What an odd month. We got a ton of bugs introduced in the Patch Tuesday patches that were — mostly, but not completely — solved by patches later in
[See the full post at: Where we stand with the February patches]

|
Patch reliability is unclear, but widespread attacks make patching prudent. Go ahead and patch, but watch out for potential problems. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
-
Where we stand with the February patches
Home » Forums » Newsletter and Homepage topics » Where we stand with the February patches
- This topic has 98 replies, 35 voices, and was last updated 6 years ago.
AuthorTopicViewing 33 reply threadsAuthorReplies-
b
AskWoody_MVPMarch 1, 2019 at 9:15 am #335490At the top of the Master Patch List; does, “Not yet ready for giving the total all clear at this point.” refer to version 1809 or February patches (as it appears under headings for both)?
-
Susan Bradley
ManagerMarch 1, 2019 at 10:26 am #335559I will be updating it tonight (sorry was busy this week), at the time it was meant for both. Today I’m okay with Feb patches (no dead bodies here at the office or at home). I’m not yet ready to give the all clear for 1809
Susan Bradley Patch Lady/Prudent patcher
-
Mr. Natural
AskWoody LoungerMarch 1, 2019 at 3:01 pm #335816I haven’t had any reports of problems pushing all current updates including February updates via WSUS to Windows 7 x86 and x64. Also Windows 10 1803 which is our established standard. We do not run any Windows 10 older than 1803. We are installing 1809 on new builds, I pushed 1809 to around 10 systems running 1803 via WSUS and have not experienced any issues. I’m still not comfortable pushing 1809 entirely to our organization so 1803 remains the standard. But new installs get 1809 to help determine any software or hardware issues we may face.
Also no issues with Office 2010 and 2013 open license versions. Our Office 365 users are on semi annual channel (not targeted).
Include .Net patches also.
Forgot to mention Server 2012r2 and Server 2016 standalone with the majority running on VMWare. No issues. I retired our last 2008r2 system last month so we don’t have those systems anymore.
Disclaimer: Confirming Susan’s findings keeping in mind we are at Defcon 2.
Red Ruffnsore
1 user thanked author for this post.
-
-
-
anonymous
Guest -
Susan Bradley
Manager
-
-
WildBill
AskWoody PlusMarch 1, 2019 at 11:58 am #335668So, will the “all clear” (upgrade to MS-DEFCON 3 or higher) except for Win10 1809 be given this weekend or sometime next week… Or Not?! Looks like everything’s basically shaken out… as for KB4491113 (‘/’ bug), I don’t have Halo: Spartan Strike, but I do use Firefox. Skip that?
Bought a refurbished Windows 10 64-bit, currently updated to 22H2. Have broke the AC adapter cord going to the 8.1 machine, but before that, coaxed it into charging. Need to buy new adapter if wish to continue using it.
Wild Bill Rides Again... -
dononline
AskWoody LoungerMarch 1, 2019 at 1:00 pm #335754I’m confused about what’s safe to upgrade and what’s not, WildBill … but I’m thinking that until Woody lights up MS Defcon 3 or higher, I’m not upgrading anything. Of course, I’m always open, and grateful, for clarification from anyone here in the Lounge.
-
woody
Manager
-
-
-
EP
AskWoody_MVPMarch 1, 2019 at 12:09 pm #335681OOOHHHH
KB4482887 just appeared on MS Update Catalog today 3/1 for Win10 v1809:
https://www.catalog.update.microsoft.com/Search.aspx?q=44828871 user thanked author for this post.
-
anonymous
GuestMarch 1, 2019 at 12:43 pm #335714That KB4482887 also applies to Win 2019.
And there is also KB4486553 Cumulative update for .NET Framework 3.5 and 4.7.2 for Windows 10, version 1809 and Windows Server 2019. Released today.
https://support.microsoft.com/en-us/help/4486553/march-1-2019-kb4486553
Jim
1 user thanked author for this post.
-
anonymous
Guest -
anonymous
Guest -
anonymous
GuestMarch 1, 2019 at 3:37 pm #335839Jim wrote:
I’m not really into seeking much like I’m not into Russian Roulette.Hmmmm. Well, I’m not sure that comparison is entirely fair… to Russian Roulette.
If you lose at Russian Roulette, seems to me your problems are over. But if you lose as a Windows 10 “seeker”, your problems are only just beginning!
3 users thanked author for this post.
-
-
-
-
-
Tex265
AskWoody PlusMarch 1, 2019 at 12:43 pm #335724Woody:
Those of you using Win10 Pro or Enterprise, who follow my recommendations, have already installed updates,
Following your recommendations (and without further settings such as setting Group Policy > Windows Update at 2), as you say, one would have already installed the February updates. Even though Defcon is still set at 2.
Is this correct, that the Quality update deferred days setting is superceding the Defcon rating?
Windows 10 Pro x64 v22H2 and Windows 7 Pro SP1 x64 (RIP)2 users thanked author for this post.
-
woody
Manager
-
-
b
AskWoody_MVPMarch 1, 2019 at 1:41 pm #335764To further complicate matters, the Win8.1 Monthly Rollup Preview, which fixes this bug, introduces a truly bizarre bug that enables Location Services and makes a nuisance of itself in the Notification (er, Action) Center.
What’s truly bizarre is to call that a bug when it’s a transparency notification which does not enable Location Services. If transparency is a nuisance, please don’t appeal for more of it.
-
krzemien
AskWoody LoungerMarch 1, 2019 at 1:48 pm #335769 -
SAS@HA
AskWoody Lounger -
Alex5723
AskWoody Plus -
honx
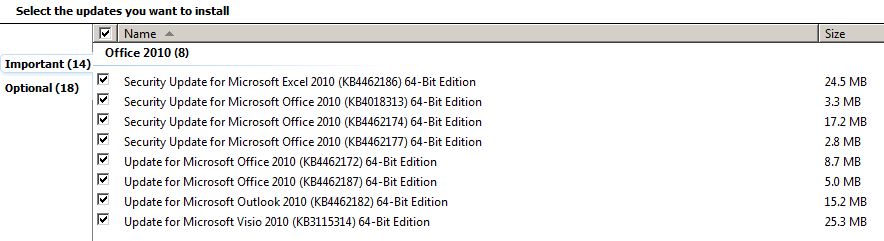
AskWoody LoungerMarch 1, 2019 at 2:14 pm #335781where do we stand regarding january patches for office 2010? are these safe to install already? following your advice in january i only installed group b windows patches, msrt, and so on. to date i still haven’t installed any patches for office 2010, so office 2010 is still on december patch level
PC: Windows 7 Ultimate, 64bit, Group B
Notebook: Windows 8.1, 64bit, Group B -
anonymous
GuestMarch 1, 2019 at 2:40 pm #335809There seems to be a lot of confusion about KB 4023057. It’s frequently referred to as a patch, but in reality it’s a program. After it is installed, it appears in Programs and Features. It can be uninstalled from there, but MS will promptly reinstall it. If you run Disk Cleanup as an Administrator after this program is installed, you’ll find a number of new entries like Compress OS, Delete all Restore Points, etc. that are clearly intended to make room for an upgrade on PCs with insufficient storage. While KB 4023057 may alter some settings, the main purpose appears to be storage related.
1 user thanked author for this post.
-
rc primak
AskWoody_MVPMarch 3, 2019 at 10:37 am #336490Those would seem to be useful things to add to Storage Sense (Disk Cleanup’s new location).
Now if only Microsoft would put the System Restore features in one place in their new settings panes. Of course, Cortana Search will lead you right there, and that’s how I find all the System Restore features now. But these System Restore features are still in the old-style interface, which could be “deprecated” at any time, just like the old-style Disk Cleanup interface.
Products like CCleaner and Glary Utilities are looking less and less necessary as new features are added to Storage Sense. Registry Cleaning is already totally unnecessary and sometimes harmful.
-- rc primak
-
-
Charlie
AskWoody PlusMarch 1, 2019 at 3:57 pm #335848 -
PKCano
Manager -
Charlie
AskWoody PlusMarch 1, 2019 at 4:56 pm #335905Okay, I should have said that I had no intention of installing them – my bad. That being said, 10 days remain for Feb. 5th updates to vanish. The Master Patch List lists only the Feb. 12th updates.
Being 20 something in the 70's was far more fun than being 70 something in the insane 20's -
PKCano
Manager
-
-
-
-
anonymous
GuestMarch 1, 2019 at 4:04 pm #335847Question….I have Win. 10 Pro 1803 with metered turned on and windows update set to defer. Once I decide to update, how do I get windows to check for updates without becoming a seeker ? In the past I have turned off metered and relaxed the settings and Windows sometimes will not check for updates on it’s own for quite some time.
-
rc primak
AskWoody_MVPMarch 3, 2019 at 12:06 pm #336516I apologize in advance for this long post. If it’s TL;DR, just look up Woody’s ComputerWorld article and work from there. His methods are very safe in my experience, and reasonably effective. But for those who want it, here’s the Whole Ball of Wax, at least as I do things:
The way to find out what would be installed if you did pull the trigger and “seek” updates is:
A) Be Prepared:
- Do any web browser cleanups you would normally do. Back up any History or Bookmarks and clean out other traces and remnants in your preferred normal way.
- Run full scans of the entire disk/file system using your favorite security program(s). Check both for viruses (Windows Defender’s main goal) and for PUPs (Malwarebytes Free’s strength). You might also want to run AdwCleaner (owned by the makers of Malwarebytes Free) to remove any remaining adware. Don’t be afraid to be fairly aggressive in removing PUPs and adware. Remember, we have a Full System Image Backup from before we began to make any system changes, right?
- Clean the disk with a mild run of any disk cleanup utility. (More and more this seems to be best handled by Microsoft’s own Windows 10 Storage Sense Disk Cleanup feature.)
- Make a fresh full System Image Backup using your favorite method. Set a Restore Point as well. Make sure you have a recent backup of the Windows Driver Store folder. This will be your local disk source for the Windows Device Manager if Microsoft tries to swap out drivers on you. (They have a habit of doing this without telling us, in my experience.)
- Now we can work with less fear that something unexpected will mess things up and force drastic measures.
B) Do a “Test Run” with wushowhide:
- Leave the connection metered.
- Set deferment value for Quality Updates (monthly cumulative and other regular updates) to 0 (zero). Leave Feature Updates deferred for at least 120 days, possibly longer. Stay on the longer-term update Channel for the Feature Updates.
- Note: Do NOT use “Pause Updates” options. As soon as you release the “Pause Button” you get everything automatically downloaded and installed, including any pending Feature Updates, metered connection or not.
- Now we are ready to use wushowhide to test what’s out there, and hide whatever needs to be hidden.
- We now know what is available, and can choose what we want and what we do not want to let Microsoft Update download and install. Nothing has yet been downloaded or placed in any automatic installation list or queue.
- Now it is safe to un-meter the connection. MS Update should do its thing, minus what we don’t want, shortly after this change. If not, I find it is now safe to Check for Updates (hit the main button).
C) When Woody or Susan Give the Go-Ahead, Run Microsoft Updates:
- When any unwanted Feature Updates (or other problem updates) are hidden, it is safe to “seek” updates, in my experience. I have never been burned by hitting the main Check for Updates button at this stage. But some folks claim they have been burned and gotten an unwanted Feature Update by doing this, even with all the above precautions. The first step in this process may be a Servicing Stack update, which may be applied separately, making a second Windows Update run necessary.
- If any updates fail to install, a second run of MS Updates may work things out, and you may need to temporarily suspend any third party security programs’ “Active Shields” or “Scan On Access (File and Folder Protection)” features while running MS Updates. (Windows Defender and the Windows Firewall will take over and protect your system during such a suspension. And WD may update itself as well in the process.)
- Note: Sometimes a failed update installation will not be reported by MS Updates. Belarc Advisor can occasionally pick up on these “installed” but actually “failed” security updates issues. It’s worth running this program and looking into the Missing MS Updates section. (What sometimes happens is that your third party security program has “protected” some system files and they were not correctly updated. Fixing this is not casual, and this is one reason why I have discontinued using third party Windows security products.)
- When the restart is offered, you can defer this as well, and Windows usually respects any Active Hours you may have set. But you will need to restart eventually.
- Upon coming back to your Windows desktop, run another “seek” operation with MS Update. There should be nothing reoffered and usually nothing new, unless a Feature Update has been applied (which we deferred above). See if anything unexpected has changed or if anything is not working. Check your Windows Updates Update History page for any Failed Updates. Try to fix these if they are relevant. (Check with AskWoody or post a question if anything doesn’t seem to add up at this point.)
- While I’m at it, let me note that for Windows 10 to do its Scheduled Maintenance, which includes defragmenting a mechanical hard drive and applying Trim to an SSD, you will need at some point every two weeks or so to leave the PC available to wake up into an Administrator Account with Internet access (metered is OK) and not to be used for a period of about two hours. This is only occasionally needed, and anything done or needing your input will show up as a Notification when Windows is finished. Many Windows issues can be lessened or resolved by doing this. But most end users don’t know this is necessary.
- If any hardware issues still show up, you probably got an unannounced Windows Driver substitution. These are common in my experience, even without a big Feature Update. Restore any drivers which need to be restored. (I have an Intel PC, so I can also look for relevant driver updates using the Intel Driver and Support Assistant. Do not use third party tools to do this!) Your best source for the original drivers is that copy of the Windows Driver Store you previously saved. Otherwise, use your PC manufacturer’s web site (whole device, not components, except for graphics or peripherals) to download the best current driver(s) for your whole PC.
D) Reset Your Deferrals:
- When you are satisfied with the outcome, or have fixed as best you can anything which did not work out correctly, it’s time to reset the Defer Quality Updates to 35 Days, or the longest period allowed.
- Reset the Metered Connection.
E) Update the Rest of Your System and Clean Up:
- Update any third party programs which need updating, especially your third party web browsers and extensions. I use KC Softwares SUMo (lite) to let me know what programs can be updated, not necessarily what I will update. (This is why I don’t use automatic downloading of third party software — I like to be in control of things.)
- Run new scans (these can be Quick Scans) with antivirus and antimalware products, as above. Include adware removal, as “piggybacks” are common in third party free software installers. (PUPs may be classified as malware or adware — it doesn’t matter, just remove the little annoyances.)
- Do a light system cleanup, as above.
- Create a new Full System Image Backup as above.
I know, this seems like a LOT of work to do, just to safely update and back up your system. But you can do this on a monthly basis, or possibly suffer the consequences when something unexpected happens. (To be honest, though the prep and post-update routines are much shorter, I do much the same routines in Linux. I like Aptik-gtk for data and settings — and even programs — backup in many popular Linux distros.)
So what might be these consequences? At best you may need to repair your Windows installation and reinstall some of your software. Settings may also have to be reset. At worst, your system may not be able to start up or get into the Windows desktop at all, requiring a full System Reset and reinstalling your software and resetting everything. Or, you could lose important data, including any photos or videos you may not have backed up anywhere. Cloud Storage is good, but local mechanical hard drive backups are better. Including data backups. (That’s what Windows File History is all about.)
Speaking of settings, there are third party tools to help you tweak, customize, and save special configuration details all in one interface. I only really care about Windows 10 privacy settings, so I use O&O ShutUp 10 and save its Config File off my main PC. Just like that Driver Store in case Microsoft pulls a Fast One. A few clicks from the config file and all is well again. Well, usually…
I expect much of what I do will prompt criticism or alternative strategies from AskWoody Loungers. That’s OK. I don’t propose everyone rigidly adhere to one person’s idea of The Perfect Windows Updates Strategy. But everyone could do some of these things one weekend, some another. And when a process runs a long time, let it go when you’re doing something away from the PC. (We all do some things AFK, right?) But most if not all of these tasks do need to happen eventually, for everyone. Best to work things into a routine, and make sure it all gets done sometime each month.
-- rc primak
4 users thanked author for this post.
-
anonymous
Guest -
Tex265
AskWoody PlusMarch 4, 2019 at 9:54 am #336954rc, thanks for your time providing such valuable information.
The only area that I would think more about before doing is utilizing the “Check for Updates” button thus becoming a “Seeker” for anything.
There has been so much written about this here at AskWoody and from Microsoft on the process that I am verrrrrry leary about ever doing this. I even recall a recent post cautioning about and providing a process to make darn sure (and still no guarantees) that an unwanted update or Feature update wasn’t hiding in the queue somewhere even after taking all precautions.
Each to make their own decisions. Just my two cents.
Windows 10 Pro x64 v22H2 and Windows 7 Pro SP1 x64 (RIP)
-
-
-
nazzy
AskWoody LoungerMarch 1, 2019 at 6:41 pm #335948February was odd indeed. For 2016 Server LTSC (1607), MS first released CU 4487026 which caused BSOD for some. Then MS later released CU 4487006 which supercedes -7026 and supposedly fixes the BSOD issues. First, is there an explanation why a superceding (top level) CU would have a LOWER kb number (7006)? Second, why would the superceding 7006 CU be listed only as “update” when the original 7026 CU is listed as “security update”? Third, 7006 has not been published to WSUS as of today 3/1/19 so I manually imported to WSUS where my 2016 servers promptly flagged 7006 as “needed”.
Any ideas guys?
-
anonymous
GuestMarch 7, 2019 at 8:50 am #338468Beware to KB4487006 – BSOD on windows terminal server.
https://support.microsoft.com/en-us/help/4487006/windows-10-update-kb4487006
1 user thanked author for this post.
-
-
mbhelwig
AskWoody LoungerMarch 1, 2019 at 7:03 pm #335959A question —
KB 4480970 (January Monthly Rollup) — 2019-01-09 has the following issue noted
FROM MICROSOFT — Known issues in this update —
After you apply this update, the network interface controller may stop working on some client software configurations. This occurs because of an issue related to a missing file, oem<number>.inf.The exact problematic configurations are currently unknown.
To locate the network device, launch devmgmt.msc. It may appear under Other Devices.
1. To automatically rediscover the NIC and install drivers, select Scan for Hardware Changes from the Action menu.
2. Alternatively, install the drivers for the network device by right-clicking the device and choosing Update. Then choose Search automatically for updated driver software or
Browse my computer for driver software.This issue has been in each monthly update since March 2018.
It does not appear in the February 2019 update (KB 4486563 ). Does this mean that the problem has been fixed ???? or ignored.
mbhelwig
1 user thanked author for this post.
-
OscarCP
MemberMarch 2, 2019 at 2:32 am #336020I have installed, in my Windows 7 Pro, SP1, x64 machine, the February Office 2010 (already fairly well vetted, i.e. in the Master Patch List and by PKCano) and the February MSRT. When I restarted and logged in once more, the OS had lost my user profile, which means the situation was the same as if I had been using the machine for the very first time after I bought it and took it out of its box. I am posting this here in case someone has had the same unfortunate experience and found a solution. I have written the problem in detail here #336010
I tend to doubt that those patches were the cause of this (also, I got rid of them by returning the PC to the state it was before I patched, but that did not fix the problem), but perhaps someone here knows better, in which case I’ll appreciate helpful suggestions.
This might also be read as a warning, if I happened to be wrong and it was those patches, not something else, that has caused the problem.
Ex-Windows user (Win. 98, XP, 7); since mid-2017 using also macOS. Presently on Monterey 12.15 & sometimes running also Linux (Mint).
MacBook Pro circa mid-2015, 15" display, with 16GB 1600 GHz DDR3 RAM, 1 TB SSD, a Haswell architecture Intel CPU with 4 Cores and 8 Threads model i7-4870HQ @ 2.50GHz.
Intel Iris Pro GPU with Built-in Bus, VRAM 1.5 GB, Display 2880 x 1800 Retina, 24-Bit color.
macOS Monterey; browsers: Waterfox "Current", Vivaldi and (now and then) Chrome; security apps. Intego AV -
PKCano
ManagerMarch 2, 2019 at 6:39 am #336047the February Office 2010 (already fairly well vetted, i.e. in the Master Patch List and by PKCano)
We are still on DEFCON2. I don’t recall recommending installation of any February patch other than KB4491113, and that only if one is experiencing the problem with IE.
Please provide the link to substantiate this claim. -
OscarCP
MemberMarch 2, 2019 at 6:59 am #336059PKCano,
I refer you to the Master Patch List, where, at the end, it says of several Office patches “OK To Install” and mentions you by name. I took my cue from there. If I misunderstood what that meant, I am sorry. Perhaps you and Sue should have a word about this, because the way it stands now it is confusing, if it is not correct.
On the other hand, I am hoping for help, as you might have noticed.
Ex-Windows user (Win. 98, XP, 7); since mid-2017 using also macOS. Presently on Monterey 12.15 & sometimes running also Linux (Mint).
MacBook Pro circa mid-2015, 15" display, with 16GB 1600 GHz DDR3 RAM, 1 TB SSD, a Haswell architecture Intel CPU with 4 Cores and 8 Threads model i7-4870HQ @ 2.50GHz.
Intel Iris Pro GPU with Built-in Bus, VRAM 1.5 GB, Display 2880 x 1800 Retina, 24-Bit color.
macOS Monterey; browsers: Waterfox "Current", Vivaldi and (now and then) Chrome; security apps. Intego AV -
PKCano
ManagerMarch 2, 2019 at 7:06 am #336060My name is there simply because I publish the list of non-Security Office patches on the first Tuesday of each month, and that is where Susan gets the list. There is nothing there saying I have vetted the list. In fact, if you look at the post on the blog, you will see otherwise. I do not ever recommend installing the non-Security Office patches on the day they are released.
The Master Patch List contains Susan’s recommendations, which are aimed at business environments, not consumers.
For AskWoody, we are still on DEFCON2.
-
b
AskWoody_MVPMarch 2, 2019 at 9:52 am #336105My name is there simply because I publish the list of non-Security Office patches on the first Tuesday of each month, and that is where Susan gets the list. There is nothing there saying I have vetted the list. In fact, if you look at the post on the blog, you will see otherwise. I do not ever recommend installing the non-Security Office patches on the day they are released.
The Master Patch List contains Susan’s recommendations, which are aimed at business environments, not consumers.
There’s no indication of that when you say, “… you should wait until Susan Bradley (Patch Lady) approves them …” as you post the list each month, and then they all get marked OK under Safe to install.
-
PKCano
Manager -
b
AskWoody_MVPMarch 2, 2019 at 10:52 am #336119Susan’s list is for the business environment, not consumers. This has been stated frequently here. And, yes, those in the related business environment should wait for Susan’s approval after testing.
Perhaps there should actually be some indication to that effect on the Master Patch List then.
And perhaps you could indicate that when you say, “… you should wait until Susan Bradley (Patch Lady) approves them …” each month.
And perhaps you shouldn’t refer questions from consumers about specific patches to that list each month, e.g.:
where do we stand regarding january patches for office 2010? are these safe to install already?
Have you checked Susan’s Master Patch List?
But on the other hand; I’ve never seen anything in the Newsletter that Susan’s patch advice only applies to business environments, even when she refers to the Master Patch List.
1 user thanked author for this post.
-
PKCano
ManagerMarch 2, 2019 at 11:22 am #336132The OP discussed installing a February Office patch. We are still on DEFCON2 for Feb patches.
Please provide a link where I recommended installing (not referencing a list for information) a non-Security Office patch for the current month that was still on DEFCON2. There is a difference between checking a list and installing a patch. You will find that I frequently say “check the list” and immediately follow with a reminder that we are still on the DEFCON “wait.”
The Newsletter has only been around for a few weeks. It has been discussed frequently on this site for much longer than that, that Susan’s recommendations for patching were based on a business environment with different needs that those for consumers. The DEFCON system is based on consumers, who do not have the technical knowledge, the test machines/VMs, or the time constraints of businesses.
-
Lars220
GuestMarch 2, 2019 at 12:16 pm #336144Clicking on the top button / tab? for MS-DEFCON System, gives information from Woody: “I have a rating system that lets individual Microsoft consumers know when it’s safe to install patches.” Important to note: individual consumers, BUT, clicking on the button – tab? for the Master Patch List, does not provide guidance about useful for Businesses, perhaps that could be added near the top of Susan Bradleys Patch Watch listings? Yes it has been noted outside the Newsletter about the two differences: https://www.askwoody.com/forums/topic/patch-watch-green-light-for-most-patches-yellow-for-win10-version-1809/#post-317383 KISS?
1 user thanked author for this post.
-
b
AskWoody_MVPMarch 2, 2019 at 12:18 pm #336156Please provide a link where I recommended installing (not referencing a list for information) a non-Security Office patch for the current month that was still on DEFCON2. There is a difference between checking a list and installing a patch. You will find that I frequently say “check the list” and immediately follow with a reminder that we are still on the DEFCON “wait.”
Why even say “check the list” then? If someone is referred to a list which says “OK to install” is it surprising that they might install the patch?
The Newsletter has only been around for a few weeks. It has been discussed frequently on this site for much longer than that, that Susan’s recommendations for patching were based on a business environment with different needs that those for consumers. The DEFCON system is based on consumers, who do not have the technical knowledge, the test machines/VMs, or the time constraints of businesses.
The newsletter has been around for 15-20 years (as Woody likes to remind us). “Patch Watch” only migrated here a year ago.
No mention of “business environment only” for Patch Watch at top right of every page either:
Plus Membership
AskWoody Plus members not only get access to all of the contents of this site — including Susan Bradley’s frequently updated Patch Watch listing — they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter)
Wouldn’t that amount to bait and switch for consumers if true?
But Woody doesn’t make the business/consumer distinction which you do (sometimes):
Patch Watch and DEFCON are directed at two different audiences.
For people who want a simple green light/red light solution, DEFCON is the way to go (with a few shades of orange in between).
If you’re comfortable wrassling with individual patches, Susan’s Patch Watch has always been my go-to source.
-
Cybertooth
AskWoody PlusMarch 2, 2019 at 12:25 pm #336158One source of confusion, which may have been a contributing factor, is Woody’s paragraph:
We’re still at MS-DEFCON 2. As far as I know, there are no major security problems solved by the February patches, so let’s give things a rest for now. Those of you using Win10 Pro or Enterprise, who follow my recommendations, have already installed updates, and everybody else should sit back and enjoy the weekend.
I can see how this could very easily leave someone shaking their head. In the second sentence, Woody says we’re at MS-DEFCON 2 and so we should wait to install the February updates, but then in the very next sentence he says that those who are on Windows 10 Pro or Enterprise have already installed the updates. How to square the two?
-
b
AskWoody_MVPMarch 2, 2019 at 12:40 pm #336160The “already” is because “my recommendations” for Pro is to defer updates for “10 or 15 or 20 days”.
10 or 15 would mean updated already, but 20 not for a couple more days.
But why are updates safe for Pro but not for Home yet? Just no rush, I guess.
3 users thanked author for this post.
-
PKCano
ManagerMarch 2, 2019 at 12:53 pm #336168Pro/Ent have test machines and IT people with tech knowledge. If a test machine crashes, the IT person knows how to deal with it. Even with production machines that’s so. Also, many businesses have guidelines to install patches within a certain number of days of release.
The consumer has one machine. If he tests and it crashes, he has NO machine and probably doesn’t have the knowledge to fix it, like the OP here. He is often with out a PC. And he had no time constraints – if he waits 28 days (except Feb) there is no rush – except in the case of an immediate security threat (which there have been FEW of).
-
b
AskWoody_MVPMarch 2, 2019 at 1:40 pm #336190Pro/Ent have test machines and IT people with tech knowledge. If a test machine crashes, the IT person knows how to deal with it. Even with production machines that’s so. Also, many businesses have guidelines to install patches within a certain number of days of release.
The reason that Pro machines may have been updated “already” due to “my recommendations” is that they updated automatically after a 10 or 15 day deferment. Nothing to do with testing in enterprises or business guidelines.
The consumer has one machine. If he tests and it crashes, he has NO machine and probably doesn’t have the knowledge to fix it, like the OP here. He is often with out a PC. And he had no time constraints – if he waits 28 days (except Feb) there is no rush – except in the case of an immediate security threat (which there have been FEW of).
In an era of personal laptops, tablets, smart TVs and phones, can it really be true that most home users only have one machine? The “no rush” is what I said, as the only possible justification for the contrast.
1 user thanked author for this post.
-
Tex265
AskWoody PlusMarch 2, 2019 at 1:55 pm #336201Not to pile on, but I had this Win 10 Pro deferral days vs Defcon rating update question yesterday way above in Reply #335724.
And while I can hardily agree with PK’s comment about what an Ent and “some” Windows Pro users may have as resources, many of us (and I suspect a growing number of new members) have Windows Pro solely to have some control over the Update process.
Maybe it would be an opportunity to clarify again the nuances of Pro’s vs Consumer’s vs Patch List vs Defcon rating, and now vs Monthly update deferral timing.
Woody’s article referred to is the typical Computerworld monthly article. And the “recommendation” referred to therein does not specify that it should be used only if you are a Business/Professional user – but simply that you have the Windows Pro version.
Windows 10 Pro x64 v22H2 and Windows 7 Pro SP1 x64 (RIP) -
Cybertooth
AskWoody PlusMarch 2, 2019 at 1:52 pm #336200All right, that brings up another spot where things could be made clearer, or else more standardized:
Woody’s explanation of the MS-DEFCON system doesn’t make any distinction between Windows 7/8, on the one hand, and Windows 10 on the other. The inference is that MS-DEFCON applies to all versions of Windows that receive updates. Given that the MS-DEFCON level typically isn’t raised above 2 until a few days before the next month’s patches are due, in effect those who follow the MS-DEFCON system are waiting 25-30 days to install the current month’s patches.
For the sake of consistency, then (not to mention, in order to avoid confusion such as is being discussed in this part of the thread), the “10 or 15 or 20 days” in Step 5 of Woody’s recommendations might be increased to, say, 25 or 30 days. (If the MS-DEFCON level is raised to 3 before 30 days pass, a Win10 user can presumably change or turn off the delay setting to let the patches install.)
1 user thanked author for this post.
-
Tex265
AskWoody PlusMarch 2, 2019 at 2:13 pm #336215Last year when I first found Woody’s, the advice here was basically to have Win 10 Pro, Set Group Policy > Windows Update to 2 (Ask to download), Set Monthly deferral days to 0. When the updates came down the chute, hide them with wushowhide and leave them there until Defcon 3 or more. Then unhide and install.
Along the line we got the Patch list and recently the “recommended” deferral setting of 10,15 or 20 days presumably leading to auto update download and install.
I’m sticking with the old advice!
Windows 10 Pro x64 v22H2 and Windows 7 Pro SP1 x64 (RIP)2 users thanked author for this post.
-
-
The Surfing Pensioner
AskWoody Plus -
OscarCP
MemberMarch 2, 2019 at 9:20 am #336099TSP: Thanks for your kind wishes, and very best of luck to you.
If this problem cannot be solved in a couple of days from now, that will mean that at long last I am not going to have to worry about Windows any longer, ever. If it came to that, I’ll just have to see if there is something I can do with the PC, besides recycling it, of course, such as installing Linux, perhaps after reformatting the disk. Fortunately, now I have the Mac I got over a year ago, so I can still do pretty much everything I need to do with it. Shame about the Windows PC, but if it is truly gone, well, I have had it for nearly eight years now, and that is quite a good long run for a PC. The interesting thing is that I have never had a problem with patches. I mean: since I started using Windows in 1998. Being cautious, looking around to see what was going on, worked for me. I hope it also does or you.
I have all my own files backed up on an external hard disk, so I imagine I’ll be able to transfer many of the important things there to the Mac.
And I don’t think it likely that the problem has been caused by the patches. One can never be sure, of course, but several people already have been reporting no problems when they install them, at least the Office ones and MSRT that I installed. Office has caused some trouble in the past to others, but the problem I am having now is very different form any of those.
Ex-Windows user (Win. 98, XP, 7); since mid-2017 using also macOS. Presently on Monterey 12.15 & sometimes running also Linux (Mint).
MacBook Pro circa mid-2015, 15" display, with 16GB 1600 GHz DDR3 RAM, 1 TB SSD, a Haswell architecture Intel CPU with 4 Cores and 8 Threads model i7-4870HQ @ 2.50GHz.
Intel Iris Pro GPU with Built-in Bus, VRAM 1.5 GB, Display 2880 x 1800 Retina, 24-Bit color.
macOS Monterey; browsers: Waterfox "Current", Vivaldi and (now and then) Chrome; security apps. Intego AV1 user thanked author for this post.
-
-
anonymous
GuestMarch 4, 2019 at 9:08 am #336919Better late than never I would like to add this to the discussion:
@woody @pkcano
The mere fact that to some the distinction between Defcon status and Master Patch List, and consumer- or enterprise-aimed is not clear, shows that the information is not clear enough to begin with.There is a famous saying in website development land called “Don’t make me think!”
Meaning: although it’s easy to give information to the visitor the way you’re used to and think it’s clear and obvious, that doesn’t mean the visitor understands it the way you do.1 user thanked author for this post.
-
-
-
-
Noel Carboni
AskWoody_MVPMarch 2, 2019 at 4:13 am #336032but 1809 isn’t “ready for business.”
I’ve been using v1809 now for a couple of months on my new office machine, a high-end Dell system running Windows 10 for Workstations v1809. I put a fair bit of demand on the machine 24/7 in a corporate engineering environment, and I’ve had no instability whatsoever. Its last reboot was due to the last set of updates I allowed in weeks ago.
Maybe – just maybe – there might be a few quirks in the (now dark themed, yeah!) Windows Explorer, but if they’re there, they’re traded for older ones I haven’t seen in a while. I’ve been able to focus on intensive work day in and day out, and not think about Windows.
I think that says “ready”, no? I’m fairly impressed, and I’m not easily impressed.
By comparison to older versions of Windows, especially going back a ways, this one seems “quite ready for business” to me.
-Noel
-
cyberSAR
AskWoody PlusMarch 2, 2019 at 6:45 am #336050My experience mirrors yours. Stable, no noticeable issues. So much so we have upgraded about 50 machines we maintain that are running Win 10 and upgraded quite a few Windows 7 machines. The machines vary in specs from a lowly pentium 1.4 with 2GB RAM to I7s with 32GB RAM running a wide assortment of software. Have had no reported issues and just a couple little glitches during the upgrades.
Not sure I’m ready to say “impressed” but very satisfied
-
warrenrumak
AskWoody Lounger -
Noel Carboni
AskWoody_MVPMarch 4, 2019 at 8:13 am #336901Not really a theme, it’s a tool called Aero Glass for Win 8+ I like that augments DWM and resurrects Aero Glass and borders, with some geekiness needed to apply it. See this forum for more info:
https://msfn.org/board/forum/180-aero-glass-for-windows-8/
Call me artsy fartsy or frivolous for running something that’s not all business, but I just don’t care for the stock, flat, lifeless look of windows on Windows 10. Better aesthetics make it easier to sit in front of a system day in and day out.
-Noel
1 user thanked author for this post.
-
-
-
Klaas Vaak
AskWoody LoungerMarch 2, 2019 at 5:32 am #336037I have now said goodbye to Windows on both my laptops,what a relief, what peace of mind to have Linux instead. M$ managed to completely p*** me off during 2018 and this year.
So, I will not need MS-Defcon anymore to give me the green light to install patches, nor will I need to jump through hoops for a category B laptop. I will now only use the Linux forum here.
1x Linux Mint 19.1 | 1x Linux antiX
-
anonymous
GuestMarch 2, 2019 at 5:47 pm #336333KB4482887 has wrecked Remote Desktop Connections for me and my 6 PCs. When I minimize the window and then restore it, there is a high probability the window will be all one colour (usually black) and not other response…. if I wait a random amount of time, it may eventually work again. Or I can close it and reconnect.
-
anonymous
Guest -
anonymous
GuestMarch 3, 2019 at 8:24 pm #336712I [stupidly] went into Windows Update and checked for updates. I was interested in the fixes for Spectre with repoline. I had hoped they would make the machine more performant. And I feel like there has been a small improvement on the front, but the RDP issue is a major pain for how I work and use my network.
I didn’t notice the RDP issue at first (as I patched a remote target and tested it over RDP and the issue seems to be on the local side of the connection.) Of course the last place I patched was the local machine, which is when I realized I may have made a bad choice.
Also of note, I’ve had the Remote Desktop Connection app max my CPU (well one core of it) on a few occasions… tied to the endpoint not being responsive.
-
anonymous
Guest
-
-
-
-
anonymous
GuestMarch 2, 2019 at 8:40 pm #336360I’ve seen KB 4023057 reappear here and there for a little while, but I keep hiding them each time I see em. Suckers are trying to force 1809 on me by offering that KB, not on my watch. I hide the sucker so it won’t mess up my computer.
Edited for HTML and content. Please use text tab for copy/paste.
-
anonymous
GuestMarch 3, 2019 at 12:12 pm #336515KB 4023057 is a small application (not a patch) to test for free space/release space…
I got KB 4023057 6 times so far. I just uninstall the installed KB 4023057 and update the new KB 4023057. No boot required.
Edit to remove HTML. Please use the “Text” tab in the entry box when you copy/paste.
-
-
anonymous
GuestMarch 3, 2019 at 12:43 pm #336529 -
KWGuy
AskWoody PlusMarch 3, 2019 at 1:39 pm #336552When Patch Lady Susan joined this site, I doubled my annual donation. Having access to both Woody’s home user focused go-no go advice in combination with Susan’s patch specific advice is, for me, the “dream team” perfect combination. As a home user with “weak intermediate” technical skills, I rely on this site daily to keep the MS wolf from the door.
With that said, I tend to agree with other posters that confusion and mixed signals are becoming evident. For example, on the Master Patch List, between the headings “February Updates” and “Previous months”, it says “Okay to install updates at this time.” Yet, for specific 1803, w7, and w8.1 patches it advises “hold for now” and “not at this time”. I find this confusing and contradictory. Perhaps the answer to my confusion would be found in various posts and elsewhere, but I haven’t found it.
While I generally wait for Woody’s Defcon 3 before applying patches, occasionally time constraints necessitate getting a headstart on the six computers that I must update each month. And, when this occurs, I find the Master Patch List helpful in assessing the risk of patching early. And, yes, I am aware that the Patch Lady’s audience is directed more toward the business environment, but I also note that posters are often referred to the Master Patch List.
I fully understand the logic for Woody’s and Susan’s different audiences and therefore different time frames for the patching green light. I just wish to note that attention to clarity would be most helpful to the non-techies such as myself.
AskWoody is a fantastic site and is continuing to evolve in a most positive way. The MVP’s are great. Please accept my above comments in the respectful and constructive manner intended.
-
DrBonzo
AskWoody PlusMarch 3, 2019 at 2:05 pm #336576Given that the sentence in question is a different font and font size, I assume that sentence is just an editing issue.
In any case, it seems to me that at some point one needs to be interested in each individual update that one is considering installing. Even with a DefCon of 5, it’s conceivable that a patch exists for which there is an issue or issues. I always scroll down to the sections of the Master Patch List that addresses the individual patches to see what Ms Bradley has to say about them. If a patch looks good sometimes I’ll install it, but usually wait anyway for Woody’s pronouncement of DefCon3 or higher.
In somewhat different terms, while it’s nice to have one number that would apply to all patches, it just doesn’t seem possible to do that given the current state of MS patching; one simply needs to be considering each patch individually.
That’s just my 2 cents worth.
Edit: By the way, I consider myself to be a non-techie, and I would have difficulty dealing with a BSOD or something similar. So, I pay a lot of attention to each Win 7 (in my case) patch that comes down the pike and am very cautious about installing them.
Edit #2: It might have sounded above that I was denigrating the DefCon system, but that was certainly not my intent. I like, just as much as the next person, a one number system, and I rarely do any patching until Woody has issued DefCon 3 or higher. That occurrence, along with his Compterworld article are extremely useful. It also seems that while there are sometimes differences in recommendations between Woody’s system and Ms Bradley’s system in the first weeks following Patch Tuesday, that by week 3 or 4, they are in essential agreement. In a nutshell: I like having both systems.
-
OscarCP
MemberMarch 3, 2019 at 8:09 pm #336713Perhaps this is another reason, one that shows how careful one has to be before installing a patch, whatever the DEFCON might be, because there are many fine points for a particular user to consider that cannot be addressed with a single number:
In another thread someone asked about a problem with a German keyboard where, suddenly, that person no longer could write umlauts on top of ‘o’ and ‘u’. I answered that this could be because some patches come with a warning at it’s corresponding MS Web page, where it might say that, after applying the patch in question, it might be necessary to reinstall font packages. I have not heard back about this, therefore I do not know if that was the problem in this case, but it could well be.
So I think that it definitely pays to right-click on the name of each of the patches available to install listed in the Windows Update window, and then choose the “most information” option in the menu that this action opens. This will connect to the MS Web page explaining the uses of and problems with that particular patch. (At least this is possible to do with Windows 7.)
Ex-Windows user (Win. 98, XP, 7); since mid-2017 using also macOS. Presently on Monterey 12.15 & sometimes running also Linux (Mint).
MacBook Pro circa mid-2015, 15" display, with 16GB 1600 GHz DDR3 RAM, 1 TB SSD, a Haswell architecture Intel CPU with 4 Cores and 8 Threads model i7-4870HQ @ 2.50GHz.
Intel Iris Pro GPU with Built-in Bus, VRAM 1.5 GB, Display 2880 x 1800 Retina, 24-Bit color.
macOS Monterey; browsers: Waterfox "Current", Vivaldi and (now and then) Chrome; security apps. Intego AV
-
-
-
Bill C.
AskWoody PlusMarch 3, 2019 at 4:20 pm #336652Update/patch Report for February.
I jumped the gun last week prior to Defcon 4 due to upcoming vision surgery. Checked Susan Bradley’s Master Patch List and reporting here and on other sites, took precautions and prepared, and decided to go for it.
Desktop Windows 7Pro-64_SP1, No GWX or Telemetry, Group B for Monthly patches, WU for Office 2010 and .Net patches. Intel DX58SO2 w/i7-960 CPU, 12 GB Ram, 3 WD Black spinning HDD, wired networking.
I updated all the February Group B patches with no problems evident after a week of use. Office 2010 is fully patched with no negatives on Outlook, Excel or Word in current or legacy file formats. Firefox and HTTPS Everwhere updates resolved a system lockup issue that appeared to be centered on HTTPS Everywhere.
Laptop Lenovo Thinkpad Edge 440, 4th gen i5 with 8GB Ram and WD Black spinning HDD running Win7Pro_SP1 No GWX or Telemetry, Group B for Monthly patches, WU for Office 2010 and .Net patches. All updates as above without issue. No Wireless or Wired Ethernet issues.
While I download the updates from the AskWoody KB200003 article when they are released, I always re-download them the day of updating in case of re-releases. It appeared the monthly Security Only patch may have received an update mid-month.
Even updated Office for the Japanese dating, so if I get an invite to the Emperor’s ascension, I am able to reply properly. So far, no issues.
Hope this helps.
Disclaimer: As always, these are my results, I pulled the trigger after preparations and research. Your results may vary due to system and software configurations. If my decision(s) hosed my system(s) it would be my fault only, and not the fault of others.
-
OscarCP
MemberMarch 3, 2019 at 8:28 pm #336716I agree entirely with this statement:
Bill C writes: ” Your results may vary due to system and software configurations. ” And would add to that: if a patch appears to have caused some harm, it is not necessarily the patch that caused it, but the state of things on the PC when one clicks “Install” that might be responsible for what happens. This makes it tricky to determine when it is really OK for oneself to go and install a patch, even if no problems have been reported and the DEFCON is glowing bright at the top of its scale. So patching must be, of necessity, always something of a gamble. And one that is not especific to MS Windows, but to any OS out there. Every choice we make in life is always a gamble, and wisdom is knowing how to place one’s bets to improve one’s chances of success — in whatever one intends to do. This might be something worthy of further discussion, somewhere in Woody’s.
Ex-Windows user (Win. 98, XP, 7); since mid-2017 using also macOS. Presently on Monterey 12.15 & sometimes running also Linux (Mint).
MacBook Pro circa mid-2015, 15" display, with 16GB 1600 GHz DDR3 RAM, 1 TB SSD, a Haswell architecture Intel CPU with 4 Cores and 8 Threads model i7-4870HQ @ 2.50GHz.
Intel Iris Pro GPU with Built-in Bus, VRAM 1.5 GB, Display 2880 x 1800 Retina, 24-Bit color.
macOS Monterey; browsers: Waterfox "Current", Vivaldi and (now and then) Chrome; security apps. Intego AV1 user thanked author for this post.
-
-
Anton Karlan
AskWoody Lounger -
b
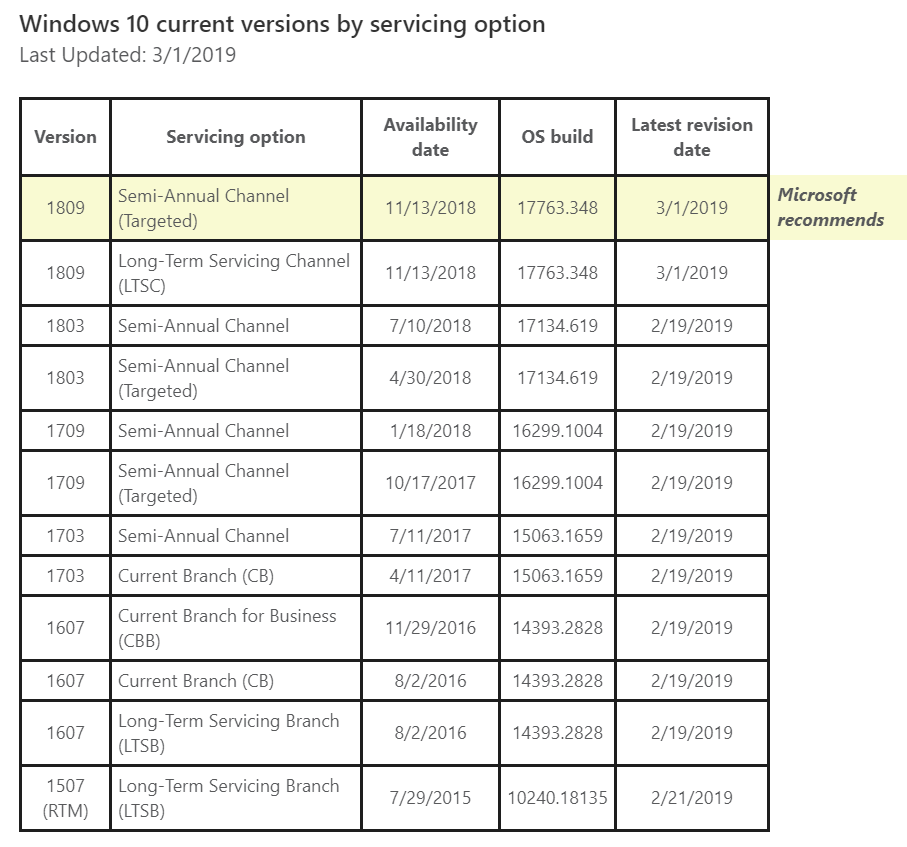
AskWoody_MVPMarch 4, 2019 at 1:42 am #336767The 3/1/2019 there is just the date of the last build number change (due to a cumulative update).
1809 has been marked “Microsoft recommends” there for about three months against Semi-Annual Channel (Targeted): https://web.archive.org/web/20181211220302/https://docs.microsoft.com/en-us/windows/windows-10/release-information
In the past “ready for business” has been indicated by a line being added for Semi-Annual Channel (i.e. NOT Targeted) with a new date when a version is released for that channel, which used to be called Current Branch for Business (see the CBB entry for 1607 and SAC entries for 1703, 1709 and 1803). That should still happen for 1809 (but will not for 1903 due to Windows Update for Business and the retirement of SAC-T.)
3 users thanked author for this post.
-
-
radosuaf
AskWoody LoungerMarch 4, 2019 at 1:51 am #336769Ahhh, I updated to 1809 and KB4482887 in the hope to regain lost performance but it turns out now CPU benchmarks are… 2.6% lower thn on 1803. Go figure :). I guess I’ll have to wait until it’s “enabled on my configuration”.
Fractal Design Pop Air * Thermaltake Toughpower GF3 750W * ASUS TUF GAMING B560M-PLUS * Intel Core i9-11900K * 4 x 8 GB G.Skill Aegis DDR4 3600 MHz CL16 * ASRock RX 6800 XT Phantom Gaming 16GB OC * XPG GAMMIX S70 BLADE 1TB * SanDisk Ultra 3D 1TB * Samsung EVO 840 250GB * DVD RW Lite-ON iHAS 124 * Windows 10 Pro 22H2 64-bit Insider * Windows 11 Pro Beta Insider -
anonymous
GuestMarch 4, 2019 at 2:06 pm #337099 -
woody
Manager -
anonymous
GuestMarch 4, 2019 at 3:31 pm #337160The BSODs are occurring intermittently. Some machines are running for six hours before crashing, others after only one hour. Most however haven’t had any crashes. They are all identical hardware and software-wise. I’m currently testing some machines with newer Intel graphics drivers to rule them out as a possible cause (previous drivers were from 2016). Tomorrow I’ll roll back the update on some other machines and keep them on the January cumulative update for the time being.
-
anonymous
Guest -
anonymous
Guest
-
-
-
WildBill
AskWoody PlusMarch 4, 2019 at 5:20 pm #337243Do both rollups have to be installed to cause BSOD, or can either 1 cause it? Referring to KB4487000 (Win8.1 AKA Group A) & KB4487080 (.NET Framework)… On Group B, but if .NET Framework causes BSOD on its own, will skip February’s.
Bought a refurbished Windows 10 64-bit, currently updated to 22H2. Have broke the AC adapter cord going to the 8.1 machine, but before that, coaxed it into charging. Need to buy new adapter if wish to continue using it.
Wild Bill Rides Again... -
Hopper15
AskWoody Plus -
anonymous
GuestMarch 5, 2019 at 9:56 pm #337906We are BSOD as well with Feb updates.
All Windows 8.1. We only run x64.
Intermittent blue screen related to win32k.sys.
Also 1 machine that restarted, after apply Feb updates, and fails to load Windows again after. A mouse pointer on the screen that you move around and that’s it. Restart again and you get into Windows can’t start recovery stuff. Three hours of bitlocker recovery keys and attempt fixes including restore point (which failed), and we ended up giving up and rebuilding it.
Assuming it is KB4487000 causing it.
I see there is an KB4487000 that applies to Server 2012 R2 as well. Pulling that as well for safety.
-
Hopper15
AskWoody PlusMarch 6, 2019 at 12:50 am #337929We are BSOD as well with Feb updates. All Windows 8.1. We only run x64. Intermittent blue screen related to win32k.sys. Also 1 machine that restarted, after apply Feb updates, and fails to load Windows again after. A mouse pointer on the screen that you move around and that’s it. Restart again and you get into Windows can’t start recovery stuff. Three hours of bitlocker recovery keys and attempt fixes including restore point (which failed), and we ended up giving up and rebuilding it.
Assuming it is KB4487000 causing it. I see there is an KB4487000 that applies to Server 2012 R2 as well. Pulling that as well for safety.
If you don’t mind me asking but who’s we?
1 user thanked author for this post.
-
anonymous
GuestMarch 6, 2019 at 10:07 pm #338377We = New Zealand Automobile Association. http://www.aa.co.nz.
Regards, Mike. Computer Operations Manager.
1 user thanked author for this post.
-
anonymous
GuestMarch 6, 2019 at 10:13 pm #338379And to stop possible confusion regarding “All Windows 8.1” above. Should be that we are only getting faults on Windows 8.1 x64. Was picked up in the test deployment of 55 computers, before hitting 1,200 prod machines. Problem occur on 2 out of the 55 computers. Why just those 2 is still unknown. I hope clearer
-
-
anonymous
Guest -
Mr. Natural
AskWoody Lounger -
anonymous
GuestMarch 14, 2019 at 12:31 am #341449Problem with KB4487000 is that it is a cumulative update.
If Microsoft don’t address the problem, it will be in the March and subsequent monthly updates as well. Am waiting for Microsoft to confirm the issue and advise they have fixed it.
Internet search each morning on this, waiting for someone authoritive answer to address / answer this. Basically means very high risk of deployments of Windows 8.1 cumulative updates, until the win32k.sys BSOD introduced by KB4487000 is confirmed as fixed.
Maybe they will fix it in a future update and never acknowledge there was ever a problem. (Can you feel the vibe from me on this. Really frustrating.)
-
-
anonymous
GuestMarch 18, 2019 at 6:26 am #342816Just fresh installed 8.1 Yesterday! My PC was designed around being 8.1 centric; 4th gen i7, mobo with ‘8.1’ features, etc. I turned off Intel Graphics due to me having an GTX 960. What is the possibility this will cause me BSODs? I love 8.1 but if this is gonna be a problem then I have to go to 10.
-
Paul T
AskWoody MVPMarch 18, 2019 at 8:44 am #342842Just fresh installed 8.1 . What is the possibility this will cause me BSODs?
Wait for the Defcon status to improve, then make an image backup and patch. If you get a BSOD, restore the image and then let us know.
cheers, Paul
-
anonymous
Guest -
Elly
AskWoody MVP -
anonymous
Guest
-
-
Viewing 33 reply threads -

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Windows 11 Insider Preview build 26200.5570 released to DEV
by
joep517
6 hours, 21 minutes ago -
Windows 11 Insider Preview build 26120.3941 (24H2) released to BETA
by
joep517
8 hours, 9 minutes ago -
Windows 11 Insider Preview Build 22635.5305 (23H2) released to BETA
by
joep517
8 hours, 11 minutes ago -
No April cumulative update for Win 11 23H2?
by
Peobody
10 hours, 29 minutes ago -
AugLoop.All (TEST Augmentation Loop MSIT)
by
LarryK
8 hours, 42 minutes ago -
Boot Sequence for Dell Optiplex 7070 Tower
by
Serge Carniol
23 hours, 45 minutes ago -
OTT Upgrade Windows 11 to 24H2 on Unsupported Hardware
by
bbearren
1 day, 3 hours ago -
Inetpub can be tricked
by
Susan Bradley
1 day, 4 hours ago -
How merge Outlook 2016 .pst file w/into newly created Outlook 2024 install .pst?
by
Tex265
8 hours, 2 minutes ago -
FBI 2024 Internet Crime Report
by
Alex5723
1 day, 7 hours ago -
Perplexity CEO says its browser will track everything users do online
by
Alex5723
18 hours, 54 minutes ago -
Login issues with Windows Hello
by
CWBillow
1 day, 18 hours ago -
How to get into a manual setup screen in 2024 Outlook classic?
by
Tex265
1 day, 6 hours ago -
Linux : ARMO rootkit “Curing”
by
Alex5723
2 days, 5 hours ago -
Employee monitoring app leaks 21 million screenshots in real time
by
Alex5723
2 days, 5 hours ago -
Google AI is now hallucinating idioms
by
Alex5723
2 days, 6 hours ago -
april update
by
69800
10 hours, 42 minutes ago -
Windows 11 Insider Preview build 27842 released to Canary
by
joep517
2 days, 7 hours ago -
Quick Fix for Slowing File Explorer
by
Drcard:))
2 days, 7 hours ago -
WuMgr not loading?
by
LHiggins
1 day, 3 hours ago -
Word crashes when accessing Help
by
CWBillow
1 day, 11 hours ago -
New Microsoft Nag — Danger! Danger! sign-in to your Microsoft Account
by
EricB
2 days, 7 hours ago -
Blank Inetpub folder
by
Susan Bradley
2 days, 4 hours ago -
Google : Extended Repair Program for Pixel 7a
by
Alex5723
2 days, 17 hours ago -
Updates seem to have broken Microsoft Edge
by
rebop2020
2 days, 4 hours ago -
Wait command?
by
CWBillow
2 days, 10 hours ago -
Malwarebytes 5 Free version manual platform updates
by
Bob99
3 days ago -
inetpub : Microsoft’s patch for CVE-2025–21204 introduces vulnerability
by
Alex5723
3 days, 6 hours ago -
Windows 10 finally gets fix
by
Susan Bradley
3 days, 15 hours ago -
AMD Ryzen™ Chipset Driver Release Notes 7.04.09.545
by
Alex5723
3 days, 17 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.

 most patches there seem to fix this japanese thingamajigs… do i really need it?
most patches there seem to fix this japanese thingamajigs… do i really need it?