-
RDRguy
AskWoody Lounger@PKCano @Kirsty @ViperJohn @RetiredGeek @SusanBradley
All, I’ve updated one of my Win7 64Bit systems with the original release Jun 2018 Security Only (KB4284867) & IE11 Cumulative (KB4230450) updates on Jun 12th and all seemed well until today.
I finally experimented with Microsoft’s newly updated Speculation Control Validation PowerShell Script version 1.0.8 to see how my previously hacked i7-990x BIOS CPU Microcode update fares with Spectre Variant 4.
Microsoft Speculation Control Validation PowerShell Script version:
1.0.8 (Current version)
Added support for querying Speculative Store Bypass Disable (SSBD) settinghttps://gallery.technet.microsoft.com/scriptcenter/Speculation-Control-e36f0050
However, since updating the Win7 (Ultimate – x64) system with the Jun 2018 Security Only (KB4284867) & IE11 Cumulative (KB4230450) updates, the PowerShell scrip fails during the “Import-Module” command. This now also occurs with the previous 1.0.7 script version which just last week ran successfully. Same results when running either PowerShell 64 Bit or 32 Bit on the 64 Bit system.
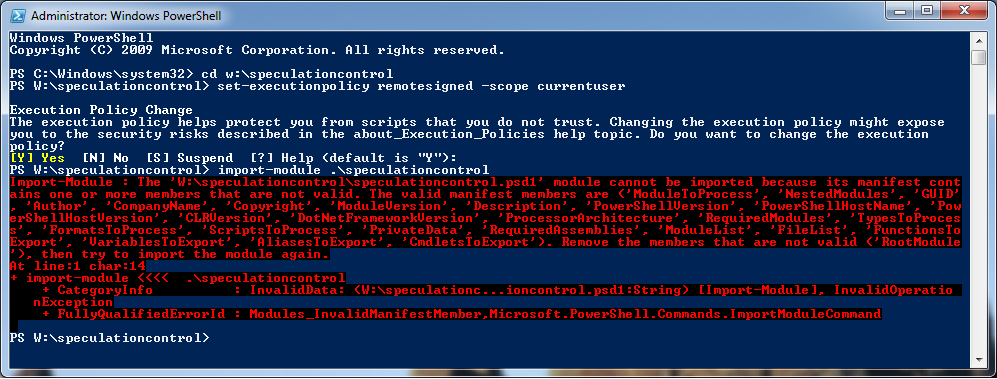
Original as downloaded from Microsoft, PowerShell Script failure indication:
Essentially during script import, PowerShell complains about:
“… module cannot be imported because its manifest contains one or more members that are not valid … Remove the members that are not valid (‘RootModule’), then try to import the module again.”
When running both versions of the script on the same Win7 (Ultimate – x64) system without the Jun 2018 Security Only update, both script versions import and run as expected.
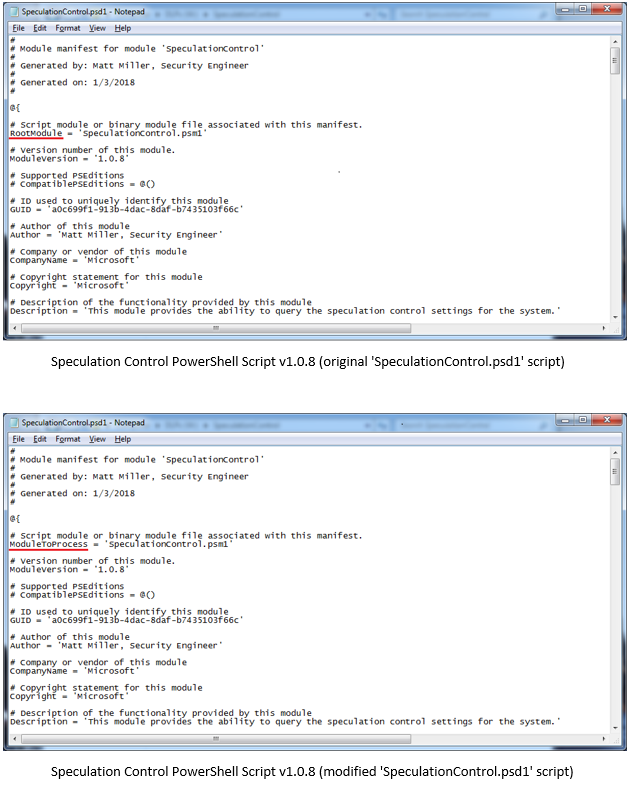
It would seem that the Jun 2018 Security Only update includes an undocumented change to Win7’s PowerShell in which it no longer recognizes the ‘RootModule’ member nomenclature.
I’ve found that by changing the ‘RootModule’ member nomenclature to ‘ModuleToProcess’ nomenclature, all is well again and both script versions run successfully on the system updated with the Jun 2018 Security Only (KB4284867) update.
Script modification edits shown below:
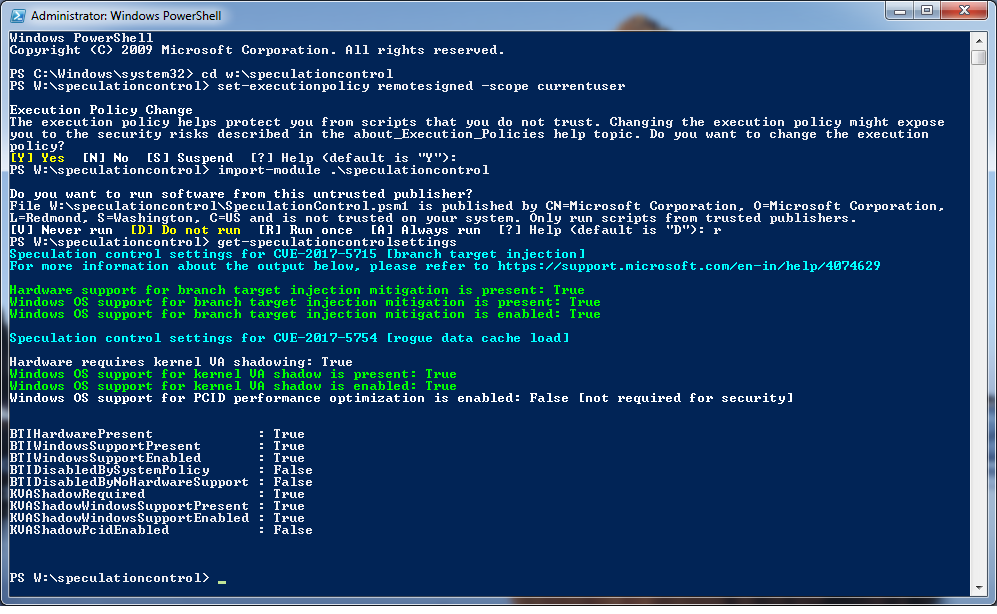
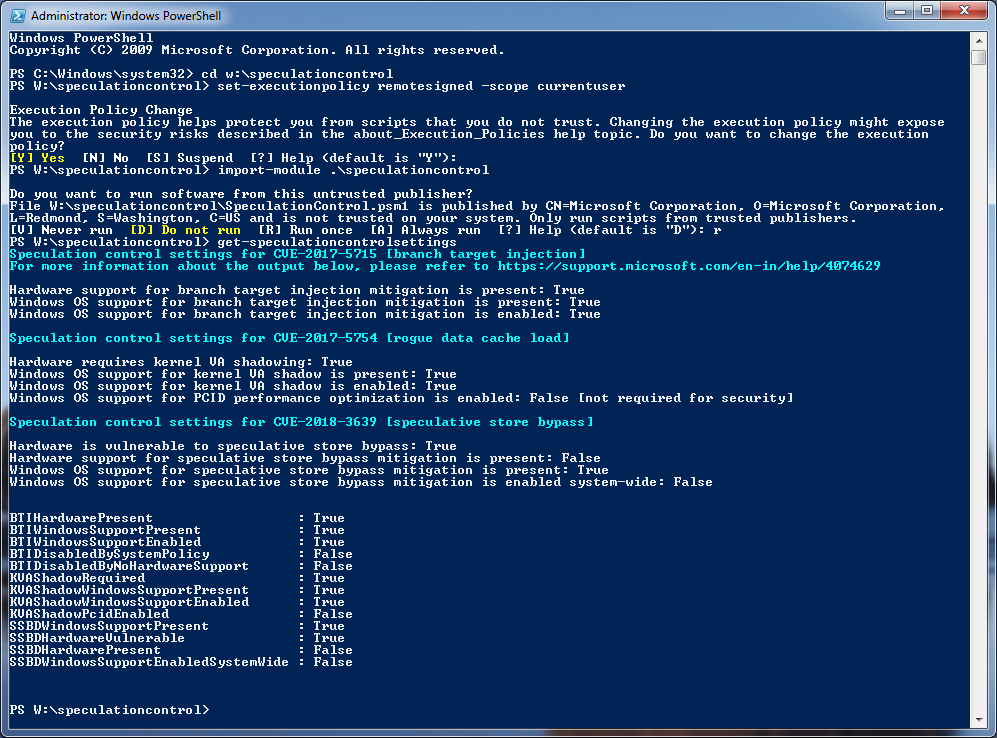
After script version 1.0.7 modification, results are:
After script version 1.0.8 modification, results are:
Not sure if this new PowerShell characteristic / feature also applies to the Jun 2018 Win7 Roll-up, Win8.1 Security Only / Roll-up or Win10 or 32Bit versions of Win7 but it sure looks like another bug put into the Win7 security update cycle for us Win10 “obstructionists”.
Now, just how many of us Win7 users are out there using PowerShell scripts and just how many of our scripts use the ‘RootModule’ member nomenclature that now fail? Luckily, I’ve only got a few.
Lastly, the latest updated CPUID 206C2 version “0x1E” CPU Microcode does not contain the required SSBD CPU Microcode update for Spectre Variant 4 so it looks like I’m waiting for either HP or Dell to release an updated BIOS for their XEON x5600 series systems.
Win7 Group B (Ultimate & Pro) [x64 & x86]
MSOffice Pro Plus 2010 SP2 (x86 Perpetual)
MSOffice Pro Plus 2013 SP1 (x64 Perpetual)
RDRguyEDIT—————-
Running GRC’s Inspectre version #8 works the same for me on Win7 Ultimate SP1 64Bit pre & post Jun 2018 Security Only update (KB4284867) so maybe there’s a new Win10 problem as noted above by @ViperJohn in post #197747.However, I do expect Steve to update his marvelous tool to add Spectre Variant 3a & 4 protection detection capability once he gets a chance to do so.
Win7 - PRO & Ultimate, x64 & x86
Win8.1 - PRO, x64 & x86
Groups A, B & ABS2 users thanked author for this post.
-
RDRguy
AskWoody LoungerJune 3, 2018 at 12:17 am in reply to: MS-DEFCON 3: Time to patch, but be aware of Network-busting bugs in Win7 #195673+1
Win7 - PRO & Ultimate, x64 & x86
Win8.1 - PRO, x64 & x86
Groups A, B & ABS -
RDRguy
AskWoody LoungerJune 3, 2018 at 12:16 am in reply to: MS-DEFCON 3: Time to patch, but be aware of Network-busting bugs in Win7 #195672Just finished installing May Win7 (Group B) & IE11 updates, system restart then followed up with Windows Update for .Net, MSRT, Windows Defender & MSOffice 2010 & 2013 updates on all my systems … no issues what-so-ever, all system NICs are Good-To-Go.
Win7 Group B (Ultimate & Pro) [x64 & x86]
MSOffice Pro Plus 2010 SP2(x86 Perpetual)
MSOffice Pro Plus 2013 SP1(x64 Perpetual)
RDRguyWin7 - PRO & Ultimate, x64 & x86
Win8.1 - PRO, x64 & x86
Groups A, B & ABS -
RDRguy
AskWoody LoungerMay 29, 2018 at 3:21 pm in reply to: Comments on AKB 2000003: Ongoing list of "Group B" monthly updates for Win7 and 8.1 #195045Seeing as we have probably 19 more months of Win7 Group B security-only patches & 55 more months of Win8.1 Group B security-only patches coming from MSFT, might I suggest splitting AKB 2000003 into separate AKBs, 1 for Win7 & another for Win8.1?
As it is now, it will only keep getting larger and may eventually grow too big to keep together in a single post. Once support for Win7 stops in 2020, it would make more sense to separate out Win8.1 and why wait until it gets larger to do it?
No real necessity to do it now but either way, I find this AKB to be extremely valuable especially to those who perform clean installs and wish to remain in Group B and I thank you all for keeping this AKB updated.
Thank you.
Group B / Win7 (Ultimate & Pro) [x64 & x86]
RDRguyWin7 - PRO & Ultimate, x64 & x86
Win8.1 - PRO, x64 & x86
Groups A, B & ABS1 user thanked author for this post.
-
RDRguy
AskWoody LoungerFYI, I’ve always downloaded CCleaner from their “builds” page …
https://www.ccleaner.com/ccleaner/builds
What I’ve noticed is whenever Piriform releases a new build, it can take anywhere from a couple of days to a week or so before the portable & slim builds become available for download.
By the way, the same thing goes for their portable versions of Speccy, Recuva, & Defraggler …
https://www.ccleaner.com/speccy/builds
https://www.ccleaner.com/recuva/builds
https://www.ccleaner.com/defraggler/builds
Group B / Win7 (Ultimate & Pro) [x64 & x86]
RDRguyWin7 - PRO & Ultimate, x64 & x86
Win8.1 - PRO, x64 & x86
Groups A, B & ABS3 users thanked author for this post.
-
RDRguy
AskWoody Lounger@kmbrite
That’s great news, I’m glad to hear you had success updating your CPU microcode and Inspectre confirmation doesn’t hurt.But I would encourage you to also run the Microsoft PowerShell script to help ensure that you’re really protected.
https://gallery.technet.microsoft.com/scriptcenter/Speculation-Control-e36f0050#content
According to VMware, even though the VMware CPU Microcode Update Driver will upload the newer microcode version during boot, Windows’ Spectre mitigation check routine may run prior to the VMware driver executing it’s microcode upload payload. If this happens, I believe that you may get a false positive to Spectre mitigation being active within windows.
In other words, the CPU will have the mitigated microcode update, but windows will already be setup in such a way that it won’t use the the corresponding mitigating system calls to make use of the CPU mitigating functions.
I’m not sure exactly how Steve Gibson coded up his Inspectre tool, does he interact with the CPU microcode directly to detect Spectre mitigation functionality or does he interact with Windows to determine whether Windows is set up to use it. He might get it from Windows the same way that the PowerShell script does but I just don’t know and I have no way of asking him.
But, I do expect the PowerShell script to simply report whether or not windows is set up to use it. Then again I may be wrong there too.
If you go the the VMware CPU Microcode Update Driver website comments section and scroll down to the “Nico Weytens” posting (posted about 1 month ago), you’ll see that the VMware driver updated his CPU microcode but the PowerShell script indicated that his windows was not set up to use it. Further down responses state that in his system, the VMware engineers believe that the driver apparently ran to late in the boot sequence for windows to detect that the CPU was mitigated which it eventually was.
Because his example showed that the PowerShell script indicated that his system was not Spectre protected even though the driver indicated that the CPU microcode was updated, at this time I would tend to trust the PowerShell script result just a wee bit more than Inspectre but only because I don’t know exactly how Inspectre determines the Spectre mitigation state of the system.
In any event, you’ve come up with an alternative but similar method to Spectre Variant 2 protect “Gulftown” and that deserves a whole hardy WELL-DONE.
Thank you for sharing (and please don’t mention the trust thing to Steve).
Group B / Win 7 (Ultimate & Pro) [x64 & x86]
RDRguyWin7 - PRO & Ultimate, x64 & x86
Win8.1 - PRO, x64 & x86
Groups A, B & ABS1 user thanked author for this post.
-
RDRguy
AskWoody LoungerMay 23, 2018 at 2:28 am in reply to: Avast and AVG blamed for bad Win10 version 1803 upgrades #193792Now everyone does realize that if MSFT got everything out the chute right each time, every time, day in and day out, for everyone and it did exactly what everyone wanted it to do and everyone knew what it did and how & why it did it whatever “IT” is, there would be no need for AskWoody.com and we wouldn’t be here amongst ourselves trying to get to know one another while we’re all here working diligently & collectively figuring this s**t out.
Therefore for the lifeblood of AskWoody.com, I say to MSFT … keep it up, we’ve got you covered, we’re more than capable of traveling the rocky, winding road you’ve sown upon us, and when we’ve completed the tasks you’ve bestowed, the world will be a much better & safer place running Linux or Mac OS, or Chrome OS or who knows maybe someday … AskWoody OS.
Aaahhh Woody, you got any time to look into this
Group B / Win7 (Ultimate & Pro) [X64 & x86]
RDRguyWin7 - PRO & Ultimate, x64 & x86
Win8.1 - PRO, x64 & x86
Groups A, B & ABS2 users thanked author for this post.
-
RDRguy
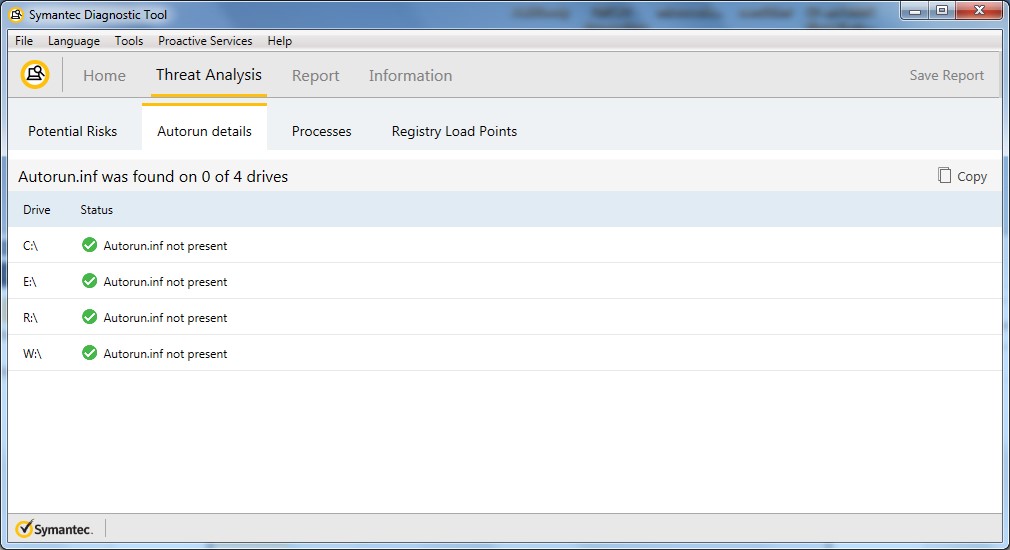
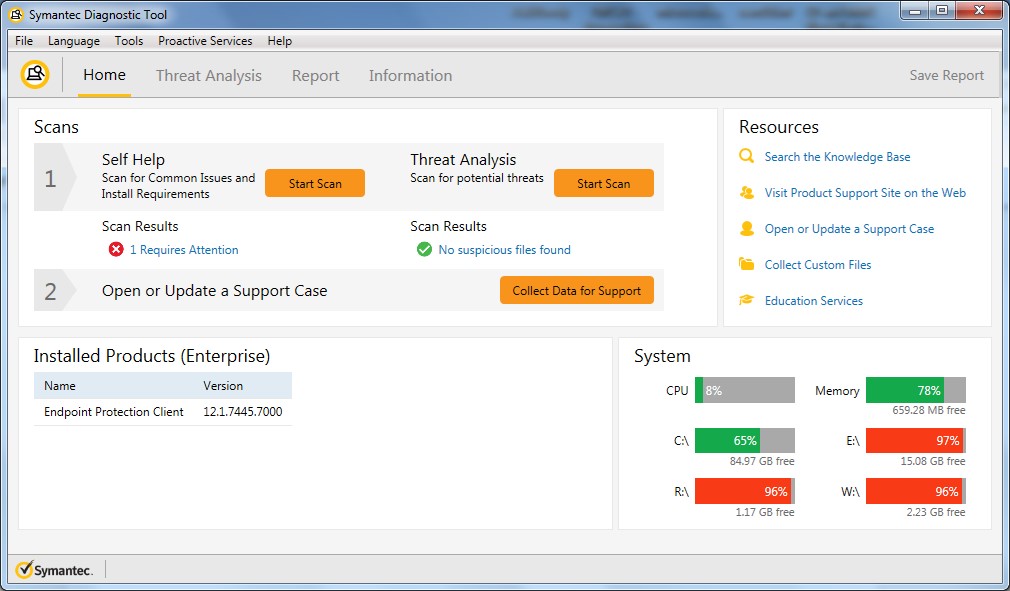
AskWoody LoungerMay 23, 2018 at 1:39 am in reply to: Avast and AVG blamed for bad Win10 version 1803 upgrades #193780Here are the SymDiag Scan Reports from above post:
Group B / Win7 (Ultimate & Pro) [x64 & x86]
RDRguyWin7 - PRO & Ultimate, x64 & x86
Win8.1 - PRO, x64 & x86
Groups A, B & ABS2 users thanked author for this post.
-
RDRguy
AskWoody LoungerMay 23, 2018 at 1:32 am in reply to: Avast and AVG blamed for bad Win10 version 1803 upgrades #193775Over the years, I’ve used several of the free anti-virus programs mentioned here & a few others including a few paid for programs & security suites & I found some to be good, some no-so good, and the rest so-so.
Not sure if my security suite of choice would be effected by this Win10 v1803 bug but I use Symantec’s Endpoint Security (SEP) Enterprise. I’ve been using this security suite for several years now on all my systems without any issues what-so-ever.
Well, there is one little issue that crops up … if you restore your system from a Windows Restore Point using System Restore, you’ll most likely need to repair the SEP installation via the control panel or you can just re-run the SEP install from it’s installation media.
I believe this problem has to do with re-synchronization of SEP’s definition sets and the program’s SymEvent and/or LiveUpdate engines. This will be detected and reported by the SymDiag tool described below if you run it. I suspect this may occur with other 3rd party anti-virus/anti-malware/firewall programs that embed themselves deeply into the Window’s environment.
Though Symantec & Norton were previously (maybe still are?) known for hogging up system resources and performance, for my setup, I find that not to be the case.
The main reason I chose SEP Enterprise vs. the similar consumer equivalent Norton Internet Security suite was due to the ability to manage network connected client internet security and client connected appliance security features on my connected laptop clients.
Though this is an enterprise endpoint security product, the client side can be installed as a stand-alone unmanaged client that allows the client administrator to control most if not all of the anti-virus, anti-malware & firewall security settings.
Unfortunately, the client side connected appliance security (i.e USB, CD, DVD, etc.) connection policies are only available if the client is set up a a managed client, not an unmanaged one. Not all security suites do this anyway so no real loss here.
As an unmanaged client though, SEP performance is quite similar to if not exactly the same as Norton Internet Security. And SEP’s cost per license is comparable to if not less than Norton’s if you get the 3 year support option (~ $32.50 per/yr/license).
Symantec Endpoint Protection 14 … Main Webpage
https://www.symantec.com/products/endpoint-protectionSymantec Endpoint Protection 14 … Datasheet
https://www.symantec.com/content/dam/symantec/docs/data-sheets/endpoint-protection-14-en.pdfI also perform monthly manual scans using these other free products: Malwarebytes, Windows Defender (auto scan disabled), Norton Power Eraser, Microsoft Safety Scanner (thank you kindly Patch-Lady) & Symantec’s Diagnostic Scan Tool. I do this just before performing monthly full system backups.
Except for an occasional “PUP” detected by Malwarebytes (must be those occasional hacking sites I download from), the rest of the scans come up … Good-To-Go nothing found.
The Symantec Diagnostic Tool (SymDiag.exe) is mainly a support tool to verify & detect system issues that may prevent SEP or other Symantec products from installing on your system. If SEP or other Symantec products are installed, it verifies installation integrity and displays problems if any are found.
However, SymDiag can also perform a complete & thorough threat scan of your entire system and generates / displays several scan report results. It does need internet connectivity to Symantec’s online file reputation database to validate the file hashes it collects/generates.
It runs relatively quickly but dependent upon your system, it may take 5-15 min, more if you scan every file on every active drive/partition within your system when you perform the scan.
I don’t know if it has the ability to scan network connected drives (i.e. NAS) as I don’t have one and I haven’t used the tool to scan files through the network on network connected clients as I prefer to do this locally on the client – it may work but I’ve never done it.
But, the best part … it’s a totally free download from Symantec. I would definitely consider adding this to your free anti-virus/anti-malware manual scan tools tool chest.
I’m not sure if the threat scan function is available if you don’t have SEP or another Symantec product installed. If any of you try this out, please reply so that I and others know – thanks.
SymDiag … Description
https://support.symantec.com/en_US/article.TECH215550.htmlSymDiag … Running a Threat Analysis Scan
https://support.symantec.com/en_US/article.TECH215519.htmlSymDiag … Download / Release Notes
https://support.symantec.com/en_US/article.TECH170752.html#newPlease see next post for SymDiag Scan Report displays … (limited file attachment)
By the way, SEP is available for Linux & Mac too though not sure about the SymDiag tool.
Group B / Win7 (Ultimate & Pro) [x64 & x86]
RDRguyWin7 - PRO & Ultimate, x64 & x86
Win8.1 - PRO, x64 & x86
Groups A, B & ABS5 users thanked author for this post.
-
RDRguy
AskWoody Lounger@Bill C.
I did a bit of poking around and this is what I’ve found – some potentially good news, some bad, and some hope. Feel free to repeat my path via enclosed links if you like.Intel’s Microcode Revision Guidance dated March 6 2018 lists the Bloomfield i7-960 Production Status “Pre-Beta” & Pre-Mitigation Production MCU is “0x1B” as seen here:
https://newsroom.intel.com/wp-content/uploads/sites/11/2018/03/microcode-update-guidance.pdfIntel’s Microcode Revision Guidance dated April 2 2018, states that Production Status for Bloomfield is “Stopped” & again Pre-Mitigation Production MCU is “0x1B” as seen here:
https://newsroom.intel.com/wp-content/uploads/sites/11/2018/04/microcode-update-guidance.pdfCPUID 106A5 is the CPUID for some i7 Bloomfield (920, 930, 950, 960, 975) & Xeon Bloomfield thereby they use the same CPU microcode. Some early versions of i7 Bloomfield (920, 940, 965) are CPUID 106A4 while CPUID 206C2 are the Gulftown CPUs (970, 980, 980x, 990x).
It should be noted that, CPUs i7-920, 930, 950, 960 & 975 are listed as CPUID 106A5 in the Mar 6 Intel Microcode Revision Guidance but they are listed as 106A4 in the Apr 2 revision.
I believe this is an error in the Apr 2 guidance as various other CPU websites list these as CPUID 106A5. I suspect the CPUIDs in the 2 adjacent Bloomfield rows were accidentally swapped probably because there are 2 versions of the i7-920.
Good 3rd party website for AMD & Intel CPU stats: (once there, search for i7-960)
http://www.cpu-world.com/index.htmlThis can also be confirmed on your system using GRC’s Revision #8 “Inspectre” tool or several other CPUID identification utilities like HWiNFO, CPUID, CPU-Z, etc. all available on-line for free download.
In any event, though not publicly released, Intel has indeed updated the CPUID 106A5 microcode to version “0x1C” with a date of 2018-01-24, (your i7-960 is CPUID 106A5) and “officially” released it to some OEMs like HP & Dell which they in turn released updated BIOS to their customers available for download from their websites.
The BIOS version 3.61A dated Mar 6, 2018 update file sp84161.exe that I’ve downloaded from HP for the Z400 system contains the 106A5 updated “0x1C” version.
https://support.hp.com/us-en/drivers/selfservice/swdetails/hp-z400-workstation/3718668/swItemId/wk-207274-1The Dell PowerEdge 610’s (likely others) BIOS version 6.5.0 dated Mar 20, 2018 update file “R610_BIOS_60HK9_WN64_6.5.0.EXE” also contains the updated CPU microcodes for CPUIDs 106A5 & 206C2.
http://www.dell.com/support/home/us/en/04/drivers/driversdetails?driverId=60HK9If you’re curious, you can download the HP and/or Dell BIOS update files, 7-Zip to extract the HP or Dell BIOS update files & the MC Microcode Extractor tool to extract the updated Intel CPU microcodes from the extracted OEM BIOS files and follow my previous post for steps I used and you can extract them for verification.
7-Zip v18.05 … a very good Zipping / Un-Zipping tool (does install in Windows)
https://www.7-zip.org/MC Extractor v1.16.3 r66 … compiled & ready to run in Windows (it does not install)
https://github.com/platomav/MCExtractor/releasesI believe this means that, unlike shown in Intel’s last Microcode Revision Guidance of Apr 2nd, Intel has mitigated & released (at least to some OEM system vendors) updated microcodes for some i7 Bloomfield, Xeon Bloomfield, Gulftown, and Westmere-EP & WS processors.
Unfortunately, unless Intel also releases these 106A5 & 206C2 updates to MSFT and they in turn release them as a Windows update to the Intel Microcode update file “mcupdate_GenuineIntel.dll” located in the c:\Windows\System32 directory which is run at Windows boot, and the sparse not-so-easy-to-use tools to hack the DX58SO2’s Phoenix BIOS like I hacked mine, it would seem to be a bit difficult to proceed further at this time.
So, here are your options as I see them today:
Wait for Intel and/or MSFT to provide an official update for your i7-960/motherboard … may or may not ever happen, let’s hope it does
Attempt the CPU microcode replacement hack … your DX58SO2 board’s BIOS is based on Phoenix BIOS – few BIOS tools available & those found are hard to use and may not work as expected (in some cases). See links below:
BIOS ID / BIOS Developer identification website: (scroll down and look for BIOS SOX5820J-86A or BOARD DX58SO2 – your board is near bottom of page)
https://www.wimsbios.com/intelphoenixbiosids.jspSome Phoenix BIOS CPU microcode hacking directions & tools:
https://www.win-raid.com/t2811f47-Guide-How-to-update-CPU-microcodes-NCPUCODE-BIN-CPUCODE-BIN-on-a-non-UEFI-Award-Phoenix-BIOS.htmlThis may help some but its set up for LGA 771 & 775 not your LGA 1366 board though tools & steps should be the same:
https://www.delidded.com/how-to-update-cpu-microcode-in-award-or-phoenix-bios/However, there’s another potentially good option to consider:
Upgrade your i7 Bloomfield to a Westmere-EP Xeon. I know this sounds like a stretch but if you follow the breadcrumbs below you’ll see that you might end up with some additional advantages.
First run Intel® Desktop Compatibility Tool links listed here:
http://processormatch.intel.com/
http://processormatch.intel.com/MotherBoards/Index/
http://processormatch.intel.com/MotherBoards/ByChipSetName?chipSetName=X58
http://processormatch.intel.com/Processors/CompatibleProcessors?componentName=DX58SO2You’ll notice that, per Intel’s Desktop Compatibility Tool (last link above), the DX58SO2 supports the i7-990x which is a “Gulftown” CPU … CPUID 206C2. I’ll explain below why this is important later below.
Next, let’s look at when the i7-990x was first supported. Click on the i7-990x CPU selection. You’ll notice that the i7-990x CPU has been supported since BIOS version 603. Clicking on the 603 BIOS version this takes you to Intel’s website here:
https://downloadcenter.intel.com/product/50242Now double clicking on “BIOS Update [SOX5820J.86A] takes you here:
https://downloadcenter.intel.com/download/23054/BIOS-Update-SOX5820J-86A-?product=50242Then clicking on Release Notes (pdf) opens up this PDF file:
https://downloadmirror.intel.com/23054/eng/SO2_0920_ReleaseNotes.pdfYou’ll notice that BIOS version 603 is the initial release BIOS for the DX58SO2 board meaning that the i7-990x has always been supported. You’ll also see that this latest BIOS version 920 added capability for “New Processor Support”.
If all the supported processors listed in the Intel Desktop Compatibility Tool have been compatible since BIOS 603, what new processors are being supported? I suspect it’s the Westmere-EP & WS Xeons as there aren’t any other 1366 processors that weren’t already supported in previous BIOS versions.
Noting your board currently supports the i7-990x is important because CPUID 206C2 is the same CPUID for both the “Gulftown” i7s and the “Westmere-EP” Xeons (i.e. 56xx series) which means your DX58SO2 board most likely also supports Westmere-EP processors which … Intel has officially finished mitigating Spectre Variant 2 microcode & officially released it (at least to some OEMs).
I’m currently planning on replacing my i7-990x with x5690 Xeon in my X58 system as many websites have confirmed this works.
If it’s publicly disclosed that it’s mitigated & released then maybe someday MSFT may be more inclined to include it, the 206C2 update, in their next Intel microcode update file “mcupdate_GenuineIntel.dll”. But then again, if they do that, they may also include the 106A5 Bloomfield as we now know that they too have been mitigated and released at least to Dell & HP. Who knows, it might happen
Though the top of the line X56xx 6-core Xeons sold new for $1600+, they’ve been discontinued and you’d be hard pressed to find any new one’s for sale now. Besides, who would spend $1600 for old tech that may not get the Spectre fix?
But, you’ll find them on Amazon for under $200 used (i.e. system pulls) and lesser 4-core versions for much less. Some sellers on Amazon list them as new but believe me they’re used. Look at seller reviews and return policies. eBay has several for a little less but I would avoid ones sold as new coming from China.
The main reason I believe Westmere-EPs are not officially listed as compatible with your X58 board is because they have additional features, mainly 2 QPI bus structures to accommodate Dual Processor capability that the X58 chipset on your DX58SO2 doesn’t support. But, these Xeons work just fine as a single processor in the dual processor 5000 series chipset boards as well as in the single processor boards using the X58 chipset.
Other FYI stuff that might be of interest …
Other additional Xeon features include: ECC memory (DX58SO2 is ECC capable) and deeper memory addressing … 288GB vs. 24GB for i7.
But unofficially, your 1st gen i7 actually supports up to 48GB if using 6 x 8GB memory. Memory specs for your board indicates that it does support 8GB memory sticks so you can upgrade to 48GB if you choose to do so. See here:
https://www.intel.com/content/www/us/en/support/articles/000006914/boards-and-kits/desktop-boards.htmlI personally know 1st gen i7’s support 48GB because they incorporate a 36 Bit memory address bus = 2^36 = 64GB. But with only 3 memory channels on your/my board, we MAX out at 48GB. I’m using 48GB in my ASUS P6T Deluxe V2 setup and there are also reports on various websites that confirm this. Here’s one:
http://wp.xin.at/archives/880I suspect when X58 chipset first came out, 8GB DDR3 memory wasn’t fully developed & readily available so it wasn’t in put the X58 board specs and we already know all about engineers revisiting “old documentation” from @Nibbles
Good primer for Westmere-EP here:
https://en.wikipedia.org/wiki/Westmere_(microarchitecture)Not-so-good (sparse info) primer for Gulftown here:
https://en.wikipedia.org/wiki/GulftownGood primer for Bloomfield here:
https://en.wikipedia.org/wiki/Bloomfield_(microprocessor)Good primer for Intel i7 Processors here:
https://en.wikipedia.org/wiki/List_of_Intel_Core_i7_microprocessorsSo it appears that all may not lost for the future of your Bloomfield i7-960 system post Spectre. If you really want to keep it going, you have some potentially viable options here to consider.
Group B / Win7 (Ultimate & Pro) [x64 & x86]
RDRguyWin7 - PRO & Ultimate, x64 & x86
Win8.1 - PRO, x64 & x86
Groups A, B & ABS4 users thanked author for this post.
-
RDRguy
AskWoody Lounger@Nibbled …
Thank you for your kind words sir, but you forgot to add “all the while starring at the brick wall ahead”Group B / Win7 (Ultimate & Pro) [x64 & x86]
RDRguyWin7 - PRO & Ultimate, x64 & x86
Win8.1 - PRO, x64 & x86
Groups A, B & ABS -
RDRguy
AskWoody Lounger@RG …
BIOS (Basic Input/Output System) can be thought of as simply a collection of file libraries consisting of modular hex data files representing either executable code and/or data that’s used to initialize (put to a known state) the hardware components of a PC or other hardware system upon power-up so that they can subsequently properly interpret software system calls (commands & responses) from a host operating system (i.e. Windows, Linux, DOS, Mac OS, etc.).Modern EFI (Extensible Firmware Interface) & UEFI (Unified Extensible Firmware Interface) moves most of the normal BIOS functions from hardware based firmware BIOS to the hard disk which allows for increased BIOS like functionality, space & features. Wikipedia is a good primer for BIOS/EFI/UEFI.
Though some system OEMs develop their own BIOS and in-house BIOS Tools, several system OEMs use BIOS OEMs (AMI, Award, Insype, Phoenix to name a few) to develop their system BIOS and various corresponding BIOS maintenance tools. It should be noted that BIOS tools from one BIOS vendor usually doesn’t work with another vendor’s BIOS structure – BIOS structures are pretty fairly unique among BIOS vendors.
Various BIOS maintenance tools are used to upload, download, customize or otherwise maintain system BIOS with custom features like system OEM’s display LOGOs, maintain (add/remove/replace) system OEM approved devices (i.e. supported CPUs, memory & other components, etc.), provide capability for fixing BIOS bugs discovered post-development/release and provide capability for other updates/improvements to the BIOS file modules.
A prime example for BIOS modification tool use would be to add BIOS support for a newly developed CPU as long as the physical & electrical characteristics of a particular motherboard also permits support of that new CPU.
In essence, this is what I’ve done. I’ve simply replaced the specific hex data file module that contains the CPU Microcode (essentially a hex data file that’s loaded at system power-up into dedicated onboard ram within the design of the CPU which is used solely to determine/modify what function(s) a particular CPU instruction will or will not perform) using a tool that was most likely developed by the BIOS OEM vendor (AMI) of my ASUS motherboard – at least I hope so
There are a lot of BIOS/EFI/UEFI programmers, technicians and other crafty hackers out there that have an intimate knowledge of the interworking’s of the various flavors of BIOS (legacy BIOS & modern EFI/UEFI) that have either bought, borrowed, stolen or developed their own BIOS tools to view / add / remove / replace / extract / inject / modify the various bits / blocks / libraries contained within a typical BIOS file.
Though some of these files/tools can be found on-line for download for free, the key is to know (or determine) which files/tools are needed, how to use them and if they’re safe & can be trusted to do no more & no less than what’s expected.
A little bit of curiosity, basic technical know-how, self-discipline and risk acceptance goes a long way and is extremely valuable and helpful if you’re modifying BIOS yourself.
“DON’T DO IT IF YOU DON’T HAVE TO” is very sound advice if you’re modifying BIOS as you can easily brick a board making it irrecoverable especially if you’re cobbling together something for the first time that may or may not be compatible – kinda like what I did.
Some motherboards do have BIOS recovery features (primarily secondary BIOS storage) but most don’t & you shouldn’t routinely depend on this feature even if you’re an expert.
If you do, it’s like driving in 4 wheel drive in the mud until you get stuck – when you do get stuck, it’s too late (though most Mud-Boggers would tend to disagree but then again, I’m fairly sure they’re not here on AskWoody). I digressed – sorry.
I know what I’ve done appears to look good on the surface, but I can’t be really say for sure that I’ll be 100% protected against a real Spectre Variant 2 attack because Intel stated publicly that they’ve stopped mitigation work on my 1st Gen i7 CPU.
Maybe as far as the CPU / Windows interface & Windows interpretation of the CPU responses go, all appears good on the surface. But, besides Intel, who really knows what’s going on inside the i7 CPU itself when paired with this version of microcode.
Before I tried my experiment, I did a ton of research on the web concerning my system & Spectre Variant 2 and my conclusion was that there was a 0% chance that Intel, ASUS or MSFT would provide the necessary Spectre Variant 2 microcode fix for my specific 1st gen i7 system.
With my system hack fix, I feel I’ve increased my chances of being Spectre protected from 0% to maybe 50-50.
But, if I stay with my system hack & swap out the i7 with a Westmere XEON (more web research), I believe my chances of protection will increase to 99+% assuming that Intel’s fix is really the 100% fix for Spectre Variant 2.
Why 99+%, because nothing is ever 100% except death & taxes and who knows what the future holds (i.e. Spectre NG ?)
Except for a simple CPU swap, I’ve potentially saved my system from the wrath of the currently published/released Spectre Variant 2 vulnerability.
Though in no way do I want to inject BIOS hacking into this forum, for those who might be just a little bit more curious, a couple of interesting websites dealing with CPU Microcode BIOS modification & tools listed are below:
http://wp.xin.at/archives/tag/microdecode … AMI BIOS & CPU Microcode specific
https://www.win-raid.com … Home page – general BIOS/UEFI/Driver modification
https://www.win-raid.com/f47-HOT-CPU-Microcode-Optimization.html … CPU Microcode topics
As best as I can determine these sites are completely safe as I’ve been visiting them for several years now and I haven’t been hit yet (fingers crossed) by any malware, unexpected hidden/backdoor downloads or infections.
Best of all, no need to join, sign-up or submit email addresses to view articles or discussions. Pretty much like AskWoody but primarily focuses discussions on problems, potential solutions ideas and modifications that relate closer to the hardware level concerning BIOS, hardware drivers, custom modifications, etc.
While I’m no expert, I feel I know just enough to give it a try but I also hope I know enough to stay out of trouble …
Group B / Win7 (Ultimate & Pro) [x64 & x86]
RDRguyWin7 - PRO & Ultimate, x64 & x86
Win8.1 - PRO, x64 & x86
Groups A, B & ABS -
RDRguy
AskWoody Lounger@nibbled …
I agree with DrBonzo, the current Dell A20 BIOS update for you system contains the Spectre Variant 2 CPU microcode fix.Also as stated by others, I believe there’s minimal risk these days if you follow your system manufacturer’s BIOS/UEFI update instructions to the letter and use the update files/tools obtained directly from your system manufacturer.
But, things can still happen during the update process that can cause the update to fail possibly rendering your system inoperable or result in other undesirable effects like system feature deletions, additions, modifications, etc.
So unless there’s some undesirable existing condition that an updated BIOS/UEFI resolves, you probably shouldn’t update unless you’re willing to except some risk.
Most importantly, NEVER interrupt the update process once started. If updating a laptop, make sure the battery has sufficient charge in case you lose power during the update process. I recommend plugging the laptop in and not performing the update if the laptop is just running on battery power.
For a desktop, it would be beneficial to run with a battery backup as risk increases if you’re in a power-loss prone situation like a major weather storm brewing, tornado, forgot to pay the electric bill
, etc.
As such, I believe the A20 BIOS/UEFI update that includes the CPU Microcode that incorporates the Spectre Variant 2 fix is warranted and worth the minimal risk. But it’s really up to you to choose when to install it.
Personally, with the recently reported discovery of 8 new variants of Spectre vulnerabilities (Spectre NG) concerning Intel (& possibly AMD) and that they (?) are working on a fix for the new vulnerabilities, I’d probably hold off updating until either there are reports of existing Spectre Variant 2 attacks detected or until Intel/AMD release a new round of CPU Microcode updates to OEMs like Dell and they intern release updates to their recently updated BIOS/UEFI files.
Or, you can use this technically desired A20 BIOS update as a practice update in preparation for the next update should that turn out to be the case. Your choice really.
Seems like Intel has taken a page out of the current MSFT playbook – update the update which updates the update to the update
Group B / Win7 (Ultimate & Pro) [x64 & x86]
RDRguyWin7 - PRO & Ultimate, x64 & x86
Win8.1 - PRO, x64 & x86
Groups A, B & ABS1 user thanked author for this post.
-
RDRguy
AskWoody LoungerWell, I’m retired so I’ve got nothing but time to research & work out Windows Update mess-ups
And I agree, the only real test to see if my method of protection against the currently disclosed Spectre vulnerabilities is to subject it to actual malicious Spectre code & see how my hacked patched system reacts.
Maybe in time, others can either confirm success or failure for this method of patching their no longer OEM supported legacy systems with Spectre mitigation.
Group B / Win7 SP1 (Ultimate & Pro) [x64 & x86]
RDRguyWin7 - PRO & Ultimate, x64 & x86
Win8.1 - PRO, x64 & x86
Groups A, B & ABS3 users thanked author for this post.
-
RDRguy
AskWoody LoungerWell, I’ve got this moderately old system that still performs GREAT and I really don’t want to put it out to pasture just yet. With the way things are going with Microsoft & Intel & ASUS & other OEMs support of their customers concerning legacy systems, it seems like with the help of AskWoody members, I’ll soon be (if not already) the main technical support provider for all of my systems.
As I find ways to do things that I would normally expect OEMs to do but they no longer do, I feel it’s my duty as a techie to pass onto others things I’ve learned so that they can also become somewhat more self-sufficient should the need arise.
Group B / Win7 SP1 (Ultimate & Pro) [x64 & x86]
RDRguyWin7 - PRO & Ultimate, x64 & x86
Win8.1 - PRO, x64 & x86
Groups A, B & ABS

|
Patch reliability is unclear. Unless you have an immediate, pressing need to install a specific patch, don't do it. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
CISA warns of hackers targeting critical oil infrastructure
by
Nibbled To Death By Ducks
2 hours, 6 minutes ago -
AI slop
by
Susan Bradley
1 hour, 17 minutes ago -
Chrome : Using AI with Enhanced Protection mode
by
Alex5723
3 hours, 23 minutes ago -
Two blank icons
by
CR2
9 hours, 52 minutes ago -
Documents, Pictures, Desktop on OneDrive in Windows 11
by
ThePhoenix
12 hours, 17 minutes ago -
End of 10
by
Alex5723
14 hours, 57 minutes ago -
End Of 10 : Move to Linux
by
Alex5723
15 hours, 26 minutes ago -
Single account cannot access printer’s automatic duplex functionality
by
Bruce
11 hours, 55 minutes ago -
test post
by
gtd12345
20 hours, 58 minutes ago -
Privacy and the Real ID
by
Susan Bradley
11 hours, 5 minutes ago -
MS-DEFCON 2: Deferring that upgrade
by
Susan Bradley
3 hours, 12 minutes ago -
Cant log on to oldergeeks.Com
by
WSJonharnew
1 day, 1 hour ago -
Upgrading from Win 10
by
WSjcgc50
2 hours, 41 minutes ago -
USB webcam / microphone missing after KB5050009 update
by
WSlloydkuhnle
20 hours, 25 minutes ago -
TeleMessage, a modified Signal clone used by US government has been hacked
by
Alex5723
1 day, 16 hours ago -
The story of Windows Longhorn
by
Cybertooth
1 day, 4 hours ago -
Red x next to folder on OneDrive iPadOS
by
dmt_3904
1 day, 18 hours ago -
Are manuals extinct?
by
Susan Bradley
6 hours, 25 minutes ago -
Canonical ditching Sudo for Rust Sudo -rs starting with Ubuntu
by
Alex5723
2 days, 4 hours ago -
Network Issue
by
Casey H
1 day, 15 hours ago -
Fedora Linux is now an official WSL distro
by
Alex5723
2 days, 16 hours ago -
May 2025 Office non-Security updates
by
PKCano
2 days, 16 hours ago -
Windows 10 filehistory including onedrive folder
by
Steve Bondy
2 days, 18 hours ago -
pages print on restart (Win 11 23H2)
by
cyraxote
1 day, 19 hours ago -
Windows 11 Insider Preview build 26200.5581 released to DEV
by
joep517
2 days, 20 hours ago -
Windows 11 Insider Preview build 26120.3950 (24H2) released to BETA
by
joep517
2 days, 20 hours ago -
Proton to drop prices after ruling against “Apple tax”
by
Cybertooth
3 days, 4 hours ago -
24H2 Installer – don’t see Option for non destructive install
by
JP
1 day, 20 hours ago -
Asking Again here (New User and Fast change only backups)
by
thymej
3 days, 15 hours ago -
How much I spent on the Mac mini
by
Will Fastie
22 hours, 47 minutes ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.