-
NetDef
AskWoody_MVPKnown reboot flags in Win 10 and up – any one of these will block many installers and updates if not cleared by the process that set it.
HKLM:\SOFTWARE\Microsoft\ServerManager\CurrentRebootAttempts – key exists
HKLM:\SOFTWARE\Microsoft\Updates – UpdateExeVolatile – Value is anything other than 0
HKLM:\Software\Microsoft\Windows\CurrentVersion\Component Based Servicing\PackagesPending – key exists
HKLM:\Software\Microsoft\Windows\CurrentVersion\Component Based Servicing\RebootInProgress – key exists
HKLM:\Software\Microsoft\Windows\CurrentVersion\Component Based Servicing\RebootPending – key exists
HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce – DVDRebootSignal – value exists
HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate\Auto Update\PostRebootReporting – key exists
HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate\Auto Update\RebootRequired – key exists
HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate\Services\Pending – Any GUID subkeys exist
HKLM:\SYSTEM\CurrentControlSet\Control\Session Manager – PendingFileRenameOperations – value exists
HKLM:\SYSTEM\CurrentControlSet\Control\Session Manager – PendingFileRenameOperations2 – value exists
HKLM:\SYSTEM\CurrentControlSet\Services\Netlogon – AvoidSpnSet – value exists
HKLM:\SYSTEM\CurrentControlSet\Services\Netlogon – JoinDomain – value existsThe following special key pair comes into play when a machine is renamed (system compares, both keys must match to prevent reboot flag)
HKLM:\SYSTEM\CurrentControlSet\Control\ComputerName\ActiveComputerName
HKLM:\SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName~ Group "Weekend" ~
-
NetDef
AskWoody_MVPThis is hitting all of our M365 Exchange customers, and it is also hitting my family’s personal MSN/Outlook accounts.
~ Group "Weekend" ~
-
NetDef
AskWoody_MVPThanks Susan!
Our team has blocked that KB now across our entire org. Some notes:
Unless you have a current Software Assurance subscription along with your correctly scaled Server 2022/2019 license core count, accepting this update WILL put you into non-compliance with your license unless you purchase new Server 2025 licenses.
In place upgrades have become drastically more reliable since the 2016 days, but there are some gotcha’s that our team has identified:
Domain controllers should be migrated to new builds, not upgraded in place. MS technically supports upgrading DC’s with some special and convoluted instructions, but it has not proven reliable for our team.
Application servers, including SQL servers, generally upgrade in place just fine, but many LOB applications will trigger a re-activation workflow. You may also need to re-apply all prerequisite packages like .Net and other third party code libraries. Be prepared and make sure your software is on a current and supported license, that the applications re-activation is possible (you have a working key), and that the system requirements for your application include the new server OS as a supported platform. If any of those checks are not in place, defer the upgrade.
Dedicated file servers generally are safe to upgrade in place.
Internal Certificate Authority server roles don’t play nice with upgrades in place, migrate the role to a new server (often on a DC.)
Radius Servers have also not played as nice as we would like, recommending migrating to a new server.
ALWAYS do a test upgrade in a sandbox with the roles and applications your business uses! Document every workaround you make during the test so you can replicate that on production.
And finally: Make sure you have a fully restorable backup image, refreshed just before the upgrade, ready to use if you need to rollback!
Never -ever- upgrade a server without a known good recent backup.
Cheers!
~ Group "Weekend" ~
-
NetDef
AskWoody_MVPNovember 13, 2023 at 7:09 pm in reply to: Outlook mobile is an awful app for iPhone or Android #2602364Are you somehow implying that Google or Apple has better controls over who or what gets access to your metadata and privacy?
I’m . . . not convinced that any of the tech companies are better or worse than their peers. Choose the bucket you feel will give you the least pain, but it’s kinda all the same.
~ Group "Weekend" ~
1 user thanked author for this post.
-
NetDef
AskWoody_MVPNovember 13, 2023 at 7:04 pm in reply to: Outlook mobile is an awful app for iPhone or Android #2602363I personally prefer Outlook (Android, iOS, Windows, MacOS) over nearly any other option. And I’ve tried them all over the years.
I like that the functions are all a flick of the finger away (Email, Schedule, Task List, Contacts) and I like that I can link pretty near as many email accounts as I want, which lets me see all emails from all accounts or narrow it down to a single account with one click.
I also prefer it for M365 Corporate accounts, by far.
But then, I am not your average user.
~ Group "Weekend" ~
1 user thanked author for this post.
-
NetDef
AskWoody_MVPReally good timing Susan!
I manage several Hyper-V clusters with “many” guest VM’s running Server 2019/22 and this coming weekend is our scheduled cluster-aware patching date. We also use Veeam . . .
Looks like I might pause them until the MSFT and Veeam get their act together regarding the Oct ’23 CU for Server 2019 and 2022.
Thank you!
~ Group "Weekend" ~
-
NetDef
AskWoody_MVPFor those who wish to keep and use Windows Server 2012 and 2012R2 past this months patch cut-off: looks like you can install Azure Arc on those servers and provision ESU to it to extend security patches to October 2026.
More info here:
https://learn.microsoft.com/en-us/azure/azure-arc/servers/prepare-extended-security-updates
~ Group "Weekend" ~
-
NetDef
AskWoody_MVPOctober 12, 2023 at 7:09 pm in reply to: The Evolution of Windows Authentication (eliminating NTLM) #2593711I’ll be interested in any info your sources can gather. My internal source thinks its a few years out still, they want to measure NTLM use over time as they press application developers to stop hard coding it into their programs – but knowing how slow some large and expensive line of business applications move it may be a decade.
I’ll likely be fully retired by then.
~ Group "Weekend" ~
-
NetDef
AskWoody_MVPOctober 12, 2023 at 4:19 pm in reply to: The Evolution of Windows Authentication (eliminating NTLM) #2593688I have a bit of bad news about this announcement,
Regarding this statement:
- NTLM is the only protocol supported when using local accounts.
When they deprecate NTLM entirely in the future, unless they add a local Kerberos authority to Windows 11/12/13/14 (right now they are only planning to add a Kerberos “cache/proxy”) then peer to peer file sharing on small networks using local machine accounts will be broken forever. I suspect they want everyone to use an online account, which can use MS as the authentication authority.
~ Group "Weekend" ~
1 user thanked author for this post.
-
NetDef
AskWoody_MVPAnother mitigation layer to consider: Use a DNS service that attempts to delist all known malware addresses.
https://blog.cloudflare.com/introducing-1-1-1-1-for-families/
~ Group "Weekend" ~
2 users thanked author for this post.
-
NetDef
AskWoody_MVPHey Susan!
Wanted to thank you for posting this. I was trying to conduct a live migration today to move several VM’s over to a new Hyper-V host on an AD network that had taken the November patches.
The Kerberos constrained delegation trust relationship between the old host and the new Hyper-V host was completely broken by the Nov 12th patch on the domain controller. Kept getting errors that one host could not connect to the other. (WinRM failures)
I installed the hot fix listed (KB KB5021655 from the MS download catalog for Server 2019) on the MS Status page link you provided on the Domain Controller and also applied the LSASS memory leak mitigation reg-key mentioned on the same page – again on that same DC.
It completely fixed the issue with my migration failures.
Weirdly, this particular customer informed me that all their workstations had been popping up an odd notification since Nov 12th asking them to lock and unlock their computer to refresh a password change . . . but none of them had recently changed their passwords. If the user complied with the lock/unlock process, the popup would repeat anyway at some random time – several times a day. That issue also went away once I installed this hotfix on the DC.
~ Group "Weekend" ~
-
NetDef
AskWoody_MVPCheap, effective mitigation for the current highest risk on new cars with remote start key fobs: a faraday box.
I got one that actually works for about $20 . . . tested by putting keys inside and trying to open a car that uses the near field to unlock doors when I touch the handle.
~ Group "Weekend" ~
3 users thanked author for this post.
-
NetDef
AskWoody_MVPThat was a source of confusion for a long time, as the tool allowed an invalid combination by accident that would not work . . . Glad they fixed it finally!
~ Group "Weekend" ~
-
NetDef
AskWoody_MVPI just had a chance to try this out for a new install of Windows 11 22H2, on a VM with networking disabled during setup, and am happy to report the bypass to allow creating a local account worked perfectly.
~ Group "Weekend" ~
3 users thanked author for this post.
-
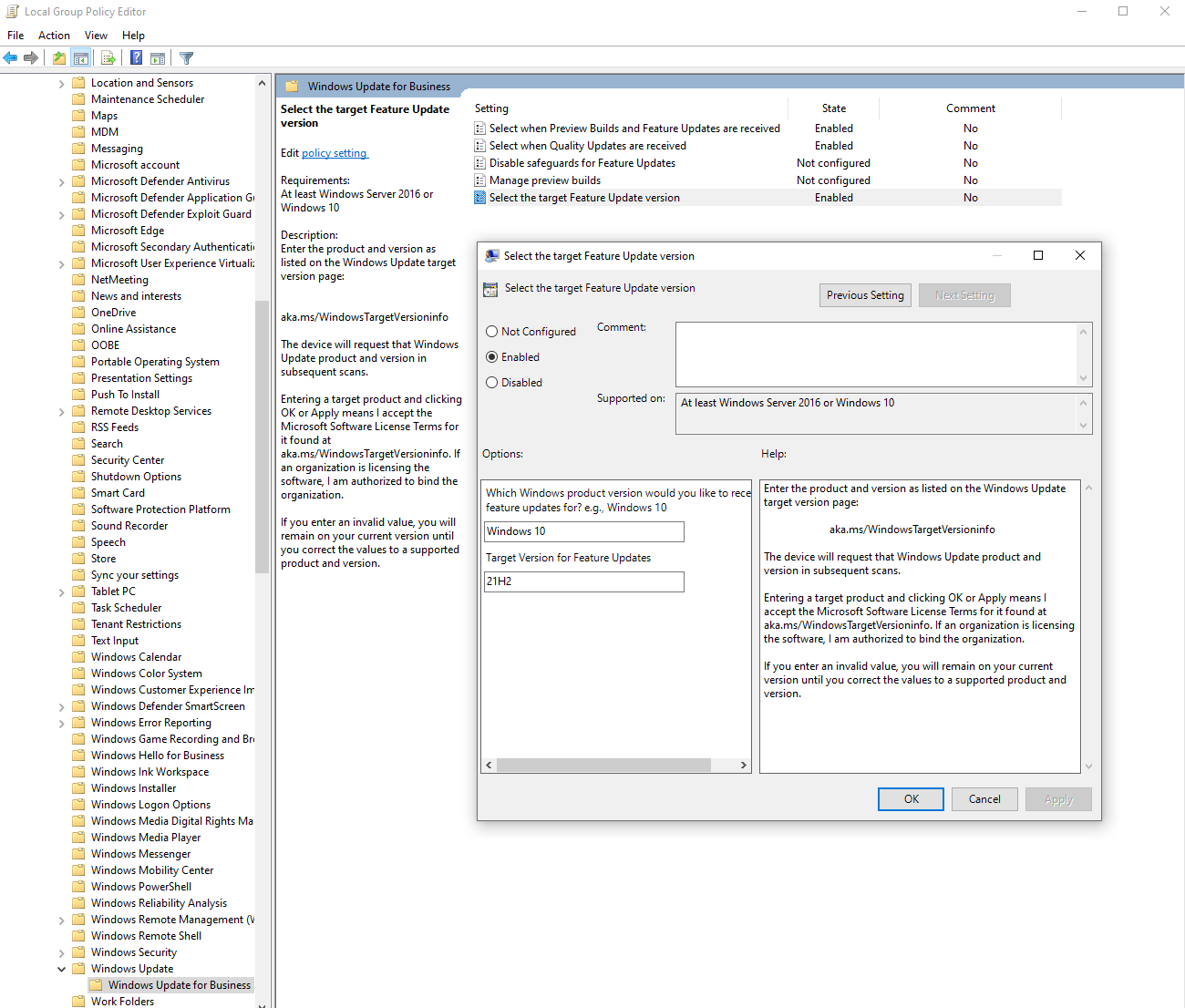
NetDef
AskWoody_MVPJune 15, 2022 at 11:08 am in reply to: Will gpedit Target Release Version stop PARTIAL download for update to Win 11? #2453705Just a quick visual aid for GPEdit.msc using PKCano’s settings above:
~ Group "Weekend" ~
1 user thanked author for this post.

|
Patch reliability is unclear, but widespread attacks make patching prudent. Go ahead and patch, but watch out for potential problems. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Why MS Teams does not isntall on Windows 8,1? (Awaiting moderation)
by
Windows 8,1 user
4 minutes ago -
Asking Again here (New User and Fast change only backups)
by
thymej
3 hours, 3 minutes ago -
How much I spent on the Mac mini
by
Will Fastie
3 hours, 47 minutes ago -
How to get rid of Copilot in Microsoft 365
by
Lance Whitney
4 minutes ago -
Spring cleanup — 2025
by
Deanna McElveen
4 hours, 36 minutes ago -
Setting up Windows 11
by
Susan Bradley
2 hours, 19 minutes ago -
VLC Introduces Cutting-Edge AI Subtitling and Translation Capabilities
by
Alex5723
4 minutes ago -
Powershell version?
by
CWBillow
57 minutes ago -
SendTom Toys
by
CWBillow
11 hours, 21 minutes ago -
Add shortcut to taskbar?
by
CWBillow
4 hours, 52 minutes ago -
Sycophancy in GPT-4o: What happened
by
Alex5723
21 hours, 15 minutes ago -
How can I install Skype on Windows 7?
by
Help
19 hours, 57 minutes ago -
Logitech MK850 Keyboard issues
by
Rush2112
2 hours, 52 minutes ago -
We live in a simulation
by
Alex5723
1 day, 11 hours ago -
Netplwiz not working
by
RetiredGeek
21 hours, 57 minutes ago -
Windows 11 24H2 is broadly available
by
Alex5723
1 day, 23 hours ago -
Microsoft is killing Authenticator
by
Alex5723
11 hours, 26 minutes ago -
Downloads folder location
by
CWBillow
2 days, 6 hours ago -
Remove a User from Login screen
by
CWBillow
1 day, 1 hour ago -
TikTok fined €530 million for sending European user data to China
by
Nibbled To Death By Ducks
1 day, 21 hours ago -
Microsoft Speech Recognition Service Error Code 1002
by
stanhutchings
1 day, 21 hours ago -
Is it a bug or is it expected?
by
Susan Bradley
2 days, 2 hours ago -
Image for Windows TBwinRE image not enough space on target location
by
bobolink
1 day, 20 hours ago -
Start menu jump lists for some apps might not work as expected on Windows 10
by
Susan Bradley
20 hours ago -
Malicious Go Modules disk-wiping malware
by
Alex5723
2 days, 10 hours ago -
Multiple Partitions?
by
CWBillow
2 days, 10 hours ago -
World Passkey Day 2025
by
Alex5723
7 hours, 3 minutes ago -
Add serial device in Windows 11
by
Theodore Dawson
3 days, 19 hours ago -
Windows 11 users reportedly losing data due forced BitLocker encryption
by
Alex5723
1 day, 20 hours ago -
Cached credentials is not a new bug
by
Susan Bradley
3 days, 23 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.