We start the new year off with – what else – vulnerabilities and some fixes. Windows 11 and 10 get releases today. Looks like 11 won’t get too many
[See the full post at: Ready for the new patching year?]
Susan Bradley Patch Lady/Prudent patcher

|
Patch reliability is unclear. Unless you have an immediate, pressing need to install a specific patch, don't do it. |
| SIGN IN | Not a member? | REGISTER | PLUS MEMBERSHIP |
Home » Forums » Newsletter and Homepage topics » Ready for the new patching year?
Tags: Patch Lady Posts
We start the new year off with – what else – vulnerabilities and some fixes. Windows 11 and 10 get releases today. Looks like 11 won’t get too many
[See the full post at: Ready for the new patching year?]
Susan Bradley Patch Lady/Prudent patcher
Hardened Windows user:
KB5034123 Cumulative Update for Windows 11 Version 23H2 for x64-based Systems
KB5033920 Cumulative Update for .NET Framework 3.5 and 4.8.1 for Windows 11, version 23H2 for x64
KB5033734 .NET 7.0.15 Security Update for x64 Client
KB890830 Windows Malicious Software Removal Tool x64 – v5.120
Updates took 2:38 from restart to login screen. No hiccups. I’ll wait for the push on my NAS and laptop. Links will open in a new tab.
Now running Windows 11 Pro Version 23H2 (OS Build 22631.3007)
My NAS and laptop got the push in the wee hours (after Active hours) this morning. They are not running identical software with my daily driver, so my NAS did not get KB5033734 .NET 7.0.15 Security Update for x64 Client.
My laptop got KB5033733 .NET 6.0.26 Security Update for x64 Client instead of KB5033734. All are now running Windows 11 Pro Version 23H2 (OS Build 22631.3007).
This update addresses a security vulnerability that could allow attackers to bypass BitLocker encryption by using Windows Recovery Environment (WinRE). For more information, see CVE-2024-20666.
IMPORTANT
Some computers might not have a recovery partition that is large enough to complete this update. Because of this, the update for WinRE might fail. In this case, you will receive the following error message:
Windows Recovery Environment servicing failed.
(CBS_E_INSUFFICIENT_DISK_SPACE)
FYI
There is a known issue relating to KB5034441 :
Known issue Because of an issue in the error code handling routine, you might receive the following error message instead of the expected error message when there is insufficient disk space:
0x80070643 – ERROR_INSTALL_FAILURE
This would explain the install error code 0x80070643 as reported by some of the posters below for KB5034441 and is not relating to .NET Framework.
HTH.
KB5034441 – Error 0x80070643. KB5034441 no longer appears in MS 2024-01 Updates, at the time of post.
I am Win10/Pro 22H2 x-64.
KB5034441 was in my WU queue today and I have used WUSHOWHIDE to hide it until MS-DEFCON is 3+
There was no ‘Error 0x80070643’ in the title or elsewhere.
I didn’t find the KB listed in the MS-Catalog, but I found something posted by Microsoft <here>.
It says that this KB addresses a vulnerability that could allow attackers to bypass BitLocker encryption by using Windows Recovery Environment, but I do not have BitLocker Encyrption turned on.
So, what does this all mean, given that I received no errorcode info when the KB appeared in the WU queue (or even after its appearance there) and given that I have BitLocker turned off???
This is one of those updates that make me grrrrrrrrr… It’s an OEM partition problem that neither Microsoft nor the OEMs will take responsibility for and make an easy tool to fix. I don’t know enough about who created the problem in the first place to point fingers, I just know that anytime I see a patch that won’t install and the resolution is that you have to use a third party tool to resize the partitions, I just want to go grab Satya and have him personally visit the homes of each impacted customer and see if he thinks Microsoft could make a tool to fix this. My bet is that after two or three home visits, he’d find a better way to fix this.
Susan Bradley Patch Lady/Prudent patcher
Could the partition issue fix (for some) be as simple as using the Disk Management snap-in (or, I believe, the diskpart command line utility) to accomplish what needs doing?
Just asking, that’s all.
EDIT/UPDATE: Turns out that you can use diskpart to change the partition size to accommodate the security update! Microsoft has detailed instructions here: https://support.microsoft.com/help/5028997. I just noticed this link in the article linked to above by @WCHS for KB5034441.
Hint: The instructions aren’t exactly for the faint of heart!
Windows Update error 0x80070643
The first Windows security updates of 2024 are here
Windows 10 version 22H2: 34 vulnerabilities, 2 critical and 32 important.
Windows Kerberos Security Feature Bypass Vulnerability — CVE-2024-20674
Windows Hyper-V Remote Code Execution Vulnerability — CVE-2024-20700Windows 11 version 22H2: 35 vulnerabilities, 2 critical and 33 important
same as Windows 10 version 22H2Windows 11 version 23H2: 35 vulnerabilities, 2 critical and 33 important
same as Windows 10 version 22H2..Windows Server products
Windows Server 2008 R2 (extended support only): 19 vulnerabilities: 1 critical and 18 important
Windows Kerberos Security Feature Bypass Vulnerability — CVE-2024-20674Windows Server 2012 R2 (extended support only): vulnerabilities: critical and important
No informationWindows Server 2016: 26 vulnerabilities: 1 critical and 25 important
same as Windows Server 2008 R2Windows Server 2019: 33 vulnerabilities: 2 critical and 31 important
same as Windows Server 2008 R2, plus
Windows Hyper-V Remote Code Execution Vulnerability — CVE-2024-20700Windows Server 2022: 36 vulnerabilities: 2 critical and 34 important.
same as Windows Server 2019
Now running Windows 11 Pro Version 23H2 22631.3007
2024-01 Cumulative Update for Windows 11 Version 23H2 for x64-based Systems (KB5034123)
2024-01 Cumulative Update for .NET Framework 3.5 and 4.8.1 for Windows 11, version 23H2 for x64 (KB5033920)
2024-01 .NET 8.0.1 Security Update for x64 Client (KB5033741)
2024-01 .NET 7.0.15 Security Update for x64 Client (KB5033734)
Windows Malicious Software Removal Tool x64 – v5.120 (KB890830)
All were installed without incident.
--Joe
FYI
1) .NET Framework January 2024 Security and Quality Rollup
2) .NET January 2024 Updates – .NET 8.0.1, 7.0.15, .NET 6.0.26
The updates contain both security and non-security improvements.
HTH.
Well, the announcement for the Framework January updates, whose link you posted above, begs to disagree with you:
Quality and Reliability
There are no new Quality and Reliability Improvements in this update.
If there are improvements in this month’s Framework releases besides the security hole fixes, nobody bothered telling the person who posted the article you linked to!
I had KB5034441 fail on 3 machines before reading here about the issue.
MSFT shows how to manually resize the recovery partition to make room for for WinRE here: https://support.microsoft.com/en-us/topic/kb5028997-instructions-to-manually-resize-your-partition-to-install-the-winre-update-400faa27-9343-461c-ada9-24c8229763bf . Kind of complicated.
So, I chose to use Mini-Tool Partition 12 free to reduce the size of the OS partition by 250 MB and increase the recovery partition by 250mb. Then my update went through. (BTW, I have NO third party recovery partitions on any of my computers.)
Philip, I should have followed your example with Mini-Tool Partition 12, but I chose instead to follow the instructions in the MS article, shrinking my boot partition 250MB, deleting the recovery partition, then recreating it to accommodate the additional 250MB. (My boot partition is partition1, and the recovery partition was partition2.) Everything worked as described in the article, except it re-enabled WinRE in boot partition1 instead of in the new and expanded recovery partition2. I now have a “Recovery” folder on my C: drive. I reran Windows Update and KB5034441 finally installed successfully. Will having WinRE assigned to my boot partition1 matter, and if so, is there a way to reassign WinRE to the new partition2?
This is unacceptable. MS will have to address this. We should not risk our computers just to be able to install an update! Pull it or fix it MS!
Seems to affect many: https://www.reddit.com/r/Windows10/comments/192l9kj/cumulative_updates_january_9th_2024/
So, I chose to use Mini-Tool Partition 12 free to reduce the size of the OS partition by 250 MB and increase the recovery partition by 250mb
This can be done only if both partitions are consecutive. Mine are not. Recovery is first partition , C partition is third partition.
This is not strictly true, although the process is not as simple as Philip describes. Partition Wizard allows you to specify whether the unallocated space will be before the partition or after it. In your case, you need to put it before the C partition. You can then select the second partion and move the unallocated space from after to before that partition. Lastly, you will select the Recovery partition and incorporate the unallocated space located after the partition. It’s convoluted, but I have done it before. It can be done in one operation or multiple operations.
This can be done only if both partitions are consecutive. Mine are not. Recovery is first partition , C partition is third partition.
Windows Recovery Environment can be anywhere one wishes it to be. Mine is in partition 1 (which I made 1G in size) on a SSD separate from the SSD with my OS partition.
Get information about your Windows RE by opening an elevated Command Prompt, typing
reatentc /info
and hit Enter. You’ll get something like this:
C:\Windows\System32>reagentc /info
Windows Recovery Environment (Windows RE) and system reset configuration
Information:
Windows RE status: Enabled
Windows RE location: \\?\GLOBALROOT\device\harddisk5\partition5\Recovery\WindowsRE
Boot Configuration Data (BCD) identifier: 215ceeaa-7c2d-11ee-ade0-cfc79b94deb9
Recovery image location:
Recovery image index: 0
Custom image location:
Custom image index: 0
REAGENTC.EXE: Operation Successful.
My computers show the following GPT partitions according to MiniTool Partition Wizard Free 12.8 after the modification:
[(Other) 128 MB] [(FAT32) 100 MB] [C: (NTFS) 231.9 GB] [(NTFS) 776 MB] <— was 526 MB
The last partition is the WinRE recovery partition. Three of my computers were installed with an MSFT iso image. One of them was an upgrade from Win7 Pro.
I was under the impression this was the standard layout. I do take backup images with Acronis and Macrium, which would allow me to recover, modify or re-order the partitions as well. As any partition tool will warn you, IT IS HIGHLY RECOMMENDED THAT YOU HAVE A BACKUP before making any changes.
In “my” case, it really was as easy as reducing the OS by 250MB and increasing the WinRE recovery size by 250MB. I did this on four of my computers using MiniTool Partition. I have one HP laptop running Win 10 Pro that did not need the resizing.
If the order is different from mine, zat_so’s method sounds like a good option, or recovering from a backup image, where the partition size is modified, is another option.
I do take backup images with Acronis and Macrium, which would allow me to recover, modify or re-order the partitions as well.
No, it won’t. You can’t manually create Restore and EFI partitions and allocate them after C: partition.
I do take backup images with Acronis and Macrium, which would allow me to recover, modify or re-order the partitions as well.
No, it won’t. You can’t manually create Restore and EFI partitions and allocate them after C: partition.
I was just going by what I’ve read in the Acronis KB. This example shows rearranging the partitions upon restore. But maybe there are limitations as you point out.
Dragging partitions from the source to the destination disk:
Alternatively, you can drag partitions from the source to the destination manually. This allows you to reorder the partitions as they are copied to the destination.
Alternatively, you can drag partitions from the source to the destination manually. This allows you to reorder the partitions as they are copied to the destination.
How does it rearrange partitions ? If I drag first the C backup from the image it will restore to current C partition not creating a C partition at the beginning of the destination drive.
Rearranging partitions can be done only if I format the drive prior to restoring.
* I don’t use Bitlocker.
Rearranging partitions can be done only if I format the drive prior to restoring.
I have no experience with Acronis or Macrium, I use Image For Windows, and I can restore an image to any partition I choose, as long as there is room, no format necessary. If there’s not enough room, I can use BootIt UEFI to make room. BootIt UEFI can also create/restore images.
In all of the discussions about increasing the size of the recovery partition, there has been talk about increasing the size by 250MB.
Nobody has said what the partition size SHOULD be for KB5034441 to install correctly.
Does anybody know what the minimum size MUST be?
On one of my computers the recovery partition is 854MB with 274MB free.
On another the recovery partition is 8.5GB and has 793MB free.
Does anybody know what the minimum size MUST be?
See https://www.askwoody.com/forums/topic/real-world-info-about-installing-kb5034441-on-windows-10/
Updated three Win11 22H2: HP low end desktop hardware install, M1 MacMini and M2 MacBook Pro in Parallels VMs.
KB5034123 2024-01 CU
KB5033290 2024-01 CU .NET Framework 3.5/4.8.1
Defender updates
No problems with these. On to Win10 and Win8.1
Update:
The HP low end desktop hardware install updated without any errors. However, when I went back and checked the Win RE, it had not updated. It was in Part 4 after the OS. It was 584MB with only 55MB free. So I restored the last Macrium image had before updating and I ended up using Mini Tool Partition Wizard Free to resize it to 1.07GB (a 500MB bump). Running the 2024-01 CU also updated the Win RE.
The Win RE on the two Parallels VM (Win11 on ARM) updated without having to resize.
FYI
2 Windows 10 Home v22H2 systems (one x64 and another x86 system)
————————————————————————
After Macrium Reflect System Image (including WinRE Partitions) backup were completed, resumed updates via Windows Update and successfully installed the following:
(a) Windows Malicious Software Removal Tool x64 (x86) – v5.120 (KB890830)
(b) 2024-01 Cumulative Update for .NET Framework 3.5 and 4.8.1 for Windows 10 Version 22H2 for x64 (x86) (KB5034275)
(c) 2024-01 Security Update for Windows 10 Version 22H2 for x64 (x86)-based Systems (KB5034441)
(d) 2024-01 Cumulative Update for Windows 10 Version 22H2 for x64 (x86)-based Systems (KB5034122)
For the x64 system, Windows Update installed the (b) patch first and duly prompted for a restart. The other 3 patches were held under the status “Pending Download” due to the “metered connection” ON status. After the restart, Windows Update proceeded to download and install the other 3 patches after hitting the “Download” button. A 2nd restart is required.
For the x86 system, Windows Update also installed the (b) patch first but there was no restart prompt. The other 3 patches were also held under the status “Pending Download” due to the “metered connection” ON status. Hit the “Download” button to complete the install of the rest of the patches. Only 1 restart required.
New OS Build 19045.3930.
1) Clarification : The 2024-01 Cumulative Update for .NET Framework 3.5 and 4.8.1 for Windows 10 Version 22H2 is listed under the parent Knowledge Base heading (KB5034275) and is recorded in ‘Settings>Windows Update>View Update History’. However, the actual specific .Net Framework CU installed is (KB5033918) and is listed under ‘Control Panel>All Control Panel Items>Programs and Features>View Installed Updates’ instead.
Refer to the tables listed in .NET Framework January 2024 Security and Quality Rollup.
2) Did not use the Registry Entry for disabling Copilot. Copilot did not appear in January 2024. Copilot started deployment in Decenber 2023.
3) A quick check both BEFORE and AFTER patching on the Windows Recovery Environment (WinRE) partition for both Systems with the “reagentc /info” and “Dism /Get-ImageInfo /ImageFile:\\?\GLOBALROOT\device\harddisk0\partition”X”\Recovery\WindowsRE\winre.wim /index:1” (where “X” is the partition number from the output of “reagentc /info”) commands confirmed that the WinRE partition were updated and modified on patching date with the “ServicePack Build : 3920” updated from “ServicePack Build : 3562” previously.
A restart via Settings > Update & Security > Recovery > Advanced Startup runs as expected.
After patching, another check on these WinRE partitions via the “Partition Explorer” tab of MiniTool Partition Wizard Free 12.8 (portable version) also confirmed that the “winre.wim” file (548.75MB for x86 system and 624.85MB for x64 system) were modified on patching date.
For the x64 system the WinRE partition is located as the last partition (1024MB with 672.10MB used) with a large adjoining unallocated space (65GB) available for any future expansion. That’s leftover space from cloning to a larger SSD in the past.
For the x86 system which was an upgrade from Windows 7, the WinRE partition was re-purposed from the original Windows 7 OEM Recovery partition located as the first partition (13GB with 9.77GB used) which I believe is still more than adequate for any future updates to the WinRE by Microsoft.
Both systems do NOT have Bitlocker available and the KB5034441 patch may have not been relevant at all. Maybe more relevant and frequent updates to the WinRE is also in store in the future. Shall look forward to Askwoody for guidance then.
4) Passed both the DISM Restorehealth and SFC Checks before and after patching. Both Windows 10 Home systems are running stable since patching 4 days ago.
HTH.
Hi Susan:
Windows Update successfully installed all updates offered for the January 2024 Patch Tuesday on my Win 10 Pro v22H2 laptop, including the KB5034441 Windows Recovery Environment (WinRE) update, and I haven’t observed any negative effects so far. This includes:
As usual, I observed the early “Restart Now” glitch this month that almost always occurs when Windows Update delivers a .NET Framework update with my other my Patch Tuesday updates (see the attached image). This month’s cumulative KB5034122 Quality Update seemed to get stuck when the Status reached “Downloading: 100%”, but I checked again about 10 min later and the Status had changed to “Pending Restart”.
As noted above, I did not see the error described in your 09-Jan-2024 post 0x80070643 – ERROR_INSTALL_FAILURE with KB5034441 while installing my WinRE update KB5034441. Prior to installing my Jan 2024 Patch Tuesday updates the reagentc /info and fsutil volume diskfree commands showed that my WinRE partiton (harddisk0/partition4) had 123.0 MB of free space, and the Dism /Get-ImageInfo command described in the section “Check the WinRE Image Version” of the MS support article Add an Update Package to Windows RE showed my WinRE image winre.wim was Version 10.0.19041 / ServicePack Build 3562 and had a size of 3.791 GB – see the attached images.
After successfully installing KB5034441 the fsutil volume diskfree command shows that the free space on my WinRE partition only decreased by ~ 26 MB to 96.7 MB …
… and the Dism /Get-ImageInfo command shows my WinRE image is now Version 10.0.19041 / ServicePack Build 3920 and has a size of 3.862 GB.

————-
Dell Inspiron 5584 * 64-bit Win 10 Pro v22H2 build 19045.3930 * Firefox v121.0.1 * Microsoft Defender v4.18.23110.3-1.1.23110.2 * Malwarebytes Premium v4.6.8.311-1.0.2242 * Macrium Reflect Free v8.0.7783
Windows Update successfully installed all updates offered for the January 2024 Patch Tuesday on my Win 10 Pro v22H2 laptop, including the KB5034441 Windows Recovery Environment (WinRE) update, and I haven’t observed any negative effects so far.
and what about BitLocker … was it turned ON prior to your running KB5034441?
Windows Update successfully installed all updates offered for the January 2024 Patch Tuesday on my Win 10 Pro v22H2 laptop, including the KB5034441 Windows Recovery Environment (WinRE) update …
and what about BitLocker … was it turned ON prior to your running KB5034441?
Hi WCHS:
No, BitLocker was (and still is) turned OFF.
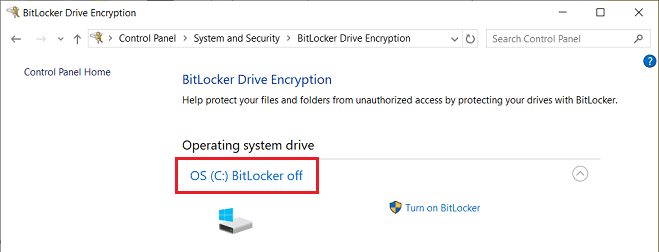
—————
Dell Inspiron 5584 * 64-bit Win 10 Pro v22H2 build 19045.3930 * Firefox v121.0.1 * Microsoft Defender v4.18.23110.3-1.1.23110.2 * Malwarebytes Premium v4.6.8.311-1.0.2242 * Macrium Reflect Free v8.0.7783
Windows Update successfully installed all updates offered for the January 2024 Patch Tuesday on my Win 10 Pro v22H2 laptop, including the KB5034441 Windows Recovery Environment (WinRE) update, and I haven’t observed any negative effects so far.
and what about BitLocker … was it turned ON prior to your running KB5034441?
If you are asking about if the actual bitlocker service “BDESVC” is running here is what I see on my system. Not sure if you referred to the actual service running or if bitlocker was turned on on the disk.
After the KB5034441 winre update I finally got to install, I noticed that in services console, bitlocker service BDESVC is running as a service, but it is not turned on.
I don’t recall the BDESVC service being running before this update, but I might be mistaken.
It is set in services to be manually triggered, to run, but not sure what is triggering it, when I run the command “manage-bde -status” in an elevated command prompt window, it clearly shows my drives are fully decrypted, and bitlocker is turned off.
I’ve never used bitlocker, I do not use TPM or secure boot either though my system is UEFI with GPT.
So I cannot say for sure if it is perhaps default for the BDESVC to be triggered or running when it is not being used. I just do not recall ever seeing the actual bitlocker service module BDESVC running within services before, seems like maybe the service is running in case you decide to turn on bitlocker on the disk. Not really sure.
After the KB5034441 winre update I finally got to install, I noticed that in services console, bitlocker service BDESVC is running as a service, but it is not turned on. I don’t recall the BDESVC service being running before this update, but I might be mistaken. … I’ve never used bitlocker, I do not use TPM or secure boot either though my system is UEFI with GPT.
Hi unstablecomic:
My experience with the BitLocker Drive Encryption Service (BDESVC) is slightly different.
After Windows Update successfully installed the KB503441 WinRE update on my Win 10 Pro v22H2 laptop (no WinRE partition resizing required, BitLocker Drive Encryption turned OFF at Control Panel | System and Security | BitLocker Drive Encryption before and after KB503441 installed – see my post # 2628138 and post # 2628191 in this topic) Windows Services shows that my BitLocker Drive Encryption Service also has a Startup Type of Manual (Trigger Start) but the Status shows that this service does not run after my system is booted up.
Both my BitLocker tasks in Task Scheduler (Task Scheduler Library | Microsoft | Windows | BitLocker) have a Last Run Result of 0x41303 (Task has not yet run).
I don’t believe it’s relevant, but if I open a Run dialog box (Windows+R keys) and enter tpm.msc to open the TPM Management Tool it shows that I have TPM 2.0 and that the status is “The TPM is ready to use”. If I open a Run dialog box and enter msinfo32 to open the System Information panel I can see the value of my “Secure Boot State” is OFF.
—————–
Dell Inspiron 5584 * 64-bit Win 10 Pro v22H2 build 19045.3930 * Firefox v121.0.1 * Microsoft Defender v4.18.23110.3-1.1.23110.2 * Malwarebytes Premium v4.6.8.311-1.0.2242 * Macrium Reflect Free v8.0.7783
Thank you for your info, and for taking the time to reply. I just checked my task scheduler and it also shows like your, Bitlocker has never been run.
In Services, BDESVC is always running, but not turned on. I think the service is triggered in case a person decides to turn on the service and encrypt a drive.
I can disable the actual service, but uses little memory and doesn’t bother anything that I can tell, I just do not recall if it used to run in services before the winre update. It is possible the BDESVC is now triggered by default, interesting though that your service is not running on your laptop. I have a Dell desktop, OPtiplex 9020 SFF, Win 10 22H2.
According to the chart at How to Restore Default Services in Windows 10, the default setting for the BitLocker Drive Encryption Service (BDESVC) is “Manual (Trigger Start)” and it’s normal status is not running.
If it’s always running on your system, then something is manually triggering it to start even if you’re not using it .
In Services, BDESVC is always running, but not turned on…I have a Dell desktop, OPtiplex 9020 SFF, Win 10 22H2
Hi unstablecomic:
If you mean that your BitLocker Drive Encryption Service (BDESVC) also has a Startup Type of Manual (Trigger Start) then there must be some trigger that is causing that service to start at boot-up on your OptiPlex 9020.
Do you have a Home or Pro edition of Win 10 v22H2, and do you log in to Windows with a local or Microsoft Account? That might explain, at least in part, why BitLocker Drive Encryption Service (BDESVC) behaves differently at startup on our Dell computers.
I log in with my Microsoft Account and I have the Pro edition of Win 10 on my Inspiron laptop, which means my system can use the “standard” BitLocker drive encryption that is managed at Control Panel | System and Security | BitLocker Drive Encryption | Manage BitLocker. BitLocker is currently turned OFF on my system but it gives me the option of encrypting a single drive if more than one drive is installed.
If you have a Home edition of Win 10 then your system does not have the “standard” BitLocker drive encryption but uses a subset of BitLocker called device encryption. If device encryption is available on a Win 10 Home edition it can be turned on or off at Settings | Update & Security | Device Encryption *** (NOTE: I do not have that setting on my Win 10 Pro machine). Device encryption encrypts your entire system and you can’t exclude a drive or partition.
*** For Win 11 Home go to Settings | Prvacy & Security | Device Encryption.
You might also be interested in reading WCHS’ Aug 2022 Why is Bitlocker Waiting for Activation?. WCHS has a Dell Inspiron 5482 2-in-1 but there are also comments in post # 2474243 in that topic from glnz about their two OptiPlex 7000 towers. Dell uses some very convoluted rules to decide how encryption is “staged” at the factory depending on the computer model, OS and hardware – see the Dell support article Automatic Windows Device Encryption or BitLocker on Dell Computers as well as System Does Not Meet BitLocker Automatic Device Encryption Requirements that is specific to OptiPlex 3060, 5060, 7060 and XE3 systems running Win 10 Pro.
I know of several Dell computer users who were prompted to enter their 48-digit BitLocker recovery key at boot-up after they installed KB5012170 (Security Update for Secure Boot DBX: August 9, 2022) with their Aug 2022 Patch Tuesday updates (see Eric Koch’s 28-Aug-2022 Windows PIN Unavailable / Bitlocker Asking for Recovery Key in the Dell Inspiron board for one example) and none of these users knew that BitLocker had been enabled on their Dell computer.
—————-
Dell Inspiron 5584 * 64-bit Win 10 Pro v22H2 build 19045.3930 * Firefox v122.0.0 * Microsoft Defender v4.18.23110.3-1.1.23110.2 * Malwarebytes Premium v4.6.8.311-1.0.2249 * Macrium Reflect Free v8.0.7783
Hi unstablecomic:
Thx for posting. I too have an Optiplex 9020 USFF. Win 10 Pro 22H2. I don’t use Bitlocker, it is OFF.
I checked my bitlocker drive encryption service (BDESVC) via ‘run’ services.msc today prior to installing the January windows updates. I can confirm mine was NOT running, and setting was ‘manual-trigger start’.
After the updates installed, BDESVC sustained that setting (not running, manual-trigger) after updates. However, I did NOT install KB5034441 (had hidden with winshowhide.) I am Uefi/GPT as well. Bitlocker never used, is OFF; I use a local account. I have TPM 1.2 & Secure Boot is on. I’m sure you have it sorted, simply wanted to let you know my Optiplex experience.

Donations from Plus members keep this site going. You can identify the people who support AskWoody by the Plus badge on their avatars.
AskWoody Plus members not only get access to all of the contents of this site -- including Susan Bradley's frequently updated Patch Watch listing -- they also receive weekly AskWoody Plus Newsletters (formerly Windows Secrets Newsletter) and AskWoody Plus Alerts, emails when there are important breaking developments.
Welcome to our unique respite from the madness.
It's easy to post questions about Windows 11, Windows 10, Win8.1, Win7, Surface, Office, or browse through our Forums. Post anonymously or register for greater privileges. Keep it civil, please: Decorous Lounge rules strictly enforced. Questions? Contact Customer Support.
Want to Advertise in the free newsletter? How about a gift subscription in honor of a birthday? Send an email to sb@askwoody.com to ask how.
Mastodon profile for DefConPatch
Mastodon profile for AskWoody
Home • About • FAQ • Posts & Privacy • Forums • My Account
Register • Free Newsletter • Plus Membership • Gift Certificates • MS-DEFCON Alerts
Copyright ©2004-2025 by AskWoody Tech LLC. All Rights Reserved.
Notifications