A good security suite will update its virus signatures and other data files and settings almost daily. To achieve maximum security protection against malware, these frequent “signature” updates are necessary.
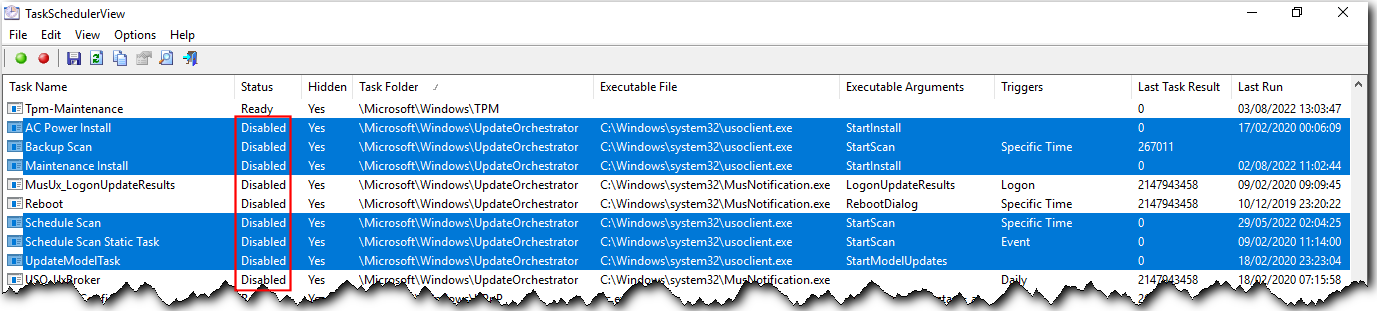
Microsoft Defender depends upon Windows Update to update its “signature” files. But if you disable or perhaps delay Windows Update in certain ways, Defender can go out of date, leaving your PC less secure.
There are ways to check the status of Defender to determine if your configuration is affected by this problem.
A workaround has been mentioned to fix this problem:
https://www.thewindowsclub.com/update-windows-defender-automatic-windows-updates-disabled
If you use a third-party antivirus solution instead of Defender, you are not affected by this Defender limitation. With the right third-party antivirus solution, these “signature” files can be automatically updated so discreetly, you never notice.
Any corrections/elaborations needed here?
Windows 10 22H2 desktops & laptops on Dell, HP, ASUS; No servers, no domain.