Gregg Keizer has a new article in Computerworld, Windows 7 takes biggest performance hit from emergency Meltdown, Spectre updates. It relies heavily o
[See the full post at: The Meltdown/Spectre patches will cause performance hits — but how much, and to whom?]

|
Patch reliability is unclear, but widespread attacks make patching prudent. Go ahead and patch, but watch out for potential problems. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
-
The Meltdown/Spectre patches will cause performance hits — but how much, and to whom?
Home » Forums » Newsletter and Homepage topics » The Meltdown/Spectre patches will cause performance hits — but how much, and to whom?
- This topic has 40 replies, 17 voices, and was last updated 7 years, 3 months ago.
Tags: benchmarks Meltdown performance Spectre
AuthorTopicwoody
ManagerJanuary 11, 2018 at 9:21 am #158470Viewing 22 reply threadsAuthorReplies-
_Reassigned Account
AskWoody LoungerJanuary 11, 2018 at 9:51 am #158484I did not run too much in tests. Ran JetStream on my older broadwell and Hazwell and really did not notice much. I think anything with heavy I/O with memory will see more issues. Most doing simple tasks probably don’t demand much from their hardware anyway. My only real observation of slowing was some in boot times. I wonder given that many PC makers have not pushed bios updates how this will add to the performance questions?
-
anonymous
Guest -
anonymous
GuestJanuary 11, 2018 at 11:21 am #158511Once these Windows Updates, (and possibly firmware updates) and browser updates for Meltdown and Spectre have been installed, there is not much that a consumer does that will inform the user that the performance has been degraded or not. The only application exception would backup or backup and recovery. There is not much else that consumers normally do that would effect the performance of a system other than this. Doing email, office based processes and/or searching the web do not do CPU or I/O intensive operations.
Of course there are some consumers who take their work home and that is different. They may be using a program that does a lot of analysis that relies on a high level of system performance. If one is doing this, they most likely already have max. RAM and a business grade system. I think this needs to be separated out from what the average consumer will see.
I get the impression that our browsers will suffer a more significant performance impact than our CPUs. Time will tell.
-
lurks about
AskWoody LoungerJanuary 11, 2018 at 11:30 am #158519My interpretation of the effects are:
For home/SOHO users; generally minor effects for most activities. Those that do serious video editing, drafting, etc. might see some slow down on those specific applications. If there is any effects it is likely due to the OS upgrades.
For office drones; generally the same as home/SOHO though more are likely to serious video editing, drafting, etc.
For servers; will see some slow down with how much varying rather wildly based on server loads and type.
-
-
satrow
AskWoody MVPJanuary 11, 2018 at 12:26 pm #158525Jampe’s T440s graph/figures on W10 (shown in the the full post and linked to elsewhere here today) looks very odd, original benchmark SSD figures look way too high for SSD/M.2 of that era (Lenovo only sold that range with 16/32GB caching drives in the M.2 slot, surely if it was PCIE connected and therefore on a bus that could double SATA 3 data throughput, it would have been highly sought after in 2013/4) yet the later drive benchmarks look fine for a SATA 3 bus SSD.
Did the patch break the Optimus GPU switching, that’s what the D2D GPU results look like.
Many of the 1st post-patch benchmarks minor dips in performance could be down to rushing the job, not allowing W10 to stabilise and Post-boot/patch Scheduled Tasks to complete, the last 2 benchmarks look very close. (I recall checking one of the W7 Public Betas for post-boot Scheduled Tasks, the last one was due ~16:30 minutes after Boot, iirc.)
-
anonymous
GuestJanuary 11, 2018 at 1:43 pm #158550satrow said:
Did the patch break the Optimus GPU switching, that’s what the D2D GPU results look like.If Meltdown KB patch for Win OS can & did indeed break GPU switching for dual-GPU systems, does that mean that user is stuck on either the integrated GPU (Intel), or the discrete GPU (Nvidia or AMD) ?
Would uninstalling the KB patch revert the situation ?
-
satrow
AskWoody MVPJanuary 11, 2018 at 6:18 pm #158626The report is too sparse to discover anything, no uptime pre- patching (it’s W10, were other patches also applied?); no patch, reboot, rest, reboot to ensure everything was patched correctly; only one before test cf. 3 tests afterwards.
Way too many possible variables.
No reboot to a previously cloned image to check again, no rollback or uninstall and fresh tests to check whether the original performance had returned.
Would reverting the patch return the performance? – we simply don’t know, I haven’t seen any detailed posts on this aspect yet.
-
-
-
anonymous
GuestJanuary 11, 2018 at 1:40 pm #158546A comment from user puppy at the above-highlighted Intel Support forum:
The only solution is that Microsoft delivers the updated CPU microcode via Windows (7, 8.1 and 10) Update and Intel should push Microsoft hard to do that. Hardware vendors aren’t reliable there at all.
Disregarding whether MS & Intel are agreeable or not, is the above method technically possible ?
On a related note, another user comment in the same Intel thread posted his e-chat with Intel Support regarding supplying a firmware fix for Dec 2017’s Intel ME bug. Intel support told him that his CPU model is no longer supported & “recommend[ed him] to get a new system”.
-
technovice
AskWoody LoungerJanuary 11, 2018 at 3:23 pm #158570Hey folks, a naive question, trying to figure out the Meltdown/Spectre thing for my 64-bit OS, Win7 Pro, Intel 2 Duo CPU E8400 @3.0 GHz. I keep reading that if I install the patches, the performance of my machine possibly slows by up to 30%. So what happens if I don’t install the patches? Thanks
-
MrBrian
AskWoody_MVPJanuary 11, 2018 at 7:18 pm #158648From Intel: Intel Security Issue Update: Initial Performance Data Results for Client Systems (January 10)
2 users thanked author for this post.
-
radosuaf
AskWoody LoungerJanuary 12, 2018 at 2:10 am #158723Why does this show that W7 after the patch on 6th gen is actually quicker than W10, contrary to what MS says?
Fractal Design Pop Air * Thermaltake Toughpower GF3 750W * ASUS TUF GAMING B560M-PLUS * Intel Core i9-11900K * 4 x 8 GB G.Skill Aegis DDR4 3600 MHz CL16 * ASRock RX 6800 XT Phantom Gaming 16GB OC * XPG GAMMIX S70 BLADE 1TB * SanDisk Ultra 3D 1TB * Samsung EVO 840 250GB * DVD RW Lite-ON iHAS 124 * Windows 10 Pro 22H2 64-bit Insider * Windows 11 Pro Beta Insider1 user thanked author for this post.
-
-
MrBrian
AskWoody_MVPJanuary 11, 2018 at 7:21 pm #1586513 users thanked author for this post.
-
OscarCP
MemberJanuary 11, 2018 at 8:04 pm #158662I think the good news about Firefox must apply now also to Waterfox, as yesterday I received and installed the upgrade to WF 56.0.2 and that includes the Firefox patch.
Ex-Windows user (Win. 98, XP, 7); since mid-2017 using also macOS. Presently on Monterey 12.15 & sometimes running also Linux (Mint).
MacBook Pro circa mid-2015, 15" display, with 16GB 1600 GHz DDR3 RAM, 1 TB SSD, a Haswell architecture Intel CPU with 4 Cores and 8 Threads model i7-4870HQ @ 2.50GHz.
Intel Iris Pro GPU with Built-in Bus, VRAM 1.5 GB, Display 2880 x 1800 Retina, 24-Bit color.
macOS Monterey; browsers: Waterfox "Current", Vivaldi and (now and then) Chrome; security apps. Intego AV1 user thanked author for this post.
-
anonymous
GuestJanuary 11, 2018 at 8:16 pm #158663I think there needs to be a better understanding of what patches are being associated with the potential performance hits. There are two different vulnerabilities here with different requirements. Users are having to deal with fixes for some hardware components, firmware and software.
The last I heard was that the most noticeable known performance hit will be from the firmware update, which is for Spectre. Meltdown was addressed in the OS(s) and the performance hit was minimal except for certain high intensity workloads.
The next round of software fixes will be whatever needs to be done to protect the operations that get performed in browsers. Google is expecting a noticeable performance hit, though testing has not yet completed. Microsoft has said that IE and Edge have already been patched in January with no specific statements on performance. Apple is totally tight lipped – no surprise there. Linux is updating the penguin websites when they get feedback on their fixes. Performance varies – lots of distros to cover.
Some experts are expecting a bevy of fixes over time, for Spectre. All these potential band-aids, glue and string will add weight and complexity. Performance has to suffer.
-
Noel Carboni
AskWoody_MVPJanuary 11, 2018 at 9:03 pm #158673I have all the data I need pre-patch about how much I/O throughput my server system can achieve. I just need to find enough assurance that unpatching a system (i.e., reverting a Windows Update) can restore dire performance losses.
Many articles seem to be downplaying I/O throughput for “typical desktop workloads”, but I don’t believe them! Even just sitting in front of a system typing, I/O is what holds back virtually all computers from doing what you want them to do ASAP. It’s CERTAINLY what a server needs to do best! I suspect any loss of I/O speed is going to affect responsiveness in ways you can sense.
Users of older chips, and those with I/O-intensive workloads, may have to consider things more carefully. I’m sure that in due course we’ll see more numbers from older processors, but Microsoft’s warning of noticeable performance decreases paints a grim picture.
SSDs have kicked I/O speeds up a lot lately – solid state storage is the single biggest reason why modern systems – servers or desktops – run rings around most of those from 5+ years ago. A patch that knocks the I/O throughput back to a much lower value is nothing to be taken lightly!
The more I research the patches the more disappointed I find myself becoming.
What price security?
-Noel
3 users thanked author for this post.
-
Noel Carboni
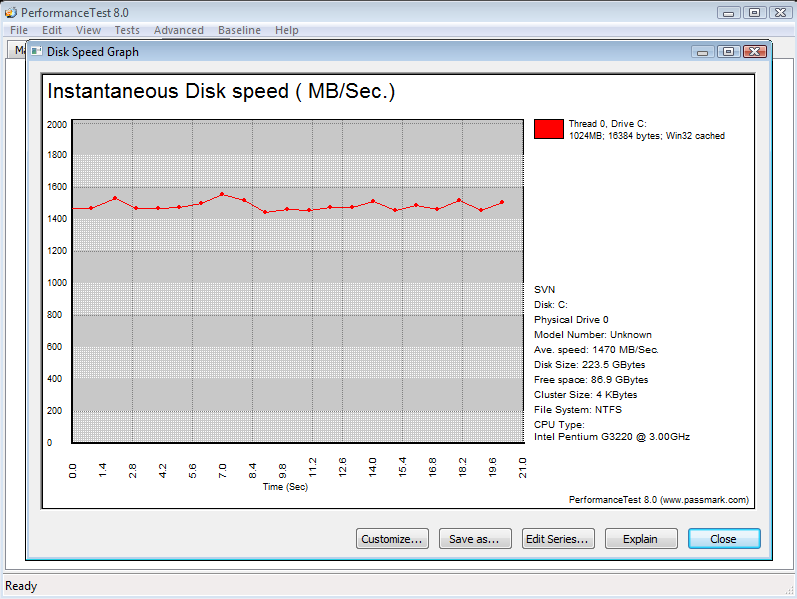
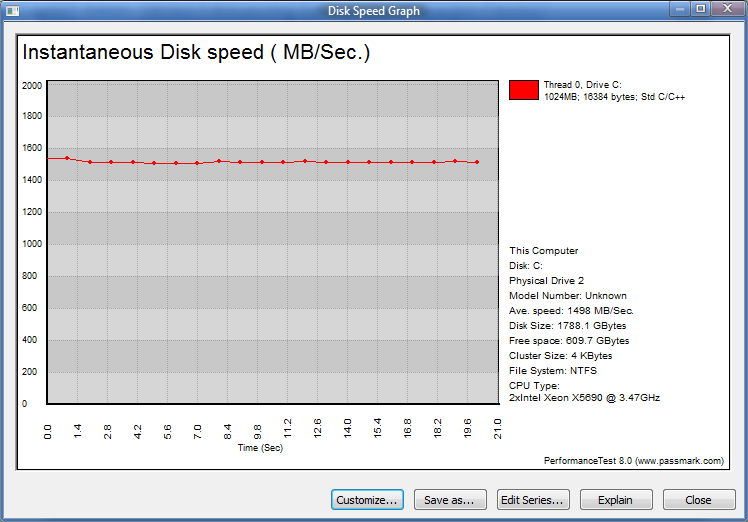
AskWoody_MVPJanuary 11, 2018 at 10:36 pm #158695The Passmark PerformanceTest benchmark actually has some very good Advanced > Disk testing capability. It creates a simulated workload with combined reads and writes, and I have found it to be a VERY good indication of how well a system actually runs.
Examples of the Advanced > Disk “Workstation” test results:
-Noel
1 user thanked author for this post.
-
Jan K.
AskWoody LoungerJanuary 11, 2018 at 11:24 pm #158704I have all the data I need pre-patch about how much I/O throughput my server system can achieve. I just need to find enough assurance that unpatching a system (i.e., reverting a Windows Update) can restore dire performance losses…
But… but… should reverting go haywire, then simply format the system disc and restore from last good system backup??
If you talk burning BIOS, then you may be in “trouble” though. This depends on mb, as I’ve been able to downgrade my Asus/Ami years ago…
Looking forward to your adventure!
Btw. no degrading registered here, fwiw.
2 users thanked author for this post.
-
Noel Carboni
AskWoody_MVPJanuary 12, 2018 at 9:09 am #158798Indeed, that can work, and I have daily system image backups, but it would mean the system would be offline for up to several hours. This particular machine is in a critical role and even a few hours downtime would be intrusive unless done at time of lowest usage (e.g., 3 am). Thanks Intel and Microsoft.
Thanks for sharing your experience about not registering degradation.
-Noel
-
Jan K.
AskWoody LoungerJanuary 12, 2018 at 3:35 pm #158897Well, you can sleep, when you get old!
But looking at the Intel performance link in post #158648, some processors actually gets faster from the patching!?
And doesn’t our cpus have so much headroom anyway, that the (small) slowdowns shown in Intel’s spreadsheet, easily could be evened out by adding a tiny bit of overclocking? My old i7-930 rarely touch 5 or 10% utilization… and it’s running at standard speed, leaving quite a big extra performance headroom for me to exploit.
From my POV there’s jst too much FUD and panic regarding this eventual slowdown thing… ymmv and all that.
Btw. the Passmark Performance Benchmark program can be downloaded for a free 28 day trial, if anyone wants to run their system through it’s paces.
Can be downloaded here… https://www.passmark.com/products/pt.htm
1 user thanked author for this post.
-
-
-
anonymous
GuestJanuary 12, 2018 at 12:12 am #158686Hm, I neglected to run Passmark PerformanceTest until after I’d already installed KB4056897. So I can tell you that my CPU Mark score has dropped from the 11643 it once enjoyed to 10800 now, and my Disk Mark score from 5089 to 5014; but those ‘before’ scores are from some time ago, and I’m not sure how much of that performance loss is due to this patch, and how much is simply from system age or other, older security updates.
What I can say with certainty is that just for laughs, I re-ran the old WEI assessment after I installed the patch. Somewhat to my surprise, my CPU stayed right at 7.8 out of a possible 7.9 just as it always has been, but my SSD’s score dropped rather dramatically from 7.9 to 5.9.
System specs, for the record:
CPU: Intel Core i7-4790K
Motherboard: GIGABYTE GA-Z97X-Gaming 3
GPU: EVGA GeForce GTX 1070 FTW GAMING ACX 3.0, 08G-P4-6276-KR
Memory: G.SKILL Ripjaws X 32GB (4 x 8GB) DDR3 2133 (PC3 17000) F3-2133C10Q-32GXM
SSD: SAMSUNG 850 EVO 500GB SATA MZ-75E500B/AM
OS: Windows 7 SP1 64-bit OEMI haven’t noticed much, if any, difference in actual use. But I’m suddenly feeling a whole lot better about what seemed, some two years ago, like the extravagance of buying more computer than I thought I really needed.
-
Ascaris
AskWoody MVPJanuary 12, 2018 at 1:36 am #158721Wow…. 7.9 to 5.9 is brutal. That really sounds excessive, especially given how relatively slight the other disk benchmark impacts were. Perhaps the patch interferes with the ability of WEI to accurately gauge the disk performance?
The Windows 7 performance scale is logarithmic, so a loss of two full points is quite severe. My Core 2 Duo laptop scored 6.1 on the Windows 7 CPU index, and your Haswell i7 is only 1.7 points higher than that… and your disk performance dropped by an even larger margin than that. It doesn’t seem realistic.
Dell XPS 13/9310, i5-1135G7/16GB, KDE Neon 6.2
XPG Xenia 15, i7-9750H/32GB & GTX1660ti, Kubuntu 24.04
Acer Swift Go 14, i5-1335U/16GB, Kubuntu 24.04 (and Win 11) -
anonymous
GuestJanuary 12, 2018 at 2:19 pm #158882Yeah, it does seem like an awfully big drop. I’m not aware of any other incidents that could have affected the drive, and there are no sign of any problems in its SMART attributes (not that those are particularly reliable, I know.) I may crack my case later and make sure all the cables are properly seated, just to be safe.
As for the Core 2 Duo vs. i7 difference, I’m wondering if that’s a limitation in WEI itself. The Haswell refresh post-dates even the release of Windows 8, which bumped the top of the scale up to 9.9. I’ve found a reported score of 8.5 for a 4790k from a Windows 8 user. Windows 7’s WEI may just not be calibrated to properly assess a processor of that era.
-
Jan K.
AskWoody Lounger
-
-
-
Ascaris
AskWoody MVPJanuary 12, 2018 at 1:28 am #158720If you talk burning BIOS, then you may be in “trouble” though. This depends on mb, as I’ve been able to downgrade my Asus/Ami years ago…
That’s the concern right there. Some of them won’t allow downgrading, which is really dumb. As always, one size does not fit all, and there are reasons for downgrading at times, like this right here. I’ll be checking this out before trying the firmware upgrade on my 2017 manufactured laptop.
Dell XPS 13/9310, i5-1135G7/16GB, KDE Neon 6.2
XPG Xenia 15, i7-9750H/32GB & GTX1660ti, Kubuntu 24.04
Acer Swift Go 14, i5-1335U/16GB, Kubuntu 24.04 (and Win 11)2 users thanked author for this post.
-
Noel Carboni
AskWoody_MVPJanuary 12, 2018 at 9:18 am #158801Ideally shouldn’t these patches come with a super user-friendly UI that allows you to just select a radio button for “no patch” vs. “patch” to facilitate testing and risk/reward/downside assessment?
Should we accept that there is only a one-way, ratcheting way forward, and that a failed patch just leaves us with a degraded or failed computer system? At one time customers demanded control; those needs haven’t vanished.
-Noel
-
Bill C.
AskWoody PlusJanuary 12, 2018 at 5:32 pm #158926My old Intel Board, an old X58 BIOS board, did not “support” downgrades, but it could be done. I never had to.
A newer build with an MSI board, Z87-G41 PC Mate with an i5-4670K and UEFI, said it did not.
When doing a rollback, it usually took using a bootable media updater and not the easy Windows installer, which warned that you had a newer version.
I suspect with this whole issue, across so many CPUs, that for newer motherboards there may be more flexibility, IF you wait for the early adopters to discover the issues and fixes to be issued for the Gen 1 ‘fixes’. I do remember one of the BIOS issued for my Intel board was problematic for some users (lost features and some bricks) and was later withdrawn, but those who did not update right away or were unaware of an update received the better version without incident. Of course there was not media frenzy over routine BIOS updates like the Meltdown/Spectre story.
Readers here have inquiring minds. Do research and then wait for the panic to subside a bit. Check your OEM forums, and remember that the happy folks are not usually posting that their update went smoothly unless they are more hands-on type than the average user.
In a nutshell, do research for your specific hardware, and follow the AskWoody DefCon.
If you are concerned about a slowdown, and are using spinning HDDs, moving to an SSD may speed up whatever slowdown you are noticing. Of course this is task dependent.
-
-
anonymous
Guest -
PKCano
ManagerJanuary 12, 2018 at 5:52 am #158751The Security only patches beginning in Oct 2016 should install OK. They are available in the Knowledge Base at AKB2000003.
CAUTION: I would hold off on the Jan. 2018 updates, particularly if you have an AMD processor, as they are causing problems.You will also need the latest IE11 Cumulative Update, also available in AKB2000003. Since they are cumulative, you only need the latest one.
If you do not intend to install the Monthly Rollups, you will need to HIDE them successively back to Oct 2016 in Windows Update. After doing that, a search for updates will give you the list of available updates. If you don’t want the telemetry updates, they are listed in AKB2000003 also. HIDE any ones you don’t want to install and install the rest that are checked by default. You may need to repeat the search/hide/install procedure till you are up to date.
-
anonymous
Guest
-
-
-
David F
AskWoody PlusJanuary 12, 2018 at 6:36 am #158765Just seen this on the The Register for those of use with older chips (I have a Haswell E myself)
1 user thanked author for this post.
-
anonymous
Guest -
Carl D
AskWoody LoungerJanuary 12, 2018 at 4:14 pm #158906Just checked and found a new BIOS update (F9b – Update CPU Microcode is the description) for my Gigabyte B250M-D3H motherboard running Windows 7 Professional 64bit on Kaby Lake.
I haven’t installed any of this month’s Windows Updates yet and I’m a bit wary about updating the BIOS at this stage (I don’t have any problems updating the BIOS on this board, I’ve already done it several times since I bought it about 8 months ago).
Might just wait a few days before “taking the plunge”. There may even be another BIOS update issued while I’m waiting. Had lots of them with this board so far – it came with F2 out of the box and I’m running F8 at the moment.
1 user thanked author for this post.
-
OscarCP
MemberJanuary 12, 2018 at 4:23 pm #158910Question:
Is the editing of the Registry Key by the AV software (or by hand, for the brave, the few) also required before installing the E 11 January security-only cumulative update?
Or is it only for the other security updates?
Ex-Windows user (Win. 98, XP, 7); since mid-2017 using also macOS. Presently on Monterey 12.15 & sometimes running also Linux (Mint).
MacBook Pro circa mid-2015, 15" display, with 16GB 1600 GHz DDR3 RAM, 1 TB SSD, a Haswell architecture Intel CPU with 4 Cores and 8 Threads model i7-4870HQ @ 2.50GHz.
Intel Iris Pro GPU with Built-in Bus, VRAM 1.5 GB, Display 2880 x 1800 Retina, 24-Bit color.
macOS Monterey; browsers: Waterfox "Current", Vivaldi and (now and then) Chrome; security apps. Intego AV1 user thanked author for this post.
-
Jan K.
AskWoody LoungerJanuary 12, 2018 at 8:11 pm #158969Redhat has performed test with updated kernels and microcode fixes… https://access.redhat.com/articles/3307751
In order to provide more detail, Red Hat’s performance team has categorized the performance results for Red Hat Enterprise Linux 7, (with similar behavior on Red Hat Enterprise Linux 6 and Red Hat Enterprise Linux 5), on a wide variety of benchmarks based on performance impact:
Highly cached random memory, with buffered I/O, OLTP database workloads, and benchmarks with high kernel-to-user space transitions are impacted between 8-19%. Examples include OLTP Workloads (tpc), sysbench, pgbench, netperf (< 256 byte), and fio (random I/O to NvME).
Modest: 3-7% – Database analytics, Decision Support System (DSS), and Java VMs are impacted less than the “Measurable” category. These applications may have significant sequential disk or network traffic, but kernel/device drivers are able to aggregate requests to moderate level of kernel-to-user transitions. Examples include SPECjbb2005, Queries/Hour and overall analytic timing (sec).
Small: 2-5% – HPC (High Performance Computing) CPU-intensive workloads are affected the least with only 2-5% performance impact because jobs run mostly in user space and are scheduled using cpu-pinning or numa-control. Examples include Linpack NxN on x86 and SPECcpu2006.
Minimal: Linux accelerator technologies that generally bypass the kernel in favor of user direct access are the least affected, with less than 2% overhead measured. Examples tested include DPDK (VsPERF at 64 byte) and OpenOnload (STAC-N). Userspace accesses to VDSO like get-time-of-day are not impacted. We expect similar minimal impact for other offloads.
NOTE: Because microbenchmarks like netperf/uperf, iozone, and fio are designed to stress a specific hardware component or operation, their results are not generally representative of customer workload. Some microbenchmarks have shown a larger performance impact, related to the specific area they stress.
-
Ascaris
AskWoody MVPJanuary 13, 2018 at 1:21 am #159022No word on the platform used for testing? Seems like it might be important.
Dell XPS 13/9310, i5-1135G7/16GB, KDE Neon 6.2
XPG Xenia 15, i7-9750H/32GB & GTX1660ti, Kubuntu 24.04
Acer Swift Go 14, i5-1335U/16GB, Kubuntu 24.04 (and Win 11) -
Jan K.
AskWoody LoungerJanuary 13, 2018 at 3:44 pm #159186From the link:
“Red Hat has tested complete solutions, including updated kernels and updated microcode, on variants of the following modern high volume Intel systems: Haswell, Broadwell, and Skylake.”
And from their to-do list (assuming Microsoft will do the same):
“Performance characterizations and development of optimizations will be an ongoing effort that may result in subsequent kernel enhancements and updated reports. In addition, we are actively working with our technology partners to reduce or eliminate these performance impacts as quickly as possible.”
But there’s one thing, that Microsoft won’t do, but Linux will… update each and all processors!
Here’s the list of Intel’s microcode update for Linux
So if you use an “old” cpu and want it patched, go Linux. Price? Free.
If you go Microsoft, upgrade motherboard, cpu and go Windows 10. Price? $1000 for my setup…
-
-
-
Jan K.
AskWoody LoungerJanuary 13, 2018 at 3:10 am #159029Ideally shouldn’t these patches come with a super user-friendly UI that allows you to just select a radio button for “no patch” vs. “patch” to facilitate testing and risk/reward/downside assessment?
Some has tuning capabilities besides just simple on/off…
“Red Hat Enterprise Linux settings for these patches default to maximum security. Recognizing, however, that customers’ needs vary, these patches may be enabled or disabled at boot time or at runtime. As a diagnostic approach, some customers may want to measure results on the patched kernel in configurations with and without the CVE patches enabled. In order to facilitate this, the kernel team has added dynamic tunables to enable/disable most of the CVE microcode/security patches through tunables and/or by building new tuned profiles.”
Snipped from https://access.redhat.com/articles/3307751
And here’s some info… “Controlling the performance impact“
-
Kirsty
ManagerJanuary 16, 2018 at 2:00 am #159571Steve Gibson, Gibson Research Corp has released a freeware tool to:
Easily examine and understand any Windows
system’s hardware and software capability to
prevent Meltdown and Spectre attacks.Just hours after release, it has already had over 2000 downloads!

Viewing 22 reply threads -

Plus Membership
Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Get Plus!
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Search Newsletters
Search Forums
View the Forum
Search for Topics
Recent Topics
-
Securing Laptop for Trustee Administrattor
by
PeachesP
1 hour, 3 minutes ago -
The local account tax
by
Susan Bradley
14 minutes ago -
Recall is back with KB5055627(OS Build 26100.3915) Preview
by
Alex5723
3 hours, 35 minutes ago -
Digital TV Antenna Recommendation
by
Win7and10
3 hours, 10 minutes ago -
Server 2019 Domain Controllers broken by updates
by
MP Support
15 hours, 27 minutes ago -
Google won’t remove 3rd party cookies in Chrome as promised
by
Alex5723
17 hours, 6 minutes ago -
Microsoft Manager Says macOS Is Better Than Windows 11
by
Alex5723
20 hours, 18 minutes ago -
Outlook (NEW) Getting really Pushy
by
RetiredGeek
9 hours, 36 minutes ago -
Steps to take before updating to 24H2
by
Susan Bradley
8 hours, 8 minutes ago -
Which Web browser is the most secure for 2025?
by
B. Livingston
3 hours, 10 minutes ago -
Replacing Skype
by
Peter Deegan
10 hours, 40 minutes ago -
FileOptimizer — Over 90 tools working together to squish your files
by
Deanna McElveen
14 hours, 10 minutes ago -
Excel Macro — ask for filename to be saved
by
nhsj
22 hours, 37 minutes ago -
Trying to backup Win 10 computer to iCloud
by
SheltieMom
1 hour, 35 minutes ago -
Windows 11 Insider Preview build 26200.5570 released to DEV
by
joep517
2 days, 20 hours ago -
Windows 11 Insider Preview build 26120.3941 (24H2) released to BETA
by
joep517
2 days, 22 hours ago -
Windows 11 Insider Preview Build 22635.5305 (23H2) released to BETA
by
joep517
2 days, 22 hours ago -
No April cumulative update for Win 11 23H2?
by
Peobody
1 day, 10 hours ago -
AugLoop.All (TEST Augmentation Loop MSIT)
by
LarryK
2 days, 22 hours ago -
Boot Sequence for Dell Optiplex 7070 Tower
by
Serge Carniol
3 days, 13 hours ago -
OTT Upgrade Windows 11 to 24H2 on Unsupported Hardware
by
bbearren
3 days, 17 hours ago -
Inetpub can be tricked
by
Susan Bradley
2 days ago -
How merge Outlook 2016 .pst file w/into newly created Outlook 2024 install .pst?
by
Tex265
2 days, 11 hours ago -
FBI 2024 Internet Crime Report
by
Alex5723
3 days, 21 hours ago -
Perplexity CEO says its browser will track everything users do online
by
Alex5723
1 day, 6 hours ago -
Login issues with Windows Hello
by
CWBillow
4 days, 8 hours ago -
How to get into a manual setup screen in 2024 Outlook classic?
by
Tex265
3 days, 20 hours ago -
Linux : ARMO rootkit “Curing”
by
Alex5723
4 days, 19 hours ago -
Employee monitoring app leaks 21 million screenshots in real time
by
Alex5723
4 days, 19 hours ago -
Google AI is now hallucinating idioms
by
Alex5723
4 days, 20 hours ago
Recent blog posts
Key Links
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.