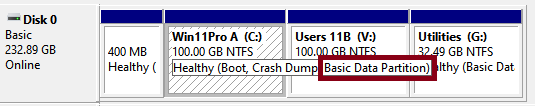
ON SECURITY By Susan Bradley Our audience consists of several different segments. As a result, there are many different risk levels. My risk tolerance
[See the full post at: Taming BitLocker and other encryption methods]
Susan Bradley Patch Lady/Prudent patcher