ducks
5 days, 11 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.
