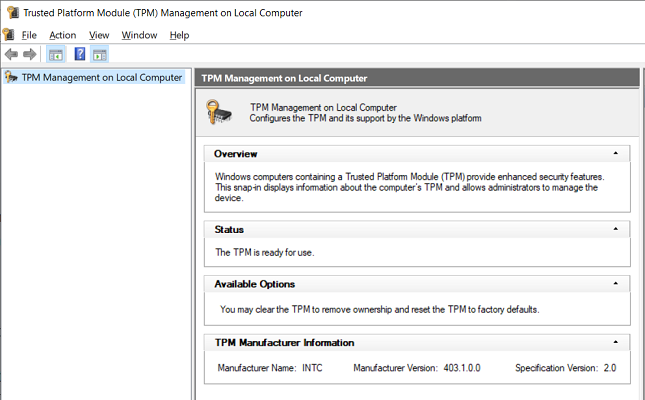
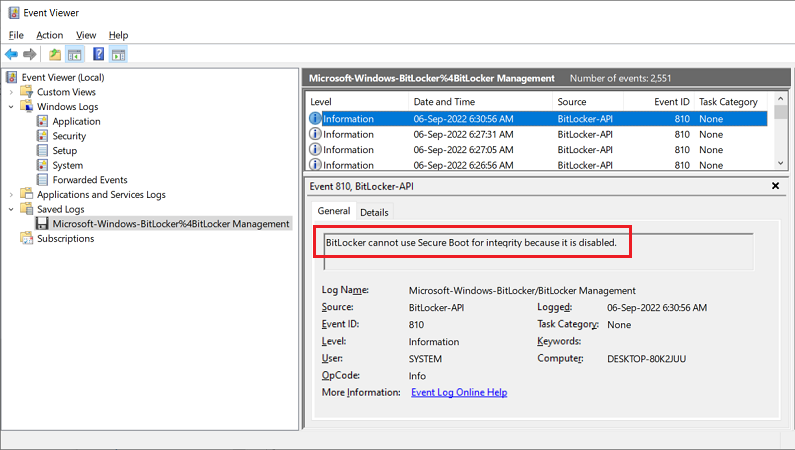
I am Win10, 21H2. I have not installed any August patch or preview. I am up-to-date as of the July patches.
I have received a notification from DELL about the need for a BIOS update. So, I updated the BIOS on my device.
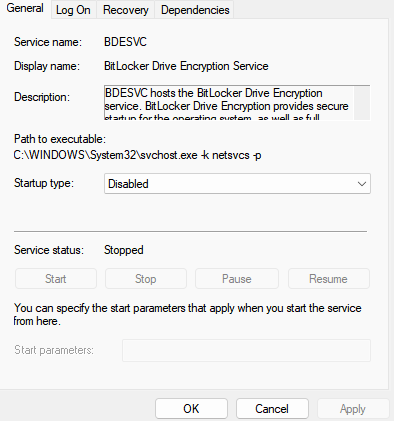
Before I updated the BIOS, I checked Manage BitLocker (Control Panel|BitLocker Drive Encryption) and it said that BitLocker was OFF. See attachment.
But, after I did the BIOS update, I checked Manage BitLocker again, and it said BitLocker waiting for Activation and there was a yellow triangle. See attachment.
I managed to get the screen to say that BitLocker was OFF with no yellow triangle by going to Settings|Update & Security|Drive Encryption and clicking on the box said ‘Turn OFF‘ Then, a screen came up (I think it was the ‘Manage BitLocker’ screen) that said ‘Decryption in progress’ and there was a line that began filling up left to right. After about 45 minutes, the screen changed to say that decryption had completed, that ‘BitLocker is OFF‘ and there was no yellow triangle anymore, i.e., the screen looked like it did before the BIOS update.
I am wondering what could have precipitated the ‘BitLocker is waiting for activation‘ and the yellow triangle. I’ve done BIOS updates before and I’ve never had BitLocker do this (i.e., say that it is waiting for activation).
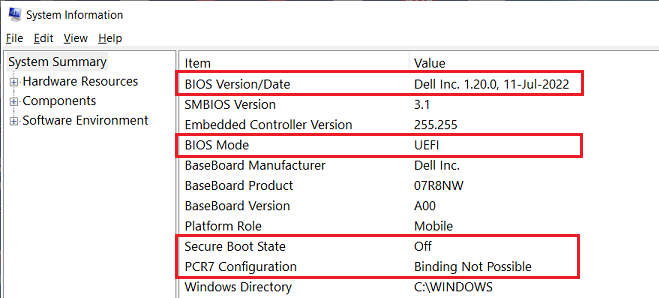
The only thing I can think of is this: I couldn’t get my Windows 10 Calendar to say ‘Microsoft Account‘ in the left panel. So I went to Group Policy|Computer Configuration|Windows Settings|Local Policies|Security Options, double clicked on the ‘Not Defined’ and used the drop-down menu to select ‘The policy is disabled’, which means that ‘Microsoft Accounts’ is not blocked. But, this didn’t make by Windows 10 Calendar say ‘Microsoft Account’ in the left panel. I later learned that it could not do this because the machine does not use a Microsoft Account to log on. However, there was no way to set the GP setting back to ‘Not Defined’. The 3rd attachment shows how it looked before I made the GP change (it comes from my other laptop, which still has the ‘Not Defined’ setting’)
The 4th attachment hows how it looked after I made the GP change.
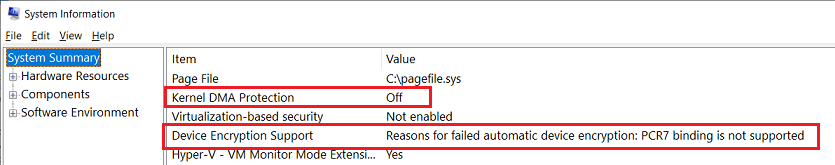
So, I am thinking that the BIOS update saw that the ‘Block Micosoft Accounts’ was disabled, so encrypted the drive and then was looking for me to complete the process by waiting for me to turn things over to my Microsoft Account so that a recovery key could be created. Fortunately, since I do not want BitLocker to be in force (i.e., I do not want BitLocker to encrypt my drive and do not want to have a recovery key created), I was able to ‘turn off’ the process, which decrypted the drive, BitLocker was no longer waiting for activation, and BitLocker remained OFF.
So, does NOT having ‘Microsoft Accounts blocked’ (instead of ‘Not Defined’) have anything to do with ‘BitLocker waiting for Activation’ when a BIOS update occurs? Or was there something in the BIOS update itself (unlike other BIOS updates) that made the ‘BitLocker waiting for Activation’ occur?