Wow. This one goes all the way back to Hacker’s Guide to Word for Windows — which was published in 1994. Etienne Stalmans and Saif El-Sherei at Sense
[See the full post at: Word’s DDEAUTO field considered harmful]

|
Patch reliability is unclear. Unless you have an immediate, pressing need to install a specific patch, don't do it. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
-
Word’s DDEAUTO field considered harmful
Home » Forums » Newsletter and Homepage topics » Word’s DDEAUTO field considered harmful
- This topic has 12 replies, 6 voices, and was last updated 7 years, 7 months ago.
Tags: DDEAUTO
AuthorTopicViewing 10 reply threadsAuthorReplies-
Pepsiboy
AskWoody Lounger -
Noel Carboni
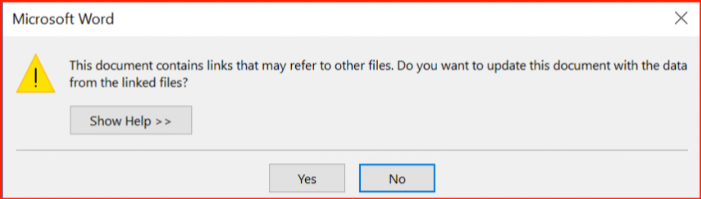
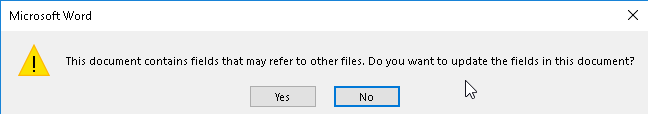
AskWoody_MVPOctober 10, 2017 at 9:41 am #136323They gloss over a key decision point that would certainly raise MY suspicions. If I received a warning like the following on a document received from elsewhere, or even just viewing an eMail you’d better believe I’d choose [ No ]!
or
They dismiss the above as “nothing malicious”, while I most certainly would not. However, I will concede that folks in, say, a corporate environment in which documents that emit such messages are regularly passed around could be fooled.
The worrisome part is that Microsoft, having been informed, might now hobble some key functionality of older versions of Office so that this “threat” will be removed. What do WE end up with? Software that works worse – and which if designed originally that way might never have been suitable for use or purchase.
It bothers me that there is much that is implied but unsaid in discussions about security. There should always be a discussion on whose responsibility it is to maintain security. It’s a bit like having a discussion about power tools and claiming a cordless drill is a threat to everyone because you could accidentally drill a hole in your hand, then demanding the manufacturer to change it so that it can’t do so. The assumption is that everyone using a power drill is ignorant, and that the manufacturer must put some kind of guard on it that doesn’t get in the way of actual work, but protects ignorant users’ hands – while such a design may not be feasible or even possible. Then, who could ever complain about it when it’s so much more secure?
In this case Microsoft HAS included warnings that would block this infection, but because it suits the writers who want to fill their space with important-looking info, it’s considered “not enough”. How much is enough?
Notably Microsoft responded appropriately, I think:
26/09/2017 – Microsoft responded that as suggested it is a feature and no further action will be taken, and will be considered for a next-version candidate bug.
-Noel
-
Bill C.
AskWoody PlusOctober 10, 2017 at 10:46 am #136343>>> The worrisome part is that Microsoft, having been informed, might now hobble some key functionality of older versions of Office so that this “threat” will be removed. What do WE end up with? Software that works worse – and which if designed originally that way might never have been suitable for use or purchase. <<<
Yep, just as they have made Outlook 2010 on a personal PC almost worthless to receive any kind of mailing from businesses or news organizations, and I do not mean ads. Tons of blank photo placeholders.
-
MrBrian
AskWoody_MVPOctober 10, 2017 at 2:51 pm #136422 -
MrBrian
AskWoody_MVPOctober 16, 2017 at 12:09 pm #138158From https://twitter.com/GossiTheDog/status/919945210746081282: “While InfoSec is busy worrying about an academic threat around Wi-Fi, Word DDE (no patch) is being used for ransomware and trojans right now”
1 user thanked author for this post.
-
MrBrian
AskWoody_MVPOctober 16, 2017 at 5:28 pm #138235From https://www.securityforrealpeople.com/2017/10/exploiting-office-native-functionality.html:
‘One final note: after I published this article, fellow Austin security pro Brian Boettcher mentioned a very simple trick to stop this exploit dead in its tracks: disabling the “update automatic links at open” option in Word.’
-
Bob99
AskWoody MVPOctober 16, 2017 at 8:28 pm #138263From https://www.securityforrealpeople.com/2017/10/exploiting-office-native-functionality.html: ‘One final note: after I published this article, fellow Austin security pro Brian Boettcher mentioned a very simple trick to stop this exploit dead in its tracks: disabling the “update automatic links at open” option in Word.’
And for those wanting to know just how to do what Brian is talking about above, go into Word’s Options menu and choose the “Advanced” options. Now, scroll ALL the way down to the heading labeled “General” on the right side of the window. Under there, you should find the check box labeled exactly as described by Brian above! Click the box to remove the check mark that’s probably in it by default, then click the OK button at the bottom of the window and you’re done!
-
-
MrBrian
AskWoody_MVPOctober 17, 2017 at 3:52 am #138314From https://twitter.com/ryHanson/status/918598525792935936: “The well known Excel DDE vector can also be manipulated, here is the formula […]”
-
MrBrian
AskWoody_MVPOctober 17, 2017 at 3:54 am #138315There are ways to avoid opening a file from the Internet in Protected View: https://enigma0x3.net/2017/07/13/phishing-against-protected-view/. Example video: https://twitter.com/enigma0x3/status/918636157461770240.
-
MrBrian
AskWoody_MVPOctober 17, 2017 at 4:49 am #138328From Hancitor malspam uses DDE attack: “Malicious spam (malspam) pushing Hancitor malware (also known as Chanitor or Tordal) changed tactics on Monday 2017-10-16. Instead of pushing Microsoft Word documents with malicious macros, this malspam began pushing Word documents taking advantage of Microsoft’s Dynamic Data Exchange (DDE) technique.”
-
MrBrian
AskWoody_MVPOctober 19, 2017 at 7:25 am #138898From https://twitter.com/GossiTheDog/status/920635876375449600: “Remember the Word DDE issue found by @sensepost? Copy the DDE from Word into Outlook, then email it to somebody.. No attachment -> calc.”
From https://twitter.com/5ecur1tySi/status/920984536774840320: “The following .reg file should prevent the loading of DDE in Outlook 2016.”
-
MrBrian
AskWoody_MVP
Viewing 10 reply threads -

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Giving UniGetUi a test run.
by
RetiredGeek
56 minutes ago -
Windows 11 Insider Preview Build 26100.4188 (24H2) released to Release Preview
by
joep517
8 hours, 34 minutes ago -
Microsoft is now putting quantum encryption in Windows builds
by
Alex5723
6 hours, 32 minutes ago -
Auto Time Zone Adjustment
by
wadeer
13 hours, 3 minutes ago -
To download Win 11 Pro 23H2 ISO.
by
Eddieloh
10 hours, 43 minutes ago -
Manage your browsing experience with Edge
by
Mary Branscombe
4 hours, 30 minutes ago -
Fewer vulnerabilities, larger updates
by
Susan Bradley
2 hours, 14 minutes ago -
Hobbies — There’s free software for that!
by
Deanna McElveen
6 hours, 31 minutes ago -
Apps included with macOS
by
Will Fastie
6 hours, 9 minutes ago -
Xfinity home internet
by
MrJimPhelps
6 hours, 4 minutes ago -
Convert PowerPoint presentation to Impress
by
RetiredGeek
6 hours, 2 minutes ago -
Debian 12.11 released
by
Alex5723
1 day, 10 hours ago -
Microsoft: Troubleshoot problems updating Windows
by
Alex5723
1 day, 13 hours ago -
Woman Files for Divorce After ChatGPT “Reads” Husband’s Coffee Cup
by
Alex5723
17 hours, 19 minutes ago -
Moving fwd, Win 11 Pro,, which is best? Lenovo refurb
by
Deo
9 hours, 43 minutes ago -
DBOS Advanced Network Analysis
by
Kathy Stevens
2 days, 6 hours ago -
Microsoft Edge Launching Automatically?
by
healeyinpa
1 day, 21 hours ago -
Google Chrome to block admin-level browser launches for better security
by
Alex5723
2 days, 9 hours ago -
iPhone SE2 Stolen Device Protection
by
Rick Corbett
2 days, 1 hour ago -
Some advice for managing my wireless internet gateway
by
LHiggins
1 day, 9 hours ago -
NO POWER IN KEYBOARD OR MOUSE
by
HE48AEEXX77WEN4Edbtm
11 hours, 14 minutes ago -
A CVE-MITRE-CISA-CNA Extravaganza
by
Nibbled To Death By Ducks
2 days, 18 hours ago -
Sometimes I wonder about these bots
by
Susan Bradley
7 hours, 4 minutes ago -
Does windows update component store “self heal”?
by
Mike Cross
2 days, 5 hours ago -
Windows 11 Insider Preview build 27858 released to Canary
by
joep517
3 days, 8 hours ago -
Pwn2Own Berlin 2025: Day One Results
by
Alex5723
1 day, 16 hours ago -
Windows 10 might repeatedly display the BitLocker recovery screen at startup
by
Susan Bradley
1 day, 5 hours ago -
Windows 11 Insider Preview Build 22631.5409 (23H2) released to Release Preview
by
joep517
3 days, 11 hours ago -
Windows 10 Build 19045.5912 (22H2) to Release Preview Channel
by
joep517
3 days, 11 hours ago -
Kevin Beaumont on Microsoft Recall
by
Susan Bradley
2 hours, 1 minute ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.